- 1National Institute of Psychology, Quaid-i-Azam University, Islamabad, Pakistan
- 2Department of Applied Psychology, The Women University Multan, Multan, Pakistan
- 3Disability and Psychoeducational Studies, The University of Arizona, Tucson, AZ, United States
- 4Department of Applied Psychology, National University of Modern Languages (NUML), Islamabad, Pakistan
The study examines both general and Internet and Communication Technology (ICT) self-efficacy in cyber-victims, cyber-bullies, and cyber bully victims in comparison to un-involved students. Gender differences were also examined. A total of 1115 Pakistani university students from six universities participated in the study. Analyses were conducted on 950 complete cases (371 males, and 579 females). Data were collected on cyberbullying/victimization, general self-efficacy (GSE), ICT self-efficacy, traditional bullying/victimization, ICT usage, social desirability, and demographics. Multinomial logistic regression analysis indicated that ICT self-efficacy significantly decreased the probability of being a cyber-victim and significantly increased the chances of being a cyber-bully whereas GSE appeared to have no role in predicting participant roles in cyberbullying after controlling for covariates (i.e., age, gender, traditional bullying, traditional victimization, social desirability, Internet usage, time spent on the Internet, and social networking sites (SNS). Findings of the study have important implications for developing and enhancing interventions with respect to the inclusion of ICT related skills in anti-cyberbullying programs. With respect to gender, findings showed that females reported a higher level of victimization while males reported higher perpetration on both traditional and cyberbullying.
Introduction
Rapid development of Internet Communication Technology (ICT) has facilitated opportunities for developing social connections, fast digital interactions, and the availability of interactive and self-directed learning (Mishna et al., 2018). Access to information and dissemination of information to a larger audience have become easy with the use of Internet and social media tools (Heirman and Walrave, 2008; Patchin and Hinduja, 2011). Although ICT and fast-growing digital technologies have provided many benefits to students in higher education, these technologies also have a darker side that can be used to inflict harm to others (Mishna et al., 2010; Musharraf and Lewis, 2016). One such harmful behavior is cyberbullying.
Cyberbullying is “any behavior performed through electronic or digital media by individuals or groups that repeatedly communicates hostile or aggressive messages intended to inflict harm or discomfort on others” (Tokunaga, 2010) that involves a power imbalance between a target and the perpetrator (Olweus, 1993; Kowalski et al., 2014). Cyberbullying can be inflicted through text messages, websites, emails, blogs, chat rooms, social networking sites (SNS), digital apps such as Instagram, Twitter, Facebook, Skype, WhatsApp, Snapchat, video sharing platforms, and game servers, etc. (Cassidy et al., 2018). These behaviors include sending intimidating, threatening shameful and harassing messages, posting false rumors about the target, sharing private and sensitive information about others online, stealing someone’s online identity by creating fake profiles and web pages, and deliberately excluding someone from an online group (Li, 2007; Willard, 2007; Nocentini et al., 2010).
Cyberbullying emerged over the past two decades with the globalization of the internet (Festl, 2016), and has become an international public health issue not only for children and adolescents but also for adults (Nixon, 2014). Research has found that cyberbullying victimization among university students is associated with wide-ranging devastating psychological and mental health problems including, anxiety, stress, depression, irritability, helplessness, loneliness, sleep disturbances, and difficulties in maintaining concentration (Faucher et al., 2014; Cassidy et al., 2017; Musharraf and Lewis, 2018) and in more extreme situations even suicidal ideation (Schenk and Fremouw, 2012; Mitchell et al., 2018). Furthermore, cyberbullying perpetration in this population is associated with low empathy, high impulsivity, hostility, depression, and psychoticism (Arıcak, 2009; Doane et al., 2014; Kokkinos et al., 2014). Despite the serious impacts of cyberbullying/victimization among university students, less attention has been given to investigate this phenomenon among university students and only few studies have investigated its association with individual level variables such as self-efficacy. Further, inconsistent findings have been found concerning gender differences in cyberbullying (Larrañaga et al., 2016).
There is a controversy in the literature over whether cyberbullying is an extension of the traditional form of bullying or a unique and separate phenomenon (Antoniadou and Kokkinos, 2015). There are two important considerations in favor of the former position. First, both traditional and cyberbullying often occur together (Beran and Li, 2005), and a high degree of overlap exists in the involvement of students in traditional and cyberbullying (Olweus, 2012a, b). Second, both types of bullying share common risks and protective factors (Hase et al., 2015; Völlink et al., 2016).
One such protective factor is self-efficacy (Sapouna and Wolke, 2013). Self-efficacy is a component of Albert Bandura’s Social Cognitive Theory (e.g., Bandura, 1994, 2008). Self-efficacy refers to an individuals’ judgment of his or her personal capabilities to achieve designated goals, organize and perform a course of action, and regulate one’s psychological functioning (Bandura, 1997). Prior research concerning traditional bullying victimization has revealed a negative association between victimization and general self-efficacy (GSE) among school students (Erath et al., 2010; Kokkinos and Kipritsi, 2012). However, inconsistent findings have been reported in the literature with reference to GSE and traditional bullying perpetration. For example, Natvig et al. (2001) found a significant positive association between self-efficacy and perpetration of bullying among adolescents, and this association was stronger for older students. In contrast, others found a negative association between GSE and the perpetration of bullying (Kokkinos and Kipritsi, 2012).
This line of inquiry has been further extended to examine the relationship of self-efficacy to cyberbullying victimization and perpetration. For instance, a study by Olenik-Shemesh and Heiman (2014) showed that a lower level of social and emotional self-efficacy was found in cyber victims than in non-victims. Other studies found a negative association between GSE and both cyberbullying victimization and perpetration (Wong et al., 2014; Eden et al., 2016). The construct of self-efficacy is highly domain-specific instead of a general disposition, and thus changes across circumstances, settings, and situations (Bandura, 1986). In view of this, Bussey et al. (2015) found that self-efficacy beliefs to engage in cyberbullying were positively associated with cyberbullying perpetration.
Considering a domain-specific approach, it is imperative to investigate the role of ICT self-efficacy in cyberbullying and victimization. Until recently, a few studies focused on ICT self-efficacy with reference to cyberbullying, and inconsistent findings have been reported. For example, Xiao and Wong (2013) found that Internet self-efficacy has a significant positive impact on the perpetration of cyberbullying. Similarly, a significant positive association between Internet self-efficacy and the perpetration of cyberbullying was detected in a study by Musharraf et al. (2018). Conversely, Savage and Tokunaga (2017) found that Internet self-efficacy was not associated with cyberbullying perpetration; however, verbal aggression moderated the relationship between social skills and cyberbullying perpetration only for those who possess high Internet self-efficacy. This study did not examine the relationship of cyber victimization with Internet self-efficacy. Additionally, Internet self-efficacy was measured by a scale (Eastin and LaRose, 2000) that only contains items relating to Internet software, hardware, and trouble shooting. Hence, these items may not reflect the skills used in cyberbullying.
Besides these inconsistent findings, there is a clear lack of research with reference to ICT self-efficacy and cyber victimization. Further, to date no study examined the comparative role of General and ICT self-efficacy in predicting cyberbullying and victimization. Bullying has been considered a group process and students involved in bullying or cyberbullying may assume different roles such as bully, victim, bully victim and un-involved (Salmivalli et al., 1996). The current research therefore was conducted to bridge the gap by examining the comparative role of general and ICT self-efficacy in determining the involvement of university students in different cyberbullying roles.
Existing research indicated several potential factors that may attribute to the variation in reports of cyberbullying/victimization (Betts, 2016). For example, variations in the prevalence rates have been reported with reference to the characteristics of the sample of the study such as their gender, age, usage of ICT, and amount of time spent online. Inconsistent findings have been reported concerning gender and cyberbullying/victimization. Some studies demonstrated greater victimization of males than females (Wensley and Campbell, 2012) while others reported greater victimization of females in comparison to males (Paullet and Pinchot, 2014; Caravaca-Sanchez et al., 2016; Webber and Ovedovitz, 2018). A number of studies found no gender differences (MacDonald and Roberts-Pittman, 2010; Wozencroft et al., 2015; Gibb and Devereux, 2016). Further, several studies found males outnumbered females for cyberbullying perpetration (Ballard and Welch, 2017), who were involved more as victims and bullies (Akbulut and Eristi, 2011; Wong et al., 2018) and as bullies and mixed victim-bullies (Cunningham et al., 2015; Kokkinos et al., 2016) in comparison to females. Conversely, some studies indicated females were found to be higher in performing cyberbullying behaviors (Schenk et al., 2013) and more involved as both victims and bullies in comparison to males (Francisco et al., 2015).
With reference to age, it has been found that younger students experience more cyberbullying than the older students (Ševčíková and Šmahel, 2009; Zalaquett and Chatters, 2014). Further, research demonstrated that higher ICT usage, more time spent online generally, or particularly on social media may influence the likelihood with which one experiences cyberbullying or performs cyberbullying perpetration (Livingstone and Helsper, 2010; Leung and Lee, 2012; Zhou et al., 2013; Navarro et al., 2017).
Olweus (2012a, b, 2013) recommended researchers to measure cyberbullying contemporarily in the broader context of traditional bullying. This allows researchers to contextualize the level of normative aggression within a particular sample. Further, he cautioned researchers that associated harms of cyberbullying/victimization should not be taken without considering the co-existing harms of traditional bullying/victimization (Olweus, 2012a, b). In addition, social desirability is another potential factor that can lead to over-reporting or under-reporting or of cyberbullying/victimization. University students generally consider cyberbullying as socially undesirable behavior (Akbulut and Eristi, 2011; Betts, 2016) and existing research reported a positive association between cyberbullying and social desirability (Doane et al., 2013).
In view of all this, the well-established covariates such as age, gender, concurrent involvement in traditional bullying and victimization, ICT usage, time spent on the Internet, time spent on SNS and social desirability (Betts, 2016; Wolke et al., 2016), were controlled for the precise estimation of the comparative role of general and ICT self-efficacy in determining the involvement of students in different roles of cyberbullying among Pakistani university students.
Materials and Methods
Sample
The sample for this study was comprised of 1115 Pakistani university students from six different universities. Only complete cases were included in the analyses using listwise deletion for handling missing which resulted in 950 valid cases. Listwise deletion means that if a participant had missing data on any variable in the analysis, their case was removed. Age of the participants ranged from 18 to 25 years with Mean ± 20.79 and SD = ±1.94. Out of the total sample, 39.05% were males and 60.95 % were females. A total of 57% participants were enrolled in undergraduate, and 43% in masters programs. Further, 73.97% participants were enrolled in social sciences and arts, and the remaining 24.96% were from natural sciences disciplines.
Measures
Cyberbullying and Cyber Victimization Scales
Following existing research (Del Rey et al., 2015), and findings of a qualitative study (Musharraf et al., 2018), the scales were developed by the first author and validated on a sample of Pakistani university students (Musharraf and Anis-ul-Haque, 2018b) Each of the cyberbullying and cyber victimization scales included 20 Likert-type items with response options ranging from (0) “Never” to (4) “More times a week.” Sample items include: “Someone posted my private pictures or videos online in a mean or hurtful way” for cyber victimization scale and “I posted someone’s private pictures or videos online in a mean or hurtful way” for cyber bullying scale.
The time frame of “past 12 months” was used to ask respondents about the frequency of cyberbullying and cyber victimization. The scales are scored in two different ways. A sum of the scores on all items of each scale represents an overall score on that scale and high scores on each scale signifies higher levels of cyberbullying and cyber victimization, respectively (Musharraf and Anis-ul-Haque, 2018b). The overall scores on each scale can be used as a continuous score. Further, the scores on the scale can be used to categorize individuals into one of the four groups: cyber victims, cyber bullies, cyber bully victims, and un-involved (see Musharraf and Anis-ul-Haque, 2018a). Following Del Rey et al. (2015), this categorization was made on the basis of behaviors participation and repetition in a particular role. Thus, cyber-victims were those participants who scored equal or higher than (2) “once a month” in any of the items of cyber victimization scale and with scores equal or lower than (1) “once or twice” in all of the items of cyber bullying scale. Cyber bullies were identified as those subjects who scored equal or higher than (2) “once a month” in any of the items of cyber bullying scale and equal or lower than (1) “once or twice” in all of the items of cyber victimization scale. Cyber bully/victims were those participants who scored equal or higher than (2) “once a month” in any of the items of both cyber victimization and cyber bullying.
For the present study, both continuous and categorical scores were used. The continuous scores were used to conduct preliminary analysis, whereas the categorical scores were used for the classification into groups by the different roles in cyberbullying. The scale has good internal consistency; Cronbach’s alphas 0.83 to 0.85 were reported (Musharraf and Anis-ul-Haque, 2018b), and for the present study Cronbach’s alphas 0.83 and 0.86 were found for the Cyberbullying and Cyber Victimization Scales, respectively.
General Self-Efficacy (GSE)
General Self-efficacy was assessed by ten-item scale (Schwarzer and Jerusalem, 1995). The scale has response options on a 4-point Likert scale ranging from 1 (Not at all true) to 4 (Exactly true). The overall score on the scale was determined by summing all the items and scores ranged from 10 to 40; higher scores signify higher levels of GSE. Example items include: “I am confident that I could deal efficiently with unexpected events” and “If I am in trouble, I can think of a good solution.” The scale has good reliability with alpha coefficients ranging from 0.76 to 0.90 (Schwarzer and Jerusalem, 1995). Alpha coefficient of 0.88 showed high internal consistency of the scale for the present study sample. The validity of the scale was established by finding positive correlations of the total score on the GSE to work satisfaction, and optimism and the negative correlations to stress, depression, burnout, and anxiety (Schwarzer and Jerusalem, 1995).
ICT Self-Efficacy Scale
ICT Self-efficacy Scale is a self-report measure comprised of 18 items and scored on a 5-point Likert type scale ranging from (1) “Disagree strongly” to (5) “Agree strongly.” The overall score on the scale is obtained by summing all the items. A higher score on the scale indicates a higher level of ICT-self-efficacy. Sample items include: “I can easily recover my email /social networking account if I forget the password” and “I can easily report a fake account pretending to be me.”
The scale was developed and validated on university students and has good internal consistency with alphas ranging from 0.92 to 0.93 (Musharraf et al., 2018) and alpha 0.92 was found for the present study.
California Bully Victimization Scale (CBVS)
Traditional bullying and victimization were measured by CBVS (Felix et al., 2011), that originally consisted of 16 items that measure traditional bullying and victimization in students. Eight items measure traditional victimization by asking the respondents to rate their responses on a five-point Likert scale ranging from (0) “Never” to (4) “More times a week.” Similarly, a parallel set of eight items measures traditional bullying. For the present study, two items related to the measurement of cyberbullying and cyber victimization were removed because we used a separate scale for this measurement. The time frame of “past 12 months” was used to measure the frequency of bullying and victimization. Example items include: “How often have you been threatened in a mean or hurtful way?” for victimization dimension and “How often have you threatened another student in a mean or hurtful way?” for bullying dimension. Atik and Guneri (2012) reported satisfactory internal consistency ranged from 0.72 to 0.83 for the scale. For the present study sample, the scales showed good internal consistency with alpha 0.79, and 0.83 for victimization dimension and for bullying dimension, respectively.
ICT Use Scale
The ICT Use scale was originally developed to measures adolescents’ ICT use (Sticca et al., 2013). The scale was adapted to use in the present study with reference to university-aged students and consists of 16 statements tapping the frequency of online activities. Examples of these activities include: phone calls, chatting, posting information online, playing computer, or video games, etc. Respondents were asked to report how often they had performed these activities in the past 12 months. Responses options are on a five-point Likert scale ranging from (1) “never” to (5) “almost daily.” The scores are summed to find an overall score, and a higher score indicates higher ICT use. The scale showed good internal consistency with alpha reliability 0.93 for the present sample. Along with online activities, respondents were also asked to report the average duration of time spent online on any weekday, on weekends (i.e., Sunday or holiday), and time spent on SNS.
Social Desirability Scale (SDS)
The social desirability scale (SDS) is a 16-item scale measuring behaviors that are considered socially desirable. The scale has a dichotomous response style with (0) “False” and (1) “True.” Six items are reversed scored. Items are summed to get an overall score on the scale and high score on the scale represent a higher level of social desirability in respondents. Sample items include: “I occasionally speak badly of others behind their back” and “During arguments I always stay objective and matter-of-fact.” The scale is a valid and reliable measure of the social desirability and Cronbach’s alpha reliability ranged from 0.72 to 0.80 in various studies (Stöber, 2001). Cronbach’s alpha reliability of 0.77 was found for the present study.
Procedure
Before data collection, the proposal for the study was evaluated and approved by the Ethical Review Board of the National Institute of Psychology, Quaid-i-Azam University, Islamabad, against the American Psychological Association ethical guidelines. Participants were approached at their respective universities. Participants were briefed about the objectives of the study and both verbal and written consent were taken. Students who agreed to participate were then asked to sign a voluntary consent form before their participation in the study. An anonymous survey composed of the measures described above was administered to participants in a group setting during class hours.
Results
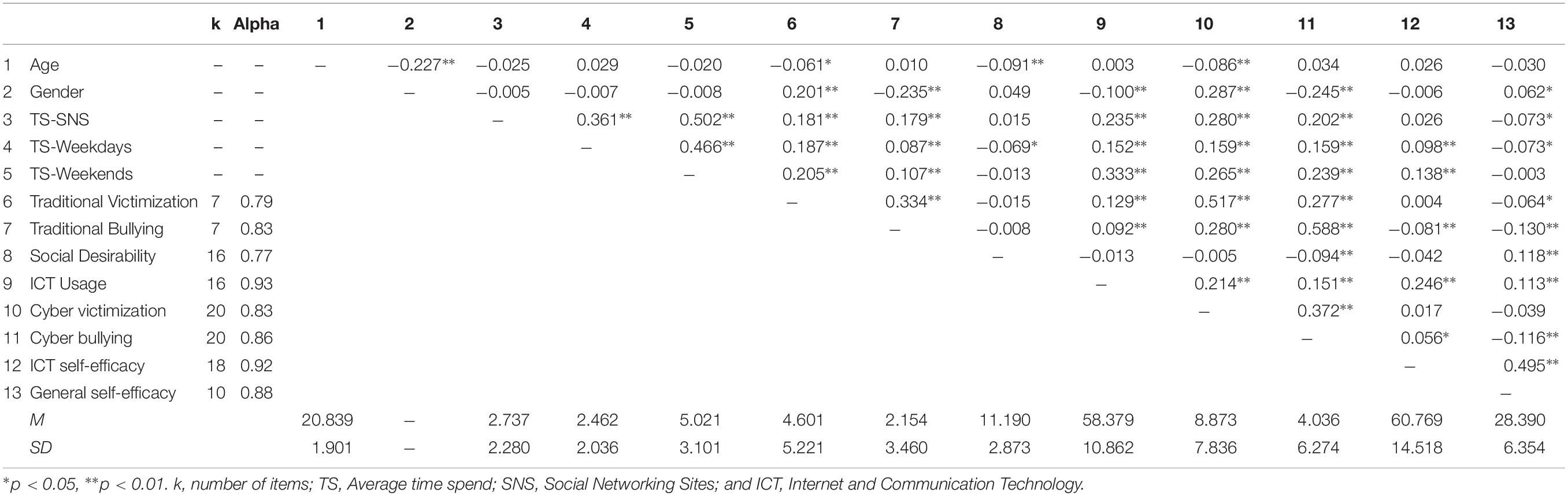
The present study was designed to investigate the comparative role of general and ICT self-efficacy in determining the different roles in cyberbullying. Following existing research by Del Rey et al. (2015), respondents ratings on cyber bullying and victimization scales were used to categorize participants into cyber-bullies (n = 66), cyber-victims (n = 286), cyber bullies-victim (n = 260), and un-involved (n = 338). Sum scores on cyberbullying and victimization scale were used for preliminary analysis. Results presented in Table 1, showed that age was negatively correlated with both traditional victimization (r = −0.06, p < 0.05), and cyber victimization (r = −0.09, p < 0.01) suggesting that younger students are more likely to be victimized. Gender appeared to be positively correlated with traditional and cyber victimization (r = 0.20, and 0.29, respectively, p < 0.01) and negatively correlated with both traditional and cyberbullying (r = 0.24, and 0.25, respectively, p < 0.01). These results suggested that females are more vulnerable to be victims both in traditional and cyber contexts whereas males are more prone to bullying perpetration. Time variables (i.e., average time spent on the internet on a weekday, weekend, and average time spent on SNS) as well as ICT usage were positively correlated with both cyber victimization (r range = 0.16 to 0.29, p < 0.01), and cyberbullying (r range = 0.16 to 0.59, p < 0.01). These results suggest that spending more time on the Internet and particularly on SNS is associated with increased cyberbullying perpetration as well as increased risk of cyber victimization. Finally, cyberbullying perpetration was positively correlated with ICT self-efficacy (r = 0.06, p < 0.05) whereas it was negatively correlated with GSE (r = −0.12, p < 0.01) indicating that ICT self-efficacy may increase cyberbullying perpetration whereas GSE may be a protective factor that decreases the likelihood of indulging in cyberbullying perpetration.
Gender differences as presented in Table 2 further confirmed the correlational findings, suggesting that both traditional and cyber victimization are higher in females as compared to male students. Female participants reported on average 2.14 (p < 0.01) points higher rates of traditional victimization and 6.15 (p < 0.01) points higher cyber victimization compared to their male counterparts. In contrast, males scored higher than females on both traditional bullying (Mean difference = 1.65; p < 0.01) and cyberbullying (Mean difference = 3.13; p < 0.01). These results also indicated that the risk for female victimization is almost three times greater and bullying perpetration of males is two times greater in the cyber context. Considering that girls were significantly younger than boys and that younger students were more vulnerable to both traditional and cyber victimization, we further extended our analysis to estimate unique role of gender by controlling confounding effect of age. Partial correlations of gender with traditional bullying and victimization and cyberbullying and victimization were computed controlling for the effect of age. The results showed very little change in partial correlation coefficient from zero-order correlation coefficient for traditional victimization (r0 = 0.20 to rp = 0.19) and cyber victimization (r0 = 0.29 to rp = 0.28) and no change in traditional bullying and cyberbullying. These results further provided evidence of gender differences in the prevalence of bullying and victimization both in traditional and cyber context. Though no significant differences emerged on time variables (i.e., average time spend on the Internet on a weekday, weekend, and average time spend on SNS), ICT usage was significantly higher (Mean difference = 2.21, p < 0.01) in male university students in comparison to their female counterparts. Similarly, no significant gender differences appeared on ICT self-efficacy, yet females scored on average 0.80 (p < 0.05) points higher on GSE.
Multinomial logistic regression analysis was conducted to test the role of general and ICT self-efficacy in the different roles in cyberbullying (the categorical outcome variables based on Del Rey et al. (2015) classification) while controlling for the effect of covariates (i.e., age, gender, average time spent on the Internet on a weekday, weekend, average time spent on SNS, ICT usage, traditional bullying, traditional victimization, and social desirability). The probability of students being classified as cyber-victims, cyber-bullies, and cyber bullies-victim was predicted in reference to the un-involved group. The log-likelihood of the model significantly decreased (χ2 = 520.53, p < 0.01) from the baseline model suggesting that the regression model explained a significant amount of variance in different roles of cyberbullying. Both Pearson and Deviance statistics appeared to be non-significant, suggesting that model is a good fit to the data. The model explained substantial variance, with Cox and Snell R2 = 0.42 (Cox and Snell, 2018), and Nagelkerke’s R2 = 0.46 (Nagelkerke, 1991). The results presented in Table 3 show that ICT self-efficacy significantly decreased the probability of being a cyber-victim (B = −0.02, p < 0.01) and significantly increased the chances of being a cyber-bully (B = 0.03, p < 0.05). The odds ratios further showed that each unit decrease in ICT self-efficacy increased the chances of being a cyber-victim by 1.02 times and each unit increase in ICT self-efficacy increased chances of becoming a cyber-bully by 1.03 times. Neither general nor ICT self-efficacy significantly predicted being a cyber bully victim. A comparison of both general and ICT self-efficacy in determining the different roles in cyberbullying is further illustrated in Figure 1, which was developed using estimated marginal means and standard errors of both general and ICT self-efficacy. The marginal means and standard errors were estimated using MANCOVA for controlling the effect of covariates. The graph shows a non-significant role of GSE in all roles of cyberbullying. In contrast, a significant decrease in ICT self-efficacy is associated with being a cyber-victim and a significant increase in ICT self-efficacy is associated with being a cyber-bully.
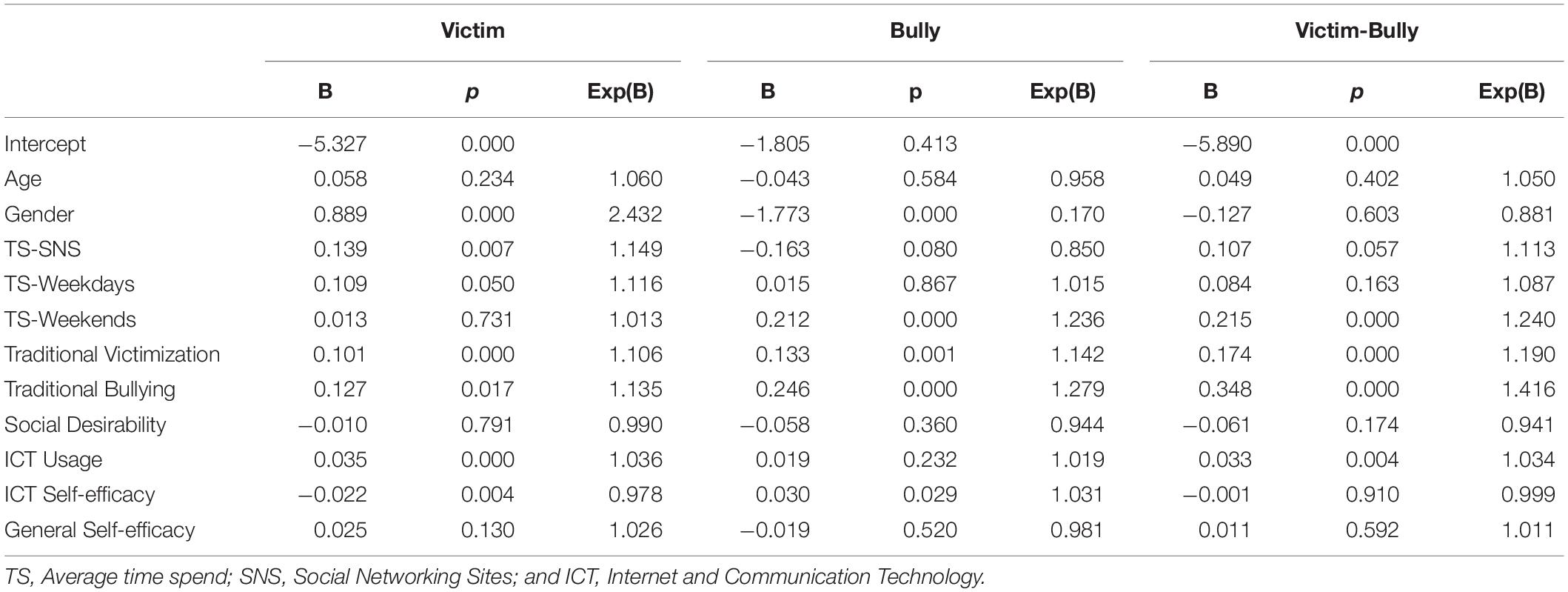
Table 3. Logistic regression coefficient and odd ratios to predict different roles in cyberbullying (N = 950).
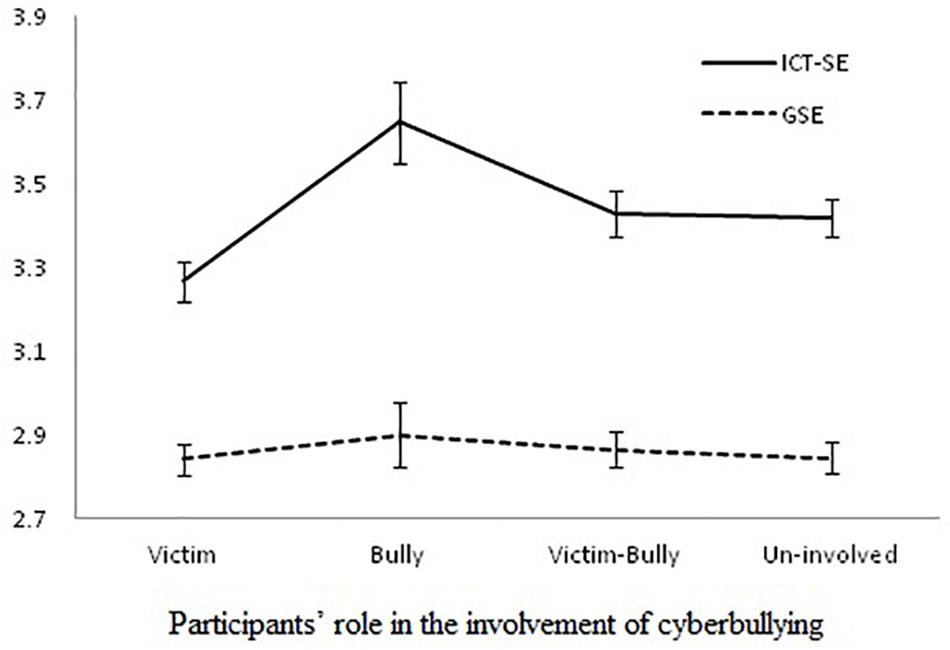
Figure 1. Comparison of general self-efficacy and ICT self-efficacy for participants’ role in the involvement of cyberbullying.
Discussion
Despite the growing evidence about the high prevalence and deleterious impacts of cyber bullying, less is known about the predictive factors particularly germane to cyberbullying. Most previous studies focused on extending the application of existing knowledge about traditional bullying to cyberbullying instead of examining the factors particularly relevant to cyberbullying with respect to digital context and online spaces. Therefore, the present aim was to examine the comparative role of general and domain-specific ICT self-efficacy in predicting the involvement of university students in various roles in cyberbullying after controlling the well-established covariates. Six points are worthy of discussion.
First, there were a significant negative associations between age and both traditional and cyber victimization. This indicates that younger students are more vulnerable to victimization. This finding is in agreement with the previous studies (Ševčíková and Šmahel, 2009; Zalaquett and Chatters, 2014) which showed that younger students were more often the victims in comparison to older students. To explain this, Smith et al. (1999) suggest that older students acquire social skills and coping techniques that help them to deal with bullying victimization more practically and successfully.
Second, findings of the present study demonstrated that females were higher on both traditional and cyber victimization than males, while males were higher on the perpetration of both traditional and cyberbullying. These findings are in agreement with the existing literature on traditional bullying (Whitney and Smith, 1993; Yang et al., 2006), that reported greater involvement of males in traditional bullying than females. Similarly, with respect to cyberbullying and victimization, our results corroborate the findings of previous studies on university students that reported greater cyber victimization among females (Faucher et al., 2014; Webber and Ovedovitz, 2018). Further, findings are also consistent with earlier studies carried out in Asian countries that demonstrated that male university students were more likely involved in cyberbullying perpetration than females (Dilmac, 2009; Akbulut and Eristi, 2011).
Third, it was found that females reported three times higher cyber victimization than traditional victimization. Additionally, males reported two times more perpetration of cyberbullying than the perpetration of traditional bullying. This finding is in contrast to existing research on school students (Kowalski and Limber, 2013; Olweus and Limber, 2018), which reported greater involvement of students in traditional bullying. This inconsistency may be explained in terms of differences between school and university students. Generally, university students have 24/7 access to ICT while school children usually have limited and monitored access to technology by parents or school staff. Therefore higher involvement of university students in cyberbullying might be due to greater access, less parental oversight, and more frequent use of technology.
Further, less involvement of university students in traditional bullying in comparison to cyberbullying may be due to the perception of greater accountability, and consideration of the norms of face-to-face interactions in the traditional context in comparison to cyber context in which norms are unclear. Another possible explanation might be the liberating environment (Erdur-Baker, 2010) and perception of the greater anonymity of the digital world (Betts, 2016) that can enhance the involvement of students in cyberbullying.
Fourth, findings confirm the association of spending more time on the Internet and particularly on SNS was associated with an increase in cyberbullying (Zhou et al., 2013; Navarro et al., 2017) and cyber victimization (Sengupta and Chaudhuri, 2011). Researchers such as Betts (2016) explains this association in terms of mere exposure effect; more exposure to technology and online spaces increase the probability of involvement in cyberbullying and victimization.
Fifth, findings demonstrated a significant negative association of GSE with the perpetration of cyberbullying which is consistent with the previous studies (Wong et al., 2014; Eden et al., 2016) which support this finding and indicates that GSE serves as a protective factor to reduce the involvement in cyberbullying perpetration.
Sixth, we tested the comparative role of both general and ICT self-efficacy in predicting the involvement of students as cyber-bullies, cyber-victims, and cyber bully victims in comparison to un-involved students after controlling the effect of covariates. Results showed that ICT self-efficacy significantly decreased the probability of being a cyber-victim and increased the probability of being a cyber-bully. No significant role of GSE was found in predicting the involvement of participants in any role of cyberbullying.
Finally, these findings suggest that ICT self-efficacy is a more important factor with respect to involvement in cyberbullying. Regarding cyber victimization, findings are in agreement with Mishna et al. (2012), who suggested that cyber victims were not aware of the skills related to online safety. Findings for the role of ICT in the involvement of cyberbullying perpetration seems to be consistent with other research which found the positive association between ICT self-efficacy and perpetration of cyberbullying (Xiao and Wong, 2013; Musharraf et al., 2018), and those who reported significant association of cyberbullying perpetration with computer skills (Walrave and Heirman, 2011), and online expertise (Livingstone et al., 2011). A possible explanation for these results may be that those who choose to cyberbully others need skills and ICT self-efficacy may failitate enacting their aggression. For example, perpetrators can conceal their identities, and remove digital footprints of their negative online behaviors by using such skills. Additionally, they may feel safe if they realize their target does not have such skills to identify them or retaliate.
Implications
Overall, these findings have important implications for developing and enhancing interventions with respect to the inclusion of ICT related skills. Prevention programs might incorporate hands-on practice as well as demonstrations to enhance ICT self-efficacy with a special focus on teaching online safety and security-related skills. Additionally, teaching of such skills should also be incorporated in awareness-raising campaigns and anti-cyberbullying intervention programs. It seems that those inclined to cyberbullying others acquire those skills, but those who may be targeted would benefit from specific instruction on those skills. Moreover, ICT self-efficacy may contribute to the power imbalance between cyberbullying and cyber-victim; ensuring all students have both skills and confidence in their ability to use those skills might diminish the power differential and reduce cyberbullying. It is also important to note that ICT self-efficacy has emerged as a valid predictor of involvement in cyberbullying perpetration. Therefore, ICT self-efficacy based interventions require extra care to teach students the effective use of these skills only for protection, and not for creating abuse.
In addition, the higher level of cyberbullying among university students in comparison to traditional bullying indicates the significance of anti-cyberbullying prevention and intervention efforts to combat cyberbullying in higher education institutions. The findings concerning gender differences contribute to the small existing literature with reference to cyberbullying among university students and indicate the influence of gender in the manifestation of bullying and cyberbullying, particularly in developing or South East Asian countries such as Pakistan.
Limitations and Recommendations
The study contributed to our understanding of the role of ICT self-efficacy in various participant roles in cyberbullying among university students; however, it has certain limitations. The cross-sectional nature of the study limits the external validity of the findings. It is recommended that future research use a longitudinal design to give a better estimation of the predictive role of ICT self-efficacy in cyberbullying and victimization. For instance, tracking changes over a course of longitudinal study may provide more reliable evidence about the role of ICT self-efficacy in cyberbullying. Additionally, examining alternate models involving potential mediators and moderators for the relationship between ICT self-efficacy and cyberbullying victimization would extend our understanding of cyberbullying phenomenon. It is also recommended that future research would investigate how different dimensions of ICT self-efficacy are related with the involvement in different roles in cyberbullying/victimization.
A potential limitation of the study is the reliance on self-report measures. Self-report measurement may prone to under or over reports of bullying/victimization. Though, we controlled the analysis for social desirability in responding, future research may consider multi-respondent design such as peer ratings to counter the potential bias.
With reference to gender differences in the prevalence of traditional and cyberbullying/victimization, it is important to note that females are significantly younger than males and younger age is correlated with cyber victimization. Therefore, these findings may confound with age variable. Though we controlled the confounding effect of age to estimate the unique role of gender in traditional and cyberbullying/victimization, it is further recommended to use comparative groups of male and female to increase the strength of the research design and precision in estimates. Further, there is discrepancy in the proportion of sample concerning gender (39.05% males versus 60.95% females) and this discrepancy may affect the findings. Therefore, future research may include sample with equal proportion of both males and females.
Data Availability
The datasets generated for this study are available on request to the corresponding author.
Ethics Statement
This study was carried out in accordance with the recommendations of “American Psychological Association Ethical Code of Conduct by Institutional Review Board of National Institute of Psychology” with written informed consent from all subjects. All subjects gave written informed consent in accordance with the Declaration of Helsinki. The protocol was approved by the IRB-NIP.
Author Contributions
SM contributed to conceptualization, data curation, visualization, methodology, formal analysis, project administration, and wrote the original draft. SB performed the formal analysis, supervision, validation, writing, review, before and editing. MA-ul-H contributed to supervision and validation. JM performed the formal analysis, writing, review, before and editing.
Conflict of Interest Statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
Akbulut, Y., and Eristi, B. (2011). Cyberbullying and victimisation among Turkish university students. Australas. J. Educ. Technol. 27, 1155–1170. doi: 10.14742/ajet.910
Antoniadou, N., and Kokkinos, C. M. (2015). Cyber and school bullying: same or different phenomena? Aggress. Violent Behav. 25, 363–372. doi: 10.1016/j.avb.2015.09.013
Arıcak, O. T. (2009). Psychiatric symptomatology as a predictor of cyberbullying among university students. Eurasian J. Educ. Res. 34, 167–184.
Atik, G., and Guneri, O. Y. (2012). California bullying victimization scale: validity and reliability evidence for the Turkish middle school children. Proc. Soc. Behav. Sci. 46, 1237–1241. doi: 10.1016/j.sbspro.2012.05.281
Ballard, M. E., and Welch, K. M. (2017). Virtual warfare: cyberbullying and cyber-victimization in MMOG play. Games Cult. 12, 466–491. doi: 10.1177/1555412015592473
Bandura, A. (1986). Social Foundations of Thought and Action: A Social Cognitive Theory. Englewood Cliffs: Prentice Hall.
Bandura, A. (1994). “Self-efficacy,” in Encyclopedia of Human Behavior, Vol. 4, ed. V. S. Ramachaudran (New York, NY: Academic Press), 71–81.
Beran, T., and Li, Q. (2005). Cyber-harassment: a study of a new method for an old behavior. J. Educ. Comput. Res. 32, 265–277. doi: 10.2190/8YQM-B04H-PG4D-BLLH
Bussey, K., Fitzpatrick, S., and Raman, A. (2015). The role of moral disengagement and self-efficacy in cyberbullying. J. Sch. Violence 14, 30–46. doi: 10.1080/15388220.2014.954045
Caravaca-Sanchez, F., Falcon Romero, M., Navarro-Zaragoza, J., Luna Ruiz-Cabello, A., Rodriges Frantzisko, O., and Luna Maldonado, A. (2016). Prevalence and patterns of traditional bullying victimization and cyber-teasing among college population in Spain (Report). BMC Public Health 16:176. doi: 10.1186/s12889-016-2857-8
Cassidy, W., Faucher, C., and Jackson, M. (2017). Adversity in university: cyberbullying and its impacts on students, faculty and administrators. Int. J. Environ. Res. Public Health 14:888. doi: 10.3390/ijerph14080888
Cassidy, W., Faucher, C., and Jackson, M. (2018). “Introduction: context, framework, and perspective,” in Cyberbullying at University in International Contexts, eds Cassidy, W., Faucher, C., and Jackson, M. (Abingdon: Routledge), 1–6.
Cunningham, C. E., Chen, Y., Vaillancourt, T., Rimas, H., Deal, K., Cunningham, L. J., et al. (2015). Modeling the anti-cyberbullying preferences of university students: adaptive choice-based conjoint analysis. Aggress. Behav. 41, 369–385. doi: 10.1002/ab.21560
Del Rey, R., Casas, J. A., Ortega-Ruiz, R., Schultze-Krumbholz, A., Scheithauer, H., Smith, P., et al. (2015). Structural validation and cross-cultural robustness of the european cyberbullying intervention project questionnaire. Comput. Hum. Behav. 50, 141–147. doi: 10.1016/j.chb.2015.03.065
Dilmac, B. (2009). Psychological needs as a predictor of cyber bullying: a preliminary report on college students. Educ. Sci. Theory Pract. 9, 1307–1325.
Doane, A. N., Kelley, M. L., Chiang, E. S., and Padilla, M. A. (2013). Development of the cyberbullying experiences survey. Emerg. Adulthood 1, 207–218. doi: 10.1177/2167696813479584
Doane, A. N., Pearson, M. R., and Kelley, M. L. (2014). Predictors of cyberbullying perpetration among college students: an application of the theory of reasoned action. Comput. Hum. Behav. 36, 154–162. doi: 10.1016/j.chb.2014.03.051
Eastin, M. S., and LaRose, R. (2000). Internet self-efficacy and the psychology of the digital divide. J. Comput. Mediat. Commun. 6:611. doi: 10.1111/j.1083-6101.2000.tb00110.x
Eden, S., Heiman, T., and Olenik-Shemesh, D. (2016). Bully versus victim on the internet: the correlation with emotional-social characteristics. Educ. Inform. Technol. 21, 699–713. doi: 10.1007/s10639-014-9348-2
Erath, S. A., Flanagan, K. S., Bierman, K. L., and Tu, K. M. (2010). Friendships moderate psychosocial maladjustment in socially anxious early adolescents. J. Appl. Dev. Psychol. 31, 15–26. doi: 10.1016/j.appdev.2009.05.005
Erdur-Baker, Ö (2010). Cyberbullying and its correlation to traditional bullying, gender and frequent and risky usage of internet-mediated communication tools. New Media Soc. 12, 109–125. doi: 10.1177/1461444809341260
Faucher, C., Jackson, M., and Cassidy, W. (2014). Cyberbullying among university students: gendered experiences, impacts, and perspectives. Educ. Res. Int. 2014:698545. doi: 10.1155/2014/698545
Felix, E. D., Sharkey, J. D., Green, J. G., Furlong, M. J., and Tanigawa, D. (2011). Getting precise and pragmatic about the assessment of bullying: the development of the California bullying victimization scale. Aggress. Behav. 37, 234–247. doi: 10.1002/ab.20389
Festl, R. (2016). Perpetrators on the internet: analyzing individual and structural explanation factors of cyberbullying in school context. Comput. Hum. Behav. 59, 237–248. doi: 10.1016/j.chb.2016.02.017
Francisco, S. M., Simão, A. M. V., Ferreira, P. C., and das Dores Martins, M. J. (2015). Cyberbullying: the hidden side of college students. Comput. Hum. Behav. 43, 167–182. doi: 10.1016/j.chb.2014.10.045
Gibb, Z. G., and Devereux, P. G. (2016). Missing link: exploring repetition and intentionality of distress in cyberbullying behaviors within a college population. Transl. Issues Psychol. Sci. 2, 313–322.
Hase, C. N., Goldberg, S. B., Smith, D., Stuck, A., and Campain, J. (2015). Impacts of traditional bullying and cyberbullying on the mental health of middle school and high school students. Psychol. Sch. 52, 607–617. doi: 10.1002/pits.21841
Heirman, W., and Walrave, M. (2008). Assessing concerns and issues about the mediation of technology in cyberbullying. Cyberpsychology 2, 1–12.
Kokkinos, C. M., Antoniadou, N., and Markos, A. (2014). Cyber-bullying: an investigation of the psychological profile of university student participants. J. Appl. Dev. Psychol. 35, 204–214.
Kokkinos, C. M., Baltzidis, E., and Xynogala, D. (2016). Prevalence and personality correlates of facebook bullying among university undergraduates. Comput. Hum. Behav. 55, 840–850. doi: 10.1016/j.chb.2015.10.017
Kokkinos, C. M., and Kipritsi, E. (2012). The relationship between bullying, victimization, trait emotional intelligence, self-efficacy and empathy among preadolescents. Soc. Psychol. Educ. 15, 41–58. doi: 10.1007/s11218-011-9168-9
Kowalski, R. M., Giumetti, G. W., Schroeder, A. N., and Lattanner, M. R. (2014). Bullying in the digital age: a critical review and meta-analysis of cyberbullying research among youth. Psychol. Bull. 140, 1073–1137. doi: 10.1037/a0035618
Kowalski, R. M., and Limber, S. P. (2013). Psychological, physical, and academic correlates of cyberbullying and traditional bullying. J. Adolesc. Health 53, S13–S20. doi: 10.1016/j.jadohealth.2012.09.018
Larrañaga, E., Yubero, S., and Ovejero, A. (2016). “Gender variables and cyberbullying in college students,” in Cyberbullying Across the Globe, eds R. Navarro, S. Yubero and E. Larrañaga (Cham: Springer).
Leung, L., and Lee, P. S. (2012). The influences of information literacy, internet addiction and parenting styles on internet risks. New Media Soc. 14, 117–136. doi: 10.1177/1461444811410406
Li, Q. (2007). New bottle but old wine: a research of cyberbullying in schools. Comput. Hum. Behav. 23, 1777–1791. doi: 10.1016/j.chb.2005.10.005
Livingstone, S., Haddon, L., Görzig, A., and Ólafsson, K. (2011). Risks and Safety on the Internet: the Perspective of European Children: Full Findings and Policy Implications from the EU Kids Online Survey of 9-16 Year Olds and their Parents in 25 Countries. London: EU Kids Online Network.
Livingstone, S., and Helsper, E. (2010). Balancing opportunities and risks in teenagers’ use of the internet: the role of online skills and internet self-efficacy. New Media Soc. 12, 309–329. doi: 10.1177/1461444809342697
MacDonald, C. D., and Roberts-Pittman, B. (2010). Cyberbullying among college students: prevalence and demographic differences. Proc. Soc. Behav. Sci. 9, 2003–2009. doi: 10.1016/j.sbspro.2010.12.436
Mishna, F., Cook, C., Gadalla, T., Daciuk, J., and Solomon, S. (2010). Cyber bullying behaviors among middle and high school students. Am. J. Orthopsychiatr. 80, 362–374. doi: 10.1111/j.1939-0025.2010.01040.x
Mishna, F., Khoury-Kassabri, M., Gadalla, T., and Daciuk, J. (2012). Risk factors for involvement in cyber bullying: victims, bullies and bully–victims. Child. Youth Serv. Rev. 34, 63–70. doi: 10.1016/j.childyouth.2011.08.032
Mishna, F., Regehr, C., Lacombe-Duncan, A., Daciuk, J., Fearing, G., and Van Wert, M. (2018). Social media, cyber-aggression and student mental health on a university campus. J. Ment. Heal. 27, 222–229. doi: 10.1080/09638237.2018.1437607
Mitchell, S. M., Seegan, P. L., Roush, J. F., Brown, S. L., Sustaíta, M. A., and Cukrowicz, K. C. (2018). Retrospective cyberbullying and suicide ideation: the mediating roles of depressive symptoms, perceived burdensomeness, and thwarted belongingness. J. Interpers. Violence 33, 2602–2620. doi: 10.1177/0886260516628291
Musharraf, S., and Anis-ul-Haque, M. (2018a). Cyberbullying in different participant roles: exploring differences in psychopathology and well-being in university students. Pak. J. Med. Res. 57, 33–39.
Musharraf, S., and Anis-ul-Haque, M. (2018b). Impact of cyber aggression and cyber victimization on mental health and well-being of Pakistani young adults: the moderating role of gender. J. Aggress. Maltreat. Trauma 27, 942–958. doi: 10.1080/10926771.2017.1422838
Musharraf, S., Bauman, S., Anis-ul-Haque, M., and Malik, J. (2018). Development and validation of ICT self-efficacy scale: exploring the relationship with cyberbullying and victimization. Int. J. Environ. Res. Public Health 15:2867. doi: 10.3390/ijerph15122867
Musharraf, S., and Lewis, C. A. (2016). Cyberbullying—bullying in the virtual world: a cautionary note for medical educators [Short Communication]. J. Pak. Psychiatr. Soc. 13, 35–36.
Musharraf, S., and Lewis, C. A. (2018). Bullying, cyberbullying, and suicide: a crisis on campus? [short communication]. J. Pak. Psychiatr. Soc. 15, 39–41.
Nagelkerke, N. J. (1991). A note on a general definition of the coefficient of determination. Biometrika 78, 691–692.
Natvig, G. K., Albrektsen, G., and Qvarnstrom, U. (2001). School-related stress experience as a risk factor for bullying behavior. J. Youth Adolesc. 30, 561–575. doi: 10.1023/A:101044860
Navarro, J. N., Clevenger, S., Beasley, M. E., and Jackson, L. K. (2017). One step forward, two steps back: cyberbullying within social networking sites. Secur. J. 30, 844–858. doi: 10.1057/sj.2015.19
Nixon, C. L. (2014). Current perspectives: the impact of cyberbullying on adolescent health. Adolesc. Health Med. Ther. 5, 143–158. doi: 10.2147/AHMT.S36456
Nocentini, A., Calmaestra, J., Schultze-Krumbholz, A., Scheithauer, H., Ortega, R., and Menesini, E. (2010). Cyberbullying: labels, behaviours and definition in three European countries. Aust. J. Guid. Couns. 20, 129–142. doi: 10.1375/ajgc.20.2.129
Olenik-Shemesh, D., and Heiman, T. (2014). Exploring cyberbullying among primary children in relation to social support, loneliness, self-efficacy, and well-being. Child Welf. 93, 27–46.
Olweus, D. (2012a). Comments on cyberbullying article: a rejoinder. Eur. J. Dev. Psychol. 9, 559–568. doi: 10.1080/17405629.2012.705086
Olweus, D. (2012b). Cyberbullying: an overrated phenomenon? Eur. J. Dev. Psychol. 9, 520–538. doi: 10.1080/17405629.2012.682358
Olweus, D. (2013). School bullying: development and some important challenges. Annu. Rev. Clin. Psychol. 9, 751–780. doi: 10.1146/annurev-clinpsy-050212-185516
Olweus, D., and Limber, S. P. (2018). Some problems with cyberbullying research. Curr. Opin. Psychol. 19, 139–143. doi: 10.1016/j.copsyc.2017.04.012
Patchin, J. W., and Hinduja, S. (2011). Traditional and nontraditional bullying among youth: a test of general strain theory. Youth Soc. 43, 727–751. doi: 10.1177/0044118X10366951
Paullet, K., and Pinchot, J. (2014). Behind the screen where today’s bully plays: perceptions of college students on cyberbullying. J. Inform. Syst. Educ. 25, 63–69.
Salmivalli, C., Lagerspetz, K., Björkqvist, K., Österman, K., and Kaukiainen, A. (1996). Bullying as a group process: participant roles and their relations to social status within the group. Aggress. Behav. 22, 1–15. doi: 10.1002/(SICI)1098-2337
Sapouna, M., and Wolke, D. (2013). Resilience to bullying victimization: the role of individual, family and peer characteristics. Child Abuse Negl. 37, 997–1006. doi: 10.1016/j.chiabu.2013.05.009
Savage, M. W., and Tokunaga, R. S. (2017). Moving toward a theory: testing an integrated model of cyberbullying perpetration, aggression, social skills, and Internet self-efficacy. Comput. Hum. Behav. 71, 353–361. doi: 10.1016/j.chb.2017.02.016
Schenk, A. M., and Fremouw, W. J. (2012). Prevalence, psychological impact, and coping of cyberbully victims among college students. J. Sch. Violence. 11, 21–37. doi: 10.1080/15388220.2011.630310
Schenk, A. M., Fremouw, W. J., and Keelan, C. M. (2013). Characteristics of college cyberbullies. Comput. Hum. Behav. 29, 2320–2327. doi: 10.1016/j.chb.2013.05.013
Schwarzer, R., and Jerusalem, M. (1995). “Generalized self-efficacy scale,” in Measures In Health Psychology: A User’s Portfolio. Causal and Control Beliefs, eds J. Weinman, S. Wright and M. Johnston (Windsor: NFER-NELSON), 35–37.
Sengupta, A., and Chaudhuri, A. (2011). Are social networking sites a source of online harassment for teens? Evidence from survey data. Child. Youth Serv. Rev. 33, 284–290. doi: 10.1016/j.childyouth.2010.09.011
Ševčíková, A., and Šmahel, D. (2009). Online harassment and cyberbullying in the Czech Republic: comparison across age groups. J. Psychol. 217, 227–229. doi: 10.1027/0044-3409.217.4.227
Smith, P. K., Madsen, K. C., and Moody, J. C. (1999). What causes the age decline in reports of being bullied at school? Towards a developmental analysis of risks of being bullied. Educ. Res. 41, 267–285. doi: 10.1080/0013188990410303
Sticca, F., Ruggieri, S., Alsaker, F., and Perren, S. (2013). Longitudinal risk factors for cyberbullying in adolescence. J. Commun. Appl. Soc. Psychol. 23, 52–67. doi: 10.1002/casp.2136
Stöber, J. (2001). The social desirability scale-17 (SDS-17): convergent validity, discriminant validity, and relationship with age. Eur. J. Psychol. Assess. 17, 222–232. doi: 10.1027//1015-5759.17.3.222
Tokunaga, R. S. (2010). Following you home from school: a critical review and synthesis of research on cyberbullying victimization. Comput. Hum. Behav. 26, 277–287. doi: 10.1016/j.chb.2009.11.014
Völlink, T., Dehue, F., McGuckin, C., and Jacobs, C. (2016). An Introduction in Cyberbullying Research. Cyberbullying: From Theory to Intervention. New York, NY: Routledge.
Walrave, M., and Heirman, W. (2011). Cyberbullying: predicting victimisation and perpetration. Child. Soc. 25, 59–72. doi: 10.1111/j.1099-0860.2009.00260.x
Webber, M. A., and Ovedovitz, A. C. (2018). Cyberbullying among college students: a look at its prevalence at a US Catholic University. Int. J. Educ. Method 4, 95–107.
Wensley, K., and Campbell, M. (2012). Heterosexual and nonheterosexual young university students’ involvement in traditional and cyber forms of bullying. Cyberpsychol. Behav. Soc. Netw. 15, 649–654. doi: 10.1089/cyber.2012.0132
Whitney, I., and Smith, P. K. (1993). A survey of the nature and extent of bullying in junior/middle and secondary schools. Educ. Res. 35, 3–25. doi: 10.1080/0013188930350101
Willard, N. (2007). Cyberbullying and Cyberthreats: Responding to the Challenge of Online Social Aggression, Threats, and Distress. Ann Arbor, MI: Malloy Inc.
Wolke, D., Lereya, T., and Tippett, N. (2016). “Individual and social determinants of bullying and cyberbullying,” in Cyberbullying: From Theory to Intervention, eds T. Völlink, F. Dehue, and C. Mc Guckin(New York, NY: Routledge).
Wong, D. S., Chan, H. C. O., and Cheng, C. H. (2014). Cyberbullying perpetration and victimization among adolescents in Hong Kong. Child. Youth Serv. Rev. 36, 133–140. doi: 10.1016/j.childyouth.2013.11.006
Wong, R. Y. M., Cheung, C. M. K., and Xiao, B. (2018). Does gender matter in cyberbullying perpetration? An empirical investigation. Comput. Hum. Behav. 79, 247–257. doi: 10.1016/j.chb.2017.10.022
Wozencroft, K., Campbell, M., Orel, A., Kimpton, M., and Leong, E. (2015). University students’ intentions to report cyberbullying. Aust. J. Educ. Dev. Psychol. 15, 1–12.
Xiao, B., and Wong, Y. (2013). Cyber-bullying among University students: an empirical investigation from the social cognitive perspective. Int. J. Bus. Inf. 8, 34–69. doi: 10.6702/ijbi.2013.8.1.2
Yang, S.-J., Kim, J.-M., Kim, S.-W., Shin, I.-S., and Yoon, J.-S. (2006). Bullying and victimization behaviors in boys and girls at South Korean primary schools. J. Am. Acad. Child Adolesc. 45, 69–77. doi: 10.1097/01.chi.0000186401.05465.2c
Zalaquett, C. P., and Chatters, S. J. (2014). Cyberbullying in college: frequency, characteristics, and practical implications. Sage Open. 4, 1–8. doi: 10.1177/2158244014526721
Keywords: traditional bullying, traditional victimization, cyberbullying, cyber victimization, ICT self-efficacy, general self-efficacy, Pakistan, university students
Citation: Musharraf S, Bauman S, Anis-ul-Haque M and Malik JA (2019) General and ICT Self-Efficacy in Different Participants Roles in Cyberbullying/Victimization Among Pakistani University Students. Front. Psychol. 10:1098. doi: 10.3389/fpsyg.2019.01098
Received: 18 February 2019; Accepted: 26 April 2019;
Published: 14 May 2019.
Edited by:
Claudio Longobardi, University of Turin, ItalyReviewed by:
Anja Schultze-Krumbholz, Technische Universität Berlin, GermanyNafsika Antoniadou, Hellenic Open University, Greece
Copyright © 2019 Musharraf, Bauman, Anis-ul-Haque and Malik. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Sadia Musharraf, c2FkaWFfbXVzaGFycmFmQGhvdG1haWwuY29t
 Sadia Musharraf
Sadia Musharraf Sheri Bauman
Sheri Bauman Muhammad Anis-ul-Haque
Muhammad Anis-ul-Haque Jamil Ahmad Malik
Jamil Ahmad Malik