- School of Business Administration and Tourism Management, Yunnan University, Kunming, China
One heated argument in recent years concerns whether requiring real name supervision on social media will inhibit users’ participation in discoursing online speech. The current study explores the impact of identification, perceived anonymity, perceived risk, and information credibility on participating in discussions on moral/ethical violation events on social network sites (SNS) in China. In this study, we constructed a model based on the literature and tested it on a sample of 218 frequent SNS users. The results demonstrate the influence of identification and perception of anonymity: although the relationship between the two factors is negative, both are conducive to participation in discussion on moral/ethical violation topics, and information credibility also has a positive impact. The results confirmed the significance of risk perception on comments posted about moral/ethical violation. Our results have reference value for identity management and internet governance. Policies regarding users’ real names on the internet need to take into account the reliability of the identity authentication mechanism, as well as netizens’ perceptions of privacy about their identity and the necessity of guaranteeing content and information reliability online. We also offer some suggestions for future research, with a special emphasis on applicability to different cultures, contexts, and social networking sites.
Introduction
The complex integration of the internet and the real world means that in both the West and China, cyberspace has become the most convenient place for free expression, which is constrained by social norms and conformity (Lipschultz, 2018). Online public opinion is becoming the mainstream public opinion domain in China (Yu, 2017). China arguably presents an interesting case study on social networking sites (SNS) because it limits social media communication on non-domestic sites, establishing a microcosm of SNS (Sullivan, 2014). The expression of online public opinion is rooted in the social and cultural background of real-life society. In Chinese culture, there has always been an emphasis on “denying self and returning to propriety”, personal behaviors should be “gentle, modest and courteous” and expressions should be humble and low-key (Chen, 2014). In interpersonal communication, a superficial balance of relationship should be pursued, and telling the truth should be avoided to prevent harming interpersonal relationships (Zhai, 1999). In fact, culture is shaped by reality. When real lives are mapped onto virtual cyberspace in a hidden form, this principle of superficial balance is no longer important (Chen, 2018). Since Chinese people lack freedom of expression of their real views with their real-life social contacts, online anonymity is of greater importance to Chinese people compared with those from the West. In an interview survey conducted in 2017, 79.1% of 48 respondents said that they assume different identities online, which is reflected in using different SNS accounts (Chen, 2018).
In the most recent couple of decades, many researchers have regarded anonymity as directly enabling free expression on the internet as well as being the root cause of anomie (Nissenbaum, 1999; Davenport, 2002; Kim et al., 2011; Salanova et al., 2013; Stroud, 2014). The system of using real names online, which is considered a way of enhancing oversight of cyberspace and regulating the behavior of netizens, has been gradually established and improved with the development of China’s internet governance (Lin, 2010; Liu, 2013).
In 2015, the State Internet Information Office of China issued a regulation named Rules on Account Name of Internet Users, which requires all users to submit real-identity registration information when using the internet. With the precondition that internet regulators can confirm users’ identities, users have the right to use virtual names in online public speech spaces, which should be respected (Chen and Li, 2013). The real-name system is a mechanism that enables an individual’s name to be mapped to that person’s identity on social media. Users must provide information on their real personal identity when engaging in online activities, so as to establish a consistent relationship between their online and offline identities, enabling a confirmatory mechanism that links the rights, obligations, and interests of individuals’ words and deeds online and in real life (Chen and Li, 2013).
China’s enforcement of the online real-name registration system sparked widespread and fierce disputes, focused on its impact on netizens’ freedom of expression. Supporters of the regulation argued that the system is conducive to creating a credible online speech environment and encouraging people to be responsible for their own speech. For those who are willing to speak frankly, real-name speech can also improve personal credibility and give weight to their words (Huang and Zhang, 2010). Opponents contend that the real-name system undermines the traditional values of equality, freedom, and openness on the internet, discourages internet users from participation in politics and scrutinizing government, and poses a covert threat to netizens’ right of “freedom of expression” (Zhang and Lu, 2010).
Public concern about things that affect the majority of society is an important force in implementing oversight and promoting social progress. In China, Weibo and WeChat, with 500 million and 1 billion active users respectively at the beginning of 2020, have become the two most important SNS for people to express public opinion, offering different kinds of platforms for open and critical debate (Rauchfleisch and Schäfer, 2015).
In recent years, China has experienced many public opinion incidents online, with some incidents (both online and offline) sparking a great deal of online reaction and widespread discussion. The vast quantity of views freely expressed online by the public on specific topics has promoted social regulation offline, including efforts to promote the optimization of the social system and to combat corruption (Liebman, 2011). This plays an important role in social justice and promoting reform of the system of governance in the real world. The ability to trace a person’s identity magnifies the risk of individual participation in exposing social problems, including interpersonal risks, moral risks, and even security risks, and this is an important reason for interrogating the online real-name system. However, to date studies on identifiability online have failed to explore this aspect. Therefore, the first research question to be tested in the current study is:
RQ1: Does the traceability of network identity information inhibit public participation in discussions on moral/ethical violation topics by internet users in China?
Anonymity in cyberspace is an important way of protecting private information (Brazier et al., 2004; Rainie et al., 2013) and is conducive to the construction of self-image (Lin and Utz, 2017). The emergence of new cyber applications has led to a heated debate over the advantages and disadvantages of anonymity in cyberspace (Chen et al., 2016, 2019a, b; Christopherson, 2007; Lapidot-Lefler and Barak, 2012; Scott and Orlikowski, 2014; Fox et al., 2015; Jardine, 2015; Levontin and Yom-Tov, 2017). A series of research studies have confirmed that the perception of anonymity has different impacts on behavior in different online environments (Jessup et al., 1990; Joinson, 2001; Reinig and Mejias, 2004; Lapidot-Lefler and Barak, 2012; Yoon and Rolland, 2012; Hsieh and Luarn, 2014).
In the current cyberspace environment, absolute anonymity does not exist (Bodle, 2013). The issue of anonymity is often the focus of research on free expression (Akdeniz, 2002). SNS, especially those in which users tend to use real names, such as Facebook and WeChat, provide users with the freedom to make choices; the social connections built and maintained by these platforms may reduce the perception of anonymity. The positive impact derived from a perception of anonymity on positive self-disclosure has been analyzed in detail (Chen et al., 2016). Positive self-disclosure relates to the construction of self-image. However, participation in the discussion of topics that violate ethics is related to social responsibilities. Everyone has the responsibility to assume the ethical responsibilities of the media (Boeyink and Borden, 2010). For Chinese who value harmony of interpersonal relationship and the dignity, online anonymity has become a “veil”, creating conditions whereby they can express their opinions freely. Anonymity in cyberspace is of great significance for Chinese netizens to express free speech about their true views. There is a lack of analysis in the current literature on the impact of perception of anonymity on users’ participation in assuming public social responsibilities. Therefore, the current study attempts to answer the following research question based on the SNS environment in China:
RQ2: Does the perception of anonymity on the internet help drive netizens’ public participation in discussions on moral/ethical violation topics in China?
Based on the understanding of the issues described above, we synthesized the existing literature to build a theoretical model, as well as referring to the theories of the social identity model of deindividuation effects (SIDE) and Borden’s communication ethical rules. Empirical research was conducted to test the hypothesis and theoretical model. The current study makes two principal contributions to the literature. First, it reveals that identification and perception of anonymity are opposite aspects of the influence mechanism of online participation in discussions on moral/ethical violation topics, and encouraging such participation needs to take into account underlying aspects of identification and the psychological perception of anonymity at the surface. Second, it confirms the role of risk perception and information credibility in participation in discussions on moral/ethical violation topics.
The remainder of the paper consists of the following sections: Section 2 reviews the theoretical foundation, and Section 3 proposes our research model and hypotheses. Section 4 explains the methodology, while Section 5 presents the results and related analysis. Section 6 discusses the results of the current study, together with the theoretical and practical limitations and potential avenues and implications for future research.
Theoretical Foundation and Literature Review
Cyber Anonymity and Online Public Opinion
Anonymity means a lack of identification of one’s real identity (Marx, 1999). As a result of the integration between the internet and the real world, identification of users’ real identity has become the basis for internet services and governance in China (Chen, 2018). According to the social identity model of deindividuation effects (SIDE), in the context of anonymous identities, people show a behavioral tendency to obey a group norm due to the prominence of an individual identity (Vilanova et al., 2017). The effects of online anonymity shown in the SIDE model are reflected in personalization, misconduct, and false information, which are related to the dark side of cyberspace (Fox and Moreland, 2015). However, anonymity in cyber-based communication may not necessarily lead to antisocial behavior (Christopherson, 2007). In some scenarios, anonymity enhances social processes related to group identity in online communication (Spears, 2017). On SNS, anonymity can also play a positive role in information exchange (Yoon and Rolland, 2012; Chen et al., 2016).
In the 1990s, use of cyber-based communication technology facilitated an anonymous communication environment, but this positive outcome is no longer the case (Chen et al., 2016). This is because anonymity is now seen by some as dangerous due to the following factors: issues in the protection of business transaction security (Chen et al., 2019a); government oversight and control; concerns about intellectual property; national and international legal implications; and the use of identity management technology (Froomkin, 2015). In SNS, user identification takes complicated forms, with complex and diversified functions and methods of interpersonal interactions.
The importance of online opinion, also called online word of mouth (e-WOM), has been confirmed (Goldsmith and Horowitz, 2006; Weeks et al., 2017). Despite the increasing disappearance of anonymity on the internet, it is still an important “safety valve” for the oppressed, dissidents, and whistleblowers to speak freely (Froomkin, 2015). This ability often comes from the psychological perception that they can engage in free speech without fear of the consequences (Chen et al., 2016). Therefore, online opinion makers can continue to participate, innovate, and explore topics and issues with a high degree of self-cognition. They boast stronger computer skills and use the internet more frequently (Lyons and Henderson, 2005).
Many studies have demonstrated a positive relationship between internet use, online speech, and political participation (Shah et al., 2005; Van den Eijnden et al., 2008; Valenzuela, 2013; Boulianne, 2015). In China, although government censorship inhibits people’s willingness to voice their opinions to some extent, thanks to its loose network structure, which provide users with flexible expression forms and places to disclose opinions, the internet has still led to progressive changes in Chinese society (Shen et al., 2009). Public opinions on the internet affect the real world through users’ discussion of specific events and dissemination of information (Yue et al., 2017). The main participants in cyberspace include stakeholders and the public (Zhang et al., 2015). The methods of participation include providing information, making comments, and involvement in decision-making or particular behaviors. The results of participation affect public decision-making or governance behaviors. Researchers have studied the impact of cyber anonymity on self-disclosure and information sharing (Yoon and Rolland, 2012; Chen et al., 2016, b).
China is in a social transformation period, bringing a high degree of uncertainty to people’s lives. The prevalent practice of concealing their true views for self-protection makes Chinese netizens present more complex mentalities and more diversified modes of behavior than before the construction of cyber identity (Chen, 2018). This also suggests that anonymous expression online plays a crucial role in alleviating potential pressure in real society and relieving the latent contradictions and conflicts. However, no empirical research has been conducted on the impact of a lack of anonymity on expression of public opinion on moral/ethical matters. The exploration of this impact mechanism is an important basis for establishing identity management and carrying out governance in cyberspace.
Participation in Moral/Ethical Oversight
The development of global media brings urgency to intercultural communications on ethics-related topics (Borden, 2016). Cyberspace transfers the function of traditional media and its societal influence from professional journalists to every netizen. Every speaker in cyberspace has the function of the media to some extent. Therefore, the discussion of ethical and moral responsibility in journalism theory provides an important reference point for individuals’ posting information and sharing behavior on SNS. From a moral/ethical standpoint, journalists have to be clearly aware of what they are and what they are not, and whether they are to stand in favor of some things and against others (Borden, 2007). Media ethicist Elliott (1986) suggests that three levels of responsibilities provide the foundations for moral excellence in journalism: general responsibilities, particular responsibilities, and individuals’ personal responsibilities.
Media participants should follow three ethical rules: truth telling, privacy, and fairness (Boeyink and Borden, 2010). In some controversial ethical violations, the three principles may come into conflict (Boeyink and Borden, 2010). However, in some cases involving ethical and moral principles in which people reach a consensus, the behavior of paying attention to and getting involved in the discussion itself is in compliance with the above three principles. Moral excellence consists of performing your ethical responsibilities well: all of us have moral responsibilities, such as to be truthful to avoid harming others and to keep our promises, so called general responsibilities, which matter in everyone’s lives. These responsibilities should give individuals the power to supervise and condemn those behaviors that violate morality and ethics and endanger the foundation of human existence.
In cyberspace, netizens participate in discussion of an event to supervise and condemn behavior which violates norms of ethics and morality (Repnikova, 2017). The power of moral supervision plays an important role in aspects such as maintaining social justice, promoting improvements in the social system, and restraining corruption (Liebman, 2011). Even though our individual actions are constrained by general and particular responsibilities, media participants have to retain autonomy as moral agents (Elliott, 1986). In particular, when events occur that violate the universal morality of humanity, the involvement of people in discussion and information sharing in cyberspace strengthens the argument for justice; thus, such participation plays an important role in maintaining universal ethics and the morality of the social system. The current study also discusses how the concealment and revelation of individuals’ real identity in cyberspace affect users’ involvement in moral supervision.
Perceived Risk and Information Credibility Sources
Studies of risk perception examine the judgments that people make when they are asked to characterize and evaluate hazardous activities and technologies (Slovic, 1987). Perceived risk has been conceptualized in terms of the expected negative utility of particular actions (Peter and Ryan, 1976). The impact of perceived risk on behavior has been confirmed in online research contexts, including information sharing and control (Gerlach et al., 2015; Hajli and Lin, 2016) and adoption behaviors (Featherman and Pavlou, 2003; Horst et al., 2007; Martins et al., 2014; van Winsen et al., 2016). Perceived risk reduces users’ perceptions of value (Snoj et al., 2004; Chang and Tseng, 2013) and destroys trust (Slovic, 1993). However, the influence of perceived risk on the expression of ethical views has been neglected in current research.
Perceived risk has an impact on people’s moral judgments Subjects in a high-risk treatment group exhibited significantly harsher ethical judgments than those in a low-risk treatment group (Cherry and Fraedrich, 2002). Reputation, a sense of belonging, and satisfaction from helping others are significantly related to e-WOM intention (Cheung and Lee, 2012). Paying attention to moral views and participating in social media posts and sharing this kind of information is of concern for the collective interest (Earle and Siegrist, 2006). The discussion of moral issues online is related to the altruistic punishment mechanism of human behavior, which holds that individuals voluntarily take risks and pay costs for punishing people who violate social norms, and this plays an important role in the evolution of social cooperation (Fehr and Fischbacher, 2004; Boyd et al., 2010).
The framing of risk depends on the media used to perceive it (Ericson and Doyle, 2003). In seeking information, people rely on information sources to build trust, which is in play whenever users exchange information, and the information source—the trusted party—may have a moral responsibility to an information seeker (Hertzum et al., 2002). Information credibility has become an important topic as the internet has become increasingly ubiquitous (Kelton et al., 2008). The influence of trust in digital information has been confirmed as a key mediating variable between information quality and information use (Pan and Chiou, 2011), but the influence of information credibility on information related to discussions on moral/ethical violation topics needs further clarification.
Research Model and Hypothesis
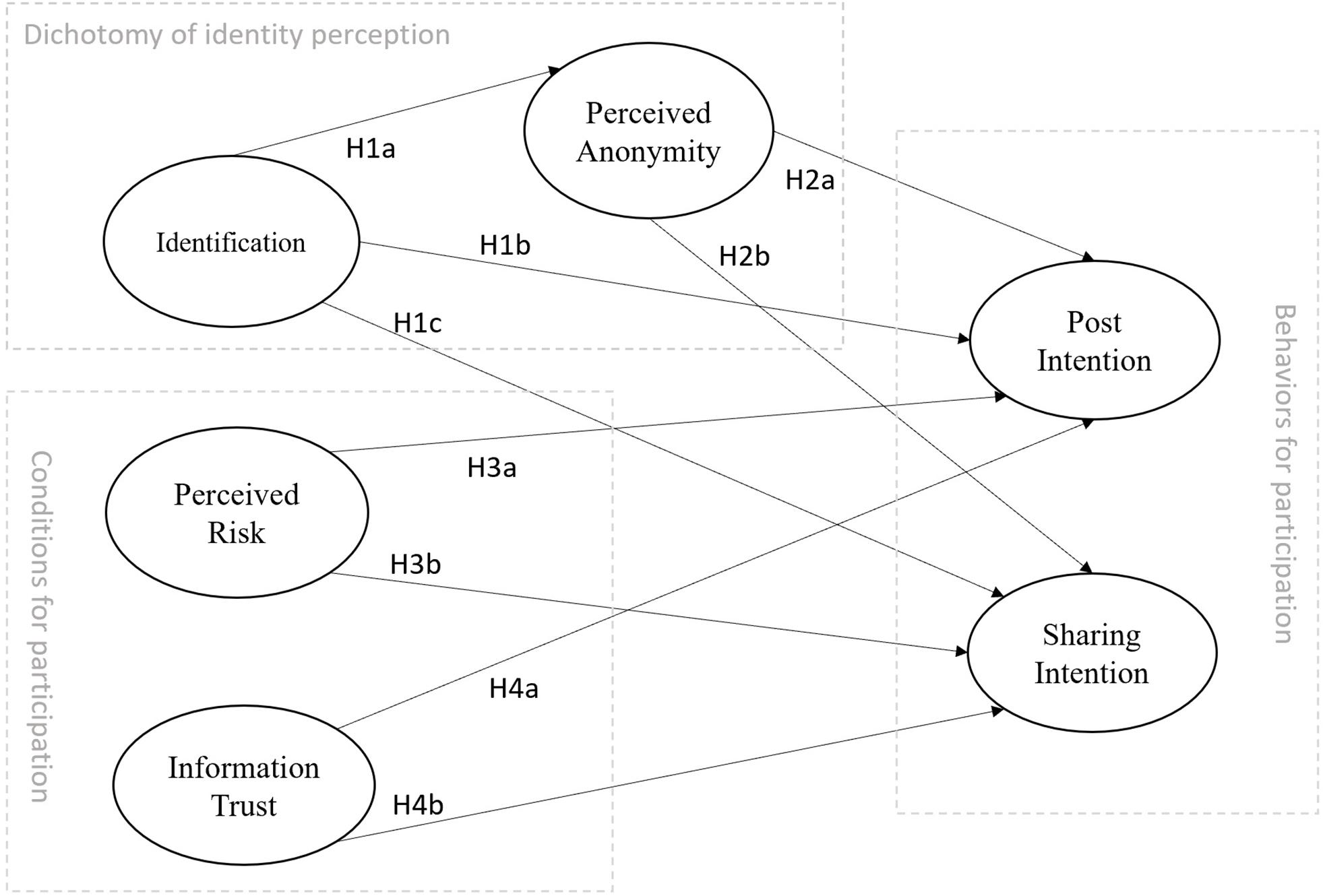
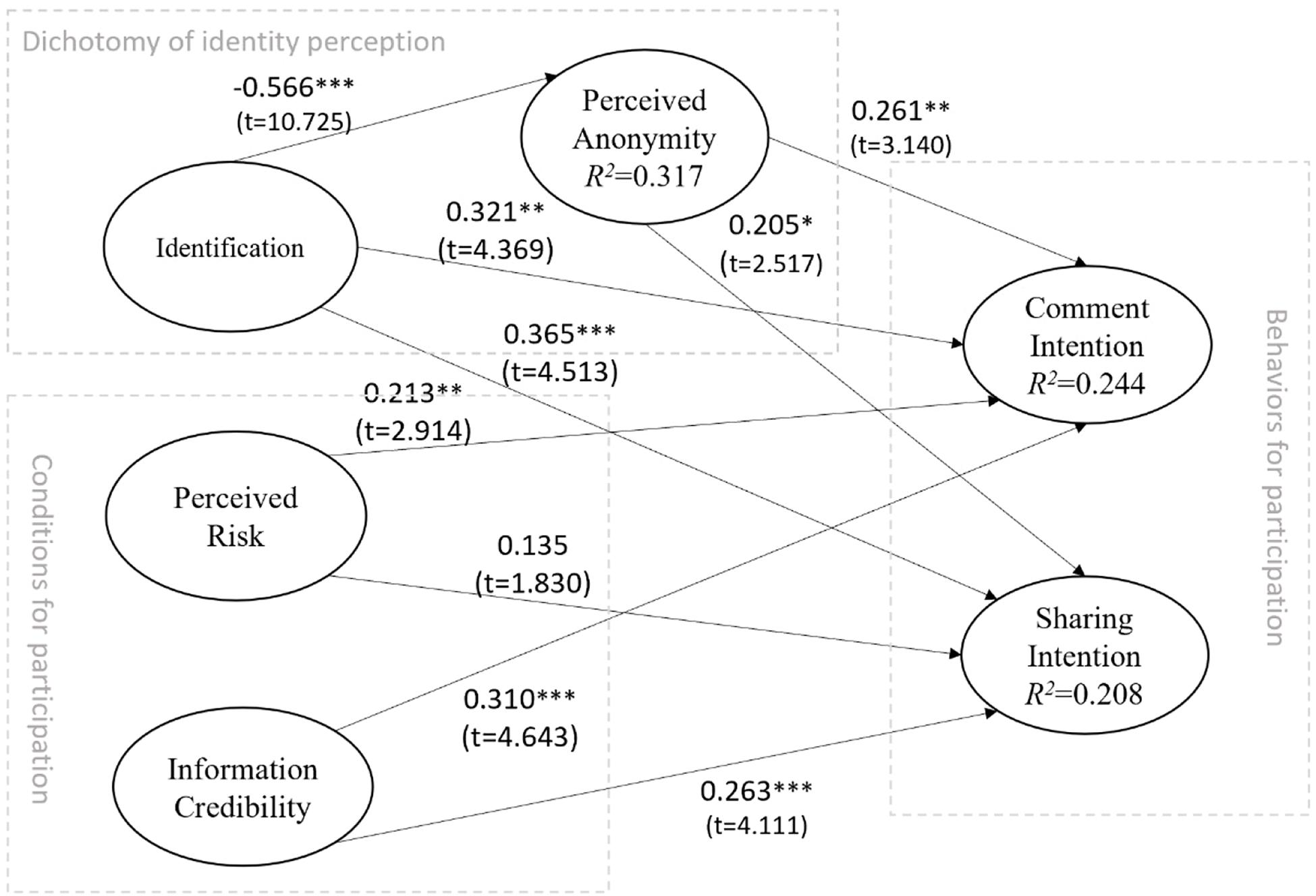
The current study constructs a model to examine how the factors of identity perception, real names, and perceived anonymity affect the intention to participate in SNS discussions on moral/ethical issues in China. In addition, the current study also explores the influence of risk perception and information credibility on participation in social media discussions on moral issues in China. The research model is depicted in Figure 1.
Identification and Anonymity on Social Networking Sites
User identifiability and perception of anonymity are not two sides of the same factor. Although they have opposing properties, they are two different factors. The ability to identify internet users refers to the process and the potential for identifying the true identity of users in cyberspace; this is not just a legal concept but also a technical means of identity detection with the help of publicly available methods (Krausová, 2009). In cyberspace, user identifiability is represented by the richness of information in terms of whether there are clues to determine a user’s real identity (Chen et al., 2019a). Identifiability is objective, whereas perceptual anonymity is subjective and is the psychological perception of the nature of the subject. Previous research has confirmed that identity has a significantly negative impact on perceptual anonymity on various online social media platforms (Chen et al., 2016, 2019a, b). The relationship between these two factors should be the same in monitoring and participating in discussions on moral/ethical violation topics on online social media. Thus, we hypothesize that:
H1a: User identification has a negative impact on their perception of anonymity in discussing moral/ethical violation topics on Chinese SNS.
Identity is perceived as a social process that aligns with internal self-identification and external identity classification (Jenkins, 2014). Identification and self-efficacy are closely intertwined, and the connection between social identity and self-efficacy is further supported by social identity theory (Guan and So, 2016). Four factors—performance accomplishments, vicarious experience, verbal persuasion, and emotional arousal—contribute to a boost in self-efficacy (Bandura, 1977). Social influence and perceived control will positively impact self-disclosure in SNS (Cheung et al., 2015). External factors, such as environment and information input, appear to affect self-efficacy through their influence on internal variables, such as motivation, ability, or performance strategies (Gist and Mitchell, 1992). The identity construction of the user depends on the creation and sharing of information. Attention to and discussion of online public opinion are also a way for the user to construct his or her own identity. The more active the user is on online social media, the deeper the recognition of the user’s online identity and thus the greater enthusiasm and self-efficacy the user has for participating in discussion on the topic. Thus, we hypothesize that:
H1b: User identification has a positive impact on comment intention in discussing moral/ethical violation topics on Chinese SNS.
H1c: User identification has a positive impact on sharing intention in discussing moral/ethical violation topics on Chinese SNS.
Perception of anonymity refers to the indiscernibility of the identity of the user, which leads to self-awareness of identity anonymity, that is, that one cannot be tracked in cyberspace (Kang et al., 2013). In an anonymous environment, social bonds are weaker, and social norms tend to be enforced more aggressively (Wright, 2014). The relationship between perception of online anonymity and behavior depends on the specific communication context (Joinson, 2007). In group discussions, it has been found that users who perceived anonymity were more likely than identified users to embellish the opinions of others (Jessup et al., 1990). For users, circumventing the possibility of authentication can protect privacy (Brennan et al., 2012). Although online anonymity introduces uncertainty into interpersonal interactions, it also reduces risks in online privacy and security (Rainie et al., 2013). According to the SIDE theory, within an anonymous context, people tend to comply with collective norms. Following the argument that general moral/ethical principles lead to collective behavior and consensus (Boeyink and Borden, 2010), the SIDE effect will promote the individual’s obedience to collective behaviors. In discussion and online decision-making on certain sensitive topics, online anonymity increases behavioral contributions and effective suggestions (Jessup et al., 1990). In addition, research on perception of anonymity in the use of online social media for information sharing found that perception of anonymity has a positive effect on self-disclosure (Chen et al., 2016). Thus, we hypothesize that:
H2a: Users’ perceived anonymity has a positive impact on comment intention in discussing moral/ethical violation topics on Chinese SNS.
H2b: Users’ perceived anonymity has a positive impact on sharing intention in discussing moral/ethical violation topics on Chinese SNS.
Perceived Risks Online
Perceived risk has been conceptualized in terms of the expected negative utility of actions (Peter and Ryan, 1976). Risk discourse is redolent with the ideologies of mortality, danger, and divine retribution (Lupton, 1993). Participation in familiar activities has a tendency to minimize the probability of bad outcomes (Douglas, 2013). Decisions about risk as moral decisions are made in the context of uncertainty (Adams, 2003). However, risk perception has different influence mechanisms in play in discussions on moral/ethical violation topics. The increase in risk entails an attendant enhancement of new moral responsibilities at multiple levels in a society (Ericson and Doyle, 2003). From a moral/ethical standpoint, the media participant has to be clearly aware of their responsibilities (Borden, 2007); in general moral/ethical events in particular, especially the event challenging the basic value and living of human being. the basic principles should be clear (Elliott, 1986). Three ethical rules—truth telling, privacy, and fairness—may come into conflict (Boeyink and Borden, 2010), and should be taken in consideration. Even though our individual actions are constrained by general and particular responsibilities, media participants have to retain autonomy as moral agents (Elliott, 1986). We believe that perception of risk in cyberspace should have a positive impact on participation in discussions on moral/ethical violation topics. Thus, we hypothesize that:
H3a: Users’ perceived risk has a positive impact on comment intention in discussing moral/ethical violation topics on Chinese SNS.
H3b: Users’ perceived risk has a positive impact on sharing intention in discussing moral/ethical violation topics on Chinese SNS.
Information Credibility
Trust in technology is constructed in the same way as trust in people (McKnight, 2005). Information credibility is a descriptive factor of perceived information quality which influences information exchange. Information quality during an exchange can help build trust and reduce perceived exchange risk (Nicolaou and McKnight, 2006). External factors, such as environment and information input, appear to affect self-efficacy through their influence on internal variables (Gist and Mitchell, 1992). Self-efficacy factors, such as perceived performance, have been confirmed as having an adverse impact on the adoption of e-services (Featherman and Pavlou, 2003), and are also positively related to a consumer’s trust expectation (Hong, 2015). The perceived trustworthiness of information determines the level of confidence developed by the user and the corresponding willingness to use the information (Kelton et al., 2008). Research has also determined the importance of trust in forecasted information sharing in television, newspapers, and online news (Kiousis, 2001), and supply chains (Özer et al., 2011). The source of information is an important factor in considering information credibility (Lucassen and Schraagen, 2010). Morality−relevant information provides the check for value similarity and generates trust (Earle and Siegrist, 2006). The impact of trust on forecasted information sharing has been confirmed (Zimmer et al., 2010; Ha and Ahn, 2011; Özer et al., 2011). Thus, we hypothesize that:
H4a: Users’ information credibility has a positive impact on their comment intention in discussing moral/ethical violation topics on Chinese SNS.
H4b: Users’ information credibility has a positive impact on sharing intention in discussing moral/ethical violation topics on Chinese SNS.
Methodology
The internet is an ideal medium for collecting data from different groups (Koch and Emrey, 2001). The current study focuses on Chinese SNS users’ participation in discussions on moral/ethical topics. In China, WeChat and Weibo are the most popular online social platforms that people use to express their opinions (Hou et al., 2018). According to the Social Global Web Index’s flagship 2018 report on the latest trends in social media, Facebook is the world’s largest SNS with more than 2.6 billion users, WeChat is ranked fourteenth, and Weibo is ranked eighteenth; the latter are also the only two Chinese social media platforms listed in the global top 20 (Global Web Index, 2018). At the end of 2019, WeChat had over 1 billion active users around the world. Weibo, which has more than 500 million active users, provides a virtual public space for users to share their opinions with their connected peers, making it the most influential opinion platform in China; this makes it a suitable arena for our research on participation in discussions on moral/ethical topics. To validate our hypotheses, we conducted a survey on the use of WeChat and Weibo by Chinese users.
The current research is based on a heated event which provoked discussion all over the world, in which a scientist named He Jiankui announced his work on editing the genes of a fetus. Scientists and authoritative academic institutions from different countries gave their opinions, arguing that He Jiankui had seriously violated academic morals and the code of conduct. What he did also caused an outcry in the international community (Cyranoski and Ledford, 2018; Normile, 2018). His behavior did not only violate scientific ethics, but also had the possibility of polluting the human gene pool and posed a threat to the future of humanity. It was noted that the ethical infractions in this work are among the most egregious that have been recorded in modern medical history since the Second World War (Kuersten and Wexler, 2019). This ethical and moral violation event is significant for the whole of humanity.
Data were collected for the current study at the point in time when this gene-editing of a fetus had just occurred, which had attracted the attention of the whole world and had become a heated topic on various SNS. This was important for focusing the participants’ attention on the research issues, and to obtain a clearer understanding on the event. The administered questionnaire consists of three parts, the first of which is a privacy and protection statement and informed consent declaration. The participants read the information carefully and confirmed it. The second part consists of two news reports about the gene-editing fetus event from People’s Daily, which is the most authoritative official media source in China, and the Beijing News, which has a wide influence and is based in Beijing. The reports (a total of 884 words) described the development of the event up to December 18, 2018, providing the objective facts calmly and without emotional appeals. The third part required the participants to complete a survey about the gene-editing situation and their feelings about it.
Data Collection
At the preliminary stage, the current study tested the research model through an investigation of frequent SNS users in China. The aim was to answer the research questions about how users’ identity impacts participation in online speech on moral/ethical violation topics on SNS. According to the relevant institutional and national guidelines and regulations, ethics approval was not required. First, the data collection of the current study did not involve implication, drugs, or mental manipulation, as the participants were only required to report their experiences and behavioral tendency according to their SNS use conditions. Thus, no issues with respect to safety, health, or protection of rights and interests were involved. Second, the data collection required no identity concealment, as no privacy or sensitive issues were involved. Third, the questionnaire for collecting the data in the current study includes an informed consent statement, and the participants were only requested to answer questions according to their SNS use conditions. The data were only to be used for scientific research, without influencing the privacy, reputation, living conditions, or health of the participants. Fourth, the potential participants were offered anonymity; they were fully aware of this option before, during, as well as after giving their responses. Fifth, the current study did not store or use the private information of participants, and any information that may lead to identity risks (only the IP address) was removed during the analysis and submission for scientific review.
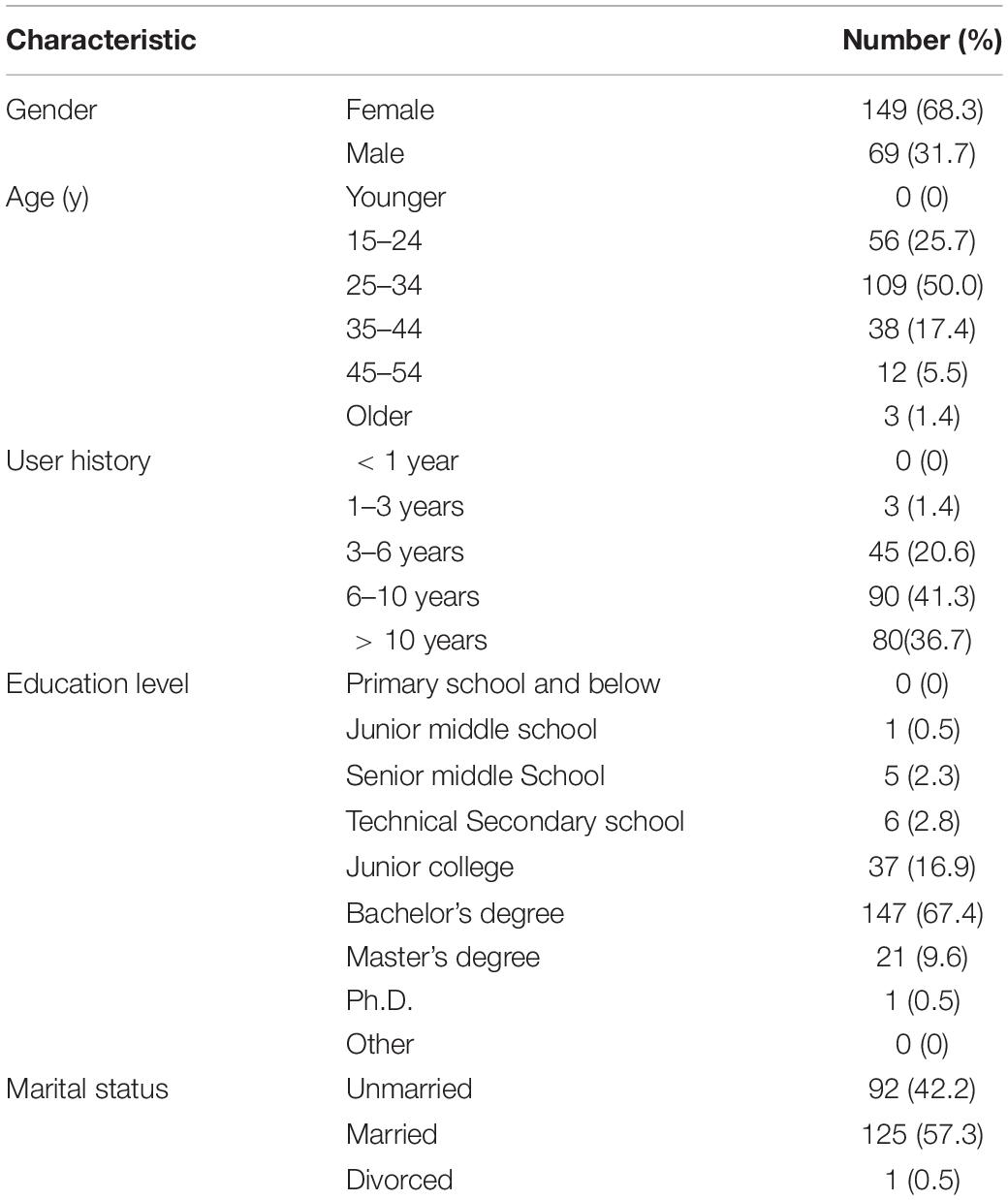
The data were collected with a questionnaire using a sample service provided by an online survey platform (wjx.cn/sample/service.aspx). This is the largest online survey agency in China, providing 2.6 million sample banks consistent with the demographic distribution of China’s netizens. The survey employed a purposive sampling method focused on the frequent users of Chinese SNS. Based on user requirements, the platform sends the invitation email to randomly selected potential participants from the sample banks. The survey would begin once the potential participants clicked the URL in the email. First, they were asked to read a news article about the topic, and then they were asked to fill in a questionnaire online. To identify frequent users of social networking platforms for the study and to confirm the quality of data, we included screening questions and limited the response time as a filter, which yielded a total of 218 valid questionnaires out of 345 responses. The service provider was paid 1 USD for each valid sample. We used the SmartPLS to conduct empirical research. One of advantage of using SmartPLS is the sample size, Some SEM based methods need samples of at least 200 samples or more, but SmartPLS is suitable for sample sizes of less than 200 (Sander and Phoey, 2014). Table 1 shows the demographic characteristics of the respondents to the survey.
The sample had a reasonable demographic distribution. Referring to the data in reports published by affiliated companies Sina and TenCent on Weibo and WeChat in 2018, the age distribution characteristics of the sample were basically consistent with those of Weibo and WeChat users. In the sample, respondents with a bachelor’s degree or above accounted for 77.5% of the total; the education level was slightly higher but within a similar range to that of Sina Weibo users in the reports, 70.8% of whom had university degrees. In WeChat (64% male users) and Weibo (57% male users), the proportion of male users was higher than that of female users. Although the gender distribution of samples may generally lead to bias in the results, gender differences do not affect research on general online sharing behaviors, as confirmed by some related studies on gender distribution differences (Yoon and Rolland, 2012; Cheung et al., 2015; Yan et al., 2016). In addition, data from the current study show that SNS users prefer to browse information rather than publish information. The participants spend on average 81.2% of their time browsing information and 18.8% of their time publishing information and participating in discussions.
Measures
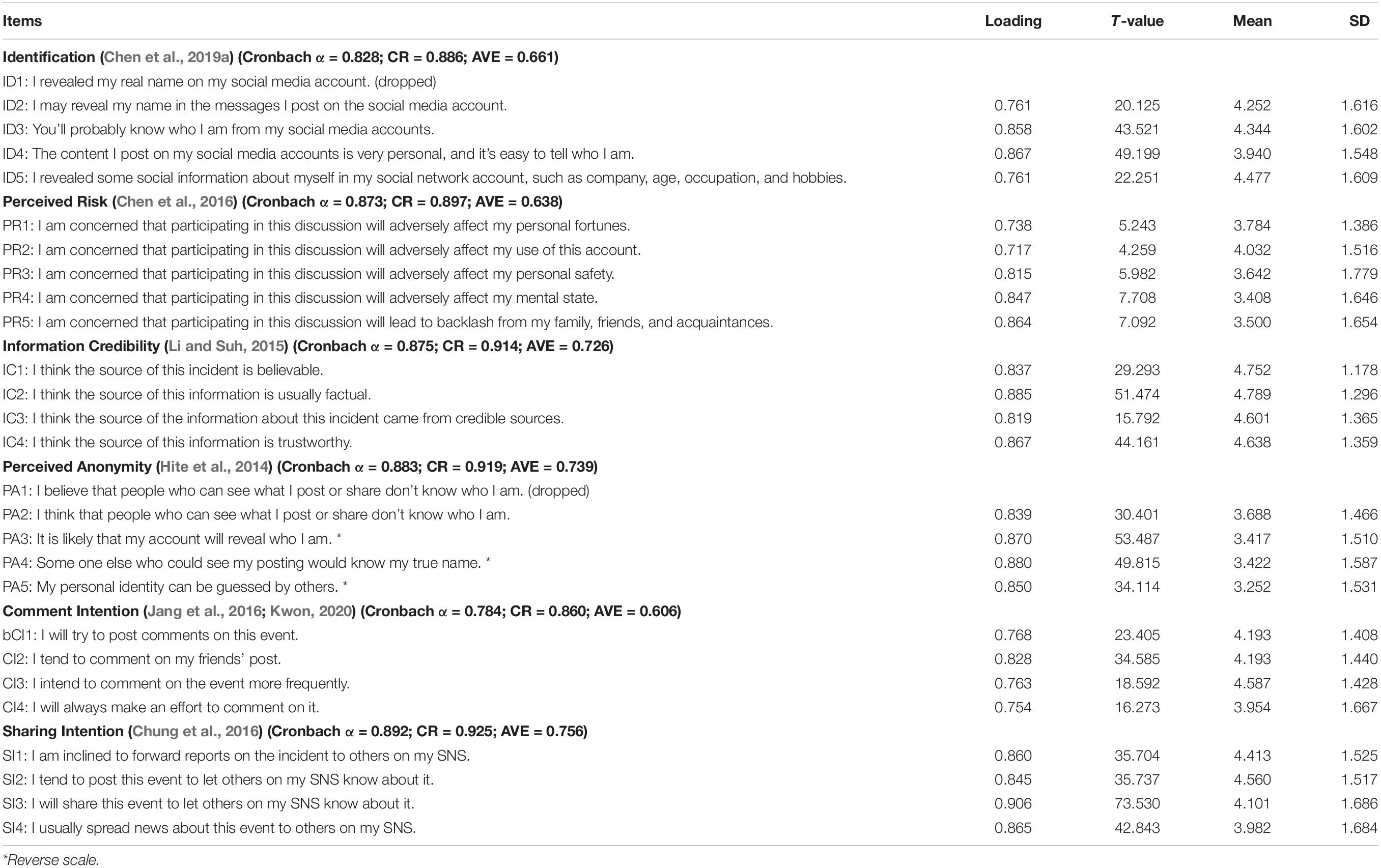
All measures were adapted from well-established scales, the validity of which had been confirmed in the relevant existing literature. Multi-item measures were applied to ensure the validity and reliability of the study. To ensure comprehension by Chinese users, we translated the scale into Chinese and then back-translated it into English. We asked two researchers to verify the consistency of the terms used in the scale to ensure that the translation and terms were consistent. The scale was modified slightly to fit the SNS context. A seven-point Likert scale (1 = strongly disagree to 7 = strongly agree) is used in all measures. Table 2 lists the constructs and measures applied in the research, as well as the source references. The psychometric properties in Table 2 include Cronbach’s α, composite reliability (CR), and average variance extracted (AVE) of the constructs, as well as the loading, T-value, mean, and standard deviation (SD) of the measure items used in the current study.
Results
We used a structural equation model to verify the research model and performed statistical analysis using the partial least squares method (PLS). In addition, we used Smart PLS version 3 (Ringle et al., 2014) to test the research model empirically; this is an analytical technique widely used in social science research because it provides a flexible and exploratory method with coherent explanations of complex relationships (Henseler et al., 2014). In accordance with the two-step analysis method (Hair et al., 2006), we tested the credibility and validity of the measured values and then evaluated the structural model.
In the next sections, we analyzed the data in two steps: first, the measurement and data were tested for reliability and validity, and then we drew conclusions about the structural relationship based on the measurement instruments with desirable psychometric properties.
Reliability and Validity of the Measurement Items
As shown in Table 2, all the indicator loadings were significant and higher than 0.70, except ID1 and PA1, whose loadings were lower than 0.7; therefore, we dropped them, ensuring the convergent validity of the measurement model. The resulting Cronbach’s α of each construct exceeds the recommended level (0.70), and the composite reliability is higher than 0.80, indicating that the reliability of all latent variables is very good. In addition, each variable has good polymerization validity, because the AVE of all latent variables surpasses 0.6.
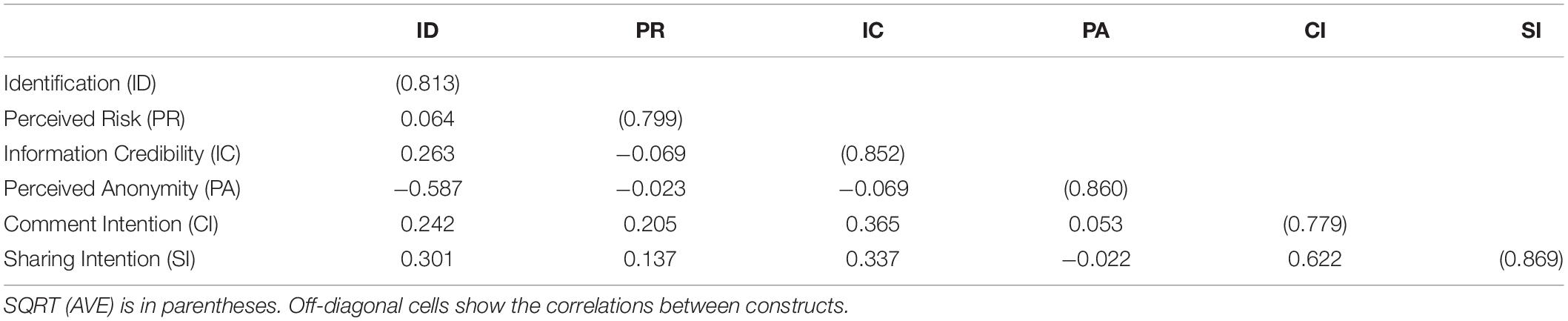
Ensuring discriminant validity requires a low correlation between measures and other structural measures (Fornell and Larcker, 1981). In Table 3, the main diagonal value is the square root of AVE and the out-of-diagonal value is the correlation coefficient between the constructs. All the diagonal values are higher than 0.7 and exceed the correlation between any pair of measures. This value indicates that the model also has good discriminant validity. Therefore, the results of our data analysis have adequately high discriminant validity.
Structural Model
Before testing the hypotheses, multicollinearity regarding the structure of the data was tested and was in accordance with the requirements. We then examined the structural model by analyzing the significance of the path coefficients and the R2 variance for the dependent constructs based on the hypothetical research model. The path and its importance for the structural model, the coefficients of each related structure, as well as their T-values on the structural model and the deterministic coefficients (R2) are illustrated in Figure 2.
For the full model, most proposed hypotheses are strongly supported by empirical evidence with significance at p < 0.05, except for H3b. In this section, we discuss how each construct in our theoretical framework influences the two types of participatory behaviors. Regarding identifiability, we found that identification has a strongly negative influence on perceived anonymity (β = −0.566, p < 0.001). This finding is consistent with results in the previous literature; those people who are objectively identifiable will not perceive themselves to be anonymous. Thus, H1a is supported. The results also show that identification leads to participatory behaviors in discussion on moral/ethic violation topics, both in terms of comment intention (β = 0.321, p < 0.01) and sharing intention (β = 0.365, p < 0.001). In the SNS context, the more personal the information is that is disclosed, the more likely the user is to attend to the discussion and carry out moral/ethical supervision. Therefore, H1b and H1c are supported. Perceived anonymity also leads to participation in discussion on related topics, both in terms of comment intention (β = 0.261, p < 0.01) and sharing intention (β = 0.205, p < 0.05). Perceptions of anonymity also declaim importance in participation in related activities. Therefore, H2a and H2b are supported. Furthermore, the coefficient of the path from identification to sharing intention is greater than that from identification to comment intention. However, the coefficient of the path from perceived anonymity to comment intention is greater than that from identification to sharing intention. Sharing related information is helpful for the user’s image, while making comments carries less interpersonal pressure. This finding suggests that identification and perceived anonymity both have a positive impact on participation in discussion on moral/ethic violation topics, but through a different influence mechanism.
Regarding the conditions for participation, perceived risk has a significant impact on comment intention (β = 0.213, p < 0.01), which is in line with the altruistic punishment mechanism of human behavior. Thus, H3a is supported. However, perceived risk has an impact on sharing intention with a significance level of p = 0.067, suggesting that H3b is not supported in the current study, while the direction of the impact is consistent with H3b. We can say that at the test standard of p < 0.05, the empirical research cannot significantly support H3b. Regarding perceived risk, people are more willing to comment on ethical and moral violations than to share information. From actual experience, the degree of exposure to information sharing in social networks is higher than that of commenting on information released by others. Without any doubt, information credibility leads to comment intention (β = 0.310, p < 0.001) as well as sharing intention (β = 0.263, p < 0.001). Trust in source information leads to confidence in a user’s participation in discussion on related topics. The results imply the importance of information credibility even in moral/ethical violation topics. Therefore, H4a and H4b are supported.
The independent variables explain a substantial portion of the variance in the dependent variables. In the current model, identification explains 31.7% (r2 = 0.317) of the variance in perceived anonymity, 24.4% (r2 = 0.244) of the variance in comment intention with a significant impact from identification, perceived risk, information credibility, and perceived anonymity, and 20.8% (r2 = 0.208) of the variance in sharing intention with a significant impact from identification, information credibility, and perceived anonymity.
In Smart-plus, Standardized Root Mean Square Residual (SRMR) and the Normed Fit Index (NFI) may assess the model fit. For SRMR, the recommended value should be lower than 0.08; NFI values between 0 and 1 are recommended. For the current model, SRMR is 0.067 and NFI is 0.781. The goodness of fit value of the model is 0.577, which is significantly higher than the standard of substantial fitting, in which 0.36, 0.25, or 0.1 can be described as, respectively, substantial, moderate, and weak (Marsh et al., 2005). The indices indicate an acceptable model fit of the data.
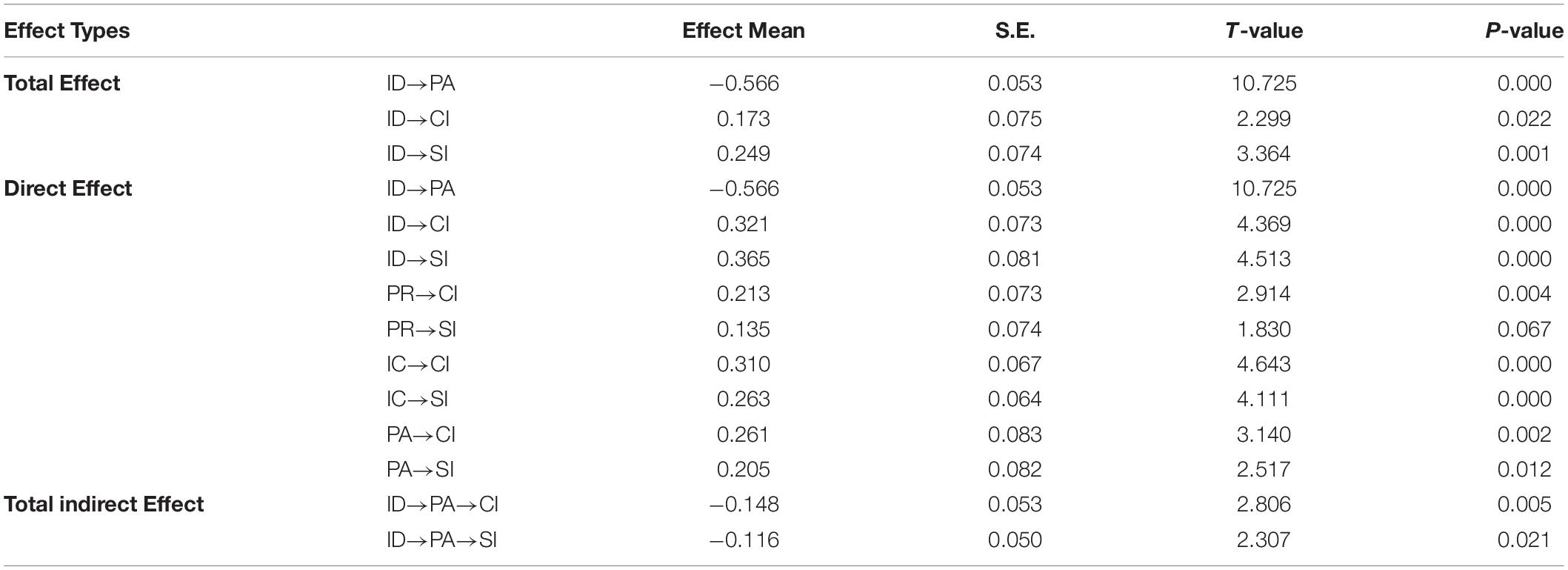
The results of direct effect (DE), total effect of each construct, and the results of indirect effects existing in the model, as well as the standard error and T-values of each effect are given in Table 4. The results show that all direct effects, except for the non-significant direct effect of perceived risk on sharing intention and the significant negative effect of identification on perceived anonymity (DE = −0.566), are positive and significant to varying degrees. Identification has the largest direct impact on comment intentions (DE = 0.321), followed by information credibility (DE = 0.310) and perceived anonymity (DE = 0.261), and perceived risk has the least direct impact on comment intention (DE = 0.213), but is still significant at p < 0.01. Among the direct influences on sharing intention, identification has the largest influence (DE = 0.365), followed by information credibility (DE = 0.263), and perceived anonymity has the smallest influence (DE = 0.205), but is still significant at p < 0.05.
Two significant total indirect effects have been identified in the model. If the sign of indirect effect is opposite to that of direct effect, the total effect will be suppressed (Wen and Ye, 2014). The suppressing effect of perceived anonymity accounts for 46.1% of the direct effect between identification and comment intention, and for 31.8% of the direct effect of identification and sharing intention. Perceived anonymity has a significant suppressing effect between identification and two participation factors.
Discussion and Conclusion
In the current study, we examined user participation in discussions on moral/ethical topics on Chinese SNS. To do so, we constructed a model to describe the influence of identification, perceived anonymity, perceived risk, and information credibility. The measurement model has been confirmed, with acceptable convergent and discriminant validity, path coefficients, and model fit.
Discussion of Results
Identifiability and perceived anonymity of SNS user identity are not two sides of an organic whole but, rather, two different elements (Chen et al., 2019a). Identifiability reflects the amount of information available on the real identity of the behavioral subject that is identified (Marx, 1999). High identifiability of users leads to low perceived anonymity of identity (Chen et al., 2016, 2019a, b), which is also suggested in the current study with the supportive result for H1a. Furthermore, with the supportive results for H1b, H1c, H2a, and H2b, the current study shows that the influence of online identification and perception of anonymity are both conducive to participation in discussion about moral/ethical violation topics. This result is in accordance with the research on self-disclosure on Weibo (Chen et al., 2016).
When users have control over their identification, perceived anonymity contributes to user participation in discussion on moral/ethical violation topics; when users have control over their perceived anonymity, identification also contributes to participation in discussion of moral/ethical issues. High user identifiability is advantageous in building a sense of identification with the social network identity and enhancing the credibility of the opinions expressed at the same time. The influence of perceived anonymity on speech behavior varies in different application scenarios; there is evidence of a negative influence on the perceived autonomy of sharing behaviors in cyberspace (Yoon and Rolland, 2012), whereas on social media it promotes self-expression without causing a reduction in the perception of self-expression risks (Chen et al., 2016). This leads us to conclude that both identification and perceived anonymity play important roles in participation in discussions of moral/ethical violation topics.
The current study also shows the positive effect of perceived risk on users’ intention to post comments on moral/ethical topics on SNS in China: in the face of an event that raises common ethical concerns, when the level of risk perceived by users is higher, so too is their intention to post comments, as shown by the supportive result for H3a. Reducing cybersecurity risk increasingly depends on information sharing (Goodwin et al., 2015). This result is in line with the statement that risk may add value to SNS in some contexts, as users are motivated to reduce uncertainty (Mitchell, 1999). However, it is not consistent with some research studies which examined the impact of risk on information sharing behavior in other SNS contexts and showed no significant impact on self-disclosure (Chen et al., 2016), and that perceived privacy risk will negatively impact the attitude towards information sharing (Hajli and Lin, 2016). Despite the risks, people participate in relevant social activities to safeguard justice because of their moral sentiments (Gintis et al., 2005). This phenomenon reveals the particularity of participation in moral/ethical-related issues. Participating in discussions on moral/ethical violation topics is out of concern for fairness and justice, as well as to reduce uncertainty. This may be attributed to the neural basis of altruistic punishment in people’s brains (Fehr and Gächter, 2002). Participation in discussions on moral/ethical violation topics on networked social media can be understood as reciprocal behavior with a price, because it is a kind of trial-and-punishment of behavior considered unethical, rather than behavior that is responsive or well-targeted. In the face of unethical events, the behavioral mechanism comes from people’s desire to impose punishment and to gain a sense of satisfaction from participation in imposing punishment (De Quervain et al., 2004). Therefore, perceived risk does not make people shrink from discussion participation, but encourages them to participate in the discussion of moral and ethical issues to some extent. The encouragement from perceived risk does not have a significant effect on sharing intention, but the direction of the impact is consistent with H3b. The relations between perceived risk and intensive participation are of value to explore further.
We also found that information credibility significantly affects participation in discussions on moral/ethics violation topics. This has a positive influence on both posting comments and sharing intention on moral/ethics violation topics, with supportive evidence for H4a and H4b. This result is in accordance with the outcomes from research studies on the impact of information credibility on involvement in discussion and sharing (Zimmer et al., 2010; Ha and Ahn, 2011; Özer et al., 2011). The perception and faith of SNS users regarding the authenticity and reliability of the information source plays a crucial role in the regulation of public speech and spreading of information about moral/ethical violation topics.
Theoretical Implications
The current study offers some implications that facilitate future research on participating in discussion on moral/ethical violation topics. Public concern and discussion about moral/ethical violation topics is important for regulating negative behaviors and maintaining social justice. User discussions of this kind of behavior on Chinese SNS in recent years plays a dominant role in promoting the advancement of social institutions and governance by drawing the public attention and letting the government know some information. Therefore, investigation into this kind of behavior can lead to a deeper understanding of theories on reputation, altruistic punishment, and regulation of public speech related to social cooperation.
The current study further clarifies the relationship between identifiability and speech behavior. We confirmed the positive impact of identification and perceived anonymity on participation in discussions on moral/ethics-related events on SNS. This lays a foundation for further exploration of the influence of online user identification on behavior. In the current study, unlike previous studies, online participation in moral/ethical violation topics in cyberspace is divided into commenting and information sharing, which are affected differently by the perception of risks in discussions on moral/ethical violation topic. This means that comments on specific events might not necessarily be seen by a user’s social contacts, but information sharing enables user opinions to be seen by a wide range of social contacts. Our research offers a new perspective for viewing the differences between them.
Practical Implications
The results have practical implications for policy makers, content moderators, and operators of online platforms. Online identification and anonymity perception influence participation in and speech about moral/ethical violation topics, which can have a significant reference value for identity management and internet governance. A network identity policy needs to take into account the reliability of user authentication mechanisms as well as user perception of privacy. This kind of network environment encourages user participation in discussions on sensitive topics. Policy makers should also note that the sense of risk does not necessarily inhibit behavior. In the current study, perceived risk is found to encourage user participation in discussions about moral/ethical violation topics. Successful information efforts require commitment, trust, cooperation, and a clear sense of value (Goodwin et al., 2015). Correct information values are conducive to promoting the sharing and exchange of information.
Besides, the reliability of the topics is very important to the users’ participation in commenting and information sharing. It is necessary to guarantee the reliability of content and information in cyberspace for the network operators and network information providers. It is necessary to regulate the information sources and provide information authentication mechanisms to identify and eliminate false information and rumors and standardize the expression form of information, etc., to promote the discussion and spread of topics.
Limitations and Future Directions
The current study has the following limitations, which open up some avenues for further research.
First, the research study and survey participants only used Weibo and WeChat in China, neglecting the difference embedded in contexts across China and the West. A trial study aimed to what was being studied, which needs further confirmation. Future research is needed to examine how and to what extent contextual and cultural differences affect the research questions and model. Second, the research provides no empirical support for H3b, which means we failed to confirm a positive impact on users from perceived risk about their sharing intention in discussing moral/ethical issues on Chinese SNS. Although differences between posting comments and sharing information are indicated in our discussion, the reasons and mechanisms should be further explored. Third, although the sample size meets the requirements of PLS SEM research with a degree of representativeness to some extent, the limitations of the study caused by the small and non-representative sample still remain; the size and representativeness of the sample need to be expanded in future research, which will contribute to the generalizability of the findings. In addition, the research sample failed to properly consider differences in age, gender, vocation, economic status, education level, and SNS use; therefore, more variables should be taken into consideration in a future study to enhance the representativeness of the research sample.
People’s participation in discussion on violations of morality and ethics on the internet is taken as a crucial form of public collective activity in the criticism and supervision of society. One of the doubts about the internet real-name system is whether identifiability will impede such power. In the current study, empirical evidence was provided on the positive effects of identification, perceived anonymity, risk perception, and information credibility on users’ participation in discussions on unethical topics in Chinese SNS, with a view to providing a reference point for subsequent academic studies, information management of SNS, and the governance of society.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author/s.
Ethics Statement
Ethical review and approval was not required for the study on human participants in accordance with the local legislation and institutional requirements. Written informed consent from the patients/participants or patients/participants legal guardian/next of kin was not required to participate in this study in accordance with the national legislation and the institutional requirements.
Author Contributions
XC performed the theory analysis and design, and contributed to drafting the manuscript. CH analyzed the data and improved the empirical analysis. YC collected data and improved the conclusions. All authors contributed to the article and approved the submitted version.
Funding
This work was supported by the China National Social Science Fund Project, named Research on Network Anonymity and Network Society Governance (Grant Number: 15CSH017), Program for Excellent Young Talents, Yunnan University, and Youth talent project of Yunnan Province, named Research on network comprehensive information management (No. C176220200).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fpsyg.2020.535605/full#supplementary-material
References
Adams, J. (2003). “Risk and morality: three framing devices,” in Risk and morality, eds Edn, eds V. E. Richard and D. Aaron (London: University of Toronto Press), 87–106. doi: 10.3138/9781442679382-006
Bandura, A. (1977). Self-efficacy: toward a unifying theory of behavioral change. Psychol. Rev. 84:191. doi: 10.1037/0033-295x.84.2.191
Bodle, R. (2013). The ethics of online anonymity or Zuckerberg vs. Moot. ACM SIGCAS Comput. Soc. 43, 22–35. doi: 10.1145/2505414.2505417
Boeyink, D. E., and Borden, S. L. (2010). Making hard choices in journalism ethics: Cases and practice. Abingdon: Routledge.
Borden, S. L. (2007). Journalism as practice: MacIntyre, virtue ethics and the press. United Kingdom: Ashgate Publishing, Ltd.
Borden, S. L. (2016). Aristotelian casuistry: Getting into the thick of global media ethics. Commun. Theor. 26, 329–347. doi: 10.1111/comt.12085
Boulianne, S. (2015). Social media use and participation: A meta-analysis of current research. Inform. Commun. Soc. 18, 524–538. doi: 10.1080/1369118x.2015.1008542
Boyd, R., Gintis, H., and Bowles, S. (2010). Coordinated punishment of defectors sustains cooperation and can proliferate when rare. Science 328, 617–620. doi: 10.1126/science.1183665
Brazier, F., Oskamp, A., Prins, C., Schellekens, M., and Wijngaards, N. (2004). Anonymity and software agents: an interdisciplinary challenge. Artif. Intell. Law 12, 137–157. doi: 10.1007/s10506-004-6488-5
Brennan, M., Afroz, S., and Greenstadt, R. (2012). Adversarial stylometry: Circumventing authorship recognition to preserve privacy and anonymity. ACM Trans. Inf. Syst. Secur. 15:12.
Chang, E. C., and Tseng, Y. F. (2013). Research note: E-store image, perceived value and perceived risk. J. Bus. Res. 66, 864–870. doi: 10.1016/j.jbusres.2011.06.012
Chen, X. (2018). Internet anonymous space: emerging order and governance logic. Chong. Soc. Sci. 08, 26–34.
Chen, X., Fang, S., Li, Y., and Wang, H. (2019a). Does Identification Influence Continuous E-Commerce Consumption? The Mediating Role of Intrinsic Motivations. Sustainability 11:1944. doi: 10.3390/su11071944
Chen, X., Sun, M., Wu, D., and Song, X. Y. (2019b). Information-Sharing Behavior on WeChat Moments: The Role of Anonymity, Familiarity, and Intrinsic Motivation. Front. Psychol. 10:2540.
Chen, X., and Li, G. (2013). Essence, evolution and freedom of expression of cyber real name system. Xinhua Digest 20, 132–135.
Chen, X., Li, G., Hu, Y., and Li, Y. (2016). How Anonymity Influence Self-Disclosure Tendency on Sina Weibo: An Empirical Study. Anthropologist 26, 217–226. doi: 10.1080/09720073.2016.11892151
Cherry, J., and Fraedrich, J. (2002). Perceived risk, moral philosophy and marketing ethics: mediating influences on sales managers’ ethical decision-making. J. Bus. Res. 55, 951–962. doi: 10.1016/s0148-2963(00)00215-0
Cheung, C., Lee, Z. W., and Chan, T. K. (2015). Self-disclosure in social networking sites the role of perceived cost, perceived benefits and social influence. Internet Res. 25:279. doi: 10.1108/intr-09-2013-0192
Cheung, C. M., and Lee, M. K. (2012). What drives consumers to spread electronic word of mouth in online consumer-opinion platforms. Decis. Supp. Syst. 53, 218–225. doi: 10.1016/j.dss.2012.01.015
Christopherson, K. M. (2007). The positive and negative implications of anonymity in Internet social interactions:“On the Internet, Nobody Knows You’re a Dog”. Comput. Hum. Behav. 23, 3038–3056. doi: 10.1016/j.chb.2006.09.001
Chung, N., Nam, K., and Koo, C. (2016). Examining information sharing in social networking communities: applying theories of social capital and attachment. Telemat. Inform. 33, 77–91. doi: 10.1016/j.tele.2015.05.005
Cyranoski, D., and Ledford, H. (2018). Genome-edited baby claim provokes international outcry. Nature 563, 607–608. doi: 10.1038/d41586-018-07545-0
Davenport, D. (2002). Anonymity on the Internet: why the price may be too high. Commun. ACM 45, 33–35. doi: 10.1145/505248.505267
De Quervain, D. J., Fischbacher, U., Treyer, V., and Schellhammer, M. (2004). The neural basis of altruistic punishment. Science 305:1254. doi: 10.1126/science.1100735
Earle, T. C., and Siegrist, M. (2006). Morality Information, Performance Information, and the Distinction Between Trust and Confidence. J. Appl. Soc. Psychol. 36, 383–416. doi: 10.1111/j.0021-9029.2006.00012.x
Elliott, D. (ed.) (1986). Foundations for news media responsibility. Responsible journalism. Thousand Oaks, CA: Sage, 32–44.
Featherman, M. S., and Pavlou, P. A. (2003). Predicting e-services adoption: a perceived risk facets perspective. Int. J. Hum. Comput. Stud. 59, 451–474. doi: 10.1016/s1071-5819(03)00111-3
Fehr, E., and Fischbacher, U. (2004). Third-party punishment and social norms. Evol. Hum. Behav. 25, 63–87. doi: 10.1016/s1090-5138(04)00005-4
Fehr, E., and Gächter, S. (2002). Altruistic punishment in humans. Nature 415, 137–140. doi: 10.1038/415137a
Fornell, C., and Larcker, D. F. (1981). Evaluating structural equation models with unobservable variables and measurement error. J. Market. Res. 18, 39–50. doi: 10.1177/002224378101800104
Fox, J., Cruz, C., and Lee, J. Y. (2015). Perpetuating online sexism offline: Anonymity, interactivity, and the effects of sexist hashtags on social media. Comput. Hum. Behav. 52, 436–442. doi: 10.1016/j.chb.2015.06.024
Fox, J., and Moreland, J. J. (2015). The dark side of social networking sites: an exploration of the relational and psychological stressors associated with Facebook use and affordances. Comp. Hum. Behav. 45, 168–176. doi: 10.1016/j.chb.2014.11.083
Gerlach, J., Widjaja, T., and Buxmann, P. (2015). Handle with care: How online social network providers’ privacy policies impact users’ information sharing behavior. J. Strat. Inform. Sys. 24, 33–43. doi: 10.1016/j.jsis.2014.09.001
Gintis, H., Bowles, S., Boyd, R. T., and Fehr, E. (2005). Moral sentiments and material interests: The foundations of cooperation in economic life. Cambridge: MIT press.
Gist, M. E., and Mitchell, T. R. (1992). Self-efficacy: A theoretical analysis of its determinants and malleability. Acad. Manag. Rev. 17, 183–211. doi: 10.2307/258770
Global Web Index. (2018). Social Global Web Index’s Flagship Report on the Latest Trends in Social Media. London: Global Web Index.
Goldsmith, R. E., and Horowitz, D. (2006). Measuring motivations for online opinion seeking. J. Interact. Advertis. 6, 2–14. doi: 10.1080/15252019.2006.10722114
Goodwin, C., Nicholas, J. P., Bryant, J., Ciglic, K., Kleiner, A., Kutterer, C., et al. (2015). A framework for cybersecurity information sharing and risk reduction. New Mexico: Microsoft Corporation.
Guan, M., and So, J. (2016). Influence of social identity on self-efficacy beliefs through perceived social support: A social identity theory perspective. Commun. Stud. 67, 588–604. doi: 10.1080/10510974.2016.1239645
Ha, S., and Ahn, J. (2011). “"Why Are You Sharing Others’ Tweets?: The Impact of Argument Quality and Source Credibility on Information Sharing Behavior,” in Proceedings of the International Conference on Information Systems, ICIS 2011, (China: ICIS), 4.
Hair, J. F., Black, W. C., Babin, B. J., Anderson, R. E., and Tatham, R. L. (2006). Multivariate data analysis 6th Edition. Pearson Prentice Hall. New Jersey. humans: Critique and reformulation. J. Abnor. Psychol. 87, 49–74.
Hajli, N., and Lin, X. (2016). Exploring the security of information sharing on social networking sites: The role of perceived control of information. J. Bus. Ethics 133, 111–123. doi: 10.1007/s10551-014-2346-x
Henseler, J., Dijkstra, T. K., Sarstedt, M., Ringle, C. M., Diamantopoulos, A., Straub, D. W., et al. (2014). Common beliefs and reality about PLS: Comments on Rönkkö and Evermann (2013). Organizat. Res. Methods 17, 182–209. doi: 10.1177/1094428114526928
Hertzum, M., Andersen, H. H., Andersen, V., and Hansen, C. B. (2002). Trust in information sources: seeking information from people, documents, and virtual agents. Interact. Comput. 14, 575–599. doi: 10.1016/s0953-5438(02)00023-1
Hite, D. M., Voelker, T., and Robertson, A. (2014). Measuring perceived anonymity: The development of a context independent instrument. J. Methods Measur. Soc. Sci. 5, 22–39. doi: 10.2458/v5i1.18305
Hong, I. B. (2015). Understanding the consumer’s online merchant selection process: The roles of product involvement, perceived risk, and trust expectation. Int. J. Inform. Manag. 35, 322–336. doi: 10.1016/j.ijinfomgt.2015.01.003
Horst, M., Kuttschreuter, M., and Gutteling, J. M. (2007). Perceived usefulness, personal experiences, risk perception and trust as determinants of adoption of e-government services in The Netherlands. Comput. Hum. Behav. 23, 1838–1852. doi: 10.1016/j.chb.2005.11.003
Hou, J., Ndasauka, Y., Pan, X., Chen, S., Xu, F., and Zhang, X. (2018). Weibo or WeChat? Assessing preference for social networking sites and role of personality traits and psychological factors. Front. Psychol. 9:545.
Hsieh, A. Y., and Luarn, P. (2014). Speech or silence: the effect of user anonymity and member familiarity on the willingness to express opinions in virtual communities. Online Inform. Rev. 38, 881–895. doi: 10.1108/oir-03-2014-0076
Huang, X. C., and Zhang, Q. L. (2010). Discussion on the real name system in the virtual society from the real name system in the real society. J. Southern Stud. 8, 60–62.
Jang, Y. J., Kim, H. W., and Jung, Y. (2016). A mixed methods approach to the posting of benevolent comments online. Int. J. Inform. Manag. 36, 414–424. doi: 10.1016/j.ijinfomgt.2016.02.001
Jardine, E. (2015). “The Dark Web dilemma: Tor, anonymity and online policing,” in Global Commission on Internet Governance Paper Series, (21), (Waterloo: Centre for International Governance Innovation).
Jessup, L. M., Connolly, T., and Galegher, J. (1990). The effects of anonymity on GDSS group process with an idea-generating task. MIS Q. 14, 313–321. doi: 10.2307/248893
Joinson, A. N. (2001). Self-disclosure in computer-mediated communication: The role of self-awareness and visual anonymity. Eur. J. Soc. Psychol. 31, 177–192. doi: 10.1002/ejsp.36
Joinson, A. N. (2007). Oxford Handbook of Internet Psychology. Oxford, UK: Oxford University Press, 2007.
Kang, R., Brown, S., and Kiesler, S. (2013). “Why do people seek anonymity on the internet? Informing policy and design,” in Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, New York, NY, 2657–2666.
Kelton, K., Fleischmann, K. R., and Wallace, W. A. (2008). Trust in digital information. J. Am. Soc. Inform. Sci. Technol. 59, 363–374.
Kim, W., Jeong, O. R., Kim, C., and So, J. (2011). The dark side of the Internet: Attacks, costs and responses. Inform. Sys. 36, 675–705. doi: 10.1016/j.is.2010.11.003
Kiousis, S. (2001).). Public trust or mistrust? Perceptions of media credibility in the information age. Mass Commun. Soc. 4, 381–403. doi: 10.1207/s15327825mcs0404_4
Koch, N. S., and Emrey, J. A. (2001). The Internet and opinion measurement: Surveying marginalized populations. Soc. Sci. Q. 82, 131–138. doi: 10.1111/0038-4941.00012
Kuersten, A., and Wexler, A. (2019). Ten ways in which He Jiankui violated ethics. Nat. Biotechnol. 37:19. doi: 10.1038/nbt.4337
Kwon, S. (2020). Understanding user participation from the perspective of psychological ownership: The moderating role of social distance. Comput. Hum. Behav. 105:106207. doi: 10.1016/j.chb.2019.106207
Lapidot-Lefler, N., and Barak, A. (2012). Effects of anonymity, invisibility, and lack of eye-contact on toxic online disinhibition. Comput. Hum. Behav. 28, 434–443. doi: 10.1016/j.chb.2011.10.014
Levontin, L., and Yom-Tov, E. (2017). Negative Self-Disclosure on the Web: The Role of Guilt Relief. Front. Psychol. 8:1068.
Li, R., and Suh, A. (2015). Factors influencing information credibility on social media platforms: evidence from Facebook pages. Proc. Comput. Sci. 72, 314–328. doi: 10.1016/j.procs.2015.12.146
Liebman, B. L. (2011). The media and the courts: towards competitive supervision? China Q. 208, 833–850. doi: 10.1017/s0305741011001020
Lin, R., and Utz, S. (2017). Self-disclosure on sns: do disclosure intimacy and narrativity influence interpersonal closeness and social attraction? Comput. Hum. Behav. 70, 426–436. doi: 10.1016/j.chb.2017.01.012
Lin, Y. Q. (2010). Debate on advantages and disadvantages of real name system on the Internet: advantages far outweigh disadvantages. Beijing: People’s daily.
Lipschultz, J. (2018). Free expression in the age of the Internet: Social and legal boundaries. London: Routledge.
Lucassen, T., and Schraagen, J. M. (2010). “Trust in wikipedia: how users trust information from an unknown source,” in Proceedings of the 4th workshop on Information credibility, (New York: ACM), 19–26.
Lupton, D. (1993). Risk as moral danger: the social and political functions of risk discourse in public health. Int. J. Health Serv. 23, 425–435. doi: 10.2190/16ay-e2gc-dfld-51x2
Lyons, B., and Henderson, K. (2005). Opinion leadership in a computer-mediated environment. J. Consum. Behav. Int. Res. Rev. 4, 319–329. doi: 10.1002/cb.22
Marsh, H. W., Hau, K. T., and Grayson, D. (2005). Goodness of fit in structural equation models. USA: Lawrence Erlbaum Associates Publishers, 2005.
Martins, C., Oliveira, T., and Popović, A. (2014). Understanding the Internet banking adoption: a unified theory of acceptance and use of technology and perceived risk application. Int. J. Inform. Manage. 34, 1–13. doi: 10.1016/j.ijinfomgt.2013.06.002
Marx, G. T. (1999). What’s in a Name? Some Reflections on the Sociology of Anonymity. Inform. Soc. 15, 99–112. doi: 10.1080/019722499128565
Mitchell, V. W. (1999). Consumer perceived risk: conceptualisations and models. Eur. J. Market. 33, 163–195. doi: 10.1108/03090569910249229
Nicolaou, A. I., and McKnight, D. H. (2006). Perceived information quality in data exchanges: effects on risk, trust, and intention to use. Inform. Sys. Res. 17, 332–351. doi: 10.1287/isre.1060.0103
Nissenbaum, H. (1999). The meaning of anonymity in an information age. Inform. Soc. 15, 141–144. doi: 10.1080/019722499128592
Normile, D. (2018). Shock greets claim of CRISPR-edited babies. Science 362, 978–979. doi: 10.1126/science.362.6418.978
Özer, Ö, Zheng, Y., and Chen, K. Y. (2011). Trust in forecast information sharing. Manag. Sci. 57, 1111–1137. doi: 10.1287/mnsc.1110.1334
Pan, L. Y., and Chiou, J. S. (2011). How much can you trust online information? Cues for perceived trustworthiness of consumer-generated online information. J. Interact. Market. 25, 67–74. doi: 10.1016/j.intmar.2011.01.002
Peter, J. P., and Ryan, M. J. (1976). An investigation of perceived risk at the brand level. J. Market. Res. 13, 184–188. doi: 10.1177/002224377601300210
Rainie, L., Kiesler, S., Kang, R., Madden, M., Duggan, M., Brown, S., et al. (2013). Anonymity, privacy, and security online. Pew Res. Center 5, 1–35.
Rauchfleisch, A., and Schäfer, M. S. (2015). Multiple public spheres of Weibo: A typology of forms and potentials of online public spheres in China. Inform. Commun. Soc. 18, 139–155. doi: 10.1080/1369118x.2014.940364
Reinig, B. A., and Mejias, R. J. (2004). The efects of national culture and anonymity on flaming and criticalness in GSS-supported discussions. Small Group Res. 35, 698–723. doi: 10.1177/1046496404266773
Repnikova, M. (2017). Media openings and political transitions: Glasnost versus Yulun Jiandu. Probl. Post Commun. 64, 141–151. doi: 10.1080/10758216.2017.1307118
Ringle, C. M., Wende, S., and Becker, J. M. (2014). SmartPLS 3. Hamburg: SmartPLS. Acad. Manag. Rev. 9, 419–445.
Salanova, M., Llorens, S., and Cifre, E. (2013). The dark side of technologies: Technostress among users of information and communication technologies. Int. J. Psychol. 48, 422–436. doi: 10.1080/00207594.2012.680460
Sander, T., and Phoey, L. T. (2014). SmartPLS for the human resources field to evaluate a model. Conference: New Challenges of Economic and Business DevelopmentAt. Latvia: University of Latvia, 346–358.
Scott, S. V., and Orlikowski, W. J. (2014). Entanglements in Practice: Performing Anonymity Through Social Media. MIS Q. 38, 873–893. doi: 10.25300/misq/2014/38.3.11
Shah, D. V., Cho, J., Eveland, W. P. Jr., and Kwak, N. (2005). Information and expression in a digital age: Modeling Internet effects on civic participation. Commun. Res. 32, 531–565. doi: 10.1177/0093650205279209
Shen, F., Wang, N., Guo, Z., and Guo, L. (2009). Online network size, efficacy, and opinion expression: Assessing the impacts of Internet use in China. Int. J. Publ. Opin. Res. 21, 451–476. doi: 10.1093/ijpor/edp046
Slovic, P. (1993). Perceived risk, trust, and democracy. Risk Anal. 13, 675–682. doi: 10.1111/j.1539-6924.1993.tb01329.x
Snoj, B., Pisnik Korda, A., and Mumel, D. (2004). The relationships among perceived quality, perceived risk and perceived product value. J. Prod. Brand Manag. 13, 156–167. doi: 10.1108/10610420410538050
Spears, R. (2017). Social identity model of deindividuation effects. Int. Encycl. Med. Effec. 4, 1–9. doi: 10.1002/9781118783764.wbieme0091
Stroud, S. R. (2014). The dark side of the online self: A pragmatist critique of the growing plague of revenge porn. J. Mass Med. Ethics 29, 168–183. doi: 10.1080/08900523.2014.917976
Sullivan, J. (2014). China’s Weibo: Is faster different? New Med. Soc. 16, 24–37. doi: 10.1177/1461444812472966
Valenzuela, S. (2013). Unpacking the use of social media for protest behavior: The roles of information, opinion expression, and activism. Am. Behav. Sci. 57, 920–942. doi: 10.1177/0002764213479375
Van den Eijnden, R. J., Meerkerk, G. J., Vermulst, A. A., Spijkerman, R., and Engels, R. C. (2008). Online communication, compulsive Internet use, and psychosocial well-being among adolescents: A longitudinal study. Dev. Psychol. 44:655. doi: 10.1037/0012-1649.44.3.655
van Winsen, F., de Mey, Y., Lauwers, L., Van Passel, S., Vancauteren, M., and Wauters, E. (2016). Determinants of risk behaviour: effects of perceived risks and risk attitude on farmer’s adoption of risk management strategies. J. Risk Res. 19, 56–78. doi: 10.1080/13669877.2014.940597
Vilanova, F., Beria, F. M., Costa, ÂB., and Koller, S. H. (2017). Deindividuation: From Le Bon to the social identity model of deindividuation effects. Cogent Psychol. 4:1308104.
Weeks, B. E., Ardèvol-Abreu, A., and Gil de Zúñiga, H. (2017). Online influence? Social media use, opinion leadership, and political persuasion. Int. J. Publ. Opin. Res. 29, 214–239.
Wen, Z. L., and Ye, B. J. (2014). Analyses of mediating effects: the development of methods and models. Adv. Psychol. Sci. 22, 731–745. doi: 10.3724/sp.j.1042.2014.00731
Wright, M. F. (2014). Predictors of anonymous cyber aggression: the role of adolescents’ beliefs about anonymity, aggression, and the permanency of digital content. Cyberpsychol. Behav. Soc. Network. 17, 431–438. doi: 10.1089/cyber.2013.0457
Yan, Z., Wang, T., Chen, Y., and Zhang, H. (2016). Knowledge sharing in online health communities: a social exchange theory perspective. Inf. Manag. 53, 643–653. doi: 10.1016/j.im.2016.02.001
Yoon, C., and Rolland, E. (2012). Knowledge-sharing in virtual communities: familiarity, anonymity and self-determination theory. Behav. Inform. Technol. 31, 1133–1143. doi: 10.1080/0144929x.2012.702355
Yu, G. M. (2017). Key elements and operation on network public opinion governance. News Writ. 1, 10–13.
Yue, H. Y., Pang, W. M., Tam, C. Y., and Fan, C. W. N. (2017). “Does Spending More Time on Facebook Makes Users Engage in Politics?,” in 2017 IEEE International Symposium on Multimedia (ISM), (Berling: IEEE), 426–431.
Zhai, X. W. (1999). Personal status: a concept and its analytical framework: the real construction of China’s daily society. Chin. Soc. Sci. 4, 144–157.
Zhang, F., and Lu, Y. (2010). Thinking about power consciousness based on the dispute of real name system on the Internet. Seek. Truth 11, 72–75.
Zhang, L., Zhao, J., and Xu, K. (2015). Who creates trends in online social media: The crowd or opinion leaders? J. Comput. Med. Commun. 21, 1–16. doi: 10.1111/jcc4.12145
Keywords: anonymity perception, risk perception, information credibility, content moderation, real names on social media
Citation: Chen X, Huang C and Cheng Y (2020) Identifiability, Risk, and Information Credibility in Discussions on Moral/Ethical Violation Topics on Chinese Social Networking Sites. Front. Psychol. 11:535605. doi: 10.3389/fpsyg.2020.535605
Received: 01 April 2020; Accepted: 17 August 2020;
Published: 23 October 2020.
Edited by:
Richard Keith Wortley, University College London, United KingdomReviewed by:
Hu Jian, Jiangxi University of Finance and Economics, ChinaPei Huang, Beijing University of Posts and Telecommunications (BUPT), China
Ivan Wen, University of Hawai‘i at Mānoa, United States
Copyright © 2020 Chen, Huang and Cheng. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xi Chen, MTM2MTA0OTFAcXEuY29t
 Xi Chen
Xi Chen Chenli Huang
Chenli Huang Yi Cheng
Yi Cheng