
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Psychol. , 24 August 2023
Sec. Personality and Social Psychology
Volume 14 - 2023 | https://doi.org/10.3389/fpsyg.2023.1124308
Introduction: Activating people’s sense of attachment security can buffer against psychological threats. Here we tested whether security priming can also buffer the adverse effects of stereotype threat among women.
Method: Three studies (a pilot study (N = 79 women, 72 men), a laboratory study; N = 474 women, and an online study; N = 827 women) compared security priming to neutral and positive affect priming.
Results: The pilot study revealed that women exposed to attachment security primes (e.g., the word “love”) had better math performance than women exposed to neutral primes (e.g., “boat”). Men’s math performance did not differ across priming conditions. Study 1 revealed that women showed better math performance in the attachment security priming condition than in the neutral or positive (e.g., “luck”) priming conditions. The effect was observed among women high on math identification. In Study 2, despite an effect of security priming on the manipulation check [higher State Adult Attachment Measure (SAAM) security score], security did not buffer stereotype threat effects.
Discussion: Our findings provide partial support to the idea that security priming (an interpersonal process) can buffer stereotype threat (an intergroup process). Theoretical and practical implications related to attachment security priming and stereotype threat are discussed.
Attachment theory is one of the most productive and interdisciplinary theories in psychology (for overviews, see Gillath et al., 2016; Cassidy and Shaver, 2018). According to the theory, people are equipped with an attachment system, which is activated when people encounter actual or symbolic threats in their environment. Once activated, the system motivates people to seek proximity to stronger wiser others termed “attachment figures”—often primary caregivers in infancy and childhood, and romantic partners/spouses or best friends in adulthood (Bowlby, 1969/1982). Being close to a supportive attachment figure makes people feel safe and secure, allowing them to regulate their emotions (“safe haven”) and explore the environment (“secure base”).
According to Ainsworth et al. (1978), people have different attachment styles—the way people think, feel, and behave in their close relationships. When a person’s attachment figures are consistently accessible and supportive, the person is likely to develop a secure attachment style. When attachment figures are not supportive, but instead are cold and rejecting, a person is more likely to develop an insecure avoidant style. Finally, when attachment figures are inconsistent (sometimes helpful and sometimes not) and intrusive in their caring, a person is more likely to develop an insecure anxious attachment style.
In the laboratory, researchers can make people feel more secure or insecure using attachment security primes. For example, researchers can expose participants to the names of their attachment figures or words such as “love” and “hug” (e.g., Gillath et al., 2010). Such priming can temporarily activate mental representations of attachment security, making participants feel, think, and behave like secure people (Gillath et al., 2022). Activating the sense of attachment security through exposure to security cues (security priming) increases people’s ability to constructively cope with internal and external stressors (Gillath et al., 2008) by buffering against threats (Gillath and Hart, 2010). For example, in one set of studies (Shaver and Mikulincer, 2007), participants were first exposed to either attachment security or neutral primes and then to either control or threat cues (e.g., threats to participants’ self-esteem or cultural worldviews). Exposure to threat cues led to a defensive derogation of outgroup members among participants in the neutral condition but not in the attachment security condition. Security primes did not affect the responses of participants who were not threatened, suggesting that activating attachment security may play an especially significant role in the face of threats (Mikulincer et al., 2001b).
Assuming that the attachment system helps coping with psychological threats, we tested whether exposure to attachment security primes would buffer against one specific psychological threat among women. Namely, stereotype threat—the state experienced by people who are, or feel themselves to be, at risk of conforming to the negative stereotypes about their social group (Steele, 1997).
Stereotype threat may be conceptualized as a self-fulfilling prophecy, in which common negative perceptions about people’s social group “get under their skin” (see Goffman, 1963), leading to adverse psychological outcomes. For women, studying and being tested in STEM fields can be psychologically threatening due to the concern about confirming negative stereotypes regarding their gender’s math ability (Spencer et al., 2016). The experience of stereotype threat, in turn, might undermine the performance of women in math (see Walton and Spencer, 2009, for a meta-analysis). Admittedly, as a part of the replication crisis in social psychology (Open Science Collaboration, 2015), the magnitude of stereotype threat effects on women’s and girls’ math performance, and even the very existence of such effects, has been questioned (e.g., Ganley et al., 2013; Flore and Wicherts, 2015). Nevertheless, a non-zero effect such that women underperform when under threat (as compared to when not threatened) seems to be supported (Shewach et al., 2019)—justifying further research on this topic.
Existing research on stereotype threat has focused on providing an in-depth understanding of this phenomenon [e.g., Schmader et al.’s (2008) integrated process model] and on identifying interventions to reduce it. According to Liu et al.’s (2021) taxonomy, there are three types of interventions: identity-based interventions—which alter the strength or salience of one’s association with the negatively stereotyped ingroup, belief-based interventions—which change one’s belief(s) about the negative stereotype, and resilience-based interventions—which increase one’s ability to respond to the stressful situation in more adaptive ways by effectively regulating one’s emotions, approaching the task without self-defeating cognitions, or improving self-confidence.
We theorized that priming attachment security might serve as a resilience-based intervention, as it has been shown to improve people’s coping with psychological threats through changing their emotion regulation strategy use (e.g., Troyer and Greitemeyer, 2018), modulating intruding negative thoughts (e.g., Bryant and Chan, 2017), and promoting a more positive self-view (e.g., Carnelley and Rowe, 2007). Security priming also promotes self-confidence and autonomous exploration (Bowlby, 1969/1982). Therefore, we predicted that the exposure of women to attachment security cues would reduce the effects of stereotype threat on their math performance.
Our prediction is consistent with research showing that, due to their membership in a negatively stereotyped group, women become sensitive to situational cues that signal their inadequacy within potentially threatening situations (Murphy et al., 2007). Consequently, subtle situational cues have far-reaching effects on their thoughts, feelings, and performance. For example, the virtual classroom design (Cheryan et al., 2011) studied how stereotype threat affected women’s (but not men’s) interest and anticipated success in computer science. Thus, women’s level of interest and anticipation of success was lower in “geeky” classrooms (e.g., with Star Trek posters) as compared to non-geeky classrooms (Cheryan et al., 2011). Similarly, women’s (but not men’s) performance was affected by the gender composition of the group in which they took a math test. Specifically, their performance was impaired when outnumbered by men (Inzlicht and Ben-Zeev, 2000). While some situational cues increase the experience of stereotype threat, we reasoned that other situational cues might decrease it.
Theoretically, the present research seeks to extend attachment theory by integrating it with the stereotype threat literature. Research on attachment theory is highly diverse, and covers areas such as infant-parent relationships, social schemas, affect regulation, romantic love, marital functioning, group dynamics, prejudice, and intergroup relations (for a review, see Gillath et al., 2016). Nevertheless, the present research is the first to examine whether the attachment system may play a role in coping with a negatively stereotyped identity.
A pilot and two studies investigate whether security primes can buffer stereotype threat effects. In the pilot, men and women were exposed to either security or neutral primes before taking a math test. We expected women, but not men, in the neutral priming condition to score lower on the math test in the presence of threat compared to women and men in the security priming condition. In Study 1, we compared the effects of attachment-security priming to positive priming to rule out the possibility that any positive prime would reduce stereotype threat effects. Another goal of Study 1 was to test the moderating effects of math identification. People who strongly identify with math (i.e., who perceived math as important and rewarding; Smith and White, 2001) are more vulnerable to stereotype threat since math is part of their self-concept (Schmader et al., 2008). High identifiers were expected to benefit more from the security priming than low identifiers. Finally, in Study 2, we used preregistration and a larger sample to increase confidence in our results. We expected participants who were exposed to stereotype threat and security priming to show less of a decrease in math performance than those who were exposed to threat and a neutral prime. We also expected the effects of the threat and the security priming to be most pronounced among participants who highly identify with math.
We tested whether exposure to attachment security primes buffers the negative effects of stereotype threat on women’s (but not men’s) math performance using a 2 [participant’s gender (woman, man)] × 2 [prime (attachment security, neutral)] design. The dependent variable was the performance on a difficult math test. To avoid a potential conflation between participants’ gender and their knowledge of math (as more men than women take math-related majors in high school and higher education; Ayalon, 2003), our analysis controlled for participants’ preexisting knowledge of math.
Participants were 79 women and 72 men undergraduate students at a large Israeli university, Mage = 24.0, SD = 2.9, from various disciplines, whose native tongue was Hebrew. They received academic credit for their participation. The sample size was determined by feasibility considerations; data collection was stopped when there were no new sign-ups.
Whereas in earlier research on stereotype threat (e.g., Spencer et al., 1999) only women in math-related majors were recruited (because the assumption was that individuals must identify with the stereotyped domain to experience stereotype threat; e.g., Aronson et al., 1999), we examined a diverse sample, in line with subsequent research (e.g., Schmader, 2002; see Shapiro and Neuberg, 2007, for a discussion of stereotype threat effects among individuals who do not identify with a particular negatively stereotyped domain). More than half of the participants (38 women and 52 men) had math-related majors (e.g., engineering). The rest (41 women and 20 men) had majors that were not math-related (e.g., social sciences).
The study, presented as “research on personality and academic performance,” consisted of two sessions. In the first session, participants individually completed an online survey, in which they reported their academic major (coded as “1” for math-related majors, and “0” for other majors), psychometric exam score [the Israeli equivalent of the Scholastic Aptitude Test (SAT) in the U.S. academic system], and their matriculation math exam’s difficulty level (“Yehidot Limod” ranging from three to five). Participants’ academic major, psychometric score, and math exam difficulty level were used as a proxy assessment of their preexisting math knowledge (e.g., acquaintance with relevant mathematical formulas). Participants also completed several background measures, such as the Experience in Close Relationship scale (ECR; Brennan et al., 1998), assessing attachment style along the dimensions of avoidance and anxiety.1 The full protocol and data are available via OSF: https://osf.io/2gd6y/?view_only=fcc001c569ed42d987303301526d73e7.
The second session was a laboratory experiment, carried out in groups of three to seventeen participants (depending on the sign-up) one week after the first session. About half of the participants in each session were women (52.3% female, SD = 18.5%). Participants first completed a priming task where they were asked to rate 20 pairs of furniture (e.g., “table” and “chair”) in terms of their degree of association on a 7-point scale (1 = not at all to 7 = very much). Participants were randomly assigned to one of two priming conditions such that before seeing each pair of furniture they were exposed either to neutral words (e.g., “boat,” “rug”) or to words, with matching length and frequency (in Hebrew), representing attachment security (e.g., “love,” “hug”). The prime was displayed in black lettering over a white background in the screen’s center for 22 ms, followed by a 500 ms mask (a visual noise pattern) and then by the names of the two pieces of furniture, separated by a hyphen (e.g., “cabinet-chair”). This task was successfully used before in various studies (e.g., Gillath et al., 2010).
Note that following the priming task, participants were asked whether they had noticed any words or letters that are not furniture pieces. More than half of the participants (63%) indicated that they had noticed such words or letters, and in most cases were able to generate at least one of the primed words. We included all participants because, according to Gillath et al. (2022), subliminal and supraliminal attachment security priming result in similar outcomes. Furthermore, our theorizing does not imply that the priming must be subliminal—we used this particular manipulation simply due to our wish to use a priming technique that was established in previous research.2
Following the priming task, participants completed a difficult math test composed of 30 multiple choice questions (see Kahalon et al., 2018, for the use of this test among Israeli women). To assure that the effects of the prime would last throughout the test after participants completed the first half of the test (20 min) they completed the priming task again. Participants then had additional 20 min to complete the second half of the test. Participants earned one point for each correct answer.
Next, participants completed the State Adult Attachment Measure (SAAM; Gillath et al., 2009). Consisting of 21 items and using a 7-point response scale. This measure captures situational fluctuations in people’s sense of attachment (in)security (e.g., “I feel like others care about me”). Note that the SAAM was developed such that security, avoidance, and anxiety should constitute different factors. However, because the differentiation between them was irrelevant for the purposes of the current study, we reverse coded the avoidance (e.g., “I’m afraid someone will want to get too close to me”) and anxiety (e.g., “I feel a strong need to be unconditionally loved right now”) items. This analytic approach is consistent with the theoretical conceptualization underlying the ECR coding (see Brennan et al., 1998), in which securely attached individuals are those low on the anxiety and avoidance dimensions. Then, participants’ responses were averaged to obtain a single SAAM score (α = 0.85).
This measure was used as a manipulation check, to verify that participants indeed felt greater security in the attachment security compared to the neutral prime condition. We did not administer the SAAM immediately after the priming manipulation—and before the math test—due to our concern that its items (e.g., “I feel loved”) might prime attachment security in both experimental conditions (by encouraging participants to think about their significant others) and thus interfere with the priming manipulation. Upon completion, participants were thanked and debriefed.
Means, SDs, and correlations are presented in Table 1. In line with previous reports (Ayalon, 2003), compared to women, men took more math-related majors (χ2 = 9.10, p = 0.003, V = 0.25) and more difficult math matriculation exams, t(149) = 2.14, p = 0.034, d = 0.68; and had higher psychometric scores, t(137) = 2.12, p = 0.040, d = 0.340. All three measures showed small to medium effect sizes, so the comparisons should be interpreted cautiously. To test our main hypothesis, we conducted a two-way analysis of covariance (ANCOVA) on participants’ math performance.3 The predictors were Gender (woman and man) and Prime type (security and neutral) and their interaction. Taking a math-related major, the difficulty of math matriculation exam, and psychometric scores were associated with participants’ math performance (see Table 1). We controlled for these variables to isolate the unique effects of priming condition on performance, which was the focus of the present inquiry (see Miyake et al., 2010, for the same analytic approach when testing the effects of a self-affirmation intervention on women’s math performance). To confirm randomization, the conditions were compared on attachment anxiety, attachment avoidance, psychometric score, math related major, math matriculation difficulty, and gender. No significant differences were found between the conditions. Results of this analysis are presented in the Supplementary material.
As seen in Table 2, which presents the obtained model, the Gender × Prime type interaction was in the expected direction but only marginally significant.4 Importantly, women’s math performance was higher in the attachment security condition than in the neutral condition, F(1,144) = 4.02, p = 0.047, η2p = 0.03, 90% CI [0.001, 0.084].5 In particular, Mdifference = 1.49, 95% CI [0.022, 2.967]. A sensitivity analysis [using Faul et al.’s (2009) calculator] revealed that for a 5% level of significance and a power of 80%, our actual sample size was sufficient to detect a minimum effect of d = 0.56; the observed effect size, d = 0.50, was somewhat below this minimum value.
Men’s performance did not differ across conditions, F(1,144) = 0.52, p = 0.473, η2p < 0.01, 90% CI [0.000, 0.037], Mdifference = 0.560, 95% CI [−0.979, 2.098]. Figure 1 illustrates the obtained pattern of results (note that the means presented in this figure are corrected for the covariates and hence different than the raw means presented in Table 1).
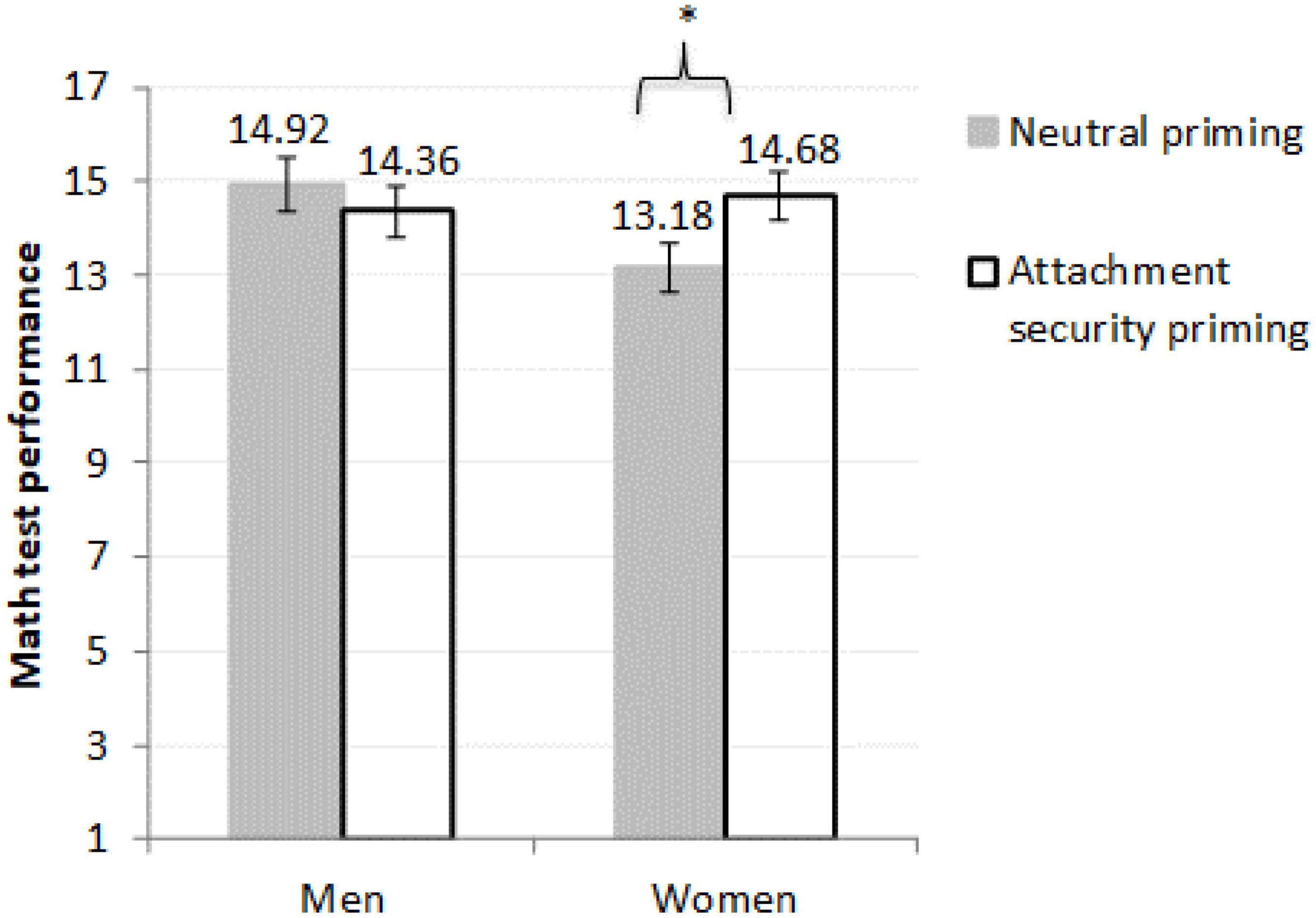
Figure 1. Mean number of correct answers and standard errors for math performance among women (N = 79) and men (N = 71) participants. Number of women = 79 and number of men = 71. Results are controlled for preexisting math knowledge. *Women in the secure priming condition scored significantly higher than women in the neutral condition [F(1,144) = 4.02, p = 0.047, η2p = 0.03].
As an alternative way to interpret this interaction, we compared women’s and men’s performance in each priming condition. We found that women performed worse than men in the control condition, F(1,144) = 4.93, p = 0.028, η2p = 0.03, 90% CI [0.002, 0.093], Mdifference = 1.733, 95% CI [0.190, 3.276]. Yet, the gender gap was eliminated in the attachment security condition, F(1,144) = 0.18, p = 0.674, η2p = 0.001, 90% CI [0.000, 0.027], Mdifference = 0.321, 95% CI [−1.828, 1.185]. This finding is consistent with the possibility that women experienced stereotype threat in the control condition (which led to the observed gender performance gap, evident even when controlling for preexisting knowledge in math), yet the exposure to attachment security primes in the experimental condition had buffered against stereotype threat effects—eliminating the gender gap in math performance.
As for the manipulation check (measured following the dependent variable), an ANOVA with participants’ SAAM score as the dependent variable revealed a significant difference between the Prime type conditions, F(1,147) = 4.35, p = 0.039, η2p = 0.028, 90% CI [0.001, 0.086], such that participants felt greater state security in the attachment security priming condition, M = 4.8, SD = 0.7, than in the neutral priming condition, M = 4.6, SD = 0.7. The effect of Gender and the Gender × Condition interaction were nonsignificant, Fs < 0.41, ps > 0.524, η2p < 0.003. These findings are consistent with the possibility that the priming manipulation induced participants with attachment security. Future studies should try to obtain bigger, more balanced groups of participants in each session if they are using the same method as we used here.
The pilot study provided initial support to our hypothesis that activating women’s attachment security can buffer the effects of stereotype threat on their math performance. Study 1 aimed to establish this effect using a sufficiently powered sample of women. It also aimed to demonstrate the uniqueness of this effect by testing whether women exposed to attachment security primes perform better not only compared to women exposed to neutral primes, but also to women exposed to positive affect primes that are unrelated to attachment security.
Performing a difficult math test might elicit negative thoughts and feelings among women (Keller and Dauenheimer, 2003; Cadinu et al., 2005). Possibly, the exposure to attachment security primes, which are more positive and pleasant than the neutral primes, simply elicited positive thoughts and feelings among women, leading to better math performance. The effects of attachment security primes, however, should stem from increasing one’s general sense of attachment safety (Mikulincer et al., 2005) rather than from the simple induction of positivity. To rule out positivity as an alternative explanation, women in Study 1 were exposed to attachment security-related primes (e.g., the word “love”), neutral primes (e.g., “lamp”), or positive primes unrelated to attachment (e.g., “luck,” “happiness”). These primes, which were matched in terms of length and language frequency (in Hebrew) and according to Mikulincer et al. (2001a) did not differ in terms of positive valence, were successfully used in previous research. We predicted that women’s math performance will be better in the attachment security priming condition than in the other priming conditions.
An additional goal of Study 1 was to explore the moderating role of domain identification. Women high in math identification suffer the most from stereotype threat both psychologically (Pronin et al., 2004) and in terms of their math performance (e.g., Keller, 2007; Kahalon et al., 2018). Thus, we tested whether the expected buffering effect of attachment security priming, compared to the other priming conditions, would be more pronounced among women who are high (vs. low) on math identification.
We tested our hypotheses among women using a three-cell experimental design [prime (attachment security, positive affect unrelated to attachment, and neutral)]. Our primary dependent variable was the performance on a math test. Consistent with the pilot study, to isolate the unique effect of the priming manipulation, we controlled for participants’ preexisting knowledge of math.
A power analysis using G*Power calculator (Faul et al., 2009) revealed that 368 participants were needed to detect a small effect size (f = 0.17, based on the size of the simple effect among women observed in the pilot study), at a significance of 5% and power of 80%. Note that the power analysis was conducted to detect the main effect of priming condition, not its moderation by math identification for which we had no a priori estimation. A sensitivity analysis indicated that our actual sample size was sufficient to detect a minimum interaction effect of f2 = 0.013. As reported below, the observed effect size, f2 = 0.010, was somewhat below this threshold. Participants were recruited through ads placed on campus and the university’s paid participant pool. They received 50 NIS (approximately 13 Euro or USD) in exchange for their participation. Data collection was stopped after the recruitment of 476 participants, once there were no new sign-ups. Participants were all women, undergraduate students, majoring in diverse disciplines (e.g., engineering, business); Mage = 23.6, SD = 2.7. All participants were Israeli, and their native tongue was Hebrew (17 bilingual).
The procedure was similar to that of the pilot study, except that, to minimize attrition, participants completed it in a single session (instead of two separate sessions). Upon their arrival at the lab, participants reported their math identification on a four-item, 7-point scale (e.g., “I enjoy math and math-related fields”; α = 0.82), as well as their academic major (“1” for math-related majors, “0” for other majors), psychometric exam score, and matriculation math exam’s difficulty level, which served as proxy assessments of their preexisting math knowledge. They also completed several background measures (e.g., the ECR; see data in the OSF).6
Next, to strengthen the experience of stereotype threat, which in the pilot study was assumed to be induced through the presence of male participants, participants were told that as a part of the study they would be asked to complete a difficult math test, the results of which would be used to assess gender differences in math ability and develop the test norms for women and men (these threatening instructions were adjusted from Johns et al., 2005). Before proceeding to the math test, participants completed the priming task in which they rated the similarity between pairs of furniture (see section “Pilot study”). They were randomly assigned to one of three conditions: exposure to words representing attachment security (e.g., “love”), positive words unrelated to attachment (e.g., “luck”), and neutral words (i.e., “boat”).
Next, participants had 15 min to complete a math test that included 30 difficult questions. The Hebrew version of this test, developed by Johns et al. (2005), was validated and used by Kahalon et al. (2020). Participants earned one point for each correct answer. As a manipulation check for priming attachment security, participants completed the SAAM (α = 0.83). Upon completion, participants were thanked and debriefed.
Means, SDs, and correlations are presented in Table 3. To test our main hypothesis, we conducted a regression analysis on participants’ math performance. The covariates (taking a math-related major, math matriculation difficulty and psychometric scores; standardized) were entered in the first step. Prime type [attachment-security vs. control (positive unrelated to attachment and neutral primes)] and math identification (standardized) were entered in the second step, and their two-way interaction was entered in the third step. Randomization was tested by comparing the prime condition on attachment anxiety, attachment avoidance, domain identification, psychometric score, math related major, and math matriculation difficulty. Attachment anxiety and math difficulty are the only measures which differed between conditions.7 Results are presented in the Supplementary material. two additional analyses, in which (a) the attachment security priming condition is compared to each of the control conditions separately, (b) the neutral priming condition is compared to each of the positive priming conditions (i.e., attachment-related and unrelated) separately, are reported in the Supplementary material. Since the effects of the positive and neutral primes were not significantly different from each other, and security priming marginally differed from both control conditions, we aggregated the two control conditions to increase statistical power.
As seen in Table 4, inconsistent with the effect observed in the pilot study, the effect of Prime type failed to reach significance, indicating that the math score of participants who were exposed to attachment security primes was not higher than that of participants who were not exposed to such primes. The Prime type × Math identification interaction was significant.8 The region of significance, calculated using Preacher et al.’s (2006) online calculator, was Zidentification > 1.50 at the higher bound, and Zidentification < −6.17 at the lower bound. Since the lower bound is practically meaningless, these results indicate that participants with relatively high math identification (whose standardized level of math identification was higher than 1.50) had better math performance if exposed to the attachment security primes rather than to neutral or positive primes that are unrelated to attachment security. Figure 2 illustrates the obtained results (note that because the slopes are presented for participants who are 1 SD above or below the mean, the slope for participants with high domain identification represents a non-significant trend).
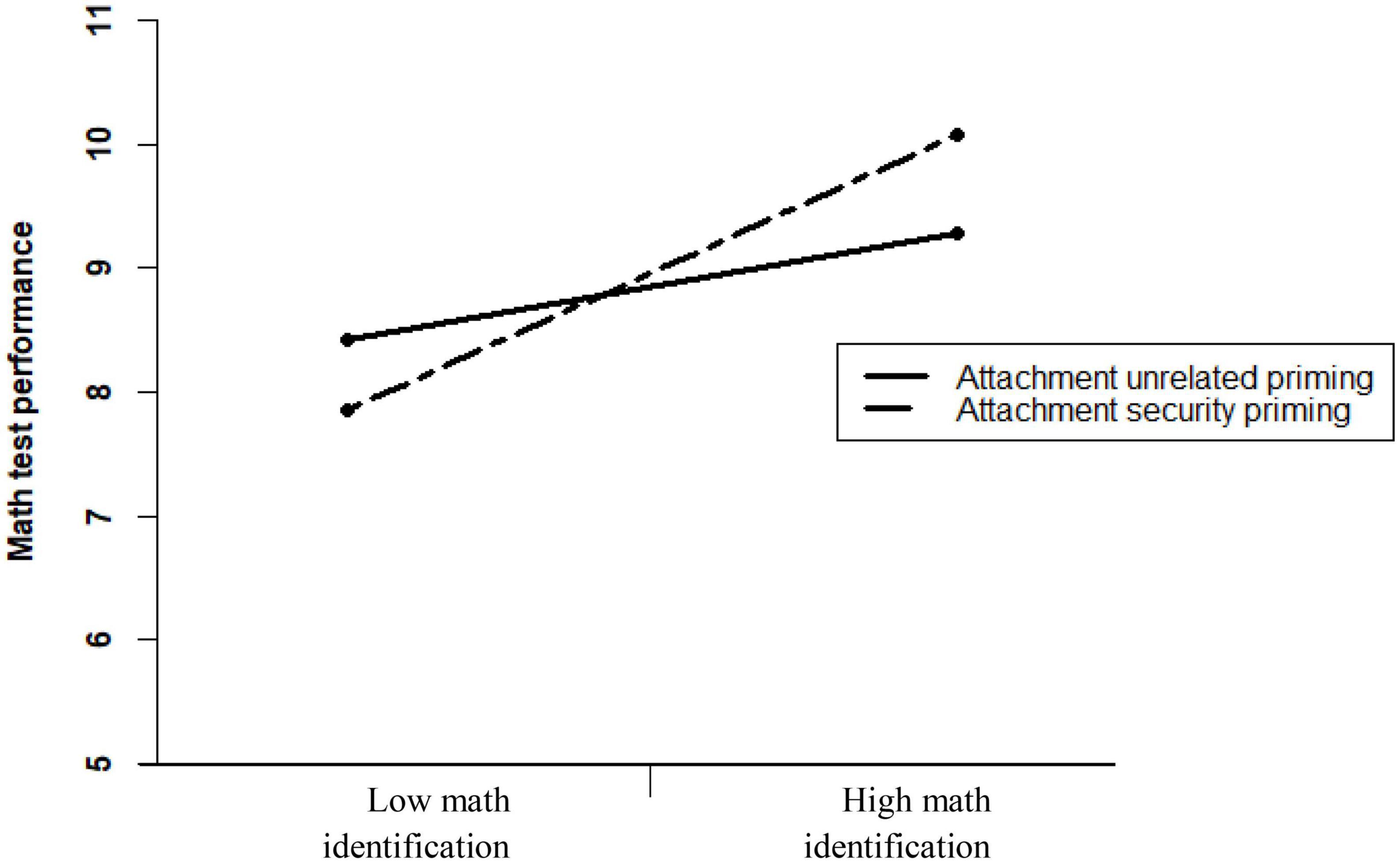
Figure 2. The effect of exposure to attachment security primes vs. control (neutral and positive) primes (N = 474) on math test performance among women whose math identification is high (+1 SD above average), B = 0.80 (SE = 0.45), t = 1.77, p = 0.077, vs. low (–1 SD), B = –0.59 (SE = 0.48), t = –1.23, p = 0.219.
As for the manipulation check, a one-way ANOVA, F(2,471) = 0.07, p = 0.931, η2p < 0.001, revealed that there was no significant difference between participants’ SAAM scores in the different priming conditions (see Table 3). Thus, inconsistent with the pilot study, we did not gain evidence that participants in the attachment security priming condition felt greater state attachment security than in the two control, attachment-unrelated conditions.
While unexpected, we believe that this result should be taken cautiously. As explained earlier, because of our concern that exposure to the SAAM’s items might induce attachment security and thus interfere with our manipulation, participants completed this measurement only after they completed the math test. By this time, the effect of the manipulation might have faded away. Previous research assumed that security had been successfully induced based on the effects of the ultimate outcome variables (e.g., outgroup derogation, Shaver and Mikulincer, 2007). We believe that a similar approach can be useful in the current study as well.
In Study 2 we wanted to replicate and extend the results of Study 1. Based on a power analysis (see details below) we recruited a large new sample to complete an online study. Study 1 partially supported the hypothesis that security primes improve math performance for women more than positive or neutral primes. To strengthen causal inference, stereotype threat was manipulated and compared to no threat in Study 2. Manipulating stereotype threat and comparing it to a no threat condition can help showing that security priming improves test performance specifically in the presence of threat. In light of the results of Study 1, and to increase power, the positive priming condition was not used in Study 2.
Women were recruited to complete an online survey about interpersonal relationships and problem-solving ability. They were exposed to either a threat or a neutral/control condition, followed by an attachment security prime (or control). Stereotype threat was induced via the instructions at the beginning of the study and again before the math test. In the threat condition participants were told we were testing math ability. In the control condition participants were told we were testing for problem-solving ability.
It was predicted that participants exposed to a stereotype threat will perform worse on the math test than participants in the non-threat condition (i.e., a main effect for the threat condition). It was further predicted that following exposure to a threat, participants in the security priming condition will perform better on the math test than participants in the neutral priming condition; the effect of security priming was expected to be smaller in the no-threat condition (i.e., a two-way Threat × Priming interaction). Finally, we predicted a three-way interaction between Threat, Priming, and domain identification. We expected that the buffering effect of security priming will be stronger among participants who were threatened and highly identify with math.
A power analysis using G*power was conducted to find the minimum sample size required to have a small effect size for the three-way interaction between priming, threat, and self-reported domain identification. The power analysis showed that ∼860 participants would be needed to detect a small effect size at a significance of 0.05 and power of 80%. Previous studies on stereotype threat were mainly done with participants physically present in the laboratory and often with the test done on paper (Shaffer et al., 2013; but see Schmader et al., 2004). We created an online version participants completed wherever they were, without coming to the lab, and using their own computer or phone. We expected these differences to increase variance among participants and reduce effect size (hence the bigger sample size). A total of (N = 960) participants were recruited via the online platform Prolific, which reached participants in the United States, the United Kingdom, and Australia (Prolific, 2014). Demographics are reported in the Supplementary material. They were compensated with $3.17 USD per participant. Preselection criteria were set to only allow participants who identified as female and native English speakers to take part. Of the 960 participants, 133 participants did not report their major, and were not included in the analysis. Participants’ ages ranged from 18 to 54 years old (Mage = 22.55, SD = 4.619).
Participants accessed the study via a link to a survey on Qualtrics (2005). After consenting, participants were randomly assigned to one of the four experimental conditions. Based on the condition assignment they were exposed to either an attachment security and a stereotype threat prime (n = 210), security and no threat prime (n = 212), non-attachment-related neutral prime and threat (n = 203), or a neutral and no threat prime (n = 202). The analysis was preregistered9 and the data were posted10 on OSF. The four items using domain identification were averaged to create a value for each participant. An exploratory analysis which used a median split for domain identification is included in the Supplementary material.
Participants were exposed to the attachment security/neutral control primes via two tasks. The first task included exposure to either an attachment security-related image (an image of an elderly woman kissing an elderly man on the cheek) or a neutral image (a black and white image of a drink container partially in frame). The secure image was sourced from McGuire et al. (2018). To ensure the control prime was neutral, 40 participants evaluated six images on how happy, sad, secure, and neutral they made them feel, using a 4-point scale ranging from 1 (not at all) to 4 (very much). The four emotional states for each of the six images were compared using a 4 × 6 repeated measures ANOVA to identify the image lowest on the emotion measures and highest on neutrality. The main effects of image, F(35,5) = 8.76, p < 0.001, and emotion, F(35,3) = 18.136. p < 0.001, were significant as well as the interaction effect of image by emotion, F(35,15) = 8.968, p < 0.001. Pairwise comparisons revealed two images differing significantly from all others, one of which had low means for each of the emotionality measures and a high mean for neutrality (see Supplementary material). Participants had 2 min to observe the image and were instructed to remember as much detail as they could about it. Then they were asked to describe the image and how they felt when observing it.
In the second priming task, participants were given a list of eight sentences (three of which were always neutral) and had 2 min to memorize them. The sentences were either attachment-security-related (e.g., “John and Betty trust each other completely”) or control sentences (e.g., “The bookshelf was set up in the living room”). This task was successfully used by McGuire et al. (2018). Next participants were asked to write as many sentences as they could remember.
Participants were exposed to a stereotype threat during the informed consent and again in the instructions to the math test. The section of the informed consent read “We are conducting this study to better understand the links between interpersonal relationships and problem-solving skills/math ability” and the test instructions had “Once again, we ask you to do your best despite the difficulty, for the test to optimally reflect your problem-solving skills/math ability.” In the control condition, the study was described as assessing problem-solving ability, whereas in the threat condition, the study was described as assessing math ability.
Math performance was assessed using ten math questions. The questions came from the same source as in Study 1. Participants were scored on how many questions they answered correctly.
Nine items from the SAAM were used to measure state attachment avoidance, anxiety, and security. The three items measuring security (α = 0.79) were used to test the effectiveness of the primes by comparing the averages between priming conditions. The questions were administered after the math test to avoid the questions having a priming effect on math performance.
Participants were asked to report their sex, age, ethnicity, education level, employment status, self-reported average high school math grade, and degree major. Majors were grouped into either STEM or non-STEM. STEM majors represented 44.7% of the participants.
Means, SDs, and correlations are presented in Tables 5 and 6. We first used a t-test to compare participants in the security priming condition with those in the neutral condition and found that participants exposed to security primes were significantly higher t(957) = 2.036, p = 0.042 on state attachment security than those in the neutral priming condition. These results are consistent with the pilot study, but inconsistent with Study 1. To test randomization, the conditions were compared on domain identification and STEM major. There were no significant differences between the conditions. The complete results are presented in the Supplementary material.
A linear regression was used to analyze the effect of security priming (prime), stereotype threat (threat), and domain identification. Prior math knowledge (STEM major and non-STEM) was controlled in the first step. The main effect of prime, threat, and domain identification were entered in the second step, followed by the two-way interactions of each variable and finally the three-way interaction. Due to the number of variables and random assignment of conditions, some of the cell sizes were less than 30 participants. This reduced the power of the results and should be taken into consideration when interpreting them. The analysis revealed a main effect for previous math knowledge in the first step, β = 1.028, t = 7.090 p < 0.001, such that STEM majors scored higher than non-STEM majors. The analysis also revealed a main effect for Domain identification in the second step, β = 0.568, t = 8.870, p < 0.001, showing that the more a participant identifies with math, the higher they scored. The two and three-way interactions were not significant (see Table 7). So, although the security prime resulted in a higher SAAM security score, it did not seem to buffer the effects of stereotype threat as reflected in the regression.
In an additional exploratory analysis we performed, we dichotomized domain identification based on a median split. Prime type, threat, major, and categorical domain identification were entered as fixed factors, and education and self-reported average high school math grade were entered as covariates. The analysis revealed a main effect for domain identification, math grade, and major, and a marginal four-way interaction between prime type, threat, major, and domain identification (p = 0.076). Pairwise comparisons of the four-way interaction did not support a buffering effect of security priming on stereotype threat. Full results can be found in the Supplementary material.
The results of our studies produced mixed support for our research hypotheses. The pilot study revealed that women, but not men, in the attachment-security priming condition had better math performance than those in the neutral priming condition. Study 1 revealed that women in the attachment-security priming condition had better math performance than those in the control, attachment-unrelated conditions (either neutral or positive primes)—yet this effect was observed mainly among participants with high math identification. Although revealing priming effects, Study 2 did not replicate the results from the pilot study and Study 1. Thus, in a pilot and a lab study we showed small effects of security priming buffering threat effects on women in STEM (in Study 1: only among women who highly identify with math). When we ran the study online (during the pandemic) the stereotype threat results were not replicated. This inability to detect stereotype threat effects online is in line with other studies that did not replicate decreased math performance due to stereotype threat online (Finnigan and Corker, 2016; Kahalon et al., 2020). Although the study was bolstered by being preregistered and having a large sample, we did not find the expected buffering effect on stereotype threat (perhaps because there was no threat to buffer–no main effect for threat).
The findings of the pilot and Study 1 align with stereotype threat theorizing, according to which subtle cues that signal and create identity safety can eliminate the performance decrements caused by stereotype threat (Murphy and Taylor, 2012). Admittedly, whereas the manipulation checks in the pilot and Study 2 provided evidence that participants in the attachment-security priming condition indeed felt greater state attachment security than in the neutral priming condition, Study 1 did not provide such evidence. However, due to the reasons detailed in the discussion of Study 1, we believe this null effect does not hamper the main finding. The manipulation check in Study 2 showed a significantly higher state attachment security for participants in the security priming condition compared to the neutral priming condition. Compared to Study 1, the manipulation check took place closer to the priming in Study 2. This might have increased the chances of the the SAAM to detect the effects of the manipulation. The priming in the pilot study and Study 2 differed from the priming in Study 1 by not explicitly mentioning gender. Conceivably, the explicit mention of gender in Study 1 could have resulted in female participants feeling motivated to overcome the stereotype.
Theoretically, the inconsistent results of our research were not able to shed light on the potential interplay between individual-level and group-level processes. One’s sense of attachment security failed to provide a consistent “symbolic shield” that could help coping with social-psychological stressors such as negative stereotyping. Within attachment theory, previous research on the interplay between the individual and group levels has focused on the positive impact of attachment security on the sources of outgroup prejudice and stereotyping (Shaver and Mikulincer, 2007; Boag and Carnelley, 2016). The present research is the first to examine the potential impact of attachment security on the targets of these negative stereotypes. Specifically, we looked at the negative stereotype imposed on female about math performance. Although we expected security to buffer the negative effects of exposure to stereotype threat (decreased performance), we only obtained partial support.
Our purpose was not just to enhance theoretical understanding but also to develop a simple strategy to improve women’s math performance in real-life settings. We reasoned that priming attachment security can be an ideal candidate for scaling up an intervention to improve women’s math performance due to its cost-effectiveness and easiness of administration—two aspects that are crucial for the scaling up of interventions to improve academic performance (Bakker et al., 2019; Kraft, 2019; see McGuire et al., 2018, for a discussion of the implementation of attachment security priming interventions in other contexts).
The effects in Study 1, however, were observed mainly among women relatively high on domain identification. Furthermore, the effects were relatively small (see raw means of participants’ math scores; in Tables 1, 3). Previous theorizing argued that a small effect observed in the lab may translate into a larger effect in a real-life intervention because academic settings create self-fulfilling cycles; namely, recursive processes in which initial psychological threat impairs performance, which further increases threat and yields consequent performance impairment (Cohen et al., 2009). It is as likely, however, that a small effect observed in the lab would disappear when tested in a noisy real-life context due to the interference of unobserved variables that were not considered when setting out a controlled lab study (Paluck and Cialdini, 2014). Our conclusion, therefore, is that priming attachment security might not be the best intervention to reduce gender gaps in math performance. More broadly, our research suggests that a single dose of security priming was not enough to reduce group-based disparities (Singal, 2021; see for example, Hanselman et al., 2017, for the fragility of widely implemented wise interventions based on self-affirmation exercises in reducing group-based achievements gaps).
Our findings also highlight the need to pay greater attention to effect sizes (Cumming, 2013). Some of the intervention studies that inspired the present research have focused solely on significance tests without discussing effect sizes. For example, Miyake et al. (2010) did not report the effect size for the improvement in physics grades among women in the self-affirmation compared to the control condition. Yet, in light of the debate about the replicability and validity of stereotype threat (e.g., Flore and Wicherts, 2015; Zigerell, 2017; Shewach et al., 2019) and priming effects (Doyen et al., 2012), effect sizes should always be discussed in research about these topics, especially when potentially practical interventions are tested.
Besides the failure to identify a “wise intervention,” a major limitation of the present research is that the studies (except for Study 2) were not pre-registered, which would strengthen the credibility of the conclusions (Nosek et al., 2018). As mentioned previously, employing stereotype threat manipulations online may have hindered the ability to detect a buffering effect. Future studies conducted in person may help disentangle the reason for our failure to detect effects (is it the online mode or security priming inability to buffer). Another limitation is that we focused on only one outcome, math performance. Future research can examine whether the activation of women’s attachment security influences other psychological outcomes of stereotype threat, such as women’s sense of misfit and inauthenticity in STEM environments (Schmader and Sedikides, 2018).
Future research could also test the impact of attachment security primes on stereotype threat among other minority group members. We suspect that the reason for the small effect observed in the present research is that besides activating attachment security, the primes (e.g., words like “hug”) unintendedly activated positive stereotypes about women’s nurturance and communality (which are related to women’s traditional roles as wives and mothers). Recent research (Kahalon et al., 2018, 2020) revealed that, despite their positivity, the activation of such stereotypes can lead to stereotype threat effects, resulting in women’s impaired math performance.
Examining the effects of attachment security priming on the reduction of stereotype threat effects among members of other negatively stereotyped groups, which are not stereotypically perceived as nurturing (e.g., African Americans performing an intelligence test; Steele, 1997), would possibly yield larger effects. Theoretically, attachment security serves two key functions: promoting a “safe haven” (i.e., relaxation) as well as a “secure base” (i.e., mobilization of energy to effectively cope with stressors). If so, then the positive effects of priming attachment security on performance should be particularly pronounced when there is “a threat in the air” (Ai et al., 2020), as is the case when African Americans take a test said to be diagnostic of intelligence (Steele, 1997).
Another direction future research should consider is using more personalized primes or repeated priming. Having a more personalized prime may increase the activation of the security schema, resulting in stronger effects. Repeated priming would further test the potential for security priming to be used as a wise intervention. The use of repeated primes may result in longer lasting effects, compared to the more transient nature of a single priming session (Gillath et al., 2008).
The current work provides partial support for the effect of security priming on math performance under stereotype threat. In the lab, attachment security was shown to buffer the negative effects of stereotype threat, mainly among those who identify strongly with the domain. However, in a preregistered online study with a large sample, security priming did not buffer the negative effects of stereotype threat on women. The mixed results may have been due to modality differences (offline vs. online) or the presence of men vs. manipulating threat vs. suggested threat. Future work should look into identifying factors that could enhance the potential impact of security priming on stereotype threat and bridge the two bodies of research on intrapersonal and intergroup processes.
The original contributions presented in this study are included in the article/Supplementary material, further inquiries can be directed to the corresponding author.
The studies involving humans were approved by the University of Kansas Internal Review Board. The studies were conducted in accordance with the local legislation and institutional requirements. The participants provided their written informed consent to participate in this study.
AS, OG, RK, and NS involved in deriving the hypotheses based on the literature, planning the experiments to test these hypotheses, analyzing the results, and writing the manuscript. All authors contributed to the article and approved the submitted version.
This research was supported by a grant from the Spencer Foundation (Award no. 201700102).
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fpsyg.2023.1124308/full#supplementary-material
Ai, T., Gillath, O., and Karantzas, G. C. (2020). The dual function model of attachment security priming: Theoretical framework and empirical evidence. Int. J. Environ. Res. Public Health 17, 80–93. doi: 10.3390/ijerph17218093
Ainsworth, M. D. S., Blehar, M. C., Waters, E., and Wall, S. (1978). Strange situation procedure. Clin. Child Psychol. Psychiatry
Aronson, J., Lustina, M. J., Good, C., Keough, K., Steele, C. M., and Brown, J. (1999). When white men can’t do math: Necessary and sufficient factors in stereotype threat. J. Exp. Soc. Psychol. 35, 29–46. doi: 10.1006/jesp.1998.1371
Ayalon, H. (2003). Women and men go to university: Mathematical background and gender differences in choice of filed in higher education. Sex Roles 48, 277–290. doi: 10.1023/A:1022829522556
Bakker, A., Cai, J., English, L., Kaiser, G., Mesa, V., and Van Dooren, W. (2019). Beyond small, medium, or large: Points of consideration when interpreting effect sizes. Educ. Stud. Math. 102, 1–8. doi: 10.1007/s10649-019-09908-4
Boag, E. M., and Carnelley, K. B. (2016). Attachment and prejudice: The mediating role of empathy. Br. J. Soc. Psychol. 55, 337–356. doi: 10.1111/bjso.12132
Bowlby, J. (1969/1982). Attachment and loss: Vol. 1. Attachment, 2nd Edn. New York, NY: Basic Books.
Brennan, K. A., Clark, C. L., and Shaver, P. R. (1998). “Self-report measurement of adult romantic attachment: An integrative overview,” in Attachment theory and close relationships, eds J. A. Simpson and W. S Rholes (New York, NY: Guilford press), 46–76.
Bryant, R. A., and Chan, I. (2017). Activating attachment representations during memory retrieval modulates intrusive traumatic memories. Conscious. Cogn. 55, 197–204. doi: 10.1016/j.concog.2017.08.010
Cadinu, M., Maass, A., Rosabianca, A., and Kiesner, J. (2005). Why do women underperform under stereotype threat? Evidence for the role of negative thinking. Psychol. Sci. 16, 572–578. doi: 10.1111/j.0956-7976.2005.01577.x
Carnelley, K. B., and Rowe, A. C. (2007). Repeated priming of attachment security influences later views of self and relationships. Pers. Relationsh. 14, 307–320. doi: 10.1111/j.1475-6811.2007.00156.x
Cheryan, S., Meltzoff, A. N., and Kim, S. (2011). Classrooms matter: The design of virtual classrooms influences gender disparities in computer science classes. Comput. Educ. 57, 1825–1835. doi: 10.1016/j.compedu.2011.02.004
Cohen, G. L., Garcia, J., Purdie-Vaughns, V., Apfel, N., and Brzustoski, P. (2009). Recursive processes in self-affirmation: Intervening to close the minority achievement gap. Science, 324, 400–403. doi: 10.1126/science.1170769
Cumming, G. (2013). Understanding the new statistics: Effect sizes, confidence intervals, and meta-analysis. Oxfordshire: Routledge.
Doyen, S., Klein, O., Pichon, C. L., and Cleeremans, A. (2012). Behavioral priming: It’s all in the mind, but whose mind? PLoS One 7:e29081. doi: 10.1371/journal.pone.0029081
Faul, F., Erdfelder, E., Buchner, A., and Lang, A. G. (2009). Statistical power analyses using G*Power 3.1: Tests for correlation and regression analyses. Behav. Res. Methods 41, 1149–1160. doi: 10.3758/BRM.41.4.1149
Finnigan, K. M., and Corker, K. S. (2016). Do performance avoidance goals moderate the effect of different types of stereotype threat on women’s math performance? J. Res. Pers. 63, 36–43.
Flore, P. C., and Wicherts, J. M. (2015). Does stereotype threat influence performance of girls in stereotyped domains? A meta-analysis. J. Sch. Psychol., 53, 25–44. doi: 10.1016/j.jsp.2014.10.002
Ganley, C. M., Mingle, L. A., Ryan, A. M., Ryan, K., Vasilyeva, M., and Perry, M. (2013). An examination of stereotype threat effects on girls’ mathematics performance. Dev. Psychol. 49, 1886–1897. doi: 10.1037/a0031412
Gillath, O., and Hart, J. (2010). The effects of psychological security and insecurity on political attitudes and leadership preferences. Eur. J. Soc. Psychol., 40, 122–134. doi: 10.1002/ejsp.614
Gillath, O., Hart, J., Noftle, E. E., and Stockdale, G. D. (2009). Development and validation of a state adult attachment measure (SAAM). J. Res. Pers. 43, 362–373. doi: 10.1016/j.jrp.2008.12.009
Gillath, O., Karantzas, G. C., and Fraley, R. C. (2016). Adult attachment: A concise introduction to theory and research. Cambridge, MA: Academic Press.
Gillath, O., Karantzas, G. C., Romano, D., and Karantzas, K. M. (2022). Attachment security priming: A meta-analysis. Pers. Soc. Psychol. Rev. 26, 183–241.
Gillath, O., Selcuk, E., and Shaver, P. R. (2008). Moving toward a secure attachment style: Can repeated security priming help? Soc. Pers. Psychol. Comp. 2, 1651–1666. doi: 10.1111/j.1751-9004.2008.00120.x
Gillath, O., Sesko, A. K., Shaver, P. R., and Chun, D. S. (2010). Attachment, authenticity, and honesty: Dispositional and experimentally induced security can reduce self- and other deception. J. Pers. Soc. Psychol. 98, 841–855. doi: 10.1037/a0019206
Goffman, E. (1963). Stigma: Notes on the management of spoiled identity. New York, NY: Simon and Schuster.
Hanselman, P., Rozek, C. S., Grigg, J., and Borman, G. D. (2017). New evidence on self-affirmation effects and theorized sources of heterogeneity from large-scale replications. J. Educ. Psychol. 109, 405–424. doi: 10.1037/edu0000141
Inzlicht, M., and Ben-Zeev, T. (2000). A threatening intellectual environment: Why females are susceptible to experiencing problem-solving deficits in the presence of males. Psychol. Sci. 11, 365–371. doi: 10.1111/1467-9280.00272
Johns, M., Schmader, T., and Martens, A. (2005). Knowing is half the battle: Teaching stereotype threat as a means of improving women’s math performance. Psychol. Sci. 16, 175–179. doi: 10.1111/j.0956-7976.2005.00799.x
Kahalon, R., Shnabel, N., and Becker, J. C. (2018). Positive stereotypes, negative outcomes: Reminders of the positive components of complementary gender stereotypes impair performance in counter-stereotypical tasks. Br. J. Soc. Psychol. 57, 482–502. doi: 10.1111/bjso.12240
Kahalon, R., Shnabel, N., and Becker, J. C. (2020). The effects of exposure to positive gender stereotypes on women’s and men’s performance in counter-stereotypical tasks and pursuit of agentic and communal goals. Soc. Psychol. 51, 50–62. doi: 10.1027/1864-9335/a000394
Keller, J. (2007). Stereotype threat in classroom settings: The interactive effect of domain identification, task difficulty and stereotype threat on female students’ math performance. Br. J. Educ. Psychol. 77, 323–338. doi: 10.1348/000709906X113662
Keller, J., and Dauenheimer, D. (2003). Stereotype threat in the classroom: Dejection mediates the disrupting threat effect on women’s math performance. Pers. Soc. Psychol. Bull. 29, 371–381. doi: 10.1177/0146167202250218
Kraft, M. A. (2019). Interpreting effect sizes of education interventions. Educ. Res. 49, 241–253. doi: 10.3102/0013189X20912798
Liu, S., Liu, P., Wang, M., and Zhang, B. (2021). Effectiveness of stereotype threat interventions: A meta-analytic review. J. Appl. Psychol. 106, 921–949. doi: 10.1037/apl0000770
McGuire, A., Gillath, O., Jackson, Y., and Ingram, R. (2018). Attachment security priming as a potential intervention for depressive symptoms. J. Soc. Clin. Psychol. 37, 44–68. doi: 10.1521/jscp.2018.37.1.44
Mikulincer, M. and Shaver, P. R. (2001). Attachment theory and intergroup bias: Evidence that priming the secure base schema attenuates negative reactions to outgroups. J. Pers. Soc. Psychol. 81, 97–115. doi: 10.1037/0022-3514.81.1.97
Mikulincer, M., and Shaver, P. R. (2007). Boosting attachment security to promote mental health, prosocial values, and inter-group tolerance. Psychol. Inq. 18, 139–156. doi: 10.1080/10478400701512646
Mikulincer, M., Hirschberger, G., Nachmias, O., and Gillath, O. (2001b). The affective component of the secure base schema: Affective priming with representations of attachment security. J. Pers. Soc. Psychol. 81, 305–321. doi: 10.1037/0022-3514.81.2.305
Mikulincer, M., Gillath, O., Halevy, V., Avihou, N., Avidan, S., and Eshkoli, N. (2001a). Attachment theory and reactions to others’ needs: Evidence that activation of the sense of attachment security promotes empathic responses. J. Pers. Soc. Psychol. 81, 1205–1224. doi: 10.1037/0022-3514.81.6.1205
Mikulincer, M., Shaver, P. R., Gillath, O., and Nitzberg, R. A. (2005). Attachment, caregiving, and altruism: Boosting attachment security increases compassion and helping. J. Pers. Soc. Psychol. 89, 817–839. doi: 10.1037/0022-3514.89.5.817
Miyake, A., Kost-Smith, L. E., Finkelstein, N. D., Pollock, S. J., Cohen, G. L., and Ito, T. A. (2010). Reducing the gender achievement gap in college science: A classroom study of values affirmation. Science 330, 1234–1237. doi: 10.1126/science.1195996
Murphy, M. C., and Taylor, V. J. (2012). “The role of situational cues in signaling and maintaining stereotype threat,” in Stereotype threat: Theory, process, and application, eds M. Inzlicht and T. Schmader (Oxford: Oxford University Press), 17–33.
Murphy, M. C., Steele, C. M., and Gross, J. J. (2007). Signaling threat: How situational cues affect women in math, science, and engineering settings. Psychol. Sci. 18, 879–885. doi: 10.1111/j.1467-9280.2007.01995.x
Nosek, B. A., Ebersole, C. R., DeHaven, A. C., and Mellor, D. T. (2018). The preregistration revolution. Proc. Natl. Acad. Sci. U.S.A. 115, 2600–2606. doi: 10.1073/pnas.1708274114
Open Science Collaboration (2015). PSYCHOLOGY. Estimating the reproducibility of psychological science. Science 349:aac4716. doi: 10.1126/science.aac4716
Paluck, E. L., and Cialdini, R. B. (2014). “Field research methods,” in Handbook of research methods in social and personality psychology, eds H. T. Reis and C. M. Judd (Cambridge: Cambridge University Press), 81–97.
Preacher, K. J., Curran, P. J., and Bauer, D. J. (2006). Computational tools for probing interaction effects in multiple linear regression, multilevel modeling, and latent curve analysis. J. Educ. Behav. Stat. 31, 437–448. doi: 10.3102/10769986031004437
Prolific, (2014). Prolific. Available online at: https://www.prolific.co/ (accessed September 20, 2022).
Pronin, E., Steele, C. M., and Ross, L. (2004). Identity bifurcation in response to stereotype threat: Women and mathematics. J. Exp. Soc. Psychol. 40, 152–168. doi: 10.1016/S0022-1031(03)00088-X
Qualtrics (2005). Qualtrics. Available online at: https://www.qualtrics.com/ (accessed September 20, 2022).
Schmader, T. (2002). Gender identification moderates stereotype threat effects on women’s math performance. J. Exp. Soc. Psychol. 38, 194–201. doi: 10.1006/jesp.2001.1500
Schmader, T., and Sedikides, C. (2018). State authenticity as fit to environment: The implications of social identity for fit, authenticity, and self-segregation. Pers. Soc. Psychol. Rev. 22, 228–259. doi: 10.1177/1088868317734080
Schmader, T., Johns, M., and Barquissau, M. (2004). The costs of accepting gender differences: The role of stereotype endorsement in women’s experience in the math domain. Sex Roles, 50, 835–850. doi: 10.1023/B:SERS.0000029101.74557.a0
Schmader, T., Johns, M., and Forbes, C. (2008). An integrated process model of stereotype threat effects on performance. Psychol. Rev. 115, 336–356. doi: 10.1037/0033-295X.115.2.336
Shaffer, E. S., Marx, D. M. and Prislin, R. (2013). Mind the gap: Framing of women’s success and representation in STEM affects women’s math performance under threat. Sex Roles 68, 454–463. doi: 10.1007/s11199-012-0252-1
Shapiro, J. R., and Neuberg, S. L. (2007). From stereotype threat to stereotype threats: Implications of a multi-threat framework for causes, moderators, mediators, consequences and interventions. Pers. Soc. Psychol. Rev. 11, 107–130. doi: 10.1177/1088868306294790
Shaver, P. R., and Mikulincer, M. (2007). “Attachment theory and research: Core concepts, basic principles, conceptual bridges,” in Social psychology: Handbook of basic principles, eds A. W. Kruglanski and E. T. Higgins (New York, NY: The Guilford Press), 650–677.
Shewach, O. R., Sackett, P. R., and Quint, S. (2019). Stereotype threat effects in settings with features likely versus unlikely in operational test settings: A meta-analysis. J. Appl. Psychol. 104, 1514–1534. doi: 10.1037/apl0000420
Singal, J. (2021). The quick fix: Why fad psychology can’t cure our social ills. New York, NY: Farrar, Straus and Giroux.
Smith, J. L., and White, P. H. (2001). Development of the domain identification measure: A tool for investigating stereotype threat effects. Educ. Psychol. Meas. 61, 1040–1057. doi: 10.1177/00131640121971635
Spencer, S. J., Logel, C., and Davies, P. G. (2016). Stereotype threat. Annu. Rev. Psychol. 67, 415–437. doi: 10.1146/annurev-psych-073115-103235
Spencer, S. J., Steele, C. M., and Quinn, D. M. (1999). Stereotype threat and women’s math performance. J. Exp. Soc. Psychol. 35, 4–28. doi: 10.1006/jesp.1998.1373
Steele, C. M. (1997). A threat in the air: How stereotypes shape intellectual identity and performance. Am. Psychol. 52, 613–629. doi: 10.1037/0003-066X.52.6.613
Steiger, J. H. (2004). Beyond the F test: Effect size confidence intervals and tests of close fit in the analysis of variance and contrast analysis. Psychol. Methods 9, 164–182. doi: 10.1037/1082-989X.9.2.164
Troyer, D., and Greitemeyer, T. (2018). The impact of attachment orientations on empathy in adults: Considering the mediating role of emotion regulation strategies and negative affectivity. Pers. Individ. Differ. 122, 198–205. doi: 10.1016/j.paid.2017.10.033
Walton, G. M., and Spencer, S. J. (2009). Latent ability: Grades and test scores systematically underestimate the intellectual ability of negatively stereotyped students. Psychol. Sci. 20, 1132–1139. doi: 10.1111/j.1467-9280.2009.02417.x
Keywords: attachment security, priming, stereotype threat, domain identification, math performance
Citation: Soares De Almeida A, Gillath O, Kahalon R and Shnabel N (2023) Effects of attachment security priming on women’s math performance. Front. Psychol. 14:1124308. doi: 10.3389/fpsyg.2023.1124308
Received: 15 December 2022; Accepted: 01 August 2023;
Published: 24 August 2023.
Edited by:
Christoph Scheepers, University of Glasgow, United KingdomReviewed by:
Jessica A. Stern, University of Virginia, United StatesCopyright © 2023 Soares De Almeida, Gillath, Kahalon and Shnabel. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Omri Gillath, b2dpbGxhdGhAa3UuZWR1
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.