- School of Criminology and Justice Studies, University of Massachusetts Lowell, Lowell, MA, United States
Anecdotal evidence supports than engaging with violent extremist content online facilitates the radicalization process. However, there is a consistent lack of empirically grounded research to provide insight into the psychological process through which this influence occurs (if at all). As such, most theories often fail to accommodate both the multifinality (the concept that many people are exposed to violent extremist material, yet never engage in violent extremism), and equifinality (the concept that people can view a range violent extremist content, yet all end up engaging in violent extremism) that naturally is observed in those who engage with violent extremist content online and those who engage in violent extremist behavior. This paper presents Reinforcement Sensitivity Theory (RST) as a theoretical framework to inform understanding of the process that governs the interaction between violent extremist material online and engaging with violent extremism. RST is a motivational theory which has been applied to a range of benevolent and deviant behaviors. Specifically, we argue that RST is suitable to explain the effect of violent extremist content online because (1) it outlines multiple differentiated motivational pathways that can account for multifinality and equifinality observed in those who engage in violent extremist behavior and (2) the extant neurological and psychophysiological research using RST provides a empirically supported framework for developing both research methods and verifiable hypotheses to advance our understanding of how, if at all, violent extremist content online contributes to the process of radicalization.
Introduction
The use of the Internet by violent extremists has become a primary focus for academic research (Neo, 2019). Extremist organizations currently use information technology, specifically the Internet, as a platform to recruit, disseminate ideological messages, deliver threats, release instructional materials to facilitate the actions of others, as well as to plan and coordinate violent extremist attacks (Weimann, 2006). The Internet plays a central role in facilitating the processes through which Western individuals support or join extremist groups by facilitating contact and planning between would-be-recruits and recruiters, and extremist material on the Internet has also directly facilitated attempts to, or inspired the perpetration of domestic attacks (see Lemieux et al., 2014)1. Over the past two decades anecdotal evidence supported a growing assertion that individuals who engage in acts of violent extremism have, at varying points, in varying ways, and to varying degrees, engaged with violent extremist content online (see Conway, 2006; Hoffman, 2006; Freiburger and Crane, 2008; Bowman-Grieve, 2009; Weimann, 2011; Bowman-Grieve and Conway, 2012; Holbrook et al., 2013; Von Behr et al., 2013; Ekman, 2014). Despite this, from a theoretical perspective “the reality […] is that insufficient substantive empirically grounded social science research has been undertaken to date in order to allow us to convincingly answer [the question whether the internet is influential]” (Conway, 2017, p. 82; Frissen, 2021).
There are several pre-existing issues that have hindered the development and testing of theories pertaining to the link between violent extremist content online and violent extremist action. Firstly, in the psychological study of extremism, as a whole, there has been a significant lack of progress in conceptualizing the radicalization process (see Sageman, 2014) with efforts hampered by little/no primary source data (Silke, 2000, 2004; Schuurman, 2019). Secondly, as highlighted by Horgan (2019), most theories often fail to accommodate the issues of multifinality (the concept that people can experience the same life events or have similar histories, yet their developmental outcomes can vary widely; Howe, 2011), and equifinality (the principle that in open systems a given end state can be reached by many potential means; Gill et al., 2021). Meaning, that theories lack pathways of differentiation that can explain why, while many people are exposed to violent extremist content, only a few progress down a pathway of radicalization. Furthermore, many people end up at a state of “being radicalized” but come from a range of diverse exposures to violent extremist content online (Horgan J. et al., 2016; Horgan J. G. et al., 2016). Despite this, a range of experimental research has shown that the effect of exposure to violent extremist content online depends on the personality of the viewer (Shortland et al., 2017, 2020). These issues, coupled with the widely espoused view that personality is critical to the radicalization process (e.g., McGregor et al., 2015), supports the need for explanations for the role of violent extremist content to (at least partly) focus on the role that individual differences in personality play on core motivations to engage in violent extremist action.
Reinforcement Sensitivity Theory
RST presupposes that individual differences in responses to stimuli stem from different sensitivities of basic brain systems that respond to novel, punishing, and reinforcing stimuli (Gray, 1973, 1982). The original version of RST (Gray, 1982) proposed a reward system (the behavioral activation system, BAS), punishment system (the behavioral inhibition system, BIS), and threat-response system (Fight/Flight system, FFS). Activation of the BAS system was posited to promote approach behavior and positive affect, while the activation of the BIS system was thought to promote withdrawal behavior and negative affect (Smillie et al., 2006). After a wave of early empirical research, many tenants of RST were not validated, leading to refinements of the theory in 2000 (Gray and McNaughton, 2000; see Pickering and Gray, 1999; Corr, 2001, 2004; Jackson, 2003). This refined model of RST altered the underlying relationship between the three systems. The BAS still functions as a reward system, while the FFS was renamed the FFFS (the additional “F” representing “freeze”). This model also expanded the role of the BIS as not simply a response to conditioned negative responses, but also to monitor and respond to motivational conflict that emerges when both the BAS and FFFS are activated. The BIS is thus no longer considered a punishment system (this function was moved to the FFFS) but is instead an anxiety-biased moderator between the BAS and FFFS (Gray and McNaughton, 2000). In the updated version of RST, stimuli perceived as positive activate the BAS and motivate approach behaviors toward target reinforcers, or goals, while stimuli perceived as negative activate the FFFS, motivating the individual to avoid potential threats. The BIS coordinates the response by attempting to resolve conflicting inputs when a stimulus activates both BAS and FFFS (Gray and McNaughton, 2000). Gray’s theory has been linked with primary psychopathy (Ross et al., 2007), aggressive inclinations (Harmon-Jones and Peterson, 2008), state anger (Carver, 2004) and general aggressive cognitions (Putman et al., 2004). It has also been applied to voter behavior after the effects of experiencing terrorism (Marcus and MacKuen, 1993).
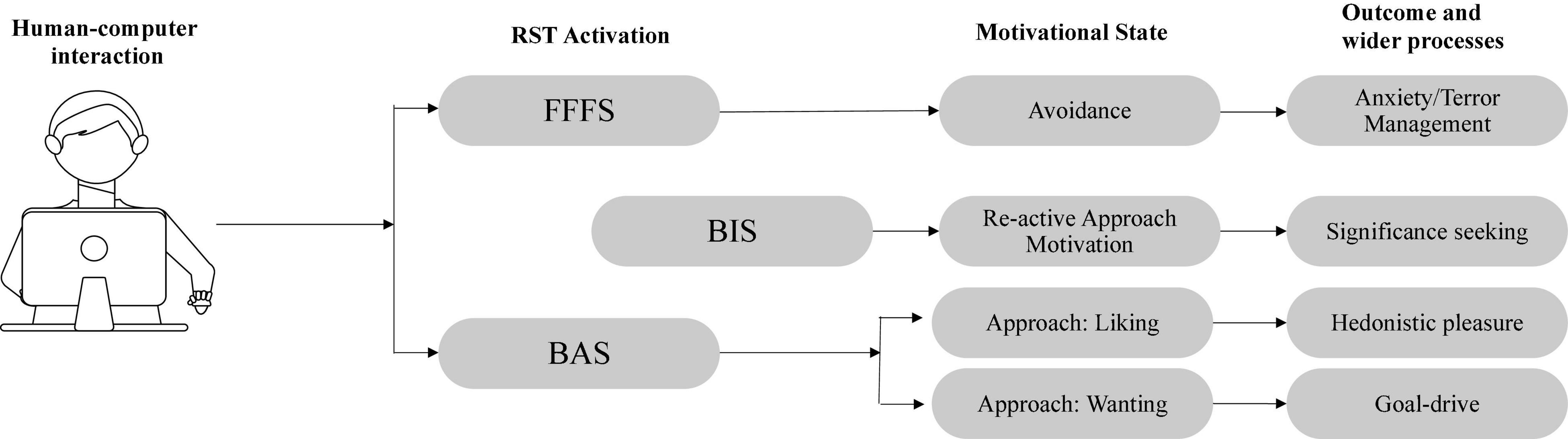
The application of RST to violent extremist material online in this article allows us to advance a preliminary theoretical model to that proposes four possible pathways that occur based on the interaction of an individual with violent extremis content online (see Figure 1). Each pathway a range of predictive personality traits that are associated with each pathway. Furthermore, each pathway does, to varying degrees, reflect extant theories of the psychology of violent extremism as well as, integrate with previous research on the correlates of RST functioning in a range of domains. What this model provides is an integration of decades of research on RST and violent extremism that allows us to how the interaction of individual state and trait functions manifest in quantifiably different RST activation states which, crucially, imply different forms of motivation toward (or away) from violent extremism in general. Leveraging the extant research on RST and violent extremism, we outline RST, and each of these pathways below.
Four Motivational Pathways Toward and Away From Violent Extremist Action
The FFFS: Avoidance as a Response to Violent Extremist Content Online
Many individuals who are exposed to violent extremist content online are repelled by the content (Shortland et al., 2017), and this is the first possible outcome pathway: an individual is being repelled from the material, driven by FFFS activation. The role of the BIS/FFFS in repelling people from terrorism is not a new assertion. Terrorism, has, after all been termed the “Politics of Fear” (Pyszczynski, 2004). BIS and FFFS processes include behavioral inhibition, driven by fear responses, trait anxiety, and threat avoidance (Gray and McNaughton, 2000; McNaughton and Corr, 2004; Perkins et al., 2007), all of which are common reactions to acts of extremism or extremist propaganda. Terror Management Theory (TMT) posits that exposure to threatening materials reminds individuals of their own mortality, creating an in-group bias involving increased pro-social behavior and empathy for the members of their in-group (Hewstone et al., 2002; Schimel et al., 2006). Accordingly, exposure to terrorist attacks is associated with increases in fear and anxiety (Marshall et al., 2007; Toohey and Taylor, 2008; Aly and Green, 2010). Consistent with this, television viewing of rebroadcast visuals of 9/11 was found to increase fear and anxiety (Fahmy et al., 2006). Anxiety is also higher in adults who directly experienced loss or witnessed a terrorist event or are exposed to televised terrorism-related material (Schuster et al., 2001; Schlenger et al., 2002). Children are equally affected by news coverage of 9/11, regardless of whether they have witnessed a terrorist attack (Pfefferbaum et al., 2001). Taken together, this body of research suggests that many individuals experience an FFFS response when exposed to extremist material which causes fear, anxiety, and a motivation to withdraw from the material.
The Behavioral Activation System: Approach Motivation as a Response to Violent Extremist Content Online
The primary function of the BAS is to move an organism from a start state (e.g., hunger) through acquisition and toward the final biological reinforcer, or goal (e.g., eating; Corr, 2013; Corr and Krupić, 2017). Individual differences in BAS processing have been found to relate to individual differences in approach-related personality traits and behavior (Gray and McNaughton, 2003; Segarra et al., 2014). Traditional BAS traits have been previously identified as possible risk factors for engagement in violent extremism (facilitated via both online and offline radicalization). Extraversion and impulsivity have been viewed as manifestations of BAS dimensions (Depue and Collins, 1999), both of which are thought to be personality traits associated with extremism. Süllwold (1981), found that increased extraversion among Red Army Faction members predisposed these youth to join terrorist movements (also see Canadian Network for Research on Terrorism, Security and Society [TSAS], 2015). Sensation seeking is also a BAS trait that psychologists have argued predisposes an individual to the processes leading to terror-related involvement (Silke, 2008). Researchers have claimed that youth become radicalized because of the “seductive” and “adventurous” dimensions of extremist groups (Atran, 2008). BAS activation is also associated with sensation and novelty seeking (Franken and Muris, 2006; Segarra et al., 2014). Along with sensation seeking (Silke, 2003), risk tolerance has also been suggested as a risk factor for terrorism (Crenshaw, 1981). Further, while BIS sensitivity predicted fear reactions after the 11 September attacks, BAS sensitivity was linked to anger responses and motivational drive (Carver, 2004) and extraversion (a BAS trait) correlates negatively with terrorism anxiety (Hawi et al., 2019). Finally, general criminality is a well-known risk factor for involvement in extremism (LaFree et al., 2018) and higher scores on assessments of trait-BAS sensitivity are associated with an individual having more frequent arrests (Taylor and Eitle, 2015). Furthermore, physiological pathways associated with BAS functioning are also linked to testosterone, social dominance, and social aggression—all of which have been postulated as risk factors related to extremist behavior (Levin et al., 2003; Caluya, 2013; Möller-Leimkühler, 2018).
One of the more recent focusses in the application of RST is disaggregating the nature of BAS activation, and the implications of this for behavior. In a review of the five most frequently used RST questionnaires, Krupić et al. (2016) classified the BAS scales from the five questionnaires into four groups that represented different forms of BAS activation: wanting, striving, liking, and capturing—these constructs then shaped the latest version of the RST-Personality Questionnaire (RST-PQ; Corr and Cooper, 2016) which separates the BAS into four interrelated processes: Reward Interest, Goal-Drive Persistence, Reward Reactivity, and Impulsivity. Each of these inter-related processes reflect a different type of approach behavior. Reward Interest represents the first stage of an approach motivation and the search for a new reward. Goal-Drive Persistence measures an individuals’ degree of persistence toward achieving that goal. Reward Reactivity measures emotional reactivity to reward and Impulsivity reflects the fast reaction at the final stage of an approach process to capture the reward. This reflects the known multidimensionality of reward systems. Berridge and Robinson (2003) introduced three components of reward system: learning, liking, and wanting to represent the difference between motivational aspects of reward (wanting something) and affective reactions to a reward. In a recent effort to unify and integrate the many different labels used to represent the same underlying BAS construct, Krupić and Corr (2017) introduced a multidimensional model of approach behavior in which they identified each of the four approach processes. In addition to this they identified the neurobiological process that underpins each form of approach. Within the study of “the terrorist” there have been long-standing calls of the need to disaggregate both the types of individual that engage in extremist behavior (see Gill and Corner, 2013) and the psychological meaning that an individual derives from their engagement (Horgan J. et al., 2016). In disaggregating approach behaviors via a multidimensional model of BAS here, we can separate the nature of approach behavior caused in response to exposure to extremist material and the ensuring implications of how, if at all, the nature of this reaction changes over time if at all. Within the current stats of RST research, there is evidence that “wanting” and “liking” are dissociable psychologically and neurologically, with each also based on different underlying physiological pathways (Berridge et al., 2009). While “wanting” is defined by the establishment of declarative goals and the expectations of future outcomes, “liking” is based positive hedonic impact, or pleasure of reward driven by opioid circuits associated with pleasure and immediate gratification (Berridge and Robinson, 2003). As defined by Krupić and Corr (2017), wanting is necessary for attaining a reward, while liking reflects an individual’s reaction after obtaining a desired reward. While in many cases we want what we like, we can also like a stimulus, but not want to explicitly set goals to acquire it. We apply this dissociation to violent extremism below.
Behavioral Activation System Liking
The term “liking” refers to the positive hedonic impact, or pleasure of reward (Berridge and Kringelbach, 2008). Where the word liking in the everyday sense refers to conscious, subjective experience of pleasure, core “liking” response represents the hedonic reaction to reward, regardless of any conscious feelings of pleasure, and is used to describe the objective emotional consequences of reward (Berridge and Robinson, 2003; Berridge and Kringelbach, 2008; Berridge, 2009). It is important to note that “liking” is purely an affective state, and no incentive target or motivation for further reward is needed to trigger hedonic “liking” (Berridge, 2009). Hedonic brain systems process and label sensations with a hedonic valence (the hedonic niceness or nastiness of a stimulus) marking that sensation as pleasurable or “liked” (Berridge and Kringelbach, 2008). Reflecting a positive hedonic valence, the pleasure of a reward elicits an affective “liking” response, which is then experienced as conscious pleasure (Berridge and Kringelbach, 2008). For example, the pleasure of sweetness is generated by the hedonic brain systems that associate pleasure with the sensation of tasting something sweet.
Scales measuring BAS sensitivity include a measure of “liking” that has been associated with reward responsiveness and reward reactivity. These scales are characterized by positive emotionality, and it is thought that this is indicative of a lower threshold of reward value needed to elicit psychological reactions to stimuli. “Liking” has also been associated with trait extraversion and agreeableness (Krupić and Corr, 2017). Further, in a study on engagement with COVID-19 prevention guidelines, approach-related liking has been associated with increased likelihood of engaging in social distancing (Krupić et al., 2021). This hedonic “liking” has distinct neural mechanisms, and objective physiological markers in the brain, as well as objective behavioral effects and subjective emotional effects (Berridge, 2009). In both humans and other animals, affective facial expressions caused by a hedonic response to sweet tastes is a commonly used “liking” measure of pleasure (Berridge and Robinson, 2003, 2016; Berridge and Kringelbach, 2008; Berridge, 2009). Sweet tastes elicit a positive facial response indicating “liking,” while bitter tastes elicit negative facial expressions, indicating “disliking” (Berridge, 2009). “Liking” is thought to involve opioid neurotransmission, and injections of opioid agonists have been found to increase facial “liking” reactions to sweet tastes (Berridge and Robinson, 2003; Berridge, 2009). Research suggests that opioid receptor activation can increase “liking” for certain foods and stimulate appetite (Berridge, 2009). It is thought that the activation of these opioid receptors can enhance the hedonic pleasure valence attributed to a reward, such as sweetness (Berridge, 2009). Additionally, even though typically associated with reward, dopamine depletion has been found to have no effect on “liking” reactions to pleasure (Berridge and Kringelbach, 2008; Berridge and Robinson, 2016). Thus, it is the opioid system that is thought to be more related to pleasure than dopamine systems (Berridge and Robinson, 2003). Dopamine is thought to have an alternative role related to “wanting.”
So, from the perspective of engaging with violent extremist content online, a “liking” response would be precisely that; liking the material and gaining a hedonistic pleasure from it, but with no necessary concurrent activation of a motivational state to acquire (or engage) with the goals being depicted in the media. In terms of access to violent extremist content online, it is viable to propose that many individuals engaging with such content are driven by an immediate liking and opioid-driven reward system without activating concurrent BAS motivations to acquire or engage with such material in the real world. Specifically, an overwhelming number of individuals currently engaging with violent extremist content grossly outweighs the number of individuals who actively seek to be involved with violent extremism (Shortland and Forest, 2020). A video depicting the beheading of Nick Berg by Islamic extremists in Iraq was downloaded over 15 million times, with sites hosting the video receiving over 60,000 hits per hour (Talbot, 2005). Between September and December 2014, 46,000 Twitter accounts were linked to ISIL supporters (Berger and Morgan, 2015). To put this point in perspective, there are currently over 1,000 open terrorist investigations in the United States pertaining to potential Islamic State (ISIS) offenders (Wray, 2018), yet there are only around 40 ISIS-related arrests in the United States each year (a 4% prevalence; see Vidino and Hughes, 2015). Furthermore, reports of the digital behavior of individuals possessing violent extremist propaganda has also noted that those individuals also possessed an array of other deviant material online such as child pornography (e.g., Ritter, 2020).
In relation to the four BAS process outlined in the RST-Personality Questionnaire (RST-PQ; Corr and Cooper, 2016) scales measuring BAS sensitivity include a measure of “liking” that has been associated with reward responsiveness and reward reactivity. These scales are characterized by positive emotionality, and it is thought that this is indicative of a lower threshold of reward value needed to elicit psychological reactions to stimuli. “Liking” has also been associated with trait extraversion and agreeableness (Krupić and Corr, 2017), traits that are associated with engagement in extremist behavior (Süllwold, 1981; Canadian Network for Research on Terrorism, Security and Society [TSAS], 2015).
Behavioral Activation System Wanting
Behavioral activation system wanting on the other hand represents the activation of a motivation drive toward the achievement of a goal. Generally referring to a conscious desire with a declarative goal, the term “wanting” refers to incentive salience, a motivational process that makes stimuli attractive (Berridge and Robinson, 2003; Berridge and Kringelbach, 2008; Berridge, 2009; Berridge and Robinson, 2016). As conceptualized by Krupić and Corr (2017), wanting has been conceptualized into two constructs, where wanting (capturing) is having a desire for a certain goal, and incentive motivation (wanting) is the motivational pathway toward engaging in those actions. These constructs of wanting are thought to have evolved early in evolution as a form of goal direction, and incentive salience is thought to be a separate process from “liking” to facilitate choosing between competing rewards that are equally “liked” (Berridge and Robinson, 2003). Incentive salience is linked to Pavlovian conditioned stimuli or reward-cues, causing cue-triggered “wanting” for a given reward. Mirroring hedonic “liking,” incentive salience is an implicit and objective motivation process that attributes the sensation of desire to rewards and their cues (Berridge and Robinson, 2003), these cues then become triggers of “wanting” (Berridge, 2009). When “wanting” is attributed to a reward stimulus representation, that stimulus (and its associated reward) gains enhanced motivational value (Berridge and Kringelbach, 2008; Berridge, 2009). Alone, a given stimulus (e.g., food or drugs) and its associated reward, are not intrinsically motivating—incentive salience, or attributed “wanting,” is what is thought to make a stimulus a target of motivation (Berridge and Robinson, 2003). Without “liking,” “wanting” is the sensation of desire without sensory pleasure, and “wanting” does not require conscious understanding of the causal relationship between a reward and the hedonic pleasure outcome (Berridge, 2009). Additionally, “wanting” can be triggered without conscious thought, and excessive incentive salience has been linked to irrational “wanting” for stimuli that are not cognitively desired or “liked” (Berridge and Robinson, 2003, 2016; Berridge, 2009).
In example, non-conscious alteration in consumption behavior has been associated with subliminal exposure to differing facial expressions, changing individuals’ desire for and rating of a beverage, with no reported conscious emotional changes (Berridge and Kringelbach, 2008). Increased dopamine levels have been found to quadruple a rat’s “wanting” for food rewards, with no corresponding changes in pleasure “liking” response (Berridge and Robinson, 2016). Dopamine release is triggered by many pleasant rewards and their associated cues (Berridge, 2009), and is related to better behavioral performance triggered by reward cues (Berridge and Kringelbach, 2008; Berridge, 2009). Additionally, dopamine suppression was found to produce no change in pleasure ratings of drug-related reward, even though it reduced desire to consume more of a drug (Berridge and Robinson, 2016). Irrational wanting behaviors, thought to originate from “wanting” without “liking,” are also associated with the activation of dopamine systems (Berridge, 2009).
Addiction related “wanting” is suggested to occur due to incentive salience creating a motivational compulsion, even if there is no pleasure outcome. Dopamine release meditates this effect, causing hyper-reactive “wanting” responses toward addiction cues and contexts that then cause more intense incentive salience (Berridge and Kringelbach, 2008; Berridge and Robinson, 2016). Individuals with other various behavioral addictions (e.g., gambling addiction, binge-eating disorders, and pornography addiction) are also thought to have hyper-reactivity toward cues related to their addiction (Berridge and Robinson, 2016). Although rewards that are “liked” are typically also “wanted,” “wanting” can occur in accordance with, in opposition to, or in the absence of cognitive desires, and without “liking” (Berridge and Robinson, 2003; Berridge, 2009). While research has demonstrated how “liking” and “wanting” can be dissociated, both are necessary for experiencing reward (Berridge, 2009). “Wanting” has also been shown to lead to behavioral changes. Scales measuring BAS sensitivity also include a measure of “wanting” associated with the reward interest, impulsivity BAS processes outlined in the RSTPQ, as well as sensation-seeking (Corr and Cooper, 2016; Krupić and Corr, 2017). Ambitiousness and social dominance are also traits associated with individuals high in “wanting” (Krupić and Corr, 2017). “Wanting” has been found to correlate with fast lifestyle behaviors, and individuals high in “wanting,” tend to favor problem solving strategies with immediate benefits (Krupić and Corr, 2017). Supporting this notion, approach-related wanting was also associated with increased level of concerns regarding the COVID-19 pandemic, and increased likelihood of following COVID-19 prevention guidelines (wearing a mask and/or gloves). Additionally, reflective of a fast lifestyle, the BAS process of “wanting” is associated with trait conscientiousness, extraversion, and social dominance (Krupić and Corr, 2017).
In the case of violent extremist content online, if a wanting response is activated, and the goal prioritized, the individual must then engage in a purposeful effort to achieve this goal (incentive motivation). This process requires delayed gratification, and investment in a further (and distal goal). In such instances, the individuals need to be able to main self-control and discipline, while also gaining suitable positive reinforcement via “local highs” (Corr and Krupić, 2017); which are short term forms of positive reinforcement. At the same time, they must not focus overly on these local highs, in favor of the long-term goal. Thus, an individual must be able to engage in this process of purposeful effort, at the same time, receive positive feedback from it, while also not forgoing the overall long-term goal in favor of these short-term “local highs.” An example of this, in the realm of online propaganda, may be an individual who begins the process with the overall long-term goal of joining an extremist group abroad (e.g., the Islamic State), but in the process of incentive motivation, receives significant positive feedback in the forms of social acceptance and positive reinforcement for their online activities and role in the online social networks associated with this group. In such instances, the individual may receive such positive feedback from these “preparatory” activities, that they forgo the ultimate goal of behaviorally engaging in terroristic activity. Especially if these “local highs” address the underlying needs that this individual that drove the individual to originally respond to extremist content with wanting. An alternative perspective, which would be in line with recent behavioral trends in the nature of extremist actions, is that if the individual does not have sufficient self-control to engage in a purposeful quest for the ultimate goal, they may impulsively engage in a short-term action that requires less persistence and behavioral commitment; such as an impulsive mass shooting (which represent 15% of lone actor shootings; Gill et al., 2017). At the end of the process the nature of the hedonistic reaction following attainment of the goal should enhance the learning process, which can then influence valuation of the goal. Research on why people leave extremism supports the role of this valuation process in the continuation of the behavior, in that individuals who have engaged in a purposeful process of becoming involved and engaged in extremist behavior can often begin a process of disengagement if they feel disillusioned with their role and actions and these behaviors no longer produce a positive reinforcement (Horgan and Bjorgo, 2009).
Behavioral Inhibition System: Reactive Approach Motivation as a Response to Violent Extremist Content Online
Behavioral inhibition system conceptualizes the BIS as a conflict detection system, responsible for inhibiting ongoing behavior when conflict is detected between simultaneously active behavioral goals (Mardaga and Hansenne, 2007; Berkman et al., 2009; Hirsh and Kang, 2016). Thus, in instances in which both BAS and FFFS are activated in response to exposure to a stimulus, the BIS governs these avoidant-activated conflict states. With regards to violent extremism, certain BIS functions are closely associated with feeling of meaningless, threats to one’s identity, and sensitivity to social and societal rejection. All of which have been advocated as potential motivators for engaging with violent extremist activity. The quest for significance (Kruglanski and Orehek, 2011) presents a model of radicalization proposes that involvement in terrorism is a route to achieve personal significance. As such, involvement in terrorism is driven by three general drivers of violent extremism: a need for significance, a narrative that provides a means to achieve significance, and a network of like-minded individuals who make the violence-justifying cognitions perceived as morally acceptable. The theory holds that central to all action is the desire to “be someone,” and to have meaning in one’s life. Kruglanski et al. (2014) found that members of the Liberation Tigers of Tamil Eelam (a militant separatist group fighting for an independent homeland for Hindu Tamils in Northeastern Sri Lanka) reported feelings of shame in the preceding weeks predicted their support and engagement in violent activities. A more recent cross-cultural survey in Indonesia, Morocco and Sri Lanka confirmed the link between quest for significance—particularly collective significance—and support for political violence (Jasko et al., 2019).
Individuals with heightened BIS sensitivity have reported feeling less meaning and purpose in their lives (McGregor et al., 2013). Additionally, individuals with increased BIS sensitivity tend to be more attentive to the negative aspects of a situation and have more pessimistic outlooks (Hirsh and Kang, 2016). Existential threats are thought to elicit BIS activation because they are indicative of a conflict between current circumstances and existential needs; additionally, exposure to mortality and uncontrollability stimuli has been found to activate BIS-related brain systems (Gray and McNaughton, 2000; Klackl et al., 2018). Most individuals will engage in compensatory behaviors to manage existential threat (Hirsh and Kang, 2016; Trip et al., 2019), and individuals may become more receptive to radicalized ideology when exposed to existential threat that induces feelings of anxiety or uncertainty about their previously accepted identity, lifestyle, or beliefs (Wiktorowicz, 2005). Loss of control, a type of existential threat, has been found to induce an approach motivated state that then drives the pursuit of salient goals (Greenaway et al., 2015). Research on the uncertainty-identity theory (Hogg and Adelman, 2013) posits that it is when these feelings become pervasive that individuals are more strongly attracted to extremist groups, which can provide individuals a sense of identity and a strict architype for behavior, thus helping to reduce uncertainty from existential threat (Trip et al., 2019).
Furthermore, the BIS is also engaged during frustrative non-reward (Gray, 1987), causing individuals to experience persistent anxiety when they cannot reach their goals (Trip et al., 2019). Thus, commitment toward a new goal (via activation of the BAS) would aid in resolving conflict due to an inability to achieve other active goals, and extreme religious beliefs were associated with personal uncertainty enabled through the achieving an active goal (McGregor et al., 2013). In all, activity in the BIS increases feelings of anxiety in situations of heightened arousal and when prolonged (due to a highly active BIS), this increased anxiety can induce feelings of uncertainty, identity conflict, social avoidance, and decreased life satisfaction. This chronic BIS activation may then serve as a trigger for subsequent BAS activation (a pattern of reactive-approach motivation) and lead to an increase motivation to engage in defensive behaviors to mitigate stress and return to a state of equilibrium (Klackl et al., 2018; Trip et al., 2019).
Anxiety is the most direct trait correlate with heightened BIS sensitivity, and high BIS sensitivity is thought to increase propensity toward anxiety and other mood disorders (Hirsh and Kang, 2016). Individuals with heightened BIS sensitivity have also reported feeling less meaning and purpose in their lives (McGregor et al., 2013). Additionally, individuals with increased BIS sensitivity tend to be more attentive to the negative experiences and have more pessimistic outlooks (Hirsh and Kang, 2016). Anxiety about one’s identity, meaning, or significance in life are classified as existential threats, or threats to the existence of something—living or non-living (e.g., one’s self, country, or ideology). Sleegers et al. (2015) indicates that a variety of existential threats are associated with heightened activity in the areas of the brain related to BIS activation. Existential threats are thought to elicit BIS activation because they are indicative of a conflict between current circumstances and existential goals. The anxiety-to-approach model of threat and defense (Jonas et al., 2014) posits that individuals facing existential threat experience heightened anxiety and self-uncertainty due to increased BIS sensitivity and often employ reactive defensive strategies to escape these feelings (Trip et al., 2019).
Circumstances in which individuals perceive life as unfair or unjust—or experience various forms of deprivation—can induce feelings of uncertainty and anxiety due to the activation of the BIS (Trip et al., 2019). This perception of deprivation has been shown to induce motivation to restore feelings of significance (Webber and Kruglanski, 2018). This anxious quest for significance creates a unique opportunity for an ideology, or narrative to assign blame for these feelings to an external source or enemy, legitimizing feelings of aggression and supporting a concrete world view of what is “right” and “wrong” (Gøtzsche-Astrup, 2019).
Wiktorowicz (2005) also discusses how individuals may become more vulnerable and receptive to radicalized ideology when exposed to existential threat and begin to feel uncertain about their value or significance. It is when these feelings become pervasive that individuals are more strongly attracted to extremist groups (Jasko et al., 2017), which provide individuals a sense of identity and a strict prototype for behavior, helping to reduce uncertainty from existential threat and provide individuals with a sense of significance (McGregor et al., 2015; Trip et al., 2019). Further, uncertainty-identity theory supports that individuals are highly motivated to reduce feelings of uncertainty about their life, future, and identity (Hogg and Adelman, 2013). Current research, as well as research dating back to the 1930s, indicates that individuals more aggressively cling to external sources of identity to avoid anxiety from existential uncertainty (McGregor et al., 2015). These results are also in line with research indicating that BIS sensitivity positively predicts for both proactive and reactive aggression (Parker et al., 2020). High BIS sensitivity is associated with individual inclinations to states of anxiety, making persons more vulnerable to feelings of meaninglessness and uncertainty, and thus increasing vulnerability to the narratives of extremist or radical groups that prescribe a sense of significance and certainty (McGregor et al., 2015). In fact, it is the concrete ideas and values of radical groups that may attract high BIS types, as in-lab concreteness manipulations have been shown not only to reduce anxiety but also to increase goal-drive in various tasks (Watkins et al., 2008). Collectively, the findings on the role of BIS in reactive approach motivation (McGregor et al., 2015) as well as the known pathway to violent extremism through anxiety and a deprivation of identity/need fulfillment (Kruglanski et al., 2017) demonstrate a clear pathway to violent extremism in which exposure to violent extremist content online creates competing avoid/approach motivations which encourages the individual toward violent extremism to satisfy an anxiety-creating void.
Discussion
Future Empirical Assessment of the Reinforcement Sensitivity Theory-Four Motivational Pathways Model
It has been long argued that to move the psychological study of terrorism forward a multidimensional framework must be adopted that emphasizes the relationships between neural, cognitive, social processes, and behavior (Decety et al., 2018). Additionally, researchers are beginning to explore the neurological underpinnings of engagement in violent extremism (Pretus et al., 2018). The model provided above does not seek to replace current theoretical models of the radicalization process that involve personal, social, and cultural factors which influence an individual’s decision (e.g., Mink, 2015), but instead provide a common language (and underlying neurological pathway) through which this process can be conceptualized. In this sense, “vulnerability” to extremism represents the activation of a motivational pathway in response to exposure to extremist content.
Individuals who engage in extremist activity have, to varying degrees, and for varying functions, engaged with extremist material online (Gill et al., 2017). That said, existing research has not examined the psychological processes that underpin the interaction between the person, extremist propaganda, and any eventual extremist behavior (Reeve, 2019). The psychological processes underpinning online exposure and engaging in extremism are likely complex and dynamic (Horgan, 2019). One plausible way to overcome the stagnation in the psychological study of the terrorist is to apply lenses from more established fields of study (e.g., Ligon et al., 2015). Adopting such theoretical perspectives can have significant benefits, in that existing theories have much longer and more established empirical backing (Hunter et al., 2017). For example, psychologists were able to apply theories from Industrial/Organizational (I/O) psychology to terrorism by identifying the overlap between the challenges of traditional organizations and those of terrorist groups (e.g., recruitment or leader development; Hunter et al., 2017). Kruglanski et al. (2017) focused on the role of deviance and extremism (in general) in terrorist behavior to develop a general framework of violent extremism. In the current paper we focus on the role of motivation. One of the benefits of focusing on the RST is that it has a wealth of behavioral, psychological, neurological and physiological research that has established both the trait level individual differences associated with each form of motivation, and the state level physiological and neurological pathways that govern each motivational pathway. As such, the extant RST literature provides a framework to further study the model proposed above. Based on the RST model outlined above, we can hypothesize that which motivational pathway is activated (and indeed the intensity of that activation) is related to state and trait personality factors, as well as the phenomenological process of engaging with the material (which may be different based on the individuals mood, or the nature of the material; see Frischlich et al., 2015). Individuals for whom exposure to violent extremist content online create a wanting motivational state likely possess personality and neurological risk factors that predict intention to engage (i.e., testosterone-driven needs such as the need for social dominance and status) but also the ability to persist and strive to achieve a long-term goal which is associated with processes such as delay-discounting, and the ability to persist despite difficulties and fear (Howard and Crayne, 2019). In Table 1, we outline the overlap between correlates of the four proposed RST pathways with both personality factors associated with each type of response. Based on Table 1 we are able to put forward several hypotheses for future testing based on the presence of BAS/BIS associated traits (e.g., impulsiveness and sensation-seeking) and their reaction when exposed to extremist material (see Table 2). Furthermore, given that different BAS motivational reactions function independently, different patterns of BAS activation may occur based on an individual’s underlying BAS sensitivities. For example, individuals high in opioid associated traits such as reward sensitivity are more likely to have an approach-based liking response to exposure to extremist propaganda that is driven by liking (hedonistic pleasure) rather than a long-term behavioral desire to achieve a long-term goal (wanting). Thus, the specific nature of an individuals’ approach motivation in response to exposure to particular types of online extremist content can be predicted (e.g., avoidance vs., reactive approach vs., wanting vs., liking) based on the extent to which their baseline tendencies are associated with the correlates of each form of motivation. However, as “liking” often leads to “wanting,” it is also possible for individuals to be characterized by both high sensitivities in both BAS-wanting and BAS-liking and their associated personality traits (see Table 1) in which case an overlap in correlates for each motivational pathway would be expected. In these instances, it would be expected, regardless of the liking response, that if a wanting response is activated and the goal prioritized, an individual would be driven by incentive motivation to engage in a purposeful effort to achieve this goal.
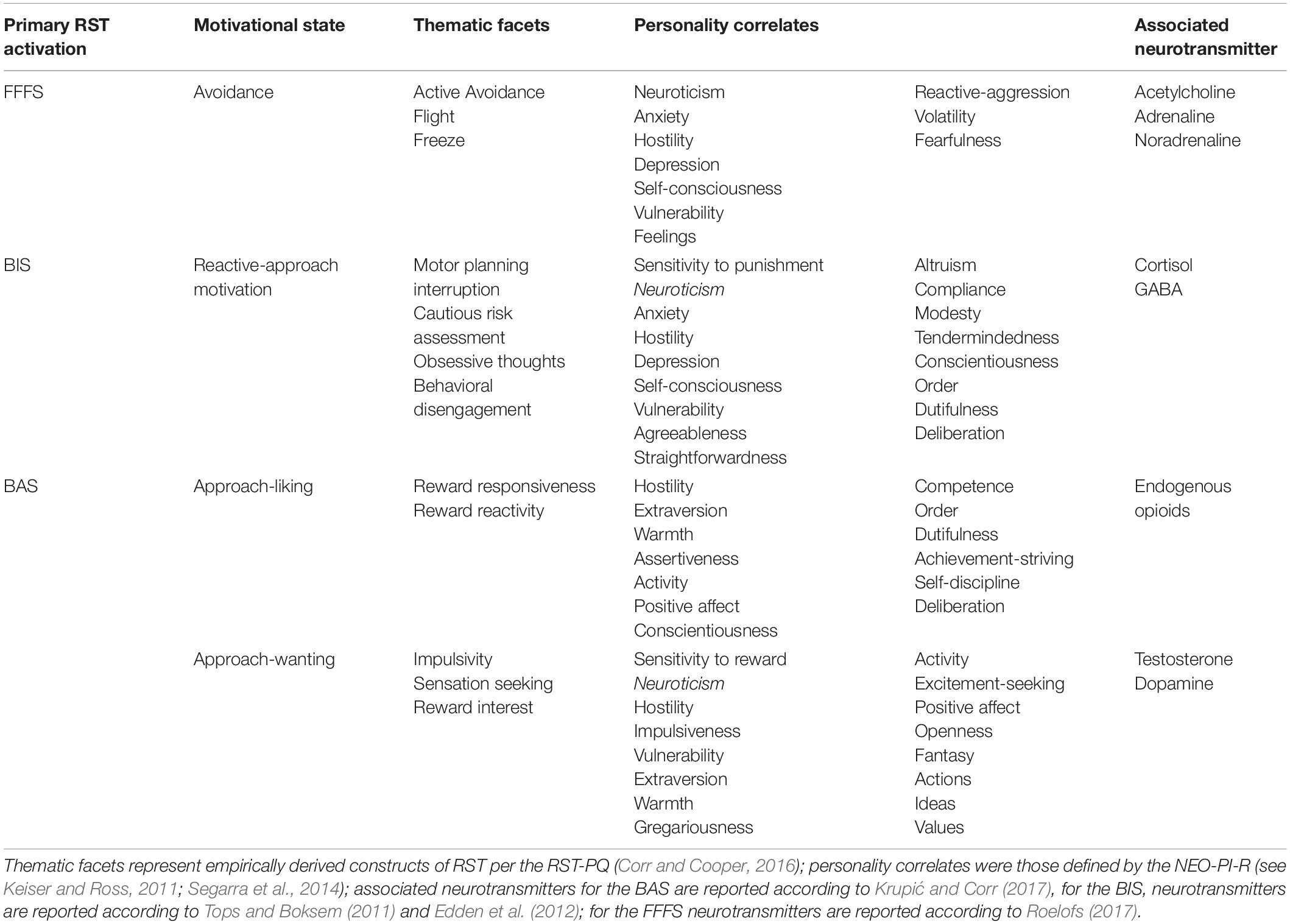
Table 1. Reinforcement Sensitivity Theory (RST) pathways and associated personality traits and neurotransmitters.

Table 2. Possible hypotheses involving Reinforcement Sensitivity Theory (RST) personality traits and reactions following exposure to extremist content.
Limitations
While the proposed pathway model provides several important benefits to the psychological study of violent extremism, there are several important limitations to consider. The first of those is that this paper does not adopt incorporate all processes that exist within the RST framework and indeed offer even more theoretical granularity as it relates to motivation. In a review of the five most frequently used RST questionnaires, Krupić et al. (2016) classified the BAS scales from the five questionnaires into four groups that represented different forms of BAS activation: wanting, striving, liking, and capturing. Despite the distinction of wanting/linking being the more established BAS separation, with current neuroscience studies not clearly disaggregated “wanting” and “incentive motivation” (e.g., Berridge and Robinson, 2003, 2016), there is an important difference within “wanting” between wishing for something (wanting) and acting to attain it (striving/capturing). Furthermore, these four BAS processes can also be viewed as stages within a single longitudinal dynamic process in which a single individual moves throughout a dynamic BAS process that begins with wanting, moves through striving, to capturing and finally liking (Corr and Krupić, 2017). Thus, within the BAS system, there is a spatial-temporal dynamic in which an individual moves through different stages BAS, rather than being differentiated across different BAS processes. In this article, we focus on the initial exposure to extremist content and the implications of four different forms of motivational reaction (avoidance, reactive-approach, approach-wanting, and approach-liking), that said the journey beyond first exposure that one takes is likely to be far more complex and potentially represent the longitudinal BAS process proposed by Krupić and Corr (2017) that include the striving and capturing aspects of the BAS not covered in the current paper. Thus, while this paper outlines what could be perceived as a first-contact typology of reactions, the longitudinal process that governs the movement toward behavior could involve multiple RST pathways working in tandem, or even in parallel. This while this paper proposes a typology of RST reactions, and emerging researching is supporting the role of BAS processes in governing reactions to extremist content (Shortland and McGarry, 2022), more research is needed to fully understand the complex role that RST processes play in the movement toward terrorist behavior.
Despite these limitations, recent reviews of terrorism research have argued that the field is no closer to answering the simple question, “What leads a person to turn to political violence?” than it was 10 years ago (Sageman, 2014). Other reviews, while less extreme in their conclusion, do maintain that the field requires better empirical assessment. Silke (2013) argues that more needs to be done before building on past research, rather than just rehashing it (p. 34). Schuurman’s (2019) analysis of over 3,000 articles published in leading terrorism-specific journals between 2007 and 2016 found that over half used primary sources. But in terms of psychological theory, most theories remain unsubstantiated and unfalsifiable, relying on metaphors such as pathways, stairways, and pyramids. Thus, this provides an opportunity for falsifiable hypotheses to be developed, tested, and if appropriate, rejected. This remains the cornerstone of the scientific method yet has long eluded those who study terrorism (Lygre et al., 2011). To put this point in perspective, we present in Table 2 a series of testable and falsifiable hypotheses using common RST principles/methods (Corr and McNaughton, 2012; Gerson et al., 2017; Bacon et al., 2018; Satchell et al., 2018). As can be seen in Table 2, a series of hypotheses involving personality traits (i.e., hostility) and reaction to exposure to extremist material.
In addition to this, while one of the important benefits of disaggregating the motivations of those who view extremist material online is the ability to infer judgments of risk, there is no a priori evidence that a liking reaction de facto implies lower risk. Instead, it could imply greater risk. For example, it is viable that the short-term hedonistic pleasure associated with the concept of liking could also be used to explain the decision for a violent extremist offender to engage in a short time-frame attack that involves little (to no) planning such as crude knife, vehicle, or firearm attacks we have seen in recent years. What this means then is that while we may differentiate viewer motivation, the liking/wanting differentiation does not necessarily dissociate those who do act, from those who do not. Instead, it may differentiate those who engage in a long-term planning process, vs. a short-term planning process. Again, this does not invalidate the need nor theoretical importance of RST in the study of violent extremism, but it does limit the conflation of differentiation of process and of outcome.
Conclusion
It has long been argued that in order to move the psychological study of terrorism forward a multidimensional framework must be adopted that emphasizes the relationships between neural, cognitive, and social processes (Decety et al., 2018). In this paper, we conceptualized the effects of exposure to extremist content online via the RST model of motivation. This model does not seek to replace current theoretical models of the radicalization process that involve personal, social and cultural factors influencing an individual’s decision (e.g., Mink, 2015), but instead provides a common language (and underlying pathways) through which this process can be conceptualized. Specifically, many of the processes conceptualized within the RST model map onto previous assertions about the process of radicalization. In most, there is a general fear reaction from exposure to violent extremism (conceptualized here as FFFS-driven avoidance; Shortland et al., 2017). In some, violent extremism provides an avenue to address underlying anxieties about oneself and their identify (reactive-approach and the quest for significance; McGregor et al., 2015; Kruglanski et al., 2017). Others are drawn to extremist content due to a range of BAS-driven correlates such as sensation-seeking, a sense of adventure, or the “thrill” and “excitement” (Haggerty and Bucerius, 2020). Finally, in those who are drawn to such content, there are those whose pleasure comes from simply viewing and engaging with extremist content (Shortland, 2016) and those whose engagement drives a long-term motivational goal to engage with violent extremist content or action (liking vs. wanting; see Berridge and Robinson, 2003).
We agree that no one theory is a panacea of violent extremism. However, the current state of the research studying violent extremist content online is missing is validated empirical frameworks that can be used to guide empirical testing of hypotheses and thus, the advancement of theory (Conway, 2017, p. 82; Frissen, 2021). RST is consistently used as a motivational framework to explain the effect of wider personality, social and environmental influences on motivational behavior. Furthermore, those who have used RST as a framework to explore a range of behaviors (both pro and anti-social) have identified that different forms of behavior are associated with different forms of BAS activation. Thus, while the outlined model is theoretical, and indeed the hypotheses are exploratory, each is based on a wealth of literature that has previously explored the relationships among personality, neurological processing, motivation, and behavioral outcomes. Furthermore, each can be tested through standard methods used by psychologists to study the role of neurological and physiological predictors of reactions to media content (e.g., Bushman, 1995; Carnagey et al., 2007; Zillmann and Weaver, 2007) and, critically, these hypotheses are falsifiable, allowing this model to be refined, validated, or rejected.
Data Availability Statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author Contributions
NS and PM developed the theoretical framework for the manuscript. JP led the investigation and outline of perspectives from biosocial criminology. AP, TG, and NS provided review and expert insight for theory development. All authors contributed to the article and approved the submitted version.
Funding
This work was supported by the Department of Defense Office of Naval Research award (#N00014-18-1-2367-A00001).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
- ^ Throughout this paper when we refer to violent extremist content online we follow the concept of “terroristic content” in that it legitimizes, motivates or enables acts of violence against civilian targets (Holbrook et al., 2013).
References
Aly, A., and Green, L. (2010). Fear, anxiety and the state of terror. Stud. Confl. Terror. 33, 268–281. doi: 10.1080/10576100903555796
Atran, S. (2008). The Making of a Terrorist: A Need for Understanding from the Field Testimony before the House Appropriations Subcommittee on Homeland Security, Washington, DC, March 12, 2008.
Bacon, A. M., Corr, P. J., and Satchell, L. P. (2018). A reinforcement sensitivity theory explanation of antisocial behaviour. Pers. Individ. Differ. 123, 87–93. doi: 10.1016/j.paid.2017.11.008
Berger, J. M., and Morgan, J. (2015). The ISIS Twitter Census: Defining and Describing the Population of ISIS Supporters on Twitter. Washington, DC: The Brookings Institution.
Berkman, E. T., Lieberman, M. D., and Gable, S. L. (2009). BIS, BAS, and response conflict: testing predictions of the revised reinforcement sensitivity theory. Pers. Individ. Differ. 46, 586–591. doi: 10.1016/j.paid.2008.12.015
Berridge, K. C. (2009). Wanting and liking: observations from the neuroscience and psychology laboratory. Inquiry 52, 378–398. doi: 10.1080/00201740903087359
Berridge, K. C., and Kringelbach, M. L. (2008). Affective neuroscience of pleasure: reward in humans and animals. Psychopharmacology 199, 457–480. doi: 10.1007/s00213-008-1099-6
Berridge, K. C., and Robinson, T. E. (2003). Parsing reward. Trends Neurosci. 26, 507–513. doi: 10.1016/S0166-2236(03)00233-9
Berridge, K. C., and Robinson, T. E. (2016). Liking, wanting, and the incentive-sensitization theory of addiction. Am. Psychol. 71:670. doi: 10.1037/amp0000059
Berridge, K. C., Robinson, T. E., and Aldridge, J. W. (2009). Dissecting components of reward:‘liking’,‘wanting’, and learning. Curr. Opin. Pharmacol. 9, 65–73. doi: 10.1016/j.coph.2008.12.014
Bowman-Grieve, L. (2009). Exploring “Stormfront”: a virtual community of the radical right. Stud. Confl. Terror. 32, 989–1007. doi: 10.1080/10576100903259951
Bowman-Grieve, L., and Conway, M. (2012). Exploring the form and function of dissident Irish Republican online discourses. Media War Confl. 5, 71–85. doi: 10.1177/1750635211434371
Bushman, B. J. (1995). Moderating role of trait aggressiveness in the effects of violent media on aggression. J. Pers. Soc. Psychol. 69:950. doi: 10.1037//0022-3514.69.5.950
Caluya, G. (2013). Sexual geopolitics: the ‘blue balls’ theory of terrorism. Continuum 27, 54–66. doi: 10.1080/10304312.2013.737193
Canadian Network for Research on Terrorism, Security and Society [TSAS] (2015). Personality Traits and Terrorism. Working Paper Series No. 15-05. Waterloo, ON: Canadian Network for Research on Terrorism, Security and Society [TSAS], 1–29.
Carnagey, N. L., Anderson, C. A., and Bushman, B. J. (2007). The effect of video game violence on physiological desensitization to real-life violence. J. Exp. Soc. Psychol. 43, 489–496. doi: 10.1016/j.jesp.2006.05.003
Carver, C. S. (2004). Negative affects deriving from the behavioral approach system. Emotion 4:3. doi: 10.1037/1528-3542.4.1.3
Conway, M. (2006). Terrorism and the internet: new media—new threat? Parliamentary Affairs 59, 283–298. doi: 10.1093/pa/gsl009
Conway, M. (2017). Determining the role of the internet in violent extremism and terrorism: six suggestions for progressing research. Stud. Confl. Terror. 40, 77–98. doi: 10.1080/1057610x.2016.1157408
Corr, P. J. (2001). Testing problems in JA Gray’s personality theory: a commentary on. Pers. Individ. Differ. 30, 333–352. doi: 10.1016/s0191-8869(00)00028-3
Corr, P. J. (2004). Reinforcement sensitivity theory and personality. Neurosci. Biobehav. Rev. 28, 317–332.
Corr, P. J. (2013). Approach and avoidance behaviour: multiple systems and their interactions. Emot. Rev. 5, 285–290. doi: 10.1177/1754073913477507
Corr, P. J., and Cooper, A. J. (2016). The reinforcement sensitivity theory of personality questionnaire (RST-PQ): development and validation. Psychol. Assess. 28:1427. doi: 10.1037/pas0000273
Corr, P. J., and Krupić, D. (2017). “Motivating personality: approach, avoidance, and their conflict,” in Advances in Motivation Science, ed. A. Elliot (London: Elsevier). doi: 10.1016/bs.adms.2017.02.003
Corr, P. J., and McNaughton, N. (2012). Neuroscience and approach/avoidance personality traits: a two stage (valuation–motivation) approach. Neurosci. Biobehav. Rev. 36, 2339–2354. doi: 10.1016/j.neubiorev.2012.09.013
Decety, J., Pape, R., and Workman, C. I. (2018). A multilevel social neuroscience perspective on radicalization and terrorism. Soc. Neurosci. 13, 511–529. doi: 10.1080/17470919.2017.1400462
Depue, R. A., and Collins, P. F. (1999). On the psychobiological complexity and stability of traits. Behav. Brain Sci. 22, 541–555. doi: 10.1017/S0140525X99462041
Edden, R. A., Crocetti, D., Zhu, H., Gilbert, D. L., and Mostofsky, S. H. (2012). Reduced GABA concentration in attention-deficit/hyperactivity disorder. Arch. Gen. Psychiatry 69, 750–753. doi: 10.1001/archgenpsychiatry.2011.2280
Ekman, M. (2014). The dark side of online activism: Swedish right-wing extremist video activism on YouTube. Mediekultur 30:21.
Fahmy, S., Cho, S., Wanta, W., and Song, Y. (2006). Visual agenda-setting after 9/11: individuals’ emotions, image recall, and concern with terrorism. Vis. Commun. Q. 13, 4–15. doi: 10.1207/s15551407vcq1301_2
Franken, I. H. A., and Muris, P. E. H. M. (2006). BIS/BAS personality characteristics and college students’ substance use. Pers. Individ. Differ. 40, 1497–1503. doi: 10.1016/j.paid.2005.12.005
Freiburger, T., and Crane, J. S. (2008). A systematic examination of terrorist use of the internet. Int. J. Cyber Criminol. 2, 309–319.
Frischlich, L., Rieger, D., Hein, M., and Bente, G. (2015). Dying the right-way? Interest in and perceived persuasiveness of parochial extremist propaganda increases after mortality salience. Front. Psychol. 6:1222. doi: 10.3389/fpsyg.2015.01222
Frissen, T. (2021). Internet, the great radicalizer? Exploring relationships between seeking for online extremist materials and cognitive radicalization in young adults. Comput. Hum. Behav. 114:106549. doi: 10.1016/j.chb.2020.106549
Gerson, J., Plagnol, A. C., and Corr, P. J. (2017). Passive and active Facebook use measure (PAUM): validation and relationship to the reinforcement sensitivity theory. Pers. Individ. Differ. 117, 81–90. doi: 10.1016/j.paid.2017.05.034
Gill, P., and Corner, E. (2013). Disaggregating terrorist offenders: implications for research and practice. Criminol. Public Policy 12:93. doi: 10.1111/1745-9133.12015
Gill, P., Clemmow, C., Hetzel, F., Rottweiler, B., Salman, N., Van Der Vegt, I., et al. (2021). Systematic review of mental health problems and violent extremism. J. Forensic Psychiatry Psychol. 32, 51–78.
Gill, P., Silver, J., Horgan, J., and Corner, E. (2017). Shooting alone: the pre-attack experiences and behaviors of US solo mass murderers. J. Forensic Sci. 62, 710–714. doi: 10.1111/1556-4029.13330
Gøtzsche-Astrup, O. (2019). Personality moderates the relationship between uncertainty and political violence: evidence from two large US samples. Pers. Individ. Differ. 139, 102–109. doi: 10.1016/j.paid.2018.11.006
Gray, J. A. (1973). “Causal theories of personality and how to test them,” in Multivariate Analysis and Psychological Theory, 16, ed. J. R. Royce (London: Academic Press), 302–354.
Gray, J. A. (1987). “The neuropsychology of emotion and personality,” in Cognitive Neurochemistry, eds S. M. Stahl, S. D. Iversen, and E. C. Goodman (Oxford: Oxford University Press), 171–190.
Gray, J. A., and McNaughton, N. (2000). The Neuropsychology of Anxiety. New York, NY: Oxford University Press.
Gray, J. A., and McNaughton, N. (2003). The Neuropsychology of Anxiety: An Enquiry into the Function of the Septo-Hippocampal System, 2nd Edn. Oxford: Oxford University Pres.
Greenaway, K. H., Storrs, K. R., Philipp, M. C., Louis, W. R., Hornsey, M. J., and Vohs, K. D. (2015). Loss of control stimulates approach motivation. J. Exp. Soc. Psychol. 56, 235–241. doi: 10.1016/j.jesp.2014.10.009
Haggerty, K. D., and Bucerius, S. M. (2020). Radicalization as martialization: towards a better appreciation for the progression to violence. Terror. Polit. Violence 32, 768–788. doi: 10.1080/09546553.2017.1404455
Harmon-Jones, E., and Peterson, C. K. (2008). Effect of trait and state approach motivation on aggressive inclinations. J. Res. Pers. 42, 1381–1385. doi: 10.1016/j.jrp.2008.05.001
Hawi, D., Osborne, D., Bulbulia, J., and Sibley, C. G. (2019). Terrorism anxiety and attitudes toward Muslims. N. Zeal. J. Psychol. 48, 80–89. doi: 10.1038/s41598-022-05678-x
Hirsh, J. B., and Kang, S. K. (2016). Mechanisms of identity conflict: uncertainty, anxiety, and the behavioral inhibition system. Pers. Soc. Psychol. Rev. 20, 223–244. doi: 10.1177/1088868315589475
Hoffman, B. (2006). The Use of the Internet by Islamic Extremists. Testimony Presented to the House Permanent Select Committee on Intelligence on May 4, 2006. Santa Monica, CA: Rand Corporation.
Hogg, M. A., and Adelman, J. (2013). Uncertainty–identity theory: extreme groups, radical behavior, and authoritarian leadership. J. Soc. Issues 69, 436–454. doi: 10.1111/josi.12023
Holbrook, D., Ramsay, G., and Taylor, M. (2013). “Terroristic content”: towards a grading scale. Terror. Polit. Violence 25, 202–223. doi: 10.1080/09546553.2011
Horgan, J. G. (2019). “Psychological approaches to the study of terrorism,” in The Oxford Handbook of Terrorism (Oxford: Oxford University Press).
Horgan, J., and Bjorgo, T. (2009). Leaving Terrorism Behind: Individual and Collective Disengagement (London: Routledge).
Horgan, J. G., Gill, P., Bouhana, N., Silver, J., and Corner, E. (2016). Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types with Implications for Criminal Justice Training and Education. Rockville, MD: National Criminal Justice Reference Service.
Horgan, J., Shortland, N., Abbasciano, S., and Walsh, S. (2016). Actions speak louder than words: a behavioral analysis of 183 individuals convicted for terrorist offenses in the United States from 1995 to 2012. J. Forensic Sci. 61, 1228–1237. doi: 10.1111/1556-4029.13115
Howard, M. C., and Crayne, M. P. (2019). Persistence: defining the multidimensional construct and creating a measure. Pers. Individ. Differ. 139, 77–89. doi: 10.1016/j.paid.2018.11.005
Howe, T. R. (2011). “Multifinality,” in Encyclopedia of Child Behavior and Development, eds S. Goldstein and J. A. Naglieri (Boston, MA: Springer), doi: 10.1007/978-0-387-79061-9_1864
Hunter, S. T., Shortland, N. D., Crayne, M. P., and Ligon, G. S. (2017). Recruitment and selection in violent extremist organizations: exploring what industrial and organizational psychology might contribute. Am. Psychol. 72:242. doi: 10.1037/amp0000089
Jackson, C. J. (2003). Gray’s reinforcement sensitivity theory: a psychometric critique. Pers. Individ. Differ. 34, 533–544. doi: 10.1016/s0191-8869(02)00305-7
Jasko, K., LaFree, G., and Kruglanski, A. (2017). Quest for significance and violent extremism: the case of domestic radicalization. Polit. Psychol. 38, 815–831. doi: 10.1111/pops.12376
Jasko, K., Szastok, M., Grzymala-Moszczynska, J., Maj, M., and Kruglanski, A. W. (2019). Rebel with a cause: personal significance from political activism predicts willingness to self-sacrifice. J. Soc. Issues 75, 314–349. doi: 10.1111/josi.12307
Jonas, E., McGregor, I., Klackl, J., Agroskin, D., Fritsche, I., Holbrook, C., et al. (2014). “Threat and defense: from anxiety to approach,” in Advances in Experimental Social Psychology, eds J. M. Olson and M. P. Zanna Vol. 49, (Cambridge, MA: Academic Press), 219–286.
Keiser, H. N., and Ross, S. R. (2011). Carver and Whites’ BIS/FFFS/BAS scales and domains and facets of the five factor model of personality. Pers. Individ. Differ. 51, 39–44.
Klackl, J., Jonas, E., and Fritsche, I. (2018). Neural evidence that the behavioral inhibition system is involved in existential threat processing. Soc. Neurosci. 13, 355–371. doi: 10.1080/17470919.2017.1308880
Kruglanski, A. W., and Orehek, E. (2011). “The role of the quest for personal significance in motivating terrorism,” in The Psychology of Social Conflict and Aggression, eds J. Forgas, A. Kruglanski, and K. Williams Hove: Psychology Press, 153–166. doi: 10.1002/ab.21863
Kruglanski, A. W., Gelfand, M. J., Bélanger, J. J., Sheveland, A., Hetiarachchi, M., and Gunaratna, R. (2014). The psychology of radicalization and deradicalization: how significance quest impacts violent extremism. Polit. Psychol. 35, 69–93. doi: 10.1111/pops.12163
Kruglanski, A. W., Jasko, K., Chernikova, M., Dugas, M., and Webber, D. (2017). To the fringe and back: violent extremism and the psychology of deviance. Am. Psychol. 72:217. doi: 10.1037/amp0000091
Krupić, D., and Corr, P. J. (2017). Moving forward with the BAS: towards a neurobiology of multidimensional model of approach motivation. Psychol. Topics 26, 25–45. doi: 10.31820/pt.26.1.2
Krupić, D., Corr, P. J., Ručević, S., Križanić, V., and Gračanin, A. (2016). Five reinforcement sensitivity theory (RST) of personality questionnaires: comparison, validity and generalization. Pers. Individ. Differ. 97, 19–24. doi: 10.1016/j.paid.2016.03.012
Krupić, D., Žuro, B., and Krupić, D. (2021). Big Five traits, approach-avoidance motivation, concerns and adherence with COVID-19 prevention guidelines during the peak of pandemic in Croatia. Pers. Individ. Differ. 179:110913. doi: 10.1016/j.paid.2021.110913
LaFree, G., Jensen, M. A., James, P. A., and Safer-Lichtenstein, A. (2018). Correlates of violent political extremism in the United States. Criminology 56, 233–268. doi: 10.1111/1745-9125.12169
Lemieux, A. F., Brachman, J. M., Levitt, J., and Wood, J. (2014). Inspire magazine: a critical analysis of its significance and potential impact through the lens of the information, motivation, and behavioral skills model. Terror. Polit. Violence 26, 354–371. doi: 10.1080/09546553.2013.828604
Levin, S., Henry, P. J., Pratto, F., and Sidanius, J. (2003). Social dominance and social identity in Lebanon: implications for support of violence against the West. Group Process. Intergr. Relat. 6, 353–368. doi: 10.1177/13684302030064003
Ligon, G. S., Harms, M., and Derrick, D. C. (2015). Lethal brands: how VEOs build reputations. J. Strateg. Secur. 8, 27–42. doi: 10.5038/1944-0472.8.1.1436
Lygre, R. B., Eid, J., Larsson, G., and Ranstorp, M. (2011). Terrorism as a process: a critical review of Moghaddam’s “Staircase to Terrorism”. Scand. J. Psychol. 52, 609–616. doi: 10.1111/j.1467-9450.2011.00918.x
Marcus, G. E., and MacKuen, M. B. (1993). Anxiety, enthusiasm, and the vote: the emotional underpinnings of learning and involvement during presidential campaigns. Am. Polit. Sci. Rev. 87, 672–685. doi: 10.2307/2938743
Mardaga, S., and Hansenne, M. (2007). Relationships between Cloninger’s biosocial model of personality and the behavioral inhibition/approach systems (BIS/BAS). Pers. Individ. Differ. 42, 715–722. doi: 10.1016/j.paid.2006.08.013
Marshall, R. D., Bryant, R. A., Amsel, L., Suh, E. J., Cook, J. M., and Neria, Y. (2007). The psychology of ongoing threat: relative risk appraisal, the September 11 attacks, and terrorism-related fears. Am. Psychol. 62:304. doi: 10.1037/0003-066X.62.4.304
McGregor, I., Hayes, J., and Prentice, M. (2015). Motivation for aggressive religious radicalization: goal regulation theory and a personality× threat× affordance hypothesis. Front. Psychol. 6:1325. doi: 10.3389/fpsyg.2015.01325
McGregor, I., Prentice, M., and Nash, K. (2013). Anxious uncertainty and reactive approach motivation (RAM) for religious, idealistic, and lifestyle extremes. J. Soc. Issues 69, 537–563. doi: 10.1111/josi.12028
McNaughton, N., and Corr, P. (2004). A two-dimensional view of defensive systems: defensive distance and fear/anxiety. Neurosci. Biobehav. Rev. 28, 285–305. doi: 10.1016/j.neubiorev.2004.03.005
Mink, C. (2015). It’s about the group, not god: social causes and cures for terrorism. J. Deradicalization 5, 63–91.
Möller-Leimkühler, A. M. (2018). Why is terrorism a man’s business? CNS Spectr. 23, 119–128. doi: 10.1017/S1092852917000438
Neo, L. S. (2019). “An Internet-mediated pathway for online radicalisation: RECRO,” in Violent Extremism: Breakthroughs in Research and Practice, ed Information Resources Management Association (Hershey, PA: IGI Global), 62–89. doi: 10.4018/978-1-5225-7119-3.ch005
Parker, K. E. M., Farrell, N., and Walker, B. R. (2020). The impact of reinforcement sensitivity theory on aggressive behavior. J. Interpers. Violence 37:NP3084–NP3106. doi: 10.1177/0886260520948144
Perkins, A. M., Kemp, S. E., and Corr, P. J. (2007). Fear and anxiety as separable emotions: an investigation of the revised reinforcement sensitivity theory of personality. Emotion 7:252. doi: 10.1037/1528-3542.7.2.252
Pfefferbaum, B., Nixon, S. J., Tivis, R. D., Doughty, D. E., Pynoos, R. S., Gurwitch, R. H., et al. (2001). Television exposure in children after a terrorist incident. Psychiatry 64, 202–211. doi: 10.1521/psyc.64.3.202.18462
Pickering, A. D., and Gray, J. A. (1999). “The neuroscience of personality,” in Handbook of Personality: Theory and Research, 2nd edn, eds L. A. Pervin and O. P. John (New York, NY: The Guilford Press).
Pretus, C., Hamid, N., Sheikh, H., Ginges, J., Tobeña, A., Davis, R., et al. (2018). Neural and behavioral correlates of sacred values and vulnerability to violent extremism. Front. Psychol. 9:2462. doi: 10.3389/fpsyg.2018.02462
Putman, P., Hermans, E., and van Honk, J. (2004). Emotional stroop performance for masked angry faces: it’s BAS, not BIS. Emotion 4:305. doi: 10.1037/1528-3542.4.3.305
Pyszczynski, T. (2004). What are we so afraid of?: a terror management theory perspective on the politics of fear. Soc. Res. 71, 827–848.
Reeve, Z. (2019). Terrorism as parochial altruism: experimental evidence. Terror. Polit. Violence 33, 1–24. doi: 10.1080/09546553.2019.1635121
Ritter, K. (2020). Man in Vegas Terror Case Charged with US Child Abuse Count. New York, NY: AP NEWS.
Roelofs, K. (2017). Freeze for action: neurobiological mechanisms in animal and human freezing. Philos. Transac. R. Soc. B Biol. Sci. 372:20160206. doi: 10.1098/rstb.2016.0206
Ross, S. R., Molto, J., Poy, R., Segarra, P., Pastor, M. C., and Montanés, S. (2007). Gray’s model and psychopathy: BIS but not BAS differentiates primary from secondary psychopathy in noninstitutionalized young adults. Pers. Individ. Differ. 43, 1644–1655. doi: 10.1016/j.paid.2007.04.020
Sageman, M. (2014). The stagnation in terrorism research. Terror. Polit. Violence 26, 565–580. doi: 10.1038/s41586-019-1725-y
Satchell, L. P., Bacon, A. M., Firth, J. L., and Corr, P. J. (2018). Risk as reward: reinforcement sensitivity theory and psychopathic personality perspectives on everyday risk-taking. Pers. Individ. Differ. 128, 162–169. doi: 10.1016/j.paid.2018.02.039
Schimel, J., Wohl, M. J., and Williams, T. (2006). Terror management and trait empathy: evidence that mortality salience promotes reactions of forgiveness among people with high (vs. low) trait empathy. Motiv. Emot. 30, 214–224. doi: 10.1007/s11031-006-9040-y
Schlenger, W. E., Caddell, J. M., Ebert, L., Jordan, B. K., Rourke, K. M., Wilson, D., et al. (2002). Psychological reactions to terrorist attacks: findings from the National Study of Americans’ Reactions to September 11. JAMA 288, 581–588. doi: 10.1001/jama.288.5.581
Schuster, M. A., Stein, B. D., Jaycox, L. H., Collins, R. L., Marshall, G. N., Elliott, M. N., et al. (2001). A national survey of stress reactions after the September 11, 2001, terrorist attacks. N. Engl. J. Med. 345, 1507–1512. doi: 10.1056/NEJM200111153452024
Schuurman, B. (2019). Topics in terrorism research: reviewing trends and gaps, 2007-2016. Crit. Stud. Terror. 12, 463–480. doi: 10.1080/17539153.2019.1579777
Segarra, P., Poy, R., López, R., and Moltó, J. (2014). Characterizing carver and white’s BIS/BAS subscales using the five factor model of personality. Pers. Individ. Differ. 61-62, 18–23. doi: 10.1016/j.paid.2013.12.027
Shortland, N. D. (2016). “On the internet, nobody knows you’re a dog”: the online risk assessment of violent extremists,” in Combating Violent Extremism and Radicalization in the Digital Era, eds M. Khader, L.S. Neo, G. Ong, E.T. Mingyi, and J. Chin (Hershey, PA: IGI Global), 349–373. doi: 10.4018/978-1-5225-0156-5.ch017
Shortland, N. D., and McGarry, P. (2022). The personality and propaganda puzzle: exploring the effect of personality on exposure to extremist content online. Psychol. Violence 12, 1–10. doi: 10.1037/vio0000396
Shortland, N. D., Nader, E., Imperillo, N., Ross, K., and Dmello, J. (2017). The interaction of extremist propaganda and anger as predictors of violent responses. J. Interpers. Violence 36, 1–21. doi: 10.1177/0886260517747599
Shortland, N. D., Nader, E., Thompson, L., and Palasinski, M. (2020). Is extreme in the eye of the beholder? An experimental assessment of extremist cognitions. J. Interpers. Violence 37:886260520958645. doi: 10.1177/0886260520958645
Shortland, N., and Forest, J. J. (2020). “Tracking terrorism: the role of technology in risk assessment and monitoring of terrorist offenders,” in Science Informed Policing, eds B. Fox, J. Reid, and A. Masys (Cham: Springer), 57–76. doi: 10.1007/978-3-030-41287-6_4
Silke, A. (2000). Beating the water: the terrorist search for power, control and authority. Terror. Polit. Violence 12, 76–96. doi: 10.1080/09546550008427562
Silke, A. (2003). Terrorists, Victims and Society: Psychological Perspectives on Terrorism and its Consequences. Chichester: Wiley.
Silke, A. (2004). “The road less travelled: recent trends in terrorism research,” in Research on Terrorism: Trends, Achievements and Failures, ed A. Silke (London: Frank Cass), 186–213. doi: 10.4324/9780203500972.ch10
Silke, A. (2008). Holy warriors: exploring the psychological processes of jihadi radicalization. Eur. J. Criminol. 5, 99–123. doi: 10.1177/1477370807084226
Silke, A. (2013). “The golden age? Assessing the state of terrorism studies,” in Proceedings of the Keynote Speech at 7th Annual Conference of Society of Terrorism Research, Vol. 27, (London).
Sleegers, W. W., Proulx, T., and van Beest, I. (2015). Extremism reduces conflict arousal and increases values affirmation in response to meaning violations. Biol. Psychol. 108, 126–131. doi: 10.1016/j.biopsycho.2015.03.012
Smillie, L. D., Jackson, C. J., and Dalgleish, L. I. (2006). Conceptual distinctions among Carver and White’s (1994) BAS scales: a reward-reactivity versus trait impulsivity perspective. Pers. Individ. Differ. 40, 1039–1050. doi: 10.1016/j.paid.2005.10.012
Süllwold, L. (1981). “Stages in the development of terrorists,” in Lebenslauf-Analysen, Vol. 2, eds J. G. Schmidtchen and L. Süllwold (Wiesbaden: VS Publishing House for Social Sciences), 79–116.
Talbot, D. (2005). Terror’s Server-Fraud, Gruesome Propaganda, Terror Planning: The Net Enables it all. The Online Industry can Help Fix it. Cambridge, MA: Technology Review.
Taylor, J., and Eitle, D. (2015). The moderating role of BIS/BAS personality tendencies in the relationship between general strain and crime. Deviant Behav. 36, 874–889. doi: 10.1080/01639625.2014.977188
Toohey, K., and Taylor, T. (2008). Mega events, fear, and risk: terrorism at the Olympic Games. J. Sport Manag. 22, 451–469. doi: 10.1123/jsm.22.4.451
Tops, M., and Boksem, M. A. (2011). Cortisol involvement in mechanisms of behavioral inhibition. Psychophysiology 48, 723–732. doi: 10.1111/j.1469-8986.2010.01131.x
Trip, S., Bora, C. H., Marian, M., Halmajan, A., and Drugas, M. I. (2019). Psychological mechanisms involved in radicalization and extremism. A rational emotive behavioral conceptualization. Front. Psychol. 10:437. doi: 10.3389/fpsyg.2019.00437
Vidino, L., and Hughes, S. (2015). Countering Violent Extremism in America. Washington, DC: The George Washington University Center for Cyber and Homeland Security.
Von Behr, I., Reding, A., Edwards, C., and Gribbon, L. (2013). Radicalisation in the Digital Era: The Use of the Internet in 15 Cases of Terrorism and Extremism. Brussels: Rand, 17.
Watkins, E., Moberly, N. J., and Moulds, M. L. (2008). Processing mode causally influences emotional reactivity: distinct effects of abstract versus concrete construal on emotional response. Emotion 8:364. doi: 10.1037/1528-3542.8.3.364
Webber, D., and Kruglanski, A. W. (2018). The social psychological makings of a terrorist. Curr. Opin. Psychol. 19, 131–134. doi: 10.1016/j.copsyc.2017.03.024
Weimann, G. (2006). Virtual disputes: the use of the Internet for terrorist debates. Stud. Confl. Terror. 29, 623–639. doi: 10.1080/10576100600912258
Weimann, G. (2011). Cyber-fatwas and terrorism. Stud. Confl. Terror. 34, 765–781. doi: 10.1080/1057610x.2011.604831
Wiktorowicz, Q. (2005). Radical Islam Rising: Muslim Extremism in the West. Lanham: Rowman & Littlefield Publishers.
Wray, L. (2018). The role of Neighbourhood Policing in Preventing Extremism. Doctoral dissertation. Huddersfield: University of Huddersfield.
Keywords: Reinforcement Sensitivity Theory, online radicalization, physiology, BIS/BAS, media
Citation: Shortland N, Portnoy J, McGarry P, Perliger A, Gordon T and Anastasio N (2022) A Reinforcement Sensitivity Theory of Violent Extremist Propaganda: The Motivational Pathways Underlying Movement Toward and Away From Violent Extremist Action. Front. Psychol. 13:858392. doi: 10.3389/fpsyg.2022.858392
Received: 31 January 2022; Accepted: 19 April 2022;
Published: 19 May 2022.
Edited by:
Petar Čolović, University of Novi Sad, SerbiaReviewed by:
Philipp Herzberg, Helmut Schmidt University, GermanyKristina Randelovic, University of Niš, Serbia
Copyright © 2022 Shortland, Portnoy, McGarry, Perliger, Gordon and Anastasio. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Neil Shortland, bmVpbF9zaG9ydGxhbmRAdW1sLmVkdQ==
 Neil Shortland
Neil Shortland Jill Portnoy
Jill Portnoy Presley McGarry
Presley McGarry Arie Perliger
Arie Perliger Thomas Gordon
Thomas Gordon Natalie Anastasio
Natalie Anastasio