- 1School of Economics and Management, Beijing Jiaotong University, Beijing, China
- 2Marketing Department, Beijing Rongqing Technology Group Co., Ltd., Beijing, China
Privacy concerns can effectively predict behavioral intention between users and short-form video platforms, but existing studies lack of multidimensional scales to measure privacy concerns towards short-form video platforms. To this end, this study took privacy concerns theory as the theoretical foundation to develop and validate a multidimensional privacy concerns scale in short-form video platforms by referring to the development of Smith, Milberg and Burke' multidimensional scale of concerns for information privacy (CFIP), Sheehan and Hoy's multidimensional scale of privacy concerns, Malhotra, Kim and Agarwal's Internet users' information privacy concerns (IUIPC) scale, and Hong and Thong's Internet privacy concerns (IPC) multidimensional scale. In this research, three representative short-form video platforms, TikTok, Kuaishou and Xigua, were selected as research samples. The multidimensional privacy concerns scale was refined by qualitative interviews and open-ended questionnaires et al. and tested by item analysis, exploratory factor analysis, confirmatory factor analysis, and discriminant validity et al. The results show that the privacy concerns scale towards short-form video platforms consists of three dimensions: collection concerns, awareness concerns, and usage concerns. And the multidimensional scale developed in this study has good reliability, convergent validity, and content validity, which can help guide short-form video platforms to take targeted measures to manage privacy concerns in business practices and provide a basis for future empirical studies on privacy concerns.
Introduction
Development of information technology has accelerated the popularization, application, and rapid expansion of social media. Today, social media are absolutely everywhere, and, among them, the short-form video platform, as a form of social media, is playing a crucial role in people's social lives. Short-form video platforms like TikTok, Kuaishou, and Twitter are widely available and have become a part of daily life for many users (Wang and Wu, 2021; Yang et al., 2021a). According to the 43rd Statistical Report on Internet Development in China released by China Internet Network Information Center (CNNIC), as of December 2021, the number of short-form video users reached 934 million, with the usage rate of 90.5 percent. It indicates that users of short-from video are already large, which become a quite active and indispensable part of social media users.
The purposes of using short-form video platforms are to establish and maintain relationships with people through virtual platforms and have a positive role in forming social capital (Yang and Ning, 2021). In order to maintain social relationships, users of short-form video platforms post various forms of information, such as profiles, short videos, comments, and online displays of their talents (Loiacono, 2015; Huang et al., 2017). However, due to the disclosure of personal information on short-form video platforms, personal privacy is exposed, and negative problems related to infringement are also occurring (Dhir et al., 2017; Choi and Sung, 2018; Mahmoodi et al., 2018; Watat and Jonathan, 2020; Wang et al., 2021). Some studies indicate that, with the continuous expansion of short-form video platforms, public privacy security issues gradually become prominent (Yang et al., 2018; Wang et al., 2021), and the continuous awakening of users' privacy awareness has become an important resistance to the further development of short-form video platforms (Emmert-Streib et al., 2019; Baker-Eveleth et al., 2021). This topic has been raised in the society, and the academic circle has also paid attention to it. There is no doubt that privacy concerns from the perspective of short-form video users have become a hot topic in the theoretical and academic area, which indicates a leading research direction in the field of short-form video platforms. It has become a meaningful question with many discussions, comments, and theoretical construction between individuals and short-form video platforms (Jozani et al., 2020; Bright et al., 2021; Herbert et al., 2021; Wang et al., 2021).
During the past decade, the issue of privacy concerns has drawn considerable attention among researchers. Scholars have conducted research of privacy concerns mainly in traditional offline market context and the traditional Internet context, and developed multidimensional scales to measure and quantify users' privacy concerns. To be specific, one is development of privacy concern scales centering on the traditional market. rewrite it as following: Under the background of traditional on line enterprises, Smith et al. (1996) developed and verified the multidimensional scale of CFIP, including four dimensions: Collection, Unauthorized secondary use, Improper access and Errors. On this basis, Stewart and Segars (2002) proposed a second-order factor model for measuring privacy concerns by using the same dimensions and measurement terms as CFIP; the other is the development of privacy concern scales in the context of traditional Internet. For example, Dinev and Hart (2004) developed a two-dimension privacy concerns scale applicable to the Internet environment, the dimensions of which are information finding and information abuse. Malhotra et al. (2004) proposed the IUIPC scale on the basis of Smith et al. (1996), containing three dimensions: Collection, Control, and Awareness. Hong and Thong (2013) further advanced and developed the study of Smith et al. (1996) and Malhotra et al. (2004) by constructing and verifying the third-order factor model. The three-order factor model includes two second-order factors of interaction management and information management, and six first-order factors of Collection, Secondary use, Error, Improper access, Control, and Awareness. At present, CFIP scale, IUIPC scale, and the Hong and Thong's three-order factor model have been widely used in internet-related fields and become important measurement tools for privacy concern research in the Internet environment.
However, unlike traditional offline market context and traditional Internet context, users' privacy concerns under short-form video platforms are quite different. Organizations can obtain users' personal data more easily for users' information disclosure is supplemented with device-generated data (e.g., device ID, the user's location, and contact list) (Belanger and Crossler, 2019). Such data are automatically shared with the developer once users accept platform permission requests (Dogruel et al., 2017). Besides, most developers share user data with third-parties for tracking and advertisement purposes; thus, enabling third-party companies to match the data from various apps and services, and make inferences about individual users (Vallina-Rodriguez et al., 2016). Users behavior can be constantly watched by platform developers or owners (Wottrich et al., 2019). Therefore, the dynamics of data sharing and disclosure have made privacy studies in this era more complicated than before (Barth and Jong, 2017; Belanger and Crossler, 2019; Wottrich et al., 2019). All of these can lead to the change of users' concept of privacy. Privacy is a subjective concept, and the change of users' concept of privacy will directly lead to the change of privacy concerns. Therefore, it is clear that dimensions of privacy concerns in prior research cannot fit the context of short-form video platforms usage, and there is a gap in research calling for more studies.
To maximize the potential of short-form video platforms, it is critical to understand short-form video platform users' privacy concerns. However, although some pioneering studies exist that work on the area of short-form video platforms (Anderson and Gerbing, 1998; Wang et al., 2021), few studies have been made to provide a theoretical framework on the specific nature of privacy concerns among short-form video platform users. To fill the gap in literature, this study examines privacy concerns from the perspective of short-form video platform users by extending to the short-form video platforms domain the current body of knowledge, centering on the traditional offline market and the traditional internet market.
Specifically, what are the constructs and constitutive dimensions of privacy concerns in short-form video platforms context? These questions are needed to be further answered. Therefore, this paper focuses on the context of short-form video platforms, redefines the connotation and constituent dimensions of privacy concerns, and develops a multidimensional measurement scale of privacy concerns in the new context. It can provide theoretical support and reference for the study of privacy issues related to short-form video platforms.
Literature review
Definitions of privacy concerns
When investigating users' attitudes toward privacy, western scholars in the field of management first introduced the concept of “Privacy Concerns” to measure users' concerns for privacy (Kerlinger, 1986). Campbell (1997) defined privacy concerns as “the degree of fairness perceived subjectively by individuals in the corresponding privacy context” in the survey of consumer market relations. In the study of consumer privacy concerns, Goodwin (1991) proposed that privacy concerns refer to the concerns that “individual privacy information stored in the database may be used by others and cause harm to individuals;” Smith et al. (1996) believed that privacy concerns are “an individual's concerns about how an organization collects and uses his or her personal information,” while Lanier and Saini (2008) defined privacy concerns as “anxiety about personal privacy.” Tan et al. (2013) described users' privacy concerns as “concern to control the acquisition and subsequent use of personal information” in the study on the influence of users' privacy concerns on the acceptability of social networking sites. When doing research on the differences of consumers' privacy concerns in different cultures and countries, Dinev and Hart (2006a) defined privacy concerns as “individuals' perceptions of what happens with the information they provide via the Internet.” In the research on privacy concerns of Internet users, Hong and Thong (2013) argued that “privacy concerns are Internet users' worries about websites' behavior of collecting and using their personal information, and reflect an individual's perception of the difference between the expected treatment of his or her personal information and the website's actual behavior.”
Thus, from the various definitions of privacy concerns, it can been seen that privacy concerns are influenced by these external contexts. As a result, although the concept of “privacy concerns” has been proposed for many years, there is still no single, widely accepted definition. In other words, privacy concerns are a complex, dynamic concept that changes with different situations (Moor, 1990; Lederer and Sethi, 1991; Jozani et al., 2020; Mwesiumo et al., 2021). In the last decade, with the continuous progress of technology, the ways that people socialize have undergone great changes. Social applications such as TikTok and Kuaishou have become the main tools for people's daily communication. However, some features of these short-form video platforms have brought great changes to people's privacy situation like data are automatically shared with the developer once users accept application's permission requests. It can constantly watch the activities of their users even when they do not use it (Dogruel et al., 2017). Therefore, with the rapid development of short-form video platforms, it is necessary to redefine users' privacy concerns from the point of view of the short-form video platform users.
Multidimensional scales of privacy concerns
As the importance of privacy concerns has been widely recognized, more and more scholars have been engaged in the field of privacy concerns measurement. Since Smith et al. (1996) developed the four-dimension CFIP scale, several scholars have successively implemented incremental modifications. For example, Dinev and Hart (2006b) proposed a scale applicable to the “transaction” situation; Rifon et al. (2005) raised a scale suitable for exploring the relationship between privacy concerns and subsequent behaviors. About multidimensional scales, Sheehan and Hoy (2000) developed the first scale suitable for measuring privacy concerns in the Internet environment, which provided a basis for exploring the antecedent variables of privacy concerns. In addition, (Malhotra et al., 2004) proposed the IUIPC scale based on the CFIP scale to make up for the deficiency of the CFIP in the network environment. Hong and Thong (2013) came up with the IPC scale. Among them, CFIP Scale, Sheehan and Hoy's Scale, IUIPC Scale, and Hong and Thong's IPC scale are the most representative ones.
Concerns for information privacy (CFIP)
The CFIP scale was developed by Smith et al. (1996) on the basis of strategic theory to capture individuals' concerns about organizational information privacy practices. It contains four dimensions: Information collection, Unauthorized secondary use, Improper access, and Errors.
Information collection refers to the process of information collection by organizations, which is likely to raise privacy concerns of individuals; information error refers to individuals' data errors caused by improper protection measures of organizations, which may lead to individuals' privacy concerns about possible personal information errors; unauthorized secondary use means that organizations use individuals' personal information for other purposes without permissions and they may share individuals' information with a third party or even sell the information for profit, resulting in the disclosure of individuals' privacy information to other organizations. Therefore, this situation will also raise privacy concerns of individuals; improper access reflects the security of information storage. Unauthorized third parties can obtain or use users' personal information, leading to unauthorized access or theft of users' information by third parties, which will also arouse users' concerns about privacy information.
The development process of CFIP included examinations of privacy literature and U.S. laws; experience surveys and focus groups; and the use of expert judges. The result was a parsimonious 15-item instrument with four sub-scales tapping into dimensions of individuals' concerns about organizational information privacy practices. The instrument was rigorously tested and validated across several heterogeneous populations, providing a high degree of confidence in the scales' validity, reliability, and generalizability.
As a reliable and valid measure, the four-dimensional model of CFIP has been successfully applied within the context of offline direct marketing (Smith et al., 1996; Campbell, 1997; Stewart and Segars, 2002). A number of studies also included the influence CFIP has on behavioral intentions (Pavlou and Xue, 2007; Melinda et al., 2008) or privacy actions (Dinev and Hart, 2006a; Son and Kim, 2008).
Sheehan and Hoy's scale
With the development of the Internet, Sheehan and Hoy (2000) realized the importance of developing a multidimensional scale to measure users' privacy concerns in the Internet environment. Therefore, on the basis of previous literature studies, a multidimensional scale for the earliest users to measure privacy concerns in the Internet environment is proposed, which contains five dimensions: Awareness of information collection, Information usage, Information sensitivity, Familiarity with entity, and Compensation.
Awareness of information collection refers to consumers' privacy concerns are likely to increase as they become aware that marketers have somehow obtained information about them without their awareness or permission (Cespedes and Smith, 1993). Moreover, they will not be as concerned about privacy if marketers obtain permission from them (Nowak and Phelps, 2010); Information usage is how marketers use consumer information. If information is used only for the purpose of the original transaction, consumers tend to be unconcerned about privacy. However, if marketers use information beyond the original transaction, consumers become increasingly concerned with privacy (Vidmar and David, 1985; Goodwin, 1991; Foxman and Paula, 1993; Cranor et al., 1999; Nowak and Phelps, 2010). Information sensitivity reflects to “the level of privacy concern an individual feels for a type of data in a specific situation” (Wacks, 1989; Weible, 1993). Consumers appear to be less concerned about the collection and usage of information about their product purchases and media habits and more concerned about the collection and usage of medical records, social security numbers, and financial information (Vidmar and David, 1985; Cranor et al., 1999; Nowak and Phelps, 2010). Sensitivity appears to be contextual; that is, what is considered sensitive differs by a person and by a situation (Jones, 1991; Milne and Gordon, 1993; Weible, 1993; Cranor et al., 1999); Familiarity with entity is closely related to people's willingness to disclose sensitive information and is the degree to which they trust the data gathering entity (Vidmar and David, 1985). If people are familiar with the entity, their privacy concerns are not likely to increase; Compensation means people's privacy concern can be decreased by compensation. Sometimes, whether an activity violates people's personal privacy is depended on how much benefit they get, because they are willing to disclose information for some type of benefits (Westin, 1968; Goodwin, 1991; Milne and Gordon, 1993).
The study of Sheehan and Hoy (2000) is one of the first to use e-mail to gather data from a national sample of online consumers. It is also one of the only studies that have attempted to examine the extent to which the knowledge of privacy concern in traditional direct marketing applies in the online context. Before their study, much of the literature on this topic has addressed privacy within the context of threats from traditional direct marketers (Sheehan and Hoy, 2000). However, different from the traditional direct market, Internet allows for interactive two-way communication and, accordingly, poses unique information privacy threats that differ from the issues previously addressed (Hoffman and Novak, 1996; Smith et al., 1996; Sheehan and Hoy, 2000). Therefore, it is very urgent to understand the privacy concerns of Internet users in the context of the Internet (Phelps and Ferrell, 2000). It was under this background that Sheehan and Hoy developed the privacy concern scale. Although this scale is not as widely used as the CFIP scale, it has great influence on the research of privacy concerns in the context of Internet. It is reasonable to argue that Sheehan and Hoy's scale is a milestone of privacy concerns research.
Internet users' information privacy concerns (IUIPC)
As Smith et al. (1996) put it, “the dimensionality is neither absolute nor static, since perceptions of advocates, consumers, and scholars could shift over time.” This is especially the case, given the fundamental change in the marketing environment caused by the widespread adoption of the Internet. Thus, in order to better measure privacy concerns in the context of the Internet, Malhotra et al. (2004) proposed the IUIPC scale based on CFIP and social contract theory, which focuses on “the subjective perceived fairness of individuals to information privacy situation,” including three dimensions of Collection, Control, and Awareness. Among them, Collection refers to the first dimension of IUIPC as the degree to which a person is concerned about the amount of individual-specific data possessed by others relative to the value of benefits received. Consumers are willing to give information to others for some benefits, which also means individuals are unwilling to release their personal information if they expect negative outcomes (Cohen, 1987); the second dimension of IUIPC is control, which reflects individuals' concerns for information privacy center on whether the individual has control over personal information as manifested by the existence of voice or exit (i.e., opt-out) (Thibaut and Walker, 1975; Gilliland, 1993; Caudill and Murphy, 2000). If there is a large potential exists for opportunistic behavior and breach of the social contract in a relational exchange, the concerns for control become more pronounced; Awareness is a passive dimension of information privacy, and it refers to the degree to which a consumer is concerned about his/her awareness of organizational information privacy practices (Foxman and Paula, 1993; Culnan, 1995).
Under the background that information privacy was identified as a major problem holding back the confidence of consumers to shop online, IUIPC appeared. It includes a 10-item, which was shown to reasonably represent the dimensionality of privacy concerns. By using this scale, it is easy to demonstrate how consumers' privacy concerns negatively influenced their willingness to carry on relationships with online companies. IUIPC can be used as a useful tool for analyzing privacy concerns of online consumers and their reactions to privacy threats on the internet. There is no denying that IUIPC is developed on the basis of CFIP. However, the overage of IUIPC includes and extends that of CFIP. It has been widely used and benefited lot scholars in their later studies.
The emergence of IUIPC scale has promoted the research on privacy concerns in the context of the Internet. Yang et al. (2008) systematically reviewed the existing scale of privacy concerns from aspects of a theoretical basis, dimension, the application field, and main contribution. Through the empirical test of 418 college students and young enterprise employees, it is found that IUIPC has higher stability and convergence validity, and is more suitable for Chinese situations; Wang et al. (2012) discussed the influencing factors of personal online privacy information by referring to IUIPC scale to design a questionnaire on privacy concerns. On the basis of planned behavior theory, privacy computing theory and other relevant theories, Qi and Liu (2018) adopted the APCO model and the IUIPC scale to construct a research model to present privacy concerns of the Chinese public in the current big data environment and its influencing factors.
Hong and Thong's scale
Given the importance of information privacy concerns and there is a lack of consistency in these conceptualizations (Culnan, 1993; Smith et al., 1996; Stewart and Segars, 2002; Chen and Rea, 2004; Malhotra et al., 2004; Earp et al., 2005; Alge et al., 2006; Eastlick et al., 2006; Buchanan et al., 2007; Castañeda and Montoro, 2007), Hong and Thong decided to develop a scale based on the network environment.
Hong and Thong (2013) integrated the CFIP and IUIPC scales and constructed factor models of different orders. Through four large-scale network surveys and confirmatory factor analysis, the study found that the integrated scale had better reliability and validity than the separate CFIP or IUIPC scales. The third-order factor model is most consistent with the empirical survey data, which include two second-order factors of interaction management and information management, and six first-order factors of Collection, Secondary usage, Errors, Improper access, Control, and Awareness.
Collection is the degree to which a person is concerned about the amount of individual-specific data possessed by websites (Malhotra et al., 2004); secondary usage is the degree to which a person is concerned that personal information is collected by websites for one purpose but is used for another, a secondary purpose without authorization from the individual (Smith et al., 1996); Errors is the degree to which a person is concerned that protections against deliberate and accidental errors in personal data collected by websites are inadequate (Smith et al., 1996); Improper access is the degree to which a person is concerned that personal information held by websites is readily available to people not properly authorized to view or work with the data (Smith et al., 1996); Control is the degree to which a person is concerned that he/she does not have adequate control over his/her personal information held by websites (Malhotra et al., 2004); Finally, awareness is the degree to which a person is concerned about his/her awareness of information privacy practices by websites (Malhotra et al., 2004).
Drawing on multidimensional developmental theory and an extensive literature review, Hong and Thong (2013) consolidated the existing knowledge about information privacy by developing an integrated conceptualization of IPC, which consists of a third-order general factor, two second-order factors of interaction management and information management, and six first-order factors. The reliability and validity of this integrated conceptualization of IPC were validated through a series of four studies involving large-scale online surveys. This research has contributed to build a better understanding of the conceptualization of IPC and provided a modified instrument for future research into IPC. This IPC model is well accepted, but the related empirical research is insufficient. Based on this research, some scholars continue to explore the dimensions of IPC: such as the study of Mwesiumo et al. (2021), which reported a confirmatory composite analysis of a scale for measuring privacy concerns, and the effect of privacy concerns on the willingness to provide personal data by replicating Hong and Thong's IPC Scale; Gaurav and Fiona (2022) examined the conceptualization of Internet privacy concerns (IPC) by extending Hong and Thong's (2013) model, with the addition of two dimensions: oversight and the RTBF.
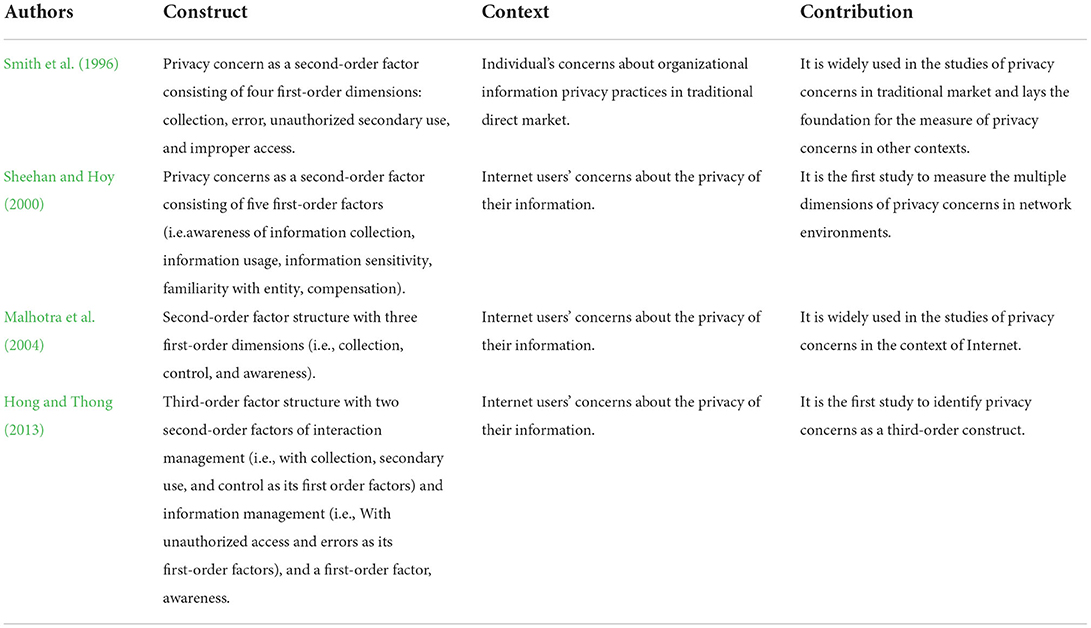
According to the studies above, the main composition, research context, and main contribution of the representative privacy concerns scale are shown in Table 1.
Research review
In summary, the number of dimensions identified varies by study. Among them, the most widely used are CFIP and IUICP. The majority of positivist empirical information system studies on privacy concerns predominantly adopt one of the two popular constructs (CFIP or IUIPC) to measure users' privacy concerns (Smith et al., 2011; Warkentin et al., 2016). However, as the external environment such as technology changes, the privacy situation is constantly changing. More and more people are visiting short-form video platforms. The emergence and the development of short-form video platforms are unstoppable; people constantly engage in social media and connect with others on mobile devices or PC, which means the preceding constructs of privacy concerns may have to be revisited (Belanger and Crossler, 2011). In view of this, based on the existing multidimensional scale of privacy concerns and combined with the usage situation of short-form video platforms, this study develops a multidimensional scale of users' privacy concerns in the context of short-form video platforms with good psychological measurement attributes. In the process of scale development, findings of privacy concerns by prior scholars in the context of traditional market and Internet will be fully considered to better analyze the degree of users' privacy concerns and behavior in the specific context.
Development process of privacy concerns scale
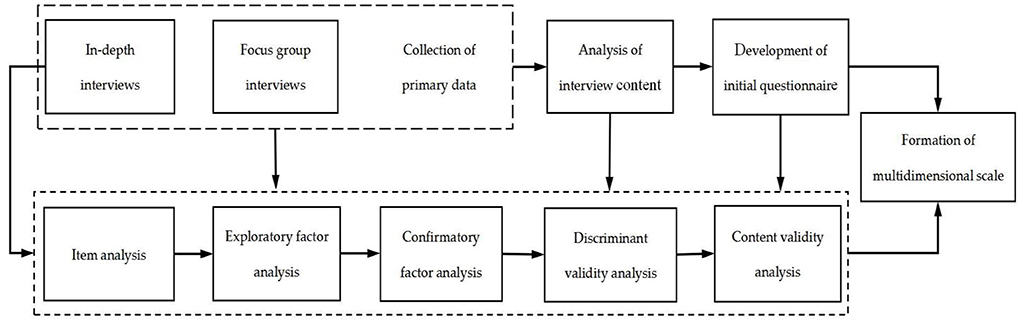
Based on the analysis of prior literature on privacy concerns, this study collected the original data of privacy concerns from the perspective of Chinese users through interviews, and developed the privacy concerns scale according to the Grounded Theory (Strauss and Corbin, 1990). There are two main reasons why this study follows this process. On the one hand, according to psychometric theory, an individual in-depth interview and a focus-group interview are advisable for collecting data to develop scale. After original data collection, through systematic coding, induction and extraction of the original data, the initial scale and measurement items are formed, and then by pretesting of the preliminary measurement items, the formal questionnaire appears. On the other hand, this study is about the user's attitudes and behavior toward short-form video platforms, that is, the phenomenon of privacy concerns and worries. Selecting representative users as interview objects to discover and reveal the concept and dimensions of privacy concerns through in-depth data mining is a typical generation process from a phenomenon to a theory. It is suitable to adopt grounded theory to develop the scale. The scale development process of privacy concerns in this study is as shown in Figure 1.
Collection of primary data
First, the existing literature on privacy concerns was sorted out, reviewed, and commented so as to know the origin, development, concept and multidimensional structure of privacy concerns. Second, the existing scale development methods of multidimensional variables of privacy concern were analyzed, mainly including the situation, dimension composition, and application of scales. The representative ones are CFIP, Sheehan and Hoy's scale, IUPIC, and Hong and Thong's IPC scale. In other words, this study developed the multidimensional scale of privacy concern in the context of short-form video platforms by referring to the scale measurement paradigm of privacy concerns theory in current hot research fields, as the theoretical basis.
Third, individual in-depth interviews and focus-group interviews were used to obtain the data of users' privacy concerns in scenarios of using short-form video platforms. This study selected people with experience in using short-form video platforms as the interviewees. In order to make sure each interviewee can express his or her ideas freely, the in-depth interviews are open-ended. The interviews were mainly focused on the following three aspects: Number one, there may be risks in disclosing or semi-disclosing user information on short-form video platforms. For example, identity theft, online stalking and online harassment, etc. Number two, private information posted on short-form video platforms can put users under public scrutiny, potentially creating a permanent record and negatively affecting users in the future. Number three, personal information is more likely to be obtained and visible by unknown third parties, damaging the protection of user privacy.
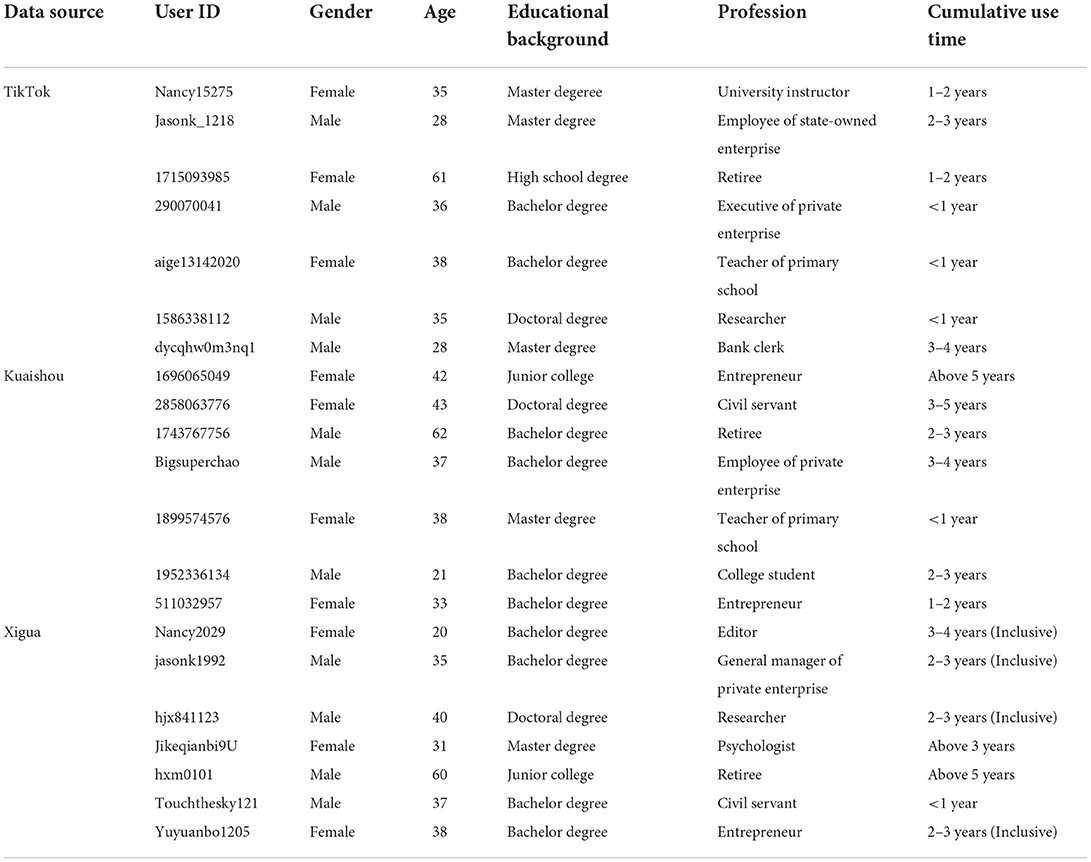
In this study, users of TikTok, Kuaishou, and Xigua platforms were tracked and interviewed from July to November 2021. Up to 13 November 2021, a total of 21 users were selected as data collection and interview objects. The interview records of 21 users were classified and cleaned to form Word files, which became the initial data for the development of an initial questionnaire on privacy concerns. Sample characteristics of interviewees are shown in Table 2.
From Table 2, it can be seen that seven interviewees are TikTok users, seven interviewees are Kuaishou users, and the rest are Xigua platform users. Most of the interviewees have certain experience in using short video applications. The proportion of males and females is balanced, and the overall age is relatively young, mainly between 20 and 42. Most of them have received higher education.
Development of the initial questionnaire
Based on interview and primary data collection, the items of privacy concerns multidimensional scale were compiled and ranked in frequency. The questions with low frequency were deleted, and the initial privacy concerns questionnaire composed of 25 questions was finally formed. To check the consistency and rigor of the questionnaire, seven of the experienced users were randomly selected for testing from November 15 to 30, 2021. And experts in the field were invited to review the contents of the initial questionnaire and modify the scale items according to the actual situation of users' privacy concerns. And then the completion and simplification of statements were completed. Since the compilation of the items adopted a bottom-up approach drawing on the interview text data, the items were not deleted and merged in this process. Finally, 20 privacy concerns measurement items based on users' perspectives in the context of using short-form video platforms were formed, as shown in Table 3.
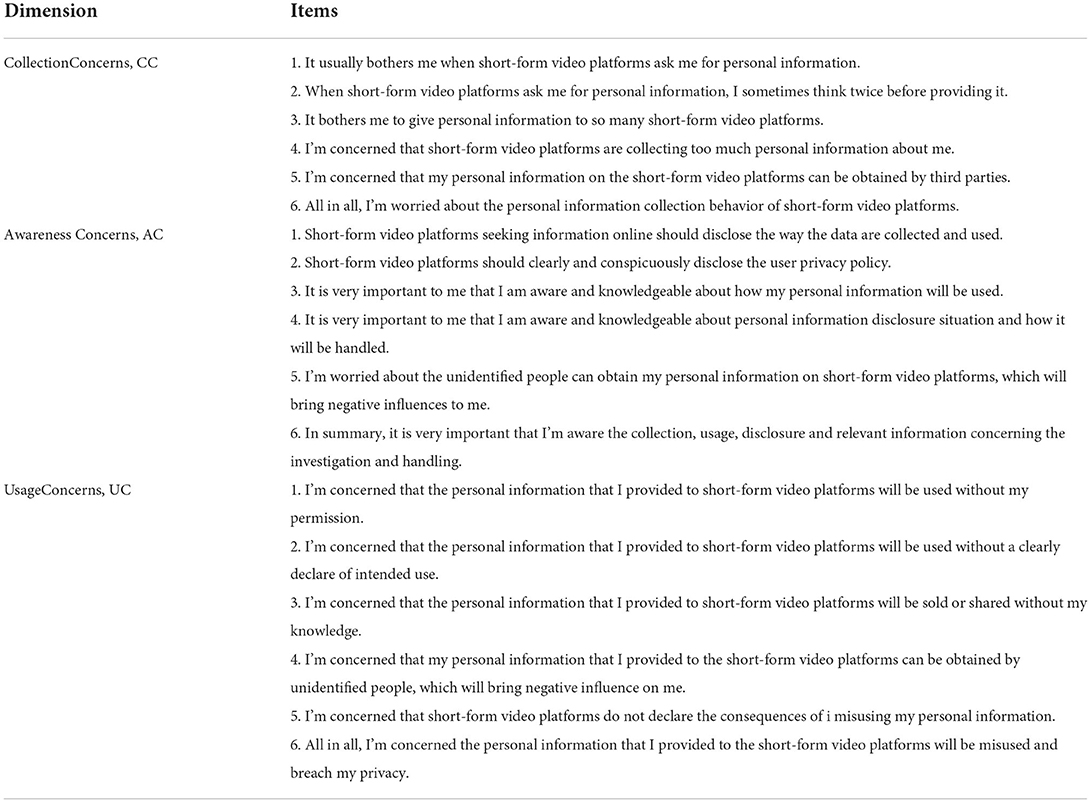
Table 3 is composed by three dimensions of privacy concerns and 20 items. The first column indicates one dimension of privacy concerns, collection concerns that contain seven items. The second column is awareness concerns with six items. And the last column is the third dimension of privacy concerns that have seven items.
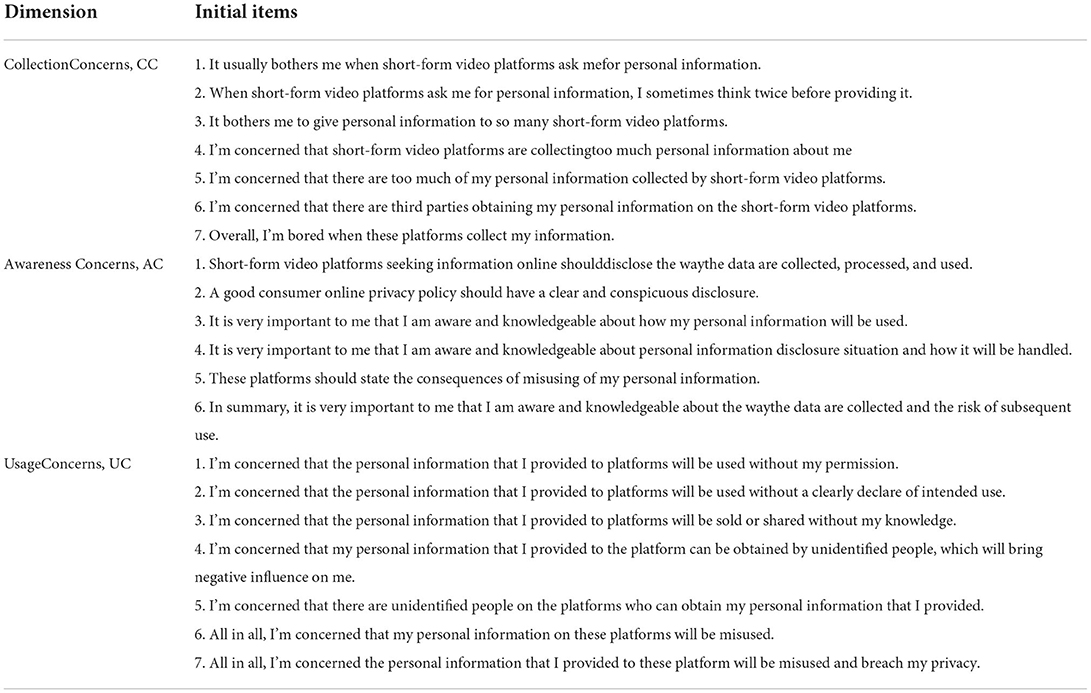
On the basis of the analysis of the privacy concerns interview content, five researchers of short-form video platforms in the field of marketing comprehensively processed the initial measurement items of privacy concerns formed by the interview information, focusing on proofreading the written expression, semantic integrity, and overall content of each measurement item. The items that did not conform to academic norms were modified to ensure content validity and surface validity. Related items were deleted and merged to further refine 18 items, thus forming a questionnaire for the development and testing of multidimensional scale of privacy concerns (as shown in Table 4).
Table 4 has two components. One is three dimensions of privacy concerns, and the other is 18 items. The first column indicates one dimension of privacy concerns, collection concerns that contain six items. The second column is awareness concerns with six items. And the last column is the third dimension of privacy concerns that have six items.
Research methods
This study applied SPSS 24.0 and Mplus 7.0 for statistical analysis of the data. First of all, all valid data were used for items analysis, and the items without discrimination were deleted to ensure the discrimination. Second, all the data were divided into two parts according to the method of random splitting, half of which was used for exploratory factor analysis, and the other half was used for confirmatory factor analysis. Then, reliability and validity tests were performed on whole data. Based on the results of factor analysis, the multidimensional scale of privacy concerns was tested to verify its reliability and validity.
Empirical testing of the privacy concern scale
Participants and procedure
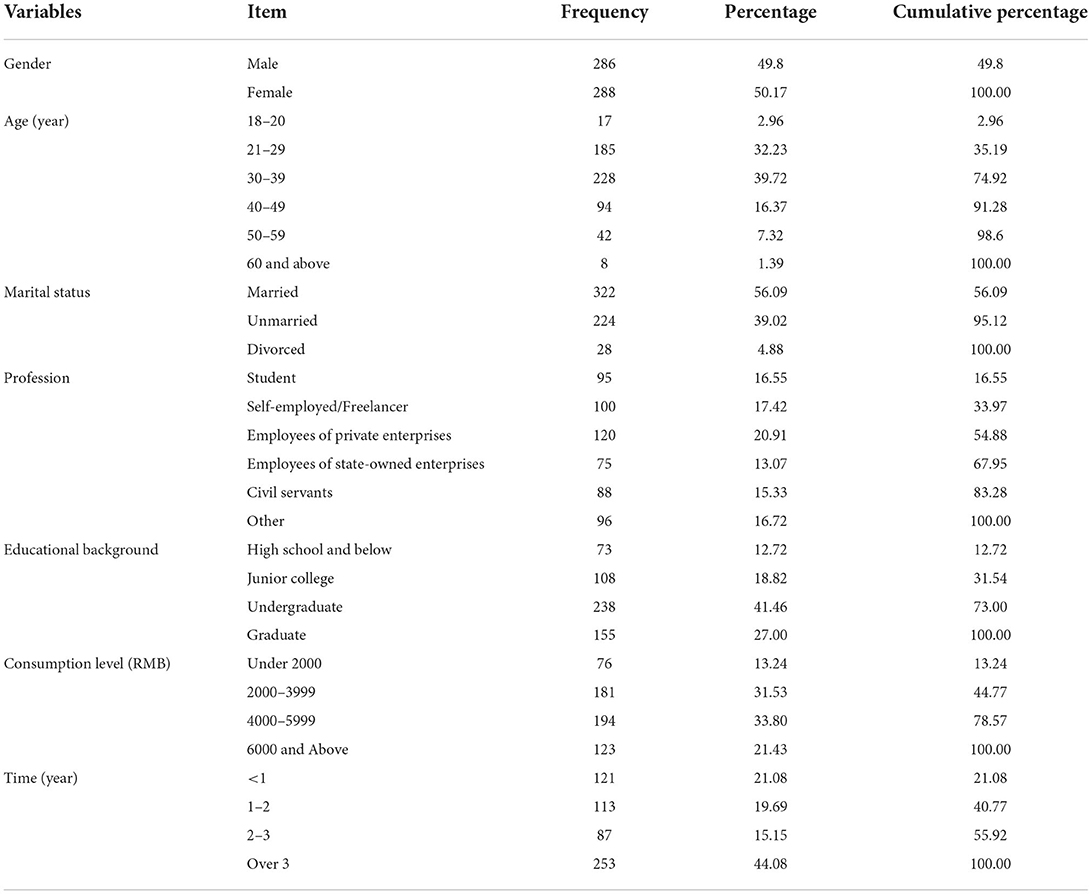
This study selected the mass users of TikTok, Kuaishou, and Xigua, three local short-form video platforms, as the research objects. The main reasons why TikTok, Kuaishou, and Xigua were selected for data investigation in this study are as follows: First of all, these three platforms belong to three different categories. TikTok mainly belongs to the short-form video platform, which is more favored by the young generation. Kuaishou is popular in general public of second and third-tier cities. Xigua is a traditional short-form video platform, so it has certain universality in category distribution; Second, TikTok, Kuaishou, and Xigua are all representative short-form video platforms, leading in their respective market segments; The last reason is that these three short-form video platforms all started and fast developed in China, and they have occupied most of the Chinese short-form video sharing market. Therefore, it is reasonable to reach the conclusion that TikTok, Kuaishou, and Xigua can be taken as representatives of short-form video platforms in China. Choosing mass users of these three platforms to carry out research is quite consistent with the original intention of this study. The survey questionnaire includes 18 items, all of which were measured by the Likert 7-point scale. The degree of agreement on the items ranges from “strongly disagree” to “strongly agree,” and is recorded as 1–7 points, respectively. Questionnaires were distributed on the Wenjuanxing platform from December 15, 2021 to January 20, 2022. In this study, a total of 666 questionnaires were sent out and 666 were collected. After excluding invalid questionnaires, a total of 574 valid questionnaires were obtained, and the effective rate of questionnaire survey was 86.19%. The specific characteristics of the samples are shown in Table 5.
Table 5 shows the variables like gender, age, marital status, profession, educational background, consumption level, time of people do the questionnaire. It is worth noting that the ration of females to males is nearly one to one, which is good for objectiveness of this research. And the majority of people do the questionnaire are aged between 21 and 39, which correspond to the reality of China that young people are more likely to use short-form video platforms. The industrial distribution of people do the questionnaire is wide.
Items analysis
It is a quite important work in scale development to ensure that the questionnaire items are effective and discriminative. Therefore, SPSS24.0 was used for the data pretest in this study. The purpose is to confirm whether the scale questions are fluent in meaning, whether there are wrong words, and whether the arrangement is appropriate. In order to remove undiscriminating questions (or variables) as a basis for improvement, one of the most important jobs is to do items analysis.
Item analysis is essentially a t-test, which verifies whether there is a difference between high and low groups. This study ranked the dimensions of privacy concerns from highest to lowest. Then, the data of all the questions were divided into the high group, the low group, and the medium group. Prior studies have shown that there should be significant differences between the average data of high and low groups. If there is no significant difference, it means that the scores of high and low groups are too close, that is, it is an invalid item, because there is no difference between the scores of all items. Obviously, it is not scattered enough, so this item should be deleted (Babbie, 2004).
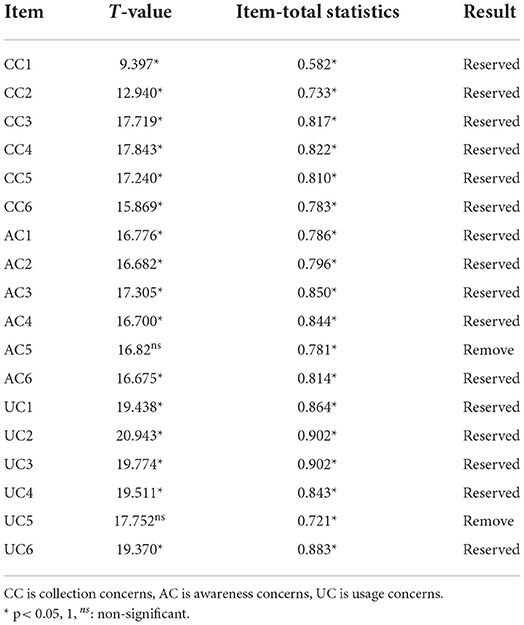
In this study, the specific steps of item analysis are as follows: First step, the items of each dimension are summed up respectively and the new variables are converted and calculated. Second, find the values of 27th and 73rd quantiles for each dimension. The third step is to divide the data of each dimension into the low group and the high group. The fourth step is to detect whether the mean difference between high and low groups in each dimension is significant, and then to judge whether the questionnaire questions are discriminative.
As shown in Table 6, t-test P of Items AC5 and UC5 is not significant, while t-test P of other items meets p <0.05, indicating that there are significant differences between high and low groups of other items, except Items AC5 and UC5. Therefore, Items AC5 and UC5 should be deleted and the other items retained. As a result, the 18 multidimensional measurement items of privacy concern were retained as 16 after item analysis.
Exploratory factor analysis
In order to test the reliability of the three dimensions extracted during the development of the multidimensional scale of privacy concerns, this study used 287 valid data extracted from the first part to conduct exploratory factor analysis on 16 items retained in the item analysis.
The exploratory factor analysis process is as follows.
First, SPSS24.0 was used to analyze data from 287 samples. The results show that the privacy concerns multidimensional scale has a KMO coefficient value of 0.925, and the Bartlett sphericity test coefficient was 2,365.59 (df = 159, p < 0.001). This indicates the possibility of sharing factors between items and significant correlation between dimensions. Therefore, the sample data are suitable for exploratory factor analysis.
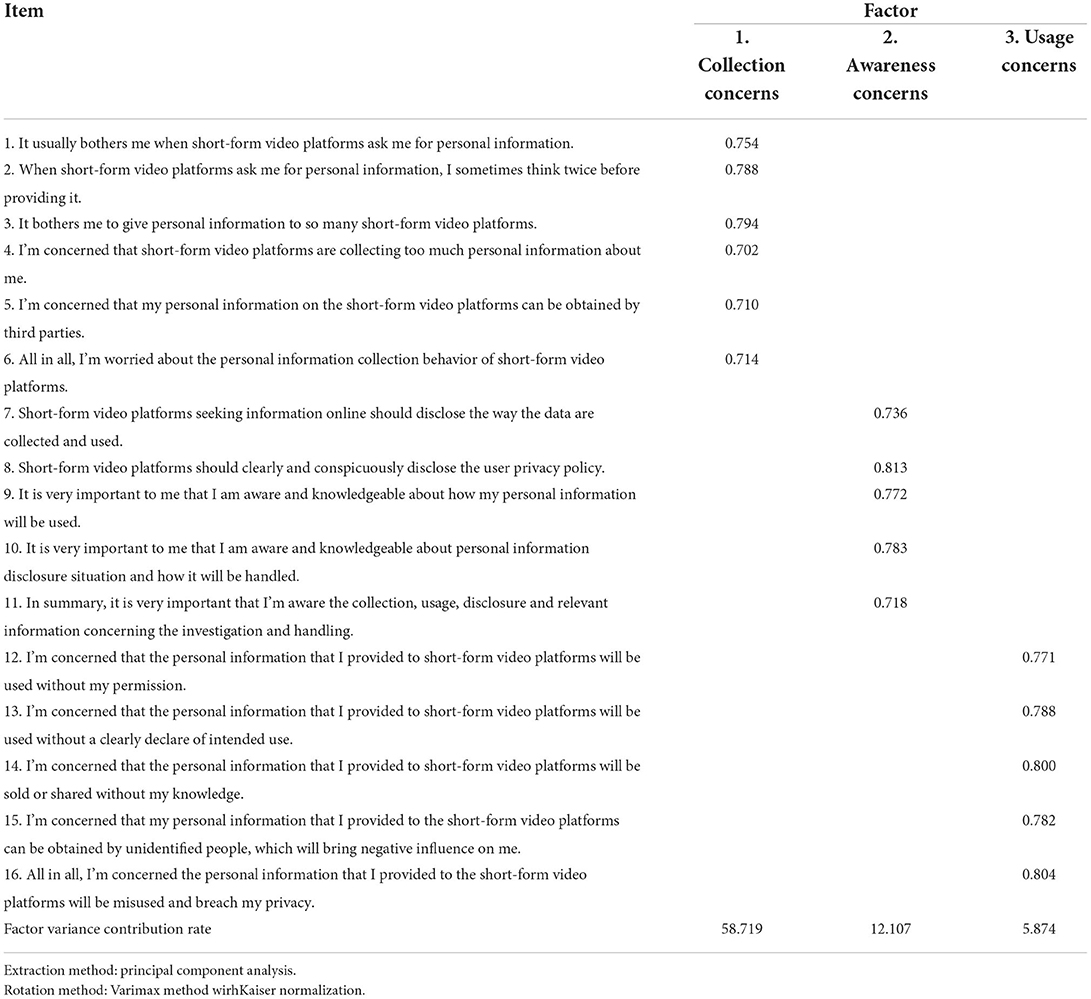
Second, this study adopts the principal component method for exploratory factor analysis and the orthogonal rotation method for factor rotation to extract factors with eigenvalues >1. At the same time, three factors are extracted combined with the gravel plot test. Delete the questions of factors according to the factor loading. Following previous scholars (Hu and Bentler, 1999; Hinkin, 2005) suggest that Standardized Factor Loading for all dimensions should be greater than at least 0.40 without multiple loadings. Factor items classification is roughly the same and retains the important elements of relevant literature and interviews, indicating that factor structure has a good factor categorization. As shown in Table 7, according to the distribution of each item in the three variables, the project was further screened in accordance with the above suggestions. After each item was deleted, factor analysis was conducted again. Finally, the factor load of each item was more than 0.40, without double loading. In addition, the cumulative variance contribution rate of the three factors is 76.7%, which further indicates that the factors are properly categorized and relatively ideal. Therefore, this study found that the structure of privacy concerns includes three dimensions. According to the meaning expressed by each factor item, this study named them separately collection concerns, awareness concerns, and usage concerns. Specifically, collection concerns are the degree to which a short-form video platform user is concerned about service providers' collection of personal information; Awareness concerns are the degree to which a short-form video platform user is concerned about his/her awareness of service providers' information privacy practices; Usage concerns are the degree to which a short-form video platform user is concerned about the acquisition and subsequent use of personal information by short-form video platforms.
Finally, according to Hinkin (2005) and Yang et al. (2021b), the optimal effect is to maintain 4–6 items in each dimension during scale development. The scale developed in this study contains six items of collection concerns, five items of awareness concerns, and five items of usage concerns, which are consistent with Hinkin (2005) and Yang et al. (2022). Therefore, the three-dimension privacy concerns scale developed in this study is reasonable in terms of the number of items.
Confirmatory factor analysis
In order to further verify whether the composition of the three-dimension scale of privacy concerns is stable, this study adopted the other 287 sample data for confirmatory factor analysis to judge whether the results of exploratory factor analysis can be supported by other samples. If the results of exploratory factor analysis can be verified by confirmatory factor analysis of the other half of the data, it indicates that the three-dimensional privacy concerns structure developed in this study has good convergence validity.
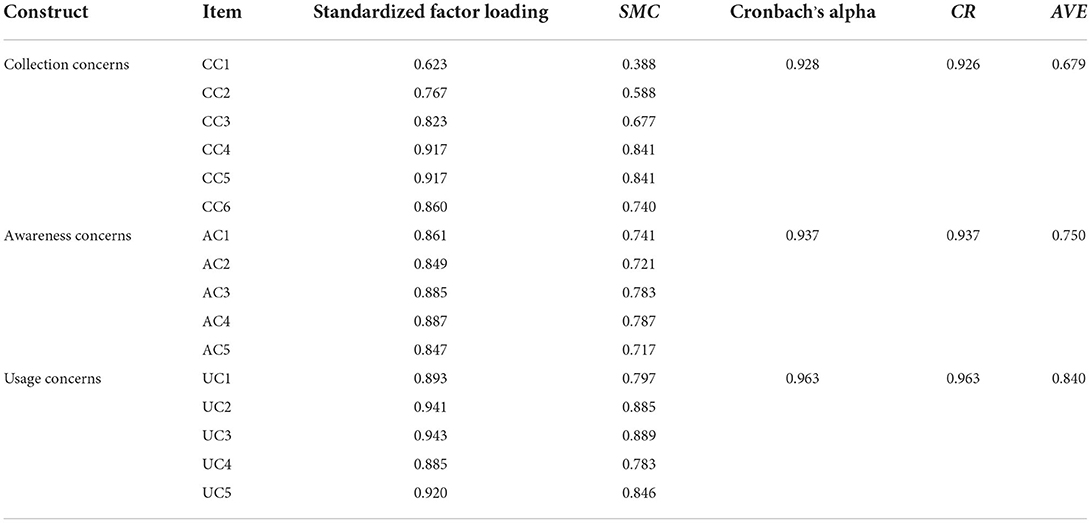
This study evaluates and revises the measurement model of Confirmatory Factor Analysis (CFA) according to the approach of Anderson and Gerbing (1998). That is, CFA should report Factor Loading, Cronbach's Alpha, Composite Reliability (CR), and Average Variance Extracted (AVE) for all variables. Fornell and Larcker (1981); Nunnally and Bernstein (1994), and Hair et al. (2017) clearly stated that, when the Factor Loading is >0.50, Cronbach's Alpha is >0.70, the CR is >0.60, and the AVE is >0.50, then the measurement model has good convergent validity.
This study applied Mplus 7.0 for CFA analysis, and the indicators of interest for the CFA are reported in Table 8. In this study, Factor loadings of all dimensions are between 0.623 and 0.943, Cronbach's Alpha is between 0.928 and 0.963, CR is between 0.926 and 0.963, and AVE is between 0.679 and 0.840. Thus, the results of Factor Loading, Cronbach's Alpha, CR, and AVE meet the criteria of Fornell and Larcker (1981); Nunnally and Bernstein (1994), and Hair et al. (2017). Therefore, the results of the CFA analysis indicate good convergence validity for all the constructs.
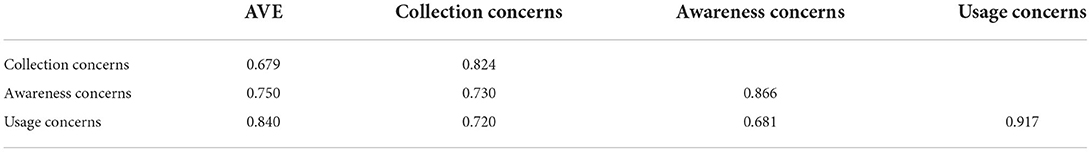
Discriminant validity
Table 9 reports the discriminant validity for the measurement model; the square roots of the AVE are reproduced on the diagonal. Discriminant validity is the extent to which the measure is not a reflection of some other variables. This research has examined discriminant validity using Fornell and Larcker (1981) recommendation. Table 9 shows that the squared root of average variance extracted for each construct is greater than the correlations between the constructs and all other constructs. The results support Fornell and Larcker's (1981) requirement of discriminant validity.
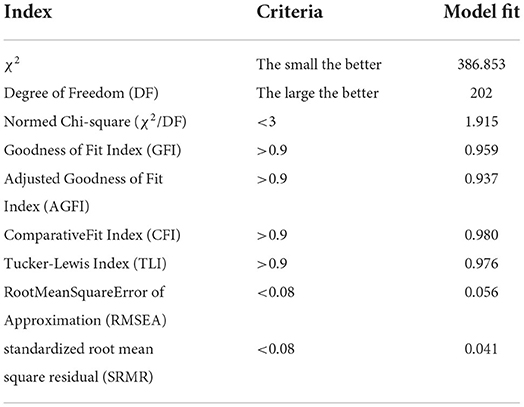
This study adopts a wide range of methods used in previous structural equation modeling studies to analyze the structural model fit. That is, the nine goodness-of-fit indicators are analyzed to determine whether the study model has a good fit Jackson et al. (2009). As suggested by Jackson et al. (2009), χ2, degree of freedom (DF), Normed chi-sqr (χ2/DF), root mean square error of approximation (RMSEA), standardized root mean square residual (SRMR), Tucker-Lewis index (TLI), comparative fit index (CFI), goodness of fit index (GFI), and adjusted goodness of fit index (AGFI) are the common metrics used to test the fit of research models (Janda, 1998; Kline, 2011). In SEM analysis, if the sample size is larger than 200, it will cause chi-square to inflate, leading to a decreased model fit (Bollen and Stine, 1992). This study used Bollen-Stine Bootstrap to corrected SEM chi-square. After Bollen-Stine bootstrapping correction, the model fits indices fit all the criteria of suggestions as shown in Table 10. The results found χ2 = 386.853, DF = 202, 1 < Normed Chi-sqr (χ2/DF) = 1.915 < 3, RMSEA = 0.056 < 0.08, SRMR = 0.041 < 0.08, TLI = 0.976 > 0.9, CFI = 0.980 > 0.9, GFI = 0.959 > 0.9, AGFI = 0.937 > 0.9. This indicates that the structural model of this study has a good fit.
Content validity analysis
According to the CFA analysis, the Crobanch's α coefficients of collection concerns, awareness concerns, and usage concerns are 0.928, 0.937, and 0.963, respectively, and the internal consistency coefficients are between 0.75 and 0.93, which all meet the range. In other words, it has good reliability. And then the content validity is needed to be further analyzed.
The privacy concerns scale in this study is a measuring tool based on the perspective of short-form video platform users. According to prior studies (Chen, 2000, 2010; You, 2010; Warren et al., 2019; Yang et al., 2022), in order to make the scale conform to the standard, this study conducted in-depth interviews and focus-group interviews with users through standardized procedures, and coded the initial interview materials step by step, drawing on the grounded theory to extract the initial questionnaire on privacy concerns (Corbin and Strauss, 1990). The whole process was carried out under the guidance of the doctoral supervisor of enterprise management major, and was jointly carried out by two doctoral students and two young teachers, who are good at comprehensive research methods. After rounds of discussions, it was concluded that privacy concerns were composed of three dimensions: collection concerns, awareness concerns, and usage concerns. The measurement items of the three dimensions of privacy concerns are designed by screening and refining the interview content, and are carefully tested. It can be seen that the development process of privacy concerns scale is scientific and rigorous. Therefore, the privacy concerns scale in this study has good content validity.
Research results and discussion
General discussion
On the basis of privacy concerns relevant theory, this study firstly developed a tool to measure users' privacy concerns in short-form video platforms through in-depth interviews, questionnaires, and focus groups. After initial data collection (21 valid samples) and questionnaire data collection (574 valid samples), the measurement tool finally retained 16 items, and extracted three main factors based on exploratory factor analysis results: the collection concerns factor, the awareness concerns factor, and the usage concerns factor. Specifically, the three factors of privacy concerns can explain the total variance by 76.7%, and the variance explained by the single factor is as follows: 58.719% of the total variance explained by the collection of the concerns factor, 12.107% of the total variance explained by the awareness concerns factor, and 5.874% of the total variance explained by the usage of the concerns factor. This indicates that the greatest concerns of users are the collection concerns, followed by awareness concerns, and, finally, usage concerns, which may be because privacy concerns are a kind of state of mind for worry and anxiety.
The reliability and validity test results of privacy concerns scale further showed that Cronbach's alpha of the collection concerns factor = 0.928 > 0.70, the awareness concerns factor = 0.937 > 0.70, and the usage concerns factor = 0.963 > 0.70. Obviously, the reliability of the three dimensions of privacy concerns is in the acceptable range, indicating that the measurement tool has good internal consistency. Therefore, the multidimensional scale of privacy concerns developed in this study has good stability and reliability. Furthermore, CFA test results showed that CR of collection concerns = 0.926 > 0.60, CR of awareness concerns = 0.937 > 0.60, CR of usage concerns = 0.963 > 0.60. AVE of collection concerns = 0.679 > 0.50, AVE of awareness concerns = 0.750 > 0.50, AVE of usage concerns = 0.840 > 0.50. This means that the privacy concerns scale developed in this study has good convergence validity (Fornell and Larcker, 1981; Hair et al., 2017). Therefore, quantitative measurement can be carried out well.
The results of discriminant validity analysis show that the AVE square root of collection concerns, awareness concerns and usage concerns are larger than the correlation coefficient between dimensions, which means that the multidimensional scale of privacy concerns has good convergence validity. In addition, the development of multidimensional scale in this study is based on previous studies of privacy concerns, such as CFIP scale, Sheehan and Hoy's scale, IUPIC scale, and Hong and Thong's IPC Scale by drawing reference from a paradigm of these existing scales and combined with findings extracted from a qualitative interview and a pre-survey. Obviously, the development process of privacy concern scale in this study is scientific and rigorous, and the scale has good content validity. Therefore, the test results of content reliability and validity of this study indicate that the multidimensional scale of privacy concerns developed in this study has good reliability and validity, which provides a basis for subsequent quantitative research.
Theoretical contributions
Several theoretical implications emerge from this work. First, this study gives a clear concept of privacy concerns in the context of short-form video platforms. The new concept of privacy concerns offers comprehensive coverage of users' privacy needs. Before this study, there are different definitions of privacy concerns in the existing literature, and no consensus has been reached yet (Moor, 1990; Jozani et al., 2020; Mwesiumo et al., 2021). Their definitions of privacy concerns are mostly from the subjective perspective of people's perceptions or perceived differences. Early scholars believed that privacy concern was people's subjective perceptions of whether their information privacy was treated fairly (Smith et al., 1996), and regarded it as a key indicator of individuals' cognition and attitude toward their privacy. As Internet gradually becomes the main platform for collecting, storing, transmitting, and publishing massive personal information, Internet privacy concerns have attracted more and more attention and discussion. Scholars in this field defined Internet privacy concerns as: privacy concerns are Internet users' worries about websites' behavior of collecting and using their personal information, and reflect an individual's perception of the difference between the expected treatment of his or her personal information and the website's actual behavior (Hong and Thong, 2013). This definition has been widely adopted by the academic community for a period of time. However, the Internet has been widely integrated into all areas of people's lives, which is a very broad situation. Users' concept of privacy concerns has changed with the technological, cultural, institutional, and self-conscious factors of their environment. As a result, a clear definition of the specific context in which the concept is applied is the basis for subsequent research. Referring to the definitions of privacy concern in existing literature, this study concluded that users' privacy concerns from the perspective of users of short-form video platforms are “users' anxiety about personal privacy and concerns about the acquisition and subsequent use of personal information by short-form video platforms.” This provides a solid guarantee for subsequent studies of short-form video users' privacy concerns.
Second, this research develops a reliable and valid scale for measuring users' privacy concerns, which can be applied in the context of short-form video platforms. The multidimensional scales of privacy concerns in the existing literature were developed against the background of western countries, which is not completely applicable to the situation of China. In addition, with the rapid development of short-form video platforms today, the general applicability of existing measurement scales is questionable. Considering that a reliable scale is the basis for follow-up studies, this study developed a scale with 16 items, which can be used to measure the privacy concerns degree of short-form video platform users. This scale was developed in the context of short-form video platforms with good reliability and validity. It is the further evolution and development of CFIP, IUIPC, and IPC scales; comparing with other specific, practice-oriented scales, this scale has the potential to be applicable to a variety of privacy-related contexts.
Third, this study lays a solid foundation for future empirical research. In prior studies, scholars did not build effective measurement tools for users' privacy concerns in the context of short-form video platforms. By referring to the multidimensional scale of user privacy concerns in the context of the traditional market and Internet, this study extends research of user privacy concern to the field of short-form video platforms, which not only enables the theory of privacy concerns to expand and apply from macroscopic Internet context to specific short-form video platform context but also provides a new perspective and useful reference for studying the relationship between users and of short-form video platforms. It lays a foundation for future empirical research on privacy concerns.
Practical implications
The findings of this study also have practical implications. Empowered by new technologies, such as big data, artificial intelligence, virtual reality, and 5G, short-form video platforms are in their “golden Age.” As information carriers, they will enter a new period of development and flourish in more fields and industries in the future, and users' needs will be more lean, individuation, and diversification. For the continuous usage of users, it is an urgent need for developers of short-form video platforms to know how to reduce the privacy concerns of users and how to meet their privacy protection needs.
First, the findings of this study remind developers of short-form video platforms that privacy concerns are multidimensional; it is unlikely that any single feature could fulfill all privacy protection needs. In other words, when it comes to privacy protection of short-form video platform users, three dimensions: collection concerns, awareness concerns, and usage concerns should be considered instead of one or two dimensions. For example, developers of these platforms should realize that users' consent should be obtained before collecting and using their personal information, and a clear statement, including the scope of collection, purpose of use and corresponding protection measures, should be given to users to ensure the users' awareness. In addition, users' information beyond the scope of permission shall not be collected without authorization, and user information shall not be used for improper purposes (such as disclosure, exchange, illegal trading, etc.). And the consequences of misusing, disclosure, etc., users' data should be listed.
Second, the findings of this research indicate that short-form video platform users concern about the availability, integrity, and effectiveness of privacy policies. For developers, they have to realize that privacy policies should be formulated with the understanding that, while big data and artificial intelligence are important forces driving social development, they should not be at the expense of users' privacy. Privacy policies are legal agreement between short-form video platforms and their users. Developers of platforms should take users as the center, and create high-quality privacy policies to meet the users' needs. The developers should bear in mind that good privacy policies cannot only protect users' personal information, ensure the users' right of awareness, but also establish a trust relationship between platforms and users so as to improve the users' trust, increase the users' activity, and improve their stickiness. Moreover, the developers of short-form video platforms should resolutely resist “Holson's choice,” and follow the principle of authorization and consent, openness, and transparency, adhering to the dominant position of users.
Third, technology protection system is another important tool to protect users' privacy and to reduce the users' privacy concerns. As mentioned above, due to technological advance, short-form video platforms can constantly collect people's information anytime and anywhere, which means a huge amount of data are stored in the databases of platforms. Without a strong technical support, even platforms obey privacy policies, third parties are still great threats to user data security. To cope with this, short-form video platforms should establish a technical barrier system to multilevel protect user data. For example, upgrade information encryption technology, multiparty secure computing, and fully homomorphic encryption and other cutting-edge cryptography technology to solve the privacy problem reduce the possibility of irregular theft.
In general, the practical significance of this study is that the theoretical research findings can be applied to solve practical problems by deepening short-form video platform developers' understanding of their users' privacy concerns and behavioral intentions psychologically and behaviorally so as to help them recognize users' preferences more accurately when making marketing strategies, designing products, and providing services.
Research limitations and future research directions
On the one hand, although the multidimensional scale of privacy concerns has been developed through rigorous procedures in this study, the data are mainly from developing countries. Considering the possible differences in sample characteristics between developing and developed countries, this may lead to the differences of final scales. Therefore, it is suggested that developed countries can be used as samples to develop the privacy concerns scale in future research so as to compare the differences between developed countries and developing countries, and further promote the development and application of the privacy concerns scale.
On the other hand, even though the privacy concerns scale developed in this study has good convergence validity and reliability through item analysis, exploratory factor analysis, confirmatory factor analysis, discriminant validity, and content validity analysis, empirical research is still needed to further test its validity. Therefore, future research can test its antecedents and consequences through empirical research or the structural equation model to further verify its validity.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author/s.
Author contributions
Conceptualization and formal analysis: QW. Investigation: HW. Writing original draft: QW and HW. Writing—review and editing: QW, HW, and WZ. All the authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Social Science Fund of China, and the grand number is 21AZD118.
Conflict of interest
Author HW was employed by Beijing Rongqing Technology Group Co., Ltd.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Alge, B. J., Ballinger, G. A., Tangirala, S., and Oakley, J. L. (2006). information privacy in organizations: empowering creative and extra-role performance. J. Appl. Psychol. 91, 221–232. doi: 10.1037/0021-9010.91.1.221
Anderson, J. C., and Gerbing, D. W. (1998). Structural equation modeling in practice, a review and recommended two-step approach. Psychol. Bull. 10, 411–423. doi: 10.1037/0033-2909.103.3.411
Babbie, E. (2004). Laud humphreys and research ethics. Int J Sociol Soc Policy. 24, 12–19. doi: 10.1108/01443330410790849
Baker-Eveleth, L., Stone, R., and Eveleth, D. (2021). Understanding social media users' privacy-protection behaviors. Inf. Comput. Secur. 30, 324–345. doi: 10.1108/ICS-07-2021-0099
Barth, S., and Jong, M. D. (2017). The privacy paradox-investigating discrepancies between expressed privacy concerns and actual online behaviorasystematic literature review. Telemat. Inform. 34, 1038–1058. doi: 10.1016/j.tele.2017.04.013
Belanger, F., and Crossler, R. E. (2011). Privacy in the digital age: a review of information privacy research in information systems. MIS Q. 35, 1017–1042. doi: 10.1002/asi.21642
Belanger, F., and Crossler, R. E. (2019). Dealing with digital traces: understanding protective behaviors on mobile devices. Inform. Age 28. 34–49. doi: 10.1016/j.jsis.2018.11.002
Bollen, K. A., and Stine, R. A. (1992). Bootstrapping goodness-of-fit measures in structural equation models. Sociol. Methods Res. 21, 205–229. doi: 10.1177/0049124192021002004
Bright, L. F., Logan, K. L., and Hayoung, S. (2021). Social media fatigue and privacy: an exploration of antecedents to consumers' concerns regarding the security of their personal informationon social media platforms. J. Interact. Advert. 16, 1–16. doi: 10.1080/15252019.2022.2051097
Buchanan, T., Paine, C., Joinson, A. N., and Reips, U.-D. (2007). Development of measures of online privacy concern and protection for use on the Internet. J. Am. Soc. Inform. Sci. Technol. 58, 157–165. doi: 10.1002/ASI.V58:2
Campbell, A. J. (1997). Relationship marketing in consumer markets: a comparison of managerial and consumer attitudes about information privacy. J. Interact. Market. 11, 44–57. doi: 10.1002/(SICI)1522-7138(199722)11:33.0.CO;2-X
Castañeda, J. A., and Montoro, F. J. (2007). The effect of Internet general privacy concern on customer behavior. Electron. Comm. Res. 7, 117–141. doi: 10.1007/s10660-007-9000-y
Caudill, E. M., and Murphy, P. E. (2000). Consumer online privacy: legal and ethical issues. Public Policy Market. 19, 7–19. doi: 10.1509/jppm.19.1.7.16951
Cespedes, F. V., and Smith, H. J. (1993). Database marketing: new rules for policy and practice. Sloan Manag. Rev. 34, 7–22. doi: 10.1057/palgrave.jdm.3240098
Chen, K., and Rea, A. I. (2004). Protecting personal information online: a survey of user privacy concerns and control techniques. J. Comput. Inf. Syst. 44, 85–92. doi: 10.1080/08874417.2004.11647599
Chen, X. M. (2000). Qualitative Research Methods and Social Science Research. Beijing: Education Science.
Chen, X. M. (2010). Qualitative Research: Reflections and Comments. Chongqing: Chongqing University Press.
Choi, T. R., and Sung, Y. (2018). Instagram versus Snapchat: self-expression and privacy concern on social media. Telemat. Inform. 35, 2289–2298. doi: 10.1016/j.tele.2018.09.009
Cohen, R. L. (1987). Distributive justice: theory and research. Soc. Just. Res. 1, 19–40. doi: 10.1007/BF01049382
Corbin, J., and Strauss, A. (1990). Grounded theory research: procedures, canons and evaluative criteria. Zeitschrift für Soziologie. 3, 3–21. doi: 10.1515/zfsoz-1990-0602
Cranor, L. F., Reagle, J., and Ackerman, M. S. (1999). Beyond concern: understanding net users' attitudes about online privacy. Comput. Sci. 16, 47–70. doi: 10.48550/arXiv.cs/9904010
Culnan, M. J. (1993). How did they get my name? An exploratory investigation of consumer attitudes toward secondary information use. MIS Q. 17, 341–363. doi: 10.2307/249775
Culnan, M. J. (1995). Consumer awareness of name removal procedures: Implications for direct marketing. Direct Market. 9, 10–19. doi: 10.1002/dir.4000090204
Dhir, A., Torsheim, T., Pallesen, S., and Andreassen, C. S. (2017). Do online privacy concerns predict selfie behavior among adolescents, young adults and adults? Front. Psychol. 2017, 00815. doi: 10.3389/fpsyg.2017.00815
Dinev, T., and Hart, P. (2004). Internet privacy concerns and their antecedents-measurement validity and a regression model. Behav. Inform. Technol. 23, 413–422. doi: 10.1080/01449290410001715723
Dinev, T., and Hart, P. (2006a). Internet privacy concerns and social awareness as determinants of intention to transact. Int. J. Electron. Comm. 10, 7–29. doi: 10.2753/JEC1086-4415100201
Dinev, T., and Hart, P. (2006b). An extended privacy calculus model for e-commerce transactions. Inf. Syst. Res. 17, 61–80. doi: 10.1287/isre.1060.0080
Dogruel, L., Joeckel, S., and Vitak, J. (2017). The valuation of privacy premium features for smart phone apps: the influence of defaults and expert recommendations. Comput. Hum. Behav. 77, 230–239. doi: 10.1016/j.chb.2017.08.035
Earp, J. B., Antón, A. I., Aiman-Smith, L., and Stufflebeam, W. (2005). examining internet privacy policies within the context of user privacy values. IEEE Trans. Eng. Manag. 52, 227–237. doi: 10.1109/TEM.2005.844927
Eastlick, M. A., Lotz, S. L., and Warrington, P. (2006). Understanding online B-to-C relationships: an integrated model of privacy concerns, trust, and commitment. J. Bus. Res. 59, 877–886. doi: 10.1016/j.jbusres.2006.02.006
Emmert-Streib, F., Yli-Harja, O., and Dehmer, M. (2019).Utilizing social media data for psychoanalysis to study human personality. Front. Psychol. 10, 2596. doi: 10.3389/fpsyg.2019.02596
Fornell, C., and Larcker, D. F. (1981). Structural equation models with unobservable variables and measurement error: algebra and statistics. J. Market. Res. 18, 382–388.32. doi: 10.1177/002224378101800313
Foxman, E. R., and Paula, K. (1993). Information technology, marketing practice, and consumer privacy: ethical issues. J. Pub. Policy Market. 12, 106–119. doi: 10.1177/074391569501200111
Gaurav, B., and Fiona, F. N. (2022). Internet privacy concerns revisited: oversight from surveillance and right to be forgotten as new dimensions. Inform. Manag. 59, 3. doi: 10.1016/j.im.2022.103618
Gilliland, S. W. (1993). The perceived fairness of selection systems: an organizational justice perspective. Acad. Manag. Rev. 18, 694–734. doi: 10.5465/AMR.1993.9402210155
Goodwin, C. (1991). Privacy: recognition of a consumer right. J. Public Policy Market. 10, 149–166. doi: 10.1177/074391569101000111
Hair, J. F., Hult, G. T. M., Ringle, C. M., Sarstedt, M., and Thiele, K. O. (2017). Mirror, mirror on the wall: a comparative evaluation of composite-based structural equation modeling methods. J. Acad. Market. Sci. 45, 616–632. doi: 10.1007/s11747-017-0517-x
Herbert, C., Marschin, V., Erb, B., Meißner, D., Aufheimer, M., and Bösch, C. (2021). Are you willing to self-disclose for science? Effects of privacy awareness and trust in privacy on self-disclosure of personal and health data in online scientific studies—an experimental study. Front. Psychol. 2021, 763196. doi: 10.3389/fdata.2021.763196
Hinkin, T. R. (2005). Research in Organizations: Foundations and Methods in Inquiry-Scale Development Principles and Practices. San Francisco, CA: Berrett-Koehler Publishers.
Hoffman, D. L., and Novak, T. P. (1996). Marketing in hypermedia computer-mediated environments: conceptual foundations. Marketing 60, 50–68. doi: 10.1177/002224299606000304
Hong, W., and Thong, J. (2013). Internet privacy concerns: an integrated conceptualization and four empirical studies. MIS Q. 37, 275–298. doi: 10.2753/MIS0742-1222290410
Hu, L. T., and Bentler, P. M. (1999). Cutoff criteria for fit indexes in covariance structure analysis: conventional criteria versus new alternatives. Struct. Equ. Model. Multidiscip. J. 6, 1–55. doi: 10.1080/10705519909540118
Huang, H. Y., Chen, P. L., and Kuo, Y. C. (2017). Understanding the facilitators and inhibitors of individuals' social network site usage. Online Inform. Rev. 41, 85–101. doi: 10.1108/oir-10-2015-0319
Jackson, D. L., Gillaspy, J. A., and Purc-Stephenson, R. (2009). Reporting practices in confirmatory factor analysis: an overview and some recommendations. Psychol. Methods 14, 6–23. doi: 10.1037/a0014694
Janda, S. (1998). A beginner's guide to structural equation modeling. Struct. Equ. Modeling. 5, 104–105. doi: 10.1080/10705519809540093
Jones, M. G. (1991). Privacy: a significant marketing issue for the 1990s. J. Public Policy Market. 10, 133–148. doi: 10.1177/074391569101000110
Jozani, M., Ayaburi, E., Ko, M., and Choo, K.-K.-R. (2020). Privacy concerns and benefits of engagement with social media-enabled apps: a privacy calculus perspective. Comput. Hum. Behav. 107, 106260. doi: 10.1016/j.chb.2020.106260
Kerlinger, F. N. (1986). Foundations of Behavioral Research, 3rd Edn. New York, NY: Holt, Rinehart and Winston.
Kline, R. B. (2011). Principles And Practice of Structural Equation Modeling, 3rd Edn. New York, NY: Guilford.
Lanier, C. D., and Saini, A. (2008). Understanding consumer privacy: A review and future directions. Acad. Mark. Sci. Rev. 12, 1–45. doi: 10.1002/dir.10071
Lederer, A. L., and Sethi, V. (1991). Critical dimensions of strategic information systems planning. Decis. Sci. 22, 104–119. doi: 10.1111/j.1540-5915.1991.tb01265.x
Loiacono, E. T. (2015). Self-disclosure behavior on social networking web sites. Int. J. Electron. Comm. 19, 66–94. doi: 10.1080/10864415.2015.979479
Mahmoodi, J., Curdová, J., Henking, C., Kunz, M., Matić, K., Mohr, P., et al. (2018). Internet users' valuation of enhanced data protection on social media: which aspects of privacy are worth the most? Front. Psychol. 2018, 01516. doi: 10.3389/fpsyg.2018.01516
Malhotra, N. K., Kim, S. S., and Agarwal, J. (2004). Internet users' information privacy concerns (IUIPC): the construct, the scale, and a causal model. Inf. Syst. Res. 15, 336–355. doi: 10.1287/isre.1040.0032
Melinda, L., Korzaan, K., and Boswell, T. (2008). The influence of personality traits and information privacy concerns on behavioral intentions. J. Comput. Inf. Syst. 48, 15–24. doi: 10.1002/pssa.200622474
Milne, G. R., and Gordon, M. E. (1993). Direct mail privacyefficiency trade-offs within an implied social contract framework. J. Public Policy Market. 12, 206–215. doi: 10.1177/074391569101200206
Mwesiumo, D., Halpern, N., Budd, T., Suau-Sanchez, P., and Bråthen, S. (2021). An exploratory and confirmatory composite analysis of a scale for measuring privacy concerns. J. Bus. Res. 136, 63–75. doi: 10.1016/j.jbusres.2021.07.027
Nowak, G. J., and Phelps, J. (2010). Understanding privacy concerns. An assessment of consumers' information-related knowledge and beliefs. J. Interact. Market. 6, 28–39. doi: 10.1002/dir.4000060407
Pavlou, P. A., and Xue, L. Y. (2007). Understanding and mitigating uncertainty in online exchange relationships: a principal-agent perspective. MIS Q. 31, 105–136. doi: 10.2307/25148783
Phelps, J., and Ferrell, N. E. (2000). Privacy and ethical issues indatabase/interactive marketing and public policy || privacy concerns and consumer willingness to provide personal information. J. Public Policy Mark. 19, 27–41. doi: 10.2307/30000485
Qi, K. P., and Liu, Z. Z. (2018). A study on privacy concerns of chinese public and its influencing factors. Sci. Soc. 8, 36–58. doi: 10.1109/MSIE.2011.5707555
Rifon, N. J., LaRose, R., and Choi, S. M. (2005). Your privacy is sealed: effects of web privacy seals on trust and personal disclosures. J. Consu. Affairs. 39, 339–362. doi: 10.1111/j.17456606.2005.00018.x
Sheehan, K. B., and Hoy, M. G. (2000). Dimensions of privacy concern among online consumers. J. Public Policy Market. 19,62–73. doi: 10.1509/jppm.19.1.62.16949
Smith, H. J., Dinev, T., and Xu, H. (2011). Information privacy research: an interdisciplinary review. MIS Q. 35, 989–1016. doi: 10.1007/s11575-011-0104-1
Smith, H. J., Milberg, S. J., and Burke, S. J. (1996). Information privacy: measuring individuals' concerns about organizational practices. MIS Q. 20, 167–196. doi: 10.2307/249477
Son, J. Y., and Kim, S. S. (2008). Internet users' information privacy-protective responses: a taxonomy and a nomological model. MIS Q. 32, 503–529. doi: 10.1128/AAC.02814-14
Stewart, K. A., and Segars, A. H. (2002). An empirical examination of the concern for information privacy instrument. Inform. Syst. Res. 13, 36–49. doi: 10.1287/isre.13.1.36.97
Strauss, A. L., and Corbin, J. M. (1990). Grounded Theory Procedures and Techniques. Newsbury Park, CA: Sage.
Tan, X., Qin, L., Kim, Y., and Hsu, J. (2013). Impact of privacy concern in social networking web sites. Internet Res. 22, 211-233. doi: 10.1108/10662241211214575
Thibaut, J., and Walker, L. (1975). Procedural Justice: A Psychological Analysis. Hillsdale, NJ: Erlbaum.
Vallina-Rodriguez, N., Sundaresan, S., Razaghpanah, A., Nithyanand, R., Allman, M., Kreibich, C., et al. (2016). Tracking the trackers: towards understanding the mobile advertising and tracking ecosystem. 7, 19–31. doi: 10.48550/arXiv.1609.07190
Vidmar, N., and David, H. F. (1985). Concern for personal privacy in an electronic age. J. Commun. 35, 91–103. doi: 10.1111/j.1460-2466.1985.tb02236.x
Wang, H. W., Zhou, M., and He, S. Y. (2012). Empirical research of individuals' intention to provide privacy information online. Syst. Eng.-Theory Pract. 32, 2186–2197. doi: 10.3969/j.issn.1000-6788.2012.10.009
Wang, Q. Q., Yang, M. S., and Zhang, W. S. (2021). Accessing the influence of perceived value on social attachment: developing country perspective. Front. Psychol. 2021, 760774. doi: 10.3389/fpsyg.2021.760774
Wang, W., and Wu, J. N. (2021). Short video platforms and local community building in China. Int. J. Commun. 15, 3269–3291. doi: 10.1080/02529200801921051
Warkentin, M., Johnston, A. C., Walden, E., and Straub, D. W. (2016). Neural correlates of protection motivation for secure IT behaviors: an fMRI examination. J. Assoc. Inform. Syst. 17, 194–215. 0.17705/1JAIS.00424
Warren, C., Batra, R., Loureiro, S. M. C., and Bagozzi, R. P. (2019). Brand coolness. J. Mark. 83, 36–56. doi: 10.1177/0022242919857698
Watat, J. K., and Jonathan, G. M. (2020). “The Influence of Privacy Concerns on Intention to Use Social Media,” in Conference of the Association-for-Information-Systems (AMCIS).
Weible, R. J. (1993). Privacy and Data: An Empirical Study of the Influence and Types and Data and Situational Context upon Privacy Perceptions (doctoral dissertation). Department of Business Administration, Mississippi State University.
Westin, A. F. (1968). Privacy and freedom. Washington Lee Law Rev. 25, 166–170. doi: 10.2307/2092293
Wottrich, V. M., Van, R., and Smit, E. G. (2019). App users unwittingly in the spotlight: a model of privacy protection in mobile apps. J. Consum. Affairs 53, 1056–1083. doi: 10.1111/joca.12218
Yang, M., Cao, C. Y., and Liao, H. L. (2018). “Social media privacy concerns and self presentation,” in International Joint Conference on Information, Media and Engineering (ICIME), 82–86.
Yang, M. S., Hu, S. G., Kpandika, B. E., and Liu, L. (2021a). Effects of social attachment on social media continuous usage intention: the mediating role of affective commitment. Hum. Syst. Manag. 40, 619–631. doi: 10.3233/HSM-201057
Yang, M. S., Suanpong, K., Ruangkanjanases, A., Yu, W., and Xu, H. (2022). Development and Validity test of social attachment multidimensional scale. Front. Psychol. 12, 757777. doi: 10.3389/fpsyg.2021.757777
Yang, M. S., Zhang, W. S., Ruangkanjanases, A., and Zhang, Y. (2021b). Understanding the mechanism of social attachment role in social media: a qualitative analysis. Front. Psychol. 12, 720880. doi: 10.3389/fpsyg.2021.720880
Yang, S., Wang, Y., and Wang, K. L. (2008). The measurement of online users' privacy concernin China context. J. Intell. 10, 3–7. doi: 10.3969/j.issn.1002-1965.2008.10.001
Yang, W., and Ning, H. (2021). Knowledge graph technology application in Chinese SSCI: an example of short videos research. J. Librarianship Inform. Sci. 28, 23–46. doi: 10.1177/09610006211063201
Keywords: privacy concerns, collection concerns, awareness concerns, usage concerns, short-form video platforms
Citation: Wang Q, Zhang W and Wang H (2022) Privacy concerns toward short-form video platforms: Scale development and validation. Front. Psychol. 13:954964. doi: 10.3389/fpsyg.2022.954964
Received: 27 May 2022; Accepted: 04 July 2022;
Published: 05 August 2022.
Edited by:
Taqwa Hariguna, Amikom University Purwokerto, IndonesiaReviewed by:
Ming Li, Beijing University of Chemical Technology, ChinaAndi Muhammad Sadat, Jakarta State University, Indonesia
Copyright © 2022 Wang, Zhang and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Wensong Zhang, d3N6aGFuQGJqdHUuZWR1LmNu; Haikun Wang, amFzb25rMTIxOEBzb2h1LmNvbQ==
 Qingqing Wang
Qingqing Wang Wensong Zhang1*
Wensong Zhang1*