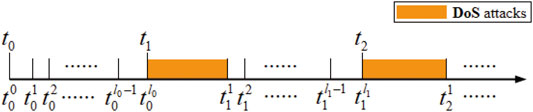- 1School of Mathematical Science, Heilongjiang University, Harbin, China
- 2School of Mechatronics Engineering, Harbin Institute of Technology, Harbin, China
This article focuses on the consensus problem of linear multi-agent systems under denial-of-service attacks and directed switching topologies. With only intermittent communication, the leader-following consensus can be preserved by fully distributed event-triggered strategies. Theoretical analysis shows that the proposed event-triggered resilient controller guarantees the exponential convergence in the presence of denial-of-service attacks and the exclusion of Zeno behavior. Compared to the existing studies where continuous communication between neighboring agents is required, the event-triggered data reduction scheme is provided to tackle the effects of denial-of-service attacks on directed switching topology as well as to avoid continuous communication and reduce energy consumption. The obtained results can be extended to the scenario without a leader. Numerical simulations are finally given to illustrate the effectiveness of the proposed method.
1 Introduction
In past decades, cooperative control of multi-agent systems (MASs) has become one of the significant research interests in many areas, such as artificial intelligent, mathematics, biology, and control engineering (Olfati-Saber and Murray, 2004; Ren et al., 2007; Mei et al., 2016). Consensus control, one of the most important cooperative controls, is to guarantee the agents to achieve an agreement ultimately via neighborhood communication. Many related works on leaderless consensus and leader-following consensus (also known as consensus tracking) have been reported by Li et al., (2016),Qin et al., (2016), Li et al., (2018), and Zhu et al., (2021).
In Ma and Yang, (2016), Wang and Yang, (2016), Wang et al., (2020), and Zhang et al., (2021), continuous communication of neighbor agents and control is required to achieve the consensus for MASs. Recently, many efforts were devoted to the consensus problem for MASs with the event-triggered strategies. The event-triggered control method has obvious advantages which can effectively avoid continuous communication and reduce energy consumption and is widely applied in dealing with the scenario in which the bandwidth of the communication channel in a multi-agent system is limited. To design appropriate event-based control laws and the triggering functions are the main works in the event-triggered consensus problem. Event-triggered and self-triggered control schemes for single- or double-integrator agents have been developed by Dimarogonas et al., (2012), Meng and Chen, (2013), Seyboth et al., (2013), and Fan et al., (2015). For MASs with general linear dynamics, Yang et al., (2016), Cheng et al., (2017), Cheng and Li, (2019), Hu et al., (2020), and Xu and Wu, (2021) considered the consensus problem by designing event-triggered communication and control schemes. Specifically, Cheng et al., (2017) studied the leader-following consensus problem and eliminated the need of continuous communication between neighboring agents, where fixed and switching topologies are considered.
Among the studies on consensus of MASs, the security problem has attracted significant attention, as surveyed by Wang and Yang, (2018) and Wang et al., (2021), due to MASs being vulnerable to malicious attacks. The denial-of-service (DoS) attack is one of the common attacks on communication networks (Qin et al., 2018; Pelechrinis et al., 20212010), in which the legitimate members of MASs are unable to access information resources due to the malicious cyber threat actors. Some interesting results for MASs under DoS attacks have been obtained by Wang and Yang, (2018), Wang et al., (2021), Lu and Yang, (2018), and Zhang et al., (2019). To effectively alleviate needless waste of network resources, the event-triggering strategies for MASs under DoS attacks are proposed by Xu et al., (2019), Feng and Hu, (2020), Sun and Yang, (2020), and Tand et al., (2021). Note that the aforementioned results studied in the fixed topologies, though, for the unreliable communication environment under DoS attacks, the research results of using event-triggered methods to the systems under DoS attacks and directed switching topologies are relatively few.
Motivated by the aforementioned discussion, this article addresses the distributed event-triggered communication and control of linear MASs under DoS attacks, where directed switching topologies are considered. Although the control strategy under DoS attack is also studied by Wang et al., (2021), the continuous controller update is required. Moreover, unlike the result in Feng and Hu, (2020), assuming that the connection network is a fixed topology, a switching topology network including intermittent communication is considered, which is more reasonable in practical application. The contribution in this article is summarized as follows: First, an event-triggered secure approach, for solving the leader-following consensus problem of tracking a time-varying state of the leader agent in the presence of DoS attacks, has been developed. Moreover, while event-triggered control problem under DoS attack is considered in this article, the analysis is focusing on the switching topologies case. Furthermore, it is shown that the event-based control strategy is capable of reducing the frequency of communication and controller updates as well as excluding the Zeno behavior and event-triggered controller for leaderless multi-agent systems is further introduced.
The rest of the article is organized as follows: In Section 2, the necessary preliminaries are introduced. The achievement of the consensus and the exclusion of the Zeno behavior are presented in Section 3. Section 4 gives the simulation results, and finally the conclusions are drawn in Section 5.
2 Preliminaries and Problem Statement
2.1 Switching Communication Topologies
Among the N + 1 agents, the communication topology is modeled by a directed switching graph
Assumption 1: The connection digraph
Assumption 2: Topology-dependent average dwell time τas satisfies
where
2.2 Intermittent DoS Attack Constraints
DoS attack refers to a class of attacks where an adversary renders certain or all components of an inaccessible control system. The DoS attacks can simultaneously affect both the measurement and control channels, which leads to the loss of data availability. One basic assumption of this article is that during the time DoS is active, only the exchange information among the group agents is interrupted, and thus the interaction information is inaccessible. The time series is shown in Figure 1.
There are two states in a complete time sequence. One is the normal communication period without any malicious actions, and the other is the period interfered by DoS attacks. Here, the two states are defined as follows: when t ∈ ΩI, intermittent communication failure occurs in the switching topologies, and thus the agent cannot obtain neighbor information; and when t ∈ ΩC, all agents can receive neighbor information, in which
2.3 Problem Statement
Consider a group of N + 1 agents consisting of N followers and one leader. The dynamics of the ith follower agents are described by
where
The dynamics of the leader agent are expressed as
where
In this article, for the directed switching topological structure, our objective is to cope with the leader-following consensus problem of multi-agent systems under DoS attacks by designing event-triggered information transmission and control scheme, which leads xi(t) − x0(t) exponentially to converge to 0, and exclude the Zeno behavior.
3 Main Results
In this section, we study the consensus problem of multi-agent systems with directed switching topologies in the presence of DoS attacks and present the design of an event-triggered control scheme.
For each follower i, the state estimate is defined as
with
where
The measurement error ei(t) is defined as
The triggering time instant
where the triggering function is given by
with c is a positive constant to be determined.
Remark 1. The expression (Eq. 7) shows that agents update their communication when topology switches or event-triggering condition is satisfied.
Theorem 1. Consider the leader-following multi-agent systems (2) and (3). Suppose that controller (4) and event-triggered function (8) are applied with K = WP−1 and
1) There exist matrices P > 0 and W such that
and
with
2) Choose μs > b0/a0 such that
Proof. Define the tracking error of each follower i as δi(t) = xi(t) − x0(t). Let δ(t) and e(t) be the column stack vectors of δi(t) and ei(t), respectively. By combining Eq. 2, Eq. 3, and Eq. 4, the dynamics of the error closed-loop system can be expressed as
Consider the multiple topology-dependent Lyapunov function candidate
with
Denote as = λmin (Σs),
For t ∈ ΩC, we assume σ(t) = s; at this time, the network communication is not subjected to attacks. Note that
Let
where
By Eq. 7, one has
which implies
According to the fact
where
Multiplying both sides of
For t ∈ [t0, t1), when the communication network switches among finite digraphs, it follows from Eq. 17 that
For
When t ∈ ΩI, the communication topology of MASs will be affected by DoS attacks, and thus the corresponding communication topology of the MASs will become paralyzed. Then, the time derivative of Eq. 12 along Eq. 11 becomes
It follows from Eq. 20 that
Next, analysis is given for t ∈ [t0, th+1]. Note that
Let
Finally, for any t ≥ 0, there exists a constant ℏ ≥ 0 such that tℏ ≤ t ≤ tℏ+1. Let
where
Remark 2. Note that under directed switching topologies and DoS attacks, the triggering mechanism design and the stability analysis of close-loop systems become even more difficult. Theorem 1 shows that the leader-following consensus problem is solved, for the situation with more practical significance; network intermittent DoS attacks are addressed in the directed switching topologies.
In the following, we show the feasibility of the proposed event-triggered protocol.
Theorem 2 There exists no Zeno behavior in the multi-agent systems (2) and (3).
Proof. Due to the average dwell-time property, they do not have Zeno behavior when the communication topology switches.
Then, considering two consecutive triggers which are induced by the triggering condition, let
Finally, the case that two consecutive triggers are brought by both switching topology and the condition of the triggers is studied. Based on the assumption that the triggering occurs when the topology switches and
Remark 3. Note that the control strategies under DoS attack are also studied in many references, and the continuous controller update is required. In this article, an event-triggered control scheme is provided for MASs in the presence of denial-of-service attacks on directed switching topology.
With the aforementioned notations, this subsection is concluded by summarizing the algorithm for generating the ui(t).
Algorithm 1 Initialization
(1) Set
(2) send
(3) compute
while t < T, T is the desired lifespan of the system.
If t ∈ ΩC,
send xi(t) to its neighbors;
if
(1) update k = k + 1 and
(2) update
end if
else (t ∈ ΩI)
ui(t) = 0;
end if
end while
Remark 4. The obtained results are then extended to achieve consensus for multi-agent systems without a leader. For a leaderless consensus problem, we assume that the undirected switching graph
The event-triggered controller for each follower agent i is proposed as
where
The triggering time instant
where the triggering function is given by
with
The feedback gain matrix is defined as K = WP−1. If there exist matrices p > 0 and W such that the following inequalities hold:
and
where
Let
and following the similar step in the proof-of-leader-following consensus problem, the leaderless consensus of the multi-agent system can be obtained, and the Zeno behavior can be excluded.
4 Simulation Example
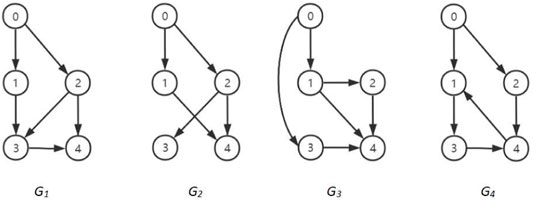
In this section, we present an example to verify the effectiveness of the theoretical results. A network of five agents with a communication graph
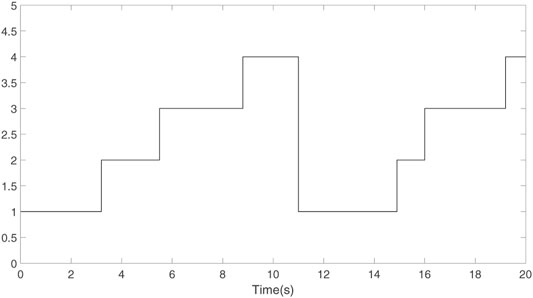
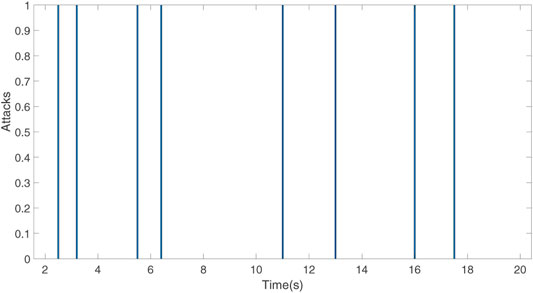
The topology switching signal and the DoS attack signal are determined by Figures 3, 4, respectively.
The parameters are selected as A = [ − 1.175, 0.987 1; −8.458, −0.877 6] and B = [ − 0.194, −0.035 93; −19.29, −3.803 6]. The initial conditions are given as x0 (0) = [0,−0.5]T, x1 (0) = [−3,−6.8]T, x2 (0) = [0,−4.5]T, x3 (0) = [1, 2]T, and x4 (0) = [−1,−2.8]T. The matrix K by solving Eq. 9 and Eq. 10 in Theorem 1 is derived as K = [23.792 3, −0.189 8; −120.689 0, 1.020 4], and the related parameters with controller design are selected as λ1 = 1.45, λ2 = 1.53, λ3 = 1.62, λ4 = 1.58, α = 2.5, and c = 0.15.
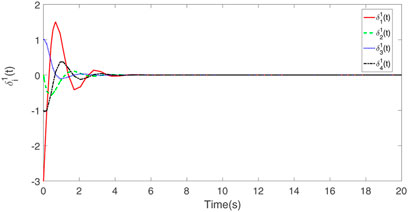
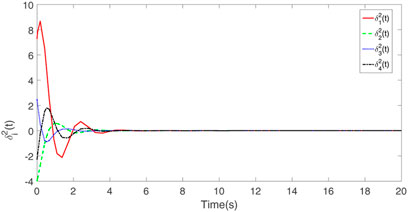
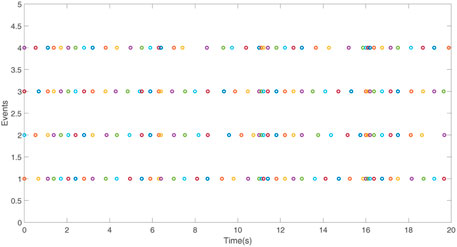
The consensus tracking errors are exhibited in Figures 5, 6, in which the multi-agent systems (2) and (3) are subjected to DoS attacks. The triggering instants of each agent are shown in Figure 7. Based on the aforementioned analysis, the event-triggered controller adopted in this article can effectively reduce the number of communications, and the leader-follower consensus can be achieved under DoS attack.
5 Conclusion
One kind of the typical consensus problem of the linear multi-agent system under DoS attacks has been developed in this article. With the directed switching communication topologies, fully distributed event-triggered strategies are proposed. It is shown that secure leader-following consensus can be achieved, and the Zeno behavior is ruled out in the presence of DoS attacks. The obtained results are then extended to achieve consensus for multi-agent systems without a leader. Future work will try to extend the event-based consensus control results to the nonlinear multi-agent system with a leader of nonzero inputs under DoS attack.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author Contributions
JL contributed to methodology and writing—original draft preparation; LS contributed to conceptualization, methodology, and writing—original draft preparation; XW contributed to supervision and writing—review and editing; and DG contributed to software and validation.
Funding
This work was supported in part by the National Natural Science Foundation of China (No. 61873087), the Natural Science Foundation of Heilongjiang Province (No. YQ2021F014), the University Nursing Program for Young Scholars with Creative Talents in Heilongjiang Province (No. UNPYSCT-2020010), and the Outstanding Youth Fund of Heilongjiang University (No. JCL201903).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Cheng, B., and Li, Z. (2019). Coordinated Tracking Control with Asynchronous Edge-Based Event-Triggered Communications. IEEE Trans. Automat. Contr. 64 (10), 4321–4328. doi:10.1109/tac.2019.2895927
Cheng, T.-H., Kan, Z., Klotz, J. R., Shea, J. M., and Dixon, W. E. (2017). Event-triggered Control of Multiagent Systems for Fixed and Time-Varying Network Topologies. IEEE Trans. Automat. Contr. 62 (10), 5365–5371. doi:10.1109/tac.2017.2693824
Dimarogonas, D. V., Frazzoli, E., and Johansson, K. H. (2012). Distributed Event-Triggered Control for Multi-Agent Systems. IEEE Trans. Automat. Contr. 57 (5), 1291–1297. doi:10.1109/tac.2011.2174666
Fan, Y., Liu, L., Feng, G., and Wang, Y. (2015). Self-triggered Consensus for Multi-Agent Systems with Zeno-free Triggers. IEEE Trans. Automat. Contr. 60 (10), 2779–2784. doi:10.1109/tac.2015.2405294
Feng, Z., and Hu, G. (2020). Secure Cooperative Event-Triggered Control of Linear Multiagent Systems under DoS Attacks. IEEE Trans. Contr. Syst. Technol. 28 (3), 741–752. doi:10.1109/tcst.2019.2892032
Hu, W., Yang, C., Huang, T., and Gui, W. (2020). A Distributed Dynamic Event-Triggered Control Approach to Consensus of Linear Multiagent Systems with Directed Networks. IEEE Trans. Cybern. 50 (2), 869–874. doi:10.1109/tcyb.2018.2868778
Li, H., Shi, Y., and Yan, W. (2016). Distributed Receding Horizon Control of Constrained Nonlinear Vehicle Formations with Guaranteedγ-Gain Stability. Automatica 68, 148–154. doi:10.1016/j.automatica.2016.01.057
Li, X., Soh, Y. C., and Xie, L. (2018). Robust Consensus of Uncertain Linear Multi-Agent Systems via Dynamic Output Feedback. Automatica 98, 114–123. doi:10.1016/j.automatica.2018.09.020
Lu, A.-Y., and Yang, G.-H. (2018). Distributed Consensus Control for Multi-Agent Systems under Denial-Of-Service. Inf. Sci. 439-440, 95–107. doi:10.1016/j.ins.2018.02.008
Ma, H.-J., and Yang, G.-H. (2016). Adaptive Fault Tolerant Control of Cooperative Heterogeneous Systems with Actuator Faults and Unreliable Interconnections. IEEE Trans. Automat. Contr. 61 (11), 3240–3255. doi:10.1109/tac.2015.2507864
Mei, J., Ren, W., and Chen, J. (2016). Distributed Consensus of Second-Order Multi-Agent Systems with Heterogeneous Unknown Inertias and Control Gains under a Directed Graph. IEEE Trans. Automat. Contr. 61 (8), 2019–2034. doi:10.1109/tac.2015.2480336
Meng, X., and Chen, T. (2013). Event Based Agreement Protocols for Multi-Agent Networks. Automatica 49 (7), 2125–2132. doi:10.1016/j.automatica.2013.03.002
Olfati-Saber, R., and Murray, R. M. (2004). Consensus Problems in Networks of Agents with Switching Topology and Time-Delays. IEEE Trans. Automat. Contr. 49, 1520–1533. doi:10.1109/tac.2004.834113
Pelechrinis, K., Iliofotou, M., and Krishnamurthy, S. V. (20212010). Denial of Service Attacks in Wireless Networks: The Case of Jammers. IEEE Commun. Surv. Tutorials 13 (2), 245–257.
Qin, J., Li, M., Shi, L., and Yu, X. (2018). Optimal Denial-Of-Service Attack Scheduling with Energy Constraint over Packet-Dropping Networks. IEEE Trans. Automat. Contr. 63 (6), 1648–1663. doi:10.1109/tac.2017.2756259
Qin, J., Yu, C., and Anderson, B. D. O. (2016). On Leaderless and Leader-Following Consensus for Interacting Clusters of Second-Order Multi-Agent Systems. Automatica 74, 214–221. doi:10.1016/j.automatica.2016.07.008
Ren, W., Beard, R. W., and Atkins, E. M. (2007). Information Consensus in Multive- Hicle Cooperative Control. IEEE Control. Syst. Mag. 27 (2), 71–82.
Seyboth, G. S., Dimarogonas, D. V., and Johansson, K. H. (2013). Event-based Broadcasting for Multi-Agent Average Consensus. Automatica 49 (1), 245–252. doi:10.1016/j.automatica.2012.08.042
Sun, Y.-C., and Yang, G.-H. (2020). Event-triggered Distributed State Estimation for Multiagent Systems under DoS Attacks. IEEE Trans. Cybern., 1–10. to be published. doi:10.1109/TCYB.2020.3034456
Tand, Y., Zhang, D., Shi, P., Zhang, W., and Qian, F. (2021). Event-based Formation Control of Nonlinear Multiagent Systems under DoS Attacks. IEEE Trans. Automatic Control. 66 (1), 452–459.
Wang, X., Park, J. H., Liu, H., and Zhang, X. (2021). Cooperative Output-Feedback Secure Control of Distributed Linear Cyber-Physical Systems Resist Intermittent DoS Attacks. IEEE Trans. Cybern. 51, 4924–4933. doi:10.1109/TCYB.2020.3034374
Wang, X., Wang, G., and Li, S. (2020). Distributed Finite-Time Optimization for Integrator Chain Multiagent Systems with Disturbances. IEEE Trans. Automat. Contr. 65 (12), 5296–5311. doi:10.1109/tac.2020.2979274
Wang, X., and Yang, G.-H. (2018). Adaptive Reliable Coordination Control for Linear Agent Networks with Intermittent Communication Constraints. IEEE Trans. Control. Netw. Syst. 5 (3), 1120–1131. doi:10.1109/tcns.2017.2687818
Wang, X., and Yang, G. H. (2016). Distributed Reliable H∞ Consensus Control for a Class of Multi-Agent Systems under Switching Networks: A Topology-Based Average Dwell Time Approach. Int. J. Robust Nonlinear Control. 26 (12), 2767–2787. doi:10.1002/rnc.3474
Xu, W., Ho, D. W. C., Zhong, J., and Chen, B. (2019). Event/Self-Triggered Control for Leader-Following Consensus over Unreliable Network with DoS Attacks. IEEE Trans. Neural Netw. Learn. Syst. 30 (10), 3137–3149. doi:10.1109/tnnls.2018.2890119
Xu, Y., and Wu, Z.-G. (2021). Distributed Adaptive Event-Triggered Fault-Tolerant Synchronization for Multiagent Systems. IEEE Trans. Ind. Electron. 68 (2), 1537–1547. doi:10.1109/tie.2020.2967739
Yang, D., Ren, W., Liu, X., and Chen, W. (2016). Decentralized Event-Triggered Consensus for Linear Multi-Agent Systems under General Directed Graphs. Automatica 69, 242–249. doi:10.1016/j.automatica.2016.03.003
Zhang, D., Liu, L., and Feng, G. (2019). Consensus of Heterogeneous Linear Multiagent Systems Subject to Aperiodic Sampled-Data and DoS Attack. IEEE Trans. Cybern. 49 (4), 1501–1511. doi:10.1109/tcyb.2018.2806387
Zhang, Z., Yan, W., and Li, H. (2021). Distributed Optimal Control for Linear Multiagent Systems on General Digraphs. IEEE Trans. Automat. Contr. 66 (1), 322–328. doi:10.1109/tac.2020.2974424
Keywords: event-triggered control, multi-agent systems (MASs), denial-of-service (DoS) attacks, switching topologies, zeno behavior
Citation: Lyu J, Sun L, Wang X and Gao D (2022) Event-Based Resilient Control of Multi-Agent Systems in Non-Ideal Communication Networks. Front. Control. Eng. 2:786318. doi: 10.3389/fcteg.2021.786318
Received: 30 September 2021; Accepted: 29 November 2021;
Published: 17 January 2022.
Edited by:
Huiping Li, Northwestern Polytechnical University, ChinaReviewed by:
Andong Liu, Zhejiang University of Technology, ChinaZhuo Zhang, Northwestern Polytechnical University, China
Copyright © 2022 Lyu, Sun, Wang and Gao. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xin Wang, eGlud2FuZ0BobGp1LmVkdS5jbg==
 Jianting Lyu1
Jianting Lyu1 Xin Wang
Xin Wang