
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
BRIEF RESEARCH REPORT article
Front. Neurosci., 10 August 2022
Sec. Decision Neuroscience
Volume 16 - 2022 | https://doi.org/10.3389/fnins.2022.878248
This article is part of the Research TopicNeuro-Dynamic Characteristics of Decision-MakingView all 5 articles
Insider threat from individuals operating within an organization presents a significant source of violations of information security. Our previous research has used scalp recorded event-related brain potentials (ERPs) and the Information Security Paradigm (ISP) to identify the neural correlates of decision-making processes related to violations of information security. In the current study, we sought to expand this research by examining the effects of two variables that were drawn from the broader decision-making literature (i.e., the benefactor and delay of a reward) on ERPs measured in the ISP. In the ISP we varied whether Josh—a hypothetical IT specialist—or a significant other was the benefactor of a violation, and whether the benefit of a violation was received after a short or long delay. The choice data revealed that individuals were less likely to endorse an unethical action than a control action. The electrophysiological data revealed ERPs that differentiated ethical scenarios from control scenarios between 200 and 2,000 ms after onset of the decision prompt, distributed over the occipital, central, and lateral frontal regions of the scalp. These ERPs were insensitive to the benefactor and delay of the reward. In contrast, there was slow wave activity over the frontal-polar region that was sensitive to both variables. The current findings provide evidence for separable neural systems that are either generally related to ethical decision-making in the ISP or are sensitive to the benefactor or delay of a reward resulting from an unethical decision.
In the context of information security, insider threat represents intentional or accidental violations of information security policies that result from the action(s) of a person or persons operating inside of an organization (Balozian and Leidner, 2017; Bailey et al., 2018). Managers of information technology resources recognize insider threat as a significant security concern that is second only to major computer viruses (Ernst and Young, 2010), and instances of insider threat may contribute to 50% of violations of information security (Richardson, 2011). The significance of insider threat has led information system researchers to explore system variables (e.g., the severity of punishment) and personal traits (e.g., self-control or moral belief) that predict violations of information security (Zhang et al., 2009; Vance and Siponen, 2012; Balozian and Leidner, 2017; Luo et al., 2020). Our own research has used event-related brain potentials (ERPs) to explore the neural correlates of ethical decision-making related to insider threat (Hu et al., 2015; West et al., 2019). The current project builds upon this work, by examining the effects of two variables (i.e., the benefactor and delay of a reward) on ERP activity in the Information Security Paradigm (ISP). These variables were drawn from the moral and economic decision-making literatures, as both are important determinants of decision-making and consistently associated with neural recruitment in the anterior frontal regions (D’Argembeau et al., 2007; Mitchell et al., 2010; Kable, 2014).
The ISP (Hu et al., 2015) was developed to explore the neural correlates of decision-making related to information security using ERPs. The measure is founded in more traditional work in information security (Hu et al., 2011), and has also been adapted for use with fMRI (Duan et al., 2021). In the task, individuals are presented with various scenarios and prompts and asked to rate how likely they would be to engage in a given behavior. Control items represent decisions that do not involve an ethical element (e.g., assisting a colleague with a project), while violation items represent decisions that involve an ethical violation related to information security (e.g., unauthorized access of a secure server). Individuals are more likely to endorse (respond Yes) to control items than violation items demonstrating a general preference for avoiding unethical behavior, with this preference being moderated by the severity of the violation (Hu et al., 2015; West et al., 2019).
Studies using ERPs with the ISP reveal that decision-making in the task is associated with modulations of the physiology that differentiate ethical violation items from control items between 200 and 2,000 ms after onset of the decision prompt (Hu et al., 2015; West et al., 2019; West and Cowger, 2021). The earliest effect of an ethical violation on the ERPs reflects a reduction in the amplitude of the posterior N2 component that may result from an inward focus of attention for violation items that limits visual processing of the prompt (West and Cowger, 2021). Between 400 and 2,000 ms the ERPs differentiate ethical items from control items over the lateral frontal, medial central, and lateral central regions of the scalp (Hu et al., 2015; West et al., 2019). These findings indicate that ethical decision making in the ISP is associated with the recruitment of a temporally and spatially distributed neural network, consistent with broader literature on the neural foundation of moral decision-making (Greene et al., 2001; Young et al., 2007; Greene and Young, 2020).
Hu et al. (2015) demonstrated that some of these modulations of the ERPs were sensitive to both the presence and severity of the ethical violation, although the effect of severity was not replicated in a later study (West et al., 2019). The effect of an ethical violation on the longer latency modulations of the ERPs is sensitive to individual differences in self-control and moral beliefs (Hu et al., 2015; West et al., 2019). Consistent with the dual processes account of moral decision-making (Greene et al., 2001, 2008), slow wave activity in the ISP is greater in those with high self-control (Hu et al., 2015; West et al., 2019) and reduced in those with high moral belief (West et al., 2019). These findings converge with behavioral evidence demonstrating that both traits are reliable predictors of decision-making related to information security (Myyry et al., 2009; Siponen et al., 2012; Li et al., 2018).
One issue that remains unclear is whether the ERPs observed in the ISP reflect activity within neural systems that are generally related to ethical decision-making or that contribute to the processing of specific attributes of the ethical dilemma. Given this, the current study had two goals: First, we sought to provide a conceptual replication of our prior research using a new set of materials in the ISP. Second, we sought to broaden our understanding of the neuro-cognitive processes contributing to ethical decision-making in this domain by examining the influence of two independent variables (i.e., the benefactor and delay of a reward) drawn from the broader literature on moral and economic decision making that are relevant in the context of information security (Balozian and Leidner, 2017). We expected the ERPs over the occipital, central, and lateral frontal regions of the scalp to distinguish ethical items from control items. The literature examining the neural foundation of self-referent processing (D’Argembeau et al., 2007; Decety and Porges, 2011) and intertemporal choice (Mitchell et al., 2010) lead to the prediction that the ERPs over the frontal region will be sensitive to the benefactor and delay of a reward.
The behavioral and physiological data used in the analyses are available at osf.io/f9dbv along with the materials for the ISP. Data for forty of the participants reported in this article were included in Kirby et al. (2019). The current work provides an expanded sample and more complete analysis of this dataset.
Seventy individuals enrolled in introductory psychology courses completed the study. The EEG data for two individuals had a high degree of artifact and could not be used, and the behavioral data for one additional participant was lost due to a computer error. Sixty-seven individuals (M = 19.88, SD = 2.80 years of age; Female = 34, Male = 33; White = 47, Asian = 8, Hispanic or Latinx = 6, Black = 2, Indigenous = 2, Other = 2) provided complete and usable data for the study. On average participants had completed M = 1.42, SD = 1.63 years of university coursework.
In the ISP individuals were instructed to respond as if they were Josh, an IT specialist with extensive knowledge of the company’s information systems. The ISP reflected a 3 (Benefactor: Control, Josh, Other) × 2 (Delay of reward: Short, Long) factorial with eight scenarios for each of the six cells of the design. The full set of materials is available online at the open science portal. Control scenarios were items involving a decision that was unrelated to an ethical violation. Josh benefit scenarios involved behaviors wherein he was rewarded for the unethical choice, and Other benefit scenarios involved behaviors wherein a friend, relative or partner was rewarded for his unethical choice. For the Other benefit scenarios, the name and relationship of the Other person was stated in the scenario. In Short delay scenarios, the reward was received after 0–3 months; and for Long delay scenarios, the reward was received after 12–14 months. The 48 scenarios and prompts were presented in a different random order for each individual that was generated by the PsychoPy software. Scenarios were limited to 300 characters and prompts were 22–50 characters. Prompts were posed in the form of a question. The prompts did not mention the benefactor or delay of the reward. Individuals were given an unlimited amount of time to read the scenario and then pressed the spacebar to view the prompt. A fixation (+) was presented for 500 ms between the scenario and prompt. The response time and EEG data were time locked to the onset of the prompt (c.f., Figure 1; West et al., 2019). Individuals responded with a four-point scale (No, Likely No, Likely Yes, Yes) using the C-V-B-N keys on the keyboard. Participants were instructed to rest their fingers on the keys during the trials to reduce movement artifacts. The scenarios and prompts were presented in white font on a black ground and were centered on the screen with the text being left justified.
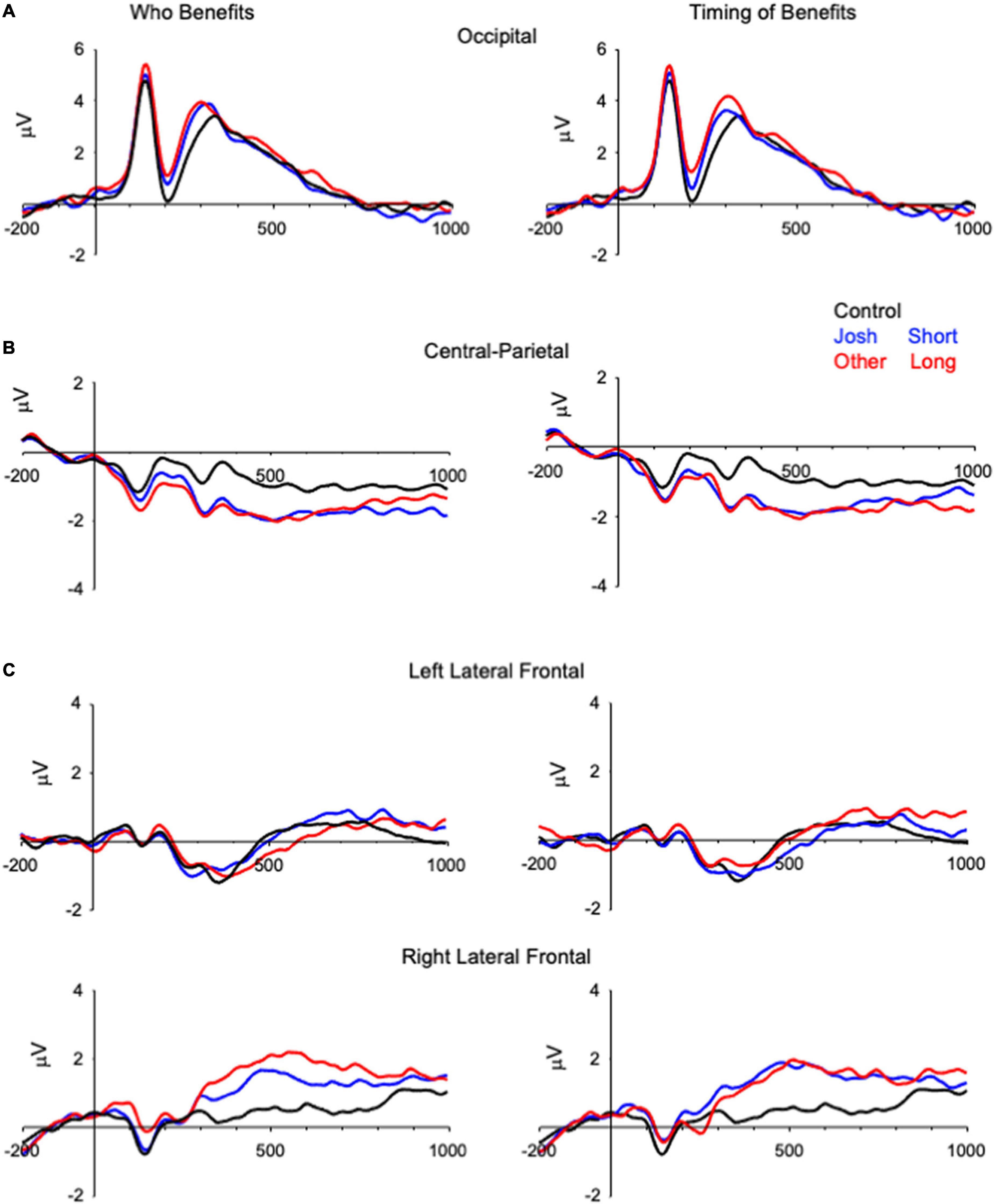
Figure 1. Grand-averaged ERPs demonstrating differences in the physiology between the two types of trials (i.e., ethical vs. control) that are averaged across the electrodes included in the analyses (e.g., for the N2 the plotted electrode is the average of O1, Oz, O2). The left side of the figure plots Control, Josh, and Other items, and the right side of the figure plots Control, Short and Long delay items. (A) N2, (B) central-parietal negativity, and (C) right frontal-temporal positivity from −200 ms before onset of the prompt to 1,000 ms after onset of the prompt. The y-axis represents onset of the prompt and the minor x-axis tick marks represent 100 ms increments.
Upon arriving at the laboratory individuals were given a brief overview of the procedure and signed informed consent was obtained. Individuals then completed a demographic survey and several questionnaires measuring individual differences related to self-control, moral foundations, media exposure, pathological gaming, and grit. Following completion of the scales, individuals were fitted with a 32 electrode actiCAP and completed the ISP, a modified version of the moral foundations task, and a picture rating task while EEG was recorded. Then the EEG cap was removed, individuals were debriefed, and compensated with either course credit or $15.
The EEG was recorded at 500 Hz with a 32 channel actiCHamp system using the Brain Vision Recorder Software and a standard actiCAP with electrodes CP5-CP6 replaced with active electrodes located below the eyes. The electrodes were grounded to Fpz and referenced to Cz during recording. The EEG data were bandpass filtered between 0.1 and 30 Hz using an IIR filter (ERPLAB 5.1.1.0; Lopez-Calderon and Luck, 2014) and referenced to an average reference following the correction of ocular artifacts (blinks and saccades) using ICA EEGLAB (13.6.5b) (Delorme and Makeig, 2004). Trials including other artifacts were rejected before averaging using a ± 100 μV threshold. ERPs were averaged for Control, Josh benefit, Other benefit, Short delay, or Long delay items from −200 to 2,000 ms around onset of the prompt. Measures of mean voltage were made using the measurement tool in ERPLAB.
The effects of Benefactor and Delay of Reward on the ERPs were examined in a set of 2 or 3 factor ANOVAs comparing the ERPs for Control, Josh or Other benefit items, or Control, Short or Long delay items, while collapsing across the other independent variable. Hemisphere was included as a factor in analyses when lateralized ERPs were expected based upon previous research, and electrodes and measurement epochs included in the analyses were based upon previous research with the ISP (Hu et al., 2015; West et al., 2019; West and Cowger, 2021). Region was included in one of the exploratory analyses based upon the pattern observed in the ERP data. The a priori analyses included: N2 (O1-Oz-O2; 200–300 ms), left frontal temporal (T8-F8-FT10/T7-F7-FT9 400–800 ms), central-parietal negativity (Cz-Pz-CP1-CP2, 300–600 ms), central-slow wave (FC2-C4-CP2/C3-C3-CP1, 400–1,800 ms). The exploratory analyses included: anterior frontal region for Benefactor (Fp1-Fp2, F3-F4, 800–1,600 ms), and anterior frontal for Delay (Fp1-Fp2, FT9-FT10). We report inferential statistics for the main effect of condition and the condition by hemisphere/region interaction where relevant; the main effect of electrode is not reported as this effect simply captures differences in amplitude across electrodes that are independent of condition.
To establish the reliability of the ISP we estimated Cronbach’s α for the Control, Josh and Other benefit items. Reliability for Control items was modest (α = 0.63, best = 0.64) and dropping any of the individual items did not result in improvement. For Josh benefit (α = 0.91, best = 0.91) and Other benefit (α = 0.88, best = 0.90) items the reliability was high, with one item (Other short 2) being negatively related to the remaining Other benefit items. These data indicate that the ISP demonstrates acceptable internal consistency, and that future work could focus on refining a subset of the items.
The behavioral data are presented in Table 1. Choice for the Josh items was significantly correlated with choice for the Other items (r = 0.80, p < 0.001). In contrast, choice for the Control items was not significantly correlated with either the Josh (r = 0.07, p = 0.57) or Other (r = 0.18, p = 0.14) items. These findings are consistent with West et al. (2019) in demonstrating that ethical violation items and control items may reflect different constructs.
A pair of 3 (Benefactor: Control, Josh, Other) × 2 (Delay: Short or Long) ANOVAs was used to examine the behavioral data. For the choice data, the main effect of Benefactor was significant, F(2, 132) = 269.35, p < 0.001, η2G = 0.58, with individuals being more likely to say yes for Control items than Josh or Other items; the main effect of Delay was significant, F(1, 66) = 7.97, p = 0.006, η2G = 0.006, with individuals being more likely to say yes for the Long delay items; and the main effects were qualified by an interaction, F(2, 132) = 20.49, p < 0.001, η2G = 0.027. A simple main effects test revealed that the effect of Delay was significant for Josh, F(1, 66) = 43.94, p < 0.001, and possibly Other, F(1, 66) = 3.99, p = 0.05, items, but not for Control items, F < 1.00.
For the response time data, the main effect of Benefactor was not significant, F < 1.00; the main effect of Delay was significant, F(1, 66) = 5.59, p = 0.021, η2G = 0.006, with individuals taking longer to respond for the Long delay items; and the interaction was significant, F(2, 132) = 6.73, p = 0.002, η2G = 0.014. A simple main effect test revealed that response time was slower for Long delay than Short delay items when Josh was the benefactor, while the effect of Delay was not significant for the Other, F < 1.00, or Control, F(1, 66) = 1.02, p = 0.32, items.
A subset of the ERP data is presented in Figures 1, 2. Consistent with previous research (Hu et al., 2015; West et al., 2019), these data reveal modulations of the ERPs that distinguish ethical from control items between 200 and 2,000 ms after onset of the prompt. These data also reveal slow wave activity over the anterior frontal region that was sensitive to the benefactor and delay of the reward (Figures 2B,C).
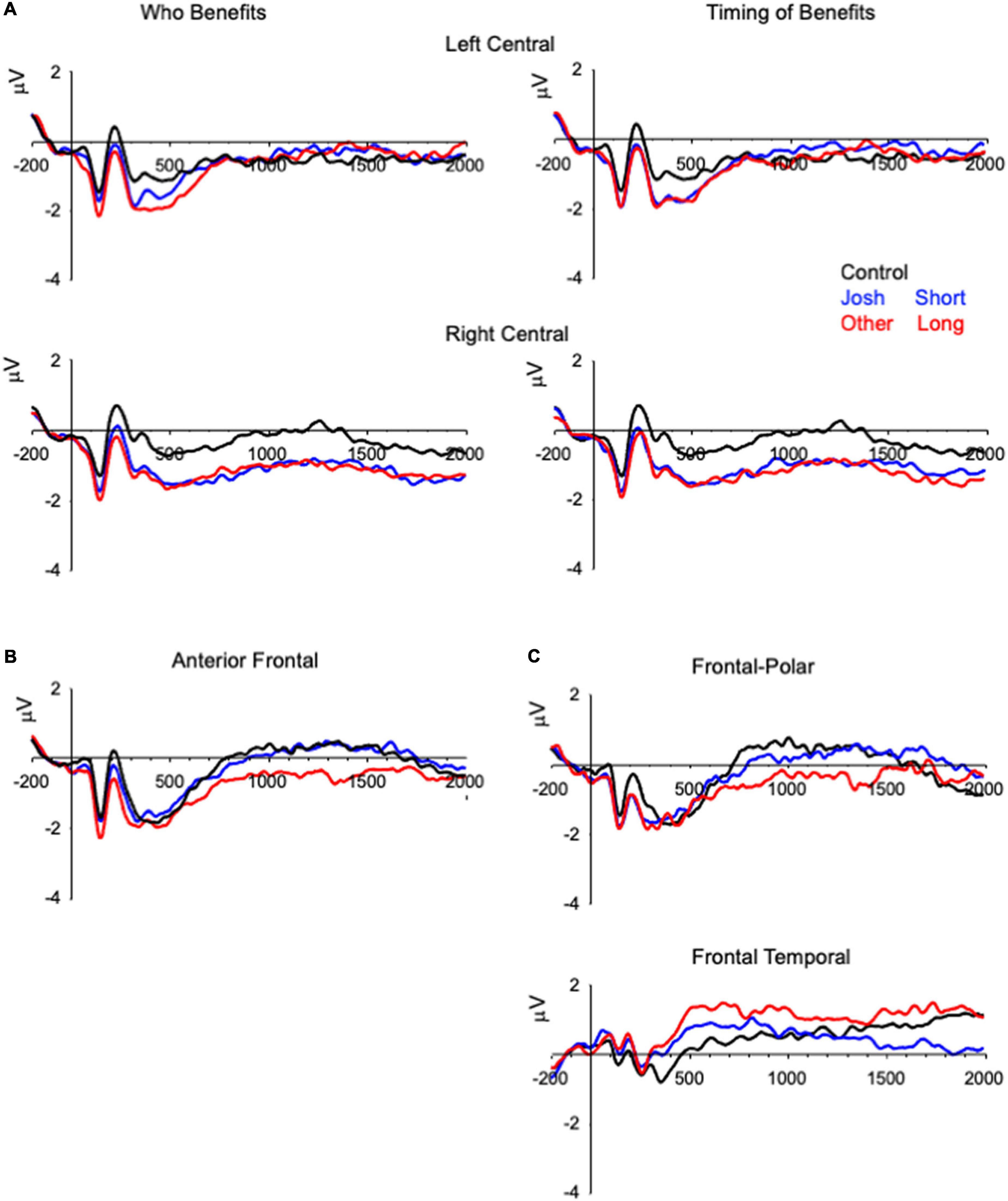
Figure 2. Grand-averaged ERPs demonstrating differences in the physiology between the two types of trials (i.e., ethical vs. control) that are averaged across the electrodes included in the analyses. (A) The right central slow wave differentiating control items from ethical violation items, (B) anterior frontal slow wave differentiating other items from Josh and control items, and (C) the frontal-polar/frontal temporal slow wave differentiating long delay items from control and short delay items. The ERPs are plotted from 200 ms before onset of the prompt to 2,000 ms after onset of the prompt, and the y-axis represents onset of the prompt.
The analysis of Benefactor revealed a significant effect of Condition, F(2, 132) = 11.26, p < 0.001, η2G, with Control items demonstrating greater negativity than Josh (t = 3.29, p = 0.004) or Other (t = 4.61, p < 0.001) items (Figure 1A and Table 2), that did not differ from one another (t = 1.32, p = 0.57). The main effect of Condition was also significant in the analysis of Delay, F(2, 132) = 11.01, p < 0.001, η2G = 0.031, with Control items revealing greater negativity than Short (t = 2.93, p = 0.012) and Long (t = 4.64, p < 0.001) delay items, that did not differ from one another (t = 1.70, p = 0.27).
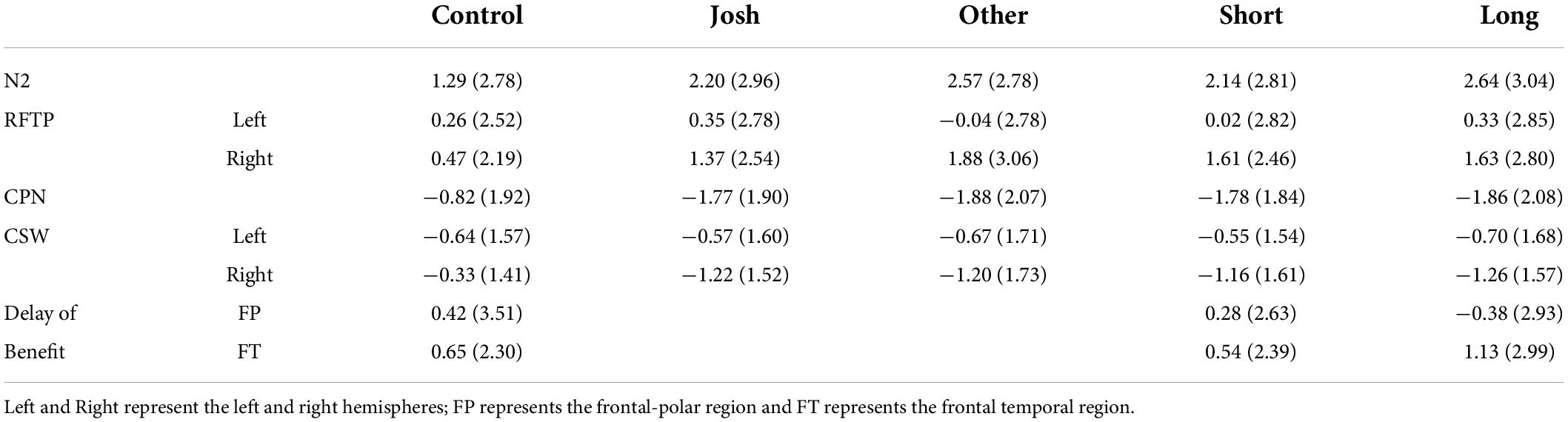
Table 2. Mean and standard deviation of voltage in microvolts for effects of Benefactor and Delay of Reward for modulations of the ERPs that were sensitive to ethical decision-making.
In the Benefactor analysis the effect of Condition was significant, F(2, 132) = 16.90, p < 0.001, η2G = 0.042; Josh (t = 4.74, p < 0.001) and Other (t = 5.29, p < 0.001) items revealed greater negativity than Control items (Figure 1B and Table 2), and did not differ from one another (t = 0.55, p = 1.00). The analysis of Delay revealed a main effect of Condition, F(2, 132) = 19.81, p < 0.001, η2G = 0.043; with Short (t = 5.24, p < 0.001) and Long (t = 0.55, p = 1.00) delay items revealing greater negativity than Control items, and did not differ from one another (t = 0.40, p = 1.00).
In the analysis of Benefactor the effect of Condition was significant, F(2, 132) = 6.41, p = 0.002, η2G = 0.005, and was qualified by a Condition × Hemisphere interaction, F(2, 132) = 6.00, p = 0.0003, η2G = 0.011, (Figure 1C); the effect of Condition was significant for the right, F(2, 132) = 10.23, p < 0.001, but not left, F(2, 132) = 1.06, p = 0.35, hemisphere. For the right hemisphere, Control items differed from Josh (t = 2.84, p = 0.016) and Other (t = 4.47, p < 0.001) items, that did not differ from one another (t = 1.63, p = 0.32). The analysis for Delay revealed an effect of Condition, F(2, 132) = 9.088, p < 0.001, η2G = 0.006, and a Condition × Hemisphere interaction, F(2, 132) = 4.56, p = 0.012, η2G = 0.008, right hemisphere, F(2, 132) = 12.35, p < 0.001), left hemisphere, F < 1.00. For the right hemisphere, Control items differed from Short (t = 4.27, p < 0.001) and Long (t = 4.34, p < 0.001) delay items, that did not differ from one another (t = 0.08, p = 1.00).
The analysis of Benefactor revealed an effect of Condition, F(2, 132) = 5.53, p = 0.005, η2G = 0.01, and a Condition × Hemisphere interaction, F(2, 132) = 12.35, p < 0.001, η2G = 0.011 (Figure 2A). A simple main effect test revealed that the effect was significant for the right, F(2, 132) = 13.95, p < 0.001, but not left, F < 1.00, hemisphere. For the right hemisphere, the ERPs for Control items were less negative than those for Josh (t = 4.61, p < 0.001) or Other (t = 4.53, p < 0.001) items, that did not differ from one another (t = 0.08, p = 1.00). The analysis of Delay revealed a main effect of Condition, F(2, 132) = 6.32, p = 0.002, η2G = 0.011, and a Condition × Hemisphere interaction, F(2, 132) = 16.79, p < 0.001, η2G = 0.011; and the effect of condition was significant for the right, F(2, 132) = 16.11, p < 0.001, but not left, F < 1.00, hemisphere. For the right hemisphere, the ERPs for Control items were less negative than those for Short (t = 4.62, p < 0.001) or Long (t = 5.17, p < 0.001) delay items, that did not differ from one another (t = 0.56, p = 1.00).
The analysis of the anterior frontal slow wave activity that was sensitive to benefactor revealed a significant main effect of Condition, F(2, 132) = 5.28, p = 0.006, η2G = 0.013 (Figure 2B), that reflected greater negativity for Other items (M = −0.50 μV) than for Josh items (M = 0.20 μV, t = 2.60, p = 0.031) or for Control items (M = 0.30 μV, t = 2.99, p = 0.01), that did not differ from one another (t = 0.39, p = 1.00).
The analysis of slow wave activity that was sensitive to timing of the benefit revealed a Condition × Region interaction, F(2, 132) = 3.94, p = 0.022, η2G = 0.007 (Figure 2C and Table 2). Follow-up analyses revealed that Short delay and Control items did not differ significantly from one another, Condition × Region F < 1.00, while Long delay items differed from Short delay, F(2, 132) = 6.38, p = 0.014, η2G = 0.008, and Control, F(2, 132) = 5.25, p = 0.025, η2G = 0.008, items.
The behavioral data reveal some noteworthy findings. The ISP demonstrated good reliability that was stronger for the violation items than the control items, providing a novel contribution to the literature. Choice behavior was highly correlated for Josh and Other items, that were in turn weakly correlated with Control items. Together, the reliability and correlations reveal that the ISP provides a robust measure of ethical decision-making that can be distinguished from more general decision-making realized in the Control items. The choice data revealed that individuals were less likely to respond yes to ethical items than control items, extending prior findings (Hu et al., 2015; West et al., 2019), and providing a measure of confidence that individuals are engaged in the task, as random responding might be expected to result in similar choice behavior across the ethical and control items.
The ERP data revealed four patterns relevant to the goals of the study that were to provide a conceptual replication of the ISP with a new set of materials, and to examine the possible effects of the benefactor and delay of a reward in the ISP. The amplitude of the posterior N2, right frontal temporal positivity, and central parietal negativity differed for violation items and control items, and the nature of the difference was similar to that observed in research using the original ISP materials (Hu et al., 2015; West et al., 2019). Together, these findings may indicate that the three modulations of the ERP reveal activity in neural systems that are generally related to ethical decision-making in the ISP, being rather insensitive to the characteristics of the ethical dilemmas.
The ERP data also revealed slow wave activity over the right central region between 400 and 1,800 ms that distinguished ethical and control items. This finding can be contrasted with the findings of West et al. (2019) who observed slow wave activity over the left central region in a similar time period. The reason for this difference is unclear. The studies were conducted using the same equipment and processing pipeline, so this seems unlikely to be driving the difference, while the materials did differ across studies. A second study using the Josh and Control items from the current task also revealed slow wave activity over the right central region for ethical than control items (West and Cowger, 2021). Given this, there may be some value in comparing the two sets of materials in the same individuals in an effort to distinguish robust findings from idiosyncratic characteristics of a dataset or set of materials.
We also observed slow wave activity over the anterior frontal region that was sensitive to the benefactor and delay of reward. The slow wave activity that was sensitive to benefactor distinguished Other items from Josh and Control items. This difference may indicate that the slow wave activity represents the engagement of a neuro-cognitive process supporting perspective taking that is recruited when contemplating an unethical action that benefits another individual rather than the self (D’Argembeau et al., 2007). The slow wave activity that was sensitive to the delay of the benefit distinguished Long delay items from Short delay and Control items. The anterior frontal distribution of the ERP activity would be consistent with the finding that the orbital and ventromedial prefrontal cortex is recruited during decision-making involving the consideration of delayed gains in the context of temporal discounting (Mitchell et al., 2010). Generally, these findings converge with ideas from the moral reasoning literature wherein moral decision-making is thought to emerge from the recruitment of general-purpose neuro-cognitive-affective mechanisms that are brought to bear on the problem at hand rather than specialized neural systems that are unique to moral reasoning (Greene and Young, 2020).
There are some limitations of the current study that should be considered. First, the sample primarily included undergraduates in the first 2 years of study that likely had limited experience with information security policies, so it could be interesting to explore neural activity in the ISP in individuals with greater knowledge of and experience with information security policy. Second, the study did not consider the impact of individual difference variables (e.g., self-control or moral belief) that are known to influence neural activity (Hu et al., 2015; West et al., 2019) and decision-making related to information security (Zhang et al., 2009; Siponen et al., 2012). The convergence between the current and other published findings have begun to reveal reliable modulations of the ERPs related to decision-making in the ISP that could serve as the foundation to address these limitations in future studies.
In conclusion, the findings of the current study demonstrate that ethical decision-making related to information security as measured in the ISP represents a reliable construct that can be distinguished from more general decision-making contributing to Control trials. The ERP data reveal that ethical decision-making in the ISP is associated with the recruitment of neuro-cognitive processes that operate in parallel beginning shortly after onset of the decision prompt and ending around the time of the behavioral response; with some evidence indicating that the right hemisphere may be preferentially engaged in decision-making within the task. The findings also reveal that ethical decision-making may be supported by the recruitment of processes that are either domain specific (i.e., distinguishing ethical from control trials) or more generally related to information processing that is relevant to the decision context (i.e., effects of benefactor and delay of the reward).
The datasets presented in this study can be found in online repositories. The names of the repository/repositories and accession number(s) can be found below: Open Science Framework—osf.io/f9dbv.
The studies involving human participants were reviewed and approved by the Institutional Review Board, DePauw University. The patients/participants provided their written informed consent to participate in this study.
RW, BK, and KM contributed to study design, data collection and analysis, and manuscript preparation. All authors contributed to the article and approved the submitted version.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Bailey, T., Kolo, B., Rajagopalan, K., and Ware, D. (2018). Insider Threat: The Human Element of Cyberrisk. London: McKinsey & Co.
Balozian, P., and Leidner, D. (2017). Review of IS security policy compliance: Toward the building blocks of an IS security theory. Data Base Adv. Inf. 48, 11–43. doi: 10.1145/3130515.3130518
D’Argembeau, A., Ruby, P., Collette, F., Degueldre, C., Balteau, E., Luxen, A., et al. (2007). Distinct regions of the medial prefrontal cortex are associated with Self-referential processing and perspective taking. J. Cogn. Neurosci. 19, 935–944. doi: 10.1162/jocn.2007.19.6.935
Decety, J., and Porges, E. (2011). Imagining being the agent of actions that carry different moral consequences: An fMRI study. Neuropsychologia 49, 2994–3001. 2011.06.024 doi: 10.1016/j.neuropsychologia
Delorme, A., and Makeig, S. (2004). EEGLAB: An open source toolbox for analysis of single-trial EEG dynamics including independent components analysis. J. Neurosci. Methods 134, 9–21. doi: 10.1016/j.jneumeth.2003.10.009
Duan, Q., Xu, Z., Hu, Q., and Luo, S. (2021). Neural variability fingerprint predicts individuals’ information security violation intentions. Fundam. Res. 2, 303–310. doi: 10.1016/j.fmre.2021.10.002
Ernst and Young (2010). Global information security survey 2010. Available online at: https://docplayer.net/2788478-Borderless-security-ernst-young-s-2010-global-information-security-survey.html (accessed August 1, 2022).
Greene, J., Morelli, S., Lowenberg, L., and Nystrom, L. (2008). Cognitive load selectively interferes with utilitarian moral judgment. Cognition 107, 1144–1154. doi: 10.1016/j.cognition.2007.11.004
Greene, J. D., Somerville, R. B., Nystrom, L. E., Darley, J. M., and Cohen, J. D. (2001). An fMRI investigation of emotional engagement in moral judgment. Science 293, 2105–2108. doi: 10.1126/science.1062872
Greene, J. D., and Young, L. (2020). The Cognitive Neuroscience of Moral Judgment and Decision-Making. in M. S. Gazzaniga and G. R. Mangun (Eds.), The Cognitive Neurosciences, 6th Edn. 1003–1014.(Cambridge, MA: MIT Press)
Hu, Q., West, R., and Smarandescu, L. (2015). The role of self-control in information security violations: Insights from a cognitive neuroscience perspective. J. Manag. Inf. Syst. 31, 6–48. doi: 10.1080/07421222.2014.1001255
Hu, Q., Xu, Z., Dinev, T., and Ling, H. (2011). Does deterrence work in reducing information security policy abuse by employees? Commun. ACM 54, 55–60. doi: 10.1145/193122.1953142
Kable, J. W. (2014). “Valuation, Intertemporal Choice, and Self-control,” in Neuroecenomics, 2nd Edn, eds P. W. Glimcher and E. Fehr (London: Academic Press), 173–192. doi: 10.1016/B978-0-12-416008-8.00010-3
Kirby, B., Malley, K., and West, R. (2019). “Neural activity related to information security decision making: Effects of who is rewarded and when the reward is received,” in Information Systems and Neuroscience, Lecture Notes in Information Systems and Organisation, Vol. 29, eds F. D. Davis et al. 19–27. (Berlin: Springer) doi: 10.1007/978-3-030-01087-4_3
Li, H., Luo, X., Zhang, J., and Sarathy, R. (2018). Self-control, organizational context, and rational choice in Internet abuses at work. Inf. Manag. 55, 358–367. doi: 10.1016/j.jm.2017.09.002
Lopez-Calderon, J., and Luck, S. J. (2014). ERPLAB: An open-source toolbox for the analysis of event-related potentials. Front. Hum. Neurosci. 8:213. doi: 10.3389/fnhum.2014.00213
Luo, X., Li, H., Hu, Q., and Xu, H. (2020). Why individual employees commit malicious computer abuse: A routine activity theory perspective. J. Assoc. Inf. Syst. 21, 1552–1593. doi: 10.17705/1jais.000646
Mitchell, J. P., Schirmer, J., Ames, D. L., and Gilbert, D. T. (2010). Medial Prefrontal Cortex Predicts Intertemporal Choice. J. Cognit. Neurosci. 23, 857–66. doi: 10.1162/jocn.2010.21479
Myyry, L., Siponen, M., Pahnila, S., Vartiainen, T., and Vance, A. (2009). What levels of moral reasoning and values explain adherence to information security rules? An empirical study. Eur. J. Inf. Syst. 18, 126–139. doi: 10.1057/ejis.2009.10
Richardson, R. (2011). CSI computer crime and security survey. https://cours.etsmtl.ca/gti619/documents/divers/CSIsurvey2010.pdf (accessed August 1, 2022).
Siponen, M., Vance, A., and Willison, R. (2012). New insights into the problem of software piracy: The effects of neutralization, shame, and moral beliefs. Inf. Manage. 49, 334–341. doi: 10.1016/j.im.2012.06.004
Vance, A., and Siponen, M. (2012). IS security policy violations: A rational choice perspective. J. Organ. End User Comput. 24, 21–41. doi: 10.4018/joeuc.2012010102
West, R., Budde, E., and Hu, Q. (2019). Neural correlates of decision making related to information security: Self-control and moral potency. PLoS One 14:e0221808. doi: 10.1371/journal.pone.0221808
West, R., and Cowger, K. (2021). “An inward focus of attention during information security decision making: Electrophysiological evidence,” in Information Systems and Neuroscience, 103-111, Lecture Notes in Information Systems and Organisation, eds F. D. Davis et al. (Berlin: Springer). 103–111. doi: 10.1007/978-3-030-88900-5_12
Young, L., Cushman, F., Hauser, M., and Saxe, R. (2007). The neural basis of the interaction between theory of mind and moral judgment. Proc. Natl. Acad. Sci. U.S.A. 104, 8235–8240. doi: 10.1073/pnas.0701408104
Keywords: information security, ethical decision making, event—related potentials (ERP), delay of reward, perspective taking
Citation: West R, Kirby B and Malley K (2022) Using event-related brain potentials to explore the temporal dynamics of decision-making related to information security. Front. Neurosci. 16:878248. doi: 10.3389/fnins.2022.878248
Received: 17 February 2022; Accepted: 25 July 2022;
Published: 10 August 2022.
Edited by:
René Riedl, University of Applied Sciences Upper Austria, AustriaReviewed by:
Azizuddin Khan, Indian Institute of Technology Bombay, IndiaCopyright © 2022 West, Kirby and Malley. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Robert West, cm9ibHdlc3QwOEBnbWFpbC5jb20=
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.