- 1The University of Sydney, Sydney, NSW, Australia
- 2South Western Sydney Local Health District, Sydney, NSW, Australia
Background: In response to the widespread transmission of COVID-19 in Australia, healthcare facilities implemented stringent infection control measures, and mandatory and manual screening procedures were introduced to ensure the safety of patients and healthcare staff. However, these necessary measures resulted in imbalances within the healthcare system, a shortage of front-line workers and impacts on patient experience and wait times. The prioritization of infection control measures shifted resources away from routine care, causing delays in accessing necessary healthcare services.
Methods and Findings: To address these challenges, we developed and implemented an Internet of Things (IoT) Smart Screening eGate solution in partnership with a large metropolitan children’s hospital in Australia. This solution integrated a contactless health self-service web app, thermal camera, and physical barrier to automate the COVID-19 health screening and data recording process. During the 3-month pilot period, we deployed the eGate at multiple entrances to the hospital, and monitored the number of users of the system in different periods. We also used a framework of formative evaluation to classify user design challenges within limited resources and improved the design of the eGate to enhance its effectiveness. Our findings show that the IoT eGate solution improved the efficiency of the screening process and reduced the workload and exposure risks of front-line staff and anyone who required access to the hospital. By automating the screening process, we reduced the need for manual screening and minimized contact between individuals, thus reducing the risk of potentially infected.
Conclusion: In conclusion, our pilot study demonstrated the potential of IoT technologies in improving the efficiency and safety of medical facilities during pandemics and provided a series of recommendations for the translation of IoT technologies for medical facilities, including the importance of co-design and collaboration with stakeholders, user-centered design, and ongoing monitoring and evaluation.
Introduction
The COVID-19 pandemic has highlighted the risk of emerging clusters of transmission in what is now an endemic and evolving disease (Chang SL. et al., 2020; Danon et al., 2021) with new variants. Health systems internationally have been severely challenged in their public health response to COVID-19 (Haldane et al., 2021; Sun et al., 2021). Discordance in infection prevention and control measures (Islam et al., 2020; Alhumaid et al., 2021) existed as the world grappled with understanding the possible breadth of COVID-19 symptoms.
Healthcare workers (HCW) are critical to deterring an operational collapse in health systems but were at high risk of contracting COVID-19 pre-vaccines. (Nguyen et al., 2020; Chang D. et al., 2020; Quigley et al., 2021). They are required to self-monitor, report signs of illness, and not engage in patient care whilst infectious (Adams and Walls, 2020). HCW could unknowingly spread the infection within facilities (Wong et al., 2020; Guan et al., 2020; Leeds, 2021) creating a cascading effect to patients and other staff who then must self-isolate. Therefore, pandemic control measures at healthcare facilities were enforced (Quigley et al., 2021; Dell’Isola et al., 2021). Pandemic control measures at hospitals include the utility of health screening for potential COVID-19 cases at entry points to limit and control who can come in. For example, an HCW, such as a nurse may ask about symptoms and perform temperature checks on people entering the building. These manual screening processes are difficult to scale up as they can be labour-intensive, risky and inefficient in a time of scarce resources (Emanuel et al., 2020; Quigley et al., 2021). Therefore a practical, less human resource-intensive, non-contact solution to support a timely response was needed (Nooraie et al., 2021; Leng et al., 2020).
The pandemic has accelerated a plethora of digital health solutions through sheer necessity (Webster, 2020; Budd et al., 2020), allowing a natural experiment in the adoption of technology at scale such as telehealth, enabling continuity of care that is safer for patients and staff (Mroz et al., 2021; Blandford et al., 2020). Despite privacy concerns (Utz et al., 2021; Wymant et al., 2021), many countries and jurisdictions use contact-tracing smartphone apps to keep track of the places an individual has been and their physical contact with other people. The app can then alert an individual if a traced contact tests positive for COVID-19. Contact tracing apps around the world may share similar features but their effectiveness is yet to be definitively proven. In Australia, a national COVID Safe app was released utilising Bluetooth technology to trace who an individual came into close proximity with (Thomas et al., 2020). Although initially touted as a useful solution, public criticism has included the large expense involved in acquiring the technology and its maintenance. Other examples include mandatory state-sponsored contact-tracing apps that require individuals to interact with the app by using a QR code ‘check-in’ process at any location they visit. Data are said to be kept in a central government database and released should it be required for contact tracing. These types of check-in apps that require some level of autonomy have appeared to have fared better for acceptability as measured by levels of usage in Australia. A recent analysis of the app found that ‘COVIDSafe was not sufficiently effective to make a meaningful contribution to the COVID-19 response in Australia’s most populous state over a 6-month period’ (Vogt et al., 2022). Other countries apparently have fared better with citizen usage levels. This includes Singapore (Huang et al., 2020), where citizens can either use the TraceTogether app on their smartphone for Bluetooth proximity tracing or get a wearable TraceTogether Token. The Corona-Warn-App worked in a similar fashion in Germany however, the system was decentralised where it did not remotely store any identifiable information about the user (Arzt et al., 2021).
Emerging research on digital tools that collect self-reported symptoms are starting to assist in reliably identifying risk factors associated with COVID-19 infection within a pandemic context (McDonald et al., 2021; Adorni et al., 2020). Self-reported symptoms have been identified as potentially useful to collect within a digital health screening system. Sudre and colleagues collect their data via an app and (Sudre et al., 2021) have quickly provided a registry of emerging evidence in the frequency of reported symptoms for COVID-19 such as loss of taste and smell (Menni et al., 2020; Izquierdo-Domínguez et al., 2020). Integrating self-reported symptoms with other types of sentinel signals such as outbreak cluster locations can be readily reduced to practice within a digital screening system. An integrated system is then able to warn people in real time if surges of symptoms or spatial transmission be scaled up, augmenting traditional epidemiological efforts such as contact tracing. Self-reporting of symptoms could also assist in increasing self-awareness (Leung et al., 2004; Johnson and Hariharan, 2017) of emerging threats and of the risk of coming into key high-risk areas such as hospitals.
Previous research on digital syndromic surveillance tools that include self-reporting and screening of symptoms has proven their value more than generalised digital syndromic surveillance. For example, when detecting respiratory symptoms and fever (Bourgeois et al., 2007; Nomura et al., 2020). Therefore, current research indicates that self-reported symptoms as part of digital syndromic surveillance systems may provide much utility in screening for clusters of COVID-19 symptoms and in providing an early signal to react. Population survey research has previously revealed that the willingness to comply with public health measures is associated with factors such as age, education, primary language and concern for family (Johnson and Hariharan, 2017; Murphy et al., 2020). Hence, informing where and how risk health communication strategies are delivered in pandemic conditions (Johnson and Hariharan, 2017; Murphy et al., 2020; McCaffery et al., 2020). Introduced digital systems where risk or public health strategies (Budd et al., 2020) are communicated should prioritise these factors. Although these types of considerations seem over and above the existing myriad of hospital and pandemic protocols that compete for the attention of busy HCWs, the aim must be to optimise not compete.
The novelty of this project is underpinned by integrating Internet of Things (IoT) protocols (Hou et al., 2019; Shaham et al., 2020) that allow faster transmission of data capture and augmentation of manual tasks currently associated with health screening at large sites, such as hospitals. Agile methodologies (Goodison et al., 2019; Mkoba and Marnewick, 2020) are not widely used in digital health technology projects. The method provides a unique research opportunity to evaluate processes and conditions for implementation success for healthcare projects that involve IoT for healthcare. We used agile methodology including an agile software development framework called extreme programming (XP) (Beck, 2000).
Methods
We designed a contactless health screening and data tracking system based on the Internet of Things, called eGate, to cope with the staff shortage caused by pandemic control measures in hospitals and to reduce the exposure risk of relevant personnel.
Motivation
In light of the ongoing COVID-19 pandemic, stringent health screening measures have been implemented at hospitals to safeguard the wellbeing of patients, staff, and visitors. Moreover, hospitals may request visitors to complete detailed health questionnaires, providing information regarding their travel history, symptoms, and exposure to COVID-19. It is important to acknowledge that the current staffing challenges faced by hospitals may result in increased processing time for questionnaires, and the wait times at hospital entrances may be prolonged.
To address the evolving circumstances, we undertook a survey targeting visitors at the hospital during this period to gather their feedback regarding the recently implemented screening process. From the survey responses, we extracted valid data from 370 participants, enabling us to gain insights into their perspectives. One aspect that garnered our attention was the additional waiting time experienced by visitors during the admission screening process. We recorded the actual time spent by visitors who completed the questionnaire and compared it with their perception of what would be deemed reasonable. The findings are depicted in Figure 1 below, illustrating the disparity between the actual waiting time and visitors’ perceived expectations.
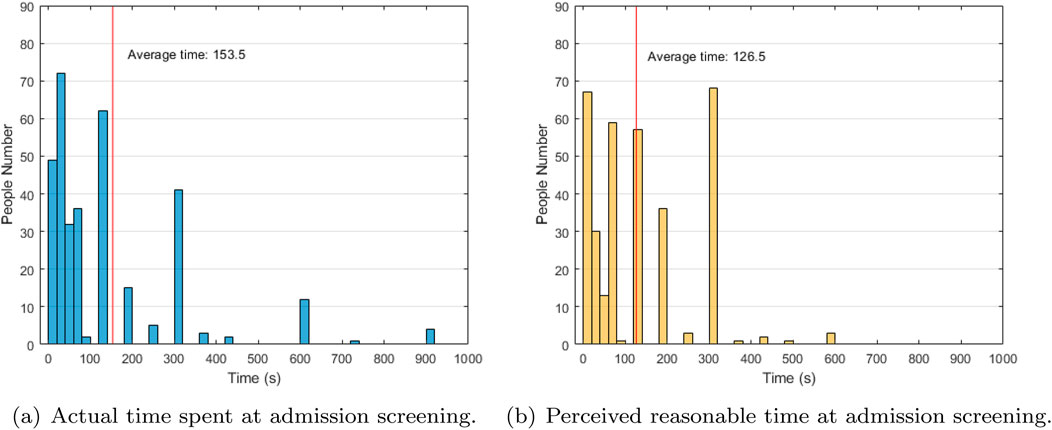
Figure 1. (A) Actual time spent at admission screening. (B) Perceived reasonable time at admission screening. Comparison of actual time spent at admission screening and perceived reasonable time.
Hence, our research on medical digital systems is driven by the objective and motivation to address the shortage of manpower, enhance screening efficiency, and facilitate expedited entry for visitors to receive essential medical services. By leveraging technology and digital solutions, we aim to streamline processes, optimize resource allocation, and ultimately improve the overall visitor experience within the hospital setting.
System framework
The eGate system provides a set of contactless COVID-19 preliminary screening methods, which is an IoT system (Leng et al., 2020; Zhai et al., 2018) as a self-service technology. Before this, the hospital had not deployed any IoT devices and systems, and mainly relied on manual inspections. Generally speaking, before entering the hospital, nurses need to manually use a thermometer to test the body temperature of visitors and ask if they have visited hot spots or have flu symptoms. But this has several problems. First, repeating this process for each visitor is time-consuming and inefficient. Secondly, such duplication of processes is an additional burden on medical staff and increases the risk of exposure. In addition, the results of the temperature measuring gun are extremely dependent on the method of use, which will cause the results of each test to be very unstable.
As shown in Figure 2, our system consists of the equipment layer, the control layer and the user layer.
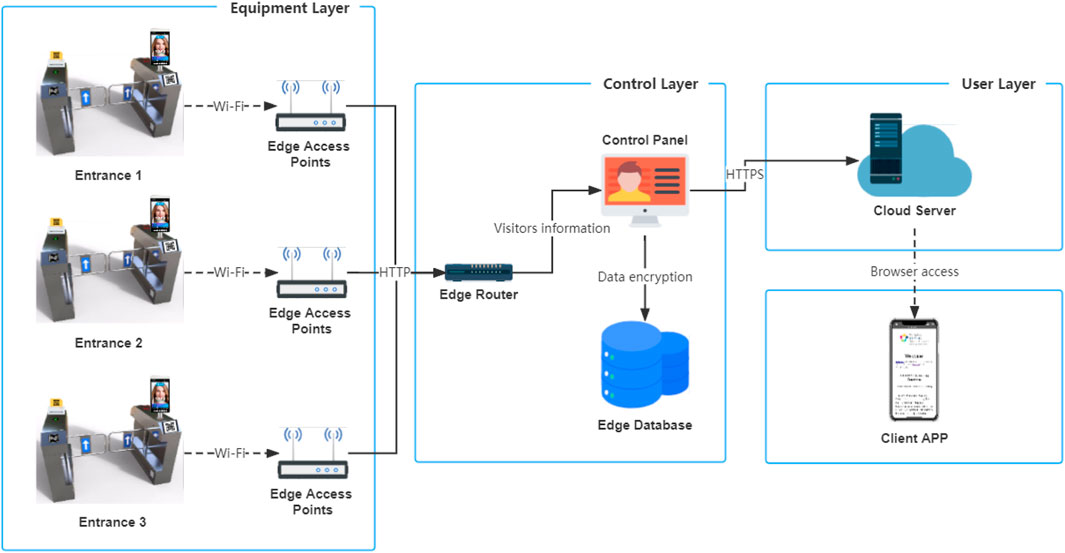
Figure 2. Schematic diagram depicting the layered architecture and connections within the eGate system.
At each entrance, the eGate reports visitors’ screening data to the edge database. Visitors can be either staff who are working at the hospital that day or visitors who have an exemption to visit their sick loved ones.
Access logic
As shown in Figure 3, the visitor is advised to answer all self-assessment questions and check the location of the COVID-19 hot spots updated on the day through the web app before arriving at the hospital, such as on the train on the way to the hospital, so as to obtain the QR code of the day. After arriving at the hospital, the visitor needs to display the QR code at the gate, and then use the thermal scanner on the gate to check the body temperature.
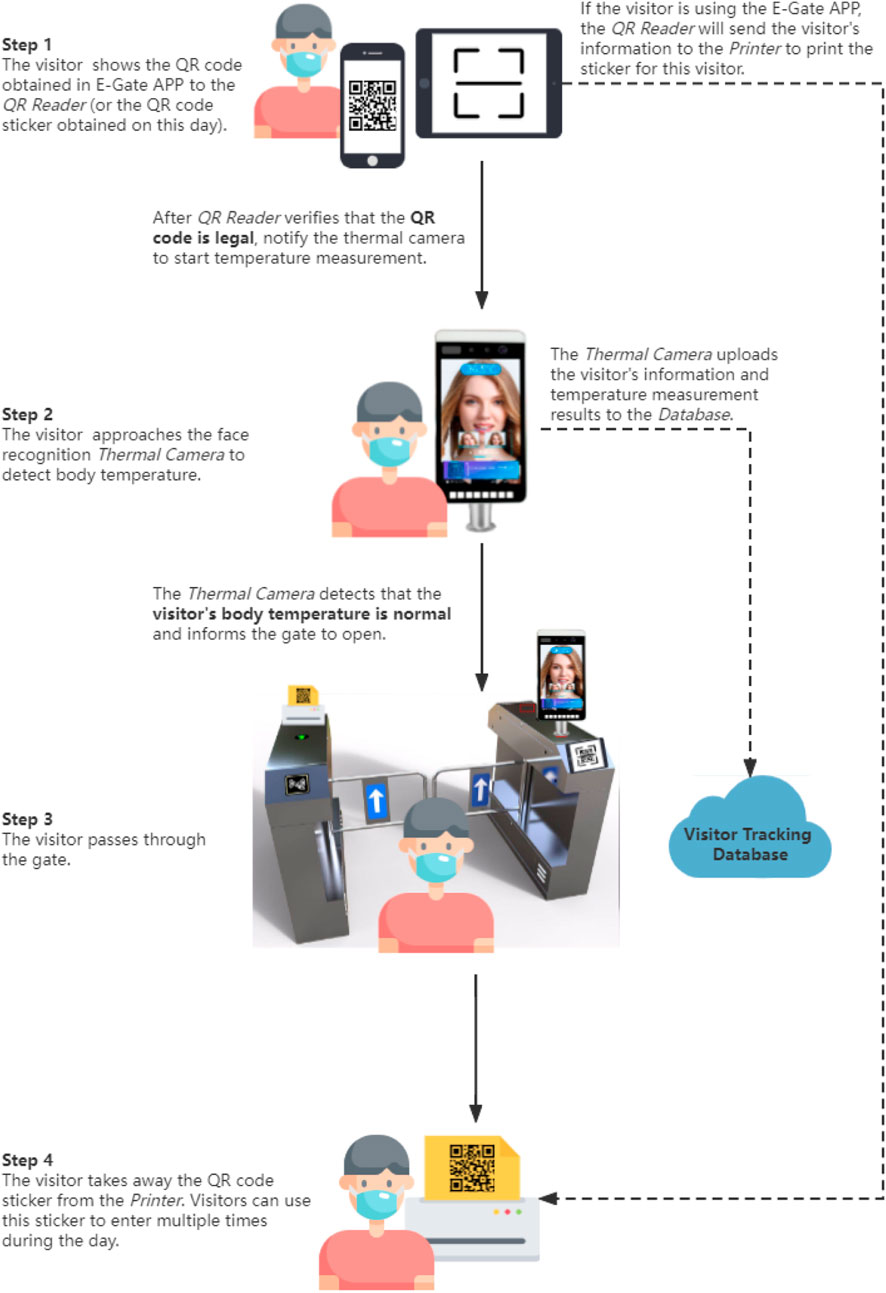
Figure 3. The process outline for visitors passing through the eGate system, including instructions for using each functional module.
Once these steps are completed, the gate will give one of the following results.
During the whole process, the visitor’s information will be transmitted and updated between different modules of the system in the form of QR codes. Although online verification can better ensure the authenticity of credentials, once network fluctuations and server crashes occur, it may cause delays or even paralysis of the hospital entry process. This is even more severe during peak traffic times. So here, we adopt an architecture that separates cloud and local systems.
First, the visitor will get a QR code containing a verification password, user ID and timestamp as an entry credential after completing the Web App questionnaire. The verification password is a pre-agreed password between the local server and the cloud, and the password is updated daily to ensure the timeliness of the QR code. Then, the visitor needs to show and verify the QR code to the QR scanner, and the code scanning module will send a temperature measurement number message to the temperature measurement module to notify the start of the temperature measurement process. The temperature measurement number is the unique number of this temperature measurement. Even if the same visitor measures the temperature multiple times in 1 day, the number will be different each time. After the visitor completes the temperature measurement, the temperature measurement module will add the visitor’s body temperature to the data and notify the gate to open the door. This information will be forwarded to the printer and edge database for storage. Finally, when the printer receives the message, it will print a QR code sticker containing the visitor’s information. The visitor can use this QR code to enter and exit multiple times during the day. When the approve field is pass, the visitor will not activate the printer to print new stickers by scanning the code again.
Results
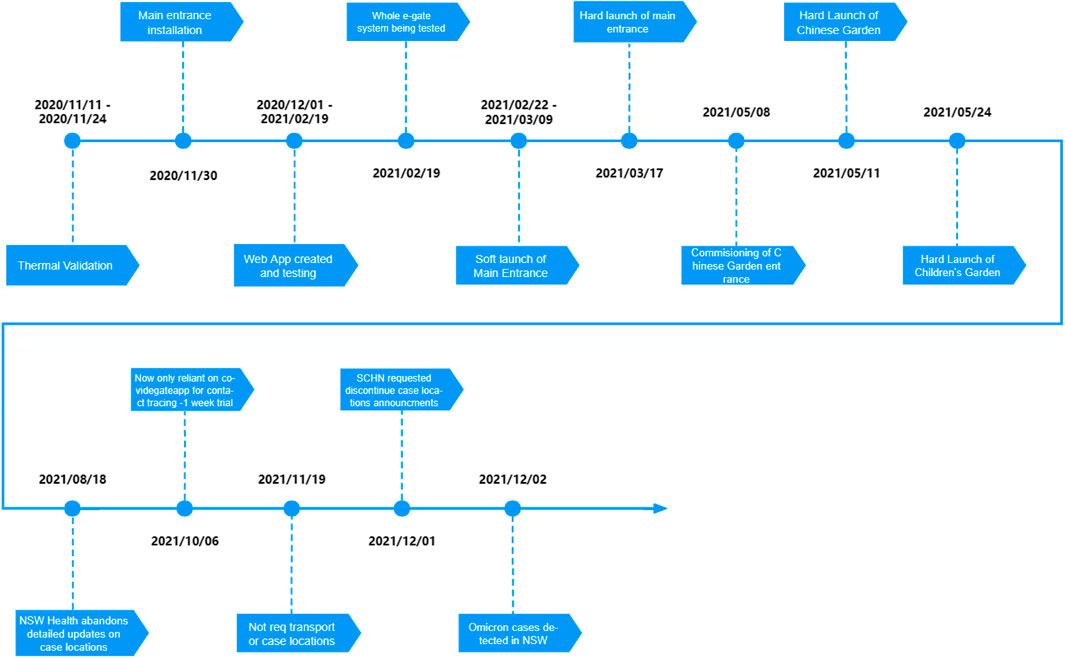
To verify the effectiveness of the IoT-based COVID-19 screening system and the visitor’s response, we have deployed and tested it in the Children’s Hospital for several months. Figure 4 shows the timeline of the pilot preparation phase. The early deployment was primarily a test and adjustment of the site and equipment, with large-scale visitor participation occurring after all three entrances were installed. Therefore, the following statistics are mainly derived from the official testing period after May 2021.
We deployed and piloted the system at the three main public entrances of the hospital, namely, the first at the main entrance (E1), second entrance called the Chinese Garden (E2) and the third entrance (E3) facing the Children’s Park. E1 and E3 have both visitors and staff, while E2 is mainly used by hospital staff due to its proximity to staff car parks and offices. As shown in Figure 5, among them, E1 and E2 use a complete temperature measurement and gate. For comparison, E3, which is not too busy, only uses station stakes for temperature measurement.

Figure 5. (A) Entrance 1: Front Entrance. (B) Entrance 2: Chinese Garden Entrance. (C) Entrance 3: Children’s Garden Entrance. Deployment and installation environment for the eGate system at the pilot site.
Participants
Throughout the pilot, high-frequency use was mainly concentrated on 24th May to 24th July, with 40,480 people using the system. Among this traffic, 97% were hospital employees and 3% were regular visitors. This is mainly because ordinary visitors do not need to visit the hospital every day, so they tend to spend more time using the manual channel than learning to use the eGate system.
As shown in Figure 6, except on weekends, about 800 people use the system to visit the hospital every day during this period. The users of the system are mainly concentrated in the morning, mainly the staff on the morning shift. The deployment of the system greatly alleviates the traffic pressure at each entrance during the morning shift.
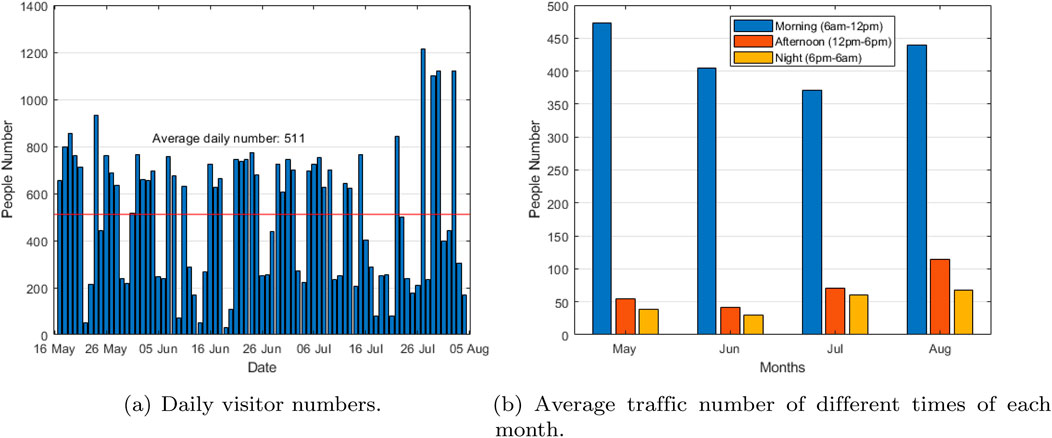
Figure 6. (A) Daily visitor numbers. (B) Average traffic number of different times of each month. Visitor traffic analysis during the pilot period.
Among them, for 4,674 registered employees, we sorted their positions and departments according to the information they filled out. As shown in Figure 7, most of the people who use the eGate system are nurses, mainly from SCHN Med and SCHN Critical Care. In addition, among these people, 971 were male, 3,702 were female. The people who most use the eGate systems are mainly between the ages of 30 and 33, the oldest is 87 years old and the youngest is 18 years old.
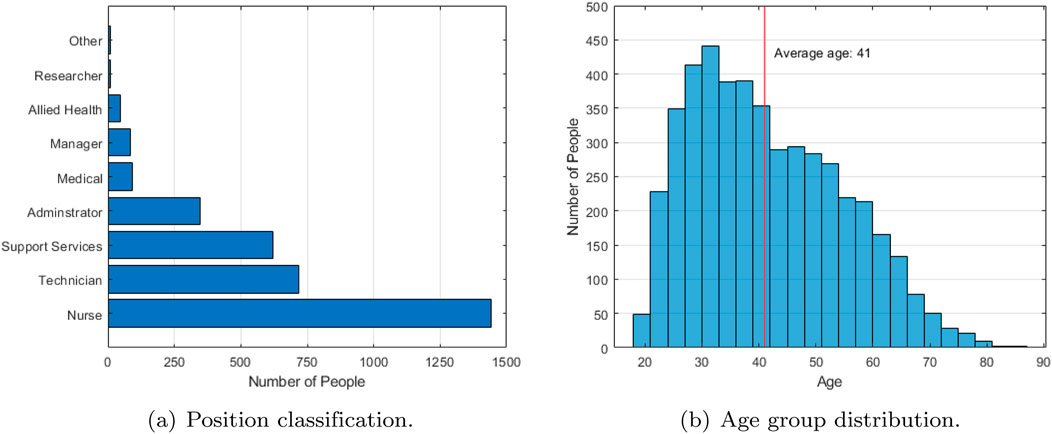
Figure 7. (A) Position classification. (B) Age group distribution. Profile analysis of participants in the pilot program.
Passing efficiency
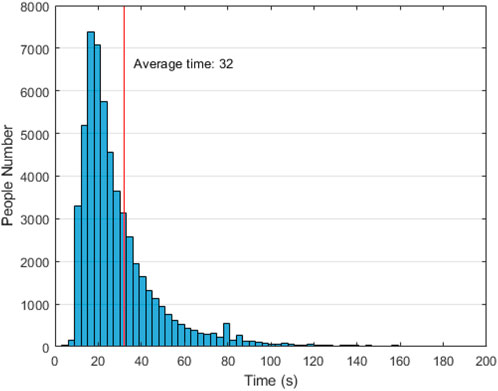
In the actual deployment, as shown in Figure 8, almost all users can use the system to complete the whole process in 1 minute, and most users can complete it in 30 s. It is worth noting that most of these users are first exposed to this system. Experienced users tend to spend less time than when they first use it.
During the pilot period, the vast majority of visitors were allowed to enter the hospital through the system, but there were also 6% users who were refused (only 308 cases), mainly because their QR codes had expired. There were also a few cases in the pilot who were rejected because of hyperthermia. They had some things in common, such as having just finished exercising and being exposed to the sun for a long time. Fortunately, there were no cases of COVID-19 at Children’s Hospital throughout the pilot period.
Discussion
From the perspectives of data and systems, the deployment of IoT-based data medical systems should meet the following requirements.
User-friendly system design
A user-friendly system should enable users to easily comprehend its function, operation method, and data output. It should not require professional expertise to operate, making it useable for doctors, nurses, and patients in hospital IoT systems. To achieve this, designers must maintain a balance between users and technology, and view issues from the user’s perspective. Before designing a system, designers must thoroughly understand the requirements and expectations of healthcare professionals and patients. This can be accomplished through surveys, interviews, questionnaires, and other methods to help identify the focus of system functions and performance from the user’s viewpoint.
Prior to utilizing an IoT system, healthcare workers and patients require training and support to comprehend its fundamental operation and functionality. For users, using an IoT system necessitates additional learning costs that designers must take into consideration. If the learning cost is deemed excessive, users may become disenchanted with the IoT system. Therefore, when designing a system, it is critical to make the entire system easy to understand and concentrate on the needs that users are most concerned about, rather than adding a plethora of superfluous functional modules. This entails providing enough information and engagement to staff and patients, as well as clear explanations and instructions on how the system operates and how data is processed. Furthermore, a user-friendly system must instill confidence in users that the data output by the system is accurate and reliable and that the system’s operation is secure and dependable. As a result, during system implementation, it is vital to pay attention to medical staff and patient feedback and keep the system transparent. This trust can help users better comprehend and utilize the system and accept its output.
In summary, deploying IoT systems in hospitals necessitates striking a balance between people and technology. This can be accomplished by comprehending user needs, engaging users and technical experts, providing training and support, ensuring privacy and security, and being transparent.
Data security and privacy
While it may be ideal to record a user’s complete indoor trajectory and timeline for maximum contact tracing in a hospital setting, this raises privacy concerns. Visitor’s personal conditions may be inferred from the departments they visit, which is sensitive information that must be protected. To prevent the disclosure of irrelevant information, we will limit data collection to only essential information, and discard any unnecessary data.
The eGate system adopts a distributed design. Each device can be regarded as an intelligent node contained in an independent internal network, and the communication between intelligent nodes is regarded as data transmission in the public network, which has the risk of eavesdropping and data leakage. During the data transmission process, users’ personal information is encrypted using the RSA algorithm, which is an asymmetric encryption algorithm based on the principle of number theory using public key encryption, private key decryption, or private key signature and public key verification to achieve data confidentiality and authentication. In the database, we use a differential privacy algorithm (Liu et al., 2021; Shaham et al., 2021a; Shaham et al., 2021b; Smith et al., 2020) to process the stored data to ensure that the relevant information cannot correspond to a specific participant when the data analysing. In terms of database management, we set strict access control rules, and only authenticated administrator rights accounts are allowed to access critical raw data.
In addition, the eGate system supports data processing locally on the end side in addition to the data collection function, allowing the deployment of distributed AI learning frameworks such as federated learning to further protect the privacy of raw data.
Network stability and scalability
For the system to function properly, all of its modules must interact within the same Local Area Network (LAN) broadcast domain. During the pilot phase, the wireless network’s instability caused significant issues for the system. Network congestion often led to gates failing to receive timely release notifications from the control layer, resulting in user complaints. The problem was particularly severe during peak traffic hours in the morning and evening when the system’s response delays became even more intolerable. To address these issues, we have implemented measures to optimize network stability and minimize congestion.
The eGate system currently provides a comprehensive initial health check solution, ranging from the cloud to the sensor level. However, to ensure long-term system development, we plan to incorporate additional functions into the system platform. Thanks to the system’s modular design, we have reserved a data interface in the control layer for future functional modules. While adding more functions to the system is desirable, it can also make the system more complex and time-consuming, leading to longer response times and poor user experiences during network delays. Moreover, complex dependencies between modules can reduce the system’s overall robustness, making it harder to identify and fix problems during unexpected situations, which increases the risk as the system scales. To simplify the system as much as possible, we have minimized dependencies between modules and designed the system with the principle of simplification in mind. This approach reduces the difficulty of system maintenance, and any plans to expand the system should be done with caution.
In practical use, the eGate system faces various unexpected challenges, such as emergencies, user errors, network problems, and power failures. Therefore, the system should leave enough design redundancy and alternatives to deal with various unknown unexpected situations, in addition to providing sufficient guidance to diverse users.
Conclusion
In order to improve the efficiency of this process and reduce the exposure risk of related personnel, we cooperated with Children’s Hospital to deploy the Internet of Things (IoT) system at multiple entrances. In this article, we designed eGate, a contact-less visitor health check and data tracking system based on IoT. By automating the health check and data recording process, we can effectively improve the efficiency of the check and reduce the workload and exposure risks of front-line medical staff. During the 3 months of the pilot, we counted the number of users of the system in different time periods, solved some problems reported by users and improved the system. Finally, we summarized the experience gained in the pilot and provided a series of suggestions for future practical IoT system deployment and user-friendly design.
Author summary
Why was this study done?
What did the researchers do and find?
What do these findings mean?
Data availability statement
The data that support the findings of this study are available on request from the corresponding author. The data are not publicly available due to restrictions e.g. containing information that could compromise the privacy of research participants. The study’s pre-registration can be found at https://osf.io/6hy2t.
Ethics statement
The studies involving humans were approved by The Human Research Ethics Committee from Sydney Children’s Hospital Network. Approval no: 2020/ETH02168 on 27 October 2020. The studies were conducted in accordance with the local legislation and institutional requirements. The participants provided their written informed consent to participate in this study.
Author contributions
JL: Writing–review and editing, Writing–original draft, Visualization, Validation, Software, Methodology, Investigation, Formal Analysis, Data curation, Conceptualization. ZL: Writing–review and editing, Visualization, Validation, Supervision, Software, Project administration, Methodology, Investigation, Formal Analysis, Conceptualization. SY: Writing–review and editing, Validation, Data curation. GS: Writing–review and editing, Validation. MD: Writing–review and editing, Visualization, Validation, Resources. BV: Writing–review and editing, Supervision. AW: Writing–review and editing, Visualization, Validation, Supervision, Resources, Project administration, Methodology, Investigation, Funding acquisition, Formal Analysis, Conceptualization.
Funding
The author(s) declare that financial support was received for the research, authorship, and/or publication of this article. This study received an institutional COVID-19 grant from Sydney Children’s Hospital Network.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Adams, J. G., and Walls, R. M. (2020). Supporting the health care workforce during the COVID-19 global epidemic. Jama 323 (15), 1439–1440. doi:10.1001/jama.2020.3972
Adorni, F., Prinelli, F., Bianchi, F., Giacomelli, A., Pagani, G., Bernacchia, D., et al. (2020). Self-reported symptoms of SARS-CoV-2 infection in a nonhospitalized population in Italy: cross-sectional study of the EPICOVID19 web-based survey. JMIR public health surveillance 6 (3), e21866. doi:10.2196/21866
Alhumaid, S., Al Mutair, A., Al Alawi, Z., Alsuliman, M., Ahmed, G. Y., Rabaan, A. A., et al. (2021). Knowledge of infection prevention and control among healthcare workers and factors influencing compliance: a systematic review. Antimicrob. Resist. and Infect. Control 10 (1), 1–32. doi:10.1186/s13756-021-00957-0
Arzt, S., Poller, A., and Vallejo, G. (2021). “Tracing contacts with mobile phones to curb the pandemic: topics and stances in people’s online comments about the official German contact-tracing app,” in Extended abstracts of the 2021 CHI conference on human factors in computing systems, 1–7.
Beck, K. (2000). Extreme programming explained: embrace change. Massachusetts, United States: Addison-Wesley.
Blandford, A., Wesson, J., Amalberti, R., AlHazme, R., and Allwihan, R. (2020). Opportunities and challenges for telehealth within, and beyond, a pandemic. Lancet Glob. Health 8 (11), e1364–e1365. doi:10.1016/s2214-109x(20)30362-4
Bourgeois, F. T., Porter, S. C., Valim, C., Jackson, T., Cook, E. F., and Mandl, K. D. (2007). The value of patient self-report for disease surveillance. J. Am. Med. Inf. Assoc. 14 (6), 765–771. doi:10.1197/jamia.m2134
Budd, J., Miller, B. S., Manning, E. M., Lampos, V., Zhuang, M., Edelstein, M., et al. (2020). Digital technologies in the public-health response to COVID-19. Nat. Med. 26 (8), 1183–1192. doi:10.1038/s41591-020-1011-4
Chang, D., Xu, H., Rebaza, A., Sharma, L., and Cruz, C. S. D. (2020b). Protecting health-care workers from subclinical coronavirus infection. Lancet Respir. Med. 8 (3), e13. doi:10.1016/s2213-2600(20)30066-7
Chang, S. L., Harding, N., Zachreson, C., Cliff, O. M., and Prokopenko, M. (2020a). Modelling transmission and control of the COVID-19 pandemic in Australia. Nat. Commun. 11 (1), 5710–5713. doi:10.1038/s41467-020-19393-6
Danon, L., Brooks-Pollock, E., Bailey, M., and Keeling, M. (2021). A spatial model of COVID-19 transmission in England and Wales: early spread, peak timing and the impact of seasonality. Philosophical Trans. R. Soc. B 376 (1829), 20200272. doi:10.1098/rstb.2020.0272
Dell’Isola, G. B., Cosentini, E., Canale, L., Ficco, G., and Dell’Isola, M. (2021). Noncontact body temperature measurement: uncertainty evaluation and screening decision rule to prevent the spread of COVID-19. Sensors 21 (2), 346. doi:10.3390/s21020346
Emanuel, E. J., Persad, G., Upshur, R., Thome, B., Parker, M., Glickman, A., et al. (2020). Fair allocation of scarce medical resources in the time of Covid-19. N. Engl. J. Med. Overseas. Ed. 382, 2049–2055. doi:10.1056/nejmsb2005114
Goodison, R., Borycki, E. M., and Kushniruk, A. W. (2019). Use of agile project methodology in health care it implementations: a scoping review. ITCH 257, 140–145.
Guan, Wj, Ni, Zy, Hu, Y., Liang, Wh, Ou, Cq, He, Jx, et al. (2020). Clinical characteristics of coronavirus disease 2019 in China. N. Engl. J. Med. 382 (18), 1708–1720. doi:10.1056/nejmoa2002032
Haldane, V., De Foo, C., Abdalla, S. M., Jung, A. S., Tan, M., Wu, S., et al. (2021). Health systems resilience in managing the COVID-19 pandemic: lessons from 28 countries. Nat. Med. 27, 964–980. doi:10.1038/s41591-021-01381-y
Hou, Z., She, C., Li, Y., and Vucetic, B. (2019). “Ultra-reliable and low-latency communications: prediction and communication co-design,” in ICC 2019-2019 IEEE international conference on communications (ICC) (IEEE), 1–7.
Huang, Z., Guo, H., Lee, Y. M., Ho, E. C., Ang, H., and Chow, A. (2020). Performance of digital contact tracing tools for COVID-19 response in Singapore: cross-sectional study. JMIR mHealth uHealth 8 (10), e23148. doi:10.2196/23148
Islam, M. S., Rahman, K. M., Sun, Y., Qureshi, M. O., Abdi, I., Chughtai, A. A., et al. (2020). Current knowledge of COVID-19 and infection prevention and control strategies in healthcare settings: a global analysis. Infect. Control and Hosp. Epidemiol. 41 (10), 1196–1206. doi:10.1017/ice.2020.237
Izquierdo-Domínguez, A., Rojas-Lechuga, M., Chiesa-Estomba, C., Calvo-Henríquez, C., Ninchritz-Becerra, E., Soriano-Reixach, M., et al. (2020). Smell and taste dysfunction in covid-19 is associated with younger age in ambulatory settings: a multicenter cross-sectional study. J. Investig. Allergol. Clin. Immunol. 30, 346–357. doi:10.18176/jiaci.0595
Johnson, E. J., and Hariharan, S. (2017). Public health awareness: knowledge, attitude and behaviour of the general public on health risks during the H1N1 influenza pandemic. J. Public Health 25 (3), 333–337. doi:10.1007/s10389-017-0790-7
Leeds, C. (2021). COVID 19: health care workers, risks, protection and transmission. Lancet Regional Health-Europe 1, 100022. doi:10.1016/j.lanepe.2020.100022
Leng, J., Lin, Z., and Wang, P. (2020). “Poster abstract: an implementation of an Internet of things system for Smart hospitals,” in 2020 IEEE/ACM fifth international conference on internet-of-things design and implementation (IoTDI), 254–255.
Leung, G. M., Quah, S., Ho, L. M., Ho, S. Y., Hedley, A. J., Lee, H. P., et al. (2004). A tale of two cities: community psychobehavioral surveillance and related impact on outbreak control in Hong Kong and Singapore during the severe acute respiratory syndrome epidemic. Infect. Control and Hosp. Epidemiol. 25 (12), 1033–1041. doi:10.1086/502340
Liu, B., Ding, M., Shaham, S., Rahayu, W., Farokhi, F., and Lin, Z. (2021). When machine learning meets privacy: a survey and outlook. ACM Comput. Surv. 54 (2), 1–36. doi:10.1145/3436755
McCaffery, K., Dodd, R. H., Cvejic, E., Ayre, J., Batcup, C., Isautier, J. M., et al. (2020). Disparities in COVID-19 related knowledge, attitudes, beliefs and behaviours by health literacy. medRxiv[Preprint]. 30(4):30342012. doi:10.17061/phrp30342012
McDonald, S. A., Van Den Wijngaard, C. C., Wielders, C. C., Friesema, I. H., Soetens, L., Paolotti, D., et al. (2021). Risk factors associated with the incidence of self-reported COVID-19-like illness: data from a web-based syndromic surveillance system in The Netherlands. Epidemiol. and Infect. 149, e129. doi:10.1017/s0950268821001187
Menni, C., Valdes, A. M., Freidin, M. B., Sudre, C. H., Nguyen, L. H., Drew, D. A., et al. (2020). Real-time tracking of self-reported symptoms to predict potential COVID-19. Nat. Med. 26 (7), 1037–1040. doi:10.1038/s41591-020-0916-2
Mkoba, E., and Marnewick, C. (2020). Conceptual framework for auditing agile projects. IEEE Access 8, 126460–126476. doi:10.1109/access.2020.3007874
Mroz, G., Papoutsi, C., and Greenhalgh, T. (2021). From disaster, miracles are wrought’: a narrative analysis of UK media depictions of remote GP consulting in the COVID-19 pandemic using Burke’s pentad. Med. Humanit. 47, 292–301. doi:10.1136/medhum-2020-012111
Murphy, K., Williamson, H., Sargeant, E., and McCarthy, M. (2020). Why people comply with COVID-19 social distancing restrictions: self-interest or duty? Aust. and N. Z. J. Criminol. 53 (4), 477–496. doi:10.1177/0004865820954484
Nguyen, L. H., Drew, D. A., Joshi, A. D., Guo, C. G., Ma, W., Mehta, R. S., et al. (2020). Risk of COVID-19 among frontline healthcare workers and the general community: a prospective cohort study. MedRxiv[Preprint], 20084111. doi:10.1101/2020.04.29.20084111
Nomura, S., Yoneoka, D., Shi, S., Tanoue, Y., Kawashima, T., Eguchi, A., et al. (2020). An assessment of self-reported COVID-19 related symptoms of 227,898 users of a social networking service in Japan: has the regional risk changed after the declaration of the state of emergency? Lancet Regional Health-Western Pac. 1, 100011. doi:10.1016/j.lanwpc.2020.100011
Nooraie, R. Y., Shelton, R. C., Fiscella, K., Kwan, B. M., and McMahon, J. M. (2021). The pragmatic, rapid, and iterative dissemination and implementation (PRIDI) cycle: adapting to the dynamic nature of public health emergencies. Res. Sq. doi:10.21203/rs.3.rs-188929/v1
Quigley, A. L., Stone, H., Nguyen, P. Y., Chughtai, A. A., and MacIntyre, C. R. (2021). Estimating the burden of COVID-19 on the Australian healthcare workers and health system during the first six months of the pandemic. Int. J. Nurs. Stud. 114, 103811. doi:10.1016/j.ijnurstu.2020.103811
Shaham, S., Ding, M., Liu, B., Dang, S., Lin, Z., and Li, J. (2020). Privacy preserving location data publishing: a machine learning approach. IEEE Trans. Knowl. Data Eng. 33, 3270–3283. doi:10.1109/tkde.2020.2964658
Shaham, S., Ding, M., Liu, B., Dang, S., Lin, Z., and Li, J. (2021a). Privacy preservation in location-based services: a novel metric and attack model. IEEE Trans. Mob. Comput. 20 (10), 3006–3019. doi:10.1109/tmc.2020.2993599
Shaham, S., Ding, M., Liu, B., Dang, S., Lin, Z., and Li, J. (2021b). Privacy preserving location data publishing: a machine learning approach. IEEE Trans. Knowl. Data Eng. 33 (9), 3270–3283. doi:10.1109/tkde.2020.2964658
Smith, D., Wang, P., Ding, M., Chan, J., Spak, B., Guan, X., et al. (2020). Privacy-preserved optimal energy trading, statistics, and forecasting for a neighborhood area network. Computer. 53 (5), 25–34. doi:10.1109/mc.2020.2972505
Sudre, C. H., Keshet, A., Graham, M. S., Joshi, A. D., Shilo, S., Rossman, H., et al. (2021). Anosmia, ageusia, and other COVID-19-like symptoms in association with a positive SARS-CoV-2 test, across six national digital surveillance platforms: an observational study. Lancet Digital Health 3, e577–e586. doi:10.1016/s2589-7500(21)00115-1
Sun, S., Xie, Z., Yu, K., Jiang, B., Zheng, S., and Pan, X. (2021). COVID-19 and healthcare system in China: challenges and progression for a sustainable future. Glob. Health 17 (1), 14–18. doi:10.1186/s12992-021-00665-9
Thomas, R., Michaleff, Z. A., Greenwood, H., Abukmail, E., and Glasziou, P. (2020). Concerns and misconceptions about the Australian Government’s COVIDSafe app: cross-sectional survey study. JMIR public health surveillance 6 (4), e23081. doi:10.2196/23081
Utz, C., Becker, S., Schnitzler, T., Farke, F. M., Herbert, F., Schaewitz, L., et al. (2021). “Apps against the spread: privacy implications and user acceptance of COVID-19-related smartphone apps on three continents,” in Proceedings of the 2021 CHI conference on human factors in computing systems, 1–22.
Vogt, F., Haire, B., Selvey, L., Katelaris, A. L., and Kaldor, J. (2022). Effectiveness evaluation of digital contact tracing for COVID-19 in New South Wales, Australia. Lancet Public Health 7 (3), e250–e258. doi:10.1016/s2468-2667(22)00010-x
Webster, P. (2020). Virtual health care in the era of COVID-19. Lancet 395 (10231), 1180–1181. doi:10.1016/s0140-6736(20)30818-7
Wong, J., Goh, Q. Y., Tan, Z., Lie, S. A., Tay, Y. C., Ng, S. Y., et al. (2020). Preparing for a COVID-19 pandemic: a review of operating room outbreak response measures in a large tertiary hospital in Singapore. Can. J. Anesthesia/Journal Can. d’anesthésie. 67 (6), 732–745. doi:10.1007/s12630-020-01620-9
Wymant, C., Ferretti, L., Tsallis, D., Charalambides, M., Abeler-Dörner, L., Bonsall, D., et al. (2021). The epidemiological impact of the NHS COVID-19 App. Nature 594 (7863), 408–412. doi:10.1038/s41586-021-03606-z
Keywords: healthcare (MeSH), internet of things (IoT), COVID-19, digital health (eHealth), system implementation
Citation: Leng J, Lin Z, Yoo S, Scandurra G, Dickinson M, Vucetic B and Wang AP (2024) Healthcare Internet of Things system implementations for COVID-19 prevention. Front. Comms. Net 5:1429460. doi: 10.3389/frcmn.2024.1429460
Received: 08 May 2024; Accepted: 15 October 2024;
Published: 23 October 2024.
Edited by:
Pushpendu Kar, The University of Nottingham Ningbo, ChinaReviewed by:
Chandana Unnithan, Torrens University Australia, AustraliaRajib Biswas, Tezpur University, India
Copyright © 2024 Leng, Lin, Yoo, Scandurra, Dickinson, Vucetic and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zihuai Lin, emlodWFpLmxpbkBzeWRuZXkuZWR1LmF1
 Jichao Leng
Jichao Leng Zihuai Lin
Zihuai Lin Soojeong Yoo
Soojeong Yoo Gabriella Scandurra1
Gabriella Scandurra1 Michael Dickinson
Michael Dickinson Audrey P. Wang
Audrey P. Wang