- 1University of Lorraine, PErSEUs EA 7312, Metz, France
- 2Aix-Marseille Univ., LPS EA 849, Aix-en-Provence, France
The main objective is a double one. First and foremost, it is a question of showing that foot-in-the-door as a proven behavioral influence technique in offline interactions maintains its efficiency in online interactions. It is then a question of exploring the impact of the anthropomorphism vs. the non-anthropomorphism of the requester avatar on the efficiency of this technique. Foot-in-the-door is based on a simple principle: you start by asking for a little in a first step to increase the probability of obtaining a lot in a second step. The research was conducted in the Second Life virtual world. In a control condition (n = 200), a requester avatar directly proposed the target request. In a foot-in-the-door condition (n = 200), the requester avatar started by presenting a preparatory request before proposing the target request. According to the conditions, the requester avatar was human-like (female or male), or non-human-like (flower, balloon, cube). As expected, our results show that overall the foot-in-the door-technique remains efficient in the virtual world; they also show that this efficiency depends on the human-like form of the requester avatar. This last result is interpreted as a reference to the theory of social presence. Non-human-like avatars could generate a weak social presence, to the point where the mechanisms of self-perception and commitment underlying the foot-in-the-door effect may not be automatically initiated. Player avatars would in this way be freed from the rules of social interaction occurring in offline interactions.
Introduction
Two decades ago, McKenna and Bargh (2000) pointed out what they had called four novel and important aspects of online interactions. Firstly, the virtual world allows for greater anonymity (Segovia and Bailenson, 2012). We can meet new people with unusual salient features; we can ourselves show features which are very different from those which characterize us in offline life. We can also choose to only divulge part of our features (age, sex, hair color, or corpulence) and even change them at a whim. In other word, we can manage and control the impression we give of ourselves, via the avatars we choose (Lin and Wang, 2014). Moreover, the possibility of being totally anonymous during our experiences in cyberspace was linked to a decrease in self-focus (Matheson and Zanna, 1989). This might explain why individuals are more inclined to commit to non-normative behaviors in computer-mediated situations than in face-to-face interactions (Suler, 2004). Secondly, the physical appearance of the player only has a small amount of importance, because they choose an avatar to represent them in the online world; whereas in the offline world, our appearance, the care we take with our clothes, fashion items, are all important elements in communication and our offline interactions. Thirdly, distance becomes blurred: being near or far loses its meaning. In other words, distance is no longer a barrier to interacting with others. Fourth, individuals have more control on the time of the interactions and their place. This gives the online user empowerment and autonomy, but can also lead to the opposite effect by blurring the border between private and public life, due to the fact that the internet is based on ubiquity. A last point which makes online interactions different from offline interactions is the absence of available social cues (Kiesler et al., 1984) such as the eyes, the tone of voice or more generally speaking, the absence of non-verbal behavior. The advent of the web 3.0 has enabled the development of some of these available social cues, and virtual worlds make it possible to have experiences, including social ones (Messinger et al., 2009; Muscanell and Guadagno, 2012).
Even if virtual worlds actually allow players to free themselves from the rules and constraints of the offline world, are the fundamental mechanisms of social interactions comparable to those of face to face social interactions? The object of this research is to focus on one of the basic social influence mechanisms, i.e., compliance and behavior change.
Foot-in-the-Door in Offline Environments
“Give ‘em an inch, they take a mile,” this old saying whereby giving a little can lead to giving a lot was experimentally demonstrated by Freedman and Fraser (1966). This technique of compliance without pressure is known as foot-in-the-door (FITD). Performing or agreeing to perform a preliminary low cost behavior (e.g., preparatory request) increases the probability of performing a second more costly one (e.g., target request). Therefore, answering a short questionnaire on consumer habits (preparatory behavior) increases the probability that you will accept to have a team of surveyors in your home for 2 h (Freedman and Fraser, 1966), and even giving trivial information increases the probability of helping others (Saint-Bauzel and Fointiat, 2012). For the last five decades, this social influence strategy has been well-documented and empirically validated (Dillard et al., 1984; Burger, 1999; Pascual and Guéguen, 2005). It still spikes interest among researchers (Dolinski, 2009, 2012; Fointiat and Saint-Bauzel, 2010; Saint-Bauzel and Fointiat, 2012; Pascual et al., 2013; Gamian-Wilk et al., 2018). The two meta-analyses conducted on FITD show a moderate effect (Beaman et al., 1983; Dillard et al., 1984).
Globally the research carried out on FITD focuses only slightly on contextual cues or the features of the requester on the efficiency of the technique. At best, researchers control a possible effect on the gender of requester and/or requested. When this gender-effect is tested, it is shown to be insignificant (e.g., Gamian-Wilk et al., 2018).
This social influence procedure has been well-documented and empirically validated for the past 50 years (Dillard et al., 1984; Burger, 1999; Pascual and Guéguen, 2005). For some authors (e.g., Gamian-Wilk et al., 2018), the FITD effect is interpreted in terms of self-perception (Bem, 1972); for others (Joule, 1987; Cialdini, 2008), this effect is based on commitment processes (Kiesler, 1971).
According to the theory of self-perception (Bem, 1972), individuals do not have direct access to their inner states (attitude, belief, emotions, etc.). He might ask himself: “what is my attitude to have behaved in such a way in this situation?” He would use this self-attributive inference to adopt the behavior which suits this reference. In other words, the individual who had just accepted a low-cost behavior (e.g., answering a little questionnaire) would infer that they are the type of person who agrees to help. Consequently, they would be inclined to agree to help again when they receive a high-cost request (e.g., having a team of several people in their home). The commitment theory (Kiesler, 1971), proposes an alternative interpretation of the FITD technique. Commitment was initially defined as “a link between individuals and their behavioral acts” (Kiesler and Sakumura, 1966, p. 349) and was then considered as “the conditions under which the performance of an act cannot be attributed to any other than the person who has performed it” (Joule and Beauvois, 1998, p. 60). The performance of a behavior under certain conditions (e.g., absence of external pressure) triggers a freezing effect, and leads the individual to continue in the same course of action, showing a need to maintain a behavioral consistency. Thus, the production of a low-cost behavior (preparatory behavior) in a context of freedom (i.e., with no constraints or threats) would serve as a guide when the opportunity arises to perform other behaviors which are part of the same course of action, even if they are actually more problematic (target behavior).
Foot-in-the-Door in Virtual Environments
For the last two decades, social psychologists have investigated the mechanism of FITD in multiple computer-mediated contexts: email (Guéguen, 2002), website (Guéguen and Jacob, 2001) or chat (Markey et al., 2003), and virtual world (Eastwick and Gardner, 2009). In the virtual environment, the principle of FITD can be presented as follows: “first, an influence agent asks for something small, usually a minor commitment. The influence agent then builds upon that small commitment to gain compliance with a second (usually related) larger request” (Guadagno and Cialdini, 2005). From our knowledge, only one research has investigated the efficiency of the FITD in virtual environment (Eastwick and Gardner, 2009). This research was carried out in the There.com virtual world. Among other things, the authors focused on the impact of the requester's appearance on the efficiency of FITD. Therefore, in the FITD condition, a requester avatar (black vs. white skin tone) approached a player avatar and under the pretext of taking part in a scavenger hunt, offering “to take a screen shot of you” (preparatory request). Immediately after having taken the screenshot, the requester avatar made a much higher-cost request (target request): to teleport to Rio (one of the remote worlds in the game) to take a screenshot. Eastwick and Gardner (2009) observed that the FITD effect was effective whatever the appearance of the avatar experimenter (black or white skin tone): there were all the more avatar participants ready to accompany the requester avatar to Rio because they had previously accepted the first screenshot, whatever the skin tone of the requester avatar.
Social Presence
In addition to this, a field of research has developed on the effects of the appearance of the avatar on the social behaviors of the players in MMOG. This theory of social presence (Short et al., 1976; Rice and Case, 1983) is based on the idea that some media (e.g., videoconference) more than others (e.g., email) are capable of conveying non-verbal information and therefore transmitting social cues about the person. The more we have or think we have social information about others, the more we feel the social presence of this other, including in a virtual world (Bente et al., 2008). By social presence we understand the degree to which a user identifies another user as a person who is present in real time in the same digital area. MMOG and more particularly virtual worlds would appear to be among the media that are based on a strong social presence, via avatars (Nowak and Biocca, 2003).
The choice of our avatar (its aspect, its gender) and more generally its appearance, clothes, and accessories are perceived as reflecting the personality of the user (Fong and Mar, 2014; Nowak et al., 2015). We may therefore think that the appearance of the avatar can trigger behavioral heuristics, in the same way as two people who meet for the first time in the street (Huang and Chen, 2006; Bélisle and Bodur, 2010). Conversely, interacting with a non-anthropomorphic avatar does not appear to trigger these heuristics (Nowak et al., 2009), and non-anthropomorphic avatars are often seen as having a lower social potential than anthropomorphic avatars (Nowak and Rauh, 2006, 2008).
In the follow-up of Eastwick and Gardner's work, we expect a FITD effect in a virtual world: we expect a stronger compliance when the participant avatars have first accepted a preparatory request than when the target request was presented directly (Hypothesis 1).
If we do not take the particularities of virtual worlds into consideration, then we expect, based on the self-perception theory (Bem, 1972) and on commitment psychology (Kiesler, 1971), a FITD effect whatever the avatar's appearance (Hypothesis 2a). On the other hand, if we take these particularities into consideration, we will then expect a more marked FITD effect when the requester avatar is anthropomorphic than when it is not (Hypothesis 2b).
Method
This study was conducted in accordance with the ethical principles outlined in European Code of conduct for Research Integrity Revised version and with the ethical principles outlined in the French Code of Deontology of psychologists (1996, revised in 2012, articles 44–52).
Pretest
57 students (46 women, Mage = 21.48, SD = 6.11) assessed the perceived gender and degree of human likeness of five avatars: three non-anthropomorphic avatars (Flower, Balloon, Cube) and two anthropomorphic avatars (female human, male human) (see Figure 1).
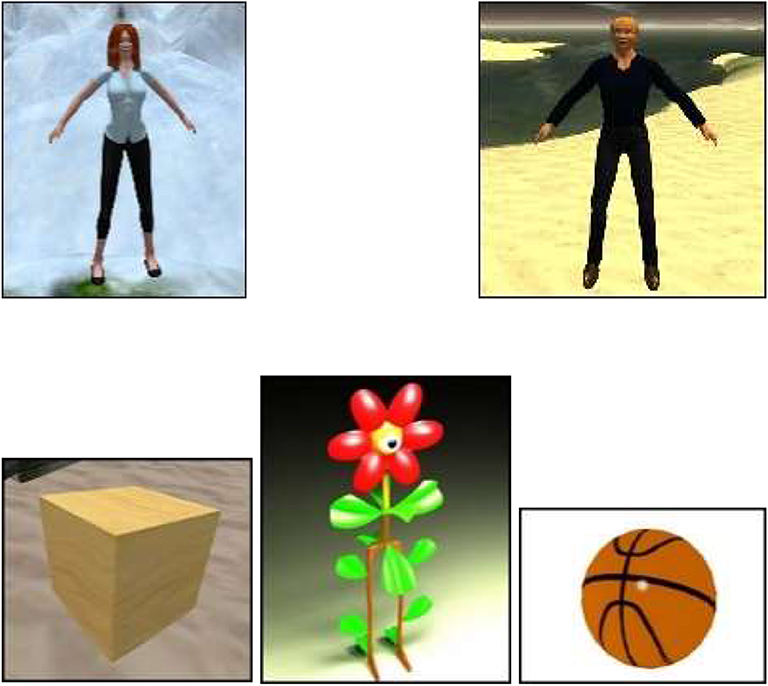
Figure 1. Second Life avatars used in the study. Line 1, anthropomorphic avatars (female and male); Line 2, non-anthropomorphic avatars (cube, flower, and balloon).
Concerning the perceived gender of the avatars, the participants responded to a single item (“what is the gender of this avatar”) by choosing between female, male, or undetermined. Not surprisingly, the female and male anthropomorphic avatars are perceived as such, respectively, 95 and 93%. As regards the non-anthropomorphic avatars, the gender attribution is more ambiguous: 54% of the students see the flower as female (46% perceive it as undetermined and 0% perceive it as male), 51% of the respondents see the ball as male (40% see it as undetermined and 4% see it as female), and 83% see the cube as being of undifferentiated gender (0% see it as female and 17% see it as male). Moreover, the degree of anthropomorphism of the five avatars, we measured by a single 7-point scale item (i.e., “this avatar is human-like” from 1: not at all to 7: very much).
Participants
Four hundred eighty-seven player avatars were contacted in the Second Life virtual world, while they were alone. Moreover, of the 487 players avatars, 240 looked masculine and 247 looked feminine. The percentage of feminine avatars varied from 48.5 to 53.5% under the five experimental conditions.
Based on the findings of Beaman et al. (1983) that found a medium size effect for FITD procedure (d = 0.22), we ran a power analysis through G*Power (Faul et al., 2007). Statistical power was set at 0.95 and alpha error probability was set at 0.05 to detect a medium-sized effect (w = 0.3). The analysis suggested a required total sample size of 271 participants, whereas our sample size was higher.
Variables and Experimental Design
Our research illustrates a 2 (Influence technique: Control vs. FITD) ×2 (Avatar Appearance: Non-human like vs. Human-like) between subjects, with compliance rate as the main measure.
Procedure
The procedure used in this study was similar to those used by Eastwick and Gardner (2009). The avatar experimenter approached Second Life avatars that were standing alone in one of the main gathering areas. In all conditions, the avatar experimenter began the interaction by saying (via the chat box): “Hi, I'm doing a photo scavenger hunt.” In a control condition (N = 200), the avatar experimenter made the target request: “Would you teleport to Brazil Rio with me and let me take a screenshot of you?” In the FITD conditions (N = 200), the avatar experimenter presented first a small request: “Can I take a screenshot of you?” and the target request only after this. If the participants agreed to the target request, the avatar experimenter teleported to Rio Brazil, took a screenshot of the participant, thanked them and left. The avatar experimenter took on one of the five following appearances: flower, balloon, cube, male human vs. female human.
Results
First of all, as for Eastwick and Gardner (2009), 87 participants out of 287 (i.e., 30.3%) refused the preparatory request. As in Eastwick and Gardner these participants were not included in the total N reported above.
We subsequently tested a possible gender effect of participant avatars on the compliance rate. As in much of the previous research (Eastwick and Gardner, 2009; Guéguen, 2011), we did not observe any gender effect: of the 200 masculine avatars, 80 complied, and of the 200 feminine avatars, 93 complied, X = 1.72, ns. The number of avatar-participants (%) who complied with the target request is presented in Table 1.
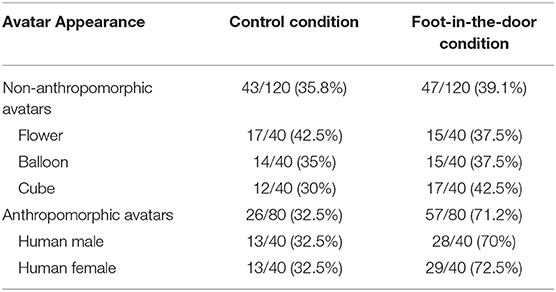
Table 1. Compliance rate (%) according to the appearance of the experimenter avatar and the influence technique.
Main Results
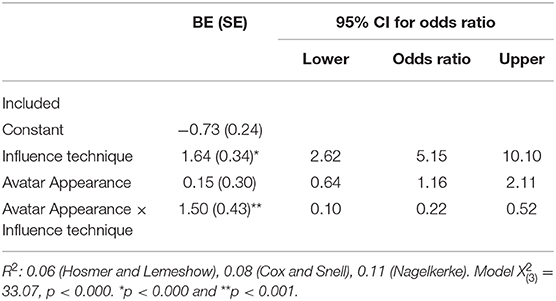
A series of binary logistic regression (see Table 2) was conducted (compliance -coded 0: refuse−1: agree- as a DV). All predictors were qualitative (nominal). As recommended by Jaccard (2001) and Gamian-Wilk et al. (2018) and for “convenient interpretation of simple effects, we applied saturated models (all possible effects of predictors and their interactions included in the model)”. We tested a model with FITD, avatar appearance on compliance with interactions. The tested model explained about 11 % of the variability in the compliance rate (Nagelkerke's R2 = 0.11).
First, in line with hypothesis 1, we observed the expected FITD effect: accepting a first low-cost behavior increases the probability of accepting a second higher-cost one (Wald X = 22.75, p <0.000, OR = 5.15, 95% CI [2.62; 10.10]). Using a preparatory request produced five times more chances of complying the target request. Secondly, no main effect of the appearance of the avatar was observed, Wald X = 0.24, ns. Third, we observed an interaction effect between the appearance of the avatar and FITD, Wald X = 11.83, p <0.001, OR = 0.22, 95% CI [0.01; 0.52].
Simple Effects of the Avatar Appearance
We explored this interaction by focusing on the simple effect of the avatar appearance. In the control condition, we did not observe any effect of the avatar appearance, X = 1.63, ns. On the other hand, we observed an effect of the appearance in the FITD condition, X = 20.11, p <0.001, Cramer's V = 0.16.
Simple Effects of the Influence Technique
Finally, we explored this interaction, focusing on the simple FITD effect for each form of avatar. Thus, when the avatar is a flower, a ball or a cube, we did not observe any FITD effect, respectively, 17/40 vs. 15/40, X = 0.21, ns; 14/40 vs. 15/40, X = 0.05, ns; 12/40 vs. 17/40, X = 1.35, ns. On the other hand, when the avatar is human-like, we observed the expected FITD effect, whether the avatar was male or female, respectively 13/40 vs. 28/40, X = 11.26, p <0.001, φ = 0.37 and 13/40 vs. 29/40, X = 12.83, p <0.001, φ = 0.40.
Discussion
First and foremost, and following on from the work carried out by Eastwick and Gardner (2009), we replicate here the FITD effect in a virtual world, in this case Second Life. In Eastwick and Gardner's research (Eastwick and Gardner's, 2009), the appearance of the avatar or more precisely the skin tone of the avatar-requester did not impact the FITD technique. But whatever the skin tone of the requester, the avatar remained anthropomorphic. However, in our research, we vary the anthropomorphism of the requester avatar. The results are clear: the FITD effect is only observed when the requester avatar is human-like, whether it is a male or female avatar, which matches previous work. On the other hand, when the requester avatar takes on the appearance of an object (flower, balloon or cube), we no longer observe an effect of the social influence procedure.
The other point to highlight is that in the control condition, we do not observe any effect of the avatar's appearance. By contrast, when the high-cost request is directly presented, the probability that it will be accepted does not depend on the appearance of the requester. Finally, the requester's taking on the appearance of an object or a human-like one does not modify their direct influence potential. But, when the experimenter avatar starts by obtaining a small behavior and consequently, a short interaction with the player avatar, the fact that their avatar is anthropomorphic doubles the probability that they will obtain from others what they want to obtain.
The self-perception (Bem, 1972) and commitment (Joule, 1987; Cialdini, 2008) theories only enable part of the results to be considered. These are two of the most cited FITD effect theories which make it possible to predict that after having accepted a first low-cost behavior, individuals are inclined to accept a second behavior which is more problematic for them, whatever the appearance of the requester. This is what we actually observe, but only when the requester avatars are anthropomorphic. This FITD effect is no longer observed when the requester avatars are non-anthropomorphic. Neither the theory of self-perception nor the commitment theory enables us to account for this failure.
These results lead us to challenge the limits of the parallels that researchers draw between the different offline and online interactions (Parmentier and Rolland, 2009). We could consider that in virtual worlds where the interactions are carried out via avatars, the players are particularly sensitive to the social cues conveyed by these avatars. The degree of anthropomorphism of an avatar is defined as “the visual closeness an avatar might have with characteristics typically associated with humans, or in other words, the degree to which an avatar looks like a human being” (McGloin et al., 2014, p. 22). We know moreover that it is easier to form impressions when the avatar is human-like. In this case, social responses are automatically activated (Reeves and Nass, 1996; Nass and Moon, 2000). They result in suitable conducts toward a human being (Nowak, 2013) in comparison with those shown toward a non-human-like avatar (Nowak et al., 2009). When the avatar is non-human-like, these processes are not triggered or little and consequently the social behaviors are often modified: we feel free to refuse to continue an interaction. Non-anthropomorphic avatars would appear to consequently generate a weak social potential and their social presence would be perceived less. The identification of the avatar as human-like or non-human-like is automatic and guides our social behaviors. In our study, we used three non-anthropomorphic avatars. This could represent a limit to the generatability of our results. However, researches on the effect of the appearance of avatars do not take into account the whole variety of the features of the avatars. For example, Chen et al. (2019) addressed the issue of the customization (vs. Non-customization) of the avatars without studying the impact of the 256 combinations at least. Moreover, our results are consistent with prior studies: the higher the humanness-like (here operationalized via appearance), the higher the influence is. One can consider alternate way to arise humanness such as the naming of the avatars (Guitton, 2010). Further research could investigate this perspective.
To our knowledge, these results are among the first to show that the rules of social influence as can be observed in offline life still apply in online life (Guadagno and Cialdini, 2005), on condition that the requester avatars allow the player avatars to perceive a social presence. It is therefore interesting to continue to question the specific situations and features of the avatar which trigger certain socio-cognitive processes (e.g., social identity, self-perception, threat of stereotype, etc.) and to provide new perspectives in terms of the induction of behavioral and/or attitudinal changes through on line interactions. In addition to this, future research should investigate the permeability of non-anthropomorphic player avatars to behavioral influence attempts such as FITD and But you are free (Guéguen and Pascual, 2000). This technique consists of matching the proposal of a request with a sentence that emphasizes the target's freedom to comply or not. Considering the specifics of virtual worlds, we could here again expect an impact of the anthropomorphic vs. non-anthropomorphic features of avatars.
Data Availability Statement
The datasets generated for this study are available on request to the corresponding author. The data were thus aggregated. The data that support the findings of this study are openly available in osf.io at https://osf.io/s3znf/?view_only=a90c03d5a9724baebe7a76a9bf16558b.
Ethics Statement
Ethical review and approval was not required for the study on human participants in accordance with the local legislation and institutional requirements. Written informed consent for participation was not required for this study in accordance with the national legislation and the institutional requirements.
Author Contributions
LB and VF contributed conception and design of the study, performed the statistical analyses, and wrote sections of the manuscript. LB collected data, organized the database, and wrote the first draft of the manuscript. All authors contributed to manuscript revision, read, and approved the submitted version.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
Beaman, A. L., Cole, C. M., Preston, M., Klentz, B., and Steblay, N. M. (1983). Fifteen years of foot-in-the-door research: a meta analysis. Pers. Soc. Psychol. Bull. 9, 181–196. doi: 10.1177/0146167283092002
Bélisle, J.-F., and Bodur, H. O. (2010). Avatars as information: perception of consumers based on their avatars in virtual worlds. Psychol. Market. 27, 741–765. doi: 10.1002/mar.20354
Bem, D. (1972). Self-perception theory. Adv. Exp. Soc. Psychol. 6, 1–62. doi: 10.1016/S0065-2601(08)60024-6
Bente, G., Rüggenberg, S., Krämer, N. C., and Eschenburg, F. (2008). Avatar-mediated networking: increasing social presence and interpersonal trust in net-based collaborations. Human Commun. Res. 34, 287–318. doi: 10.1111/j.1468-2958.2008.00322.x
Burger, J. M. (1999). The foot-in-the-door compliance procedure: a multiple-process analysis and review. Pers. Soc. Psychol. Rev. 3, 303–325. doi: 10.1207/s15327957pspr0304_2
Chen, Z. H., Lu, H. D., and Lu, C. H. (2019). The effects of human factors on the use of avatars in game-based learning: customization vs. non-customization. Int. J. Human Comput. Interact. 35, 384–394. doi: 10.1080/10447318.2018.1543090
Dillard, J. P., Hunter, J. E., and Burgoon, M. (1984). Sequential request persuasive strategies: meta-analysis of foot-in-the-door and door-in-the-face. Hum. Commun. Res. 10, 461–488. doi: 10.1111/j.1468-2958.1984.tb00028.x
Dolinski, D. (2009). People in a freezer: self-perception as an explanatory mechanism for the effectiveness of the foot-in-the-door technique. Polish Psychol. Bull. 40, 1–4. doi: 10.2478/s10059-009-0028-9
Dolinski, D. (2012). The nature of the first small request as a decisive factor in the effectiveness of the foot-in-the-door technique. Appl. Psychol. 61, 437–453. doi: 10.1111/j.1464-0597.2011.00477.x
Eastwick, P. W., and Gardner, W. L. (2009). Is it a game? Evidence for social influence in the virtual world. Soc. Influence 4, 18–32.doi: 10.1080/15534510802254087
Faul, F., Erdfelder, E., Lang, A. G., and Buchner, A. (2007). G* Power 3: a flexible statistical power analysis program for the social, behavioral, and biomedical sciences. Behav. Res. Methods 39, 175–191. doi: 10.3758/bf03193146
Fointiat, V., and Saint-Bauzel, R. (2010). Appearance (ethnic origin) of requester affects the foot-in-the-door technique. Percept. Motor Skills 111, 694–700. doi: 10.2466/07.17.PMS.111.6.694-700
Fong, K., and Mar, R. A. (2014). What does my avatar say about me? Inferring personality from avatars. Pers. Soc. Psychol. Bull. 41, 237–249. doi: 10.1177/0146167214562761
Freedman, J. L., and Fraser, S. C. (1966). Compliance without pressure: the foot-in-the-door technique. J. Pers. Soc. Psychol. 4, 195–202. doi: 10.1037/h0023552
Gamian-Wilk, M., Dolinski, D., and Danieluk, B. (2018). Mindfulness and compliance: the way we make requests influences compliance with the foot-in-the-door strategy. Psychol. Rep. 12, 147–166. doi: 10.1177/0033294117745885
Guadagno, R. E., and Cialdini, R. B. (2005). “Online persuasion and compliance: social influence on the Internet and beyond,” in The Social Net: The Social Psychology of the Internet, ed Y. Amichai-Hamburger (New York, NY: Oxford University Press). 91–113.
Guéguen, N. (2002). Foot-in-the-door technique and computer-mediated communication. Comput. Human Behav. 18, 11–15. doi: 10.1016/S0747-5632(01)00033-4
Guéguen, N. (2011). Influence of a positive versus negative social labeling on helping behavior: testing the requests connectivity hypothesis. Eur. J. Soc. Sci. 19, 175–179.
Guéguen, N., and Jacob, C. (2001). Fund-raising on the web: the effect of an electronic foot-in-the-door on donation. Cyber Psychol. Behav. 4, 705–709. doi: 10.1089/109493101753376650
Guéguen, N., and Pascual, A. (2000). Evocation of freedom and compliance: the ‘but you are free of…'technique. Curr. Res. Soc. Psychol. 5, 264–270.
Guitton, M. J. (2010). Cross-modal compensation between name and visual aspect in socially active avatars. Comput. Human Behav. 26, 1772–1776. doi: 10.1016/j.chb.2010.07.004
Huang, J. H., and Chen, Y. F. (2006). Herding in online product choice. Psychol. Market. 23, 413–428. doi: 10.1002/mar.20119
Joule, R. V. (1987). Le pied-dans-la-porte: un paradigme à la recherche d'une théorie [The foot-in-the-door procedure: a paradigm for research on a theory]. Psychol. Française 32, 301–306.
Joule, R. V., and Beauvois, J.-L. (1998). La soumission librement consentie: comment amener les gens à faire librement ce qu'ils doivent faire?. Paris: Presses universitaires de France.
Kiesler, C. A. (1971). The psychology of commitment: Experiments linking behavior to belief. New York: Academic Press.
Kiesler, C. A., and Sakumura, J. (1966). A test of a model for commitment. J. Pers. Soc. Psychol. 3, 349–353. doi: 10.1037/h0022943
Kiesler, S., Siegel, J., and McGuire, T. W. (1984). Social psychological aspects of computer-mediated communication. Am. Psychol. 39, 1123–1134. doi: 10.1097/0003-066X.39.10.1123
Lin, H., and Wang, H. (2014). Avatar creation in virtual worlds: Behaviors and motivations. Comput. Hum. Behav. 34, 213–218. doi: 10.1016/j.chb.2013.10.005
Markey, P. M., Markey, C. N., and Wells, S. M. (2003). “Applications of social and personality psychology to computer mediated communications,” in Trends in Social Psychology, ed J. Z. Arlsdale (New York, NY: Nova Science Publishers, Inc.), 91-109.
Matheson, K., and Zanna, M. P. (1989). Persuasion as a function of self-awareness in computer-mediated communication. Soc. Behav. 4, 99–111.
McGloin, R., Nowak, K. L., and Watt, J. (2014). Avatars and expectations: influencing perceptions of trustworthiness in an online consumer setting. Psychol. J. 12, 7–28.
McKenna, K. Y. A., and Bargh, J. A. (2000). Plan 9 from cyberspace: the implications of the Internet for personality and social psychology. Pers. Soc. Psychol. Rev. 4, 57–75. doi: 10.1207/S15327957PSPR0401_6
Messinger, P. R., Stroulia, E., Lyons, K., Bone, M., Niu, R. H., Smirnov, K., et al. (2009). Virtual worlds – past, present, and future: new directions in social computing. Dec. Sup. Syst. 47, 204–228. doi: 10.1016/j.dss.2009.02.014
Muscanell, N. L., and Guadagno, R. E. (2012). Make new friends or keep the old: gender and personality differences in social networking use. Comput. Hum. Behav. 28, 107–112. doi: 10.1016/j.chb.2011.08.016
Nass, C., and Moon, Y. (2000). Machines and mindlessness: social responses to computers. J. Soc. Issues 56, 81–103. doi: 10.1111/0022-4537.00153
Nowak, K. L. (2013). Choosing buddy icons that look like me or represent my personality: using buddy icons for social presence. Comput. Hum. Behav. 29, 1456–1464. doi: 10.1016/j.chb.2013.01.027
Nowak, K. L., and Biocca, F. (2003). The effect of the agency and anthropomorphism on users' sense of telepresence, copresence, and social presence in virtual environments. Pres. Teleoper. Virt. Environ. 12, 481–494. doi: 10.1162/105474603322761289
Nowak, K. L., Fox, J., and Ranjit, Y. S. (2015). Inferences about avatars: sexism, appropriateness, anthropomorphism, and the objectification of female virtual representations. J. Comput. Med. Commun. 20, 554–569. doi: 10.1111/jcc4.12130
Nowak, K. L., Hamilton, M. A., and Hammond, C. C. (2009). The effect of image features on judgments of homophily, credibility, and intention to use as avatars in future interactions. Media Psychol. 12, 50–76. doi: 10.1080/15213260802669433
Nowak, K. L., and Rauh, C. (2006). The influence of the avatar on online perceptions of anthropomorphism, androgyny, credibility, homophily, and attraction. J. Comput. Med. Commun. 11, 153–178. doi: 10.1111/j.1083-6101.2006.tb00308.x
Nowak, K. L., and Rauh, C. (2008). Choose your “buddy icon” carefully: the influence of avatar androgyny, anthropomorphism and credibility in online interactions. Comput. Hum. Behav. 24, 1473–1493. doi: 10.1016/j.chb.2007.05.005
Parmentier, G., and Rolland, S. (2009). Les consommateurs des mondes virtuels :construction identitaire et expérience de consommation dans second Life. Recherche et Applications en Marketing 24, 43–56. doi: 10.1177/076737010902400303
Pascual, A., and Guéguen, N. (2005). Foot-in-the-door and door-in-the-face: a comparative meta-analytic study. Psychol. Rep. 96, 122–128. doi: 10.2466/pr0.96.1.122-128
Pascual, A., Guéguen, N., Pujos, S., and Felonneau, M.-L. (2013). Foot-in-the-door and problematic requests: a field experiment. Soc. Influence 8, 46–53. doi: 10.1080/15534510.2012.696038
Rice, R. E., and Case, D. (1983). Electronic message systems in the university: a description of use and utility. J. Commun. 33, 131–152. doi: 10.1111/j.1460-2466.1983.tb02380.x
Saint-Bauzel, R., and Fointiat, V. (2012). The sweet smell of the requester: vanilla, camphor, and foot-in-the-door. Soc. Behav. Pers. 40, 369–374. doi: 10.2224/sbp.2012.40.3.369
Segovia, K. Y., and Bailenson, J. N. (2012). Virtual imposters: responses to avatars that do not look like their controllers. Soc. Influence 7, 285–303. doi: 10.1080/15534510.2012.670906
Short, J., Williams, E., and Christie, B. (1976). The Social Psychology of Telecommunications. New York, NY: John Wiley.
Keywords: avatar, behavioral influence, foot-in-the-door, virtual world, anthropomorphism
Citation: Barbier L and Fointiat V (2020) To Be or Not Be Human-Like in Virtual World. Front. Comput. Sci. 2:15. doi: 10.3389/fcomp.2020.00015
Received: 24 January 2020; Accepted: 20 April 2020;
Published: 15 May 2020.
Edited by:
Egon L. Van Den Broek, Utrecht University, NetherlandsReviewed by:
Laurent Moccozet, Université de Genève, SwitzerlandWalter Gerbino, University of Trieste, Italy
Copyright © 2020 Barbier and Fointiat. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Laura Barbier, bGF1cmEuYmFyYmllciYjeDAwMDQwO3VuaXYtbG9ycmFpbmUuZnI=
 Laura Barbier
Laura Barbier Valerie Fointiat
Valerie Fointiat