- School of Electronic Information Engineering, Henan Institute of Technology, XinXiang, China
In this study, we consider a security efficiency maximization problem in a multiple unmanned aerial vehicle (UAV)-aided system with mobile edge computing (MEC). Two kinds of UAVs, including multiple computing UAVs (CUAVs) and multiple jamming UAVs (JUAVs), are considered in this system. CUAVs would receive partial computation bits and send the computation results to ground users. JUAVs do not undertake computing tasks and only send interference signals to counter potential ground eavesdroppers. We jointly optimize the ground user scheduling, UAV power, and UAV trajectory to maximize the security efficiency. The original problem is non-convex and difficult to solve. We first use the Dinkelbach method combined with continuous convex approximation technology, and then propose three corresponding subproblems, including user scheduling subproblem, UAV power subproblem, and UAV trajectory problem. Further, we apply the branch and bound method to solve the user scheduling subproblem, and optimize the two remaining subproblems by introducing auxiliary variables and Taylor expansion. The simulation results show that the proposed scheme can obtain better secure off-loading efficiency with respect to the existing schemes.
1 Introduction
The application of 5G mobile communication technology has brought many conveniences to people’s life and production activities. The 5G network meets the needs of users for high bandwidth, low latency, and a large number of connected services. MEC is an important application in the 5G era. MEC provides local off-loading, which can effectively alleviate the data transmission pressure of the core network. In addition, mobile edge computing has flexible routing, efficient computing and storage capabilities, and can solve the key challenges of realizing the 5G vision (Pham et al., 2020). In many emerging applications, the demand for MEC is mainly reflected in the three aspects of delay, bandwidth, and security (Zhang et al., 2019). For instance, due to the limited battery capacity and energy consumption of mobile devices, MEC brings storage and computing resources to the edge of the network, enabling programs to run on mobile devices and meet latency requirements (Mach and Becvar, 2017). MEC-enabled loV can meet its heterogeneous needs for communication, computing, and storage, and to minimize the energy consumption of RSU (Ning et al., 2019). MEC cooperates with cloud computing to off-load the computing tasks in the vehicle network to the car, which can effectively reduce computing time and improve system practicability (Zhao et al., 2019). With the emergence of 5G, the industrial Internet is also developing rapidly. Data cleaning based on mobile edge nodes can maintain the reliability and integrity of data while improving the efficiency of data cleaning and reducing the energy consumption of industrial sensor cloud systems (Wang et al., 2020). In order to solve the problem of limited battery lifetime and low computing power of wireless devices, Mozaffari et al. (2019) proposed an MEC system supported by wireless power transfer to enhance computational capability. In the study by Han et al. (2020), the authors proposed a new algorithm to measure the efficiency of mobile edge computing systems. The maximum efficiency of MEC can be jointly optimized by the unloading time, CPU frequency, transmit power of users, and UAV trajectory (Bi and Zhang, 2018). Ding et al. (2019) studied the energy-saving resource allocation of MEC networks using NOMA.
MEC applications are deployed on general-purpose servers and are close to users, so UAVs are used to assist mobile edge computing. UAV-assisted MEC expands the coverage area of edge computing and improves computing capabilities. Due to the high mobility and flexibility of UAVs (Zeng and Zhang, 2017), UAV communication technology is widely used in many fields of electronic design, leading to rapid development of wireless communication technology (Gupta et al., 2016; Wu et al., 2018). Among them, Wu et al. (2018) considered a multi-UAV–enabled wireless communication system to provide services for ground users. UAVs can quickly cover the target area and divert services, which have a wide range of application scenarios (Sebastian and Jochen, 2014; Nader et al., 2018). For example, in smart cities, UAVs can be used for traffic management, environmental monitoring, pollution monitoring, and civil defense control (Hua et al., 2018). The use of drone aerial survey technology can effectively improve the efficiency and accuracy of topographic surveying and mapping work (Roberge et al., 2013). In the military field, UAVs can plan routes. Specifically, UAVs can plan a safe path in an obstacle environment according to their environment and maneuverability (Cao et al., 2018). When mobile edge computing is used to off-load computing tasks to UAVs, the off-loaded information may be destroyed by eavesdroppers. With the increasing demand for global cellular network coverage, UAVs combined with cellular networks can support UAV communications in a low-cost and highly maneuverable manner (Wu et al., 2018). As an aerial base station, UAVs help the ground macro base station to provide high-rate data coverage when there are multiple or large service demands in the target area (Sun et al., 2019). In the cellular-connected UAV mobile edge computing system, parts of the tasks are migrated to the terrestrial base station for calculation, and the other part is calculated on the UAV (Hua et al., 2018). When the cellular system is attacked by jamming, the UAV can select a relay strategy for the mobile users in the cellular system (Lu et al., 2020).
In order to improve traffic efficiency, the UAV-assisted MEC system with three-layer integrated architecture is used to solve the dynamic optimization problem of energy perception (Zhang et al., 2018). UAV-assisted MEC systems need to meet the requirements of low energy consumption and high computing bits (Loke, 2015; Zhou Z. et al., 2018). In the study by Zhou F. et al. (2018), the problem of maximizing computational efficiency is studied by jointly optimizing the computational shunt and the UAV trajectory design in the UAV-assisted MEC network. The problem of maximizing the unloading efficiency of the multi-UAV–assisted MEC system is studied.
The study considers the calculation of bits and energy consumption (Zhang et al., 2020). In order to expand the coverage of edge computing, multiple UAVs can be used to assist MEC systems (Narang et al., 2017). But UAV-assisted MEC systems are at risk of eavesdropping. Zhao et al. (2019) proposed an energy-saving computing off-loading technology focusing on physical layer security. UAVs are used to send jamming signals to combat against eavesdroppers and improve the transmission security rate (Li et al., 2019).
The rest of the article is organized as follows: Section 2 introduces the multiple UAV group–assisted MEC system and formulates the joint optimization problem. In Section 3, the optimal solution is proposed, while Section 4 details numerical simulations. Finally, Section 5 provides concluding remarks.
2 The System Model and Problem Formulation
2.1 The System Model
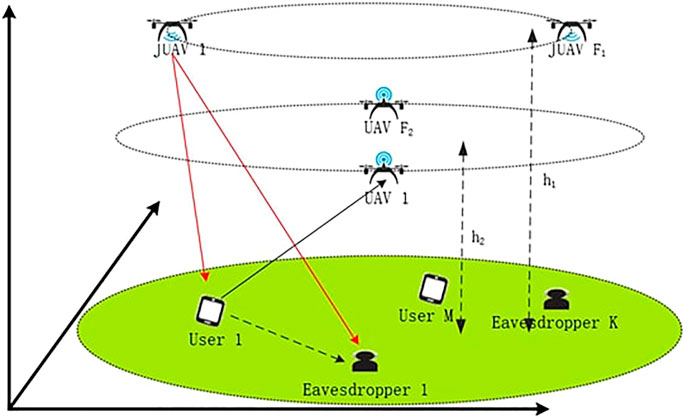
As shown in Figure 1, we consider a multiple UAV group–assisted MEC system, which includes
Taking into account the 3-D Cartesian coordinate system, every legitimate device
The flight path of the slot projected by
Therefore, we can obtain the distance between UAVs
In general, for UAV-SMD wireless communication links, line-of-sight channels are more dominant than other channels. Similar to Hu et al. (2019) and Jeong et al. (2018), we consider that the wireless channel between ground equipment
where
The channel from the legal device to the listener can be modeled as follows:
where φ is the path loss index, ξ is a random variable with exponential distribution, and its unit average represents small-scale Rayleigh fading.
For each legal device, its data can be calculated locally or its data can be off-loaded to the UAV for calculation. A binary variable
2.1.1 Security Rate
Here, a UAV can serve up to one legitimate user:
Under the above conditions, the data transmission rate that the user can reach can be expressed as
where
where
Similarly, the achievable rate of the kth eavesdropper eavesdropping on user m in time slots is given by
where
Therefore, in the case of k eavesdropper in the horizon time T, the worst-case security rate of the user
So the total expression is
in which
2.1.2 System Energy
The total energy consumption of the system consists of five parts: UAV transmission and unloading energy, UAV propulsion energy, ground equipment calculation energy, UAV calculation energy, and JUAV interference energy. According to Zeng and Zhang (2017), the propulsion energy of the UAV is much higher than other orders of magnitude, so only the propulsion energy of the UAV is calculated. The flight energy consumption of UAVs can be expressed as
where g represents the acceleration of gravity,
As a result, the total expression is expressed as
According to Sun et al. (2019), the computational efficiency is considered to be the ratio of the total calculation bit to the total energy consumption, as given below:
2.2 Problem Formulation
This study focuses on maximizing the off-loading efficiency of multi-UAV–assisted edge computing, which jointly optimizes user resource scheduling, UAV flight power, andUAV trajectory. Based on the above analysis, the problem in this study can be expressed as
3 Proposed Solution
In this section, the computational efficiency maximization problem is solved by the iterative optimization algorithm. Since problem P is a nonlinear fractional problem, in order to make the problem easier to deal with, the Dinkelbach method is used to eliminate the fractional structure. Considering the coupling of user association, resource allocation, and trajectory scheduling, we decompose the original problem into three subproblems and propose an iterative optimization algorithm to solve it.
3.1 Dinkelbach-Based Problem Reconstruction and Solution
With the application of the Dinkelbach method P, solving a fractional programming problem transforms the original problem into a parameter programming problem on the basis of the
Assuming that
Lemma 1: the optimal solution
Proof: please refer to Dinkelbach (1967).
Problem p can be transformed into a parameter problem
where η is a nonnegative parameter. We then define the following equation:
which is a strictly monotonic decreasing function for η (Li et al., 2019). If the optimal
To obtain the optimal computational efficiency, a set of increments η is obtained by the Dinkelbach method, and the value of
3.2 Joint Optimization
Although problem
3.2.1 User Association Optimization
We first propose the following definition:
in which
According to the previous results, we formulate the following alternative problem:
Equation 21 is a convex problem, which can be solved by the existing toolbox, such as CVX. We then focus on the resource allocation optimization.
3.2.2 Resource Allocation Optimization
In the case of given UAV user association and a flight trajectory, the power optimization of P1 in the problem can be changed into a new problem SP2 as follows.
It can be noticed that power p contains the UAV power pm and the jamming UAV power
It can be seen from the original formula of SP2 that
where
As a result, we transform the original problem p as follows:
whose gradient can be expressed as follows:
We then carry out the first-order Taylor expansion of
Combining Eqs. 27, 28, we get the following problem:
Similarly, we transform the constraint
Further, we carry out the first-order Taylor expansion of
The convex transformation of UAV power is discussed as above, and the following is the same for interfering with UAV power
We get the definition as
which can be expressed as
It can be seen that the original formula is not simple enough, so it should be further optimized. We assume
We similarly utilize the Dinkelbach method for the formula to optimize the fraction into an integral:
whose gradient can be expressed as
According to the expression of
3.2.3 Trajectory Scheduling of UAVs
Finally, we can optimize the trajectory scheduling of UAVs at a given user association and given power and frequency. The total SMD energy consumption for processing computing tasks is as follows:
where the relaxation variable
which can be transformed into
It is worth noting that optimizing the original formula, we get the following formula:
In this way, the original problem becomes a convex expression as in Eq. 42, which can be solved by CVX.
4 Numerical Results
In this section, we provide a visual representation of our proposed scheme and comparison scheme. Since the space-to-ground channel is a LoS channel, we further assume that the ground signal obeys Rayleigh fading. We use MATLAB to generate artificial data, and in each setting, 1,000 experiments are used to take the average of the results. Specific parameter setting is provided in Table 1.
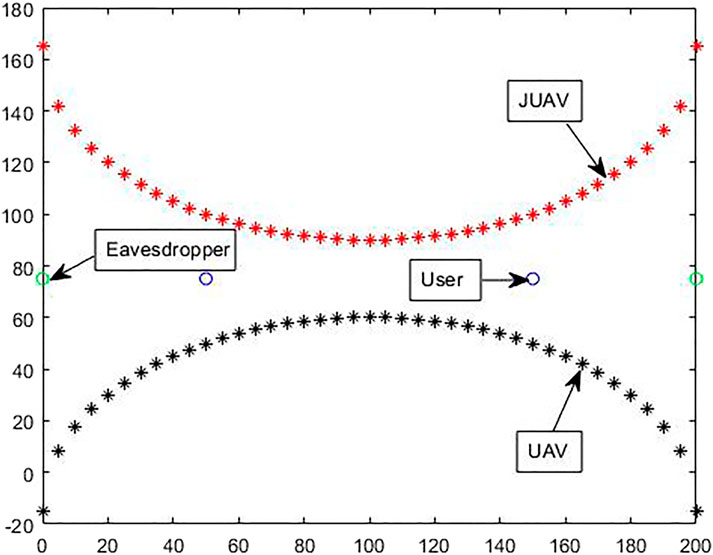
Figure 2 shows the UAVs’ flight trajectory and the location of the ground user. The red discrete points represent the flight trajectory of the interference UAV, and the black discrete points represent the flight trajectory of the UAV. The blue dots represent ground users, and the green dots represent eavesdroppers. It can be seen from the figure that the flying speed of the drone will slow down when it is close to the user, and the flying speed will increase when it is far away from the user.
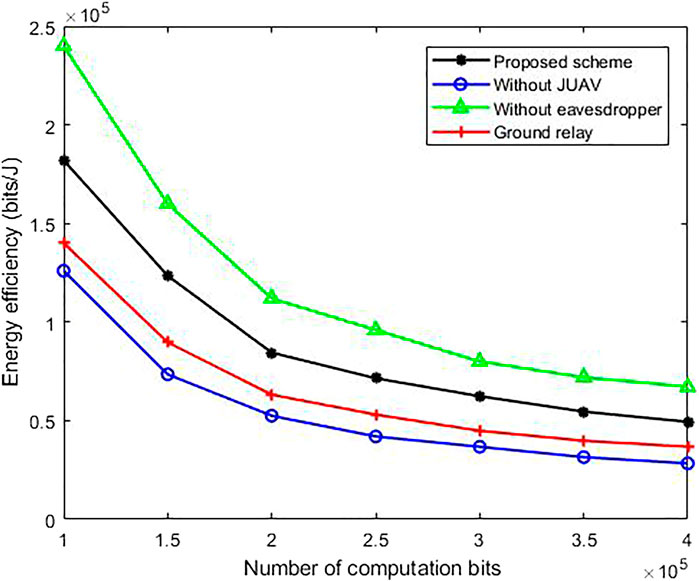
Figure 3 represents how energy efficiency varies with the number of calculated bits. We have provided the results of four schemes for comparison: 1) the scheme proposed in this article, 2) the scheme without JUAV, 3) the case without eavesdroppers, and 4) the scheme with ground jammers. According to Figure 3, as the number of calculation bits increases, the energy efficiency gradually decreases. Furthermore, our proposed scheme has better performance than other benchmark schemes.
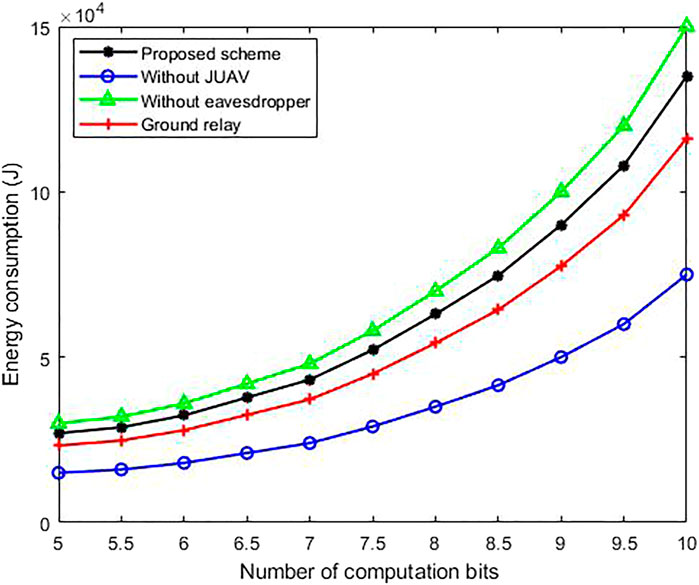
In Figure 4, it shows the variation of energy consumption with the number of bits. Since our proposed scheme is to maximize energy efficiency rather than minimizing energy consumption, we must consider whether the actual energy consumed is reasonable. The results in Figure 4 show that the proposed scheme still has better performance in terms of energy consumption.
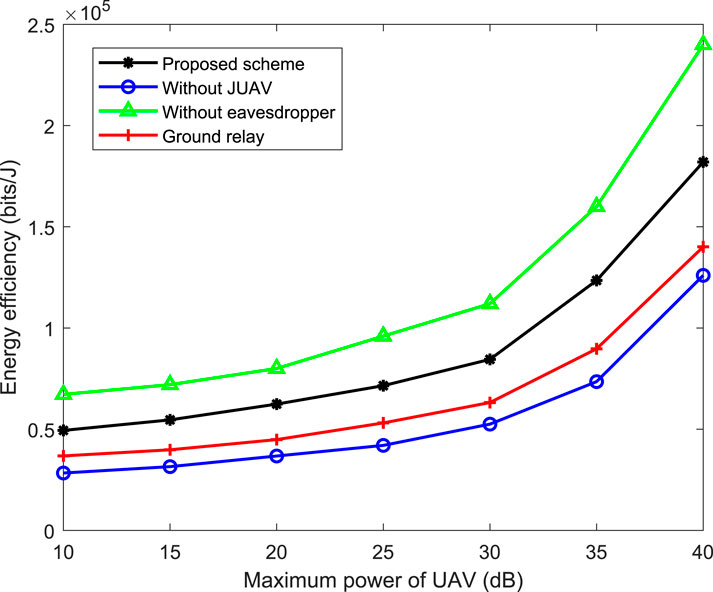
In Figure 5, we show the energy efficiency curve with the maximum power on the drone. It is worth noting that as the maximum power of the UAV increases, the energy efficiency also increases. This is because when the energy is severely limited, the function of interfering with the eavesdropper and the auxiliary communication can seriously damage the safe rate. The greater the power of the UAVs, the less the impact of eavesdroppers.
5 Conclusion and Discussion
In this article, we propose a multi-UAVs–assisted mobile edge computing system in which different multi-UAVs undertake computing tasks and interference tasks, respectively. We propose an alternate optimization algorithm and transform different subproblems into convex problems for easy solution. The simulation results prove the superiority of our proposed scheme.
It is worth noting that we assume that both the air-to-ground channel and the terrestrial channel are perfectly known. However, in practical applications, the channel from the user to the potential eavesdropper is usually imperfect. In this case, how to enhance the robustness of the system is the direction of our follow-up work.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author Contribution
GM finished this paper independently, including the conception of the study, analysis and manuscript preparation, manuscript writing, and the experiment.
Funding
This work was supported in part by the key scientific and technological project of Henan Province, Grant 212102210558.
Conflict of Interest
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
Bi, S., and Zhang, Y. J. (2018). Computation Rate Maximization for Wireless Powered mobile-edge Computing with Binary Computation Offloading. IEEE Trans. Wireless Commun. 17, 4177–4190. doi:10.1109/TWC.2018.2821664
Cao, X., Xu, J., and Zhang, R. (2018). “Mobile Edge Computing for Cellular-Connected Uav: Computation Offloading and Trajectory Optimization,” in 2018 IEEE 19th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), 1–5. doi:10.1109/SPAWC.2018.8445936
Ding, Z., Fan, P., and Poor, H. V. (2019). Impact of Non-orthogonal Multiple Access on the Offloading of mobile Edge Computing. IEEE Trans. Commun. 67, 375–390. doi:10.1109/TCOMM.2018.2870894
Dinkelbach, W. (1967). On Nonlinear Fractional Programming. Management Sci. 13. doi:10.1287/mnsc.13.7.492
Gupta, L., Jain, R., and Vaszkun, G. (2016). Survey of Important Issues in Uav Communication Networks. IEEE Commun. Surv. Tutorials 18, 1123–1152. doi:10.1109/COMST.2015.2495297
Han, Q., Zheng, G., and Xu, C. (2020). “Energy-efficient Resource Allocation for mobile Edge Computing in Noma-Enabled Small Cell Networks,” in 2020 IEEE 20th International Conference on Communication Technology (ICCT), 415–419. doi:10.1109/ICCT50939.2020.9295762
Hu, Q., Cai, Y., Yu, G., Qin, Z., Zhao, M., and Li, G. Y. (2019). Joint Offloading and Trajectory Design for Uav-Enabled mobile Edge Computing Systems. IEEE Internet Things J. 6, 1879–1892. doi:10.1109/JIOT.2018.2878876
Hua, M., Huang, Y., Wang, Y., Wu, Q., Dai, H., and Yang, L. (2018). Energy Optimization for Cellular-Connected Multi-Uav mobile Edge Computing Systems with Multi-Access Schemes. J. Commun. Inf. Networks 3 (4), 33–44. doi:10.1109/iccs.2018.8689226
Jeong, S., Simeone, O., and Kang, J. (2018). Mobile Edge Computing via a Uav-Mounted Cloudlet: Optimization of Bit Allocation and Path Planning. IEEE Trans. Veh. Technol. 67, 2049–2063. doi:10.1109/TVT.2017.2706308
Li, A., Wu, Q., and Zhang, R. (2019). Uav-enabled Cooperative Jamming for Improving Secrecy of Ground Wiretap Channel. IEEE Wireless Commun. Lett. 8, 181–184. doi:10.1109/LWC.2018.2865774
Loke, S. W. (2015). The Internet of Flying-Things: Opportunities and Challenges with Airborne Fog Computing and mobile Cloud in the Clouds. Computer Sci.
Lu, X., Xiao, L., Dai, C., and Dai, H. (2020). Uav-aided Cellular Communications with Deep Reinforcement Learning against Jamming. IEEE Wireless Commun. 27, 48–53. doi:10.1109/MWC.001.1900207
Mach, P., and Becvar, Z. (2017). Mobile Edge Computing: A Survey on Architecture and Computation Offloading. IEEE Commun. Surv. Tutorials 19, 1628–1656. doi:10.1109/COMST.2017.2682318
Mozaffari, M., Saad, W., Bennis, M., Nam, Y.-H., and Debbah, M. (2019). A Tutorial on Uavs for Wireless Networks: Applications, Challenges, and Open Problems. IEEE Commun. Surv. Tutorials 21, 2334–2360. doi:10.1109/COMST.2019.2902862
Nader, M., Jameela, A. J., Imad, J., Ahmed, I., and Farhan, M. (2018). Unmanned Aerial Vehicles Applications in Future Smart Cities. Technol. Forecast. Soc. Change 153, S0040162517314968. doi:10.1016/j.techfore.2018.05.004
Narang, M., Xiang, S., Liu, W., Gutierrez, J., Chiaraviglio, L., Sathiaseelan, A., et al. (2017). “Uav-assisted Edge Infrastructure for Challenged Networks,” in 2017 IEEE Conference on Computer Communications Workshops, Atlanta, GA, United States, (INFOCOM WKSHPS), 60–65. doi:10.1109/INFCOMW.2017.8116353
Ning, Z., Huang, J., Wang, X., Rodrigues, J. J. P. C., and Guo, L. (2019). Mobile Edge Computing-Enabled Internet of Vehicles: Toward Energy-Efficient Scheduling. IEEE Netw. 33, 198–205. doi:10.1109/MNET.2019.1800309
Pham, Q.-V., Fang, F., Ha, V. N., Piran, M. J., Le, M., Le, L. B., et al. (2020). A Survey of Multi-Access Edge Computing in 5g and beyond: Fundamentals, Technology Integration, and State-Of-The-Art. IEEE Access 8, 116974–117017. doi:10.1109/ACCESS.2020.3001277
Roberge, V., Tarbouchi, M., and Labonte, G. (2013). Comparison of Parallel Genetic Algorithm and Particle Swarm Optimization for Real-Time Uav Path Planning. IEEE Trans. Ind. Inf. 9, 132–141. doi:10.1109/TII.2012.2198665
Sebastian, S., and Jochen, T. (2014). Mobile 3d Mapping for Surveying Earthwork Projects Using an Unmanned Aerial Vehicle (Uav) System. SciencDirect Automation in Constructin. 41, 1–14. doi:10.1016/j.autcon.2014.01.004
Sun, H., Zhou, F., and Hu, R. Q. (2019). Joint Offloading and Computation Energy Efficiency Maximization in a mobile Edge Computing System. IEEE Trans. Veh. Technol. 68, 1. doi:10.1109/TVT.2019.2893094
Wang, T., Ke, H., Zheng, X., Wang, K., Sangaiah, A. K., and Liu, A. (2020). Big Data Cleaning Based on mobile Edge Computing in Industrial Sensor-Cloud. IEEE Trans. Ind. Inf. 16, 1321–1329. doi:10.1109/TII.2019.2938861
Wu, Q., Zeng, Y., and Zhang, R. (2018). Joint Trajectory and Communication Design for Multi-Uav Enabled Wireless Networks. IEEE Trans. Wireless Commun. 17, 2109–2121. doi:10.1109/TWC.2017.2789293
Zeng, Y., and Zhang, R. (2017). Energy-efficient Uav Communication with Trajectory Optimization. IEEE Trans. Wireless Commun. 16, 3747–3760. doi:10.1109/TWC.2017.2688328
Zhang, J., Zhou, L., Zhou, F., Seet, B.-C., Zhang, H., Cai, Z., et al. (2020). Computation-efficient Offloading and Trajectory Scheduling for Multi-Uav Assisted mobile Edge Computing. IEEE Trans. Veh. Technol. 69, 2114–2125. doi:10.1109/TVT.2019.2960103
Zhang, L., Zhao, Z., Wu, Q., Zhao, H., Xu, H., and Wu, X. (2018). Energy-aware Dynamic Resource Allocation in Uav Assisted mobile Edge Computing over Social Internet of Vehicles. IEEE Access 6, 56700–56715. doi:10.1109/ACCESS.2018.2872753
Zhang, X., Zhong, Y., Liu, P., Zhou, F., and Wang, Y. (2019). Resource Allocation for a Uav-Enabled mobile-edge Computing System: Computation Efficiency Maximization. IEEE Access 7, 113345–113354. doi:10.1109/ACCESS.2019.2935217
Zhou, F., Wu, Y., Hu, R. Q., and Qian, Y. (2018). Computation Rate Maximization in Uav-Enabled Wireless-Powered mobile-edge Computing Systems. IEEE J. Select. Areas Commun. 36, 1927–1941. doi:10.1109/JSAC.2018.2864426
Zhou, Z., Feng, J., Tan, L., He, Y., and Gong, J. (2018). An Air-Ground Integration Approach for mobile Edge Computing in Iot. IEEE Commun. Mag. 56, 40–47. doi:10.1109/MCOM.2018.1701111
Zhao, J., Li, Q., Gong, Y., and Zhang, K. (2019). Computation Offloading and Resource Allocation for Cloud Assisted mobile Edge Computing in Vehicular Networks. IEEE Trans. Veh. Technol. 68, 7944–7956. doi:10.1109/TVT.2019.2917890
Zhu, Z., Chu, Z., Wang, N., Huang, S., Wang, Z., and Lee, I. (2017). Beamforming and Power Splitting Designs for An-Aided Secure Multi-User Mimo Swipt Systems. IEEE Trans.Inform.Forensic Secur. 12, 2861–2874. doi:10.1109/TIFS.2017.2721908
Keywords: mobile edge computing, multi-UAV, computation efficiency, secure transmission, jamming, trajectory scheduling
Citation: Mu G (2021) Security Efficiency Maximization for Multi-UAV–Aided Network With Mobile Edge Computing. Front. Comput. Sci. 3:691854. doi: 10.3389/fcomp.2021.691854
Received: 07 April 2021; Accepted: 11 May 2021;
Published: 04 June 2021.
Edited by:
Wei Wu, Nanjing University of Posts and Telecommunications, ChinaReviewed by:
Yi Song, Huaiyin Normal University, ChinaPei Li, Nanjing University of Posts and Telecommunications, China
Hongjiang Lei, Chongqing University of Posts and Telecommunications, China
Copyright © 2021 Mu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Guangchen Mu, aG5neHltZ2NAMTI2LmNvbQ==
 Guangchen Mu
Guangchen Mu