- School of Information Engineering, East China University of Technology, Nanchang, China
The problem of robust predictability against sensor attacks is investigated. The objective of a diagnoser is to predict the occurrence of a critical event of a discrete event system (DES) under partial observation. An attacker may rewrite the diagnoser observation by inserting fake events or erasing real events. Two novel structures, namely, real diagnoser and the fake diagnoser, are constructed based on the diagnoser of the system. We compute the hybrid diagnoser as the parallel composition of the real diagnoser and the fake diagnoser. The hybrid diagnoser can be used to verify if a critical event of the system is robustly predictable when an attacker tampers with the diagnoser observation.
1 Introduction
Suppose that a plant is modeled by a discrete event system (DES) under partial observation, predictability is a property that describes if a diagnoser can predict the occurrence of a critical event (either observable or unobservable) according to its observation of the system. As the system and the diagnoser are connected via a network, a malicious attacker may corrupt such a communication channel with the insertion of fake events and the deletion of real events that have happened in the system. Therefore, the problem of robust predictability against sensor attacks is addressed. It characterizes the ability of a diagnoser to predict the occurrence of a critical event, even if an attacker may tamper with its observation.
Genc and Lafortune [1] proposed the problem of predictability in the centralized case, and Kumar and Takai [2] considered this problem in the decentralized case. From this point, many studies have focused on this topic in different contexts and problem settings. Takai and Kumar [3, 4] considered the problem of failure prognosis with communication delays. In [5–7], the problem of predictability is studied in the context of stochastic DESs. Benmessahel et al. [8] investigated the problem of predictability in fuzzy DESs. Yin and Li [9] studied the problem of reliable decentralized fault predictability. They supposed that only partial local prognostic decisions are accessible to the coordinator. In [10], the authors showed how to use one prognoser to predict the occurrence of any failure for a set of models. Xiao and Liu [11] considered the problem of robust fault prognosis against loss of observations, where some observable events may become unobservable because of sensor failures. Finally, the problem of predictability is investigated in [12–14] in the framework of Petri nets.
The notion of diagnosability was first proposed in [15]. We assume that a DES contains an unobservable fault event. A fault event is said to be diagnosable if we can determine its occurrence within a limited delay. We point out that if the property of predictability is stronger than that of diagnosability, i.e., if an event is predictable, then this event is also diagnosable.
The problem of robust codiagnosability against Denial-of-Service and deception attacks has been considered in [16]. The authors assume that an attacker can insert fake packages into the network that transmits the sensor readings such that delays and loss of observations may occur. They construct a new diagnoser to verify the property of robust codiagnosability. In [17], the problem of robust codiagnosability against sensor attacks under cost constraint is proposed. The considered attacks include symbol insertion, symbol erasure, and symbol replacement attacks. They assumed that each attack action consumes a certain amount of cost. They developed a strategy to verify the robust codiagnosability against an attacker with a bounded total cost.
Mainly inspired by [16, 17] that considered the problem of robust diagnosability in DESs subject to cyberattacks, we propose the problem of robust predictability in DESs subject to sensor attacks. To the best of the author’s knowledge, this problem has not been considered in the framework of DESs. We finally mention that in [18], a structure named joint estimator is addressed to solve the problem of joint state estimation under attacks. This is a general structure that can be used to consider a set of problems in DESs subject to sensor attacks. In this work, we extend such a structure to solve the problem of robust predictability against sensor attacks.
In Section 2, the automata model and the notions of predictability and diagnoser are given. In Section 3, the problem considered in this study is presented. In Section 4, the real diagnoser is computed. It characterizes the real evolution of the diagnoser subject to sensor attacks. In Section 5, the fake diagnoser is constructed. It characterizes the fake evolution of the diagnoser subject to sensor attacks. In Section 6, the hybrid diagnoser is computed. It allows us to test if a critical event is robustly predictable. Section 7 summarizes the main results of this work, and the possible future work is also pointed out.
2 Preliminaries
Let E be an alphabet and L a language defined over E*. The prefix closure of L is defined by
A deterministic finite-state automaton (DFA), denoted by G, is a four tuple G = {X, E, δ, x0}, where X is a set of states; E is a finite set of events; δ: X × E → X is the transition function and can be extended from the domain X × E to the domain X × E*, that is, δ(x, ɛ) ≔ x, and δ*(x, σe) ≔ δ(δ*(x, σ), e), where e ∈ E, σ ∈ E*, and x0 is the initial state. The generated language of G is defined by L(G) = {σ ∈ E* | δ*(x, σ) is defined}. The set of active events at state x of G is defined by ΓG(x) = {e ∈ E | δ(x, e) is defined}.
A set of states {x1, x2, …, xn}⊆ X and a word σ = e1e2…en ∈ E* form a cycle if δ(xi, ei) = xi+1, i = 1, 2, …, n − 1, and δ(xn, en) = x1. The accessible part of G with respect to state x is defined as Ac(G, x) = (Xac, E, δac, x0), where Xac = {x′ ∈ X | (∃σ ∈ E*) δ*(x, σ) = x′},
Due to the lack of observability in the system, E is divided into the set of observable events Eo and the set of unobservable events Euo. The natural projection on Eo is denoted as
Definition 1. [1] Consider a prefix-closed and live language L on alphabet E. An event f is said to be predictable with respect to P if
∀u ∈ L such that P(u) = P(t), f∉u. ∀v ∈ L/u such that |v|≥ n ⇒ f ∈ v.
In plain words, an event f is predictable if it holds that once the observation P(t) is produced, f will necessarily occur within n steps, where t is a normal prefix of a word σ that ends with f.
Definition 2. [1] Let G = (X, E, δ, x0) be a plant and f an event that needs to be predicted. The diagnoser is a DFA, denoted as Dg = (B, Eo, δd, b0), where
• B ⊆ 2X×{N,F}, for example, b = {(x1, l1), …, (xn, ln)}, and x1, x2…, xn ∈ X;
• δd: B × Eo → B, for example, if ∃e ∈ Eo such that δd(b, e) = b′, where b = {(x1, l1), …, (xm, lm)} and
If a state of the diagnoser is labeled N, it indicates that event f has not happened when the current state is reached. If a state of the diagnoser is labeled F, it implies that event f has happened when the current state is reached. By convention, the unobservable reach is not included in a diagnoser state.
Definition 3. [1] In the diagnoser Dg = (B, Eo, δd, b0),
• We define Bn = {b = {(x1, l1), …, (xn, ln)} ∈ B | ∀ li ∈ {l1, …, ln}, li = N} as the set of normal states of Dg.
• We define Bc = {b = {(x1, l1), …, (xn, ln)} ∈ B | ∀ li ∈ {l1, …, ln}, li = F} as the set of certain states of Dg.
• We define Buc = {b = {(x1, l1), …, (xn, ln)} ∈ B | ∃ li, lj ∈ {l1, …, ln}, li = N, lj = F} as the set of uncertain states of Dg.
• We denote by Bd the set of normal states with an instantaneous continuator, which is not normal, that is, Bd = {b ∈ Bn | (∃e ∈ Eo) δd(b, e)∉Bn}.
In other words, a state b ∈ B is normal if all the labels within it are N; a state b ∈ B is certain if all the labels within it are F; and a state b ∈ B is uncertain if there exist labels N and F within it.
Theorem 4. [1] Let G be a plant and Dg = (B, Eo, δd, b0) its diagnoser. An event f is predictable if and only if for all bd ∈ Bd, in the accessible part of the diagnoser Ac(Dg, b), all cycles are cycles of certain states.
3 Problem formulation
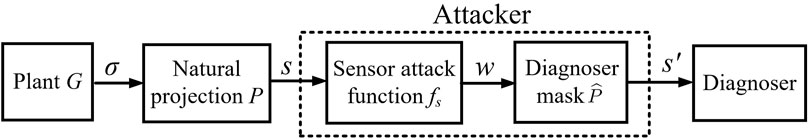
Let G = (X, E, δ, x0) be a plant modeled by a DFA. As shown in Figure 1, if the word σ ∈ E* is generated by G, the observation s = P(σ) may be corrupted by an attacker. Then, the diagnoser predicts the occurrence of a critical event in accordance with the corrupted observation s′. It should be noted that the internal structure of the attacker within the dotted lines will be discussed later.
Suppose that an attacker can only tamper with a subset of events of G, we call this subset the set of compromised events Ecom. We divide Ecom into two subsets, that is, Ecom = Eins ∪ Eera, where Eins is the set of events that may be inserted into the diagnoser observation, and Eera is the set of events that may be deleted from the diagnoser observation. The sets Eins and Eera may contain common events.
To make a distinction between the attacker’s action from the original behavior of G, we define two new sets of events. We denote by E+ the set of inserted events, defined as E+ = {e+ | e ∈ Eins} [19]. We denote by E− the set of erased events, defined as E− = {e− | e ∈ Eera} [19]. If e+ ∈ E+ happens, it indicates that an attacker inserts the fake symbol e ∈ Eins into the diagnoser observation. If e− ∈ E− happens, it indicates that an attacker erases the real symbol e ∈ Eera from the diagnoser observation. Finally, we denote by Ea the attack alphabet, defined as Ea = Eo ∪ E+ ∪ E−. We point out that the three subsets Eo, E+, and E− are disjoint.
Definition 5. Let G be a plant and Ecom = Eins ∪ Eera the set of compromised events. An attacker is defined by a sensor attack function
(1)
(2) ∀se ∈ P[L(G)]:
Condition (1) means that a word in
Let G be a plant. We denote by L(fs, G) the attack language, defined by
Definition 6. The real mask
In plain words, the real mask transforms events in Ea into real events that have happened in the system. As e− means an erased event that has happened in the system, e− is transformed into the corresponding event e ∈ Eo. e+ is neglected because it is a fake event.
Definition 7. The diagnoser mask
In simple words, the diagnoser mask characterizes how the diagnoser observes events in Ea. Namely, the diagnoser cannot distinguish the real event e ∈ Eo from the inserted event e+ ∈ E+, and it cannot observe erased events in E−.
As shown in Figure 1 within the dotted lines, the observation s ∈ Eo is corrupted into the attack word
In this study, let G be a plant. The following two assumptions are made:
1) The generated language L(G) is live.
2) In G, there does not exist a cycle that consists of unobservable events only.
Assumption 1) is made for the sake of simplicity. Assumption 2) guarantees that plant G does not generate unobservable words with infinite length.
Definition 8. Let G be a plant that satisfies Assumption 1) and Assumption 2). An event f is robustly predictable with respect to P if
In Definition 8, let t be a normal prefix of a word σ that ends with f. We use t to find all the attack words
We point out that, for each attack word w, we distinguish the observations
4 Real diagnoser
The real diagnoser Dr describes the real evolution of the diagnoser in accordance with the attack alphabet Ea. Namely, the real diagnoser changes its states the same way in terms of e ∈ Eera and the corresponding events e−; the real diagnoser does not change its states when the fake event e+ ∈ E+ happens.
Definition 9. Let G = (X, E, δ, x0) be a plant and Dg = (B, Eo, δd, b0) the diagnoser. The real diagnoser is a DFA Dr = (B, Ea, δr, b0), and its transition function δr satisfies the following:
The construction of the real diagnoser can be explained as follows: first, we set the transition function of the real diagnoser Dr equal to the transition function of the diagnoser Dg. Then, each time there is a transition labeled e ∈ Eera, we add a transition labeled e−. Finally, for each event in Eins, for each state of Dr, we add a self-loop labeled e+.
We point out that the real diagnoser Dr is similar to the attacker observer constructed by Algorithm 1 in [18]. Although the input of Algorithm 1 is the observer of G, here we replace it with the diagnoser of G.
Example 10. As sketched in Figure 2A, let G be the plant, Eo = {a, b}, and Euo = {f}. Assume that f is the event that needs to be predicted. The diagnoser Dg = (B, Eo, δd, b0) is sketched in Figure 2B.
Let Eins = Eera = {a}. The real diagnoser is shown in Figure 3. We add a transition δr({0N}, a−) = {1N} in Dr because there exists a transition δd({0N}, a) = {1N} such that e ∈ Eera in Dg. Self-loops labeled a+ are added at all the states of Dr because a ∈ Eins.
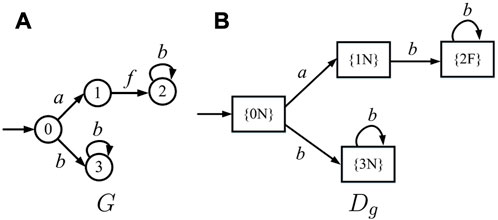
FIGURE 2. (A) Plant G and (B) diagnoser Dg in Example 10.
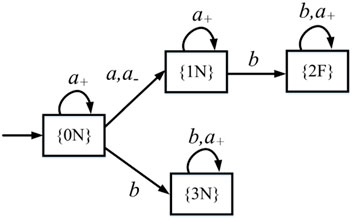
FIGURE 3. Real diagnoser Dr in Example 10.
Proposition 11. Let G be the plant, Dg = (B, Ea, δ, b0) its diagnoser, and Dr = (B, Ea, δr, b0) the real diagnoser.
(i)
(ii) ∀s L(Dg),
Proof. The proof is neglected because it is the same as the proof of Proposition 1 in [18]. In simple words, item 1) means that the real diagnoser generates the union of all the attack languages. Item 2) indicates that the state arrived in Dr by implementing
5 Fake diagnoser
The fake diagnoser Df describes the fake evolution of the diagnoser in accordance with the attack alphabet Ea. Namely, the fake diagnoser changes its states the same way in terms of e ∈ Eins and the corresponding events e+ because it cannot distinguish the real event of the plant e from the fake event e+. The fake diagnoser does not change its states in case of the occurrence of e− ∈ E− because it cannot observe the erased event e−. We add a new state b∅ in Dr. The diagnoser knows that the plant is under attack when this state is reached.
Definition 12. Let G = (X, E, δ, x0) be a plant and Dg = (B, Eo, δd, b0) the diagnoser. The fake diagnoser is a DFA Df = (Bf, Ea, δf, b0) such that Bf = B ∪ b∅, and its transition function δf satisfies the following:
The construction of the fake diagnoser can be explained as follows: first, we set the transition function of Df equal to the transition function of the diagnoser Dg. Then, each time there is a transition labeled e ∈ Eins, we add a transition labeled e+ ∈ E+. Self-loop labeled events in E− are added at all the states of Df. Finally, for each event in Ea and each state in B, we set δf(b, ea) = b∅ for all the undefined transitions. Note that state b∅ has no input and output arcs.
We point out that the fake diagnoser Df is similar to the operator observer computed by Algorithm 2 of [18]. Although the input of Algorithm 2 is the observer of G, here we replace it with the diagnoser of G.
Example 13. Recall plant G with its diagnoser Dg in Example 10. Suppose that Eins = Eera = {a}. Figure 4 shows the fake diagnoser.
First, we add a transition δr({0N}, a+) = {1N} in Df as there is a transition δd({0N}, a) = {1N} such that e ∈ Eins in Dg. Then, for all the states of Df, self-loops labeled a− are added because a ∈ Eera. Finally, all the undefined transitions lead to the state b∅.
The following definitions are given to formalize the generated language of the fake diagnoser Df.
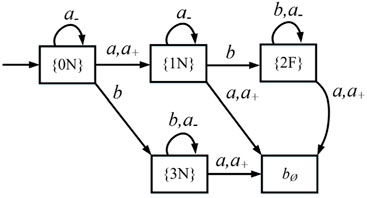
FIGURE 4. Fake diagnoser Df in Example 13.
Definition 14. Consider a plant G with the fake diagnoser Df.
• A sensor attack function fs is stealthy if
• The set of stealthy words is defined as
• The set of exposing words is defined as
According to Definition 14, fs is stealthy if the attack words in
Proposition 15. Let G be the plant, Dg = (B, Eo, δd, b0) the diagnoser, and Df = (B, Ea, δf, b0) the fake diagnoser.
(i) L(Df) = Ws ∪ We;
(ii) ∀w ∈ L(Df): if w ∈ Ws, then
Proof. The proof is ignored because it is the same as the proof of Proposition 2 in [18]. In plain words, item (i) implies that the language of the fake diagnoser equals the union of Ws and We. Item (ii) means that the state arrived in Df by implementing
6 Hybrid diagnoser
The notion of the hybrid diagnoser is given on the basis of the real diagnoser and fake diagnoser.
Definition 16. Let G = (X, E, δ, x0) be a plant, Dr = (B, Ea, δr, b0) the real diagnoser, and Df = (Bf, Ea, δf, b0) the fake diagnoser. The hybrid diagnoser Dh = (R, Ea, δh, r0) is defined as the parallel composition of Dr and Dh, that is, Dh = Dr‖Df, where
• R = (b, bf) ⊆ 2X×{N,F}× 2X×{N,F};
• δh[(b, bf), e] = [δr(b, e), δf(bf, e)] if
• the initial state is r0 = (b0, b0).
Now, we investigate the complexity of building the hybrid diagnoser Dh. Let G = (X, E, δ, x0) be a plant. Its diagnoser Dg is built in 2|X| steps. In accordance with Definition 9, the real diagnoser Dr contains at most 2|X| states. In accordance with Definition 12, the fake diagnoser Df contains at most 2|X| + 1 states. As Dh = Dr‖Df, the computational complexity to build Dh is O(2|X|⋅ 2|X|).
Example 17. Recall plant G in Example 10. The hybrid diagnoser Dh = Dr‖Df is sketched in Figure 5, where Dr (Df) is sketched in Figure 3 (Figure 4).
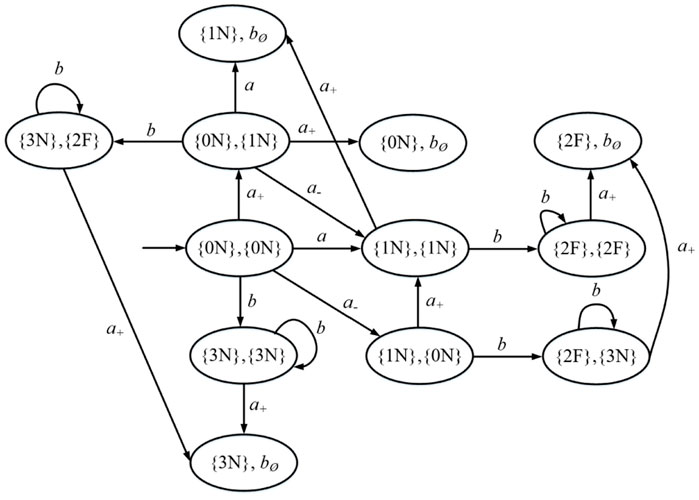
FIGURE 5. Hybrid diagnoser Dh in Example 17.
Definition 18. Let G be the plant, and Dh = (R, Ea, δh, r0) be the hybrid diagnoser:
• We define
• We define
• We define
• We denote by Rd the set of normal states with an instantaneous continuator, which is not normal, that is, Rd = {r ∈ Rn | (∃ea ∈ Ea) δh(r, ea)∉Rn}.
We point out that Definition 18, defined in hybrid diagnoser Dh, is the counterpart of Definition 3, defined in the diagnoser Dg.
Theorem 19. Let G be a plant, Dg = (B, Eo, δd, b0) the diagnoser, and Dh = (R, Ea, δh, r0) the hybrid diagnoser.
(a)
(b) ∀s ∈ P[L(G)],
(i) If w ∈ Ws, then
(ii) If w ∈ We, then
Proof. The proof is neglected because it is the same as the proof of Theorem 1 in [18]. In other words, item (a) implies that the language of the hybrid diagnoser Dh equals the intersection of the language of the real diagnoser and the language of the fake diagnoser.
Item (b) means that (i) if w ∈ Ws and the state (b, bf) is arrived in Dh by implementing w = fs(s), then the first element of this state equals the state arrived in the diagnoser Dg by implementing
Proposition 20. Let G be a plant and Dh = (R, Ea, δh, r0) the hybrid diagnoser. In Dh, we suppose that a set of states {r1, r2, …, rn}⊆ R and a word
Proof. Proposition 20 means that in a cycle of Dh, if a certain state exists, then all the other states in this cycle are certain. The proof follows from the fact that the label F propagates; once a state is labeled as a certain state, all the states that are reachable from this state are also certain.
Proposition 21. Let G be a plant, Dg = (B, Eo, δd, b0) the diagnoser, and Dh = (R, Ea, δh, r0) the hybrid diagnoser. In Dh, if a set of states {(b1, bf1), (b2, bf2), …, (bn, bfn)}⊆ R and a word
Proof. Assume that, in the hybrid diagnoser Dh, a set of states {(b1, bf1), (b2, bf2), …, (bn, bfn)}⊆ R and a word
As Dh = Dr‖Df, a set of states {b1, , b2, …, bn}⊆ B and the word
In accordance with Theorem 19, if w ∈ Ws, then
Note that as state b∅ has no output arcs in the fake diagnoser Df, then in Dh, the cycle does not contain the state whose second element is b∅. Therefore, the case of w ∈ We is not considered when we use the results of Theorem 19. For the same reason, we exclude this case in the proof of Theorem 22.
Theorem 22. Let G = (X, E, δ, x0) be a plant and Dh = (R, Ea, δh, r0) the hybrid diagnoser. An event f is robustly predictable if and only if, for all rd ∈ Rd, in the accessible part of the hybrid diagnoser Ac(Dh, rd), all cycles are cycles of certain states.
Proof. (If) Assume that for all rd ∈ Rd, in Ac(Dh, rd), all cycles are cycles of certain states. Consider a word σ ∈ Ψ(f, L(G)) such that δ*(x0, σ) = x. Let σuoeo ∈ L/σ such that eo ∈ Eo and δ*(x, σuoeo) = x′.
Consider a word w such that
a) If
b) If
In any case, we can conclude that r′ ∈ Ruc ∪ Rc. As δh(r, eo) = r′, the following two cases are possible:
1) If r ∈ Rn, it means that r ∈ Rd because δh(r, eo) = r′ ∈ {Ruc ∪ Rc}. Let σ = tf, where t ∈ E*. ∀u ∈ L(G) such that
2) If r ∈ Ruc ∪ Rc, then we can always find a state r″ ∈ Rd such that state r is reachable from state r″. As a result, the proof for case 2) is reduced to the proof for case 1) by replacing r with r″.
(Only if) Assume that event f is robustly predictable, and there exists rd ∈ Rd such that Ac(Dh, rd) has a cycle that contains a state that is uncertain.
According to Proposition 20, in Ac(Dh, rd), as there exists a state that is uncertain in the cycle, then none of the states is certain in this cycle. In accordance with Proposition 21, as there exists a cycle where all the states are uncertain in Ac(Dh, rd), there exists a cycle where all the states are labeled N in plant G.
Suppose that, in Dh,
Example 23. Recall plant G in Example 10, where Eo = {a, b} and Euo = {f}. Assume that event f needs to be predicted. Let Eins = {a} and Eera = {a}.
In the diagnoser Dg in Figure 2B, state {1N} ∈ Bd. As Ac(D, {1N}) only contains one cycle (self-loop) labeled b at state {2F}, that is a certain state, according to Theorem 4, event f is predictable when no attack occurs.
In the hybrid diagnoser Dh visualized in Figure 5, states ({0N}, {1N}), ({1N}, {0N}), ({1N}, {1N}) ∈ Rd. As Ac[Dh, ({0N}, {1N})] includes a cycle labeled b at state ({3N}, {2F}), that is not a certain state, and Ac[Dh, ({1N}, {0N})] contains a cycle labeled b at state ({2F}, {3N}), that is not a certain state, in accordance with Theorem 22, event f is not robustly predictable when the attack occurs.
7 Conclusion
We consider the problem of robust predictability against sensor attacks. Based on a novel structure called hybrid diagnoser, an approach to test robust predictability is provided.
In the future, on one hand, as the construction of the diagnoser has exponential complexity, we intend to construct a verifier, which has polynomial complexity, to test robust predictability. On the other hand, we will try to extend the approach proposed in this work to the decentralized case.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author contributions
QZ writes the manuscript. The author agrees to be accountable for the content of the work.
Funding
This work was supported by the Scientific Research Startup Fund of East China University of Technology.
Conflict of interest
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Genc S, Lafortune S. Predictability of event occurrences in partially-observed discrete-event systems. Automatica (2009) 45:301–11. doi:10.1016/j.automatica.2008.06.022
2. Kumar R, Takai S. Decentralized prognosis of failures in discrete event systems. IEEE Trans Autom Control (2010) 55:48–59. doi:10.1109/TAC.2009.2034216
3. Takai S, Kumar R. Distributed failure prognosis of discrete event systems with bounded-delay communications. IEEE Trans Autom Control (2012) 57:1259–65. doi:10.1109/TAC.2011.2173419
4. Takai S, Kumar R. Distributed prognosis of discrete event systems under bounded-delay communications. In: Proc 48h IEEE Conf Decis Control, & 28th Chinese Control Conf; December 2009; Shanghai, China. IEEE (2009). p. 1235–40. doi:10.1109/CDC.2009.5399980
5. Chang M, Dong W, Ji Y, Tong L. On fault predictability in stochastic discrete event systems. Asian J Control (2013) 15:1458–67. doi:10.1002/asjc.748
6. Chen J, Kumar R. Stochastic failure prognosability of discrete event systems. IEEE Trans Autom Control (2015) 60:1570–81. doi:10.1109/TAC.2014.2381437
7. Liao H, Liu F, Wu N. Robust predictability of stochastic discrete-event systems and a polynomial-time verification. Automatica (2022) 144:110477. doi:10.1016/j.automatica.2022.110477
8. Benmessahel B, Touahria M, Nouioua F. Predictability of fuzzy discrete event systems. Discrete Event Dyn Syst (2017) 27:641–73. doi:10.1007/s10626-017-0256-7
9. Yin X, Li Z. Reliable decentralized fault prognosis of discrete-event systems. IEEE Trans Syst Man Cybern: Syst (2016) 46:1598–603. doi:10.1109/TSMC.2015.2499178
10. Takai S. Robust prognosability for a set of partially observed discrete event systems. Automatica (2015) 51:123–30. doi:10.1016/j.automatica.2014.10.104
11. Xiao C, Liu F. Robust fault prognosis of discrete-event systems against loss of observations. IEEE Trans Autom Sci Eng (2022) 19:1083–94. doi:10.1109/TASE.2021.3049400
12. Ammour R, Leclercq E, Sanlaville E, Lefebvre D. Fault prognosis of timed stochastic discrete event systems with bounded estimation error. Automatica (2017) 82:35–41. doi:10.1016/j.automatica.2017.04.028
13. Yin X. Verification of prognosability for labeled petri nets. IEEE Trans Autom Control (2018) 63:1828–34. doi:10.1109/TAC.2017.2756096
14. You D, Wang S, Seatzu C. Verification of fault-predictability in labeled petri nets using predictor graphs. IEEE Trans Autom Control (2019) 64:4353–60. doi:10.1109/TAC.2019.2897272
15. Sampath M, Sengupta R, Lafortune R, Sinnamohideen K, Teneketzis D. Diagnosability of discrete-event systems. IEEE Trans Autom Control (1995) 40:1555–75. doi:10.1109/9.412626
16. Alves MV, Barcelos RJ, Carvalho LK, Basilio JC. Robust decentralized diagnosability of networked discrete event systems against Dos and deception attacks. Nonlinear Analysis: Hybrid Syst (2022) 44:101162. doi:10.1016/j.nahs.2022.101162
17. Li Y, Hadjicostis CN, Wu N, Li Z. Error- and tamper-tolerant state estimation for discrete event systems under cost constraints. IEEE Trans Autom Control (2023) 1–8. doi:10.1109/TAC.2023.3239590
18. Zhang Q, Seatzu C, Li Z, Giua A. Joint state estimation under attack of discrete event systems. IEEE Access (2021) 9:168068–79. doi:10.1109/ACCESS.2021.3135870
Keywords: discrete event system, automaton, predictability, diagnoser, sensor attack
Citation: Zhang Q (2023) Robust predictability in discrete event systems under sensor attacks. Front. Phys. 11:1185103. doi: 10.3389/fphy.2023.1185103
Received: 13 March 2023; Accepted: 31 March 2023;
Published: 17 April 2023.
Edited by:
Kaijie Xu, University of Alberta, CanadaReviewed by:
Peng Nie, Xidian University, ChinaYihui Hu, Xi’an University of Posts and Telecommunications, China
Jiazhong Zhou, Huaqiao University, China
Copyright © 2023 Zhang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Qi Zhang, emhhbmdxaUBlY3V0LmVkdS5jbg==
 Qi Zhang
Qi Zhang