- 1Electric Power Research Institute of Guizhou Power Grid Co, Ltd, Guiyang, China
- 2Guiyang Power Supply Bureau of Guizhou Power Grid Co, Ltd, Guiyang, China
- 3Electric Power Research Institute of China Southern Power Grid, Guangzhou, China
In order to realize the intelligent management of photovoltaic power generation system, wireless sensor network (WSN) is considered as a promised solution. However, the energy of sensor nodes in WSN is limited and the security is not guaranteed. In order to prolong the service life of WSN and to improve the security of monitoring, this paper comprehensively considers the factors those affect the security and efficiency of WSN, such as transmission power, sensor association and the choice of Cluster Head (CH). Therefore, this paper proposes a joint sensor secure rate and energy efficiency optimization algorithm to obtain the optimal topology and transmission power design. Then, an effective iterative algorithm based on Block Coordinate Descent (BCD) technology is proposed to obtain the optimal solution to minimize the energy consumption of WSN and maximize the secure rate of sensor networks, thus ensuring the security and reliability of monitoring. Sensor association is modeled as a 0–1 multi-knapsack optimization problem. Different complexity methods are implemented to solve this NP-hard problem, and their performance are compared with simulations.
1 Introduction
Under the global energy crisis and environmental problems, clean energy has attracted more attention and has become a research hot point in recent years. In this context, the use of light to generate electricity has become more popular. Photovoltaic power generation is a technology that converts light energy into electric energy through photovoltaic effect. Taking photovoltaic power generation as an example, the significance of photovoltaic energy storage for joint participation in electricity market was studied in (Xing et al., 2020), which shows that photovoltaic power generation has a good prospect in the power market.
After 2020, the grid-connected solar photovoltaic system has increased its global cumulative capacity by almost 250 times, exceeding 300 GW by the end of 2016, which is double in 2020 (Jäger-Waldau et al., 2017). In the European Union, renewable energy is also widely used at present, such as photovoltaic panels. The influence of series and parallel resistors on photovoltaic panels is described (Pavlík et al., 2022). Photovoltaic system is one of the fastest growing systems in the world. By smoothly switching the maximum power point tracking mode and Constant Power Generation (CPG) mode, high performance and reliable operation are ensured. The proposed control can be directly applied to the existing photovoltaic system without additional hardware equipment, such as irradiance sensor, which gives up the design of the system by combining sensors in consideration of the cost in the application (Helmers and Bett, 2016; Suryawanshi and Patil, 2019). However, in practical application, the situation that the photovoltaic system does not use sensors at all is relatively limited.
In recent years, more and more sensors are applied to photovoltaic systems in the application of photovoltaic equipment. There are more and more attempts on the application of current sensor in photovoltaic system. For example, in practical application, when more distributed photovoltaic power generation systems are connected to the distribution network, the corresponding current sensor should be selected to detect the current Direct Current (DC) component. Transmitting optical power is a better scheme to supply power for wireless sensor nodes. At the sensor, the light power in the form of monochromatic laser is converted from photovoltaic laser power to electric energy by photovoltaic laser power converter (Zhu et al., 2021).
With the continuous opening of wireless network, the number of wireless terminals is also increasing. How to ensure the security of wireless communication is a problem worth thinking about. Compared with traditional encryption methods, the physical layer of wireless communication generally guarantees security from the perspective of information theory (Hu and Li, 2014; Kong et al., 2019). This paper introduces the security objectives and implementation constraints of wireless sensor networks, summarizes the possible attacks and main defense means of wireless sensor networks, and analyzes various security technologies that are currently hot research topics (Zhu et al., 2008; Kong et al., 2016; Kong et al., 2021). A centralized, secure and low-energy adaptive clustering system is proposed, which uses gateway resources to extend the network life and provide trust management. It provides security, energy efficiency and memory efficiency, and can prevent all kinds of attacks, from spoofed messages to damaged node attacks, and it provides confidentiality (Yang, 2011; Zhong et al., 2019; Zhong et al., 2022).
Based on the above description, a secure communication system for photovoltaic power generation is designed, which collects the voltage and current information of the system through sensors. The Frequency Division Multiple Access (FDMA) method is used to connect the sensor with the base station. The nodes of the model include acquisition node, eavesdropping node and base station. Considering that such a system with more nodes will consume more energy, all the acquisition nodes are clustered. The work of this paper is as follows.
1) This paper analyse the factors that affect the security and efficiency of Wireless sensor network (WSN), such as transmission power, sensor association and the choice of Cluster Heads (CHs). In order to prolong the service life of WSN and to improve the security of monitoring, a joint sensor secure rate and energy efficiency optimization algorithm (TPTCO) is proposed. The optimal topology and transmission power design are obtained.
2) A joint optimization problem of multi-constrained mixed integer programming is proposed, and an effective iterative algorithm based on Block Coodinate Descent (BCD) technology is proposed to obtain the second-best solution to minimize the power consumption of WSN and maximize the secure rate of sensor networks, thus ensuring the security and reliability of monitoring.
3) Topology control is build as a 0–1 multi-knapsack optimization problem. Different complexity methods are put forward to solve this problem, and their performance differences are compared by simulation, so that they can be selected according to the actual needs.
The rest of this paper is organized as follows: Section 2 summarizes the literature review of related work. In Section 3, we introduce the system model of communication model. In Section 4, the formulation and optimization of related problems are put forward. In Section 5, the simulation analysis of the whole system is given.
2 Literature review
Based on the digital signal processing (DSP) chip of the controller, this paper presents the hardware circuit of the control system. Moreover, the circuit can be used normally in areas with strong light. The photovoltaic power generation system includes a driving circuit, a current and voltage sampling circuit, a main circuit DC-DC converter and a protection circuit, and has a micro-pulse transscleral ciliary body photocoagulation function (Kuang et al., 2020). When the photovoltaic power generation device works outdoors for a long time, it is easily disturbed by the external environment, which affects the absorption of solar energy, greatly reduces the power generation efficiency of the device, and also leads to further damage of the device. In order to prevent this problem, a photovoltaic monitoring system is proposed in this paper (Chen et al., 2021). This paper presents a coupling modeling method, which compares the energy consumption of three different vehicles in different places in the integrated photovoltaic system. The method provides the required energy through the battery. A transparent 3D printing package is proposed to prevent the battery from being impacted by the outside world and reduce the battery loss (Ntagios et al., 2020). Complementary metal oxide semiconductor (CMOS) imaging and wearable devices can also be applied in battery biomedicine and wearable devices (Gu et al., 2021). The above results show that photovoltaic systems are widely used in different fields, and sensors are gradually applied in photovoltaic systems (Gu et al., 2021). An optimization model of distributed photovoltaic power generation is proposed. The goal of this model is to punish the cost of distributed photovoltaic power generation (Saffih, 2017).
A photovoltaic power supply model is proposed, which regards the energy consumption of WSN as the energy consumption of photovoltaic energy collector. The low power consumption C O 2 gas sensor is used for simulation analysis (Yue et al., 2017). Generally, the photovoltaic power generation management system based on the Internet of Things will use a third-party platform to manage IoT devices, but the security of the system is poor. In order to improve the flexibility and security of the system, a photovoltaic power generation management system based on narrow-band Internet of Things and a new photovoltaic equipment access protocol are proposed, which uses multi-sensor reporting data analysis rules (Yang and Zhou, 2021). A PV module is proposed, which supplies power to the implanted temperature sensor and is suitable for remote self-powered systems in various applications (Hung et al., 2018).
In the complex power field, intelligent sensors are often used to monitor the status of power equipment, as the core of the monitoring system, but how to supply energy to the sensors is an important problem, which attracts much attention. Solar energy can be easily obtained from the outside world. A photovoltaic cell model is proposed to ensure a stable energy supply for monitoring equipment. In the complex power field, intelligent sensors are often used to monitor the status of power equipment, as the core of the monitoring system, but how to supply energy to the sensors is an important problem, which attracts much attention. Solar energy can be easily obtained from the outside world. A photovoltaic cell model is proposed to ensure a stable energy supply for monitoring equipment (Xiang et al., 2021).
A photovoltaic optimizer based on single inductor and single sensor is proposed. The optimizer includes inductor, sensor and MPPT unit, which improves the maximum output power of submodules, reduces the number of components, realizes the best current point tracking strategy and reduces the cost of photovoltaic optimizer (Pichel et al., 2018). A photovoltaic charging scheme based on MPPT strategy with single sensor is proposed, and a new optimization algorithm based on single current sensor is proposed to track MPPT (Kumar et al., 2017).
3 System model
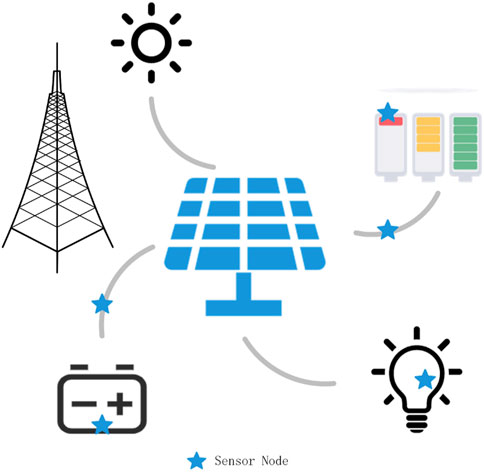
As shown in Figure 1, we propose a photovoltaic power generation system that includes power generation equipment, energy storage equipment, and energy consumption equipment. In order to make the system stable, the paper uses a wireless sensor network to monitor the operation of the system. The energy consumption devices in this system include not only the energy consumed by the user but also the energy consumed by the wireless sensor network. Therefore, we consider a secure communication system for photovoltaic power generation systems, which collects information about the voltage and current of the system through sensors. In order to realize the intelligent management of the whole platform and ensure the safe operation of the whole system, the model consists of acquisition nodes, eavesdropping nodes and base stations. The acquisition node is responsible for transmitting the collected confidential data to the base station, while the eavesdropping node attempts to eavesdrop on the confidential data. It is assumed that the locations of all nodes are fixed, and all acquisition nodes will be eavesdropped when transmitting data. Considering that all nodes directly transmit data to the base station will consume a lot of energy, in order to reduce the energy consumption of the whole sensor network, all the acquisition nodes are clustered in this paper. After the sensor nodes are divided into multiple clusters, a central node is selected from each cluster as CHs, and CHs is used as a collection node, and the data of surrounding nodes are collected and transmitted to the base station. The sensor set is
In this paper, FDMA is used as the communication connection between the sensor and the base station. FDMA is usually used for uplink transmission between the device and the server. It orthogonalizes the transmission of different users and completely reduces the intra-cell interference (Wang et al., 2020). According to Shannon formula, the achievable transmission rate from node i to node j is:
Similarly, the reachable rate from eavesdropping node to node j can be expressed as:
pi is the transmission power of the acquisition node. pe is the transmitting power of the eavesdropping node. σ is Gaussian white noise.
3.1 Communication model
Due to the position of each sensor node is fixed, the energy consumed by the sensor node when transmitting data to the base station is mainly determined by the power of the sensor. Therefore, this paper defines a cost function related to the power of sensor nodes, which increases in proportion to the power. The greater the power of sensor nodes, the greater the cost function and the more energy consumed. The energy consumption of sensor transmitting data once is shown as follows:
3.2 Secure rate
In the system model proposed in this paper, a safe rate is proposed to represent the rate at which data can arrive safely when data is transmitted between different sensor nodes. Security rate is defined as the transmission rate between node i and node j minus the transmission rate between eavesdropping node and node j. Only when the transmission rate between node j and node j is greater than that between eavesdropping node and node j, data can be safely transmitted from node j to node j. The security rate of data transmission from node j to node j can be expressed as follows:
The transmission rate from node i to node j is ri,j on the left side of the formula, and the transmission rate from eavesdropping node to node j is re,j. The final ri,j is the security rate between node i and node j. CHs the secure rate to the base station is expressed as rj,c. All sensor nodes are divided into multiple clusters, and each cluster has a CH to collect all CMs data and transmit it to the base station. Other sensor nodes in the cluster automatically join the CMs. Every CM can select one CH for association, Assume that is the association silver between CMs and CHs, and represents the CMs association CHj, otherwise. In addition, is expressed as the maximum associated number of CHs. Then the secure rate that all CMs can achieve is:
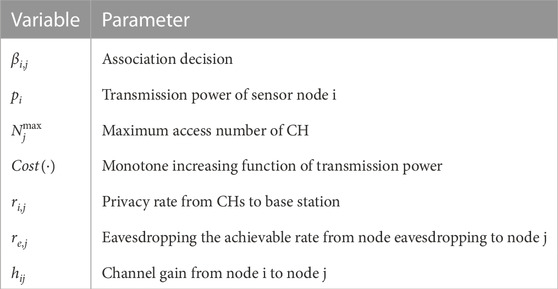
The above symbols are summarized in Table 1.
4 Problem formulation and problem solution
The core of this paper is to reduce the power loss of the sensor and improve the use efficiency. Therefore, considering the topology of the sensor and the transmission power when transmitting data, the topology of the sensor can be optimized by CHs selection and sensor correlation. Therefore, this paper considers three optimization problems to reduce the energy consumption of sensor nodes, including transmission power design, CHs selection and sensor association. This paper selects CHs according to the designed CHs selection algorithm. Then, a multi-constrained mixed integer optimization problem based on joint transmission power and topology control is proposed. The algorithm proposed in this paper is used to solve the optimization problem, and at the same time, the correlation between the solved transmission power and the sensor under the current CHs is obtained. However, it is uncertain that the transmission power and sensor correlation obtained at this time are the optimal solution of this optimization problem, so it is necessary to iterate continuously until the CHs, transmission power and sensor correlation obtained is fixed. Through the above scheme, it can be considered that a suboptimal solution is obtained. Our proposed solution almost traverses all sensor nodes, so K CHs are randomly selected at the beginning of the simulation experiment.
4.1 Problem formulate
In this part, we formulate a joint optimization problem based on joint transmission power design and sensor association, aiming at maximizing the security of sensor transmission and reducing the energy consumption of sensor. Note that the transmission power of all sensors is p. The relationship between CMs and CHs is
The weight factors ω1 > 0, ω2 > 0 are the tradeoff between secure rate and energy consumption. Constraints 6a indicates the limit of transmission power of sensor nodes of CMs; Constraints 6b and 6c mean that each CM can only access one CH; A constraint of 6 d means that the maximum number of CMs accessed by each CH is
Because the correlation factor is a binary variable, problem P is a non-convex mixed integer optimization problem. It is difficult to obtain the optimal solution of this problem by standard convex optimization techniques. Therefore, this paper adopts the block coordinate descent algorithm to decompose the optimization problem into two sub-problems, and solves problem P by iteratively solving the optimal solution of the sub-problems.
4.2 Problem solving
In this part, we use the BCD method of convex optimization to decompose problem P into two optimization problems: transmission power p and sensor node association β, and get a suboptimal solution through continuous iterative optimization. In each iteration, the transmission power design problem in the fixed sensor correlation result β is first solved. Then, we optimize the sensor association under the given power control design p. When the proposed algorithm converges to the predetermined accuracy, the suboptimal solution can be obtained.
4.2.1 Power control optimization
When the node association β is given, the power control optimization problem can be simplified as follows:
When
Among
Then, the dual problem is given through.
The original problem is convex about pi, so the solution satisfying KKT condition is also the optimal solution of the original problem. By finding the first derivative of the objective function to pi, the optimal transmission power allocation, denoted as
After we find
where sk = dfrac gamma‖gk‖ is defined as the step size of the kth cycle, and sk > 0. gk is defined as the gradient corresponding to the kth cycle. On the basis of Lagrange duality and projection sub-gradient method, we propose a cyclic optimization algorithm, as shown in Algorithm 2.
4.2.2 Node association optimization
Given the transmission power p, the optimization problem of node association can be simplified as follows:
The problem is a 0–1 multi-knapsack problem. With the increase of the dimension of the problem, the time complexity of the algorithm for solving the problem will also increase dramatically. How to solve the integer optimization problem is a problem worth thinking about. With the increase of the dimension of the problem, the time complexity of the algorithm for solving the problem will also increase dramatically. How to solve the integer optimization problem is a problem worth thinking about. In this paper, an algorithm is proposed to get the sub-optimal solution of the node association optimization problem. fij will be defined as the income of sensor node i accessing CHj, The expression fij is:
In the iteration of the algorithm, all unallocated sensor nodes are considered first. If the maximum distance between the current node and the second node is the largest, the sensor i is connected to the CHj until all sensor nodes are connected to the CH, and the iteration of the algorithm is stopped. The proposed algorithm of sensor association scheme based on MTHG is shown in Algorithm 1.
Algorithm 1. MTHG-Based Topology Control (MTHG)
1: Evaluation random CHs and topology control β0.
2: Evaluation (λ,ν)1 and r1, r2, r3 = 0.
3: repeat
4: repeat
5: repeat
6: Calculate
8: Calculate r1 = r1 + 1.
9: until Sub-gradient algorithm reaches a certain value.
10: Update fij by Eq. 15.
11: while
12: d* = −∞.
13: for all
14:
15: Update
16: if d > d* then
17: d* = d.
18: βij′ = 1.
19: end if
20: end for
21: delete sensor i in
22: end while
23: Calculate r2 = r2 + 1.
24: until The target reaches a certain value.
25: Acquire the CHs by CHs selection algorithm.
26: Update r3 = r3 + 1.
27: until CHs and topology control β is fixed.
4.3 CH selection
In order to improve the security of the whole photovoltaic system and reduce the energy consumption of the system, the CHs selection algorithm is proposed in this paper. CHs selection algorithm divides sensor nodes into multiple clusters, and selects CHs according to the minimum transmission distance between CHs and CMs, thus making the transmission energy consumption between each CM smaller. At the same time, the transmission distance between CH and the base station should be as small as possible to reduce the transmission energy consumption of CHs to the base station. We use the sum of the minimum Euclidean distances between CHs and CMs to select CHs. CHs selection formula is as follows:
Among, ℧ represents the deletion of the set of nodes m. ∑distm, ∀m ∈ ℧ is the sum of the distances from sensor m to other sensor in the cluster.
4.4 Overall algorithm design
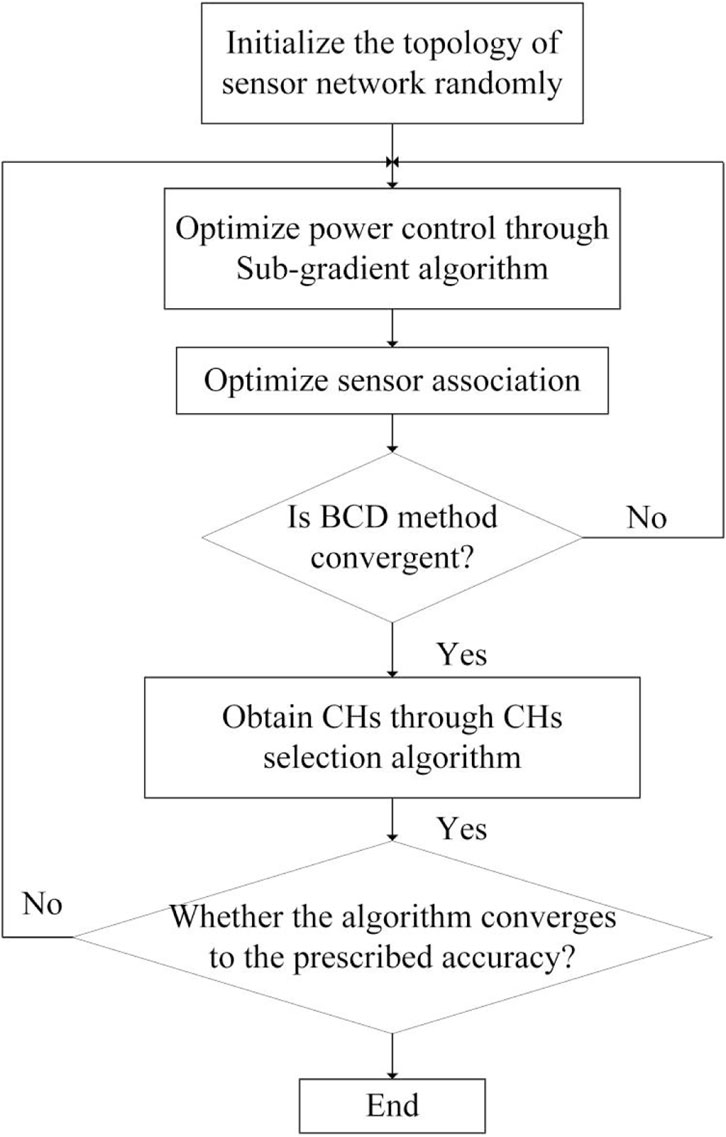
We propose a whole iterative loop algorithm, as shown in Algorithm 2, aiming at effectively solving the optimization problem with reduced algorithm complexity. Firstly, the topological association of sensor networks is randomly initialized, and the transmission power is solved by sub-gradient algorithm. Then, the price of knapsack problem is calculated by the obtained transmission power, and the corresponding sensor association result is obtained by traversing all CMs. Iterate for many times, reach the accuracy given by BCD algorithm, and get a solution. The solution obtained at this time is not suboptimal, because CHs is random. Finally, the CHs is selected according to the given CHs selection algorithm, and the transmission power and sensor correlation results are recalculated. After repeated iterations, until the CH sum does not change any more and the target value converges to the predetermined accuracy, we think that a suboptimal solution has been found for this problem. Repeated iterations are because CHs is randomly initialized in the initialization process, and after repeated iterations, high-quality topology control strategies can be obtained. The details of this algorithm are summarized as algorithm TPTCO. The flowchart of the TPTCO algorithm is shown in Figure 2.
Algorithm 2. Transmission Power and Topology Control Optimization (TPTCO)
1: Evaluation random CHs and topology control β0.
2: Evaluation (λ,ν)1 and r1, r2, r3 = 0.
3: repeat
4: repeat
5: repeat
6: Calculate
8: Update r1 = r1 + 1.
9: until Sub-gradient algorithm reach to a fixed value.
10: Acquire topology control through Algorithm 1 (MTHG).
11: until BCD method reduce to a certain value.
12: Calculates the sum of Euclidean distances between each node and other nodes.
13: CH is the node of the sum of the minimum Euclidean distances.
14: until Topology control and CHs is fixed.
5 Simulation analysis
We prove the effectiveness of the algorithm proposed in this paper by simulation results. In the simulation, it is assumed that a WSN topology is randomly deployed, and the sensor nodes are randomly deployed in a certain range. Where d > 0 represents the Euclidean distance from CH to BS and from CMs to CH (Heinzelman et al., 2000). The MTHG algorithm proposed in this paper is compared with GREEDY, Relax-CVX and other algorithms by simulation.
5.1 Simulation parameters
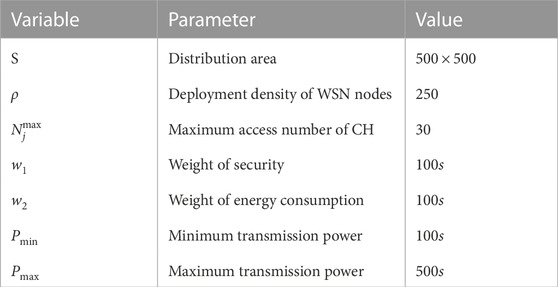
This paper evaluates the performance of the proposed algorithm by analyzing the clustering results, the energy consumption of the algorithm, the convergence of the algorithm, the transmission security and the load of the cluster head. The simulation results are obtained by running Matlab 2016b simulation software on a computer equipped with Intel Core i7-7700,296 3.6 GHz CPU and 16 GB memory. The parameters used in the simulation experiment are shown in Table 2.
5.2 Analysis of simulation results
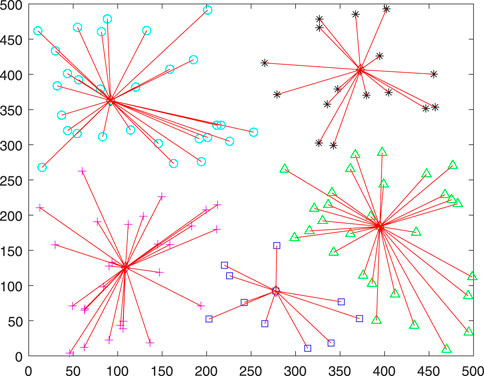
Figure 3 shows the topology of WSN in the first round of operation, and the results of sensor association after running MTHG algorithm in this topology. In the simulation process, all sensor nodes are randomly deployed according to PPP density, and MTHG algorithm divides sensor nodes into CHs and CMs. CM is associated with CH for data transmission. Using different sensor node deployment algorithms will lead to uneven density of sensor nodes in different areas, and higher CH load in denser areas, which will lead to increased energy consumption of CH and thus the energy consumption of the whole system. Therefore, it is necessary to limit the maximum number of CH associations. In this paper, sensor nodes are divided into five clusters. It can be seen from the figure that according to the CHs selection algorithm, each CH is distributed in the center of each cluster as much as possible, which will shorten the Euclidean distance between CH and CM, thus reducing the energy consumption during data transmission.
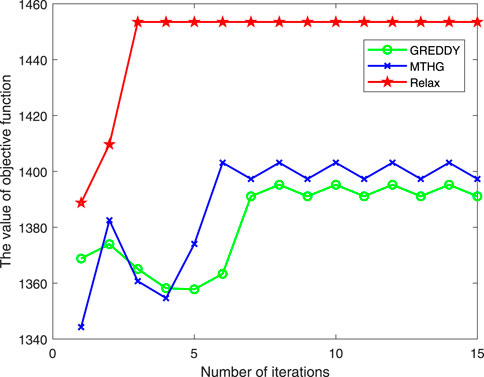
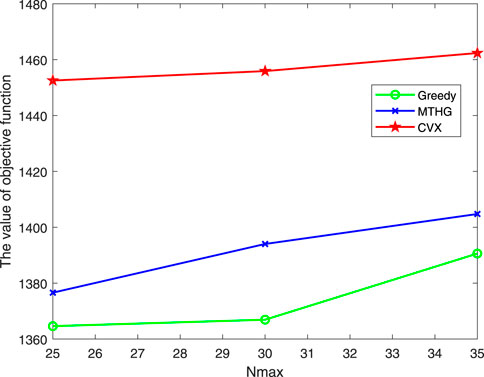
Figure 4 shows the convergence of the algorithm proposed in this paper compared with other algorithms. It can be seen from the figure that, at the beginning, the convergence curves of all algorithms keep rising with the number of iterations. After iteration for a period of time, the correlation between CHs and sensors will not change, and then all algorithms will gradually converge. It can be seen from the convergence curves of different algorithms that CVX has the best convergence performance. The convergence curve gap between MTHG algorithm and Relax algorithm proposed in this paper is very small, while the performance of GREEDY algorithm is worse. The reason why there is little difference between MTHG algorithm and GREEDY algorithm may be that both of them use the minimum Euclidean distance for clustering. Therefore, we can know that the MTHG algorithm proposed in this paper can also get high-quality approximate suboptimal solutions. Even if there is a certain gap between the solution and the optimal solution. GREEDY got a feasible solution with the lowest algorithm complexity. Compared with GREEDY algorithm, MTHG algorithm has more obvious improvement when the complexity increases little.
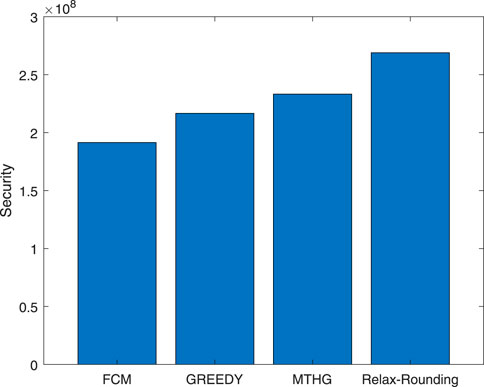
Figure 5 shows the security of different algorithms for unit energy consumption, with Realx-Rounding being the best. MTHG proposed in this paper is the closest to Realx-Rounding, GREEDY algorithm is the third, and Fuzzy C-Means (FCM) algorithm is the worst. Realx-Rounding takes the most time. For FCM algorithm, security in the transmission process is not considered, so the security of FCM algorithm is poor. For GREEDY algorithm, in the process of optimizing sensor association, only the minimum energy consumption is considered, so CMs will associate with its nearest CHs as much as possible, without considering the security of data transmission, which will also lead to the reduction of security during transmission. However, the computational complexity of MTHG proposed in this paper is significantly reduced. It can be seen from the above that MTHG proposed in this paper improves the security requirements in the process of data transmission.
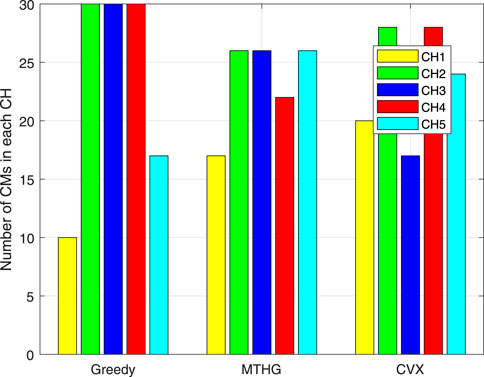
Figure 6 shows the CHs load under different algorithms. For CMs, they will always reduce the energy consumed in the transmission process as much as possible under the CHs constraint, so CMs will choose to associate with its nearest CHs as much as possible. It can be seen from the figure that under the same constraints, the load calculated by MTHG algorithm is the most balanced, followed by CVX, and the CHs load calculated by Greedy algorithm is the most unbalanced. For GREEDY algorithm, in the process of optimizing sensor association, only the minimum energy consumption is considered, so CMs will associate with its nearest CHs as much as possible, which will lead to the unbalanced load of CHs. The MTHG algorithm proposed in this paper iteratively solves the transmission power, sensor association and CHs selection for many times until the obtained results are unchanged. The CVX algorithm optimizes the problem as a whole, and does not consider the load balance too much, so the CHs load is not so balanced. Therefore, MTHG can balance the load of CHs as much as possible, which can greatly improve the service life of sensor nodes.
Figure 7 shows the convergence performance of the algorithm under the changed conditions. CVX has the best convergence, because CVX considers the optimization problem as a whole in the optimization process, and obtains the optimal correlation result. Therefore, when it changes, the target value calculated by CVX algorithm does not change much, but CVX algorithm consumes the most time. The MTHG algorithm proposed in this paper has better convergence than GREEDY algorithm. GREEDY algorithm only considers the minimum energy consumption in the process of optimizing sensor association. When it increases, CMs will be associated with its nearest CHs as much as possible, and the energy consumption will be correspondingly reduced. The objective function value of the optimization problem will be improved, but at the same time, the load imbalance of CHs will be more serious. The MTHG proposed in this paper reduces the complexity of CVX algorithm and is very important for the implementation of solutions.
6 Conclusion
The intelligent management of photovoltaic power generation system needs to collect information from all parts of the system through sensors. In order to improve the security of WSN and reduce the energy consumption of sensors, this paper uses BCD method to solve the joint optimization problem of transmission power and sensor association, and proposes MTHG algorithm to solve the problem of sensor association optimization, and uses sub-gradient method to solve the transmission power. Select CHs again according to the association of sensors. The simulation results show that the algorithm can effectively improve the security of the transmission process, reduce the energy consumption of the sensor, and thus prolong the service life of the wireless sensor network. In the future work, we will try to improve the algorithm by reducing the gap between the suboptimal solution and the optimal solution and reducing its complexity. In addition, a more realistic environment will be considered in the optimization problem.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
Methodology, XX; software, YL; formal analysis, XX and YL; investigation, YC; resources, XX; data curation, YL and XH; writing—original draft preparation, YX; visualization, BH; supervision, YX; project administration, XJ; funding acquisition, BH All authors have read and agreed to the published version of the manuscript.
Funding
China Southern Power Grid Corporation key technology project: GZKJXM20220052.
Conflict of interest
XX, YL, and YC were employed by Electric Power Research Institute of Guizhou Power Grid Co, Ltd; XH was employed by Guiyang Power Supply Bureau of Guizhou Power Grid Co, Ltd.; YX, BH, and XJ are employed by Electric Power Research Institute of China Southern Power Grid.
The authors declare that this study received funding from China Southern Power Grid Corporation. The funder had the following involvement in the study: data collection and analysis, preparation of the manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Chen, Y., Ma, J., Ma, Y., Zhang, Y., Zhou, X., and Zhou, R. (2021). “The design and implementation of dust monitoring system for photovoltaic power generation,” in 2021 IEEE 23rd Int Conf on High Performance Computing and Communications; 7th Int Conf on Data Science and Systems; 19th Int Conf on Smart City; 7th Int Conf on Dependability in Sensor, Cloud and Big Data Systems and Application (HPCC/DSS/SmartCity/DependSys) (Haikou, Hainan, China: IEEE), 1458–1465. doi:10.1109/HPCC-DSS-SmartCity-DependSys53884.2021.00218
Gu, J., Zhao, L., and Zhu, C. (2021). “Optimal planning of distributed photovoltaic in integrated electricity and heat systems,” in 2021 4th International Conference on Energy, Electrical and Power Engineering (CEEPE), 982–986. doi:10.1109/CEEPE51765.2021.9475729
Heinzelman, W., Chandrakasan, A., and Balakrishnan, H. (2000). “Energy-efficient communication protocol for wireless microsensor networks,” in Proceedings of the 33rd Annual Hawaii International Conference on System Sciences (Maui, HI, USA: IEEE), 10. doi:10.1109/HICSS.2000.926982
Helmers, H., and Bett, A. W. (2016). “Photovoltaic laser power converters for wireless optical power supply of sensor systems,” in 2016 IEEE International Conference on Wireless for Space and Extreme Environments (WiSEE) (Aachen, Germany: IEEE), 152–154. doi:10.1109/WiSEE.2016.7877321
Hu, A., and Li, G. (2014). Physical layer security in wireless communication: Survey. J. Data Acquis. Process. 5, 237. doi:10.23919/JCIN.2020.9200889
Hung, Y. J., Cai, M. S., Chen, J. F., Su, H. W., Jen, P. C., Chen, P., et al. (2018). High-voltage backside-illuminated cmos photovoltaic module for powering implantable temperature sensors. IEEE J. Photovoltaics 8, 342–347. doi:10.1109/JPHOTOV.2017.2775440
Jäger-Waldau, A., Huld, T., and Szabo, S. (2017). “Residential photovoltaic electricity generation in the European Union 2017-opportunities and challenges,” in 2017 IEEE 44th Photovoltaic Specialist Conference (PVSC) (Washington, DC, USA: IEEE), 2167–2169. doi:10.1109/PVSC.2017.8366336
Kong, Z., Song, J., Wang, C., Chen, H., and Hanzo, L. (2021). Hybrid analog-digital precoder design for securing cognitive millimeter wave networks. IEEE Trans. Inf. Forensics Secur. 16, 4019–4034. doi:10.1109/TIFS.2020.3039697
Kong, Z., Yang, S., Wang, D., and Hanzo, L. (2019). Robust beamforming and jamming for enhancing the physical layer security of full duplex radios. IEEE Trans. Inf. Forensics Secur. 14, 3151–3159. doi:10.1109/TIFS.2019.2908481
Kong, Z., Yang, S., Wu, F., Peng, S., Zhong, L., and Hanzo, L. (2016). Iterative distributed minimum total mse approach for secure communications in mimo interference channels. IEEE Trans. Inf. Forensics Secur. 11, 594–608. doi:10.1109/TIFS.2015.2493888
Kuang, S., Chang, K. C., Chu, K. C., Lin, Y. C., Wang, H. C., Hsu, T. L., et al. (2020). “Study of dsp (tms320f2812) chip for advanced photovoltaic power generation maximum power point tracking control system,” in 2020 15th International Microsystems, Packaging, Assembly and Circuits Technology Conference (IMPACT) (Taipei, Taiwan: IEEE), 294–297. doi:10.1109/IMPACT50485.2020.9268608
Kumar, N., Hussain, I., Singh, B., and Panigrahi, B. K. (2017). Single sensor-based mppt of partially shaded pv system for battery charging by using cauchy and Gaussian sine cosine optimization. IEEE Trans. Energy Convers. 32, 983–992. doi:10.1109/TEC.2017.2669518
Ntagios, M., Escobedo, P., and Dahiya, R. (2020). “3d printed packaging of photovoltaic cells for energy autonomous embedded sensors,” in 2020 IEEE SENSORS (Rotterdam, Netherlands: IEEE), 1–4. doi:10.1109/SENSORS47125.2020.9278635
Pavlík, M., Kolcun, M., Bucko, S., and Kohan, V. (2022). “Analysis and evaluation of photovoltaic cell defects and their impact on electricity generation,” in 2022 22nd International Scientific Conference on Electric Power Engineering (EPE) (Kouty nad Desnou, Czech Republic: IEEE), 1–4. doi:10.1109/EPE54603.2022.9814105
Pichel, N., Vivar, M., and Fuentes, M. (2018). “Optimization study of a photovoltaic-photochemical hybrid system (solwat) for meeting the needs of electricity and clean water,” in 2018 IEEE 7th World Conference on Photovoltaic Energy Conversion (WCPEC) (A Joint Conference of 45th IEEE PVSC, 28th PVSEC and 34th EU PVSEC) (Waikoloa, HI, USA: IEEE), 1222–1224. doi:10.1109/PVSC.2018.8547320
Saffih, F. (2017). “Artificially-intelligent imaging (AI2) sensors: How intelligent CMOS imaging devices can benefit photovoltaics?,” in 2017 7th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO) (Sharjah, UAE: IEEE). doi:10.1109/ICMSAO.2017.7934899
Suryawanshi, S. Y., and Patil, M. D. (2019). “Implementation of a DC side sensor-less cascaded H-bridge multilevel converter for photovoltaic system,” in 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI) (Tirunelveli, India: IEEE), 1104–1108. doi:10.1109/ICOEI.2019.8862535
Wang, Q., Tan, L. T., Hu, R. Q., and Qian, Y. (2020). Hierarchical energy-efficient mobile-edge computing in iot networks. IEEE Internet Things J. 7, 11626–11639. doi:10.1109/JIOT.2020.3000193
Xiang, S., Du, L., Li, C., Li, Y., Yu, H., and Huang, P. (2021). “An optimization method based on lm-ga for parameter identification of photovoltaic cell,” in 2021 6th Asia Conference on Power and Electrical Engineering (ACPEE) (Chongqing, China: IEEE), 405–409. doi:10.1109/ACPEE51499.2021.9437110
Xing, C., Xi, X., He, X., and Liu, M. (2020). “Research on the mppt control simulation of wind and photovoltaic complementary power generation system,” in 2020 IEEE Sustainable Power and Energy Conference (iSPEC) (Chengdu, China: IEEE), 1058–1063. doi:10.1109/iSPEC50848.2020.9350965
Yang, M., and Zhou, G. (2021). “Design and implementation of photovoltaic power generation management system based on NB-IoT,” in 2021 IEEE International Conference on Information Communication and Software Engineering (ICICSE) (Chengdu, China: IEEE), 255–259. doi:10.1109/ICICSE52190.2021.9404117
Yue, X., Kauer, M., Bellanger, M., Beard, O., Brownlow, M., Gibson, D., et al. (2017). Development of an indoor photovoltaic energy harvesting module for autonomous sensors in building air quality applications. IEEE Internet Things J. 4, 2092–2103. doi:10.1109/JIOT.2017.2754981
Zhong, L., Ge, M.-F., Zhang, S., and Liu, Y. (2022). Rate-aware fuzzy clustering and stable sensor association for load balancing in wsns. IEEE Internet Things J. 9, 3559–3573. doi:10.1109/JIOT.2021.3098352
Zhong, L., Li, M., Cao, Y., and Jiang, T. (2019). Stable user association and resource allocation based on stackelberg game in backhaul-constrained hetnets. IEEE Trans. Veh. Technol. 68, 10239–10251. doi:10.1109/TVT.2019.2937941
Zhu, Y., Wen, H., Chu, G., Hu, Y., Li, X., and Ma, J. (2021). High-performance photovoltaic constant power generation control with rapid maximum power point estimation. IEEE Trans. Industry Appl. 57, 714–729. doi:10.1109/TIA.2020.3029128
Keywords: photovoltaic, wireless sensor network, cluster head, sensor association, transmission power
Citation: Xiao X, Li Y, He X, Cai Y, Xiao Y, Huang B and Jin X (2023) Optimal topology control of monitoring sensor network based on physical layer security for smart photovoltaic power system. Front. Energy Res. 11:1124700. doi: 10.3389/fenrg.2023.1124700
Received: 15 December 2022; Accepted: 09 January 2023;
Published: 30 January 2023.
Edited by:
Zhi-Wei Liu, Huazhong University of Science and Technology, ChinaReviewed by:
Yun Feng, Hunan University, ChinaFeng Liu, Stevens Institute of Technology, United States
Tao Huang, James Cook University, Australia
Copyright © 2023 Xiao, Li, He, Cai, Xiao, Huang and Jin. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xiaobing Xiao, MjUzNTcwODY4QHFxLmNvbQ==
 Xiaobing Xiao
Xiaobing Xiao Yue Li1
Yue Li1