
95% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Phys. , 18 March 2025
Sec. Interdisciplinary Physics
Volume 13 - 2025 | https://doi.org/10.3389/fphy.2025.1535906
The interference environment faced by GNSS receivers is unknown, dynamic, and uncertain, making it difficult for a single interference mitigation method to address all interference threats. In this paper, we introduce an intelligent interference mitigation approach. By leveraging a deep learning network model, our method automatically selects the optimal interference mitigation technique based on the specific characteristics of the interference. This enhances the receiver’s anti-jamming performance and overall robustness. Our experimental results show that the proposed method effectively suppresses narrowband interference, pulse interference, and chirp interference, demonstrating insensitivity to interference parameters. Statistically, it outperforms traditional methods, with the proportion of the carrier-to-noise ratio (C/N0) above a given threshold (initial C/N0 reduced by 3 dB) increasing by over 10%.
Global Navigation Satellite Systems (GNSS) provide users with positioning, velocity, and timing (PVT) services. It is the only positioning and navigation system that offers high precision, global coverage, and all-weather availability. After decades of development, GNSS has been widely and deeply applied across various sectors.
Because GNSS plays a fundamental and key role in military, commercial and civil fields, its vulnerability has also received more and more attention. As we all know, the power of the signal emitted by the navigation satellite is very weak when it reaches the ground, and GNSS users are extremely vulnerable to radio frequency interference and spoofing attacks [1, 2]. Studies have shown that [3] an interference source with a radiation power of only 1 W can render GNSS receivers within a range of approximately 15 km unable to function properly.
Radio frequency interference can be categorized into unintentional and intentional interference. Unintentional interference is generally caused by spectrum leakage or improper operation of radar or communication systems adjacent to the navigation frequency band. Intentional interference is typically used to attack an opponent’s navigation equipment or to protect one’s privacy [4]. Typical GNSS interference includes continuous wave interference, narrowband interference, pulse interference, sweep chirp interference and broadband interference [5–7]. The impact of different types of interference on GNSS receivers can be quantitatively characterized by the equivalent C/N0 [8].
To address the threat of radio frequency interference, researchers have proposed a series of interference suppression methods. The basic principle is similar: utilizing the sparsity of interference in a certain dimension to detect and eliminate it. For example, due to the sparsity of continuous wave interference and narrowband interference in the frequency domain, Frequency Domain Pulse Blanking (FDPB) and Adaptive Filtering (AF) [9–12] have been proposed for suppression. In light of the sparsity of pulse interference in the time domain, Time Domain Pulse Blanking (TDPB) [13, 14] has been proposed for suppression. For chirp interference, it has been found that [15, 16] it also exhibits time-domain sparsity within a specific sweep frequency range, allowing it to be suppressed by setting the time-domain pulse to zero. Broadband interference is unique in that it does not exhibit sparsity in either the time or frequency domains; it must be received by an array antenna or polarized antenna to demonstrate sparsity in the spatial or polarization domain for suppression. This paper does not address broadband interference.
The interference mitigation method of radio frequency has been a topic not only in electronics but also in space and astrophysics. Among these, deep learning methods were already employed. References [17–19] investigate how to detect and identify radio-frequency interference using deep learning methods, which have achieved good results in the field of radio interferometry. However, these methods do not provide further approaches for interference cancellation or signal recovery. References [20, 21] study the use of Bayesian methods to eliminate interference and restore signals. This method performs well under the condition that the prior distribution of the data is known. However, the interference faced by GNSS receiver is unknown, dynamic, and uncertain. Moreover, under different types of interference, the data exhibit different probability distributions. Therefore, it is difficult to directly apply this method in GNSS interference mitigation. For a given type of interference, different mitigation methods yield varying suppression effects. This paper aims to design an interference mitigation method that not only identifies interference, but also automatically selects the optimal approach to suppress interference based on its characteristics, thereby enhancing the performance and robustness of the receiver. This method is referred to as the intelligent interference mitigation (IIM) method.
The innovative contributions of this paper can be summarized as follows: (a) We propose a GNSS IIM method that utilizes spectrum sensing to convert input data into spectrograms, followed by the application of a deep learning network to output the optimal interference mitigation method. (b) We present an implementation framework for the IIM method, which employs Short Time Fourier Transform (STFT) for time-frequency two-dimensional spectral sensing, with GoogLeNet chosen as the pre-trained model to build our deep learning network. (c) Finally, we conduct experiments using a data collector and a software-defined receiver (SDR) for interference mitigation and signal processing to evaluate the performance of the proposed method under various interference conditions. The results demonstrate the effectiveness of the proposed method and its ability to mitigate different types of interfering signals.
The content of this article is organized as follows: Section 2 establishes the signal model for the GNSS receiver; Section 3 introduces three typical GNSS interference mitigation methods—FDPB, AF, and TDPB—and analyzes their interference suppression effects. Section 4 proposes the basic principles and implementation framework of the GNSS IIM method. Sections 5, 6 design simulations and open-sky experiments to verify the performance of the proposed method. Finally, the main conclusions drawn from this study are presented.
For the sake of simplicity, we consider the reception of a single GNSS satellite signal due to the very low cross-correlation of the pseudorandom spreading codes. The signal received by a GNSS receiver, after being amplified, down-converted, filtered, and sampled, can be expressed in complex baseband form as:
Where
Where
When the receiver adopts active interference mitigation processing, the generalized interference mitigation process can be modeled by Equation 3 as follows:
In Equation 4,
After that, the receiver further performs correlation despreading on the anti-jamming output. The goal is to estimate the Doppler frequency shift and pseudo-code phase of the GNSS signal. This process can be achieved by maximizing the ambiguity function [8]:
In Equation 4,
The purpose of anti-jamming is to suppress the interfering signals and retain the useful signal to the greatest extent. The effect can be evaluated by the C/N0 after correlation dispreading, which can be described by Equation 5 as follows:
where
Without considering special forms of receiving antennas such as array antennas or polarized antennas, conventional GNSS receivers employ three representative interference mitigation methods: FDPB, AF, or TDPB. The following sections introduce each method separately.
The FDPB method first transforms the signal into the frequency domain through discrete Fourier transform (DFT):
In Equation 6,
Borio et al. [9] proposes a more robust method:
In Equation 7,
Finally, the interference eliminated spectrum is transformed back from the frequency domain to the time domain through inverse discrete Fourier transform (IDFT) to obtain interference mitigation output, which can be described by Equation 8:
AF can be achieved using finite impulse response (FIR) or infinite impulse response (IIR) filters, which can adaptively adjust coefficients based on certain algorithms and automatically form zeros in the frequency band where interference occurs, thereby achieving interference suppression. Considering that FIR filters are more robust than IIR filters, this paper adopts adaptive FIR filters.
Assuming the length of the FIR filter is L, the signal filtered by the FIR filter can be described as [11]:
In Equation 9,
The coefficients of the FIR filter can be updated using the Normalized Least-Mean-Square (NLMS) algorithm [11]:
In Equation 10,
The TDPB directly processes the sampled data, and the threshold-free method is also used here. The process can be described by Equation 11 as follows [9]:
We have constructed a MATLAB simulation platform consisting of a signal generator and a SDR, employing the Monte Carlo simulation method to analyze the performance of interference suppression. The analysis focuses on the effectiveness of traditional anti-jamming methods against three types of interference: narrowband (continuous wave interference can be considered as a special form of narrowband interference), pulse, and chirp. The configuration of the simulation platform is illustrated in the Figure 1.
The main parameter settings in the simulation are shown in the table below.
Set the narrowband interference bandwidth to be randomly distributed between 0 and 4 MHz (20% signal bandwidth), simulate narrowband interference with different bandwidths, and use three methods of FDPB, AF, and TDPB for interference mitigation processing. Conduct 500 Monte Carlo experiments, obtain 500 samples, and statistically analyze the output C/N0. The results are as follows:
Figure 2A shows the C/N0 results of the first 30 experiments in 500 Monte Carlo simulations. It can be seen that the interference suppression performance of the AF algorithm is similar to that of the FDPB algorithm. The C/N0 obtained by the AF algorithm is slightly higher than that of the FDPB algorithm in most cases, but also slightly lower than that of the FDPB algorithm in a few samples. The TDPB algorithm has a poor suppression effect on narrowband interference, and its output C/N0 is generally lower than 30 dB Hz. Figure 2B shows the statistical results of 500 Monte Carlo experiments, with the horizontal axis representing the C/N0 threshold and the vertical axis representing the proportion of experiments with a C/N0 exceeding the given threshold to the total number of experiments. Figure 2B statistically illustrates that the AF algorithm has the best suppression effect on narrowband interference, followed by the FDPB algorithm and the TDPB algorithm.
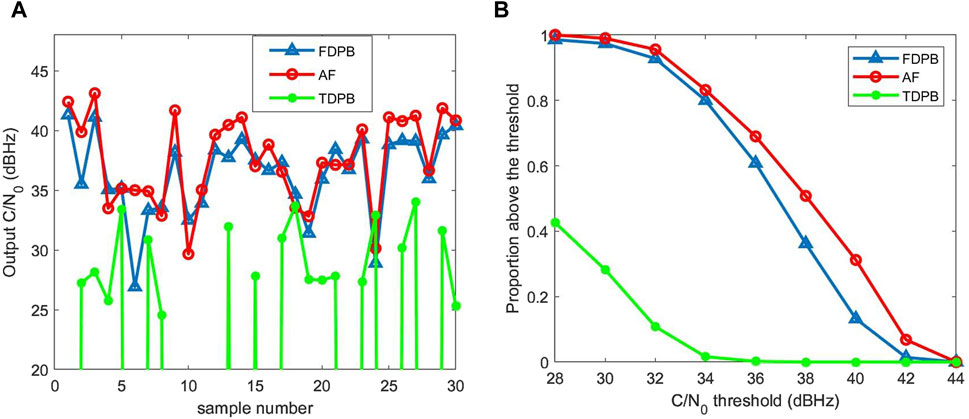
Figure 2. Comparison of narrowband interference suppression performance. (A) C/N0 results of the first 30 experiments. (B) Statistical results of C/N0 of 500 experiments.
The pulse repetition period of pulse interference is randomly distributed between 0.04 and 1 ms, and the duty cycle is randomly distributed between 0 and 0.4 (Gaussian band-limited noise modulated within pulse signals). The bandwidth covers the entire front-end bandwidth of the receiver (20 MHz). The Monte Carlo experimental results are shown in Figure 3, indicating that statistically speaking, the TDPB algorithm has the best performance for pulse interference, followed by the FDPB algorithm, and the AF algorithm has the worst performance.
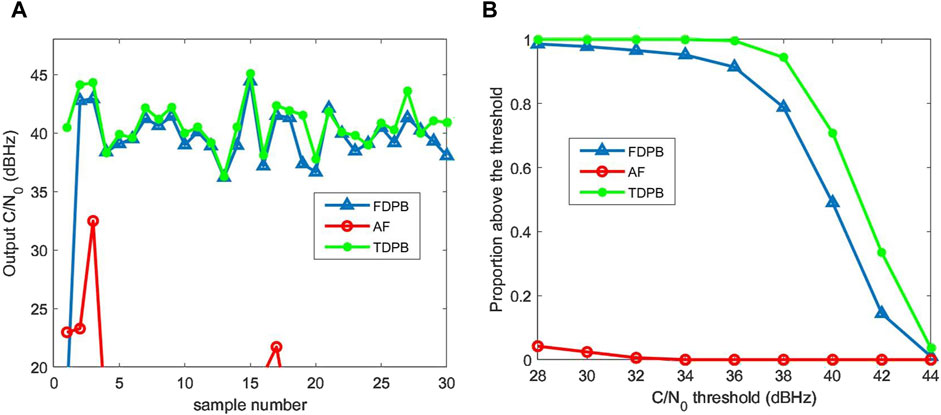
Figure 3. Comparison of pulse interference suppression performance. (A) C/N0 results of the first 30 experiments. (B) Statistical results of C/N0 of 500 experiments.
The sweep bandwidth of the chirp interference is randomly distributed between 4 and 20 MHz, and the sweep period is randomly distributed between 0.01 and 1 ms. The Monte Carlo experimental results are shown in Figure 4. At this time, statistically speaking, the TDPB algorithm has the worst performance. When the C/N0 threshold is less than 42 dB Hz, the FDPB algorithm performs better than the AF algorithm, but when the C/N0 threshold is greater than 42 dB Hz, the AF algorithm performs better than the FDPB algorithm.
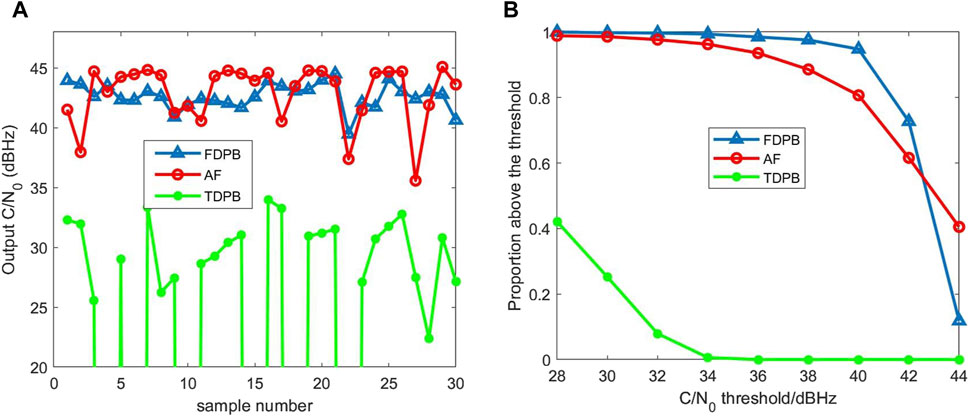
Figure 4. Comparison of chirp interference suppression performance. (A) C/N0 results of the first 30 experiments. (B) Statistical results of C/N0 of 500 experiments.
From the above analysis, it can be seen that for different types of interference, the optimal interference mitigation method in a statistical sense is different. For example, the AF algorithm has the best suppression performance for narrowband interference, and the TDPB algorithm has the best suppression performance for pulse interference. On the other hand, it is not difficult to see from Figures 1A, 2A, 3A that even for the same type of interference with different interference parameters, the optimal interference mitigation method is not the same.
Considering that the interference environment faced by the receiver is unknown, dynamic, and uncertain, this paper proposes an IIM method, which automatically selects the optimal method to suppress interference based on the characteristics of interference, thereby improving the interference mitigation performance and robustness of the receiver.
The schematic diagram of the IIM method is shown in Figure 5. The input for IIM is the digital complex baseband signal received by the GNSS antenna and processed by signal conditioning (including amplification, frequency conversion, filtering, and sampling quantization). On one hand, the IIM processing performs three types of interference mitigation processing on the signal: FDPB, AF, and TDPB; On the other hand, it performs two-dimensional spectrum perception on the input signal. The deep learning network outputs the optimal method among the three anti-jamming processing based on the two-dimensional time-frequency spectrum and controls the switch to direct the output of the optimal anti-jamming method to signal acquisition, tracking, and PVT solution processing.
Different types of interference or different parameters of the same interference will result in different time-frequency two-dimensional spectra, which means that the differences in interference types and parameters will be reflected in the time-frequency two-dimensional spectra. Therefore, a deep learning network can be constructed to automatically select the optimal interference mitigation method based on the time-frequency two-dimensional spectrum of the input signal. During the training stage, for each input sample, by traversing three interference mitigation methods, the corresponding output C/N0 can be obtained. The interference mitigation method with the highest output C/N0 is selected as the output (or label) of the deep learning network. After the network is trained, the network architecture and weights are fixed. During the deployment stage, the deep learning network automatically selects the optimal interference mitigation method based on the input interference type and parameters, and sends its interference mitigation output to subsequent processing through switch switching.
The purpose of time-frequency two-dimensional spectrum sensing is to unfold the digital complex baseband signal after signal conditioning in the time-frequency two-dimensional plane. When there is interference, the unfolded time-frequency two-dimensional spectrum will reflect the type and parameters of interference.
This paper uses STFT to achieve time-frequency two-dimensional spectral sensing, and the process can be described by Equation 12 as follows [22]:
where
Figure 6 shows a sample of time-frequency two-dimensional spectra obtained for narrowband interference, pulse interference, and chirp interference. Each time-frequency image is in RGB format, with a size of 224 × 224 × 3.
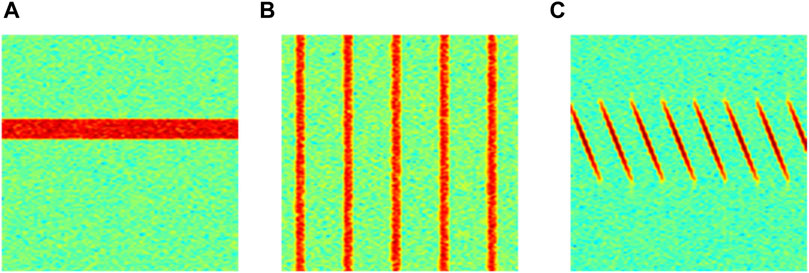
Figure 6. Time frequency two-dimensional spectra of different interference types. (A) Narrowband interference. (B) Pulse interference. (C) Chirp interference.
Using pre-trained deep learning networks for optimal interference mitigation method selection, pre-trained network are deep learning networks that have been trained in millions of natural images and have good image feature extraction capabilities. When applied to the specialized field of GNSS IIM, only a small number of samples are needed to fine tune the pre trained network.
The selection of pre-training network should strike a balance between recognition performance (recognition accuracy) and resource consumption (recognition time). In this paper, GoogLeNet [23] is used as the pre-trained network model. GoogLeNet connects multiple well-designed Inception blocks in series with other layers (convolutional layer, fully connected layer) to form a 22-layer deep network. GoogLeNet was once one of the most effective models on ImageNet: it provides high recognition accuracy with low computational complexity.
Firstly, based on the simulation platform in Section 3, the Monte Carlo simulation method is used to generate sample data. The specific generation process is as follows: the signal received by the GNSS receiver is generated according to the signal model in Formula 1, and the global parameter settings are shown in Table 1. The parameters of the three types of interference are consistent with Section 3.4. 1,000 samples are generated under each interference, and a sample set containing 3,000 samples is generated in total. For each sample, by traversing three interference mitigation methods, one can obtain their respective output C/N0. The interference mitigation method with the highest output C/N0 is selected as the label for the sample.
The entire sample set is divided into three parts: 2,400 samples are used as the training set (800 samples for each disturbance), 300 samples are used as the verification set (100 samples for each disturbance), and 300 samples are used as the test set (100 samples for each disturbance), so 80% of the whole sample is used for training, and 20% is used for verification and testing.
The experiment utilizes the PyTorch [24] deep learning framework to complete the model construction, training and testing. The hyperparameters of the neural network are set as follows: the optimizer selects Adam; the learning rate is set to 0.001; the batch size is set to 20; the maximum number of training epoch is set to 10; and the loss function is cross entropy loss.
Load the trained network model into the IIM method proposed in Section 4, validate it on the test set, and compare it with three traditional interference mitigation methods. The comparison results of interference mitigation performance are shown in Figure 7.
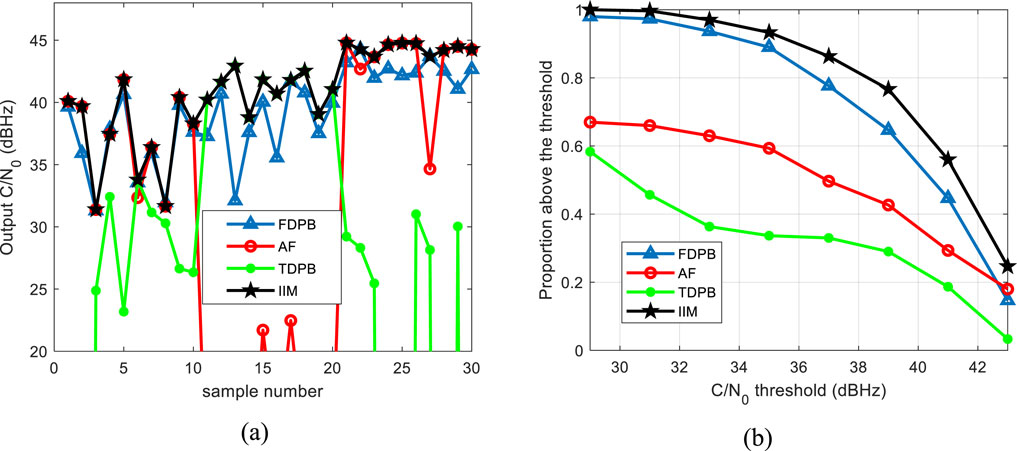
Figure 7. Comparison of interference suppression performance between proposed method and traditional methods. (A) C/N0 results of the first 30 experiments. (B) Statistical results of C/N0 on the entire test set.
Figure 7A shows the C/N0 results obtained from the first 30 samples in the test set (including 10 narrowband interference, 10 pulse interference, and 10 chirp interference samples each). It can be seen that traditional interference mitigation methods have good suppression effects on one or two types of interference, but it is difficult to achieve good suppression effects on all three types of interference at the same time. However, the IIM method proposed in this paper can achieve this. Although the output C/N0 obtained by the IIM method is not the highest on individual samples (because there is also a probability of errors in the prediction results of the network model), overall, the output C/N0 obtained by it is the highest in most cases. Figure 7B shows the statistical results on the entire test set. It can be seen from the figure that the IIM method is the optimal interference mitigation method in a statistical sense, and the proportion of the C/N0 above a given threshold (In engineering applications, it is generally agreed that the initial C/N0 reduced by 3 dB is used as the threshold.) is more than 12% higher than traditional methods.
It should be particularly noted that, compared to traditional methods, IIM incorporates a spectrum sensing module and a deep learning network. The introduction of the deep learning network significantly increases the computational complexity by thousands of times. As a result, a dedicated GPU chip must be added specifically to accelerate the inference process of the deep learning model. Additionally, the inference process of the deep learning model introduces an extra processing latency of several milliseconds. The increase in computational complexity and processing latency limits the deployment of IIM in low-cost and real-time demanding GNSS receivers.
To further verify the proposed method, an open sky experiment is carried out. In this test, an antenna array based data collector is placed at a fixed position in the open wild for GNSS signal collection, while interfering signals are simulated and added in our SDR. This method is often used in GNSS jamming experiments [25, 26] to avoid impacting civil GNSS users. The open sky experiment configuration is shown in Figure 8.
The data collector includes 7 antennas, a front-end, an A/D converter, and a lighting port output. It should be mentioned that only data from antenna 1 (i.e., the center antenna) is used in our experiment. The output baseband data (sampling frequency is 62/3 MHz and duration is 2,300 ms) of the data collector are stored on a personal computer (PC) and processed by the SDR.
For the SDR, firstly, interference signals are generated and added to the baseband data at 1,000 ms, the parameters of the three types of interference signals are consistent with Section 3.4. For each type of interference, 30 random samples are generated, totaling 90 samples. For each sample, the SDR is used for processing, and the performance of different interference mitigation methods is compared.
Figure 9 shows the processing results of the SDR for the B3I signal (PRN 1) under sweep chirp interference (ISR is 64.53 dB, sweep bandwidth is 16.27 MHz, and sweep period is 0.935 ms). It can be observed that before the interference is turned on (0–1000 ms), with direct pass-through processing, the output C/N0 is around 43 dB Hz. After applying the IIM algorithm, the output C/N0 is slightly lower than that of the direct pass-through processing, due to the insertion loss introduced by the interference mitigation processing. After the interference is turned on (1000 ms–2300 ms), the output C/N0 of the direct pass-through processing drops rapidly, and the receiver loses track of the signal, while the output C/N0 of the IIM algorithm remains essentially unchanged, allowing the receiver to maintain normal tracking of the signal, as seen in Figure 10.
Figure 11 compares the time-frequency diagrams of the output signals obtained from direct pass-through and IIM. It can be seen that after applying IIM processing, the power of the chirp interference is significantly reduced, with a power level similar to that of the surrounding thermal noise, indicating that the IIM algorithm effectively suppresses the interference.
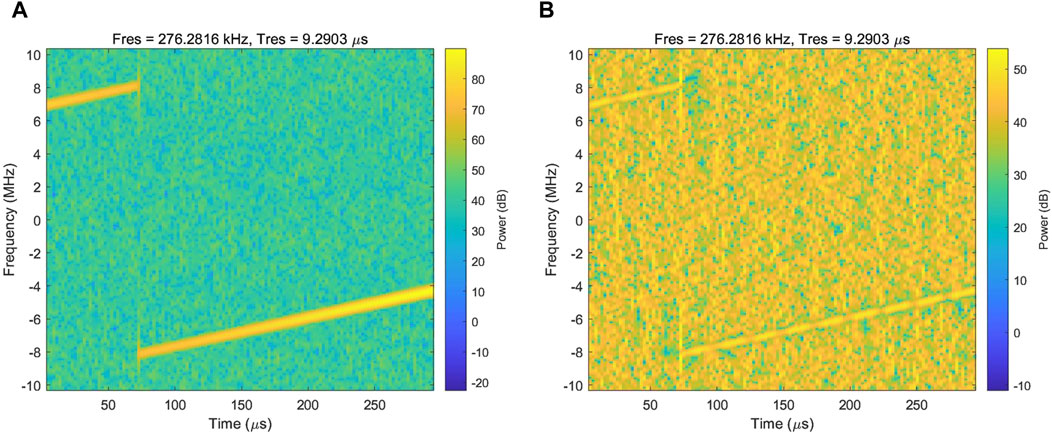
Figure 11. Interference mitigation performance for IIM. (A) Time-frequency diagrams of the output signals obtained from direct pass-through. (B) Time-frequency diagrams of the output signals obtained from IIM.
Finally, Figure 12 presents the statistical results across all 90 sample sets. For each sample, we take the average of the output C/N0 results after the interference is turned on (with a duration of 1.3 s) as the final output C/N0 result. It can be observed from the figure that the IIM method is statistically the optimal method, with its proportion above the threshold (initial C/N0 minus 3 dB, i.e., 40 dB Hz) being more than 16% higher than that of traditional methods. This result is basically consistent with the outcomes derived from the simulation, with only minor differences in specific numerical values.
This article examines the interference challenges encountered by GNSS receivers and introduces a deep learning-based approach for GNSS interference mitigation. The method begins by analyzing the input signal in a two-dimensional spectrogram and then employs a deep learning network to determine the optimal strategy among three interference mitigation algorithms. The selected optimal interference mitigation strategy is subsequently conveyed to the signal capture tracking and PVT calculation processes via a switching mechanism. Compared to traditional interference mitigation techniques, the method outlined in this paper is capable of adapting to various types of interference and different interference parameters, demonstrating effective suppression across a range of interference scenarios. Simulation and open-sky experimental results have confirmed the efficacy of this approach.
In conclusion, the proposed technique is a potent interference mitigation tool that can substantially broaden the operational range of GNSS receivers under interference conditions. Future enhancements could focus on reducing computational complexity and enhancing performance in scenarios with multiple concurrent interference signals.
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
FC: Writing–original draft. ZL: Writing–review and editing. LH: Writing–review and editing. YX: Writing–review and editing. BR: Writing–review and editing. QZ: Writing–review and editing.
The author(s) declare that financial support was received for the research, authorship, and/or publication of this article. This research was supported in part by the Natural Science Foundation of China (NSFC), grants No. 62303475 and U20A20193.
The authors would like to thank the editors and reviewers for their efforts in supporting the publication of this paper.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
The author(s) declare that no Generative AI was used in the creation of this manuscript.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
1. Ren B, Chen F, Ni S, Han C, Lu Z, Han S. Performance analysis of repeater spoofing suppression based on GNSS multi-beam receiver. Front Phys (2022) 10:970132. doi:10.3389/fphy.2022.970132
2. Ni S, Binbin R, Chen F, Lu Z, Wang J, Ma P, et al. GNSS spoofing suppression based on multi-satellite and multi-channel array processing. Front Phys (2022) 10:905918. doi:10.3389/fphy.2022.905918
3. Chen F. GNSS antenna array receiver interference suppression and measurement deviation compensation technology. Changsha: National University of Defense Technology (2017).
4. Gao GX, Sgammini M, Lu M, Kubo N. Protecting GNSS receivers from jamming and interference. Proc IEEE (2016) 104(6):1327–38. doi:10.1109/JPROC.2016.2525938
5. Morales Ferre R, de la Fuente A, Lohan ES. Jammer classification in GNSS bands via machine learning algorithms. Sensors (2019) 19(22):4841. doi:10.3390/s19224841
6. Morales Ferre R, Richter P, Falletti E, Fuente ADL, Lohan ES. A survey on coping with integral interference in satellite navigation for manned and unmanned aerial. IEEE Commun Surveys&Tutorials (2020) 22(1):249–91. doi:10.1109/COMST.2019.2949178
7. Wang P, Cetin E, Dempster A, Wang Y, Wu S. GNSS interference detection using statistical analysis in the time frequency domain. IEEE Trans Areospace Electron Syst (2018) 54(1):416–28. doi:10.1109/TAES.2017.2760658
8. Kaplan ED, Yanhong K. Principles and applications of GPS. 2nd ed. Beijing: Electronic Industry Press (2007).
9. Borio D, Gioia C. GNSS interference mitigation: a measurement and position domain assessment. NAVIGATION: J Inst Navigation (2021) 68(1):93–114. doi:10.1002/navi.391
10. Borio D, Camorano L, Presti LL. Two pole and multi pole notch filters: a computationally effective solution for GNSS interference de-tection and mitigation. IEEE Syst J (2008) 2(1):38–47. doi:10.1109/JSYST.2007.914780
11. Song J, Lu Z, Xiao Z, Li B, Sun G. Optimal order of time domain adaptive filter for anti jamming navigation receiver. Remote Sensing (2021) 14(1):48. doi:10.3390/rs14010048
12. Fan G, Huang Y, Su Y, Li J, Sun G. A reduced bias delay lock loop for adap-tive filters. Advancements Space Res (2017) 59(1):230–5. doi:10.1016/j.asr.2016.09.007
13. Huo S, Nie J, Wang F. Block flow noise power estimation algorithm for pulse interference detection of GNSS receivers. Electronics Lett (2015) 51(19):1522–4. doi:10.1049/el.2015.1445
14. Danielle B, Pau C. Complex signal non linearity for robust GNSS interference mitigation. IET Radar, Sonar&Navigation (2018) 12(8):900–9. doi:10.1049/iet-rsn.2017.0552
15. Chen F, Liu Z, Huang L, Lu Z. Low complexity suppression method for fast sweep interference in satellite navigation receivers. J Natl Univ Defense Technology (2023) 45(5):105–10. doi:10.11887/j.cn.202305012
16. Borio D. Swept GNSS jamming mitigation through pulse Blanking. In: 2016 European navigation conference (ENC). IEEE (2016). p. 1–8. doi:10.1109/EURONAV.2016.7530549
17. Akeret J, Chang C, Lucchi A, Refregier A. Radio Frequency Interference mitigation using deep convolutional neural networks. Astron Comput (2016) 18:35–9. doi:10.1016/j.ascom.2017.01.002
18. Alireza VS, Bassett BA, Nadeem O, Yabebal F, Chris F. Deep learning improves identification of radio frequency interference. Monthly Notices R Astronomical Soc (2020)(1) 1. doi:10.1093/mnras/staa2724
19. Haomin S, Hui D, Feng W, Ying M, Tingting X, Oleg S, et al. A robust RFI identification for radio interferometry based on a convolutional neural network. Monthly Notices R Astronomical Soc (2022)(2) 2. doi:10.1093/mnras/stac570
20. Kennedy F, Bull P, Wilensky MJ, Burba J, Choudhuri S. Statistical recovery of 21 cm visibilities and their power spectra with Gaussian-constrained realizations and gibbs sampling. IOP Publishing Ltd (2023). doi:10.3847/1538-4365/acc324
21. Leeney SAK, Handley WJ, Acedo EDL. Bayesian approach to radio frequency interference mitigation. Phys Rev (2023) 108(6 Pt.A):062006. doi:10.1103/physrevd.108.062006
22. Ouyang X, Amin MG. Short-time fourier transform receiver for nonstationary interference excision in direct sequence spread spectrum communications. IEEE Trans Signal Process (2001) 49:851–63. doi:10.1109/78.912929
23. Szegedy C, Liu W, Jia Y, Sermanet P, Reed S, Anguelov D, et al. Going deeper with convolutions. In: Proceedings of the IEEE conference on computer vision and pattern recognition (2015). USA. 18-20 June 1996. p. 1–9.
24. Paszke A, Lerer A, Killeen T, Antiga L, Yang E, Tejani A, et al. PyTorch: an imperative style, high-performance deep learning library. In: Advances in neural information processing systems 32, volume 11 of 20: 32nd conference on neural information processing systems (NeurIPS 2019). (2020) Vancouver (CA), December 8-14, 2019.
25. Xie Y, Chen F, Huang L, Liu Z, Wang F. Carrier phase bias correction for GNSS space-time array processing using time-delay data. GPS Solutions (2023) 27(3):113. doi:10.1007/s10291-023-01456-y
Keywords: satellite navigation, interference mitigation, deep learning, receiver, interfering signals
Citation: Chen F, Liu Z, Huang L, Xie Y, Ren B and Zhou Q (2025) GNSS interference mitigation method based on deep learning. Front. Phys. 13:1535906. doi: 10.3389/fphy.2025.1535906
Received: 29 November 2024; Accepted: 19 February 2025;
Published: 18 March 2025.
Edited by:
Riccardo Meucci, National Research Council (CNR), ItalyReviewed by:
Sunita Khichar, Chulalongkorn University, ThailandCopyright © 2025 Chen, Liu, Huang, Xie, Ren and Zhou. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zhe Liu, bF96QG51ZHQuZWR1LmNu
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.