- 1Department of Electrical and Electronics Engineering, University of Liverpool, Liverpool, United Kingdom
- 2School of Advanced Technology, Xi’an Jiaotong-liverpool University, Suzhou, China
- 3School of Electronic and Information Engineering, Harbin Institute of Technology, Shenzhen, China
- 4College of Information Science and Technology, Donghua University, Shanghai, China
Compressive sensing (CS) has been extensively employed in uplink grant-free communications, where data generated from different active users are transmitted to a base station (BS) without following the strict access grant process. Nevertheless, the state-of-the-art CS algorithms rely on a highly limited category of measurement matrix, that is, pilot matrix, which may be analyzed by an eavesdropper (Eve) to infer the user’s channel information. Thus, the physical layer security becomes a critical issue in uplink grant-free communications. In this article, the channel reciprocity in time-division duplex systems is utilized to design environment-aware (EA) pilots derived from transmission channels to prevent eavesdroppers from acquiring users’ channel information. The simulation results show that the proposed EA-based pilot approach possesses a high level of security by scrambling the Eve’s normalized mean square error performance of channel estimation.
1 Introduction
Internet of Things (IoT) covers the domain of machine-to-machine and industrial communication technologies with automation applications Wei et al. (2020), Wang et al. (2021a). The explosively increasing number of users of IoT leads to the requirement of simultaneous support of massive users. To cope with it, non-orthogonal multiple access (NOMA) is employed to tackle the challenges of limited radio resources in IoT. Specifically, signals generated by different users are transmitted on the same radio resource through the use of dedicated multiple access signatures (e.g., power or code) to manage inter-user interference Parvez et al. (2018), Yuan et al. (2020).
However, NOMA depends on the conventional request-grant-based user access, where the procedure of scheduling/connection request and grant imposes prohibitive training overhead and latency. To this end, grant-free transmission is highly desirable, which can provide simultaneous support for massive users without undergoing assignment through a handshake process Wang et al. (2021b). In fact, the users who sporadically wake up from the idle state, referred to as burst users, only account for a small fraction of the total potential users Wang et al. (2020). Hence, the signals generated by burst users are sparse in the time domain. Since compressive sensing (CS) exploits the sparsity of a signal to recover it from far fewer samples than required by the Nyquist criteria, it makes the base station (BS) possible to recover the desired signals from far fewer measurements Tropp and Gilbert (2007). Built upon this structure, CS-based techniques for grant-free transmission have attracted a lot of attention Gao et al. (2016).
The existing CS-based grant-free techniques focus on channel estimation of active users, where the pilot matrix is mainly marked by Bernoulli distribution Wang et al. (2020) and Gaussian distribution Gao et al. (2015). In the study by Dai et al. (2018), the geometrical structure of the BS’s antenna array is utilized to design the non-orthogonal pilot for channel estimation, where the pilot matrix is equivalent to the discrete Fourier transform (DFT) matrix in the virtual angular domain. In our previous work Wang et al. (2021b), Bernoulli-based pilot in the time domain was proposed for channel estimation of active users in uplink grant-free communications. In light of that the majority of users transmit their signals during consecutive slots in practice, the temporal correlation of the active user sets between adjacent slots is employed to design the pilot sequence to enhance the performance of multi-user detection in grant-free communications. Given this guideline, Du et al. (2018) investigated the relationship between the block sparsity of the uplink access signals and the improved CS-based channel estimation, where the pilot matrix remains unchanged over the entire transmission period.
Since the existing channel estimation techniques rely on the specific pilot matrix in grant-free communications, the constant pilot matrix may introduce serious security problems when an eavesdropper has the knowledge of the pilot information. In this context, the physical layer security draws lot of attention Wei et al. (2022) Wei et al. (2021b). Rachlin and Baron (2008) showed that the CS-based encryption does not achieve Shannon’s definition of perfect secrecy, but a computationally unbounded adversary can easily infer that the correct sparse signal has been recovered. Hence, there are still issues left to be addressed in the security of pilot design for uplink grant-free communications.
Motivated by the aforementioned open challenges, in this article, an environment-aware (EA) pilot scheme is designed to ensure secure uplink grant-free communications. The contributions of this article are given as follows.
• The standard CS forms of the channel estimation for the proposed approach are derived based on the time domain and virtual angular domain, respectively. Furthermore, the gain pattern of the uniform linear array (ULA) antenna with a fixed direction angle of arrival (AoA) is given to show sparse signals in the virtual angular domain.
• Based on different domains, an environment-aware pilot scheme is designed to meet the requirement of secure uplink grant-free systems, where the eavesdropper can hardly acquire the channel information for different users. Furthermore, the proof of the validity of the pilot design, that is, measurement matrix, is given. The channel estimation performance of the proposed scheme is presented based on the different sparse bases in the LTE-Advanced (LTE-A) systems with the frequency selective channel.
Notation: We use the following notation throughout this article: Matrices are denoted by boldface uppercase letters, for example, A, while boldface lowercase letters are used to represent vectors, for example, a. ‖A‖2 denotes the l2 norms of matrix A. AT denotes the transpose of matrix A. We use diag(a) to transform the vector a into a diagonal matrix. Furthermore, ⊗ and vec (.) represent the Kronecker product and vectorization, respectively.
2 System Model
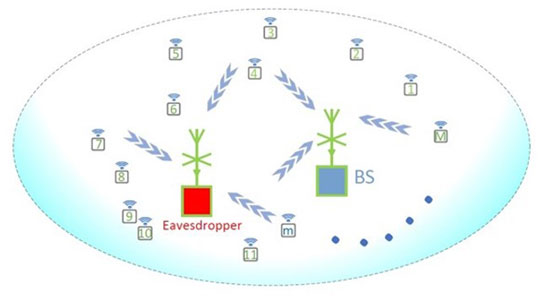
We consider a typical uplink grant-free communication with a base station (BS) and M potential active users, where the Time Division Duplex (TDD) communication protocol is employed to achieve the high-frequency spectrum efficiency. Furthermore, we use NOMA as an advanced radio access technology to fulfill the requirement of massive user connectivity. Without loss of generality, each user and BS is equipped with a single antenna and R antennas, respectively. As shown in Figure 1, there are M burst users who simultaneously wake up and transmit signals to the BS. An eavesdropper with the same number of antennas as the BS keeps monitoring the potential active users and tries to decrypt messages generated by active users.
The channel impulse for the m-th user in the time domain can be modeled as
where Lm, τl,m, and fd denote the number of multipath, the l-th path delay, and the maximum Doppler shift, respectively. Furthermore, the amplitude and phase of the m-th user are given by
where ϵl,m denotes the l-th path of complex gain. The azimuth AoA θl,m and the azimuth angle of departure ϕl,m follow uniform distribution. Furthermore, steering vectors at the BS and user can be, respectively, expressed by
where U denotes the number of user’s antenna. Accordingly and based on the frequency domain, (2) can be expressed by
where fs and p denote the sampling rate and the p-th of P pilots, respectively.
Each user is equipped with only one antenna, that is, U = 1. Hence, steering vectors at the user side are formed into a unit matrix. In this article, we focus on the low-velocity service, and hence, the small-scale follows a slow time-varying channel.
3 Proposed Secure Uplink Grant-Free Transmission
In this section, CS-based grant-free channel estimation in the time domain is firstly given in Section 3.1, followed by CS-based grant-free channel estimation in the virtual angular domain in Section 3.2. Finally, a secure uplink grant-free transmission scheme and a novel pilot design are proposed to enhance the wireless security, which are shown in Section 3.3.
3.1 CS-Based Grant-Free Channel Estimation in Time Domain
The time channel impulse of the k-th orthogonal frequency division multiplexing (OFDM) symbol between the m-th user and the r-th antenna at the BS can be expressed as
where
where
Since P ≪ ML, (6) indicates a standard CS structure Crespo Marques et al. (2019), where the CS theory can be employed to obtain the channel information.
3.2 CS-Based Grant-Free Channel Estimation in Virtual Angular Domain
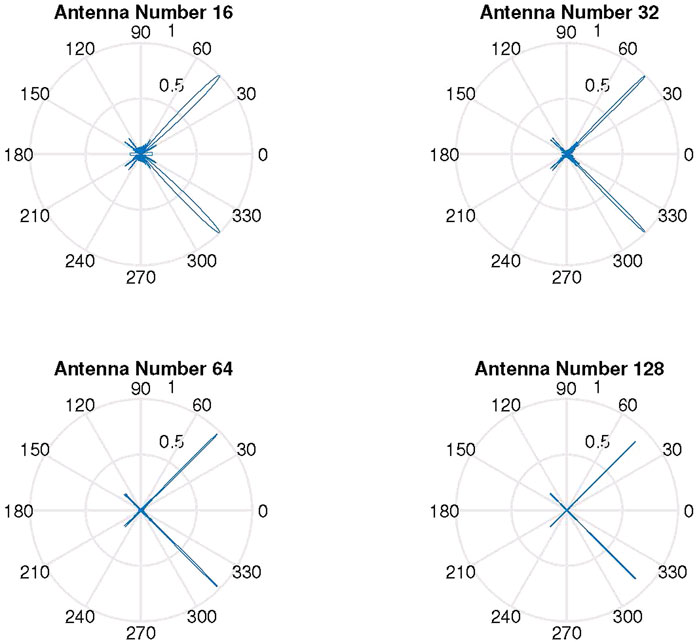
Tse and Viswanath (2005) and Zhou et al. (2007) introduced the concept of the virtual angular domain, where the energy of the received signal is limited to a restricted region. Accordingly, we simulate the gain pattern of a uniform linear array antenna with a fixed direction AoA as shown in Figure 2, where the AOA is set to 45° with 16, 32, 64, and 128 antennas at the BS, respectively. It can be observed that the resolution of AoA in the virtual angular domain increases with the number of antennas. Furthermore, there are limited scatters around the BS, where the signal is sparse in the virtual angular domain with finite AoA. Given this guideline, the channel estimation of sparse users is detailed later in this subsection.
The classical communication theory depicts the explicit channel characteristics on different use cases, where coherence time quantifies the similarity of the channel impulse at different times Lee (1997). Hence, the coherence time Tc in Rayleigh fading channel is expressed by
where simultaneously estimated consecutive symbols can be performed if transmission time is far less than the coherence time. Applying the multi-path slowly varying channels, the received pilot sequence of the p-th pilot of R antennas for K continuous transmission symbols at the BS can be written as
where
The channel matrix can be expressed as a sparse form, such as
where ABS = [ψBS(0), …, ψBS(R − 1)] and AUE = 1. Hence, we can arrive at
where
3.3 Secure Uplink Grant-free Communications and Pilot Design
Based on Sections 3.1, 3.2, it is clear that the eavesdropper needs to know all users’ pilots to acquire channel information of active users. In other words, grant-free communications cannot be conducted under a blanket of secrecy once the pilot book is disclosed. Hence, the unchanged users’ pilots may lead to severe security problems in uplink grant-free communications. To that end, the pilot in our approach is designed to be extracted from changeable environments, referred to as EA pilot, to keep users’ pilots updated and thus ensure secure grant-free transmission. In detail, if a user’s amplitude of channel information at the p-th pilot is higher than a set threshold at current transmission, the values of this users’ pilot at the p-th pilot for the next transmission are set to 1. Otherwise, they are set to −1. In particular, the channel reciprocity in the TDD mode is utilized to keep users’ pilots changing without signaling exchange between users and BS. By doing so, the transmitter can determine the downlink channel information upon the channel information obtained through the uplink channel estimation. Hence, it is hard for eavesdroppers to acquire pilot information and steal information generated by the target users.
Since the value of pilot is set to 1 or −1, it can be observed that the values in
and
where the element of
4 Simulation Results
This section demonstrates the efficacy of the proposed scheme with EA pilots in LTE-A systems. Furthermore, the normalized mean square error (NMSE) performance of eavesdroppers without knowledge of EA pilots is given to show the superiority of the proposed secure grant-free communications. The pilots are uniformly distributed throughout the symbol. Note that the linear interpolation algorithm is used to obtain channel information in non-pilot positions. Furthermore, the realization of grant-free communications, including user activity detection and channel estimation, is mainly based on our previous work Wang et al. (2021b).
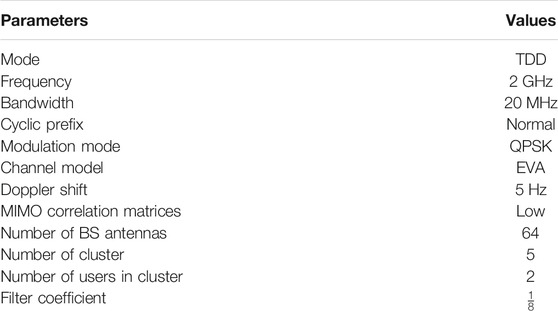
Considering the property of multipath slowly varying channels, the slight Doppler shift is employed. For example, given Doppler shift 5 Hz and the conventional Rayleigh fading channel, the coherence time Tc is equal to 8.46 ms based on (7), which is far less than a transmission subframe in LTE-A. Referring to 3GPP (2018), we evaluate the channel information performance of the active users based on the Extended Vehicular A (EVA) channel model, where the multipath propagation conditions consist of the maximum delay and relative power. The simulation parameters are given in Table 1.
Figure 3 shows the impact of SNR for the proposed scheme on the NMSE performance of channel estimation in the time and the virtual angular domain, respectively. Furthermore, the NMSE performance at the eavesdropper side is presented to show the superiority of the EA pilots. It can be observed that by employing CS on the time sparse basis and virtual angular basis, the EA pilot approach brings higher security in terms of the NMSE of channel estimation, which means the eavesdropper finds it hard to perform channel estimation. Hence, we can reasonably infer that by utilizing the EA pilot in the TDD mode, the uplink grant-free transmission can be conducted in a secure manner. In particular, it can be seen that the performance of the channel estimation in the time domain outperforms the receiver in the angular virtual domain. We consider this result reasonable since the receiver with a small number of BS antennas is influenced by the leakage power.
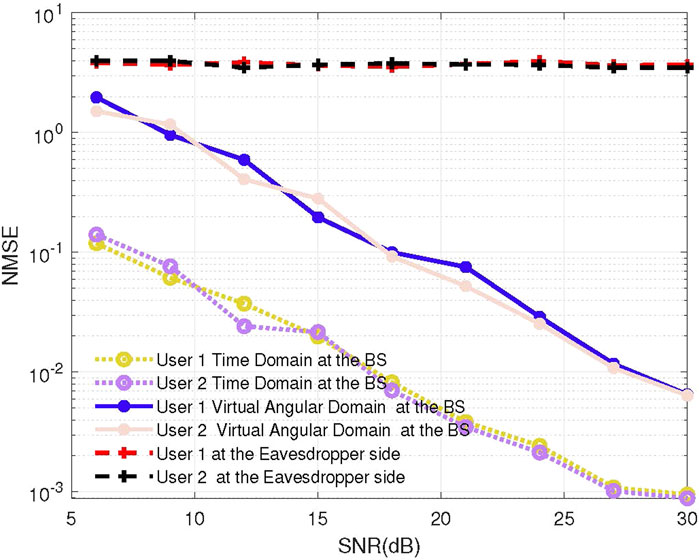
FIGURE 3. Impact of SNR for the proposed scheme on the NMSE performance of channel estimation in the time and virtual angular domain, where the number of BS antennas is set to 64.
5 Conclusion
This article focuses on the uplink grant-free communications and derives the standard CS form for channel estimation based on different sparse bases. In particular, the essentially invariant character of the channel impulse within the coherence time has been utilized to perform channel estimation in the virtual angular domain. Furthermore, an EA pilot scheme is proposed to meet the requirement of secure uplink grant-free communications, and the validity of the pilot design, that is, measurement matrix, is proven. Finally, we compare the channel estimation performance based on the different sparse bases in the LTE-A system. The simulation results show that the proposed EA-pilot-based uplink grant-free communications are conducted in a secure manner.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Funding
This work was supported by the AI University Research Centre (AI-URC) through XJTLU Key Programme Special Fund (KSF-P-02) and Jiangsu Data Science and Cognitive Computational Engineering Research Centre.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Calderbank, R., Howard, S., and Jafarpour, S. (2010). Construction of a Large Class of Deterministic Sensing Matrices that Satisfy a Statistical Isometry Property. IEEE J. Sel. Top. Signal. Process. 4, 358–374. doi:10.1109/jstsp.2010.2043161
Crespo Marques, E., Maciel, N., Naviner, L., Cai, H., and Yang, J. (2019). A Review of Sparse Recovery Algorithms. IEEE Access 7, 1300–1322. doi:10.1109/access.2018.2886471
Dai, J., Liu, A., and Lau, V. K. N. (2018). FDD Massive MIMO Channel Estimation with Arbitrary 2D-Array Geometry. IEEE Trans. Signal. Process. 66, 2584–2599. doi:10.1109/TSP.2018.2807390
Du, Y., Dong, B., Zhu, W., Gao, P., Chen, Z., Wang, X., et al. (2018). Joint Channel Estimation and Multiuser Detection for Uplink Grant-Free NOMA. IEEE Wireless Commun. Lett. 7, 682–685. doi:10.1109/LWC.2018.2810278
Gao, Z., Dai, L., Wang, Z., and Chen, S. (2015). Spatially Common Sparsity Based Adaptive Channel Estimation and Feedback for FDD Massive MIMO. IEEE Trans. Signal Process. 63, 6169–6183. doi:10.1109/tsp.2015.2463260
Gao, Z., Hu, C., Dai, L., and Wang, Z. (2016). Channel Estimation for Millimeter-Wave Massive MIMO with Hybrid Precoding over Frequency-Selective Fading Channels. IEEE Commun. Lett. 20, 1259–1262. doi:10.1109/LCOMM.2016.2555299
GPP (2018). Evolved Universal Terrestrial Radio Access (E-UTRA); User Equipment (UE) Radio Transmission and Reception. Sophia Antipolis, France: 3rd Generation Partnership Project. TS 36.101.
Lee, W. C. (1997). Mobile Communications Engineering: Theory and Applications. New York City: McGraw Hill Professional.
Parvez, I., Rahmati, A., Guvenc, I., Sarwat, A. I., and Dai, H. Y. (2018). A Survey on Low Latency towards 5G: RAN, Core Network and Caching Solutions. IEEE Commun. Surv. Tutorials 20, 3098–3130. doi:10.1109/Comst.2018.2841349
Rachlin, Y., and Baron, D. (2008). “The Secrecy of Compressed Sensing Measurements,” in Proceedings of the 2008 46th Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, September, 2008, 813–817. doi:10.1109/allerton.2008.4797641
Scherzer, O. (2010). Handbook of Mathematical Methods in Imaging. Berlin/Heidelberg, Germany: Springer Science & Business Media.
Tropp, J. A., and Gilbert, A. C. (2007). Signal Recovery from Random Measurements via Orthogonal Matching Pursuit. IEEE Trans. Inf. Theor. 53, 4655–4666. doi:10.1109/TIT.2007.909108
Tse, D., and Viswanath, P. (2005). Fundamentals of Wireless Communication. Cambridge, UK ; New York: Cambridge University Press.
Wang, Y., Lim, E. G., Xue, X., Zhu, G., Pei, R., and Wei, Z. (2021a). Interference Utilization Precoding in Multi-Cluster IoT Networks. Front. Signal Process. 1, 11. doi:10.3389/frsip.2021.761559
Wang, Y., Zhu, X., Lim, E. G., Wei, Z., and Jiang, Y. (2021b). Grant-free Communications with Adaptive Period for IIoT: Sparsity and Correlation Based Joint Channel Estimation and Signal Detection. IEEE Internet Things J. doi:10.1109/jiot.2021.3106546
Wang, Y., Zhu, X., Lim, E. G., Wei, Z., Liu, Y., and Jiang, Y. (2020). “Compressive Sensing Based User Activity Detection and Channel Estimation in Uplink NOMA Systems,” in Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea (South), May, 2020, 1–6. doi:10.1109/WCNC45663.2020.9120664
Wei, Z., Liu, F., Masouros, C., and Vincent Poor, H. (2022). Fundamentals of Physical Layer Anonymous Communications: Sender Detection and Anonymous Precoding. IEEE Trans. Wirel. Commun. 21 (1), 64–79. doi:10.1109/TWC.2021.3093722
Wei, Z., Masouros, C., Liu, F., Chatzinotas, S., and Ottersten, B. (2020). Energy- and Cost-Efficient Physical Layer Security in the Era of IoT: The Role of Interference. IEEE Commun. Mag. 58, 81–87. doi:10.1109/MCOM.001.1900716
Wei, Z., Masouros, C., and Liu, F. (2021b). Secure Directional Modulation with Few-Bit Phase Shifters: Optimal and Iterative-closed-form Designs. IEEE Trans. Commun. 69, 486–500. doi:10.1109/TCOMM.2020.3032459
Yuan, Y., Yuan, Z., and Tian, L. (2020). 5G Non-orthogonal Multiple Access Study in 3GPP. IEEE Commun. Mag. 58, 90–96. doi:10.1109/MCOM.001.1900450
Keywords: grant-free communications, compressive sensing, physical layer security, channel estimation, pilot design
Citation: Wang Y, Lim EG, Zhang Y, Zhong B, Pei R and Zhu X (2022) Compressive Sensing-Based Secure Uplink Grant-Free Systems. Front. Sig. Proc. 2:837870. doi: 10.3389/frsip.2022.837870
Received: 17 December 2021; Accepted: 25 January 2022;
Published: 23 February 2022.
Edited by:
Zhongxiang Wei, Tongji University, ChinaReviewed by:
Dawei Wang, Northwestern Polytechnical University, ChinaHongjiang Lei, Chongqing University of Posts and Telecommunications, China
Copyright © 2022 Wang, Lim, Zhang, Zhong, Pei and Zhu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Eng Gee Lim, ZW5nZ2VlLmxpbUB4anRsdS5lZHUuY24=; Xu Zhu, eHV6aHVAaWVlZS5vcmc=
 Yuanchen Wang
Yuanchen Wang Eng Gee Lim2*
Eng Gee Lim2* Yanfeng Zhang
Yanfeng Zhang Xu Zhu
Xu Zhu