- 1Department of Human Sciences for Education, University of Milano-Bicocca, Milan, Italy
- 2Department of Psychology, Catholic University of the Sacred Heart, Milan, Italy
- 3Human Behavior Laboratory, University of Iceland, Reykjavik, Iceland
- 4Faculty of Psychology, Institute of Neurosciences, University of Barcelona, Barcelona, Spain
Deception has evolved to become a fundamental aspect of human interaction. Despite the prolonged efforts in many disciplines, there has been no definite finding of a univocally “deceptive” signal. This work proposes an approach to deception detection combining cognitive load manipulation and T-pattern methodology with the objective of: (a) testing the efficacy of dual task-procedure in enhancing differences between truth tellers and liars in a low-stakes situation; (b) exploring the efficacy of T-pattern methodology in discriminating truthful reports from deceitful ones in a low-stakes situation; (c) setting the experimental design and procedure for following research. We manipulated cognitive load to enhance differences between truth tellers and liars, because of the low-stakes lies involved in our experiment. We conducted an experimental study with a convenience sample of 40 students. We carried out a first analysis on the behaviors’ frequencies coded through the observation software, using SPSS (22). The aim was to describe shape and characteristics of behavior’s distributions and explore differences between groups. Datasets were then analyzed with Theme 6.0 software which detects repeated patterns (T-patterns) of coded events (non-verbal behaviors) that regularly or irregularly occur within a period of observation. A descriptive analysis on T-pattern frequencies was carried out to explore differences between groups. An in-depth analysis on more complex patterns was performed to get qualitative information on the behavior structure expressed by the participants. Results show that the dual-task procedure enhances differences observed between liars and truth tellers with T-pattern methodology; moreover, T-pattern detection reveals a higher variety and complexity of behavior in truth tellers than in liars. These findings support the combination of cognitive load manipulation and T-pattern methodology for deception detection in low-stakes situations, suggesting the testing of directional hypothesis on a larger probabilistic sample of population.
Introduction
Deception is a matter of everyday life, as several studies have underlined. Turner et al. (1975) estimated that 62% of the statements in everyday general conversations could be somehow classified as deceptive. DePaulo et al. (1996) employed a 1-week diary study to record people’s everyday communication, specifically deceptive communication. Their results suggest that people tell approximately two lies per day on average and that approximately 20 to 33% of our daily interactions are deceptive. Serota et al. (2010) report an average of 1.65 lies in a 24-h period. These data have been supported in two other empirical studies (Hancock et al., 2004; George and Robb, 2008). With a similar methodology, Hancock et al. (2004) observed 26% of our everyday communication to be involving some form of deception, while George and Robb (2008) estimated that 22–25% of our daily communication might be deceptive.
Even though percentages slightly change among different studies, we can affirm deception is a ubiquitous phenomenon which has evolved to become a fundamental aspect of human interaction (O’Sullivan, 2003; Trivers, 2011). Despite prolonged efforts across a broad array of contexts and disciplines, a diagnostic cue to deception has not been found yet (DePaulo et al., 2003; Sporer and Schwandt, 2007; Vrij, 2008).
Two cognitive lie detection approaches emerge from the literature, both relying on the classic Cognitive Capacity Theory (Kahneman, 1973) and adapted from the Cognitive Load Theory (Van Merrienboer and Sweller, 2005). The “mere cognitive load approach” and the “imposing cognitive load approach.”
The first approach (“mere cognitive load”), assumes that the act of lying itself generates observable signs of cognitive load (intrinsic cognitive load). This is also known as the traditional cognitive lie detection approach, based on the work by Zuckerman et al. (1981). Several authors agree in stating that some aspects of lying contribute to the increased mental load (e.g., DePaulo and Kirkendol, 1989; Buller and Burgoon, 1996; DePaulo et al., 2003; Kassin and Norwick, 2004; Kassin, 2005; Vrij et al., 2006; Walczyk et al., 2013).
Lying is not always more cognitively demanding than truth telling (McCornack, 1997). Differences between liars and truth-tellers may be relatively small, and perhaps not readily discernable by observers (Zuckerman et al., 1981; DePaulo et al., 2003), especially when considering low-stake lies. Low-stake lies include pedagogic or white lies, day-to-day polite lies (DePaulo et al., 1980), as well as different kinds of concealment, omission, and evasive messages. On these occasions deceivers and truth-tellers are assumed either to have little to gain (or lose) by being judged deceptive by the addressee or to feel little fear of being caught telling these lies as required by a polite society (Frank and Ekman, 1997). The liar can be at ease in these contexts and does not need particular cognitive demands in generating this kind of deceptive message (Anolli et al., 2002). Conversely, high-stakes lies may have serious effects and consequences for both the deceiver and the deceived. Generally, these kinds of lies are likely to happen in complicated relational situations and in conflicting or face-threatening contexts, such as police interrogations, customs inspections, and high-stake poker games (Frank and Ekman, 1997; Anolli et al., 2002). The speaker has to face up to high cognitive demands since, telling the truth or telling a lie, he has to fabricate a message with the lowest risk of penalty. Many studies focused on the cognitive design of deception in high-stake contexts (Tsiamyrtzis et al., 2007; for an overview see Vrij et al., 2017), while low-stake ones have been scarcely investigated.
The second approach (“imposing cognitive load”), is based on the manipulation of extraneous cognitive load and, for this reason, we think it is particularly suited for low-stakes lies detection. In this perspective, an additional cognitive demand is imposed on individuals to highlight the observable differences between lying and truth telling. Two variations of this method can be identified: in some studies, cognitive demand was increased by making the lie task harder (e.g., Vrij et al., 2008, 2011), while other ones adopted the dual-task paradigm (Baddeley and Hitch, 1974; Baddeley, 1992). For this study, we chose the second option.
Techniques under the heading of dual-task paradigm seek to induce cognitive load selectively on liars not making the lie task harder but rather by altering other aspects of the examination procedure or context. In dual-task paradigm experiments on deception, researchers ask subjects to carry out a secondary task while lying. Because of the additional resources needed for fabricating and telling the lie, people should find dual task more cognitively difficult when they lie than when they tell the truth, and as a result, they should perform worse when they lie. A powerful framework for understanding multi-task interference effect is the Adaptive Executive Control (AEC), which claims that the major sources of interference are in the competition between concurrent tasks for the same perceptual or motor response systems and the executive process performing one task before another (due to its higher priority given the performer’s goals) (Meyer and Kieras, 1997; Meyer et al., 2002). The second task, therefore, will be as more effective as its execution activates the same underlying mechanisms, loading on the same systems used for creating, processing and telling the specific kind of lie being investigated.
As it happens in standard communication, liars are able to arrange a set of different signaling systems to communicate and make their communicative intentions effective, like language, the paralinguistic system, the face and gestures system, gaze, proxemics and the haptic system, or the chronemic system.
Since no diagnostic cue to deception occurs, it could be that a diagnostic pattern does arise when a combination of cues is taken into account (Vrij, 2008). Several studies showed that multimodal data collection could be effective in deception detection. Vrij (2008) claims that, with a combination of four different variables (illustrators, hesitations, latency period, and hand/finger movements) he was able to classify correctly 84.6% of liars and 70.6% of true tellers (Vrij et al., 2000). Jensen et al. (2010), focused on cues extracted from audio, video and textual data, with the aim of building a paradigm for deception detection via a multi-layered model. They reached a classification accuracy of 73.3%, claiming that deception indicators are subtle, dynamic, and transitory, and often elude a human’s conscious awareness. Other studies have shown that between 71 and 78% of correct classifications were made when the researchers investigated a cluster of behaviors (Heilveil and Muehleman, 1981; Vrij et al., 2004; Davis et al., 2005). In other words, more accurate truth/lie classifications can be made if a cluster of non-verbal cues is examined rather than each of these cues are treated separately.
Of course, people can easily control only those patterns that are manifest and have a macroscopic nature, easily readable from the outside time by time. However, patterns in behavior are frequently hidden from the consciousness of those who perform them as well as to unaided observers (Magnusson, 2006). As Eibl-Eibesfeldt (1970) argued, “behavior consists of patterns in time. Investigations of behavior deal with sequences that, in contrast to bodily characteristics, are not always visible.” When the order of events is the only variable considered, the main challenge is to detect the pattern without being distracted by background noise from other events. T-pattern analysis was developed by Magnusson (2000, 2005, 2006) to find temporal and sequential structure in behavior. The term T-pattern stands for temporal pattern; this approach focuses on determining whether arbitrary events sequentially occur within a specified time interval at a rate greater than that expected by chance. In this way, it detects repeated patterns of behavior units coded as events on one-dimensional discrete scales. Temporal pattern analysis and its related software THEME (Magnusson, 2000) have been applied to a great number of research experiments in very different fields. Patterns have been used to describe, interpret and understand phenomena such as deceptive communication (Anolli and Zurloni, 2009; Zurloni et al., 2013, 2016; Diana et al., 2015), animal and human behavior (Kerepesi et al., 2005; Casarrubea et al., 2015), patient–therapist communication in computer assisted environments (Riva et al., 2005), a wide variety of observational and sports studies, such as analysis of soccer team play (Camerino et al., 2012; Cavalera et al., 2015; Diana et al., 2017), motor skill responses in body movement and dance (Castañer et al., 2009) and deception detection in doping cases (Zurloni et al., 2015).
Moreover, patterns of this kind may often be hard or impossible to detect with the well-known statistical methods that are found in major statistical program packages and behavior research software, such as The Observer (Noldus, 1991; Noldus et al., 2000) or GSEQ (Bakeman and Quera, 1995).
Basing on the literature discussed above and results from previous studies (Vrij, 2008; Zurloni et al., 2013, 2016; Burgoon et al., 2014, 2015; Diana et al., 2015), this work proposes an approach to deception detection combining cognitive load manipulation and T-pattern methodology with three objectives: (a) testing the efficacy of dual task-procedure in enhancing differences between truth tellers and liars in a low-stakes situation; (b) exploring the efficacy of T-pattern methodology in discriminating truthful reports from deceitful ones in a low-stakes context; (c) setting the experimental design and procedure for future and follow-up research.
Method and Data Analysis
Participants
The convenience sample was initially composed by 46 students, (50% male and 50% female), aged from 21 to 31, born in Italy and living in the same geographic area (inclusion criteria). They were volunteers, contacted through the University’s online study recruiting platform. Due to the exploratory aim of this study, the recruiting lasted 2 months, until 23 males and 23 females fitting the inclusion criteria signed for the experiment. Six students never showed up for the experiment, restricting our final sample to 40.
Instructions on the recruiting platform informed candidates they would participate in an experiment involving their communicative abilities and working memory. At the beginning of the experiment, all participants signed an informed consent to both audio and video recording and authorized the use and processing of personal data; they were also explicitly informed of the possibility to withdraw from the experiment at any time. To increase motivation further, we guaranteed a restitution of results, giving information about their communicative skills.
Instruments and Materials
– post hoc controls and manipulation check instruments, based on cognitive abilities and possible arousal interferences for the participants involved in the experiment (anxiety levels too high or cognitive capacities too distant from the average). For this purpose, we used the State-Trait Anxiety Inventory (STAI; Spielberger, 1983) to measure trait and state anxiety at different times of the experiment. We also used a digit span test and a Corsi test (Mammarella et al., 2008) for short term memory (phonological and spatial).
– a short video clip was made for the experiment, divided in two segments, which were showed separately (see procedure for information about the trials order). The whole video is a no-dialog story about four characters organizing a bank robbery and committing it. The video is silent because we wanted to avoid having participants use words from the characters and to let them free in the interpretation and accounting of the story (no violent acts or emotionally involving events are depicted, in order to avoid arousal interference). The video was cut approximately in half, so that each segment’s length would be about the same as the other and contain the same number of events.
– dual task procedure. In the experimental condition, participants were asked, on two occasions, to memorize a series of four sentences. The two series are different, balanced to contain the same number of words and the same syntactic structure. Participants were told to remember these sentences since they could be asked to recall them at any time during the experiment. This extra memory task was added to produce interference in visual-spatial memory.
– observation instrument: the behavior categories we identified refer to self-contact gestures (ADAPTOR in the coding grid), illustrator gestures (ILLUSTRATOR), rhythmic gestures (RHYTHMIC), emblems or symbols (SYMBOL), leg movements (LEG), feet movements (ONLY_FOOT), finger movements (ONLY_FINGERS). These behaviors have been chosen according to what emerged in our previous study (Zurloni et al., 2013, 2016), in other studies found in literature (Caso et al., 2006), and also according to what was affirmed by Anolli (2012) concerning the scarcity of distal movements compared to proximal ones during deception, as well as the results obtained by Burgoon et al. (2014) on kinesic T-patterns related to deception. The objective was to create a coding grid that would satisfy the need to simplify interpretation of patterns while identifying specific components in patterns that could be more relevant, when combined, than the configurations tested until now.
– Research Randomizer -Version 4.0- computer software (Urbaniak and Plous, 2013), to randomize the order of trials;
– Behavior Coder software, for manually coding non-verbal behaviors from video sources;
– SPSS 22 software, for statistical analysis of behavior frequencies and pattern data.
– Theme 6.01 software for T-pattern detection. This software detects the temporal structure of data sets, revealing repeated patterns (T-patterns) that regularly or irregularly occur within a period of observation. It allows the detection of repeated temporal patterns even when multiple unrelated events occur in between components of the patterns.
Procedure
This study was carried out at the University of Milano-Bicocca in an audio-isolated laboratory room equipped with four cameras, set to video-record participants’ full-lengths and close-ups. The cameras were connected to a 2-channel quad device (split-screen technique).
The participants, males and females, were assigned to conditions using a procedure (control condition for the first male participant, experimental for the second and so on; the same with the female group) designed to have the same number of participants, balanced for gender, per group (as near as possible).
The whole experiment, in both conditions, lasted 40–50 min. After signing the informed consent form, all participants filled in the STAI_T inventory. After this, the experimenter administered them a digit span memory test and a Corsi test for spatial memory.
The experiment, in general, consisted of watching two segments of a video (see Instruments and Materials) and then report to a confederate the truth about the content of one segment and lie about the content of the other. The order of trials has been randomized within the two conditions with a randomization software (Research Randomizer, Urbaniak and Plous, 2013), so that half of the participants would lie about the first video, while the other half about the second one (see Table 1).
In the control condition, before the first video, participants are asked to watch and pay attention to every detail, explaining that the next part of the experiment will concern that particular video. After watching the video, the examiner asks them to fill out a STAI_S inventory, to measure state anxiety (and verify possible changes in arousal provoked by watching the video or other conditions). Then, depending on the trial, they are asked to report what they saw in the video or to lie about what they saw in the video to an interlocutor who, to their knowledge, does not have prior information about its content. Participants are given a list of things they can use in their report (if they have to lie, there are examples of details that can be changed, such as the number or gender of the characters, their features, their actions, etc.). They are given 5 min alone to recall and organize their report (mentally); after this, the confederate enters the room and is introduced to the participant as a fellow participant. The examiner exits the room and starts the recording. An audio signal cues the participant to start telling his/her report to the interlocutor, who does not participate in the conversation. After this part, the examiner ends the recording, goes back to the room and restarts the same routine with the second video (second part of the story). Participants are given the same instructions as before, adding the information that the interlocutor does not know which part of their story is made up but knows that one part is. This was necessary so they would not have to justify inconsistencies with their first report, since they are expected.
In the experimental condition (cognitive load manipulated), the procedure is the same but participants have to perform a dual task; before starting each of their reports, they are given a list of 4 numbered sentences to memorize and are told that they will have to recall them (when asked by the examiner) at random times during their report. They do not know when they will be interrupted or which sentence will be asked to recall, nor how many times this will happen. To enhance interference, instructions suggest to keep recalling the sentences mentally during the whole report. After the instructions, participants are given two extra minutes to memorize the sentences. Then, like in the control condition, the interlocutor enters the room and, after an audio signal, participants start their report.
At the end of the two segments, the examiner tells participants that the experiment is over and answers any question they might have about the procedure or the study.
Data Analysis
The memory span and anxiety tests we used for exclusion criteria did not show outliers. Nonetheless, 3 participants out of the initial 40 had to be excluded for technical problems with the recordings, restricting our sample to 37 participants and 74 reports (data from the 37 participants included in the analysis were available for all the measures considered, see Table 1). The videos were coded on Behavior Coder software by two coders, using a blind coding procedure. The occurrences of each event-type within the selected observation period form the so called T-dataset’.
To assess inter-rater reliability of the T-dataset, Cohen’s Kappa was calculated on 10% of the encodings. Although differing through categories, inter-coder reliability was found to be good to satisfactory (ranging from 0.78 to 0.90; p < 0.05). When disagreements were identified or the agreement was not perfect, the specific cases were discussed and agreed on by both coders.
Single Cues
We carried out a descriptive analysis of the behaviors’ frequencies coded through Behavior Coder, using SPSS (22). The aim was to show shape and characteristics of the distributions. Next, we carried out Mann-Whitney and Wilcoxon Signed Rank Tests, as a guideline for interpreting data and exploring differences between groups.
T-Pattern Detection
T-datasets were then analyzed with Theme 6.02 for T-pattern detection. A T-pattern is essentially a combination of events where the events occur in the same order, with the consecutive time distances between consecutive pattern components remaining relatively invariant, regardless of the occurrence of any unrelated event in between them (Magnusson, 2005).
The 74 datasets were analyzed with THEME software to search for patterns and describe behavior structure and complexity (number of unique T-patterns, mean T-patterns’ lengths and levels) in the truth and deception data, exploring differences between groups in the control and experimental conditions. The software allows to set statistical parameters for the pattern detection, according to research aims and scope. For this study, the threshold pattern significance was set to p < 0.005 and the minimum number of pattern occurrences was set to 2 (chosen based on mean length of the observation period, 2 min; Zurloni et al., 2015).
A descriptive analysis on T-pattern frequencies was carried out to show shape and characteristics of the distributions; Mann–Whitney and Wilcoxon Signed Rank Tests as a guideline for interpreting data and exploring differences between groups.
An in-depth analysis on more complex patterns was performed to get qualitative information on the behavior structure expressed by the participants. We chose to consider the more complex patterns because they represent the highest level of organization expressed by the participants in the two conditions.
Results
Single Cues
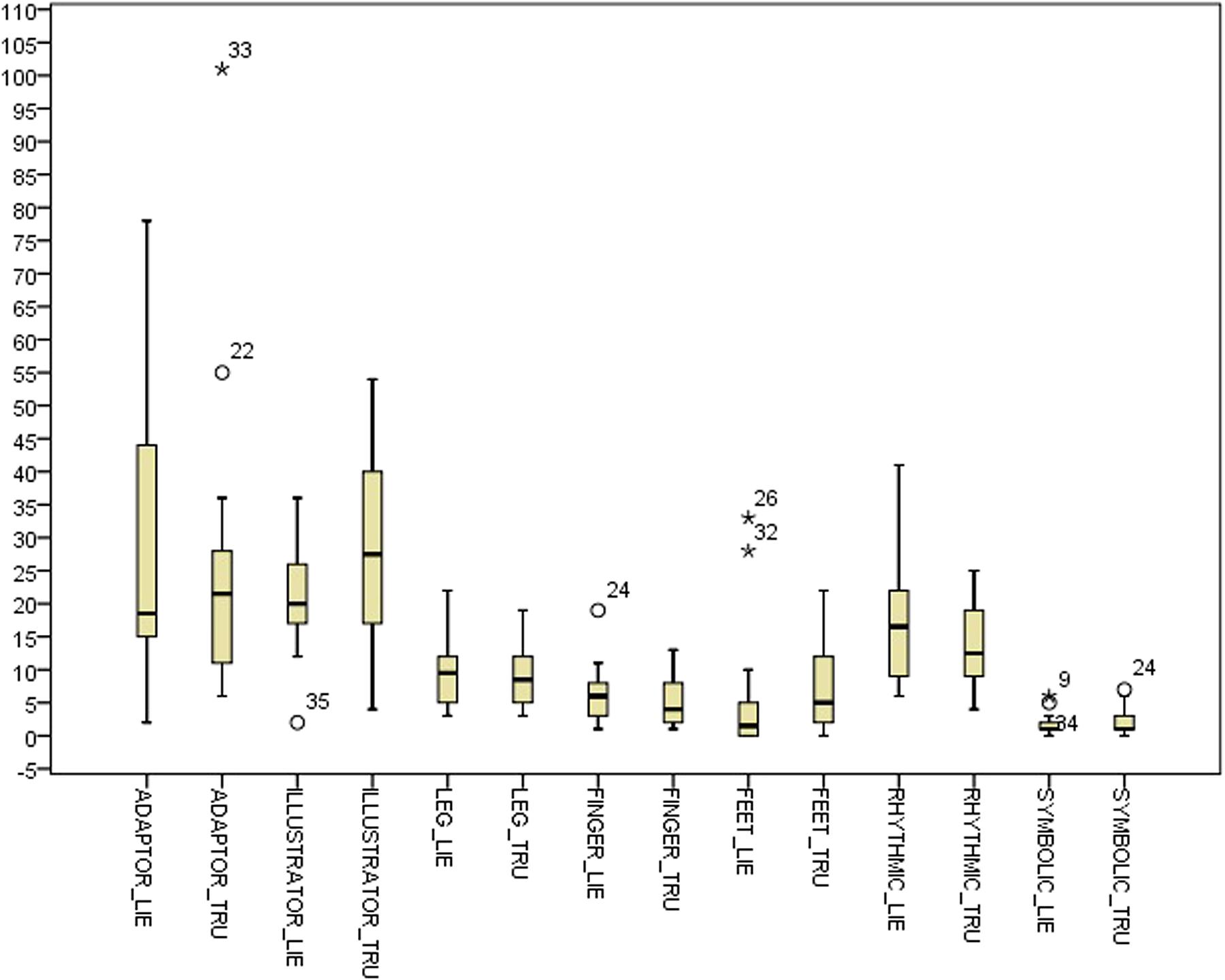
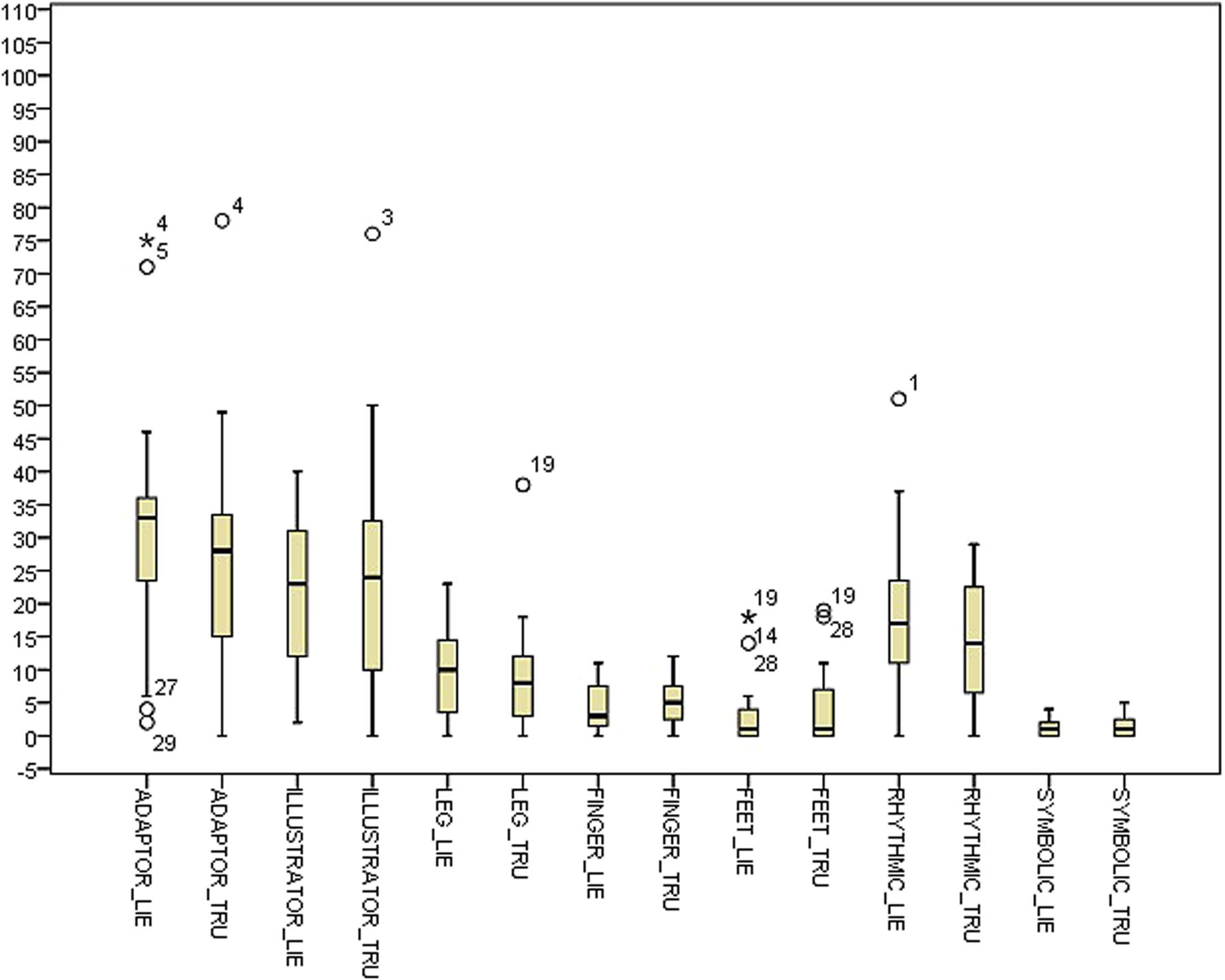
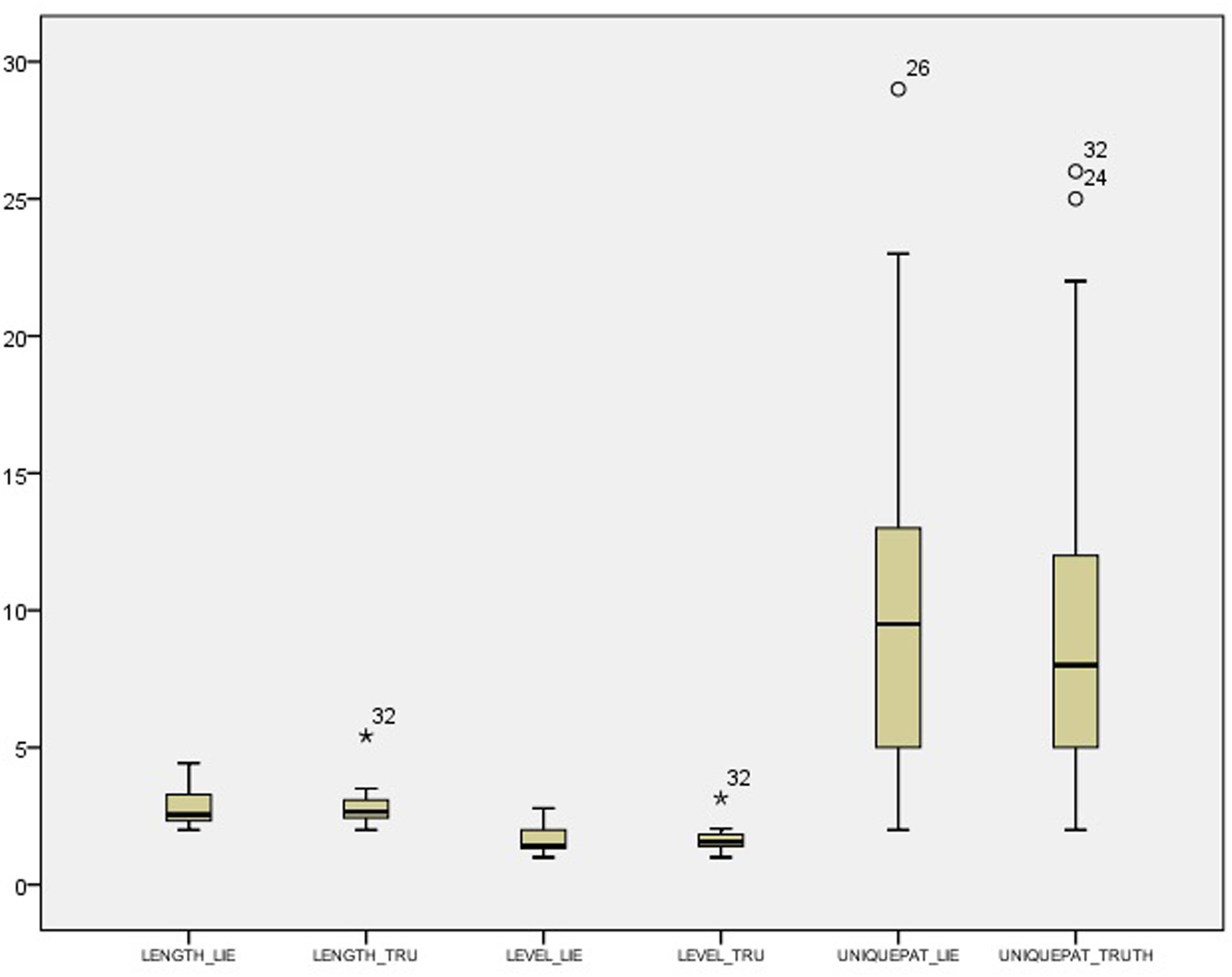
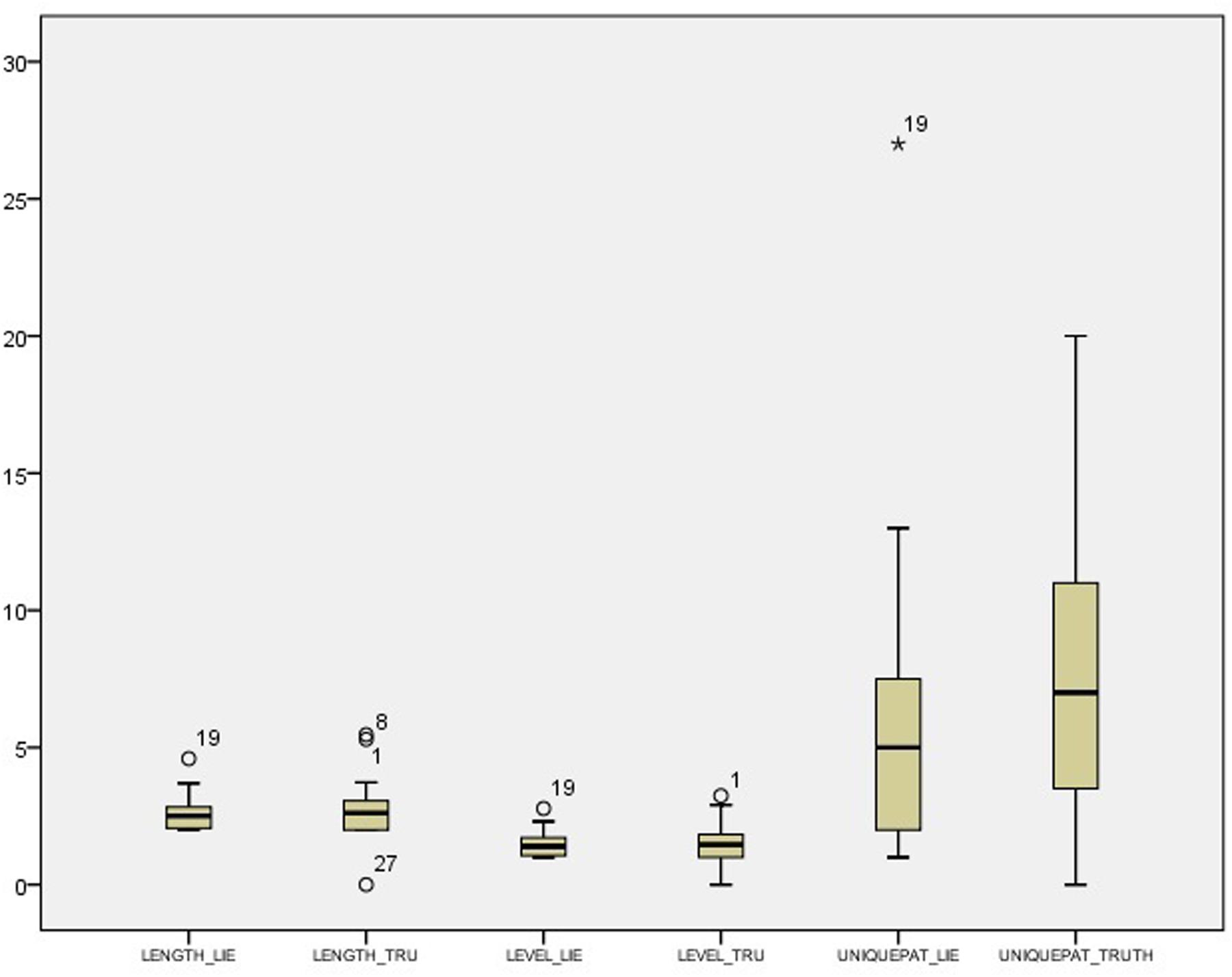
Table 2 shows descriptive statistics for the difference between the deceptive and truthful reports for the single cues within the control condition. Table 3 shows the corresponding statistics within the experimental condition. Table 4 and Figure 1 show descriptive statistics of single cues in truthful and deceptive reports within the control condition, while Table 5 and Figure 2 show descriptive statistics of single cues in truthful and deceptive reports within the experimental condition.
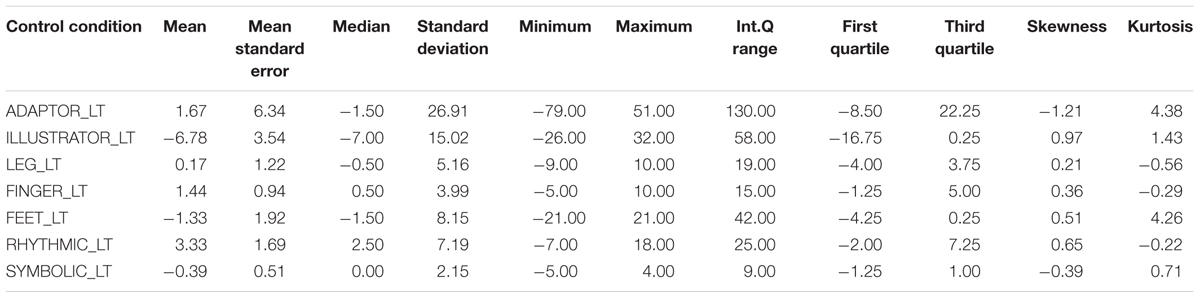
TABLE 2. Descriptive statistics for the difference between the deceptive and truthful reports for the single cues within the control condition.
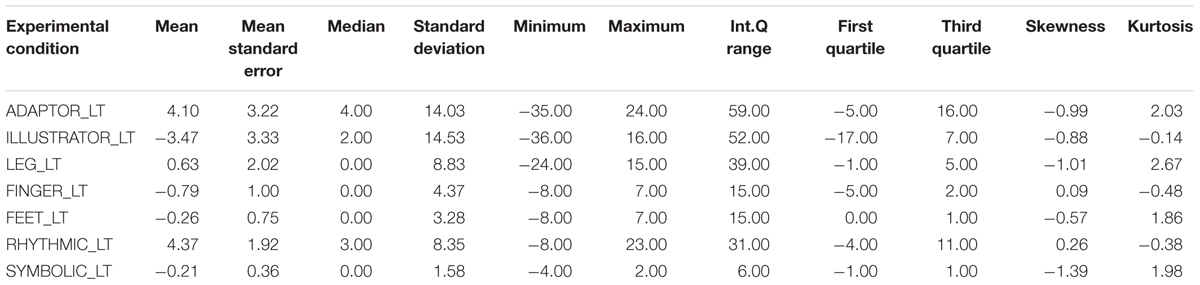
TABLE 3. Descriptive statistics for the difference between the deceptive and truthful reports for the single cues within the experimental condition.
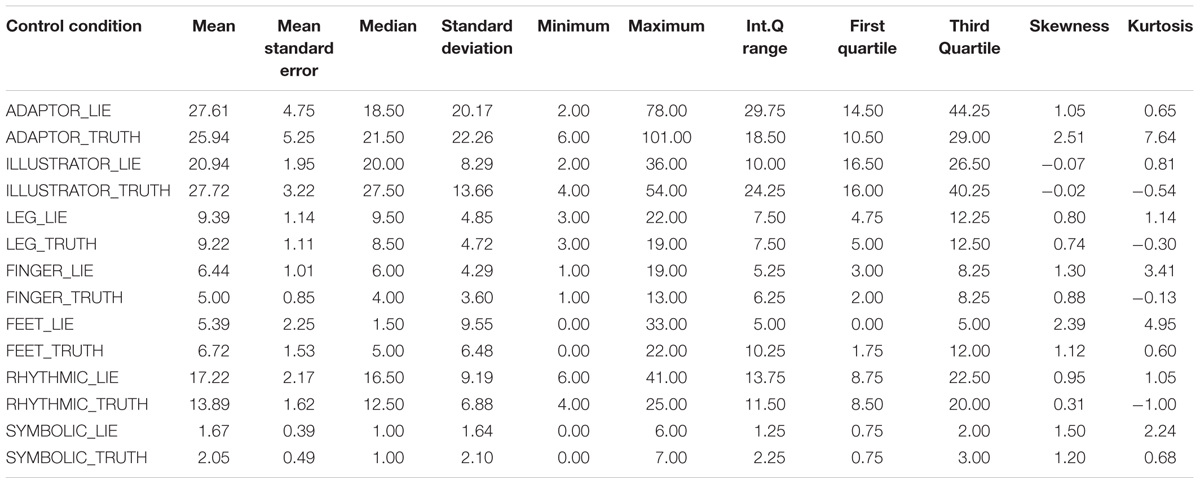
TABLE 4. Descriptive statistics for the single cues in truthful and deceptive reports within the control condition.
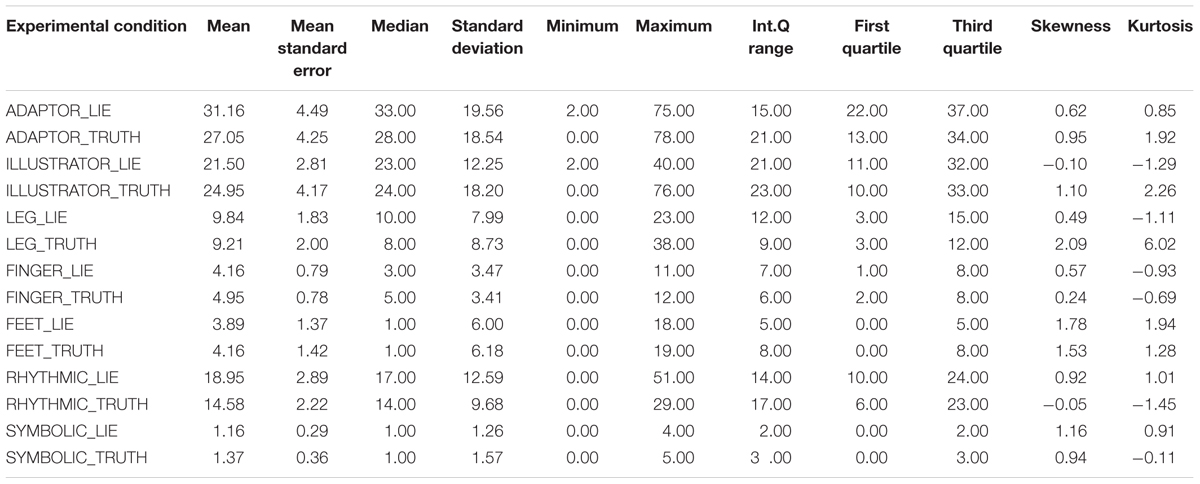
TABLE 5. Descriptive statistics for the single cues in truthful and deceptive reports within the experimental condition.
Results highlight some differences between conditions, especially regarding the distribution of ADAPTOR gestures. In deception data, the median increases from 18.50 in the control condition to 33.00 in the experimental one, while the data dispersion decreases (inter-quartile range: 29.75 in the control condition to 15.00 in the experimental one). Considering data distribution within the control condition, ILLUSTRATOR gestures were more frequently observed in truthful reports (median 27.50) rather than deceptive ones (median 20.00). In the experimental condition, RHYTHMIC gestures were more frequent in deceptive reports (median 17.00), rather than in truthful ones (median 14.00). Independent samples Mann–Whitney U Test seems to show no differences in distributions across the two conditions for all the considered indexes. Differences between truth tellers and liars were explored within groups using related samples Wilcoxon Signed Rank Test (Wilcoxon, 1945). Results in the control condition seem to show no differences except for the ILLUSTRATOR behavior (p = 0.047), which appeared to be less present in deception than in truthful reports (see Table 5).
Results in the experimental condition show a difference in the distributions of RHYTHMIC gestures (p = 0.033), more present in deceptive reports than in sincere ones (see Table 5).
T-Pattern Analysis
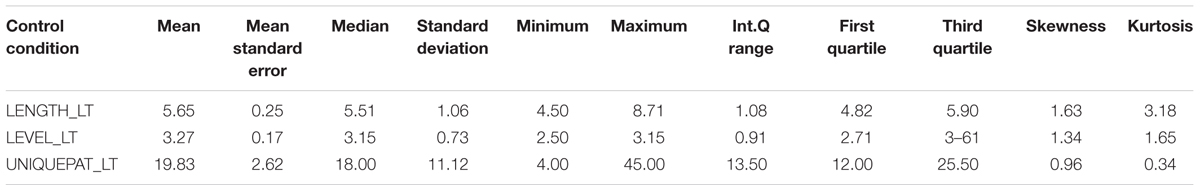
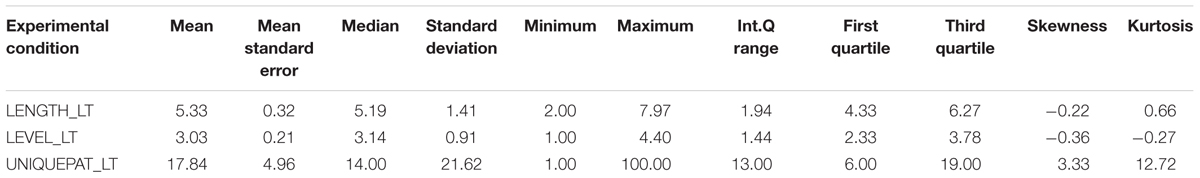
Descriptive statistics and distributions of T-patterns in the control condition are presented in Table 6, while the experimental condition data are presented in Table 7.
Descriptive statistics and distributions of T-patterns of truthful and deceptive reports in the control condition are presented in Table 8 and Figure 3, while the experimental condition data are presented in Table 9 and Figure 4. Independent samples Mann–Whitney U Test suggest a difference in the distributions of unique patterns between the two conditions (p = 0.026). In fact, while the control condition shows no differences between truthful and deceptive data (in number of unique T-patterns, mean T-patterns’ lengths and levels), the experimental condition shows a difference in terms of unique patterns between truth tellers and liars (Wilcoxon’s test, p = 0.036). In particular, the number of unique patterns is substantially higher in truthful reports than in deceptive ones with a less dispersion in data distribution (see Table 9).
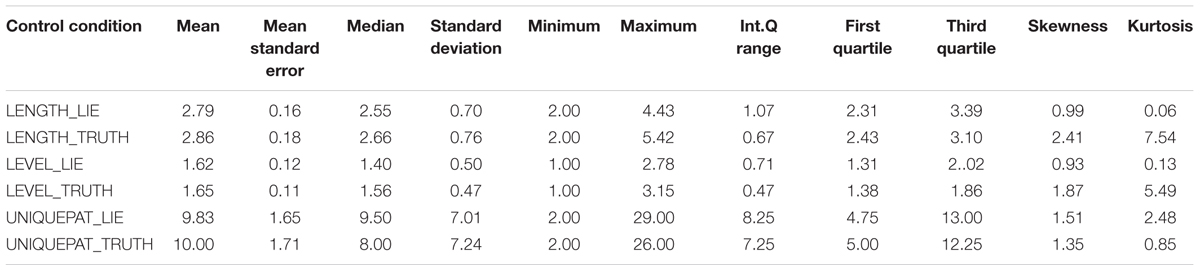
TABLE 8. Descriptive statistics for T-pattern data in truthful and deceptive reports within the control condition.
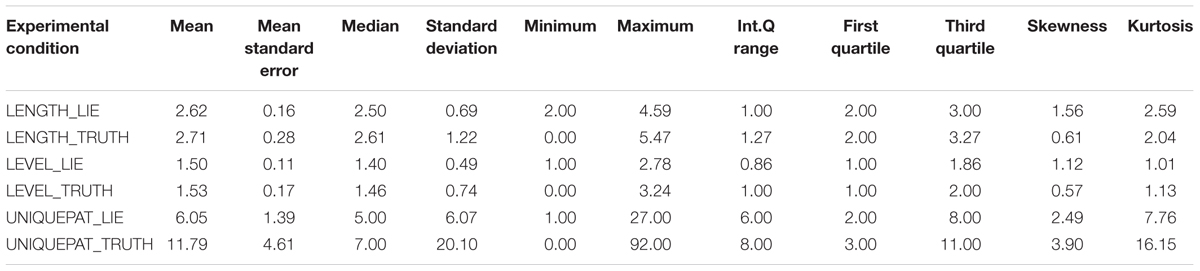
TABLE 9. Descriptive statistics for T-pattern data in truthful and deceptive reports within the experimental condition.
The most distinctive patterns for both conditions have also been qualitatively analyzed. In the control condition, there are few quantifiable differences in detected T-patterns, but it is possible to notice a trend for half of the participants, showing less complex patterns in deceitful accounts and more complex ones in truthful accounts. An example is shown in Figure 53, relative to a sincere report in control conditions: it is a complex pattern, characterized by 6 levels, 11 event-types for its length, compared to an average in control conditions of 1.6 levels (SD = 0.5) and 2.86 (SD = 0.76) event-types. It is composed of rhythmic, illustrator gestures, feet and leg movements. It occurs twice during the whole observation period. Some “blocks” (or sub-patterns) included in this T-pattern are also identified by the software (singularly) and appear next to the complete pattern, occurring often and involving illustrator gestures, mostly.
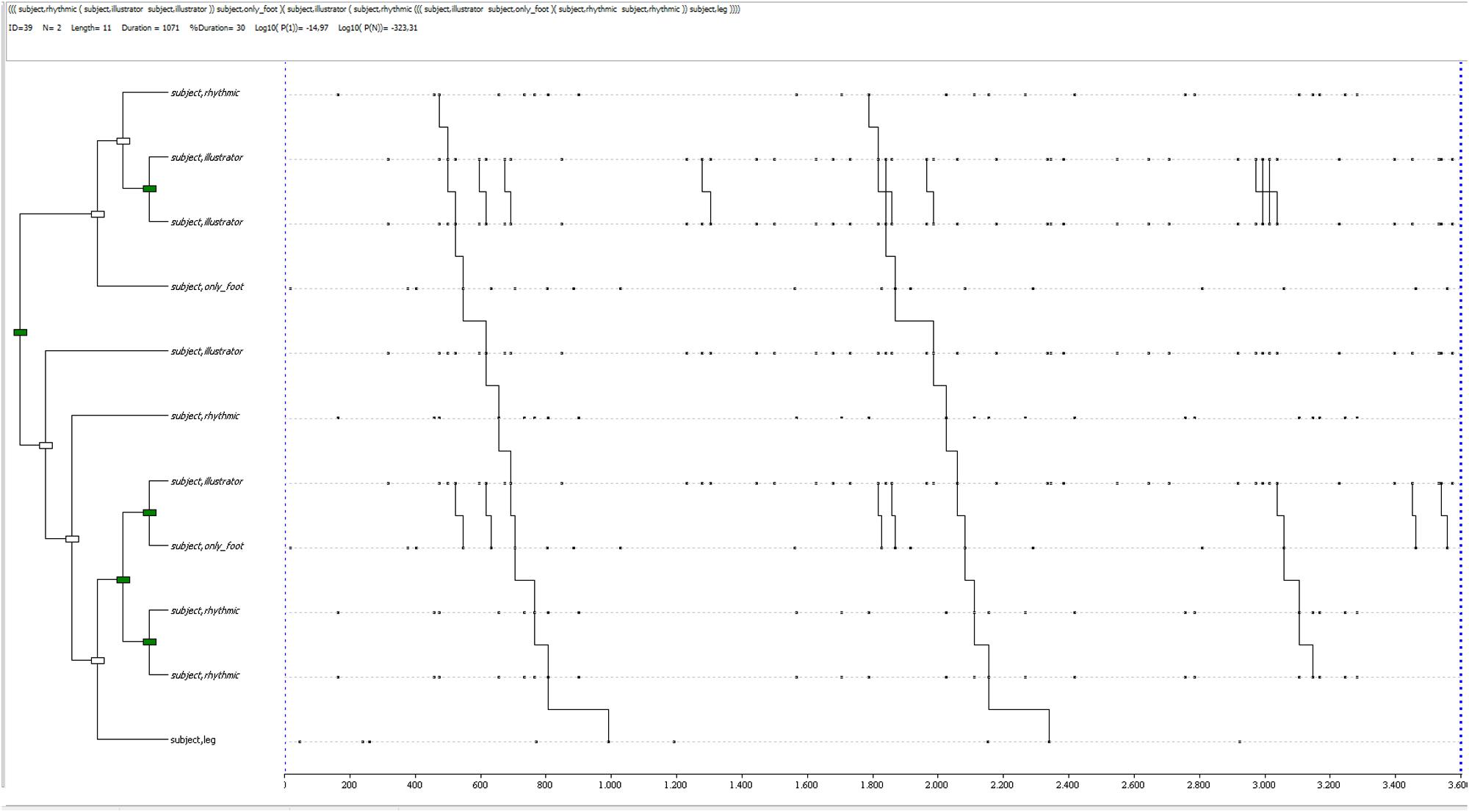
FIGURE 5. T-pattern extracted from a truthful dataset in the control condition. The events occurring begin with a rhythmic gesture, linked to a sub-pattern made of two illustrator gestures, followed by feet movement; then, another illustrator gesture is followed by a rhythmic one, a sub-pattern including an illustrator gesture and feet movement, another sub-pattern made of rhythmic gestures, to finally end with legs movement. This pattern has a length of 11 event-types, 6 levels and it occurs twice during the whole observation period.
A deception-related T-pattern for the control condition by the same participant is shown in Figure 6: it is a complex pattern (3 levels, 6 events, with a mean in control deceptive reports of 1.6 levels and 2.8 events), characterized by an alternation of rhythmic and self-contact gestures. It occurs twice during the observation period, toward the end, although different combinations of the same behaviors occur in earlier sections of the observed period.
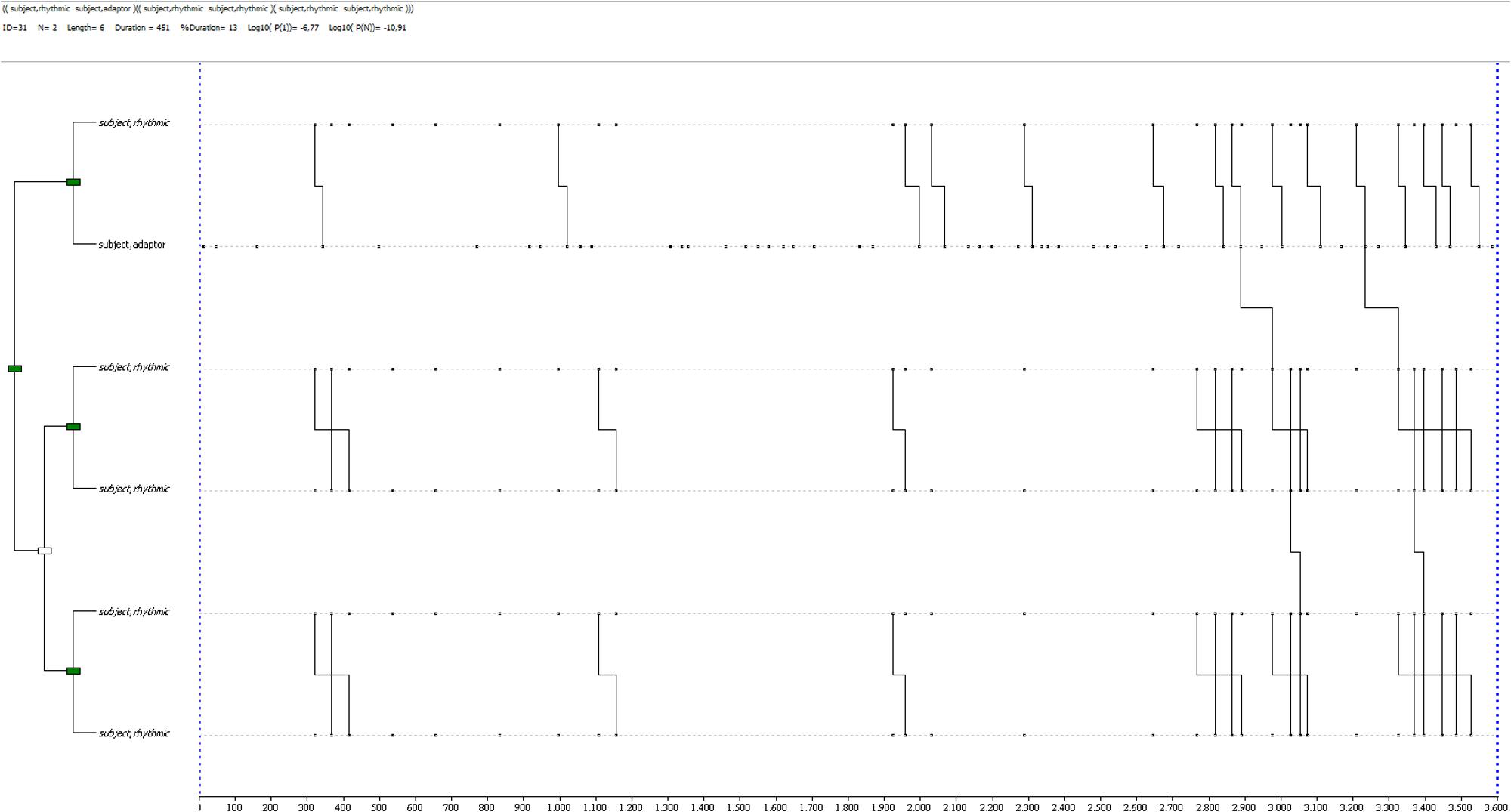
FIGURE 6. T-pattern extracted from a deception dataset in the control condition. The events occurring begin with a rhythmic gesture, linked to a self-contact gesture, then followed by 2 sub-patterns of linked rhythmic gestures. This pattern has a length of 6 event-types, 3 levels and it occurs twice during the observation period.
In experimental conditions, the qualitative evaluation of patterns confirms the lack of richness suggested by the exploratory analysis in deception: T-patterns are generally simple; in some cases, the most complex one is only made by 2 different events. In more complex cases, repetition of gestures of the same category are found, linked in sub-patterns of this kind. Rhythmic gestures are identified in many deception-related patterns.
The truth condition shows variety in T-pattern compositions, with a general trend toward a complex and varied non-verbal behavior, similar to the control condition patterns. An example is shown in Figure 7: a complex pattern, 2 levels and 4 event-types, with a general mean in its group of 1.53 levels (SD = 0.74) and 2.71 event-types (SD = 1.21). It is made of two sub-patterns including self-contact gestures, finger movements and illustrator gestures.
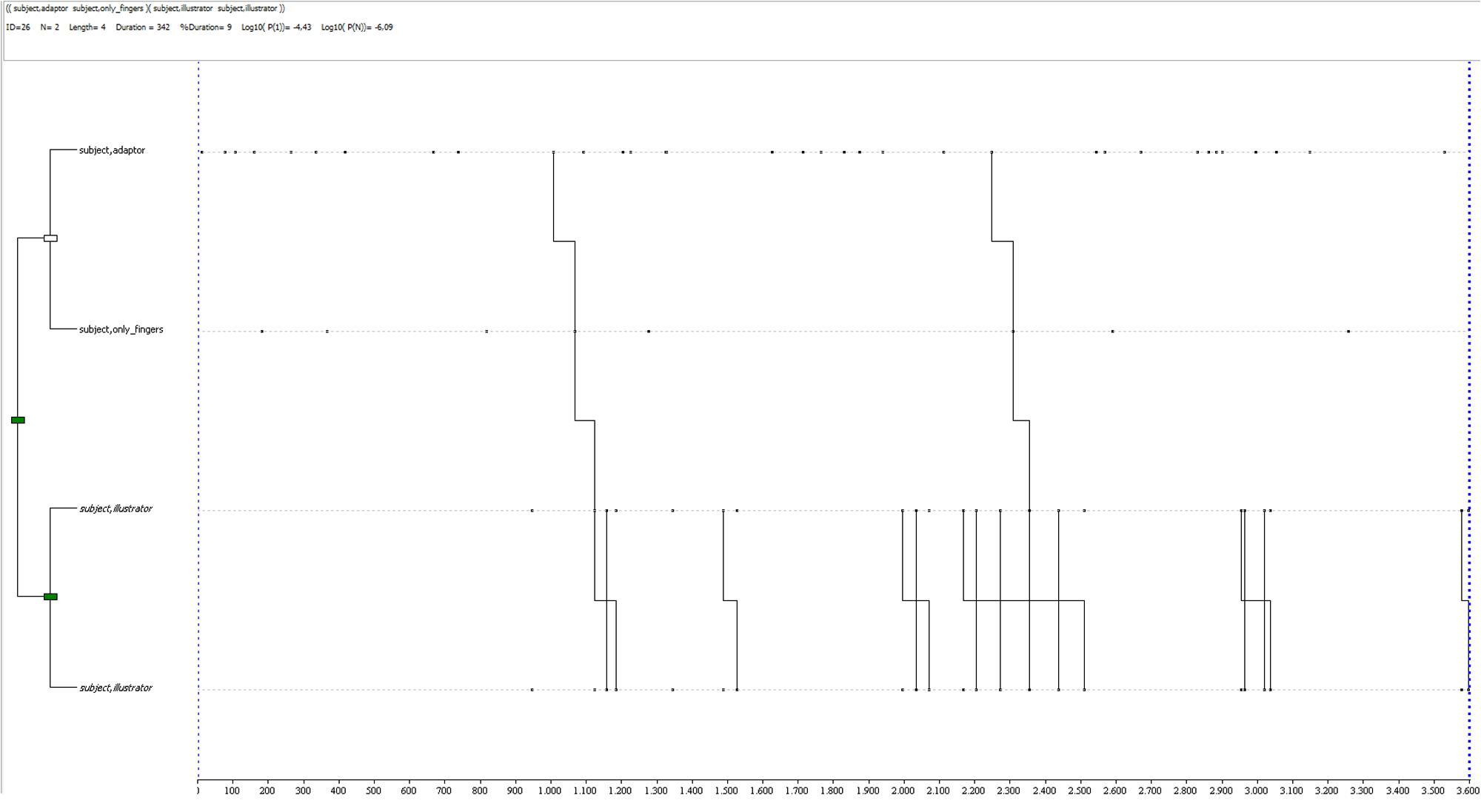
FIGURE 7. T-pattern extracted from a truthful dataset in the experimental condition. The events occurring begin with a self-contact gesture linked to finger movement (not a gesture), and two illustrator gestures. This pattern has a length of 4 event-types, 2 levels and it occurs twice during the observation period.
A T-pattern related to deception reports by the same participant is shown in Figure 8: it is a very simple one (1 level, 2 event-types, with a general mean of 1.5 levels and 2.6 events), being made of an alternation of self-contact and rhythmic gestures. It occurs 10 times during the observation period.
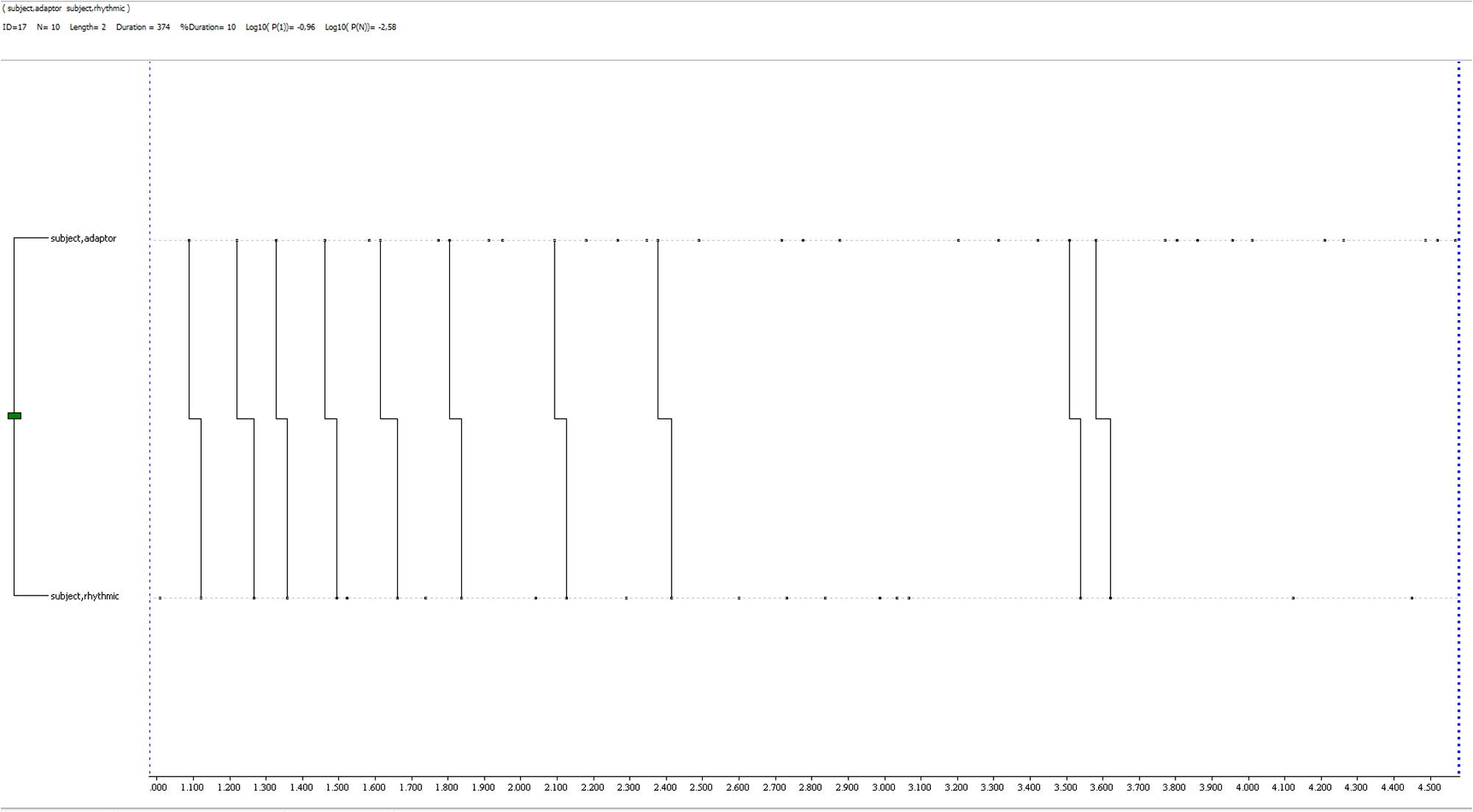
FIGURE 8. T-pattern extracted from a deception dataset in the experimental condition. It is made of two event-types only, a self-contact gesture and a rhythmic one, both very close to each other. It has a 2 event-types length, 1 level and it occurs 10 times during the observation period.
Discussion and Conclusion
Research on deception detection has been focused for a long time on the identification of single unmasking cues, while there have been few studies where deceptive behavior has been observed in a temporal and sequential structure perspective (Vrij, 2008; Burgoon et al., 2015). T-pattern analysis allowed to identify repeated patterns of behavior with different qualities and quantities between deception and truth.
The frequencies observed for single cues suggest that cognitive load manipulation did not affect the occurrence of specific behaviors, except for the adaptor gestures, which clearly decrease in the experimental condition, especially when lying. The decrease in data dispersion could be an effect of cognitive load manipulation. Adaptors (self-contacts and self-manipulations) are self-regulating gestures, that can increase with the increase in emotional or cognitive load (e.g., Vrij et al., 2008). Exploring differences within conditions, illustrator gestures seem to occur more in the truth excerpts of the control group (the less cognitively demanding setting). The decrease of illustrator gestures occurrences during deception has been discussed and linked to the intrinsic cognitive load increase by DePaulo et al. (2003), and by Sporer and Schwandt (2007) in their meta-analyses; our findings seem to confirm that direction. In the experimental condition, rhythmic gestures were found to be more present in deceptive reports than in truthful ones. It is interesting to underline how this supports what was observed by Caso et al. (2006) in a study which used an experimental variable such as the rise of suspicion level, operationalized in a phase of the interview where the interlocutor directly accused the participant to be lying. The cognitive load manipulation condition used in our study could have produced the same result of the invasive interview used in the study by Caso et al. (2006). In conclusion, the behaviors identified in this analysis have already been found to be intrinsic of a cognitively demanding condition; in fact, these could be the effects of the increased arousal related to cognitive overload.
T-pattern frequencies show that the distribution of unique patterns seems to be affected by cognitive load manipulation. These data have to be confirmed by further studies (since the p-value was here used as a guideline), but it is interesting to notice that the dual-task procedure interfered on the behavior structure and variety rather than on single behavior’s occurrences. As for the control condition, our data did not show any relevant difference between truth and deception in terms of unique patterns, mean lengths and levels. This result, although to be confirmed, is in accordance with what emerged from literature and supports using techniques that interfere with cognitive load; in fact, the cognitive effort demanded by “low stakes” lying could have been not enough to produce observable effects on non-verbal behavior. In the experimental condition, instead, a difference seems to exist between truth and deception in terms of unique T-patterns, with a higher number of them in truthful reports than in deceptive ones. No differences were found in the number of levels and lengths of T-patterns, although we think that this result might be affected by the length of the observation period. In general, it appears that the cognitive effort related to dual task affected non-verbal behavior variability and richness, making it more stereotypical and “mechanical” (Zurloni et al., 2015).
Qualitative in-depth analysis of detected T-patterns has shown a wide range of behaviors exhibited in patterns of all conditions. It is clear that, in control conditions, differences in non-verbal behavior between lying and truth-telling are subtle or very hard to interpret. For some participants (less than half of the sample), deception and truth-telling were characterized by similar patterns, while for others there is a decrease in complexity while lying (described by the lower mean of lengths, levels, and the number of unique patterns). These differences are not systematic enough to be ascribed to a general rule, although we do not expect them to be, since the huge amount of studies carried out in recent years produced similar results (DePaulo et al., 2003). We can speculate that the lying task might have elicited different responses because of different factors, among them a stronger or weaker inclination to deception (Anolli, 2012), or a more specific advantage or disadvantage caused by the cognitive capabilities used to lie (such as working memory, Baddeley, 1992). As suggested by findings above, in the control condition, many truth-related patterns are characterized by one or more illustrator gestures. In literature, illustrator gestures have been linked to sincerity and rhythmic gestures to deception (DePaulo et al., 2003; Caso et al., 2006). Finding these data in the structures detected by THEME contributes to support its usefulness in observational studies on deception. In the experimental condition, patterns detected by the software clearly indicate the difference between truth telling and lying conditions. In the latter one, in fact, structures of minimal complexity are detected, often as a chain of occurrences of the same kind of gesture. In many cases, patterns related to deception include rhythmic gestures. Caso et al. (2006), in their study on sincerity and deception based on the gestures’ frequencies, have observed the same increase in rhythmic gestures, and we believe a cognitive load increase could explain both results. Patterns related to truth-telling in the experimental condition show a certain variety in composition, similar in its abnormal distribution of frequencies to patterns related to the control condition. These patterns are still less complex than the ones detected in the control condition, but for some participants they are similar to the first ones, including numerous illustrator gestures.
This exploratory study gave results which are in line with findings from our previous studies (Zurloni et al., 2013, 2015), and with the picture described by analyzing existent literature (DePaulo et al., 2003; Sporer and Schwandt, 2007; Vrij, 2008; Burgoon et al., 2014, 2015). Overall, THEME proves to be an effective tool for discriminating truth-telling and deceptive reports in manipulated cognitive load conditions, and the dual-task procedure seems to be effective in this sense. Differences that are not detectable in terms of single cues emerged within the structure of behavior, which, as we have discussed, seems to result less rich and more stereotypical in deception.
Limits and Future Directions
This work had its main limitations in size and characteristics of the sample but it allows us to proceed in further research, aiming at testing directional hypotheses and confirming these findings. A stratified sampling and a longer observation period will be crucial to enhance the validity of all data extracted by THEME software. The procedure used to assign participants to conditions was meant to make the groups as equivalent as possible, despite the small sample size, but may have provoked biases according to personal characteristics of participants, for instance their motivation level (generally, the participants who enroll first to an experiment are also the most motivated). Manual coding could be an obstacle due to time-consuming practices and may have had negative effects on data quality. New technologies can help with this issue, with automatic data quality control integrated within the observation software (e.g., Castañer et al., 2017) or automatic extraction of relevant data from the source [even motor information, such as facial expressions, gestures and movement, etc. (Zhang, 2012)]. Common examples are motion capture devices like Kinect (e.g., Yu et al., 2011) wearable sensors for the extraction of biofeedback data or unobtrusive techniques like thermal imaging (Pavlidis et al., 2002; Dcosta et al., 2015). Machine learning algorithms, for example (Bartlett et al., 2005) can extract information from video or audio sources and process them through advanced algorithms that can automatically code facial expressions, body movement, typical gestures, emotions, glance direction and tone of speech. All this cues, if collected in a systematic manner, give access to a large-scale analysis, both from an observational and a statistical point of view. THEME software can work with all kind of data or events detected in a particular moment in time, making the potential applications to include a large range of sources. The experimental procedure could be improved, for example adding a naïve interlocutor and considering the interaction as moderator of behaviors. The observation instrument built for this study could be enriched with behavior cues from other systems, such as head movements or facial expressions; although, it is fundamental to keep a balance between the exhaustivity of observed behaviors and the interpretability of results.
Impact
Deception is a ubiquitous phenomenon, regulated by the same processes used in “standard” communication. Furthermore, lying implicates an additional use of cognitive resources which, in “low stakes” conditions (low risk, low gain), common to daily life and to which humans are more “practiced,” is an insignificant (or at least, not currently measurable) amount. We believe that, with cognitive approaches, a step forward was made in studying deception as a standard communication phenomenon: manipulating cognitive load allows unveiling differences otherwise inaccessible to analysis, because they are usually intrinsic to communication processes. In our experiment, THEME software was able to detect differences in behavior structure when the cognitive load experienced from participants was the highest. Although these findings need to be confirmed (a physiologic and a self-report measure of the cognitive effort could be important), it would be interesting to explore if the intrinsic higher cognitive load characterizing high-stakes deception could be enough to allow a detection without manipulation. If proved, the transferability and application of this methodology in real life contexts could be easier and potentially include several research and interventions areas, such as public security monitoring (frontiers, airports, stations, etc., Burgoon et al., 2014) or the detection of illegal and/or dangerous behaviors, for instance doping in sport (Zurloni et al., 2015).
Ethics Statement
At the time we collected data for this study, the IRB approval, in our institution, was not mandatory for minimum-risk studies. For this reason, the present study was conducted according with the ethical principles stated by the Association of Italian Psychologists and the general principles stated in The Federal Policy for the Protection of Human Subjects (or the “Common Rule”), defining “minimum” the risk in which “the probability and magnitude of harm or discomfort anticipated in the research are not greater in and of themselves than those ordinarily encountered in daily life or during the performance of routine physical or psychological examinations or tests” (45 CFR 46.102). The literature agrees in considering low-stakes deception to be a daily-life phenomenon.
Author Contributions
BD and VZ contributed in method development, study designing, data analysis, and paper writing. ME contributed in data acquisition and coding, data analysis, and paper writing. CC contributed in study designing and data acquisition and coding. OR contributed in study designing and data analysis. GJ contributed in method development and data analysis. MTA contributed in method development and paper writing. All authors made suggestions and critical reviews to the initial draft and contributed to its improvement until reaching the final manuscript, which was read and approved by all authors.
Conflict of Interest Statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
The handling Editor declared a shared affiliation, though no other collaboration, with one of the authors CC.
Acknowledgments
The authors are gratefully acknowledge the support of two Spanish government projects (Ministerio de Economía y Competitividad): (1) La Actividad Física y el Deporte Como Potenciadores del Estilo de Vida Saludable: Evaluación del Comportamiento Deportivo Desde Metodologías No Intrusivas [Grant No. DEP2015-66069-P, MINECO/FEDER, UE]; (2) Avances Metodológicos y Tecnológicos en el Estudio Observacional del Comportamiento Deportivo [Grant No. PSI2015-71947-REDP, MINECO/FEDER, UE]. In addition, they thank the support of the Generalitat de Catalunya Research Group, GRUP DE RECERCA I INNOVACIÓ EN DISSENYS (GRID). Tecnología i Aplicació Multimedia i Digital als Dissenys Observacionals [Grant No. 2017 SGR 1405]. Lastly, MTA also acknowledge the support of University of Barcelona (Vice-Chancellorship of Doctorate and Research Promotion).
Footnotes
- ^ http://patternvision.com/
- ^ http://patternvision.com/
- ^ How to read the pattern tree graph: the left box of Figures 5–8 shows the events occurring within the pattern, listed in the order in which they occur within the pattern. The first event in the pattern appears at the top and the last at the bottom. The lower right box shows the frequency of events within the pattern, each dot means that an event has been coded. The pattern diagram (the lines connecting the dots) shows the connection between events. The number of pattern diagrams illustrates how often the pattern occurs. Sub-patterns also occur when some of the events within the pattern occur without the whole of the pattern occurring. The upper box illustrates the real-time of the pattern. The lines show the connections between events, when they take place and how much time passes between each event.
References
Anolli, L., Balconi, M., and Ciceri, R. (2002). Deceptive miscommunication theory (DeMiT): a new model for the analysis of deceptive communication. Emerg. Commun. 3, 73–100.
Anolli, L., and Zurloni, V. (2009). Cooperative and non cooperative lies in close and casual relationships. Stud. Commun. Sci. 9, 7–25.
Baddeley, A. (1992). Working memory: the interface between memory and cognition. J. Cogn. Neurosci. 4, 281–288. doi: 10.1162/jocn.1992.4.3.281
Baddeley, A. D., and Hitch, G. (1974). Working memory. Psychol. Learn. Motiv. 8, 47–89. doi: 10.1016/S0079-7421(08)60452-1
Bakeman, R., and Quera, V. (1995). Analyzing Interaction: Sequential Analysis with SDIS and GSEQ. Cambridge: Cambridge University Press.
Bartlett, M. S., Littlewort, G., Frank, M., Lainscsek, C., Fasel, I., and Movellan, J. (2005). “Recognizing facial expression: machine learning and application to spontaneous behavior,” in Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Vol. 2 (Piscataway, NY: IEEE), 568–573.
Buller, D. B., and Burgoon, J. K. (1996). Interpersonal deception theory. Commun. Theory 6, 203–242. doi: 10.1111/j.1468-2885.1996.tb00127.x
Burgoon, J. K., Proudfoot, J. G., Schuetzler, R., and Wilson, D. (2014). Patterns of nonverbal behavior associated with truth and deception: illustrations from three experiments. J. Nonverb. Behav. 38, 325–354. doi: 10.1007/s10919-014-0181-5
Burgoon, J. K., Schuetzler, R., and Wilson, D. W. (2015). Kinesic patterning in deceptive and truthful interactions. J. Nonverb. Behav. 39, 1–24. doi: 10.1007/s10919-014-0190-4
Camerino, O. F., Chaverri, J., Anguera, M. T., and Jonsson, G. K. (2012). Dynamics of the game in soccer: detection of T-patterns. Eur. J. Sport Sci. 12, 216–224. doi: 10.1080/17461391.2011.566362
Casarrubea, M., Jonsson, G. K., Faulisi, F., Sorbera, F., Di Giovanni, G., Benigno, A., et al. (2015). T-pattern analysis for the study of temporal structure of animal and human behavior: a comprehensive review. J. Neurosci. Methods 239, 34–46. doi: 10.1016/j.jneumeth.2014.09.024
Caso, L., Maricchiolo, F., Bonaiuto, M., Vrij, A., and Mann, S. (2006). The impact of deception and suspicion on different hand movements. J. Nonverb. Behav. 30, 1–19. doi: 10.1007/s10919-005-0001-z
Castañer, M., Barreira, D., Camerino, O., Anguera, M. T., Fernandes, T., and Hileno, R. (2017). Mastery in goal scoring, T-pattern detection, and polar coordinate analysis of motor skills used by Lionel Messi and Cristiano Ronaldo. Front. Psychol. 8:741. doi: 10.3389/fpsyg.2017.00741
Castañer, M., Torrents, C., Anguera, M. T., Dinušová, M., and Jonsson, G. K. (2009). Identifying and analyzing motor skill responses in body movement and dance. Behav. Res. Methods 41, 857–867. doi: 10.3758/BRM.41.3.857
Cavalera, C., Diana, B., Elia, M., Jonsson, G. K., Zurloni, V., and Anguera, M. T. (2015). T-pattern analysis in soccer games: relationship between time and attack actions. Cuad. Psicol. Deporte 15, 41–50. doi: 10.4321/S1578-84232015000100004
Davis, M., Markus, K. A., Walters, S. B., Vorus, N., and Connors, B. (2005). Behavioral cues to deception vs. topic incriminating potential in criminal confessions. Law Hum. Behav. 29, 683–704. doi: 10.1007/s10979-005-7370-z
Dcosta, M., Shastri, D., Vilalta, R., Burgoon, J. K., and Pavlidis, I. (2015). “Perinasal indicators of deceptive behavior,” in Proceedings of the 11th IEEE International Conference and Workshops on Automatic Face and Gesture Recognition (FG), Vol. 1, (Ljubljana: IEEE), 1–8.
DePaulo, B. M., Kashy, D. A., Kirkendol, S. E., Wyer, M. M., and Epstein, J. A. (1996). Lying in everyday life. J. Pers. Soc. Psychol. 70, 979–995. doi: 10.1037/0022-3514.70.5.979
DePaulo, B. M., and Kirkendol, S. E. (1989). “The motivational impairment effect in the communication of deception,” in Credibility Assessment, ed. J. C. Yuille (Dordrecht: Kluwer Academic), 51–69.
DePaulo, B. M., Lindsay, J. J., Malone, B. E., Muhlenbruck, L., Charlton, K., and Cooper, H. (2003). Cues to deception. Psychol. Bull. 129, 74–118. doi: 10.1037/0033-2909.129.1.74
DePaulo, B. M., Zuckerman, M., and Rosenthal, R. (1980). Detecting deception: modality effects. Rev. Pers. Soc. Psychol. 1, 125–162. doi: 10.1016/j.ijpsycho.2016.04.010
Diana, B., Elia, M., Zurloni, V., Elia, A., Maisto, A., and Pelosi, S. (2015). “Multimodal deception detection,” in Proceedings of the ACM on Workshop on Multimodal Deception Detection, (New York, NY: ACM Press), 21–28. doi: 10.1145/2823465.2823466
Diana, B., Zurloni, V., Elia, M., Cavalera, C. M., Jonsson, G. K., and Anguera, M. T. (2017). How game location affects soccer performance: T-pattern analysis of attack actions in home and away matches. Front. Psychol. 8:1415. doi: 10.3389/fpsyg.2017.01415
Eibl-Eibesfeldt, I. (1970). Ethology. The Biology of Behavior. New York, NY: Holt, Rinehart and Winston Inc.
Frank, M. G., and Ekman, P. (1997). The ability to detect deceit generalizes across different types of high-stake lies. J. Pers. Soc. Psychol. 72, 1429–1439. doi: 10.1037/0022-3514.72.6.1429
George, J. F., and Robb, A. (2008). Deception and computer-mediated communication in daily life. Commun. Rep. 21, 92–103. doi: 10.1080/08934210802298108
Hancock, J. T., Thom-Santelli, J., and Ritchie, T. (2004). “Deception and design: the impact of communication technology on lying behavior,” in Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, (New York, NY: ACM), 129–134.
Heilveil, I., and Muehleman, J. T. (1981). Nonverbal clues to deception in a psychotherapy analogue. Psychother. Theory Res. Pract. 18, 329–335. doi: 10.1037/h0088382
Jensen, M. L., Meservy, T. O., Burgoon, J. K., and Nunamaker, J. F. Jr. (2010). Automatic, multimodal evaluation of human interaction. Group Decis. Negot. 19, 367–389. doi: 10.1007/s10726-009-9171-0
Kassin, S. M. (2005). On the psychology of confessions: does innocence put innocents at risk? Am. Psychol. 60, 215–228. doi: 10.1037/0003-066X.60.3.215
Kassin, S. M., and Norwick, R. J. (2004). Why people waive their Miranda rights. Law Hum. Behav. 28, 211–221. doi: 10.1023/B:LAHU.0000022323.74584.f5
Kerepesi, A., Jonsson, G. K., Miklósi,Á, Topál, J., Csányi, V., and Magnusson, M. S. (2005). Detection of temporal patterns in dog–human interaction. Behav. Processes 70, 69–79. doi: 10.1016/j.beproc.2005.04.006
Magnusson, M. S. (2000). Discovering hidden time patterns in behavior: T-patterns and their detection. Beha. Res. Methods Instrum. Comput. 32, 93–110. doi: 10.3758/BF03200792
Magnusson, M. S. (2005). “Understanding social interaction: discovering hidden structure with model and algorithms,” in The Hidden Structure of Interaction: From Neurons to Culture Patterns, eds L. Anolli, G. Riva, S. Duncan, and M. S. Magnusson (Amsterdam: IOS Press), 3–22.
Magnusson, M. S. (2006). “Structure and communication in interaction,” in From Communication to Presence: Cognition, Emotions and Culture Towards the Ultimate Communicative Experience. Festschrift in Honor of Luigi Anolli, eds G. Riva, M. T. Anguera, B. K. Wiederhold, and F. Mantovani (Amsterdam: IOS Press), 127–146.
Mammarella, I. C., Toso, C., Pazzaglia, F., and Cornoldi, C. (2008). BVS-Corsi. Batteria per la valutazione della memoria visiva e spaziale. Con CD-ROM. Trento: Edizioni Erickson.
McCornack, S. (1997). “The generation of deceptive messages: laying the groundwork for a viable theory of interpersonal deception,” in Message Production: Advances of Communication theory, ed. J. O. Greene (Mahwah, NJ: Erlbaum), 91–126.
Meyer, D. E., and Kieras, D. E. (1997). A computational theory of human multiple-task performance: the EPIC information-processing architecture and strategic response deferment model. Psychol. Rev. 104, 1–65.
Meyer, D. E., Kieras, D. E., Lauber, E., Schumacher, E. H., Glass, J., Zurbriggen, E., et al. (2002). “Adaptive executive control: flexible multiple-task performance without pervasive immutable response-selection bottlenecks,” in Cognitive Modeling, eds T. A. Polk, A. Thad, and C. M. Seifert (Cambridge, MA: MIT Press), 101–128.
Noldus, L. P., Trienes, R. J., Hendriksen, A. H., Jansen, H., and Jansen, R. G. (2000). The Observer video-pro: new software for the collection, management, and presentation of time-structured data from videotapes and digital media files. Behav. Res. Methods Instrum. Comput. 32, 197–206. doi: 10.3758/BF03200802
Noldus, L. P. J. J. (1991). The Observer: a software system for collection and analysis of observational data. Behav. Res. Methods Instrum. Comput. 23, 415–429. doi: 10.3758/BF03203406
O’Sullivan, M. (2003). The fundamental attribution error in detecting deception: the boy-who-cried-wolf effect. Pers. Soc. Psychol. Bull. 29, 1316–1327. doi: 10.1177/0146167203254610
Pavlidis, I., Eberhardt, N. L., and Levine, J. A. (2002). Human behaviour: seeing through the face of deception. Nature 415, 35–35. doi: 10.1038/415035a
Riva, G., Zurloni, V., and Anolli, L. (2005). “Patient-therapist communication in computer assisted environment,” in The Hidden Structure of Interaction. From Neurons to Culture Patterns, eds L. M. Anolli, S. Duncan, M. S. Magnusson, and G. Riva (Amsterdam: IOS Press), 159–177.
Serota, K. B., Levine, T. R., and Boster, F. J. (2010). The prevalence of lying in America: three studies of self-reported lies. Hum. Commun. Res. 36, 2–25. doi: 10.1111/j.1468-2958.2009.01366.x
Spielberger, C. (1983). Manual for the State-Trait Anxiety Inventory STAI (form Y). Palo Alto, CA: Consulting Psychologists Press.
Sporer, S. L., and Schwandt, B. (2007). Paraverbal indicators of deception: a meta-analytic synthesis. Appl. Cogn. Psychol. 20, 421–446. doi: 10.1002/acp.1190
Trivers, R. (2011). The Folly of Fools: The Logic of Deceit and Self-Deception in Human Life. New York, NY: Basic Books.
Tsiamyrtzis, P., Dowdall, J., Shastri, D., Pavlidis, I. T., Frank, M. G., and Ekman, P. (2007). Imaging facial physiology for the detection of deceit. Int. J. Comput. Vis. 71, 197–214. doi: 10.1007/s11263-006-6106-y
Turner, R. E., Edgley, C., and Olmstead, G. (1975). Information control in conversations: honesty is not always the best policy. Kans. J. Soc. 11, 69–89. doi: 10.17161/STR.1808.6098
Urbaniak, G. C., and Plous, S. (2013). Research Randomizer (Version 4.0) [Computer software]. Available at: http://www.randomizer.org/ Retrieved on [accessed June 22, 2013].
Van Merrienboer, J. J., and Sweller, J. (2005). Cognitive load theory and complex learning: recent developments and future directions. Edu. Psychol. Rev. 17, 147–177. doi: 10.1007/s10648-005-3951-0
Vrij, A. (2008). Detecting Lies and Deceit: Pitfalls and Opportunities. Chichester: John Wiley & Sons.
Vrij, A., Akehurst, L., Soukara, S., and Bull, R. (2004). Detecting deceit via analyses of verbal and nonverbal behavior in children and adults. Hum. Commun. Res. 30, 8–41. doi: 10.1111/j.1468-2958.2004.tb00723.x
Vrij, A., Edward, K., Roberts, K. P., and Bull, R. (2000). Detecting deceit via analysis of verbal and nonverbal behavior. J. Nonverbal Behav. 24, 239–263. doi: 10.1023/A:1006610329284
Vrij, A., Fisher, R., Mann, S., and Leal, S. (2006). Detecting deception by manipulating cognitive load. Trends Cogn. Sci. 10, 141–142. doi: 10.1016/j.tics.2006.02.003
Vrij, A., Fisher, R. P., and Blank, H. (2017). A cognitive approach to lie detection: a meta-analysis. Legal Criminol. Psychol. 22, 1–21. doi: 10.1111/lcrp.12088
Vrij, A., Granhag, P. A., Mann, S., and Leal, S. (2011). Outsmarting the liars: toward a cognitive lie detection approach. Curr. Dir. Psychol. Sci. 20, 28–32. doi: 10.1177/0963721410391245
Vrij, A., Mann, S. A., Fisher, R. P., Leal, S., Milne, R., and Bull, R. (2008). Increasing cognitive load to facilitate lie detection: the benefit of recalling an event in reverse order. Law Hum. Behav. 32, 253–265. doi: 10.1007/s10979-007-9103-y
Walczyk, J. J., Igou, F. P., Dixon, A. P., and Tcholakian, T. (2013). Advancing lie detection by inducing cognitive load on liars: a review of relevant theories and techniques guided by lessons from polygraph-based approaches. Front. Psychol. 4:14. doi: 10.3389/fpsyg.2013.00014
Wilcoxon, F. (1945). Individual comparisons by ranking methods. Biom. Bull. 1, 80–83. doi: 10.2307/3001968
Yu, X., Wu, L., Liu, Q., and Zhou, H. (2011). “Children tantrum behaviour analysis based on Kinect sensor,” in Proceedings of the 3rd Conference on Intelligent Visual Surveillance, (Beijing: IEEE), 49–52.
Zhang, Z. (2012). Microsoft kinect sensor and its effect. Multimed. IEEE 19, 4–10. doi: 10.1109/MMUL.2012.24
Zuckerman, M., DePaulo, B., and Rosenthal, R. (1981). “Verbal and nonverbal communication of deception,” in Advances in Experimental Social Psychology, Vol. 14, ed. L. Berkowitz (New York, NY: Academic Press), 1–57.
Zurloni, V., Diana, B., Cavalera, C., Argenton, L., Elia, M., and Mantovani, F. (2015). Deceptive behavior in doping related interviews: the case of Lance Armstrong. Psychol. Sport and Exerc. 16, 191–200. doi: 10.1016/j.psychsport.2014.02.008
Zurloni, V., Diana, B., and Elia, M. (2013). “Imposing cognitive load to unmask prepared lies a temporal pattern detection approach,” in Proceedings of the 10th IEEE International Conference and Workshops on Automatic Face and Gesture Recognition, (Shanghai: IEEE), 1–6. doi: 10.1109/FG.2013.6553801
Zurloni, V., Diana, B., Elia, M., and Anolli, L. (2016). “Imposing cognitive load to detect prepared lies: a T-pattern approach,” in Discovering Hidden Temporal Patterns in Behavior and Interaction: T-Pattern Detection and Analysis with THEME, eds M. S. Magnusson, J. K. Burgoon, and M. Casarrubea (Basel: Springer International Publishing), 63–82.
Keywords: deception detection, cognitive load manipulation, kinesics, analysis of observational data, T-patterns
Citation: Diana B, Zurloni V, Elia M, Cavalera C, Realdon O, Jonsson GK and Anguera MT (2018) T-Pattern Analysis and Cognitive Load Manipulation to Detect Low-Stake Lies: An Exploratory Study. Front. Psychol. 9:257. doi: 10.3389/fpsyg.2018.00257
Received: 16 January 2017; Accepted: 16 February 2018;
Published: 02 March 2018.
Edited by:
Pietro Cipresso, Istituto Auxologico Italiano (IRCCS), ItalyReviewed by:
Colin Robert Muirhead, Independent Researcher, United KingdomIoannis Pavlidis, University of Houston, United States
Copyright © 2018 Diana, Zurloni, Elia, Cavalera, Realdon, Jonsson and Anguera. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Valentino Zurloni, dmFsZW50aW5vLnp1cmxvbmlAdW5pbWliLml0
 Barbara Diana
Barbara Diana Valentino Zurloni
Valentino Zurloni Massimiliano Elia
Massimiliano Elia Cesare Cavalera
Cesare Cavalera Olivia Realdon
Olivia Realdon Gudberg K. Jonsson
Gudberg K. Jonsson M. Teresa Anguera
M. Teresa Anguera