- 1Department of Computer Science, Abdul Wali Khan University Mardan, Mardan, Pakistan
- 2Department of Computer Science, COMSATS University Islamabad, Wah Campus, Punjab, Pakistan
- 3Department of Information Systems, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University (PNU), Riyadh, Saudi Arabia
Internet of Things (IoT) has become an interesting research domain as numerous devices, preferably equipped with sensors, communication, and actuator modules, are deployed to capture real-time data in the different application areas, such as smart healthcare and industries. These devices have the built-in capacity to directly interact with the physical phenomenon and report any unusual situation within their respective coverage areas, i.e., monitoring a critical patient in the smart hospital but direct communication with a common destination module is not guaranteed and could possibly be very challenging if two or more devices, preferably those in closed proximity, are interested to transmit simultaneously. Therefore, in this manuscript, we are going to present a hybrid slot allocation approach, which is specifically designed for those devices resided in neighborhood and are eager to communication concurrently with a common destination device, i.e., server. In the beginning, the k-mean clustering algorithm is used to group these devices into clusters where server is forced to collect data from devices deployed in the respective coverage areas. Thus, every server generates dedicated slots for active devices and an additional slot for server(s). Similarly, the proposed neighborhood-enabled time division multiple access (TDMA) has the flexibility of assigning multiple slots to a requesting device if available, which is needed in scenarios, such as detection of pest in the field. Additionally, a member device is allowed to migrate (if needed and possible) from one server's coverage region to another. Simulation results confirmed that the proposed approach is better than the existing algorithms (opportunistic TDMA, hybrid TDMA, and non-orthogonal multiple access), particularly in terms of bandwidth, end-to-end delay, and empty slot utilization. The proposed scheme has improved bandwidth and empty slot utilization, which are approximately 15% and 12%, respectively, whereas it has achieved approximately 94.89% utilization of the available slots which was previously 93.4%.
1 Introduction
Internet of Things (IoT) is defined as a self-organized network of various devices Ci, i.e., things, which are dispersed either randomly or deterministically (if feasible) to periodically monitor a physical phenomenon, i.e., controlling manufacturing process in the hazard environment when entry of the human being is susceptible to possible danger (Song et al., 2020). These devices are attached directly to the equipment and programmed such that the required information is captured precisely and accurately after a fixed time interval (Alam et al., 2024). Furthermore, these devices Ci depend on the on-board battery that is most probably not rechargeable and equipped with transceiver module that has a limited coverage area, and thus, every device is not able to communicate directly with the base station (Nassereddine and Khang, 2024). It is important to note that these wearable devices Ci may be embedded with various application-dependent sensors and actuator modules in IoT networking infrastructures(Alshehri et al., 2018). Reliable and timely transmission of the capture data is one of the difficult problems with IoT networks (Wang et al., 2024). This captured data are either transmitted directly (if possible) or through multi-hop communication mechanism where a group of these wearable devices acts as relaying devices and is bounded to transmit data of the neighboring devices in addition to their own data (Gope et al., 2021). In these scenarios, it is high likely that multiple devices may be interested to communicate with a common destination module, i.e., server in this case.
Due to the concurrent communication in the IoT, the probability of collision among various packets is very high in industrial Internet of Things (IIoT) networks (Alshehri et al., 2019). Therefore, various simultaneous transmission-enabled communication approaches have been presented to guarantee concurrent transmission of packets from multiple wearable devices Ci to IIoT networks. These mechanisms are primarily based on the idea allocating dedicated sub-channels or a time slot or a separate code for the communication. Orthogonal Frequency Division Multiple Access (OFDMA) is one of the common mechanisms which is used to guarantee simultaneous transmission of multiple wearable devices Ci with a common receiver, i.e., server Sj in this case (Nguyen et al., 2020). OFDMA generates smaller frequency bands by dividing available bandwidth which is called sub channelization. These channels are assigned to various competing wearable devices preferably in first-come-first-serve or priority bases in IIoT networking infrastructures. Similalrly, OFDMA with a single carrier is presented to address concurrent communication of multiple devices through a hybrid of time and frequency domains. Apart from it, non-orthogonal multiple access (NOMA) was reported in the literature to enable packet transmission of multiple wearable devices Ci, concurrently using a shared medium of communication in the IoT networks (Khan et al., 2020). An extended version of the NOMA, i.e., power-enabled NOMA, was reported to address the aforementioned issue; power levels are utilized as a differentiating factor in the concurrent communication among multiple devices (Shahab and Shin, 2018; Sun et al., 2019). Wastage of the available bandwidth is among the core issues associated with these approaches, particularly in the IoT networks. In addition to these schemes, time division multiple access (TDMA)-based schemes were presented, where available sliding window (preferably time-based) is divided into various slots, and these available time slots are allocated to needy wearable devices either permanently or preemptive-based strategy (Johari and Krishna, 2020). A hybrid mechanism, i.e., TDMA and hierarchical, was reported in the literature to enable concurrent or simultaneous transmission of packets among multiple active wearable devices in the IoT networks. Although this mechanism has addressed various problems linked to the TDMA-based approaches, it is susceptible or vulnerable to the failure of a single point that is parent device Ci. Apart from these, neighborhood-based schemes have been presented for static and mobile IoT networks, respectively; however, both schemes do not consider applicability of the machine learning approaches, especially in scenarios where networks become mature (Khan et al., 2021, 2023). Therefore, an effective, reliable, and efficient wireless communication algorithm is required to be proposed that not only ensure simultaneous communication among multiple devices but also equally resolve the aforementioned issues.
In this study, we present a machine learning and neighborhood slot allocation-enabled wireless communication methodology that is particularly developed for the edge-enabled IoT infrastructure. In this approach, k-mean clustering (AI-based methodology) is utilized to organize randomly deployed wearable devices Ci into an operational hierarchical IIoT networks, where every server or cluster head (CH) has a specific set of member devices Ci. Second, every server Sj has been forced to form two groups of time slots, where one group, preferably large, is dedicated for the ordinary member devices Ci and other, particularly small, is reserved for server modules Sj, which are not able to transmit directly. The major contributions to the research community of the work presented in this study are as follows:
1. Machine learning and neighborhood slot allocation-enabled transmission for IoT networks with minimum possible communication overheads.
2. K-mean algorithm is used to ensure maximum possible utilization of the available bandwidth and empty slots in IoT.
3. Migration aware TDMA approach where wearable devices Ci may migrate from coverage area of a server to another, a common scenario in the smart hospitals.
4. A two tier machine learning-enabled slot allocation approach which is specifically designed for the hierarchical IoT networks.
The rest of the study is organized as follows. In Section 2, a brief but comprehensive literature review of the most relevant techniques is presented. In Section 3, we have focused on explaining how the proposed machine learning and neighborhood slot allocation-enabled mechanism are formed and how it is used to be applicable in the problem domain. In Section 4, a detailed and thorough analysis of the proposed and available schemes is presented in terms of numerous performance metrics. Finally, concluding remarks and future directions are presented.
2 Literature review
In this section, a brief literature review of numerous related approaches have been presented as complete review is beyond the scope of this study. Moreover, as existing approaches cover different research domains such as non-orthogonal multiple access (NOMA) and time division multiple access (TDMA), details of these schemes are shown in separate subsections.
2.1 Non-orthogonal multiple access-based approaches
Unlike single sub-carrier approach, where a high rate or power stream is transmitted to enable simultaneous wireless communication, a multiple sub-carrier concept is utilized in OFDMA. In this scheme, multiple small sub-carriers, preferably within the same single carrier stream, enable simultaneous communication among multiple interest devices in both traditional and constraint-oriented networking infrastructures (Nguyen et al., 2020). In OFDMA-enabled approaches, the available bandwidth (single stream) is divided into smaller multiple sub-carries or frequency bands which are allocated to those interested wearable devices. It is observed that these sub-carriers were bounded to transmit in parallel, where guard carriers are used to reduce channel interference and transmission delay. Similarly, vector OFDMA was reported which is based on the concept of multiple input and multiple output (MIMO), whereas flash OFDM is based on the concept of multiple tone and fast hoping to enable simultaneous wireless transmission among multiple devices. Single-carrier OFDMA is an alternative solution to the traditional OFDMA which has the capacity to allow more powerful transmitters. Additionally, NOMA scheme, that is a random access approach-based technique, has been reported in the literature to enable simultaneous transmission of multiple devices over a common channel (Khan et al., 2020). NOMA is reliable and has the ability to achieve expected goal of the 5G networks. In this scheme, every device is bounded to operate in the same frequency band, where power levels of every device are different from other, which is used as a differentiating factor at the destination module or device. Generally, NOMA utilized super position coding-enabled transmitters which are helpful to differentiate between down-link and up-link channels at the respective receiver that is a successive interference cancellation-enabled. An extended version of NOMA, that is power-enabled NOMA, was reported, where numerous devices use completely different power level in order to transmit data values (Shahab and Shin, 2018; Sun et al., 2019). Although these methods have addressed the communication problem (concurrent) with IoT networks, one of the frequent problems with these techniques is bandwidth waste.
2.2 Time division multiple access-based approaches
Contention-enabled multiple access approach, that is primarily a four-way hand shake approach, was presented to allow simultaneous transmission of more devices, preferably active and interested, with a common receiver. Furthermore, the situation becomes more and more complex only if devices have to utilize a common channel or medium for communication (Adame et al., 2014; Doost-Mohammady et al., 2016). Although this mechanism has resolved the collision issue, excessive time for registration is a challenging issue with this approach. Combined authentication/association (Shahin et al., 2016), distributed authentication control (Bankov et al., 2016), and centralized authentication control (Pawlowski et al., 2014) were reported in the literature to address numerous possible problems with the contention-enabled multiple access mechanism. Similarly, a reliable and efficient handshaking approach (four way), that is RTS and CTS which are used to represent request and clear-to-send, respectively, was presented specifically to resolve the challenging issue that is hidden terminal scenario (Chen et al., 2018). This mechanism ensure the reliability of an ongoing communication session by forcing other devices to hold their transmission until the session is completed. The exposed terminal scenario, where devices that can interact without interruption are constrained to wait for the successful conclusion of an ongoing communication session, is a strongly connected problem with this technique. Faruque (2019) have presented a TDMA-enabled communication mechanism to enable simultaneous transmission of multiple devices. In TDMA, the sliding window, time based, is divided into numerous slots, preferably of equal size. These available time slots are allocated to wearable devices on first-come-first-serve basis preferably in a non-preemptive manner. A member device must communicate (if it has data to send) in its dedicated slot, and slot is empty if a particular device does not have any data to send. In a dedicated TDMA approach, collision is completely avoided, but wastage of the available bandwidth is very high. Lee and Cho (2017) presented an alternative approach to the traditional TDMA scheme that is a hybrid scheme. TDMA and hierarchical approaches were integrated to form an exceptional communication scheme for the IoT network. However, single-point failure and transmission delay (maximum) are among the common issues associated with this approach. Similarly, a contention-free MA scheme was proposed by Zhai et al. (2016), to enable a proper schedule-based transmission of packets in time and frequency domains. It has used an automatic repeat request-based scheme to improve reliability and efficiency. However, specific hardware-oriented is one of the core issues associated with this scheme. Similarly, a slotted hybrid approach, that is based on CSMA/CA and TDMA, was presented by Shahin et al. (2018), to enable simultaneous transmission of multiple interested wearable devices preferably in their own time slot. This scheme is quite effective to address the excessive registration problem associated with the IoT networks. In this system, member devices are compelled to broadcast their authentication request messages via CSMA/CA, while association request messages are handled exclusively by TDMA. Batta et al. (2019a,b) have proposed various extensions to the traditional TDMA approach, especially distributed to improve latency in IoTs. A distributed and token-based mechanism was developed to resolve the hidden terminal scenario problem preferably in the IoTs and Mobile Ad Hoc Networks (MANETs) (Ye and Zhuang, 2017). Prolong end-to-end latency, concurrent packet transmission, and single-point failure are among the core problems with this scheme. Similarly, distributed TDMA was reported in the literature to minimize bandwidth wastage in the IoT networks, where slots are allocated to various devices using a mature scheduling policy (Li et al., 2017). This scheme has used priority metric of a device to guarantee the allocation of a slot. However, starvation and simultaneous communications are not guaranteed, as time slot assignment strategy is prioritized. Thus, a low-priority device should wait longer. Similarly, a time slot assignment approach, which is based on the distributed TDMA, was presented by Bhatia and Hansdah (2013) where the allocation process of available slots is random. Synchronization is among the core problems, which is closely linked to this approach. A novel multi-channel hybrid approach was presented to resolve the aforementioned issue in IoMT (Ramachandran et al., 2020). On-board power efficiency and complexity are the main problems linked to this methodology. Similarly, topological orders-enabled TDMA scheme was reported in the study mentioned in the reference (nguyen et al., 2020), where wearable device maintained valuable information about the scheme, and it is very useful to get a time slot. However, slots' waiting time has a direct co-relation to the network density.
3 Proposed machine learning and neighborhood slot allocation-enabled communication scheme for Internet of medical things
A thorough and in-depth explanation of the suggested machine learning and neighborhood slot allocation-enabled communication technique is provided in this section. The proposed methodology is advanced enough to enable the transmission of packets, especially simultaneous of several devices, ideally close neighbors, to a single destination device, such as a server module or cluster head (CH) in IIoT networks. In the beginning, a hierarchical IIoT network is created using the K-mean clustering technique, one of the unsupervised learning and partitioning clustering mechanisms, where each member device is placed so that it may connect directly with the desired CH module in the IIoT networks. Below is a thorough explanation of the K-mean clustering method.
3.1 K-mean clustering in the proposed communication approach
Usually, k-mean clustering approach is used to divide data values (preferably non-labeled) into clusters, and it is high likely that data values belong to a particular cluster have the similar characteristics, particularly those on which clustering is performed. Initially, k-means clustering is bounded to randomly select K devices Sj, where K represents the expected number of clusters in the IoT networks as the intended CH Sj. In the proposed setup, CHs Sj are devices preferably with higher communication and processing capabilities than the ordinary devices Ci in the IoT networks. These devices Sjj may reside at different locations, as the deployment process or mechanism is random, and it is high likely that a balance clustering approach, where every cluster has similar member devices Ci, is not feasible. These cluster heads are deployed randomly using Equation 1, where every CH module Sj represents a particular centroid in the modified k-mean clustering approach as follows:
where k=1…..K clusters in the IoT network. In the second step of the k-mean algorithm, member devices Ci of every CH Sj are identified through a systematic processing that is using a well-known distance measure, such as Euclidean distance measure. Euclidean distance between a CH Sj and ordinary device Ci is calculated as described in Equation 2
where l represents various metrics used to calculate the distance between a particular CH and its neighboring devices preferably those reside in the coverage area of the communication module. Furthermore, a specific threshold value, i.e.„ δ = 0.05 in this case, is assumed to divide member and non-member devices Ci using Equation 3 which is presented below.
It is necessary to find the best possible set of nearest neighboring devices Ci for every CH module Sj in the IoT network. Additionally, every ordinary device finds the nearest CH module Sj, which is computed using Equation 4 as follows:
where j=1…m. Thus, a particular member device Ci joins the CH module Sj which is deployed at the least possible distance in the IoT networks.
Additionally, every CH module Sj is bounded to broadcast its location information to the neighboring devices Ci, which is quite similar to the process of computing a new centroid in the traditional K-mean clustering mechanism as given in Equation 5.
where a represents the numerical or attribute value of possible set of member devices in the coverage area of a particular cluster head module Sj. It is noteworthy that a modified version of the traditional k-mean approach is used, where the cluster head selection process is repeatedly applied. However, in the proposed setup, CH modules are powerful devices, and the rotation process for the CH module is not needed. In this way, every device Ci becomes a member of the nearest possible CH module in the operational IoT networks. Furthermore, unlike balanced clustering mechanism where every cluster has similar number of member devices Ci, the proposed model adopts a non-balanced clustering methodology. It is due to the random deployment nature of these devices, i.e., Ci & Sj, where it high likely that a particular area may have dense deployment than other areas. As soon as the clustering formation mechanism is complete, the next process is to generate a dedicated time slot for every member device Ci in a particular CH module Sj.
4 Proposed neighborhood-enabled slot allocation approach for Internet of medical things
In this phase, it is assumed that every CH module Sj has completed the membership process of the ordinary devices Ci (preferably neighboring devices). Furthermore, a member device is bounded to be a part or member of a particular CH module Sj even though the another CH module is located in its coverage area. However, devices Ci reside on the edges of two or more clusters should keep the record of other CH modules Sj+1, which are at second and third (if any) positions as far as distance is concerned. Initially, every CH module Sj divides the allocated frequency domain (preferably radio) into time slots of equal size such that a particular time slot is sufficient for the transmission of data captured by a member device Ci. Moreover, every CH has to make sure that slots are allocated to those devices only which fall within the direct coverage area, i.e., having minimum possible distance. To understand the complete methodology, a detailed flow chart of the entire working process of the proposed neighborhood-enabled slot allocation scheme is shown in Figure 1.
Furthermore, a single device is allowed to transmit its data in a particular time interval, whereas other devices wait for their allocated time slots. Thus, the net rate of transmission in scenarios, where load remains constant, is shown in the following Equation 6.
where M is the total number of member devices Ci in the coverage area of a particular CH module Sj. In the proposed TDMA approach, every CH module has a different number of member devices, and thus, it is high likely that the number of slots is different in every CH module Sj. For example, if a CH Sj has twelve (12) member devices, then it is forced to generate or divide the radio frequency into 12 equal time slots. Furthermore, these time slots are assigned in first-come-first-serve (FCFS) basis. Time slot T1 is assigned to device Ci only if the time slot has reserved the device before other member devices Ci+…n in a particular CH module Sj. It is important to note that spectral efficiency of the proposed TDMA scheme is computed using the following Equation 7.
where metric τ represent the duration of a particular time slot, Mt is used to represent the total number of slots per frame, and Tf is used to depict the duration of a particular frame in the IoT networks. As soon as time slots are assigned to the member devices Ci, the next step is the transmission of data captured by these member devices. In the proposed neighborhood-enabled TDMA approach, it is possible that a particular CH module Sj has maximum number of member devices than other CH modules Sj+1 in the networks. Therefore, a member device Ci in this particular CH is expected to wait longer for its particular time slots. For example, the nth device Cn has to wait for ψn, which is represented by the following Equation 8.
where Wi and μ represent arrival and transmission time of a particular device Ci, respectively, in the proposed TDMA approach. Meanwhile, the serving time μ is represented by Equation 9.
where T represent the time interval of a particular time slot which is constant in the proposed mechanism. Thus, putting the value of μ in Equation 8, we get Equation 10 as given below.
which is further simplified into the following Equation 11, as given below.
To resolve this issue, the proposed TDMA approach allows devices deployed on edges of two or more clusters to switch from one cluster to another. This process is applicable only if its waiting time interval with the first cluster is longer than its expectation. However, this shifting process is bounded by certain rules which are given below.
1. Migration is applicable in early stages of the IIoT and only once for every interested wearable device Ci.
2. slot waiting time or the expected value of ψn for a wearable device Ci is greater than the defined threshold value.
3. The number of wearable devices Ci in current cluster Sj should be greater than that of neighboring cluster Sj+1 (if any exist).
4. A wearable device Ci, that is interested in migration, should be in direct communication range of the intended CH module Sjj + 1.
5. The intended CH module has not accepted any or at-most one migrated device Ci.
If a particular member device Ci fulfills the aforementioned restrictions, the proposed scheme allows this device to migrate from current CH module Sj to another CH Sj+1. For this purpose, this device Ci should inform the current CH module Sj before sending a cluster joining request to another CH module that is Sj+1. This previous information is helpful for the current CH; current CH Sj utilizes this time slot by assigning it to other member devices Ci+1 or repeating the process of dividing the radio frequency into the time slots. However, it is noteworthy that the migration process of any member device Ci is possible until the network becomes fully operational.
When a device interested in migration sends a request to join cluster message to the intended cluster head, it waits for a certain time interval which is sufficient to receive response message from the expected CH module Sj, as described in Equation 12
where Tb represents back-off or waiting time interval of device Ci, which is interested in migration and joining another CH module Sj. The concerned CH module Sj generates time slot for the migrated device Ci by dividing the radio frequency domain into time slots. However, every CH module is bounded to repeat (if necessary) slot generation process once or twice, but it should be completed before the network becomes fully operational. Once time slots are generated, the alloted time slot is shared with the migrated device Ci in the IoT networks.
Migration activity of member device Ci from one CH to another is very helpful in the efficient utilization of the available bandwidth, maximizing throughput of the underlined networks. Apart from it, slot waiting time is reduced, which is directly proportional to the number of member devices in a particular CH module Sj. Additionally, the proposed TDMA approach allows a device Ci to hold multiple slots (if available) as long as other member devices Ci+1 are not eager to communicate with the CH module Sj. However, a request should be sent by the concerned device Ci to the intended CH module Sj that multiple slots are required. For example, an IoT network is considered which has five CH modules Sj and fifty devices Ci where j=1…..5 and i= 1….50. Since the deployment process is random, it is quite likely that every CH module has different number of member devices. Apart from that, it is possible that a member device may be a part of two or more clusters, which is possible for those devices that are deployed on the edges of these clusters. However, unlike existing TDMA schemes, the proposed approach does not allow any device Ci to be a member of multiple cluster heads, resulting in data duplication and wastage of resources. Let us further assume that CH1, CH2, CH3, CH4, and CH5 have 15, 10, 10, 7, and 8 member devices, respectively. Thus, cluster heads CH1, CH2, CH3, CH4, and CH5 are bounded to generate 15, 10, 10, 7, and 8 time slots, respectively, and assign these slots to the member devices in FCFS. However, slot waiting time in CH1 is approximately double than that of CH4 and CH5, respectively. Thus, as suggested in the proposed TDMA approach, if two devices are migrated from CH1 to CH4 and tow to CH5, then waiting time interval in cluster head one,i.e., CH1, is reduced considerably, which enhances throughput of the networks. Although slot waiting time intervals in both cluster heads, i.e., CH4 and tow to CH5, are increased approximately, its impact on overall waiting time of the member devices is less as member devices are less than other modules in the network. The proposed neighborhood-enabled slot allocation scheme bounds every CH to maintain a closed ratio with the number of available slots and member devices in the IoT. Additionally, every member device is bounded to communicate within its allocated time slot and more slots are required, these should be assigned based on their availability. Furthermore, reserve slots are utilized only if a new device enters in the coverage area of the respective CH, and free slots are not available. A complete description of this whole process is graphically presented in a diagram or system model, which is shown in Figure 2.
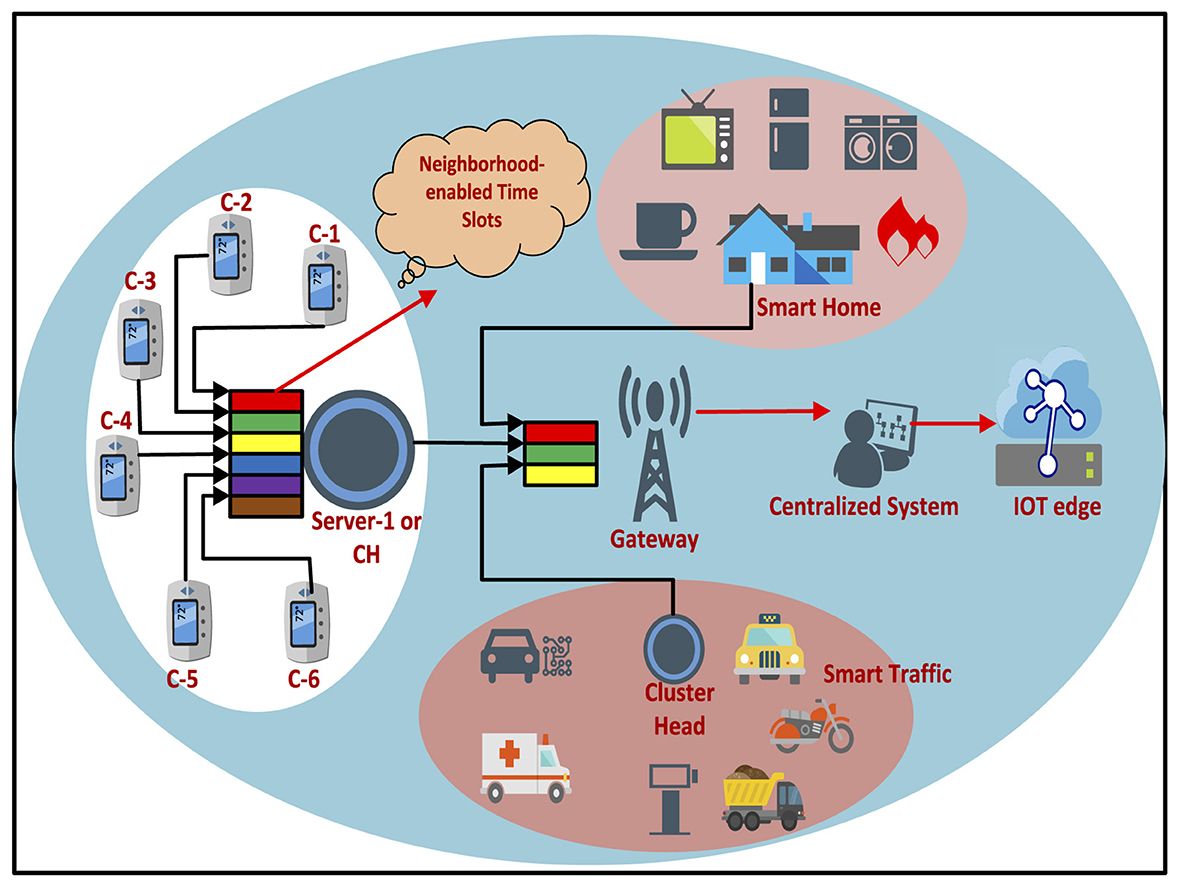
Figure 2. Graphical representation of the proposed neighborhood-enabled slot allocation scheme in the IoT.
5 Simulation results and discussion
In this section, a detailed analysis on the performance of the proposed machine learning and big data analytic-enabled approach in the light numerous evaluation metrics is presented. For this purpose, the proposed scheme along with the existing schemes is implemented in OMNET++ (?), where the signal to noise ratio and interference are assumed to be constant. Every member device was assumed to have initial energy of 52000 mAh, which was similar to the capacity of WaspMote Technology Pro-board (?). Moreover, we have assumed that transmission and processing power of the CH module are far more greater than an ordinary device. Simulation parameters, which are used in conducting these experiments both for existing and proposed approaches, are shown in Table 1. In this simulation, the expected channel rate was assumed as 9600 and 2400 bps, where value of μ = 0.5 and 2.8. For example, if channel rate is 9600 bps, then the length of a single packet is 86 * 8 bits ⇒ approximate length of a single slot is Ts = 64*8/9600 = 0.05s. Now, if the total member devices in a particular cluster is 15, then the frame length TsM = 0.75 s. Apart from it, channel delay was assumed as constant in both schemes, i.e., proposed and existing. These algorithms are evaluated using different and well-known performance metrics, such as message or packet delay during transmission, packet loss ratio, slot waiting time, and utilization of the empty slots.
5.1 Average slot waiting time in the industrial Internet of Things
Usually in TDMA schemes, a shorter average waiting time for a respective slot (preferably for dedicated time slot of a particular device) of a particular member device is considered as the best possible solution in the IIoT networks. Slot waiting is the approximate time a device must be in the waiting state for the allocated time slot in every frame. Generally, slot waiting time has a direct proportionality ratio to member devices in a particular cluster or server device. Figure 3 shows that the proposed approach is a feasible solution than the existing approaches for the resource-constraint devices as it reduces the waiting time of a particular member device to an expected level. On X-axis, individual slot time, that is based on the number of devices in the coverage area of the respective server, is presented, whereas the Y-axis shows the approximate time required for a member device to wait for its dedicated slot in the IoT. Furthermore, the proposed scheme achieves this milestone without compromising on other performance metrics in the IIoT networks. Similarly, the proposed scheme outperforms than the existing scheme if migration of member devices, preferably from one cluster to another, is carried out properly, as shown in Figure 4.
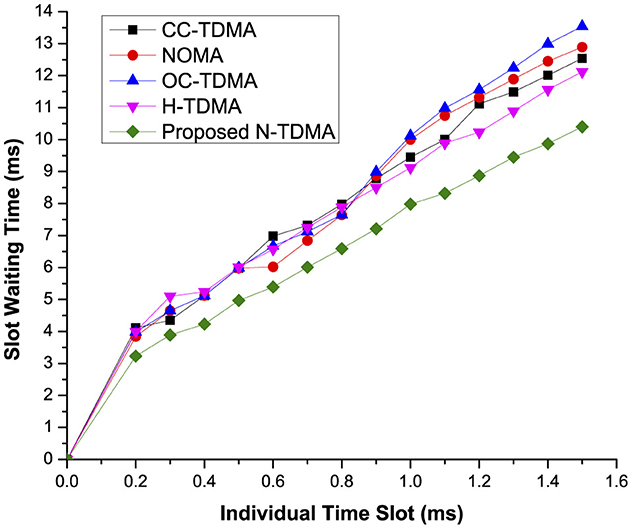
Figure 3. Proposed MLTDMA-based and field-proven approach evaluation (empty slots [without migration aware strategy]).
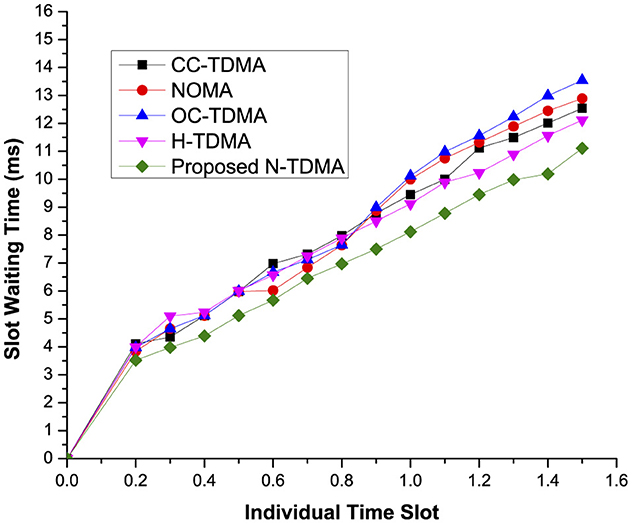
Figure 4. Proposed MLTDMA-based and field-proven approach evaluation (empty slots [with migration aware strategy]).
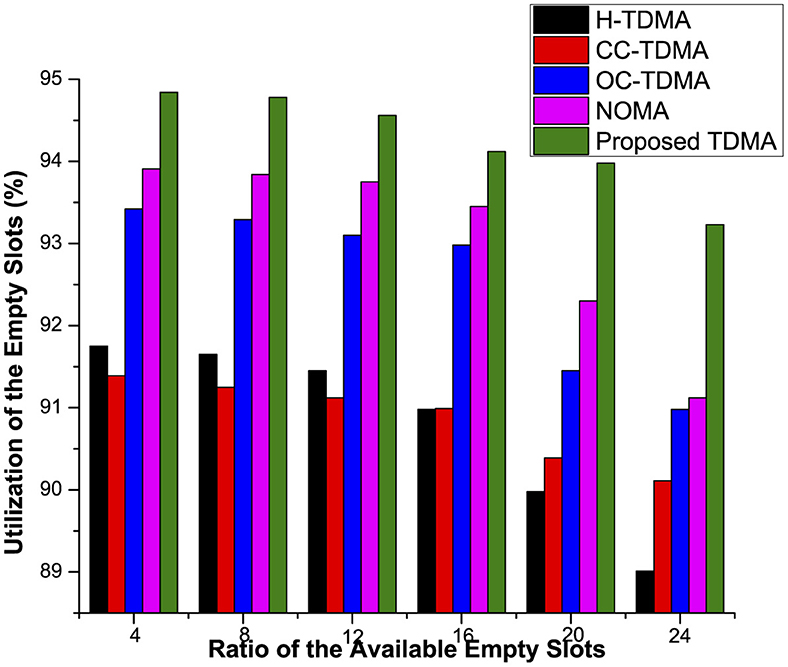
5.2 Empty slot utilization in the industrial Internet of Things
In both traditional and IIoT networking, it is high likely that a particular device may not be interested in the transmission activity either due to non-availability of data or other issues. Thus, slots allocated to such type of devices are empty, i.e., no data values, which is a wastage of the valuable resources that are bandwidth in this case. To address this issue, the proposed machine learning and TDMA-enabled approach allowed a particular device to use two or more slots in a single frame if available. Figure 5 presents a comparative analysis of the proposed and existing approaches preferably how efficiently empty slots are utilized. On X-axis, individual slot time, that is based on the number of devices in the coverage area of the respective server, is presented, whereas Y-axis show the approximate time required for a member device to wait for its dedicated slot in the IoT. Similarly, in even-based application, it is possible that only those member devices are interested in communication, where the expected event is triggered in their vicinity. Figure 6 shows that the proposed scheme outperformed approximately all the existing schemes by allocated two or more slots (depending on their availability) to those devices, which are eager to communicate the expected event information.
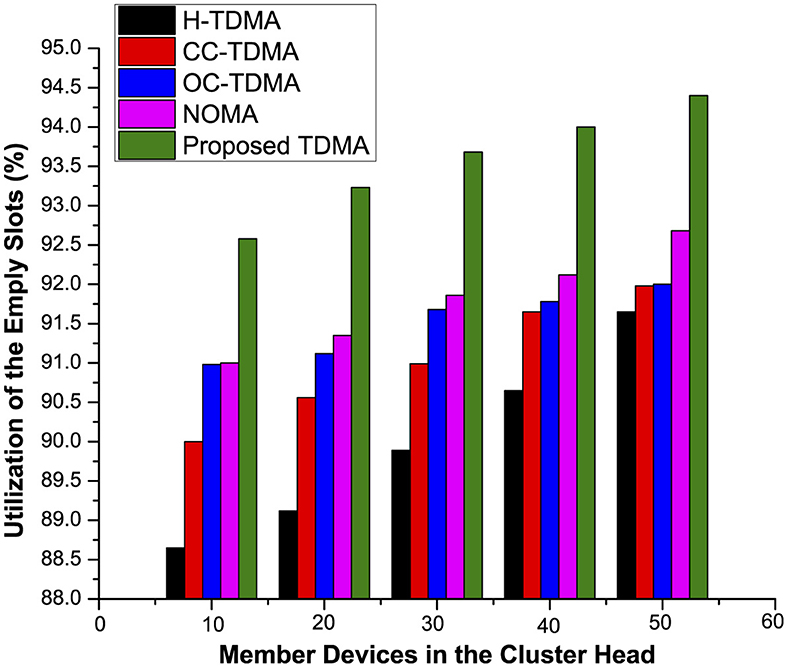
Figure 6. Proposed MLTDMA-based and field-proven approach evaluation (empty slots [event-based application]).
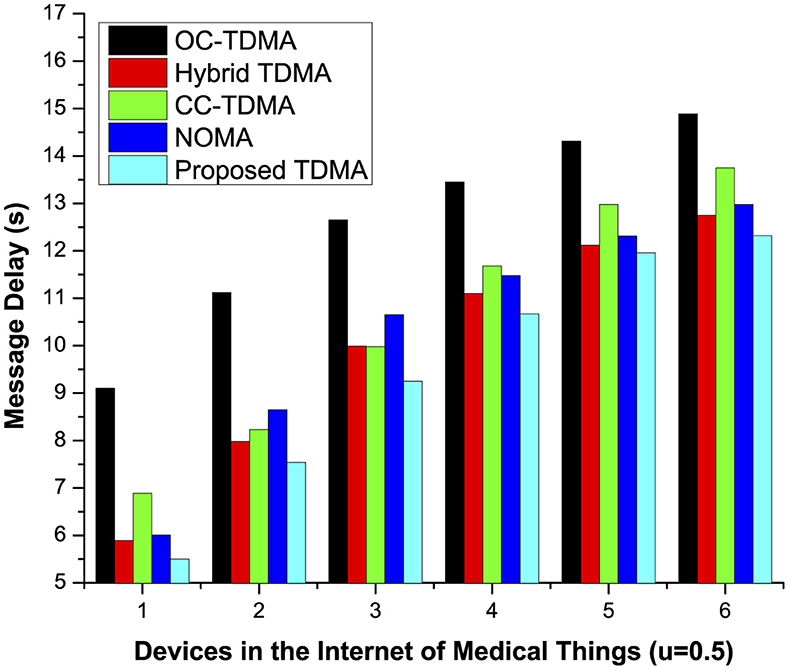
5.3 Average packet transmission delay in the industrial Internet of Things
The performance of the proposed machine learning-enabled communication and existing approaches preferably with respect to the average packet transmission delay is shown in Figure 7, which clearly depicts that the proposed scheme has achieved the minimum possible transmission delay, where value of μ = 0.5. On X-axis, member devices belong to the internet of things and have an average transmission delay of 0.5 are represented, whereas on Y-axis, the approximate ratio of delay is encountered or observed during the whole communication process. The proposed approach has accomplished this minimum possible ratio due to the allocation of multiple slots and migration of member devices from heavy loaded clusters. Furthermore, processing delay at both ends, i.e., source and destination devices, is minimized due to availability of slot(s) in the IIoT networks. The proposed machine learning and big data analytic-enabled approach have reduced approximately 13% of the average packet transmission delay in an active IIoT networking infrastructure.
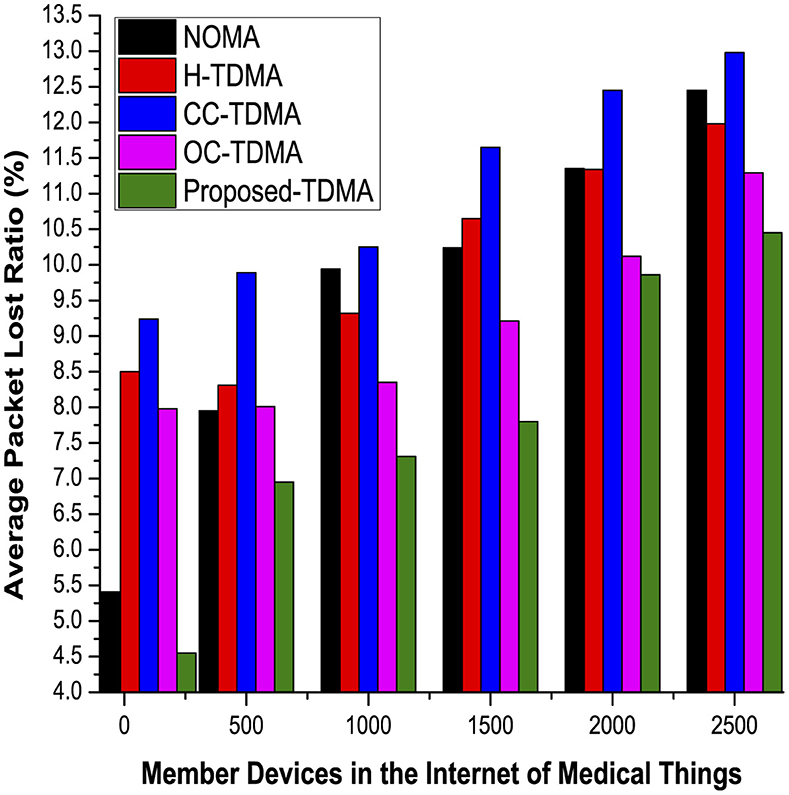
5.4 Packet or frame loss ratio in the industrial Internet of medical things
Packet or frame loss ratio is one of the common evaluating metrics which is used by researchers and scientific organizations to judge the performance of a communication approach in the realistic environment of IIoT networks. APLR is defined as the possible ratio of the total transmitted packets to those which are delivered successfully to the server Sj. APLR is assumed as the challenging evaluation and effective metrics to judge the performance of a communication protocol, particularly in the IIoT networking infrastructures. Therefore, the proposed machine learning and big data analytic-enabled communication approach are compared with the existing approaches with respect to their performance while using APLR as evaluation metric. Figure 8 shows that the proposed scheme has the ability to maintain the lowest possible ratio of the average packets, which are lost during the communication process. On X-axis, member devices belong to the IoT are represented, whereas on Y-axis, the approximate ratio of those packets which are lost during the communication process is depicted. The proposed scheme has achieved this milestone by allowing member devices to migrate from heavy loaded, i.e., CH with approximately maximum members, clustering into others where load is minimum.
5.5 Computational complexity
Generally, every physical object is defined through time and space parameters. Similarly, efficiency of an algorithm is determined through the complexity of these two parameters, particularly time and space. Both of these parameters are very crucial particularly in situations where devices are resources-constraint, i.e., IoT. The time complexity of the proposed scheme is O(n) as compared to other algorithms, that is On2 or even higher.
6 Conclusion and future directions
During the last two decades, the efficient utilization of resources, preferably bandwidth, was assumed as a challenging issue for communication approaches both in traditional and resource-constraint networks. In this study, machine learning and neighborhood slot allocation-enabled wireless communication approach were presented to address the aforementioned issue, particularly in the IoMT. Initially, uniform clustering is achieved through a modified k-mean clustering algorithm, where centroids were constants, i.e., cluster head in this case, which are approximately 5–10% of the ordinary devices. Then, a well-known distance measure was used to find member devices of every CH module, whereas devices reside on the edge of two or more CH modules were allowed to select any one of them. Furthermore, member devices are encouraged to migrate (in terms of membership not mobility) from one cluster to another cluster with certain rules and restrictions. Similarly, a member device was allowed to hold two or more slots if available in IIoT networks. Simulation results have verified that the proposed machine learning and big data analytic-enabled communication scheme are one of the best candidates than the existing approaches, especially IIoT networks. The proposed scheme has improved empty slot utilization ratio, approximately 13%, than the existing scheme with available resources.
In future, we will investigate performance of the proposed machine learning and big data analytic-enabled approach in the IoMT environment, where wearable devices are mobile. Furthermore, it will be interesting to observe the results of the proposed scheme in those IoMT networks where both wearable devices and CH are mobile.
Data availability statement
Publicly available datasets were analyzed in this study. This data can be found here: https://home.uncg.edu/cmp/downloads/lwsndr.html.
Author contributions
RK: Investigation, Software, Supervision, Writing – original draft, Writing – review & editing, Conceptualization, Funding acquisition, Project administration. MK: Formal analysis, Software, Writing – original draft, Writing – review & editing, Conceptualization, Investigation, Methodology, Project administration, Resources. NS: Conceptualization, Data curation, Methodology, Supervision, Writing – review & editing, Formal analysis, Project administration, Resources, Software. AA-R: Formal analysis, Funding acquisition, Project administration, Validation, Visualization, Writing – review & editing. AK: Investigation, Methodology, Project administration, Software, Validation, Writing – review & editing.
Funding
The author(s) declare financial support was received for the research, authorship, and/or publication of this article. This work was supported by Princess Nourah bint Abdulrahman University Researchers, supporting project number (PNURSP2024R235), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Acknowledgments
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2024R235), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Adame, T., Bel, A., Bellalta, B., Barcelo, J., and Oliver, M. (2014). IEEE 802.11 ah: the wifi approach for M2M communications. IEEE Wireless Commun. 21, 144–152. doi: 10.1109/MWC.2014.7000982
Alam, M., Ahmed, N., Matam, R., and Barbhuiya, F. A. (2024). Analysing the suitability of IEEE 802.11 ah for next generation internet of things: A comparative study. Ad Hoc Networks, page 103437, doi: 10.1016/j.adhoc.2024.103437
Alshehri, M. D., Hussain, F., Elkhodr, M., and Alsinglawi, B. S. (2019). “A distributed trust management model for the internet of things (DTM-IoT),” in Recent Trends and Advances in Wireless and IoT-enabled Networks (Cham: Springer).
Alshehri, M. D., Hussain, F. K., and Hussain, O. K. (2018). Clustering-driven intelligent trust management methodology for the internet of things (CITM-IoT). Mobile Netw. Appl. 23, 419–431, doi: 10.1007/s11036-018-1017-z
Bankov, D., Khorov, E., and Lyakhov, A. (2016). “The study of the distributed control method to hasten link set-up in IEEE 802.11 ah networks,” in 2016 XV International Symposium Problems of Redundancy in Information and Control Systems (REDUNDANCY) (St. Petersburg: IEEE), 13–17.
Batta, M. S., Aliouat, Z., and Harous, S. (2019). “A distributed weight-based TDMA scheduling algorithm for latency improvement in IoT,” in 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON) (New York, NY: IEEE), 0768-0774.
Batta, M. S., Harous, S., Louail, L., and Aliouat, Z. (2019). “A distributed tdma scheduling algorithm for latency minimization in internet of things,” in 2019 IEEE International Conference on Electro Information Technology (EIT) (Brookings, SD: IEEE), 108–113.
Bhatia, A., and Hansdah, R. C. (2013). “A distributed tdma slot scheduling algorithm for spatially correlated contention in WSNS,” in 2013 27th International Conference on Advanced Information Networking and Applications Workshops (Barcelona: IEEE), 377–384.
Chen, Y., Ji, F., Guan, Q., Wang, Y., Chen, F., and Yu, H. (2018). Adaptive RTO for handshaking-based MAC protocols in underwater acoustic networks. Future Generat. Comp. Syst. 86:1185–1192. doi: 10.1016/j.future.2017.08.022
Doost-Mohammady, R., Naderi, M. Y., and Chowdhury, K. R. (2016). Performance analysis of csma/ca based medium access in full duplex wireless communications. IEEE Trans. Mobile Comput. 15, 1457–1470. doi: 10.1109/TMC.2015.2462832
Faruque, S. (2019). “Time division multiple access (tdma),” in Radio Frequency Multiple Access Techniques Made Easy (Cham: Springer), 35–43.
Gope, P., Sikdar, B., and Millwood, O. (2021). A scalable protocol level approach to prevent machine learning attacks on puf-based authentication mechanisms for internet-of-medical-things. IEEE Trans. Indust. Inform. 18, 1971–1980. doi: 10.1109/TII.2021.3096048
Johari, S., and Krishna, M. B. (2020). Tdma based contention-free MAC protocols for vehicular ad hoc networks: a survey. Vehic. Commun. 28:100308. doi: 10.1016/j.vehcom.2020.100308
Khan, M., Khan, R., Shah, N., Ghani, A., Chelloug, S. A., Nisar, W., et al. (2023). Sensing and device neighborhood-based slot assignment approach for the internet of things. Appl. Sci. 13, 4682, doi: 10.3390/app13084682
Khan, M., Shah, N., Khan, R., Nisar, M. W., Khan, M., Ali, I., et al. (2021). Neighbourhood oriented TDMA scheme for the internet of things-enabled remote sensing. Eur. J. Remote Sens. 19:1–11, doi: 10.1080/22797254.2021.1977717
Khan, W. U., Jameel, F., Jamshed, M. A., Pervaiz, H., Khan, S., and Liu, J. (2020). Efficient power allocation for noma-enabled IoT networks in 6g era. Phys. Commun. 39:101043, doi: 10.1016/j.phycom.2020.101043
Lee, J. H., and Cho, S. H. (2017). Tree TDMA MAC algorithm using time and frequency slot allocations in tree-based wsns. Wireless Person. Commun. 95, 2575–2597. doi: 10.1007/s11277-016-3938-9
Li, Y., Zhang, X., Zeng, J., Wan, Y., and Ma, F. (2017). A distributed tdma scheduling algorithm based on energy-topology factor in internet of things. IEEE Access 5, 10757–10768, doi: 10.1109/ACCESS.2017.2710304
Nassereddine, M., and Khang, A. (2024). “Applications of internet of things (IoT) in smart cities,” in Advanced IoT Technologies and Applications in the Industry 4.0 Digital Economy (Boca Raton, FL: CRC Press), 109–136.
Nguyen, T. T., Kim, T., and Kim, T. (2020). A distributed tdma scheduling algorithm using topological ordering for wireless sensor networks. IEEE Access 8, 145316–145331. doi: 10.1109/ACCESS.2020.3014802
Nguyen, T. T., Pham, Q. V., Nguyen, V. D., Lee, J. H., and Kim, Y. H. (2020). Resource allocation for energy efficiency in OFDMA-enabled WPCN. IEEE Wireless Commun. Lett. 9, 2049–2053, doi: 10.1109/LWC.2020.3012206
Pawlowski, M. P., Jara, A. J., and Ogorzalek, M. J. (2014). “Extending extensible authentication protocol over IEEE 802.15. 4 networks,” in 2014 Eighth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (Birmingham: IEEE), 340–345.
Ramachandran, A., Taj, M. A., Maheshwari, M., and Karuppiah, A. (2020). “Design and simulation of multi-channel V-TDMA for IoT-based healthcare systems,” in Smart Trends in Computing and Communications: Proceedings of SmartCom 2020 (Cham: Springer), 319–329.
Shahab, M. B., and Shin, S. Y. (2018). Time shared half/full-duplex cooperative noma with clustered cell edge users. IEEE Commun. Lett. 22, 1794–1797, doi: 10.1109/LCOMM.2018.2853627
Shahin, N., Ali, R., and Kim, Y. T. (2018). Hybrid slotted-CSMA/CA-TDMA for efficient massive registration of IoT devices. IEEE Access 6:18366–18382, doi: 10.1109/ACCESS.2018.2815990
Shahin, N., Tann, L., and Kim, Y. T. (2016). “Enhanced registration procedure with NAV for mitigated contentions in M2M communications,” in 2016 18th Asia-Pacific Network Operations and Management Symposium (APNOMS) (Kanazawa: IEEE), 1–6. doi: 10.1109/APNOMS.2016.7737198
Song, Y., Yu, F. R., Zhou, L., Yang, X., and He, Z. (2020). Applications of the internet of things (IoT) in smart logistics: a comprehensive survey. IEEE Internet Things J. 8, 4250–4274, doi: 10.1109/JIOT.2020.3034385
Sun, Y., Ding, Z., Dai, X., and Dobre, O. A. (2019). On the performance of network NOMA in uplink comp systems: a stochastic geometry approach. IEEE Trans. Commun. 67, 5084–5098, doi: 10.1109/TCOMM.2019.2906307
Wang, R., Lai, J., Li, X., He, D., and Khan, M. K. (2024). Rpifl: reliable and privacy-preserving federated learning for the internet of things. J. Netw. Comp. Appl. 221:103768, doi: 10.1016/j.jnca.2023.103768
Ye, Q., and Zhuang, W. (2017). Token-based adaptive MAC for a two-hop internet-of-things enabled manet. IEEE Inter. Things J. 4, 1739–1753, doi: 10.1109/JIOT.2017.2679119
Keywords: Internet of Things, remote sensing, k-mean, clustering, time division multiple access (TDMA), communication
Citation: Khan R, Khan M, Shah N, Al-Rasheed A and Khan AA (2024) Device-enabled neighborhood-slot allocation for the edge-oriented Internet of Things. Front. Comput. Sci. 6:1343778. doi: 10.3389/fcomp.2024.1343778
Received: 24 November 2023; Accepted: 10 July 2024;
Published: 26 July 2024.
Edited by:
Saif Ul Islam, Institute of Space Technology, PakistanReviewed by:
Cheng Wang, Beijing University of Posts and Telecommunications (BUPT), ChinaLexi Xu, China United Network Communications Group, China
Lorena Parra, Universitat Politécnica de Valéncia, Spain
Copyright © 2024 Khan, Khan, Shah, Al-Rasheed and Khan. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Amal Al-Rasheed, YWFhbHJhc2hlZWRAcG51LmVkdS5zYQ==; Rahim Khan, cmFoaW1raGFuQGF3a3VtLmVkdS5waw==
 Rahim Khan
Rahim Khan Mushtaq Khan2
Mushtaq Khan2 Nadir Shah
Nadir Shah