- 1College of Mathematics and Statistics, Sichuan University of Science and Engineering, Zigong, China
- 2South Sichuan Applied Mathematics Research Center, Zigong, China
In the digital era, the significance of cryptographic algorithms has grown significantly within the realm of cybersecurity. This research presents an innovative approach to image encryption that eliminates the security limitations of the conventional one-dimensional logistic mapping. This approach relies on an enhanced two-dimensional logistic-fraction hybrid chaotic mapping (2D-LFHCM) and deoxyribonucleic acid (DNA) computing. Initially, the improved 2D-LFHCM is utilized to effectively scramble the image by incorporating chaotic sequences. Then, two novel algebraic DNA computing rules are introduced to enhance diffusion encryption. Experimental findings show that this approach offers superior security performance, even with renowned attacks.
1 Introduction
Chaos, which refers to complex and unpredictable behavior displayed by nonlinear dynamic systems, is a phenomenon characterized by the inherent unpredictability of deterministic nonlinear systems. The slightest change in the initial state can lead to unforeseen results. Chaos is not restricted to a particular domain but can be observed in various aspects of human society. The profound exploration of chaos has given rise to a natural problem: what are the potential applications of chaos? This query stands as a paramount concern not only in the present world but also in the future. As fundamental and applied sciences progress, chaos theory has evolved into a crucial focal point within the realm of nonlinear science, blossoming into a discipline that has thrived over the past few decades. Contemporary electronic engineering and image processing heavily draw upon chaos theory, utilizing its principles to yield numerous innovative and advantageous advancements in these fields.
The characteristics of chaos systems include nonlinearity, ergodicity, pseudo-random behavior, and a high sensitivity to initial conditions. As a result, chaos theory serves as a solid foundation for the development of excellent image encryption algorithms. However, it has been observed that employing a single chaotic system often leads to a limited range of possible encryption keys, thereby rendering the algorithm susceptible to attacks from malicious entities. Consequently, to ensure the creation of a robust and efficient image encryption algorithm, researchers frequently integrate chaotic systems with other disciplines, including the analysis of deoxyribonucleic acid (DNA) sequences [1–4], the utilization of optical maps [5,6] or cellular automata (CA) [7,8], the application of compressed sensing [9,10], and chaotic circuits [11–17].
Therefore, chaos theory holds immense potential for research and practical significance in the domain of image encryption. Ever since R. Matthews [18] introduced a broader logistic map and relied on it in the data encryption domain, a new era of chaotic systems generating pseudo-random numbers is beginning. Thus, fresh impetus is provided to cryptography. Consequently, chaos and cryptography became intertwined. Subsequently, Alvarez [19] formulated the fundamental requisites and rules of chaotic cryptosystems, gaining recognition from experts in the field of cryptography. Since then, there has been a robust development regarding chaotic digital image encryption. In 2012, Wang [20] invented a novel technique employing a traditional logistic map for the encryption of color images. Nevertheless, the key space induced by one-dimensional chaos is limited, and the algorithm’s handling of chaotic sequences is not sufficient, resulting in unsatisfactory robustness of the algorithm. In an attempt to address this issue, Wang [21] put the latest method for creating high-dimensional digital chaotic systems, but the drawback lies in the complexity of the system structure and the inefficiency of the algorithms. More recently, Huang [22] proposed a fine-tuned cubic color image encryption scheme that operates jointly by chaos and hyperchaos. Its core idea is based on an improved logistic-fraction hybrid chaotic mapping (LFHCM) proposed to address the limitations of one-dimensional chaotic mapping and expand the key space. This mapping is then linked with a four-dimensional hyperchaotic system to generate the key stream, which is used to rotate and shift the rows and columns of each component in the red (R), green (G), and blue (B) channels of the color image. Wang [23] attempted to accomplish global scrambling by creating a chaotic sequence using the Lorenz system for binary and Gray code translation. Remarkably, this algorithm exhibits a favorable encryption effect on grayscale images. Building upon these advancements, Gao [24] introduced a multi-image encryption technique founded on single-channel scrambling, diffusion, and chaotic systems. Performance investigation validates that this technique demonstrates exceptional capabilities in ensuring security and achieving efficient encryption speed. Furthermore, in his study [25], Alexan proposes a method for encrypting color images. This approach effectively combines KAA mapping with various chaotic mappings in a synergistic manner. Notably, this approach maximizes the utilization of Shannon’s security idea and encrypts the image through bit obfuscation and diffusion.
However, amidst a plethora of algorithms, our specific interest lies in encryption methods rooted in chaotic dynamics and deoxyribonucleic acid (DNA) sequences. The encryption performance of this algorithm, proposed by Chai [26], is not only exceptional but also demonstrates the ability to withstand a range of conventional attacks. In 2018, an image encryption algorithm was introduced by Wu [27], which employed a combination of DNA coding and Henon-Sine mapping. To increase the complexity of the encryption process and strengthen the algorithm’s security, XOR operations and DNA coding were added to the diffusion process. In 2020, Patel [28] introduced a novel algorithm for encrypting images, which combined DNA coding and a three-dimensional chaotic mapping technique. In addition to utilizing the idea of eight complementary encodings for picture encryption, this approach employed a chaotic sequence to jumble the image. Both of these algorithms are applicable for encrypting grayscale and color images. Liu [29] then applies an improved Arnold transformation to scramble the three components and uses the DNA sequence generated through the chaotic sequence to conduct diffusion encryption of the color image. Hua [30] presented an innovative dynamic image encryption technique that enhanced the security of image data by utilizing quantum walk and chaos-induced DNA. Inspired by them, a plagiarism detection method is presented utilizing an improved two-dimensional logistic-fraction hybrid chaotic mapping (2D-LFHCM) and DNA computation. This method incorporates DNA chaotic diffusion and scrambling techniques.
The organization of this paper is outlined below. Section 2 delves into the 2D-LFHCM and analyzes its chaotic characteristics. The fundamental principles of encryption and decoding are covered in Section 3. Section 4 presents the devised method for key creation as well as the encryption and decryption methods for DNA images. Section 5 elucidates the numerical simulation findings of the proposed cryptosystem, supplemented by a comprehensive exploration of its security analysis. Ultimately, Section 6 furnishes a thorough recapitulation of the study’s content and outlines potential directions for future research.
The main contributions of this paper are highlighted below:
(i) Development of an enhanced two-dimensional logistic-fraction hybrid chaotic mapping (2D-LFHCM) for image encryption.
(ii) Design and implementation of novel deoxyribonucleic acid (DNA) computing techniques in the proposed encryption method, including right shift addition, right shift subtraction, right shift XOR, and other DNA computing methods.
(iii) A comprehensive performance analysis of the encryption algorithm was conducted, including aspects such as encryption speed, key space, histograms, information entropy, and correlation coefficients.
2 An improved 2D-LFHCM
2.1 The definition of 2D-LFHCM
Parabolic mapping is a generic term used to describe a kind of chaotic maps. The classical insect population model (or logistic mapping, shortly, LM) is represented as Equation 1.
where
where
In Equation 3,
Based on the original one-dimensional logistic map, the LFHCM (logistic-fraction hybrid chaotic mapping) derived from the logistic map and fraction map is proposed by Huang [22]. The fraction mapping is proposed by Lu et al. [33] to address the practical needs of multi-objective optimization and multi-model issues. The definition equation of fraction mapping is Equation 4.
where
where
Thanks to their excellent chaotic performance, LM, 2D-LM, 2D-LMM, and LFHCM are often used as pseudo-random signal generators in engineering fields such as cryptography and dynamics. However, LFHCM has not yet been extended to two-dimensional. The traditional logistic-fraction mapping serves as the fundamental basis for the 2D-LFHCM described in this study, and its difference equation is
where,
2.2 Analysis and comparison of chaotic properties of 2D-LFHCM
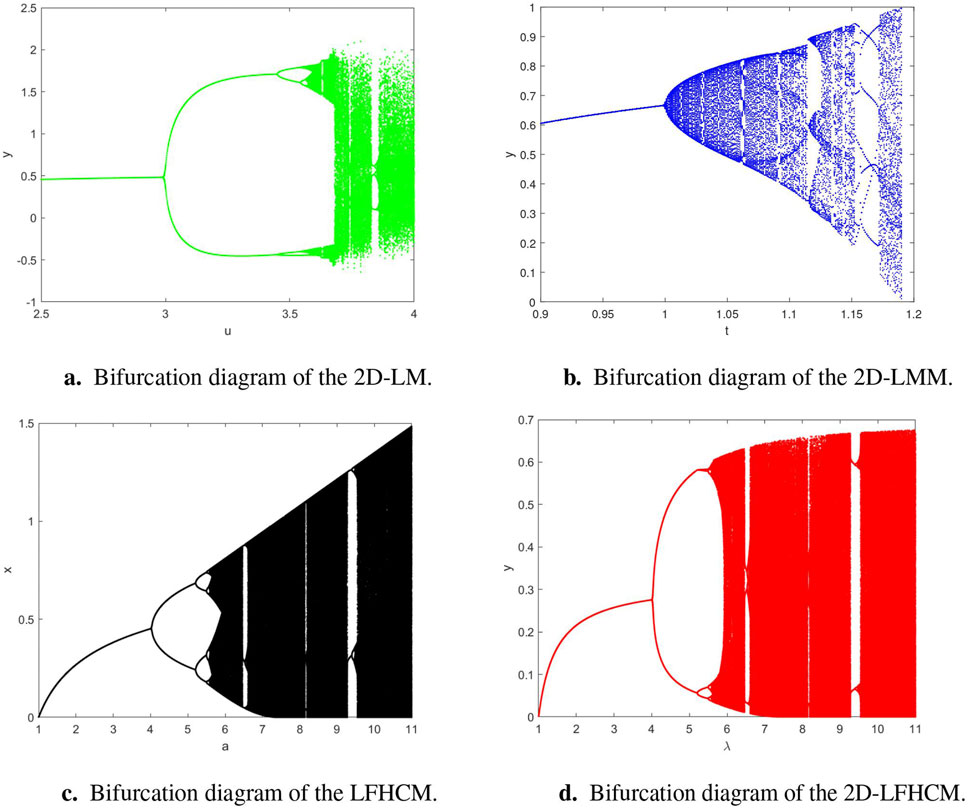
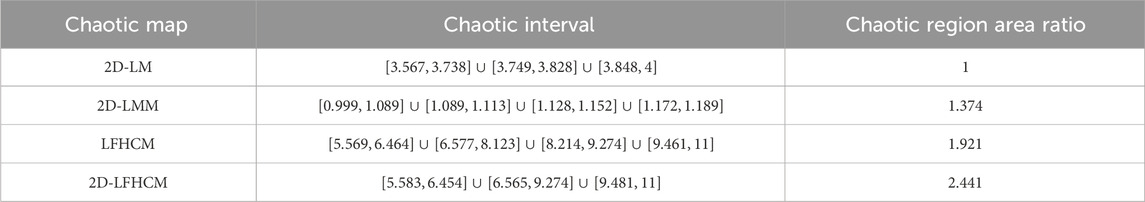
In the preceding section, different classical maps were defined, and enhancements were made to the two-dimensional map, referred to as 2D-LFHCM. This section assesses and compares the chaotic properties of the following chaotic maps: 2D-LM, 2D-LFHCM, 2D-LMM, and LFHCM. The study is done from the perspectives of the phase trajectory diagrams, Lyapunov exponents, bifurcation diagrams, and chaotic analysis of the iterative sequences. It will be shown that the improved two-dimensional chaotic map 2D-LFHCM has better chaotic characteristics.
2.3 Bifurcation diagrams
Assume that the initial conditions of the following four mappings are (0.1, 0.1), and their control parameters are
2.4 Lyapunov exponents spectrum
In general, the Lyapunov exponent is a very important statistical feature. It characterizes the stability of dynamic systems and can be used to judge whether the system presents chaotic behavior and the degree of chaos. The Lyapunov exponent describes the exponential growth rate of the system under small changes in initial conditions, which reflects the sensitivity and predictability of the system. To rephrase, determining the Lyapunov exponent spectrum can aid in our comprehension of the system’s dynamic behavior, as well as in determining whether or not chaos exists inside the system and to what extent. For a discrete chaotic mapping
the Lyapunov exponent can be expressed as Equation 8.
where
Two Lyapunov exponents,
2.5 Iteration sequence and phase diagram
For the 2D-LFHCM, with fixed parameters
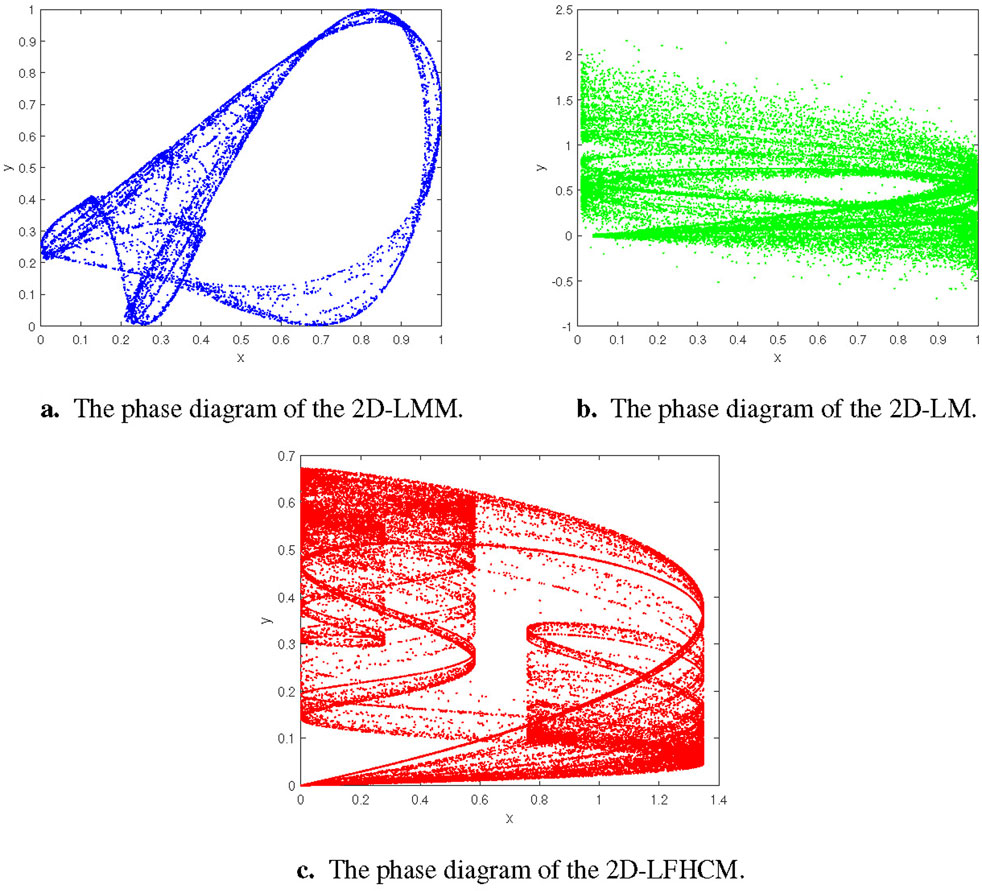
Based on diverse parameters, maps in the specified interval can generate chaotic effects, resulting in a chaotic phase diagram. Figure 4 illustrates the chaotic phase portraits of 2D-LMM, 2D-LM, and 2D-LFHCM under specific conditions (
By analyzing the numerical simulation results presented in Figure 4, it becomes evident that the 2D-LFHCM proposed in this research exhibits a larger chaotic range in the phase plane compared to 2D-LMM and 2D-LM. This observation indicates that the 2D-LFHCM can generate a more diverse range of chaotic pseudo-random outcomes, thereby enhancing ergodicity. This improvement is valuable for potential applications, including signal generation and the utilization of chaotic systems in image encryption.
3 The basic principles of encryption and decryption
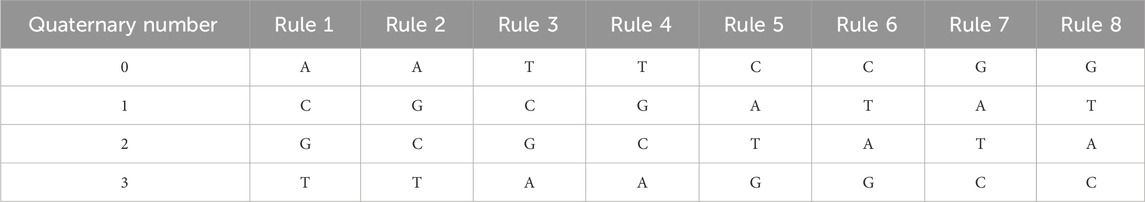
In the field of biology, deoxyribonucleic acid (DNA) stands as a fundamental biomolecule present within the cells of all organisms, serving as the genetic material for the majority of living entities. It is gratifying that DNA also plays an indispensable role in cryptography [34]. If the nucleotide bases in DNA information are matched to the binary digits 00, 01, 10, and 11, there are a total of 8 DNA coding rules [35], each corresponding to its own rules for addition, subtraction, and XOR operations. DNA primarily achieves the genetic code through the arbitrary combination of four bases: adenine (A), cytosine (C), guanine (G), and thymine (T), where A and T are complementary, C and G are complementary. The binary numerals 0 and 1, which complement each other, also serve a purpose in computers to store information. By leveraging these characteristics, when implementing DNA’s quaternary encoding with four bases, there can be a total of eight pairing rules. The coding table is shown in Table 2.
In a computer, the quaternary system is a digital system based on the number 4. The four numbers 0, 1, 2, 3, and A, T, C, G one-to-one mapping. If four bases in DNA are used for four-image coding, there are a total of eight rules that can be paired with each other. The coding table is shown in Table 2. Following the rules provided in Table 2, a 4-digit quaternary number can be directly represented by a 4-length DNA sequence. As an example, the quaternary number “1320” can be used to represent the decimal 120 Gy value. Since the numbers 0, 1, 2, and 3 are mapped one by one with A, T, C, and G, they are eventually converted into TGCA.
The cryptosystem in modern cryptography can be succinctly denoted as a five-tuple
Mathematically, the well-known technique of the right cyclic shift involves rearranging a collection of data sequences. The specific procedure entails relocating the final number to the initial position and shifting all the remaining elements to the right, aligning them with their corresponding positions. On the other hand, the left circulation shift is similar. Throughout the shifting process, the cyclicity is maintained, ensuring that the removed element reappears at the opposite end of the sequence.
Let
Correspondingly,
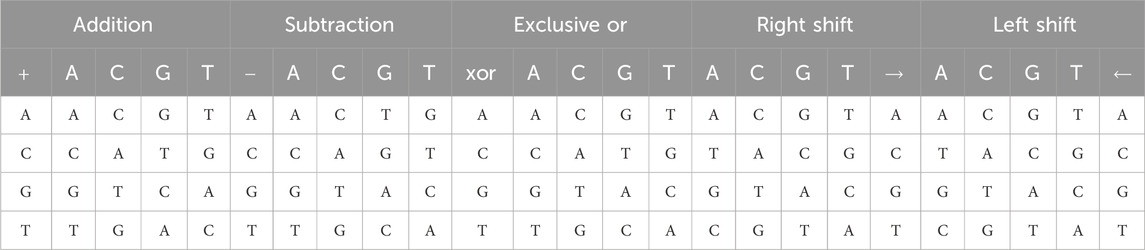
As per the operational guidelines provided in Table 3, DNA left shift and DNA right shift algebraic operators, grounded in DNA sequences, facilitate the definition of six DNA algebraic operations. These include DNA right (left) shift addition, DNA right (left) shift subtraction, and DNA right (left) shift XOR.
As an illustration, for the DNA operation before the shift and the DNA right shift XOR, one can get
The DNA right shift addition
The DNA right shift subtraction
The DNA right shift XOR
4 Proposed image encryption scheme
This section includes a thorough overview of the important parts of the encryption mechanism, such as key creation, chaotic DNA scrambling, and diffusion. Specifically, the scrambling operation exchanges the position and interference of pixels in the ordinary image, minimizing the strong correlation between adjacent pixel values. The pixel data diffusion serves as a critical measure to enhance security. By integrating scrambling and diffusion, both the position and grayscale value of the pixel are simultaneously altered, ensuring that the grayscale information of any pixel is concealed within numerous other pixels.
Let

Figure 5. Flowchart of the encryption process (where the picture of Lena is sourced from [38]).
Step 1. Key stream generation.
(i) Let
(ii) After iterating
(iii) To eliminate transient effects for increased security, the first
(iv) The encrypted chaotic sequence
where, the function sort is employed to arrange the data and provide the corresponding index values.
(v) Generation of the encrypted chaotic sequence
where
(vi) The generation of an encrypted chaotic sequence, referred to as
Step 2. DNA encoding of the original image.
(i) Let
(ii) Reshape the original image
(iii) Encode each pixel value of
(iv) The DNA image
Step 3. DNA chaotic confusion and diffusion.
(i) To initiate the initial chaotic confusion, the following Equation 13 is employed to disrupt the positions of
(ii) The sequence
(iii) The implementation of the DNA diffusion operation between the DNA sequence
(iv) To further scramble the positions, we employ the method presented in (i), which is Equation 16 in this case, to disrupt the position of
(v) Following rule 1 in Table 2, every nucleotide A, C, G, and T in the diffused DNA image
(vi) Encoded as integer values in the range of 0–255 for every 4 bits, these values are then transformed into a grayscale cipher image
Step 4. Cipher image.
The gray cipher image
The image decryption process closely mirrors the encryption procedure, involving the sequential inversion of steps utilized in encryption and relying on the application of a cryptographic key. Similarly, if DNA right shift addition is utilized in the encryption phase, it would be reversed in the decryption phase.
5 Performance evaluation
In this section, various images (such as Lena, Onion, and Cameraman) will be utilized to evaluate the performance of the proposed cryptosystem based on image statistical performance and security analysis. All experimental results were calculated using MATLAB 2018b on a compatible computer with Windows 10, 8.00 GB RAM, and Intel (R) Core (TM) i5-7300HQ CPU @ 2.50 GHz. Figure 6 displays the encryption performance of the proposed cryptographic system. Each part begins with a row displaying the plain image, followed by the encrypted image, and concludes with the decrypted image, from left to right. The second line exhibits histograms for both the plain and encrypted images. We have documented all experimental data in a table, which provides evidence of the outstanding capabilities of our cryptographic system in effectively addressing various security and statistical risks.
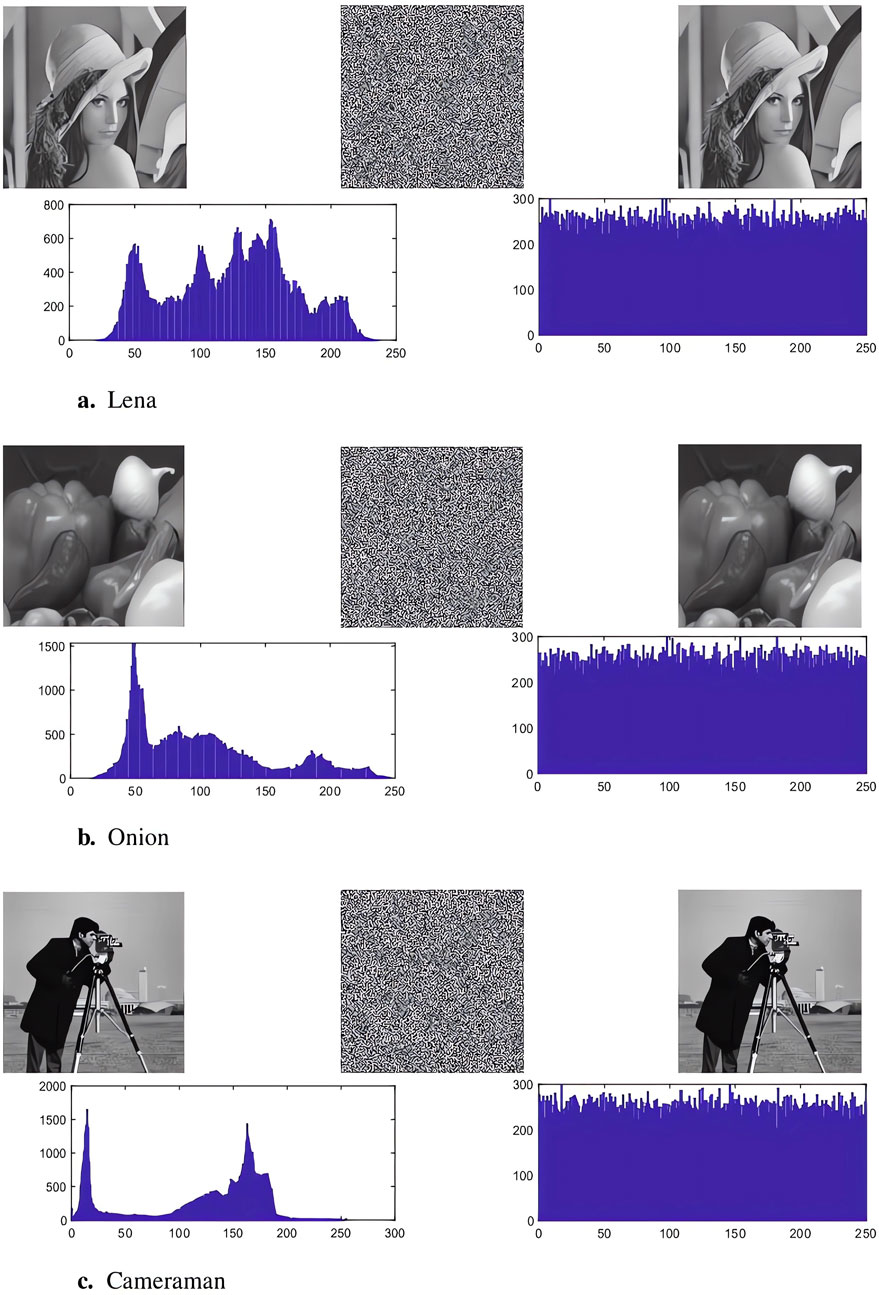
Figure 6. The original images, encrypted images, decrypted images, and histograms of the original and encrypted images of Lena (A), Onion (B), and Cameraman (C), respectively (where the pictures of Lena, Onion, and Cameraman are sourced from [38], [43], and [27], respectively).
5.1 Key space analysis
The extent of the key space in an image encryption scheme is a pivotal factor in determining its security. The key space encompasses all authorized keys for the scheme. Evidently, an expanded key space augments the scheme’s resilience against exhaustive attacks, thereby ensuring an elevated level of security for the encrypted image algorithm. As a general rule, if the key space exceeds
5.2 Time cost and speed analysis
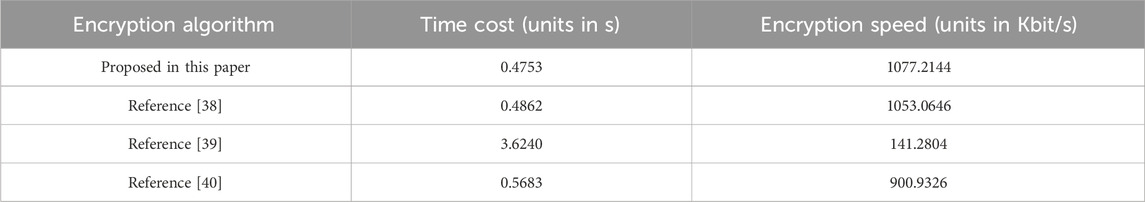
A superior encryption scheme should not sacrifice encryption time but instead strive to minimize it while ensuring security. In certain application scenarios, such as image transmission, real-time performance is paramount. This necessitates that encryption algorithms be capable of completing data encryption within a short timeframe to ensure real-time transmission. The average encryption time for the aforementioned grayscale images of size
5.3 Histogram analysis
During everyday practical use, there is a potential risk of theft or attack on encrypted images while they are being transmitted. Thus, it becomes crucial to assess both the statistical properties and security of these encrypted images. One of the most basic and intuitive techniques for examining the frequency distribution in plaintext and encrypted images is histogram analysis. Examining the histogram is instrumental in assessing the performance of the encryption algorithm. In case the histogram of the encrypted image exhibits an even or irregular distribution, it indicates that the statistical characteristics have been concealed or destroyed, suggesting that the encryption algorithm might be more efficient. If the histogram of the ciphertext image displays noticeable characteristics or exhibits a notably dissimilar distribution pattern compared to that of the plaintext image, it could indicate potential vulnerabilities in information leakage or the encryption algorithm. Such observations are valuable in identifying encryption issues and enhancing the encryption scheme. In Figure 6, the histograms for various images (Lena, Onion, and Cameraman) can be observed. From an intuitive perspective, it becomes apparent that encrypted images exhibit a uniform histogram, while the histograms of plaintext images vary. If the histogram of encrypted images exhibits an approximately uniform distribution, indicating a lack of discernible regularity in pixel value distribution, it signals the heightened robustness of the encryption scheme against statistical attacks.
5.4 Chi-square analysis
Non-uniformly distributed pixel values can imply that there are some specific features or structures in the image, which may make it easier for the encrypted image to infer some information from the histogram, thereby compromising the encryption’s security level. On the contrary, when pixel values are uniformly distributed, potential intruders are prevented from extracting reliable information from the histogram, because the histogram lacks discernible peaks or features, indicating that the image’s statistical characteristics are to some extent concealed. Consequently, inferring information about the original image from the histogram becomes challenging.
The
is called the Pearson
Given the image dimensions as
Equation 18 obeys the
The generally used significance level is
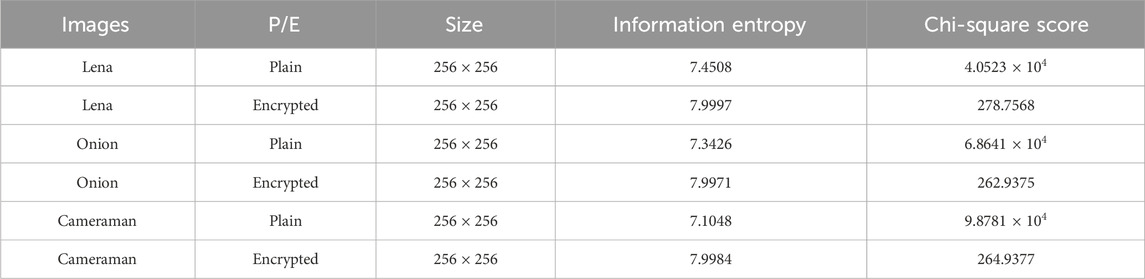
Table 5. The entropy values and scores of the original images and encrypted images of Lena, Onion, and Cameraman, respectively.
5.5 Information entropy
The unpredictability of image information is reflected in information entropy. It is widely accepted that higher entropy corresponds to increased uncertainty, greater disorder within the information, and reduced visual information. The calculation formula for information entropy can be expressed as Equation 19.
where,
For a randomly generated grayscale image with a gray level of
5.6 Correlation
Evaluating the correlation properties of both the original and encrypted images is essential, complementing the analysis of the image’s histogram and information entropy. Neighboring pixels in the horizontal, vertical, main diagonal, and sub-diagonal directions exhibit a strong correlation in the original image. The objective of image encryption algorithms is to minimize the correlation between adjacent pixels in the encrypted image, providing a defense against statistical attacks. A correlation value of zero is ideal. This study randomly samples 2000 pairs of neighboring pixels along the horizontal, vertical, main diagonal, and secondary diagonal directions from both the plain and encrypted images. In this study, 2000 pairs of adjacent pixels are randomly selected from both the original and encrypted images in the horizontal, vertical, main diagonal, and secondary diagonal directions. The correlation coefficient between the two adjacent pixels can be computed by applying Equation 20.
where
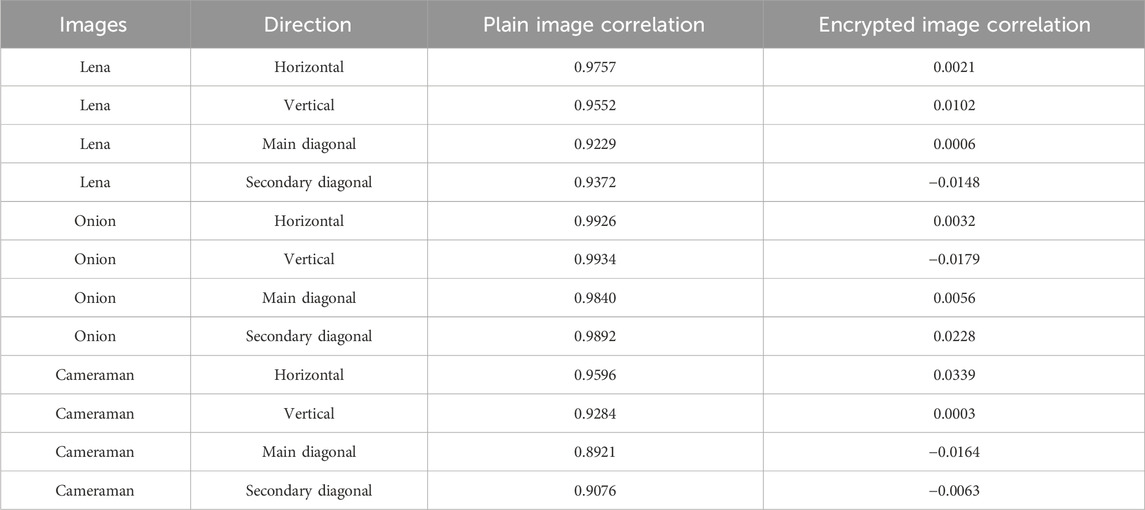
Table 6. Results of the correlation coefficient between original and encrypted images of Lena, Onion, and cameraman in various directions.
The correlation between adjacent pixels in the original and encrypted images of Lena, Onion, and Cameraman is depicted in Figure 7 for the horizontal, vertical, and main diagonal directions (from left to right). The experimental results indicate a lack of significant correlation between neighboring pixels in the encrypted images, in contrast to the noticeable correlation present in the original images. The efficacy of the encryption system described in this study is highlighted by this conclusion. It’s important to note that these results are obtained after only a single round of encryption. If multiple encryptions are performed, the effect may be more significant.
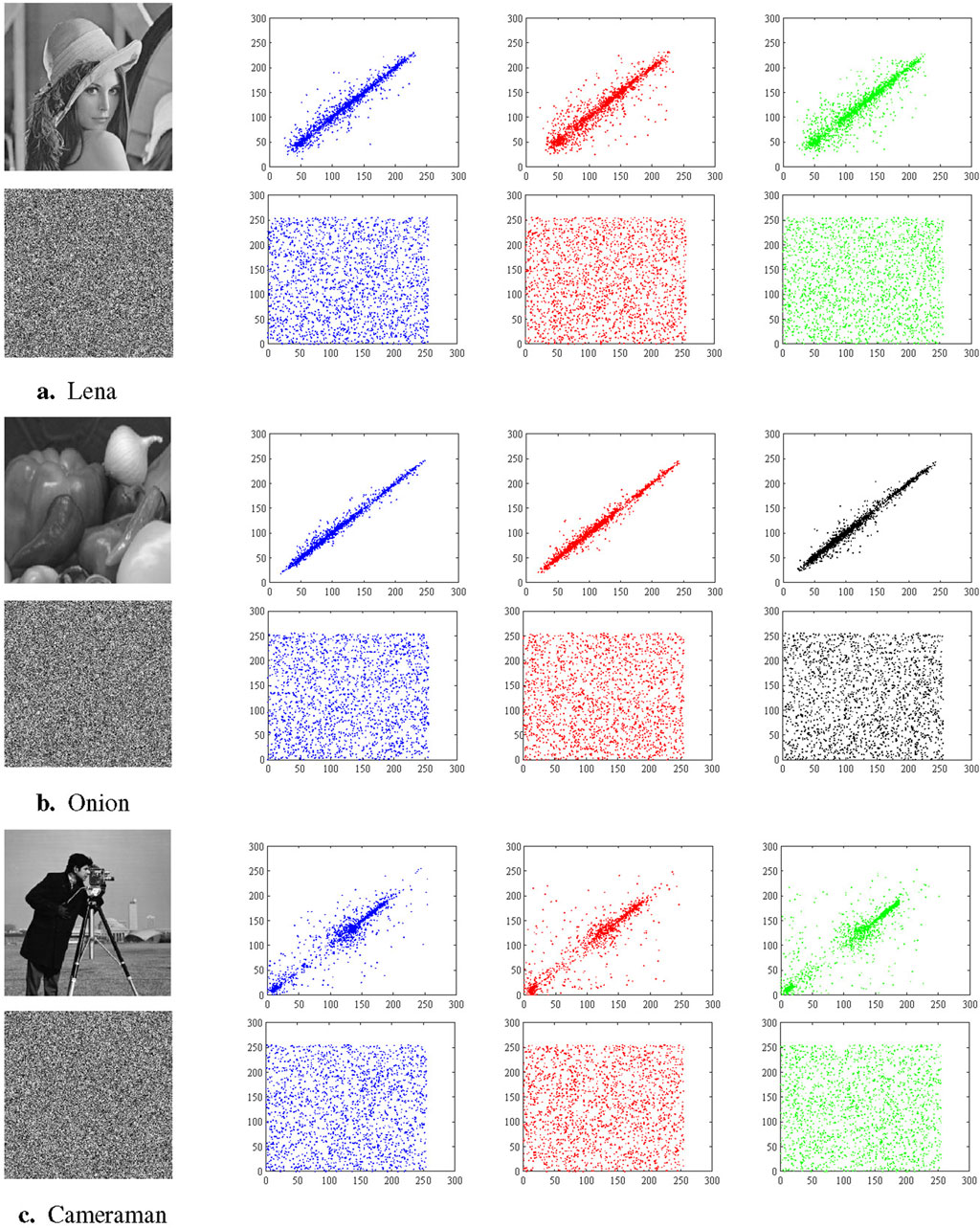
Figure 7. The first row of the three sets of images Lena (A), Onion (B), and Cameraman (C), from left to right, are the original images and the correlation of adjacent pixels of the original images in the horizontal, vertical, and diagonal direction, respectively. The second row is the same, only for their encrypted images. (The pictures of Lena, Onion, and Cameraman are sourced from [38], [43], and [27], respectively).
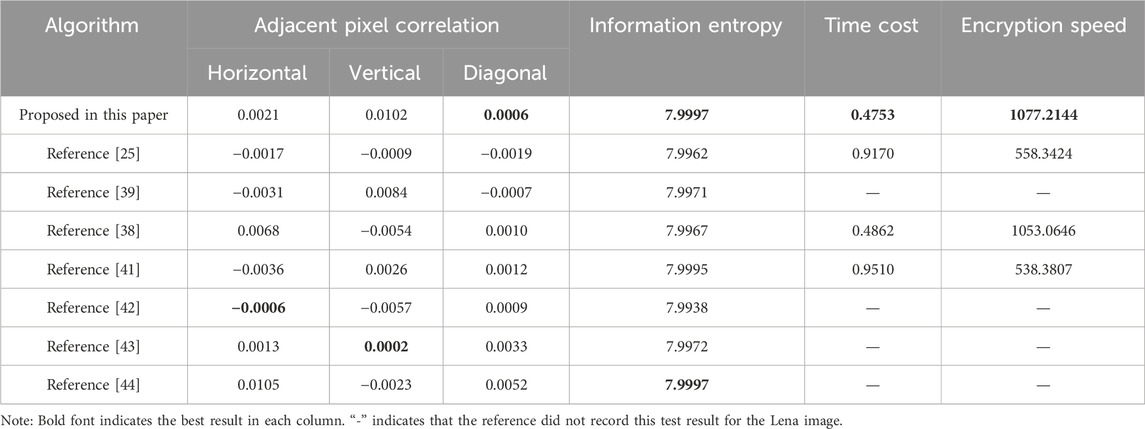
5.7 Comparison and analysis
The algorithm in this paper is used to encrypt and test the performance of image Lena, and compared with other encryption algorithms. The test results of other algorithms are directly quoted from the corresponding papers. The comparison results are shown in Table 7. It can be observed that the performance difference of adjacent pixel correlation analysis of each algorithm is small. In terms of information entropy and other resistance to statistical attacks and encryption speed, the algorithm in this paper has better performance, indicating that the algorithm in this paper has better security.
6 Conclusion
The hybrid image encryption method described in this paper integrates DNA computing theory with the improved 2D-LFHCM. Furthermore, the security, histogram, correlation coefficient, and information entropy aspects of the proposed scheme are examined to demonstrate its rationality. Numerical simulations demonstrate the notable efficacy of the image encryption technique introduced in this study.
A feasible idea for future work is to apply the proposed method to multi-image encryption [24,36], which can improve efficiency while ensuring security. Another possibility is to combine encryption with quantum technology. In light of the advancements in quantum information technology, numerous technologies have been proposed to enhance traditional image encryption algorithms. The exponentially accelerating capabilities of quantum technology, as opposed to traditional computing, are critical for mitigating the vulnerability of encryption algorithms to decipherment. To harness the potential benefits of combining quantum computing with conventional image encryption approaches, Hua Hua et al. [30] came up with dynamic image encryption via quantum walks and chaos-induced DNA to boost image security. Wen Wen and Lin [37] analyzed the security of an existing image encryption algorithm based on quantum chaotic map and DNA coding (QCMDC-IEA), and proposed a low-complexity attack method, which provides some theoretical tips and suggestions for improving the security of the system based on DNA coding and chaotic image encryption. Our upcoming study aims to investigate the potential synergy between quantum walking and the recently proposed DNA computing principles to develop an innovative encryption method. This novel approach is expected to enhance the security measures for image encryption, thus carrying significant implications.
Data availability statement
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Author contributions
YC: Software, Validation, Writing–original draft. TL: Funding acquisition, Supervision, Writing–review and editing. CC: Conceptualization, Formal Analysis, Writing–review and editing. YX: Investigation, Writing–review and editing.
Funding
The author(s) declare that financial support was received for the research, authorship, and/or publication of this article. This work was funded by Sichuan Science and Technology Program (No. 2023NSFSC0070), the Opening Project of Sichuan Province University Key Laboratory of Bridge Non-destruction Detecting and the Engineering Computing (No. 2023QYJ06), and Innovation Team Program of Sichuan University of Science and Engineering (No. SUSE652B002).
Acknowledgments
Many thanks to Prof. Simin Yu, Prof. Yong Wang, and Prof. Xiaoyuan Wang for their help in achieving this work.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Chen L, Li CQ, Li C. Security measurement of a medical communication scheme based on chaos and dna coding. J Vis Commun Image Representation (2022) 83:103424. doi:10.1016/j.jvcir.2021.103424
2. Wang S, Peng Q, Du B. Chaotic color image encryption based on 4d chaotic maps and dna sequence. Opt Laser Technology (2022) 148:107753. doi:10.1016/j.optlastec.2021.107753
3. Wen H, Lin Y. Cryptanalyzing an image cipher using multiple chaos and dna operations. J King Saud University-Computer Inf Sci (2023) 35:101612. doi:10.1016/j.jksuci.2023.101612
4. Zhang Z, Tang J, Zhang F, Ni H, Chen J, Huang Z. Color image encryption using 2d sine-cosine coupling map. IEEE Access (2022) 10:67669–85. doi:10.1109/access.2022.3185229
5. Huang Z, Cheng S, Gong L, Zhou N. Nonlinear optical multi-image encryption scheme with two-dimensional linear canonical transform. Opt Lasers Eng (2020) 124:105821. doi:10.1016/j.optlaseng.2019.105821
6. Wu C, Hu K, Wang Y, Wang J, Wang QH. Scalable asymmetric image encryption based on phase-truncation in cylindrical diffraction domain. Opt Commun (2019) 448:26–32. doi:10.1016/j.optcom.2019.05.009
7. Li X, Li C, Lee I-K. Chaotic image encryption using pseudo-random masks and pixel mapping. Signal Process. (2016) 125:48–63. doi:10.1016/j.sigpro.2015.11.017
8. Supreeti K, Sukanta D. A study of chaos in non-uniform cellular automata. Commun Nonlinear Sci Numer Simulation (2019) 76:116–31. doi:10.1016/j.cnsns.2019.04.020
9. Chai X, Zheng X, Gan Z, Han D, Chen Y. An image encryption algorithm based on chaotic system and compressive sensing. Signal Process. (2018) 148:124–44. doi:10.1016/j.sigpro.2018.02.007
10. Gong L, Qiu K, Deng C, Zhou N. An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt Laser Technology (2019) 115:257–67. doi:10.1016/j.optlastec.2019.01.039
11. Chen Y, Lu T, Wang Q. The chaotic properties and circuit design of a generalized high-dimensional integer-domain system. Chaos, Solitons and Fractals (2024) 181:114610. doi:10.1016/j.chaos.2024.114610
12. Li C, Gao Y, Lei T, Li RYM, Xu Y. Two independent offset controllers in a three-dimensional chaotic system. Int J Bifurcation Chaos (2024) 34:2450008. doi:10.1142/s0218127424500081
13. Li Y, Li C, Zhong Q, Liu S, Lei T. A memristive chaotic map with only one bifurcation parameter. Nonlinear Dyn (2024) 112:3869–86. doi:10.1007/s11071-023-09204-0
14. Kong X, Yu F, Yao W, Cai S, Zhang J, Lin H. Memristor-induced hyperchaos, multiscroll and extreme multistability in fractional-order hnn: image encryption and fpga implementation. Neural Networks (2024) 171:85–103. doi:10.1016/j.neunet.2023.12.008
15. Wang X, Zhang X, Gao M, Iu HHC, Wang C. A color image encryption algorithm based on hash table, halbert curve and hyper-chaotic synchronization. Mathematics (2023) 11:567. doi:10.3390/math11030567
16. Yu F, Kong X, Yao W, Zhang J, Cai S, Lin H, et al. Dynamics analysis, synchronization and fpga implementation of multiscroll hopfield neural networks with non-polynomial memristor. Chaos, Solitons and Fractals (2024) 179:114440. doi:10.1016/j.chaos.2023.114440
17. Wang MJ, Gu L. Multiple mixed state variable incremental integration for reconstructing extreme multistability in a novel memristive hyperchaotic jerk system with multiple cubic nonlinearity. Chin Phys B (2024) 33:020504. doi:10.1088/1674-1056/acddd0
18. Matthews R. On the derivation of a chaotic encryption algorithm. Cryptologia (1989) 13:29–42. doi:10.1080/0161-118991863745
19. Alvarez G, Li S. Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos (2006) 16:2129–51. doi:10.1142/s0218127406015970
20. Wang X, Teng L, Qin X. A novel colour image encryption algorithm based on chaos. Signal Process. (2012) 92:1101–8. doi:10.1016/j.sigpro.2011.10.023
21. Wang Q, Yu S, Li C, Lu J, Fang X, Guyeux C, et al. Theoretical design and fpga-based implementation of higher-dimensional digital chaotic systems. IEEE Trans Circuits Syst Regular Pap (2016) 63:401–12. doi:10.1109/tcsi.2016.2515398
22. Huang L, Wang S, Xiang J. A tweak-cube color image encryption scheme jointly manipulated by chaos and hyper-chaos. Appl Sci (2019) 9:4854. doi:10.3390/app9224854
23. Wang X, Su Y, Zhang H, Zou C. A new hybrid image encryption algorithm based on gray code transformation and snake-like diffusion. Vis Computer (2021) 38:3831–52. doi:10.1007/s00371-021-02224-0
24. Gao X, Mou J, Xiong L, Sha Y, Yan H, Gao Y. A fast and efficient multiple images encryption based on single-channel encryption and chaotic system. Nonlinear Dyn (2022) 108:613–36. doi:10.1007/s11071-021-07192-7
25. Alexan W, Elkandoz M, Mashaly M, Azab E, Aboshousha A. Color image encryption through chaos and KAA map. IEEE Access (2023) 11:11541–54. doi:10.1109/access.2023.3242311
26. Chai X, Chen Y, Broyde L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng (2017) 88:197–213. doi:10.1016/j.optlaseng.2016.08.009
27. Wu J, Liao X, Yang B. Image encryption using 2d henon-sine map and dna approach. Signal Process. (2018) 153:11–23. doi:10.1016/j.sigpro.2018.06.008
28. Patel S, Bharath K-P, Kumar R. Symmetric keys image encryption and decryption using 3d chaotic maps with dna encoding technique. Multimedia Tools Appl (2020) 79:31739–57. doi:10.1016/j.cnsns.2019.04.020
29. Liu Q, Liu L. Color image encryption algorithm based on dna coding and double chaos system. IEEE Access (2020) 8:83596–610. doi:10.1109/access.2020.2991420
30. Hua N, Liu H, Xiong X, Wang JL, Liang JQ. A dynamic image encryption scheme based on quantum walk and chaos-induced dna. Quan Eng (2023) 2023:1–15. doi:10.1155/2023/3431107
31. Wu Y, Yang G, Jin H, Noonan JP. Image encryption using the two-dimensional logistic chaotic map. J Electron Imaging (2012) 21:013014. doi:10.1117/1.jei.21.1.013014
32. Ye X, Wang X. Design a novel image encryption algorithm based on a prng with high performance. IEEE MultiMedia (2022) 99:1–11. doi:10.1109/mmul.2022.3232180
33. Lu J, Wu X, Lv J, Kang L. A new discrete chaotic system with rational fraction and its dynamical behaviors. Chaos, Solitons and Fractals (2004) 22:311–9. doi:10.1016/j.chaos.2004.01.010
34. Watson JD, Crick FHC. Molecular structure of nucleic acids: a structure for deoxyribose nucleic acid. Nature (1953) 171:737–8. doi:10.1038/171737a0
35. Lone PN, Singh D, Mir UH. Image encryption using dna coding and three-dimensional chaotic systems. Multimedia Tools Appl (2022) 81:5669–93. doi:10.1007/s11042-021-11802-2
36. Chen X, Mou J, Cao Y, Banerjee S. Chaotic multiple-image encryption algorithm based on block scrambling and dynamic dna coding. Int J Bifurcation Chaos (2023) 33:2350190. doi:10.1142/s0218127423501900
37. Wen H, Lin Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and dna coding. Expert Syst Appl (2024) 237:121514. doi:10.1016/j.eswa.2023.121514
38. Sun S. A novel hyperchaotic image encryption scheme based on dna encoding, pixel-level scrambling and bit-level scrambling. IEEE Photon J (2018) 10:1–14. doi:10.1109/jphot.2018.2817550
39. Xu L, Li Z, Li J, Hua W. A novel bit-level image encryption algorithm based on chaotic maps. Opt Lasers Eng (2016) 78:17–25. doi:10.1016/j.optlaseng.2015.09.007
40. Brindha M, Gounden NA. A chaos based image encryption and lossless compression algorithm using hash table and Chinese remainder theorem. Appl Soft Comput (2016) 40:379–90. doi:10.1016/j.cnsns.2019.04.020
41. Zarebnia M, Pakmanesh H, Parvaz R. A fast multiple-image encryption algorithm based on hybrid chaotic systems for gray scale images. Optik (2019) 179:761–73. doi:10.1016/j.ijleo.2018.10.025
42. Kaur G, Agarwal R, Patidar V. Chaos based multiple order optical transform for 2d image encryption. Eng Sci Technol Int J (2020) 23:998–1014. doi:10.1016/j.jestch.2020.02.007
43. He P, Sun K, Zhu C. A novel image encryption algorithm based on the delayed maps and permutation-confusion-diffusion architecture. Security Commun Networks (2021) 2021:1–16. doi:10.1155/2021/6679288
Keywords: image encryption, chaotic system, DNA computing, logistic mapping, 2D-LFHCM
Citation: Chen Y, Lu T, Chen C and Xiang Y (2024) A novel image encryption method based on improved two-dimensional logistic mapping and DNA computing. Front. Phys. 12:1469418. doi: 10.3389/fphy.2024.1469418
Received: 23 July 2024; Accepted: 19 August 2024;
Published: 09 September 2024.
Edited by:
Fei Yu, Changsha University of Science and Technology, ChinaReviewed by:
Jun Mou, Dalian Polytechnic University, ChinaLi Xiong, Hexi University, China
Mengjiao Wang, Xiangtan University, China
Copyright © 2024 Chen, Lu, Chen and Xiang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Tianxiu Lu, bHViZWVsdHhAMTYzLmNvbQ==
 Yuanlin Chen1
Yuanlin Chen1 Tianxiu Lu
Tianxiu Lu