
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Phys., 22 December 2023
Sec. Interdisciplinary Physics
Volume 11 - 2023 | https://doi.org/10.3389/fphy.2023.1331072
This article is part of the Research TopicLong-Range Dependent Processes: Theory and Applications, Volume IIView all 6 articles
The routing protocol of wildlife monitoring Wi-Fi (Wireless Fidelity) networks cannot balance node energy consumption, leading to early node death. Therefore, the research on energy balance in wildlife monitoring Wi-Fi networks is a hot topic. In order to balance the energy consumption of Wi-Fi networks and extend the lifespan of wireless networks, we designed the low energy dynamic routing protocol LEACH-EP (Low Energy Adaptive Clustering Hierarchy- Energy Prediction) based on energy prediction by analyzing the long-range dependent characteristics of the remaining energy time series (RETS) of wireless network nodes. This protocol uses the LSTM (Long Short-Term Memory) model to predict the remaining energy of network nodes, and then dynamically plans routes using future remaining energy. We conducted a networking experiment in the Anzihe Nature Reserve in Chengdu, China, and the Energy Balance Factor index of the wireless network significantly improved. The Mean Absolute Error value of network nodes is less than 60 mW, which is less than 10% of the average daily energy consumption of nodes. Half of the surviving network nodes have achieved an increase to 55.2%, and the network death time has been extended by 38.6%. The experimental results show that the energy prediction routing protocol LEACH-EP can significantly extend the node survival life and balance network energy consumption.
Wildlife is a precious ecological resource bestowed upon humans by nature and an important component of the ecosystem. Strengthening the protection of wildlife species is an urgent task for the entire society [1]. Researchers collect information on the number, behavior, distribution, ecological environment, and other aspects of wildlife through wireless sensor networks (WSNs) deployed in the wild. It can achieve tracking and early warning of wildlife, providing scientific basis and decision-making support for wildlife protection. This method does not require manual data collection, but it also has problems such as low transmission bandwidth and inability to provide timely feedback [2–8], and cannot collect video and image data captured by infrared cameras.
The Northeast China Tiger and Leopard National Park used to combine cable television with an infrared camera network, but the network transmission bandwidth was not high [9, 10]. Yu Zhouyan [11] uses Zigbee and 3G networks to transmit wildlife data. The system can remotely and automatically monitor wildlife, but is not capable of transmitting wildlife video. The wireless sensor networks in [12–15] also have similar drawbacks.
Karunanithy et al. [16] used WSN and IOT technology to track wildlife and identify their territory, quantity, and behavior. The disadvantage of this system is that it can only collect location information. Wotherspoon et al. [17] used a 433 MHz wireless Lo-Ra module, which can transmit up to 5,500 m of wireless network transmission distance at a power of 20 dBm and has a packet loss rate of only 2%. The disadvantage of this system is that it cannot transmit images and videos. Camacho et al. [18] used a 900 MHz radio frequency network to establish an infrared camera network in the rainforest. Data was collected through drones, and the distance between adjacent sensor nodes in this network was only a few tens of meters. Giordano et al. [19] proposed a farmland protection monitoring system that uses a Wi-Fi gateway to transmit node data to the internet. The distance between network nodes and base stations can reach 500 m, but the system has high power consumption.
Wi-Fi wireless monitoring networks have solved the bandwidth problem of video transmission, but there are still several problems: 1) High energy consumption of Wi-Fi transmission; 2) Difficult to remotely control and unable to provide timely feedback on device status; 3) Unable to adapt to changes in node energy consumption, nodes die prematurely, and network lifespan is not long.
Therefore, we need to establish a new Wi-Fi routing mechanism to balance the energy consumption of Wi-Fi networks, in order to reduce Wi-Fi network power consumption, extend service life, and improve the performance of Wi-Fi networks in complex outdoor environments.
Generally, we classify WSN routing protocols into two categories: flat routing and hierarchical routing [20]. The flat routing protocol is simple and robust, but the network latency is high and the response speed is slow. Typical planar routing protocols include Rumor [21], SPIN [22], and SAR [23]. The hierarchical routing protocol belongs to the cluster routing protocol, and typical cluster routing protocols include PEGASIS [24], LEACH [25], HEED [26], etc.
Cluster routing technology meets the needs of WSN in data collection, environmental monitoring, energy consumption balancing, and is currently one of the main research directions of WSN. Heinzelman et al. [25] proposed an adaptive, low-power WSN routing protocol LEACH, which lays the foundation for WSN layered protocols. In cluster routing, cluster head election is a key issue. The HEED [26] protocol uses probabilistic methods to generate pre-selected cluster heads, and nodes compete within the cluster to generate cluster heads.
By using this method, a more uniform cluster head can be obtained, but it incurs a large cost of cluster head election. The LEACH-C [27] protocol optimizes cluster head selection through base stations and transfers node election costs to base stations. The PEGASIS [24] protocol considers WSN as a chain topology at the beginning of a chain, which can easily lead to early cluster head death. The MMR [28] protocol layers nodes based on their distance from the base station, selecting secondary and primary cluster heads in different layers. The LEACH-X [29] protocol modifies the cluster head election threshold function based on the current remaining energy of nodes, without considering the future energy consumption of the network.
Due to these clustering low-power routing protocols selecting cluster heads and updating routes based on lagged and fixed energy information within an election cycle. Therefore, it is unable to respond to the latest energy changes of nodes in a timely manner, which leads to imbalanced network energy consumption, premature consumption of network node energy, and premature death of wireless transmission networks.
Therefore, existing clustering routing protocols cannot meet the needs of wildlife monitoring wireless networks, and more optimized low-power routing algorithms must be designed in conjunction with wildlife monitoring environments. We propose a Wi-Fi dynamic routing algorithm LEACH-EP based on energy prediction by analyzing the long-range dependent characteristics of the remaining energy time series (RETS) of network nodes. This routing algorithm introduces predictive energy into Wi-Fi routing planning, enabling its routing structure to reflect the current and future changes in energy consumption of the network, balancing the overall energy consumption of the Wi-Fi network. This routing algorithm can better balance the energy consumption of network nodes, extend the service life of the network, and improve the stability of the field WSN.
The Wi-Fi network structure is shown in Figure 1, which is based on the Lo-Ra network. Due to the high power consumption of Wi-Fi networks, the communication link is only opened during data transmission. When users retrieve data from infrared camera nodes, the server calculates the optimal path from the base station to the node through a routing protocol and sends control commands to open the corresponding network node. Due to the limited communication distance between individual Wi-Fi nodes in the monitoring area, the network may require multi-level relay stations (Sinks) to reach the terminal nodes.
The optimal path routing protocol LEACH-EP (Low Energy Adaptive Clustering Hierarchy Energy Prediction) for our designed Wi-Fi network considers the residual energy of network nodes as a time series with long-range dependent characteristics. The residual energy of network nodes in the future is predicted through Long Short Term Memory Network (LSTM), and the residual energy of network nodes is introduced into the routing cluster head selection function, Network routing protocols can reflect real-time fluctuations in network energy. The Remaining Energy Time Series (RETS) of a network node is composed of the remaining energy values of an infrared camera every half hour, and the design lifespan of a network node with one energy replenishment is greater than 160 days.
Theorem. Let
where,
Proof. Let the mean
Let the autocovariance
where,
The ACF of sequence
Bring Eq. 2.3 into Eq. 2.4, get Eq. 2.5.
This finishes the proof.
Figure 2 show the ACF values of the RETS network nodes. Figures a, b, and c show the daily energy consumption, the RETS, and the ACF values of RETS at 10th node, 20th node,30th node.
If we believe that a time series may be long-rang dependence sequence, then the ACF value of the sequence is greater than zero or has tailing phenomenon [30]. Figure 2C shows that the ACF value of the RETS is greater than zero, which indicates that the RETS may be the long-range dependent sequence.
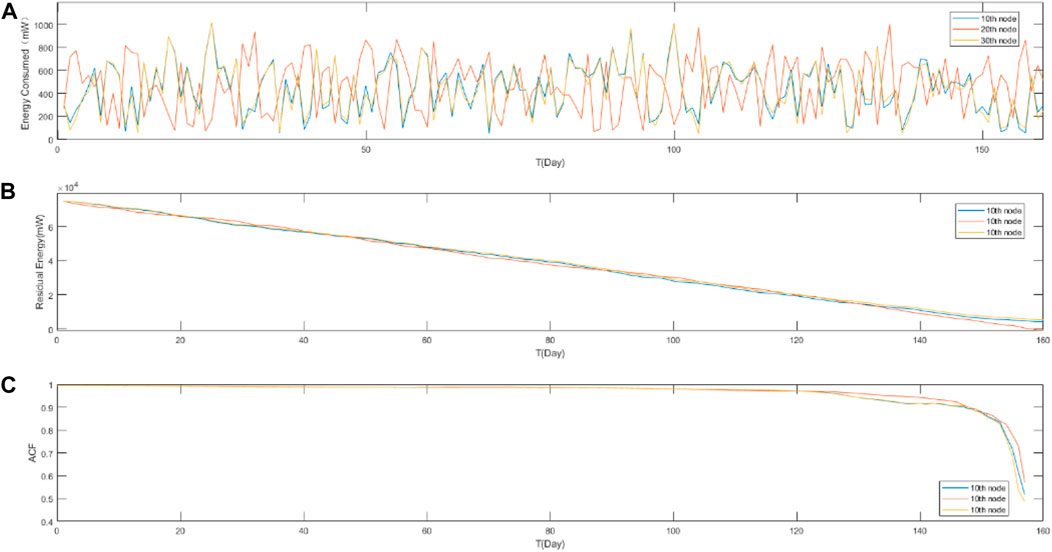
FIGURE 2. The ACF values of the RETS of network nodes at 10th node, at 20th node, at 30th node. (A) The daily energy consumption, (B) The RETS, (C) The ACF values of RETS.
Hurst exponent (
When 0.5 < H < 1, according to the fractional Gaussian noise model, time series data has long-range dependence [32].
Through the analysis in Section 2.2, we can see that the RETS sequence may have long-range dependence. Next, we use the r/s method to calculate the H index and further determine that RETS has long-range dependence [33]. The calculation process is as follows:
1. Divide the sequence
2. Calculate the mean value
3. Calculated deviation
4. Calculate cumulative deviation
5. Calculate range
6. Calculate standard deviation
7. Get value
The average value
Finally,
Figure 3 shows the
From Figure 3, we can see that the
In order to better verify the long-range dependent characteristics of the RETS sequence of infrared cameras, we calculated the Hurst index of the RETS sequence of infrared camera nodes, as shown in Figure 4. The Hurst index of each node RETS sequence is close to 1, indicating that the daily RETS sequence of infrared camera nodes has good long-term memory characteristics, and the daily residual energy of infrared camer nodes can be predicted.
The Long Short Term Memory (LSTM) [34] model has been widely used in time series prediction, with unique advantages in dealing with long-range dependency problems and capturing nonlinear relationships. And it alleviates the problem of gradient vanishing caused by backpropagation during training. Therefore, we use LSTM to predict the remaining energy of network nodes in the future. The prediction model consists of an LSTM layer, a fully connected layer, a Dropout layer, and a fully connected layer. The residual energy prediction network model is shown in Figure 5.
In the training set, a sliding window is used to partition the training set, as shown in Figure 6. The size of the training set window X for the prediction task is m, and the label is the remaining energy of the node at time T. Predict the remaining energy of nodes at the future T+1 time using the remaining energy of the last m T time nodes. The model predicts the remaining energy E of network nodes after time T+1 by moving a sliding window.
We construct a new routing algorithm LEACH-EP based on the LEACH routing protocol and the predicted residual energy of network nodes. Firstly, the cluster head is selected based on the remaining energy of the current node in the next day as the main factor; Then, based on the distance between nodes and cluster heads, network nodes are clustered. When transmitting data from network nodes, the distance between ordinary nodes and Sink nodes is considered. Within a limited distance range, network nodes directly transmit data to the aggregation node, further saving energy consumption and improving data transmission efficiency.
The LEACH-EP algorithm process is shown in Figure 7, and the specific steps are as follows.
1) Calculate the distance
where,
2) Use LSTM to predict the remaining energy
where,
3) Calculate the threshold
where,
4) The node will generate a random number of [0,1]. If the random number is less than this threshold
5) After all cluster heads are selected, the LoRa network broadcasts the location information of all cluster head nodes. The remaining ordinary nodes select the closest cluster head to enter the cluster based on the distance information S, and record their own identification as the identification number of the cluster head.
6) All nodes have completed clustering and transitioned to the data transmission phase. Compared to the distance between the cluster head and the Sink node, ordinary nodes within the cluster can directly transmit data to the Sink node if the distance to the Sink node is smaller. This reduces the consumption of network energy.
7) The cluster head node receives data from non cluster head nodes within the cluster, and sends the data to the Sink node after calculation and fusion. After running one round in this stage, proceed to the next round, proceed to step 2), and calculate the average remaining energy
Due to the maximum Wi-Fi communication distance of the infrared camera node being less than 100 m. The Sink node has photovoltaic power generation, and its energy can be infinitely large. At the same time, in order to verify the networking capability of routing protocols in outdoor environments. Therefore, in areas that cannot be covered by 5G signals, infrared cameras are deployed in a single or multi hop manner, communicating with Sink nodes through Wi-Fi.
So, the site for the field experiment is located in the Anzihe Nature Reserve in Sichuan, China. The nodes of the field infrared camera network are distributed in an area of 4,000 m
The Mean Absolute Error (MAE) indicator reflects the average change in the distance between the predicted values of the model and the true values of the sample, and has the characteristics of insensitivity to outliers and inclusiveness.
We use the MAE index to evaluate the accuracy of residual energy prediction for infrared camera nodes, as shown in formula 5.1.
where,
We use the LSTM model from Section 3 to predict the remaining energy data of infrared cameras. The infrared camera captures the remaining energy every 10 min, and the remaining energy of each life form a time series of remaining energy in the infrared camera. Conduct two rounds of experiments on 50 infrared cameras to form the training set data for the remaining energy time series (RETS). The dataset contains 100 remaining energy time series samples, each with a total of 25,920 points. The parameter T of the LSTM model is set to 10 days, and the sliding window size is set to 20. The model starts from the 1440th data of each sequence and predicts the remaining energy of T+1 for the next day.
Figure 9 shows the actual and predicted residual energy values of the 10th infrared camera node, while Figure 10 shows the MAE curves of between predicted residual energy values and actual residual energy values of all nodes in the network. It can be seen that the MAE value is less than 60mW, which is less than 10% of the average daily energy consumption of nodes, indicating that it can timely reflect changes in network energy consumption.
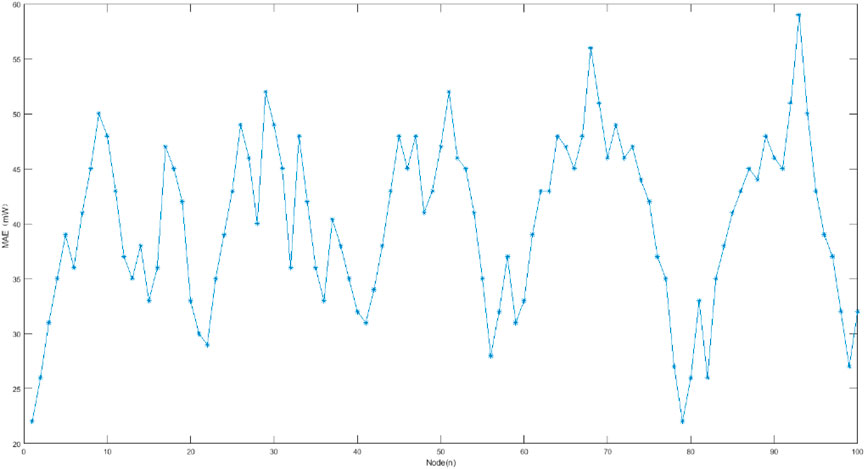
FIGURE 10. The deviation curve between the predicted residual energy values of all nodes in the network and the true residual energy values.
In infrared camera wireless networks, once the camera node runs out of energy, the node cannot do any work, and it may also affect the transmission of data by other nodes. Therefore, this article compares the changes in the number of surviving nodes over time in the network under three protocols: LEACH [25], LEACH-X [29], and LEACH-EP. Figure 11 shows the curve of the number of surviving nodes in the network over time.
From Figure 11, it can be seen that the LEACH protocol had the first node die on the day 64th, the surviving nodes were less than 50 on the day 84th, and all nodes died on the day 98th; The LEACH-X protocol causes the first node to die on the 82nd day, with 50 surviving nodes on the 109th day, and all nodes dying on the 134th day; LEACH-EP died on the first node on the 99th day, half of the nodes on the 166th day, and all nodes on the 191th day. Compared with LEACH and LEACH-X algorithms, the LEACH-EP algorithm has a greater number of surviving nodes in routing at all times, and its routing energy balance advantage is obvious.
Compared with the LEACH-X algorithm, the LEACH-EP algorithm has a delay of approximately 55.2% and 31.5% when the network energy loss is 50%; When the network energy loss is 95%, the LEACH-EP algorithm has a delay of approximately 68.8% and 38.6%.
The Energy Balance Factor (EBF) index can reflect the fluctuations of the residual energy sequence. We use the EBF indicator to evaluate the overall energy balance performance of the network. EBF is shown in formula 5.2.
Where
The EBF indicator measures the balance of energy consumption of sensor nodes by observing the changes in energy consumption factors over time. The smaller the EBF value, the stronger the routing protocol’s ability to balance energy consumption. As shown in Figure 12, without energy prediction, the EBF of LEACH-X and LEACH-EP remain consistent; After 45 days, the EBF curve of LEACH-EP is below that of LEACH-X, indicating that LEACH-EP can better balance network energy consumption; As time goes on, the EBF curve of LEACH-X rapidly decreases as nodes gradually die, and the predicted route EBF changes relatively smoothly, indicating that LEACH-EP nodes have a longer survival time.
Due to the fact that the infrared camera Wi-Fi network does not require the establishment of a downlink network from the base station to the camera node, we only measure uplink data transmission. The relationship between the data received by the base stations of the LEACH, LEACH-X, and LEACH-EP algorithms is shown in Figure 13.
From the three curves in Figure 13, it can be seen that the data volume of the LEACH algorithm no longer changes in less than 80 days, the data volume of the LEACH-X algorithm no longer changes in less than 110 days, and the LEACH-EP algorithm reaches 161 days. By analyzing the total data volume of the LEACH-EP and LEACH-X routing protocols, we can find that the data volume of LEACH-EP is more than 20 times that of the LEACH-X algorithm. It can be seen that the network life cycle using the LEACH-EP protocol is longer, and the overall network sends more data. Therefore, the LEACH-EP algorithm is more optimized overall than the LEACH-X algorithm.
In order to reduce Wi-Fi network power consumption, extend service life, and improve the performance of Wi-Fi networks in complex outdoor environments. To ensure reliable and stable operation of the infrared camera wireless network and balance network energy consumption, we have designed a Wi-Fi dynamic routing based on energy prediction.
We first analyzed the long-term memory characteristics of the residual energy sequence of infrared cameras using the Hurst index, and then used the LSTM prediction model to predict the residual energy of network nodes. Finally, the predicted remaining energy is fed back into the LEACH-EP routing protocol to achieve dynamic routing planning.
We conducted a LEACH-EP networking experiment in the Anzihe Nature Reserve in Sichuan, China, testing the number of Wi-Fi network data transfers and network lifetime indicators. The wireless network constructed using LEACH-EP achieved a 55.2% improvement in the survival of half of the network nodes, a 38.6% extension in network death time, and a significant improvement in data throughput. Experiments have shown that energy prediction routing effectively prolongs node survival time and balances network energy consumption. These indicate that our proposed routing protocol LEACH-EP has significant advantages and is more suitable for field monitoring scenarios.
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
YS: Writing–original draft, Methodology, and Software. PZ: Writing–original draft, Data curation, Investigation, Supervision, Validation. TH: Writing–reviewing and editing, Visualization, Resources. HS: Writing–review and editing, Conceptualization, Methodology, Validation, and Writing commentary.
The author(s) declare financial support was received for the research, authorship, and/or publication of this article. This research is supported by the Science and Technology Program of Guangdong (2018B030333001) and the Chengdu Research Base of Giant Panda Breeding (NO. 2020CPB-C09, NO. CPB2018-01).
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
1. Wang Y. Study on the evaluation of wildlife protection value. Harbin: Northeast Forestry University (2018). p. 1–4.
2. Xue Y, Li D, Sun Z, Yuan H. Using satellite tracking collars to monitor released captive-bred wild Bactrian camels. Acta Theriologica Sinica (2017) 37(04):336–43. doi:10.16829/j.slxb.201704003
3. Gor M, Vora J, Tanwar S, Tyagi S, Sadoun B. GATA: GPS-Arduino based tracking and alarm system for protection of wildlife animals. In: Proceedings of the 2017 International Conference on Computer; July 2017; Dalian, China (2017). p. 3630–3.
4. Shafiq M, Ashraf H, Ullah A, Tahira S. Systematic literature review on energy efficient routing schemes in WSN–a survey. Mobile Networks Appl (2020) 25(1):882–95. doi:10.1007/s11036-020-01523-5
5. Osamah I, Khalaf AG. Energy efficient routing and reliable data transmission protocol in WSN. Int J Adv Soft Compu (2020) 12(3):45–53. doi:10.30534/ijatcse/2021/1491032021
6. Zeng Z, Zeng F, Han X, Elkhouchlaa H, Yu Q, Lü E. Real-time monitoring of environmental parameters in a commercial gestating sow house using a zigbee-based wireless sensor network. Appl Sci (2021) 11(3):972. doi:10.3390/app11030972
7. Lianshuai S. Design of wild animal image acquisition system based on wireless sensor network. Beijing: Beijing Forestry University (2020). p. 17–8.
8. Chen S'an. Design of wildlife monitoring system based on wireless image sensor network. Beijing: Beijing Forestry University (2017). p. 7–8.
9. Wang T, Limin F, Yang H, Bao L, Wang H, Ge J. Overview of the Northeast tiger and leopard biodiversity infrared camera monitoring platform. Biodiversity Sci (2020) 28(09):1059–66.
10. Wenli W. Study on the habitat suitability of wild amur tiger and leopard based on remote sensing and GIS. Changchun: Jilin University (2019). p. 1–12.
11. Yu Z. Design and research of wireless multimedia sensor network nodes for wildlife monitoring. Beijing: Beijing Forestry University (2013). p. 13–9.
12. Wang D. Construction and routing optimization of wireless sensor networks based on 6LoWPAN. Suzhou: Suzhou University (2018). p. 9–13.
13. Zhang B. Research on energy-saving algorithms for agricultural wireless sensor networks based on energy balance strategy. Fuzhou: Fujian Agricultural and Forestry University (2022). p. 4–7.
14. Yang D. Research on energy collection and energy conservation strategies of Lo-Ra forestry IoT system. Kunming: Southwest Forestry University (2020). p. 3–7.
15. Ma W. Research on the application of wildlife localization and tracking technology based on wireless sensor networks. Guiyang: Guizhou University (2018). p. 5–6.
16. Karunanithy K, Velusamy B. An efficient data collection using wireless sensor networks and internet of things to monitor the wild animals in the reserved area. Peer-to-Peer Networking Appl (2022) 15(2):1105–25. doi:10.1007/s12083-021-01289-x
17. Wotherspoon J, Wolhuter R, Niesler T. Choosing an integrated radio-frequency module for a wildlife monitoring wireless sensor network. In: Proceedings of the 2017 IEEE AFRICON; September 2017; Cape Town, South Africa (2017). p. 314–9.
18. Camacho L, Baquerizo R, Palomino J, Zarzosa M. Deployment of a set of camera trap networks for wildlife inventory in western amazon rainforest. IEEE Sensors J (2017) 17(23):8000–7. doi:10.1109/jsen.2017.2760254
19. Giordano S, Seitanidis I, Ojo M, Adami D, Vignoli F. IoT solutions for crop protection against wild animal attacks. In: Proceedings of the 2018 IEEE international conference on Environmental Engineering (EE); March 2018; Milan, Italy (2018). p. 1–5.
20. Fu F. Research on energy efficient routing algorithm for wireless sensor networks based on improved LEACH. Lanzhou: Lanzhou Jiaotong University (2021). p. 17–8.
21. Braginsky D, Estrin D. Rumor routing algorthim for sensor networks. New York, USA: the 1st ACM international workshop (2002). p. 22–31.
22. Kulik J, Heinzelman W, Balakrishnan H. Negotiation-based protocols for disseminating information in wireless sensor networks. Wireless Networks (2002) 2(1):8–15. doi:10.1023/A:1013715909417
23. SohrabiGao KJ, Ailawadhi V, Pottie G. Protocols for self-organization of a wireless sensor network. IEEE Personal Commun (2000) 7(5):16–27. doi:10.1109/98.878532
24. Yong-Chang YU, Wei G. An improved PEGASIS algorithm in wireless sensor network. Acta Electronica Sinica (2008) 36(7):1309–13. doi:10.1155/2018/9472075
25. Heinzelman WR, Chandrakasan A, Balakrishnan H. Energy-efficient communication protocol for wireless microsensor networks. Proc 33rd Annu Hawaii Int Conf Syst Sci Maui, HI, USA (2000) 10(2):186–92. doi:10.1109/HICSS.2000.926982
26. Younis O, Fahmy S. HEED: a hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks. IEEE Trans mobile Comput (2004) 3(4):366–79. doi:10.1109/tmc.2004.41
27. Muruganathan SD, Ma D, Bhasin R, Fapojuwo A. A centralized energy-efficient routing protocol for wireless sensor networks. IEEE Commun Mag (2005) 43(3):8–13. doi:10.1109/mcom.2005.1404592
28. Aghera K, Pambhar H, Tada N. Proceedings of international conference on communication and networks. Singapore: Springer (2017). p. 205–14.MMR-LEACH: multi-tier multi-hop routing in LEACH protocol.
29. Jia X, Zhang L. Efficient LEACH algorithm based on energy equalization. Commun Netw (2023) 49(1):63–8. doi:10.16157/j.issn.0258-7998.223052
30. Li M. Fractal time series—a tutorial review. Math Probl Eng (2010) 2010:1–26. doi:10.1155/2010/157264
31. Hurst HE. Long-term storage capacity of reservoirs. Trans Am Soc Civil Eng (1951) 116:770–99. doi:10.1061/taceat.0006518
32. Li M. Modified multifractional Gaussian noise and its application. Physica Scripta (2021) 96(12):125002. doi:10.1088/1402-4896/ac1cf6
33. Li M. Generalized fractional Gaussian noise and its application to traffic modeling. Physica A (2021) 579(22):126138. doi:10.1016/j.physa.2021.126138
Keywords: time series, long-range dependent, dynamic routing algorithm, energy prediction, Hurst exponent, wireless network
Citation: Song Y, Ziyang P, Hui T and Shaoxiang H (2023) A Wi-Fi dynamic routing algorithm based on energy prediction for wildlife monitoring wireless network. Front. Phys. 11:1331072. doi: 10.3389/fphy.2023.1331072
Received: 31 October 2023; Accepted: 07 December 2023;
Published: 22 December 2023.
Edited by:
Ming Li, Zhejiang University, ChinaReviewed by:
Lin Xu, Chengdu University of Traditional Chinese Medicine, ChinaCopyright © 2023 Song, Ziyang, Hui and Shaoxiang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Hu Shaoxiang, aHVzaGFveEAxMjYuY29t
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.