Abstract
This work investigates the cooperative formation control problem of unmanned surface vehicle-remotely operated vehicles (USV-ROVs) subject to uncertainties under deceptive attacks. In the control design, with the utilization of the desired formation as well as the geometric position between USV and ROVs, a geometric transformation approach is developed and a geometric constraint relationship of governing formation positions is derived. Under the terminal sliding mode control (TSMC) design framework, a novel terminal sliding surface is crafted to circumvent the singularity issue. To further bolster robustness, using the sliding mode damper concept, a variable damping reaching law is devised. To refrain from the effectiveness of attacks and uncertainties, the adaptive technique is integrated into the TSMC framework. To save the communication resources, an event-triggering mechanism is established between the distributed controller and ROVs. Then, an event-triggered adaptive finite-time cooperative formation control scheme is developed for the USV-ROVs. The Lyapunov theory analysis shows that the cooperative formation control issue of USV-ROVs is realized and the deceptive attack can be suppressed efficaciously. The simulation, comparison, and quantitative analysis demonstrate the relative effectiveness and superiority of the developed scheme.
1 Introduction
In recent years, the field of marine engineering has witnessed a significant shift towards the exploration of collaborative multi-intelligent body formation control. This research direction involves the coordination and cooperation of multiple intelligences, which has the advantages of improving survivability, reducing operation cost, and expanding operation range compared with the traditional operation of a single intelligence (Xu et al., 2022). Intelligent aircraft and underwater operation equipment such as unmanned surface vehicles (USV), remotely operated vehicles (ROV), and autonomous underwater vehicles (AUV) play an important role in related engineering scenarios (Li et al., 2023b). Therefore, control issues become critical in order for multi-intelligence bodies to achieve safe cooperative formation navigation and to perform smoothly according to pre-designed missions. In USVs in unmanned control mode, the network becomes an important medium for executing tasks, and in open network links between sensors, controllers, and actuators, the exchanged data are vulnerable to attacks because of protocol vulnerabilities, misconfigurations, and other situations. In recent years, a number of maritime security incidents related to network attacks have been triggered around the world, raising serious security concerns (Swaszek et al., 2013). Hence, addressing the issue of network attacks is pivotal for achieving secure formation navigation of USV-ROVs and the successful execution of assigned missions.
Network attack methods are generally categorized into Denial of Service (DoS) attacks, replay attacks, and deceptive injection attacks (Chen et al., 2019). DoS attacks are crafted to overwhelm a system’s resources, rendering it incapable of processing legitimate service requests. Replay attacks and deceptive injection attacks can be collectively categorized as deceptive attacks, centered around manipulating and corrupting transmitted data within the network. Replay attacks involve maliciously resending the same data repeatedly, constituting a specialized form of deception attack. In deceptive injection attacks, attackers inject spoofed commands into sensors that receive ship data, subsequently integrated into the control system. In contrast, deceptive injection attacks are more harmful to USV-ROVs formation control because of their stealthy nature (Ding et al., 2016). Maritime security mechanisms for network control systems (NCS) have primarily focused on IT-level designs (Li et al., 2022), such as setting up firewalls, to enhance security control and detect potential threats at the computer system level. However, these measures alone are insufficient for regulating the control of formation devices when they come under deceptive attacks (Sandberg et al., 2015). To address this issue, security control strategies need to be developed at the control level to ensure the safety and integrity of marine operations, in conjunction with security software. Researchers have explored various control techniques, such as sliding mode control (Shi et al., 2018a), observer-based control (Jin, 2018), and adaptive control (Zhang and Zhang, 2015), due to their robustness in dealing with system uncertainties and external disturbances. These techniques constitute a resilient compensation mechanism (Wu et al., 2019) to mitigate the impact of attacks on the system. Sliding mode control has attracted many scholars to study it because it relies less on the accuracy of the system model and has less influence of system parameter variations and external perturbations compared to other control techniques. W Wang (Wang et al., 2021) investigated the problem of formation control for uncertain systems under deceptive attacks, incorporating adaptive methods to improve control efficiency, performance, and system resilience. T Yin (Yin et al., 2022) investigated the problem of event-based intermittent formation control under deceptive attacks by introducing an averaging method in the event triggering mechanism to reduce the burden on the network bandwidth. DW Zhang (Zhang and Liu, 2023) proposed a predictive sliding mode control method to improve the closed-loop system robustness of the formation by introducing a sliding variable to defend against random deceptive attacks. In the field of cyber security control, the issue of chattering associated with sliding mode control is often overlooked (Saihi et al., 2019). Additionally, some researchers have employed the theory of uncertain system state estimation to model attack damage control commands as virtual unknown states. They transformed these commands into unknown state estimation problems, established adaptive resilience policies using continuous incentive mechanisms, and designed event-triggered filters to counter deceptive attacks (Liu et al., 2020). Other studies have proposed novel observers (Huang and Dong, 2019) to address attack problems from a modeling perspective by algebraically modifying the attack abstraction model of the device. However, the effectiveness of resilient compensation and the associated constraints still require further exploration and validation due to the sudden and unpredictable nature of attacks.
In addition to the aforementioned challenges, formation control differs from single-vessel trajectory tracking control as it requires maintaining a specific formation. Common formation control methods include the leading-following method, virtual structure method, behavior-based method, and artificial potential field method; among these, the leading-following method has garnered extensive attention due to its simplicity and practical applicability. Essentially, this method involves designating an individual within the formation as a navigator and the remaining members as followers; a relationship is then established between the navigator and the followers to achieve effective formation control. H Xu (Xu et al., 2023) et al. proposed a leading-follower formation control method combined with a fixed-time perturbation observer, which solved the problem of USVs formation control in the presence of unknown perturbations. L Ding (Ding and Guo, 2012) et al. aimed at the synergy problem between USVs, combined the leading-follower method and backstepping method together to design a new formation control law. Based on the virtual leader strategy, M Fu (Fu et al., 2018) et al. designed a new control law by simplifying the backstepping control technique through coordinate transformation, and proved the stability of the whole formation system. Based on graph topology theory, Li Y (Yun and Ying, 2016) et al. introduced a hybrid leading-follower method to design control strategies to control the formation sequentially according to the motion patterns in different phases, and Lin et al. used the pilot-follower method to divide the ships in the formation into virtual leader and follower, and introduced an observer to eliminate the virtual leader and follower. Lin A (Lin et al., 2018) et al. used the leading-follower method to categorize the ships in the formation into a virtual leader and followers, introduced observers to eliminate unknown disturbances, and reduced the complexity of designing formation controllers by transforming the formation control into the design of controllers for three subsystems. The above studies conducted intelligent control research on different tasks from the perspective of equipment coordination, but most of them focused on power localization and did not bring out the unmanned advantages that USVs themselves possess, and the motion control of USV-ROVs in formation coordination was not further studied.
During navigation, USV-ROVs are affected by a variety of uncertainties in addition to network attacks, such as external perturbations caused by wind, waves, and currents, and internal uncertainties such as ship dynamic uncertainties and model errors (Li et al., 2023a). USV-ROV formation systems are characterized by offshore operations, and the time-varying disturbances caused by sea winds and waves to the USV-ROV are the primary control challenges from the external environment (Skjetne et al., 2005). These components can affect the control performance of the whole formation control system and reduce the robustness of the system. In order to deal with these problems, some effective uncertainty estimation and reconstruction methods have been presented, such as sliding mode, observer, and parameter adaptive techniques, among which terminal sliding mode control has been widely used by many scholars due to its strong anti-interference ability. Yang G (Yang and Chen, 2020) et al. proposed a power convergence law, which can adaptively select parameters to improve the convergence speed of the convergence law. Kang Z (Kang et al., 2020) et al. proposed a double power convergence law, which adaptively combined the terminal sliding mode with the double power convergence law, which can better accomplish the tracking task while weakening the jitter phenomenon. Tian Y (Tian et al., 2020) et al. designed a fast convergence fixed-time non-singular terminal sliding mode method for a class of second-order non-linear systems with matching uncertainty, which avoids the singularity phenomenon, improves the fast response capability of the system, and suppresses the jitter phenomenon of the sliding mode control. Sun R (Sun et al., 2018) et al. combined a neural network based neural network-based formation switching strategy and terminal sliding mode control technology to design the controller, which effectively improves the control accuracy and reduces the real-time computational load of the controller. Many scholars have achieved good results in the field of network attack formation and terminal sliding mode control, but since USV-ROVs are a kind of multi-input non-linear system, the design is usually more complicated, and the convergence law has a crucial role in the rapidity and stability of the controller. Based on the aforementioned approach, the primary objective of this paper is to design a novel terminal sliding mode control to address the formation problem under deceptive attacks. The main contributions of this paper are as follows.
-
In this paper, mathematical abstraction modeling of stealthy attacks and perturbations caused by internal and external factors including actuator matching perturbations is carried out in part 2. Aiming at the stealthy nature of a deceptive attack, a sliding mode control scheme is adopted from the perspective of control system robustness. In part 3.1, considering the singularity and trajectory tracking time requirements, a new terminal sliding mode surface design is carried out to complete the convergence phase and sliding phase in a limited time to improve the control efficiency.
-
In part 3.2, based on the dynamic characteristics of the sliding mode convergence phase, a dynamic dampener is introduced, and a novel variable damping sliding mode convergence law is developed. In this approach, the convergence speed at the junction of convergence and arrival phases have been reduced, thereby minimizing sliding mode chattering. Moreover, it increases dynamic speed when moving away from the sliding mode surface to improve response efficiency, leading to better response and compensation effects in sliding mode control.
-
To tackle the challenges related to saturation filtering, a non-linear saturation fitting function has been devised in part 3.3, which is coupled with an event-triggering mechanism. This innovative approach serves to decrease the utilization of communication resources and effectively mitigates communication congestion triggered by deceptive attacks.
Notations: is -dimensional Euclidean space, is sinusoidal function, is cosine function, is Euclidean parameter, is symbolic function, is hyperbolic tangent function, is saturation function, is diagonal matrix, and and are minimum and maximum values, respectively.
2 Problem description
2.1 Mathematical model
The investigation of USV-ROVs formation control in this paper is based on the three degrees of freedom planar motion synergy problem (Min et al., 2020; Fan et al., 2021; Chen et al., 2023), wherein the kinematics of the two devices are described within the generalized coordinate system.
The kinematics and dynamics equations of USV (Zhu and Du, 2018) are described as (Equations 1) and (2).
where is the transformation matrices for dynamics and kinematics in the coordinate system; is the vector of first-order derivatives of the position coordinate vector. is uncertain. is the ship system input. is the external perturbation of the converted system, with low-frequency accretion characteristics. is a matrix of system control input conversion coefficients. is the ship type relationship and hydrodynamic additional relationship matrix, is the Coriolis centripetal matrix, and is the hydrodynamic damping coefficient matrix.
A tracked differential ROV with incomplete constraint characteristics is selected for underwater navigation according to the requirements of ocean engineering. The kinematics and dynamics equations of ROV (Wu and Wang, 2020) are described as (Equations 3) and (4).
where is the ROVs transformation matrix; is the first derivative vector of the position coordinate vector. The robot system input is the left and right wheel drive torque vector. is the external perturbation of the converted system, with low-frequency accretion characteristics. is uncertain. . is the friction matrix; is a non-complete constraint matrix; is the Lagrange multiplier. is the matrix of system input conversion coefficients, is the moment of inertia; is the quality of ROV; is the ROV width; and is the driving wheel radius.
2.2 Attack models
The USV-ROV formation system, employing a centralized control scheme and formation strategy for command transmission, faces security risks in its semi-open wireless network environment. Deceptive attacks are a common threat, involving IP hijacking and the injection of false data, bypassing firewalls and compromising the control of USV-ROV formations. Additionally, these attacks can result in offline damage to wireline switching equipment, impacting overall formation effectiveness. Existing network control systems often neglect post-attack damage and lack adequate countermeasures. Therefore, it is crucial to design security control strategies specifically at the control level to comprehensively address these threats.
Remark 1: Element in the USV identification, represents the leader USV and the virtual leader sequence, and . The USV smart device with device identification sequence is a follower of the ROV device of , . Then is the set of follower identification.
A stealth deceptive attack uses a hidden identity to access the IP and injects bounded interval false data that mimics normal data to the control command data; the deceptive data injection logic is shown in Figure 1.
Figure 1

Stealth deceptive attack data injection.
From a control instruction perspective, this attack can be abstracted as an unknown additive signal (Ito and Takanami, 1997). Consequently, the actuator input signal modeled by the stealth deceptive attack is (Equation 5).
where is a control command sent by the controller to be transmitted to the system inputs in the physical perception layer after a stealthy deceptive attack at the receiver side of the network layer. is bounded unknown data. is the NCS output.
The success rate of the attack can be represented using the Bernoulli series, and the final form of the false data is (Equation 6).
where is the attack rate concomitant matrix with Bernoulli distribution properties and is the false data value. An attacker injects bounded random data in order to reduce the probability of being captured by a security program; , is the tampering probability when the attack is unsuccessful or not performed during the three interactions.
2.3 Formation model
During the actual operational process, each device exhibits a saturation characteristic in its execution performance. To represent this physical attribute, a saturation function is introduced. The control input is (Equation 7).
where is the constant absolute value of the physical saturation of the actuator and is the saturation function.
The global motion model of USV and ROV considering attack, matching, external disturbance, and uncertainty is (Equation 8).
where is the model physical item of equipment, is the USV equipment identification sequence, and is the ROV equipment identification sequence.
is the matrix of geometric features of the desired formation of leaders and followers in the global generalized coordinate system, is the real formation feature matrix, is the follower device, and is the leader device. Taking the geometric position of a single ship and a single robot as an example, the formation relationship of the formation system is shown in Figure 2.
Figure 2
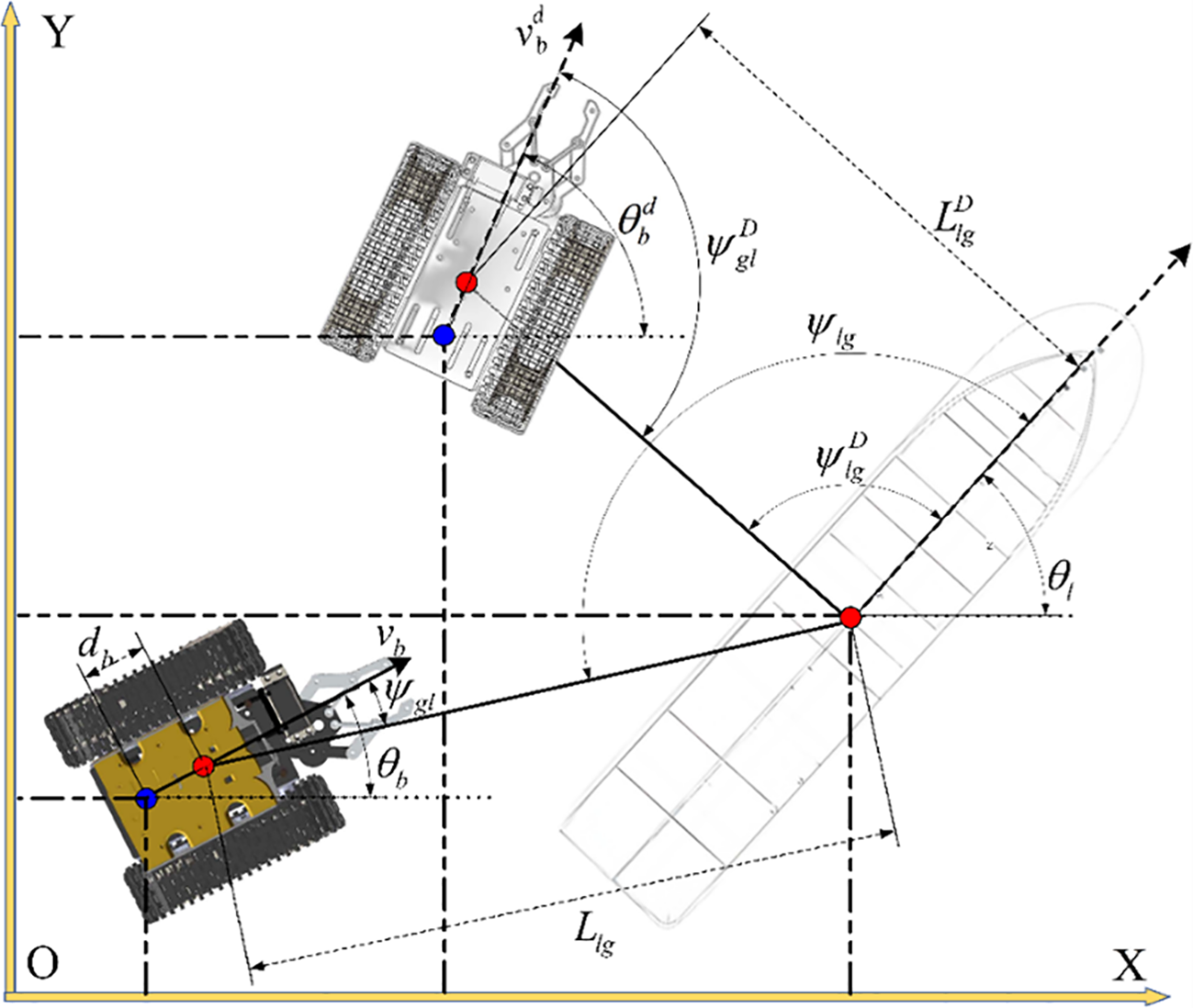
Geometric relationship of USV-ROV formation system.
Assumption 1: The motion state of the formation system represents the actual configuration of the formation once each local equipment achieves a specific geometric arrangement within the formation.
The essence of synergistic control of formation geometry and formation motion is that the control system allows the current formation geometry feature described as
(Equation 9) illustrates if the collaborative goal can be achieved is dependent on the transformation form of the dynamic characteristics of each device. The relationship between the dynamic positions of each device and the dynamic transformation characteristics is (Equation 10).
where is the motion conversion item of the X-axis; is the dynamic component conversion item in the direction of the Y-axis; and is the motion conversion item of the speed.
After collation, it becomes evident that the formation motion difference model that requires control within the formation scheme is (Equation 11). Subsequently, this formation relationship matrix will be utilized for formation control system design with a view to achieving the target expectation to accomplish the formation control task.
where is the expected position vector of the leader and is the position vector of the leader. According to assumption 1, they are all virtual leaders, the formation differences are split according to kinematics and dynamics to give dynamic errors and .
To facilitate the heterogeneous formation control, the error is divided by the equipment labeling, the first-order derivation of (Equation 11) is carried out and brought into the model (10) deformation can be shown that the dynamic formation cooperative model is (Equation 12).
where is the virtual movement expectation of the leader, is the virtual movement expectation of the follower, and and are the speed states of the leader and the followers, respectively.
If every device, under the influence of two synergy programs, attains the expected state simultaneously, the formation’s motion state can be maintained. The geometric synergy program successfully guides the controlled system to achieve the desired geometric characteristics, signifying the completion of the formation restoration process. Moreover, if the speed of each device, governed by the motion synergy program, tends to converge, it indicates that the formation system has achieved the anticipated motion state.
3 Controller design and stability analysis
3.1 Design and analysis of non-singular terminal sliding mode surface
To address the singularity issue of the terminal sliding mode surface, following the traditional terminal sliding mode surface design concept (Min et al., 2020), the non-singular terminal sliding mode surface can be expressed as
where , , and are normal constant diagonal matrices.
Deriving (Equation 13), the result shown in (Equation 14) can be obtained. It is evident that there are no singular points in , signifying that the non-singular sliding mode surface will not encounter issues related to singularities.
Analysis of (Equation 13) shows that the design meets the sliding mode dynamic standard Equation 15) (Shi et al., 2018b).
To verify that the terminal sliding mode (13) can converge in a finite time, assuming that when , transform (14), and the definite integral is calculated on both sides in the convergence time interval, and according to , it can be described as
where and are the maximum and minimum values of , respectively.
It can be seen that the terminal sliding mode surface (13) can converge in finite time when . It is evident that the terminal sliding mode surface can achieve convergence during the sliding phase within a finite time.
3.2 Dynamically adjusted approach rate design
In pursuit of achieving global finite-time convergence of the sliding mode while optimizing chattering and enhancing robust response capability, a dynamic damper is designed based on the dynamic information of the sliding mode can be described in (Equation 17). Additionally, based on the traditional reaching law, a dynamic adjustment reaching law can be described in (Equation 18).
where , is a diagonal matrix with positive definite coefficients. When , dynamically adjust the approach law , which can prove that it will not cause over-switching of the control approach and weaken the chattering. According to (Equation 18), it can be seen that the closer to the sliding mode surface, the smaller the reaching law, and the farther away from the sliding mode surface, the larger the reaching law value.
Lemma 1 (Chen et al., 2023). If a continuous non-linear system, such as , is controllable, then for , the Lyapunov function exists and is positive definite. If , , , , and , then it can be stabilized in finite time, and is the finite time horizon.
Establishing Lyapunov positive definite function and deriving it, the equation can be gotten:
where , , , . (Equation 19) satisfies Lemma 1; it can be seen that the finite time approach can be realized under the action of this reaching law.
3.3 Event trigger mechanism design
Taking into consideration the control physical saturation characteristics of each device, the event trigger condition can be described as
where ; is the trigger condition value, , . Triggered at the time , at which point the control input is updated. If the calculation at the control end cannot satisfy (Equation 20), the control command transmission will not be performed, and the USV-ROVs will execute the control command in under the action of the zero-order keeper. is the controller output after smooth saturation fitting, is the control threshold parameter for saturated non-linear filtering, and is the filtering error.
3.4 Formation controller design
The dynamic adjustment terminal sliding mode formation controller will be designed in two steps, and the control process is depicted in Figure 3.
Figure 3
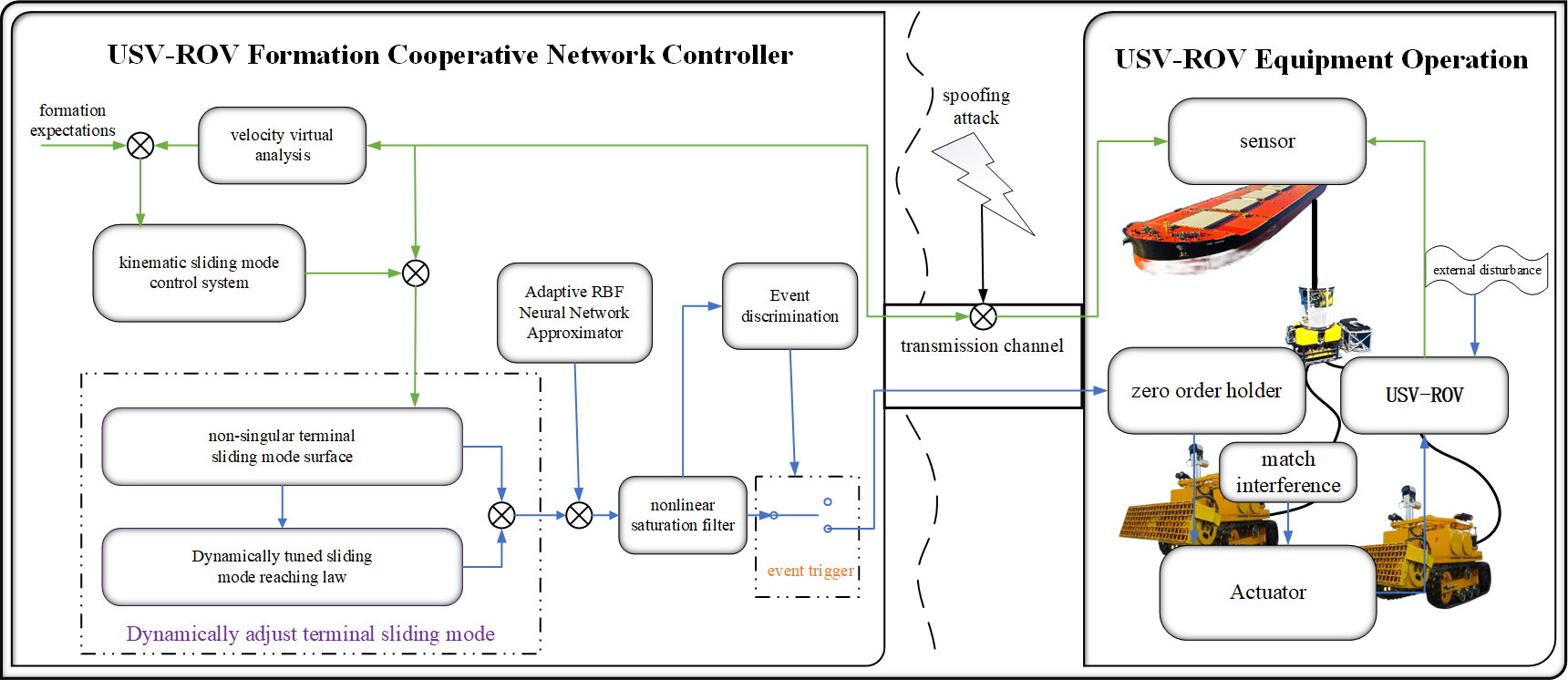
Schematic diagram of USV-ROV dynamic adjustment terminal skid formation control process.
To simplify the algorithm design and address the issue of heterogeneous equipment with varying orders, derived after introducing auxiliary variables in (12), the new error surface is (Equation 21).
where and are the ROV auxiliary sliding mode surfaces, , , , .
Based on the system model (Equation 8) and the coordination model (Equation 16), the problem of geometric kinematics coordination for the formation is reformulated as the coordination and stabilization problem of the relative pose coordinates of each equipment. The virtual inversion finite-time kinematics controller is (Equation 22).
where , . Among them, and are positive parameter matrices of the kinematic controller, and are auxiliary quantities. , , , , and are all normal constants, and is a dynamic regulator.
Lemma 2 (Gao et al., 2016). The Radial Basis Function Neyral Network (RBFNN) is cited because of the non-linear characteristics of system uncertainty. If there exists m-dimensional compact set and there is an unknown non-linear function with initial value 0 defined on , then the RBFNN approximator is used to fit the dynamic values of , where is the bounded RBF fitting error, which is defined on the compact set . , and is the maximum nuclear distance. To improve the non-linear local approximation ability, the Gaussian function is selected as the smooth kernel function. The is approaching the center column distance vector. The is varying constant value. is the order m-dimensional weight row vector of optimally fitted, as , where is the minimum estimate of .
Using the RBF neural network in Lemma 2 to estimate the dynamic uncertainty of the model, the RBF neural network approximator is constructed and brought into (Equation 12), and in (Equations 21) and (22), once the outer-loop model is organized based on the classification of formation equipment, using the design concept of the back-stepping virtual control law, the error dynamic Equation 23 can be described as
where is the approximation error of device and is the neural network weight matrix. is the hyperbolic tangent kernel function for feature extraction.
Utilize terminal sliding mode surfaces and dynamically regulate convergence laws to exploit sliding mode robust response with two-stage global finite time convergence capability for passive resilient aggression tolerant formation control of deceptive attacks.
where is the sliding mode reaching law dynamic regulator.
Based on the model (8) and the dynamic adjustment approach law (Equation 24), the inner loop formation controller and the adaptive law are described in (Equations 25) and (26), respectively.
where , , , and are bounded normal constants. , . is an adaptive RBF disturbance compensator, , , .
3.5 Stability analysis
The stability verification of the kinematics controller and the dynamics controller will be conducted separately.
A. Kinematics stability proof
Based on the formation system, the Lyapunov direct method is utilized to design , and deriving it, one can get
Substituting (Equations 22) and (24) into (Equation 27) results in, when combined with Young’s inequality, the equation
where , , , , , , , and . , , , and . , , and . (Equation 28) can prove that the dual-loop controller can stabilize the global motion of the formation system in a finite time.
B. Proof of dynamic stability of USV-ROV system
Based on (Equations 8), (14), and (26), design Lyapunov function , where . Deriving , using the norm inequality and the minimum learning parameter reduction method, combined with Young’s inequality, the Equation 29 can be gotten:
where and .
Lemma 3 (Liu et al., 2020). For , any , there exists a constant such that exists, then is said to satisfy the Lipschitz condition on the tight set .
Based on (Equation 27), the Lyapunov global function is established, and after derivation and simplification, the equation can be gotten:
where , . The boundary term is . It can be seen that (Equation 30) can converge in a finite time.
Based on the convergence and boundedness of the closed-loop system, when , it can be seen that there is boundedness in the system. is the bounded time for convergence, .
C. Event trigger proof of Zeno-free phenomenon
Since , , can be known according to (Equation 20), thus , where . Then, integrating the trigger error with , it can be gotten that
According to Equation 31 and the controller output time correlation, and the input is limited by saturation , can be obtained. From this we can know that , so the trigger condition (20) can avoid the proof of Zeno’s phenomenon.
Hence, the stability of the entire formation control system has been demonstrated.
4 Simulation analysis
For the scientific rigor of the simulation, the ROV in the USV-ROV formation system uses the submarine operation ROV in the literature (Chen et al., 2023); the mass is , the width is , the driving wheel radius is , the distance between the center of mass and the center of gravity is , the driving input is , and the moment of inertia is . The USV chooses the ship CyberShip II (Zhang et al., 2022) of the Norwegian University of Science and Technology as the simulation object, which has double symmetrical propellers, double tail rudders, and single side thrusters; the mass is the length of the hull is , the width is , and the drive input is . At the same time, the parameters are , , , , , , , and .
The stealthy deception attack probability is , and is the attack random tampering amount. are wind, wave, and current disturbances (Zhang et al., 2022), , , and ; is the amount of external disturbance (Chen et al., 2023) encountered by the ROV during its movement, and is Gaussian white noise with a power of one. The total simulation time is , and the step size of the simulation is . The amount and number of USV three-channel attack tampering is shown in Figure 4.
Figure 4
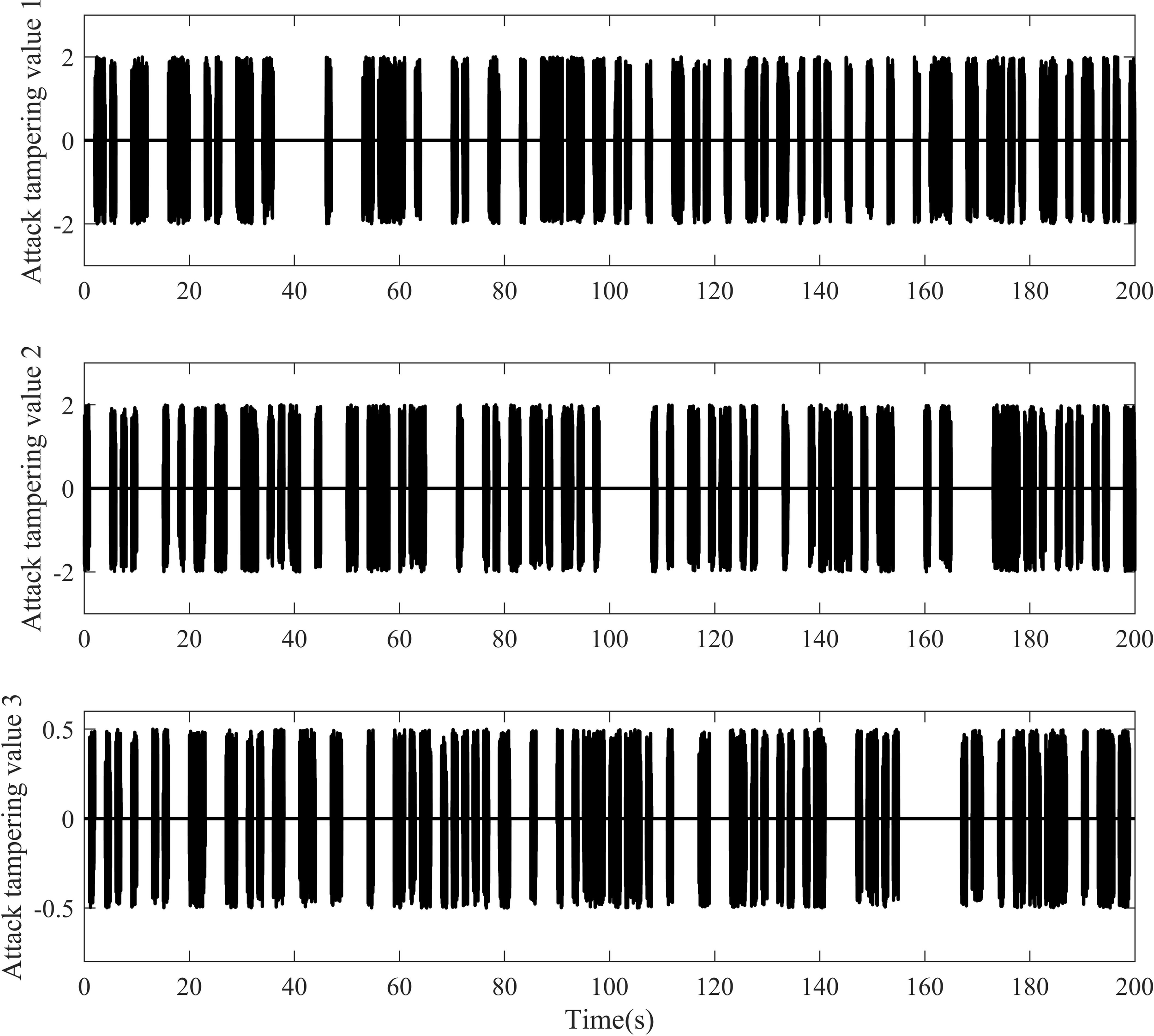
Deceptive attack onset time and amount of tampering.
To verify the control performance of the control algorithm in different tasks, the curvature-transformed trajectory that synthesizes the broken line and curve characteristics is selected as the reference trajectory of the virtual leader ; to facilitate the verification of the USV-ROV formation control effect, one USV is selected as the leader, and two ROVs are selected as follows: is the USV initial position, and and are ROV initial positions. To verify the superiority of the algorithm in this paper, is introduced, and the comparison controller is designed in combination with the exponential reaching law, and Equation 32 can be obtained
The parameters for the formation kinematics and dynamics controller can be described in Table 1.
Table 1
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| 0.4 | |||
| 1.15 | |||
| 0.5 | |||
Formation controller parameters.
To quantitatively assess the effectiveness of the algorithm presented in this paper, the following metrics are employed: mean integral absolute control (MIAC) is used to compute input energy, mean integral square error (MISE) is utilized to measure error control accuracy, and mean integral total variation (MITV) is designed to assess incoming communication transmission frequencies. The results are summarized in Tables 2 and 3, providing quantitative insights. , , .
Table 2
| Evaluation criteria | MIAC | MISE | MITV | Transfer times |
|---|---|---|---|---|
| equipment | [0.8, 1.19, 2.66] | [3.62, 3.32, 4.60] | [7.8, 6.19, 6.01] | [7980, 8610] |
| equipment | [0.9, 1.69] | [3.35, 2.82, 2.02] | [5.9, 6.31] | [8433, 9106] |
| equipment | [1.1, 1.09] | [3.10, 2.93, 2.66] | [5.1, 5.90] | [6621, 7638] |
Quantitative analysis of control effect of controller (25).
Table 3
| Evaluation criteria | MIAC | MISE | MITV | Transfer times |
|---|---|---|---|---|
| equipment | [1.8, 2.37, 4.06] | [4.12, 4.01, 4.71] | [8.61, 5.90, 8.21] | 20000 |
| equipment | [1.20, 3.71] | [4.27, 3.46, 2.52] | [5.85, 7.01] | 20000 |
| equipment | [0.85, 2.52] | [2.87, 2.73, 2.81] | [6.43, 6.40] | 20000 |
Quantitative analysis of control effect of controller (32).
Figure 5 illustrates the formation recovery and hold control achieved under deceptive attacks using the controller (25) proposed in this paper. Position error comparisons in Figures 6–8 reveal that the algorithm presented in this study exhibits higher control accuracy than controller (32). Under the control of controller (25), the formation can attain the desired position in approximately 18 seconds, demonstrating superior tracking efficiency compared to controller (32). Quantitative values of MISE in Tables 2, 3 further confirm the enhanced control accuracy of this paper’s algorithm, showcasing improvements of , , and , respectively, for position error compared to controller (32). Additionally, during the attack phase of 50s-150s in Figures 6–8, the error fluctuation of controller (25) is smaller than that of controller (32), indicating better stability for the proposed algorithm in this paper.
Figure 5
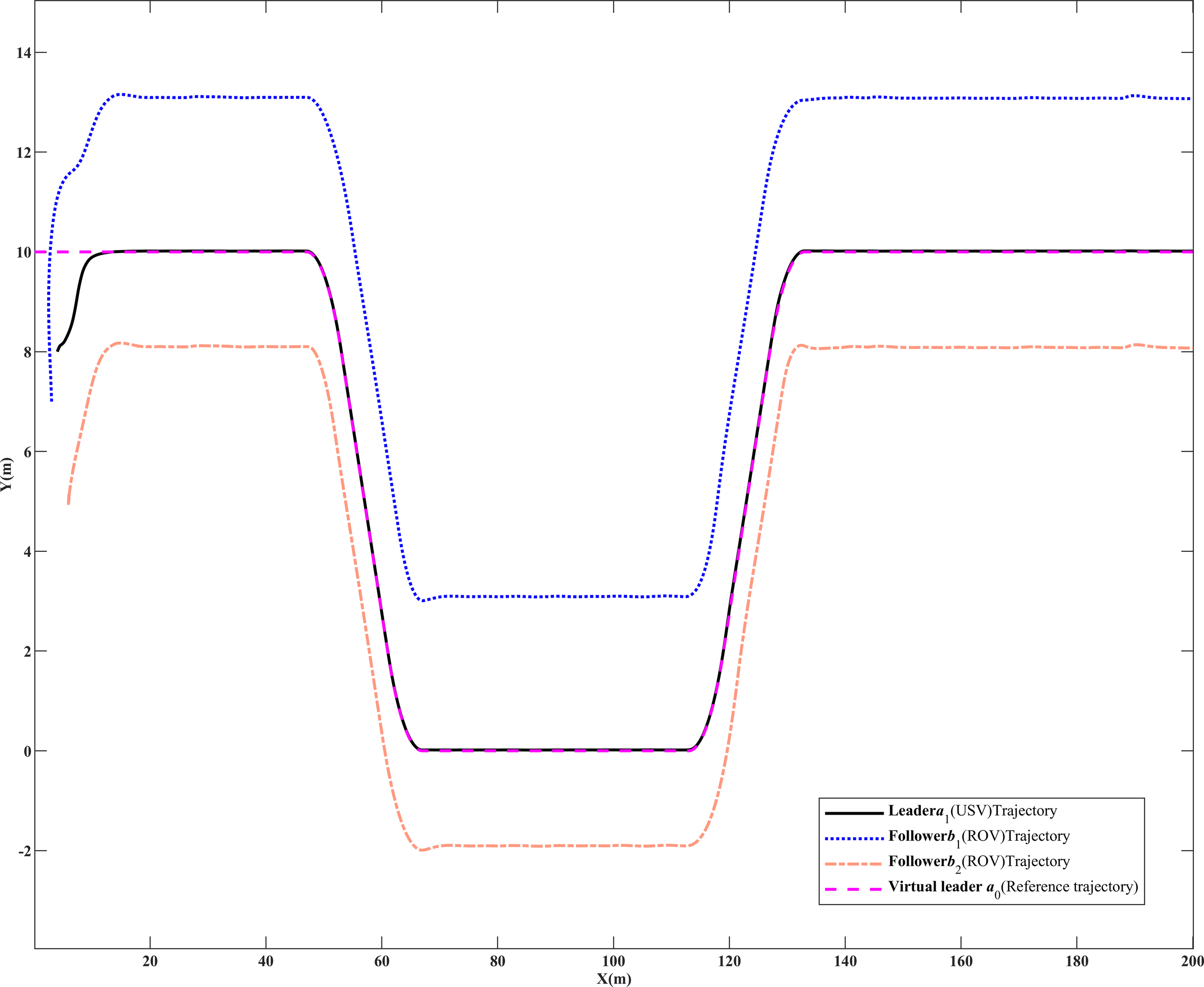
USV-ROV formation collaborative tracking movement.
Figure 6
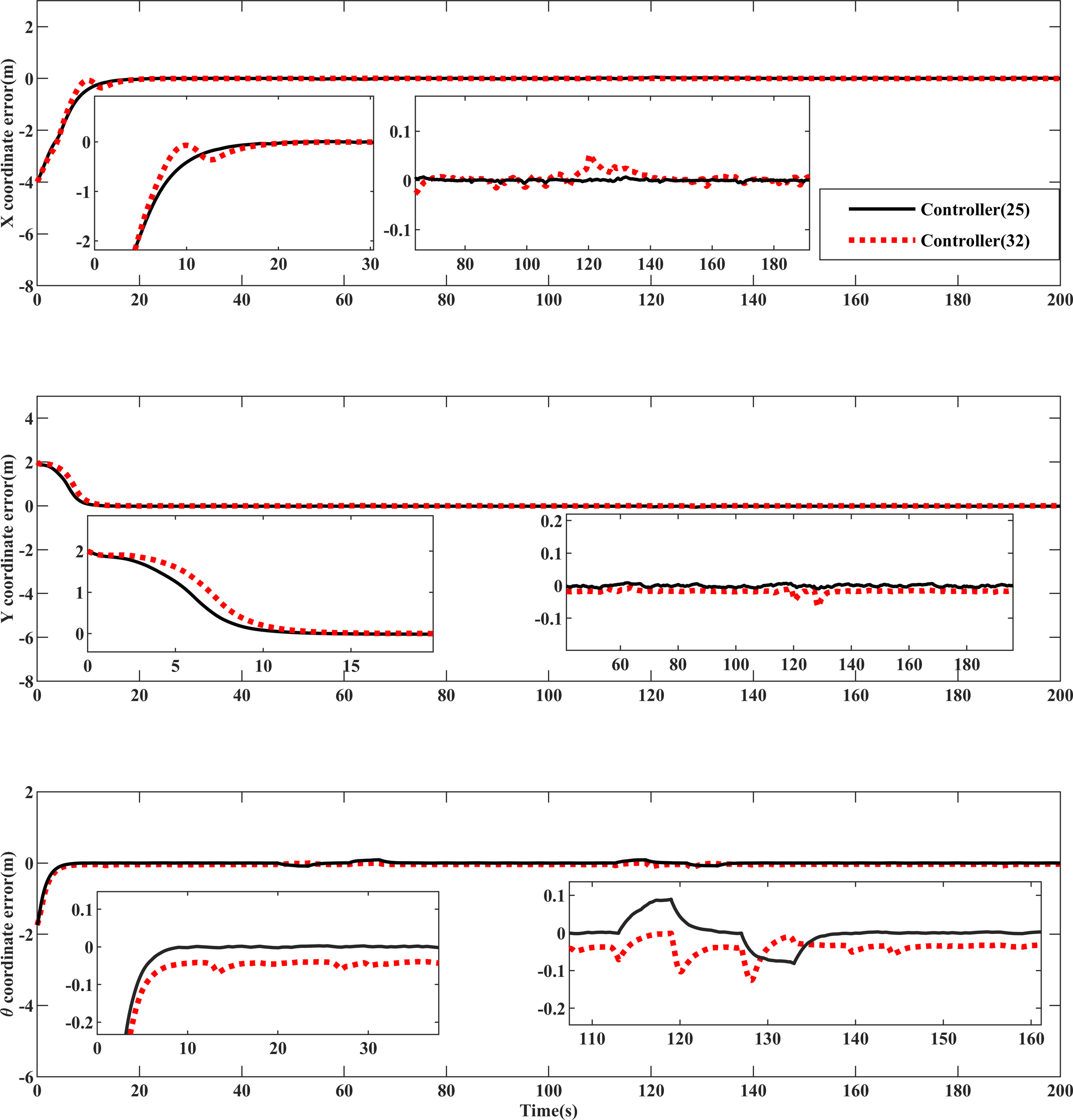
Comparison of position error convergence of USV equipment .
Figure 7
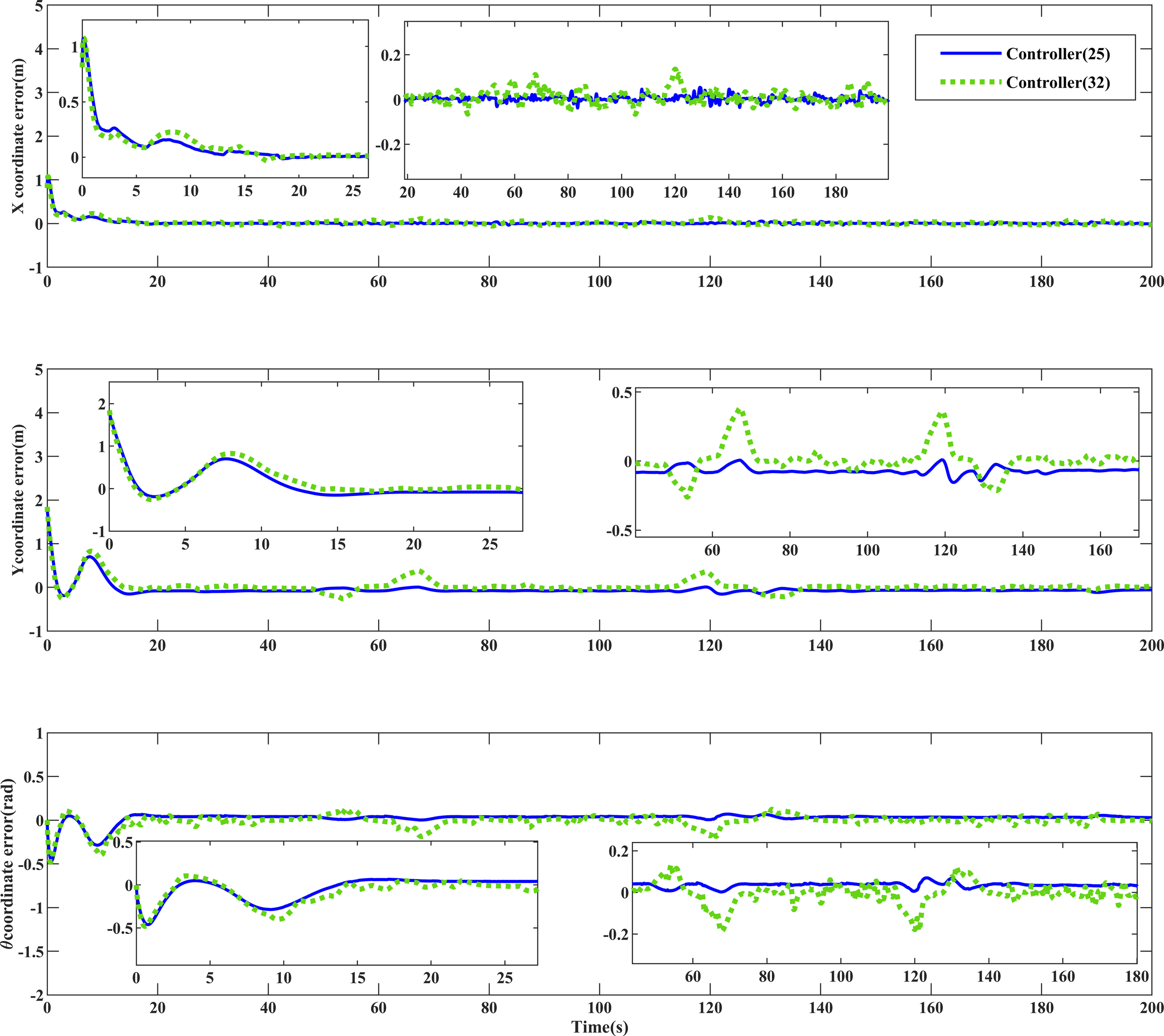
Convergence comparison of position error of ROV equipment .
Figure 8
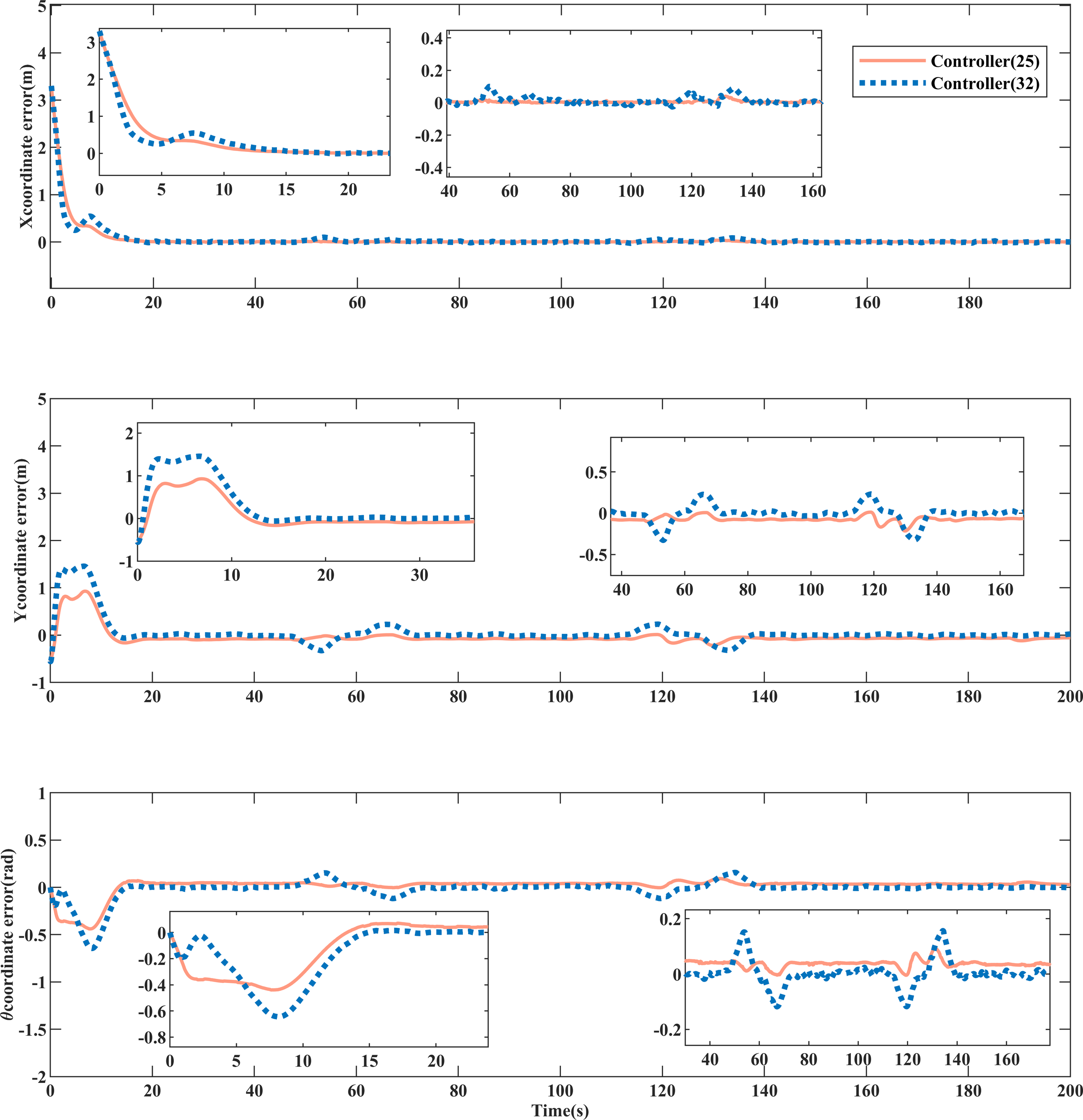
Convergence comparison of position error of ROV equipment .
Analyzing Figures 9–11 reveals that, in comparison to controller (32), controller (25) is more effective in reducing jitter. The sliding phase converges faster to the expectation , and during the sliding mode switching in the attack phase, controller (25) experiences less jitter under the influence of dynamic convergence law (24), achieving faster convergence and meeting design expectations. Taking 140-160s in Figures 10–12 as an illustration, the proposed method exhibits smaller jitter fluctuations and shorter convergence recovery response times compared to controller (32).
Figure 9
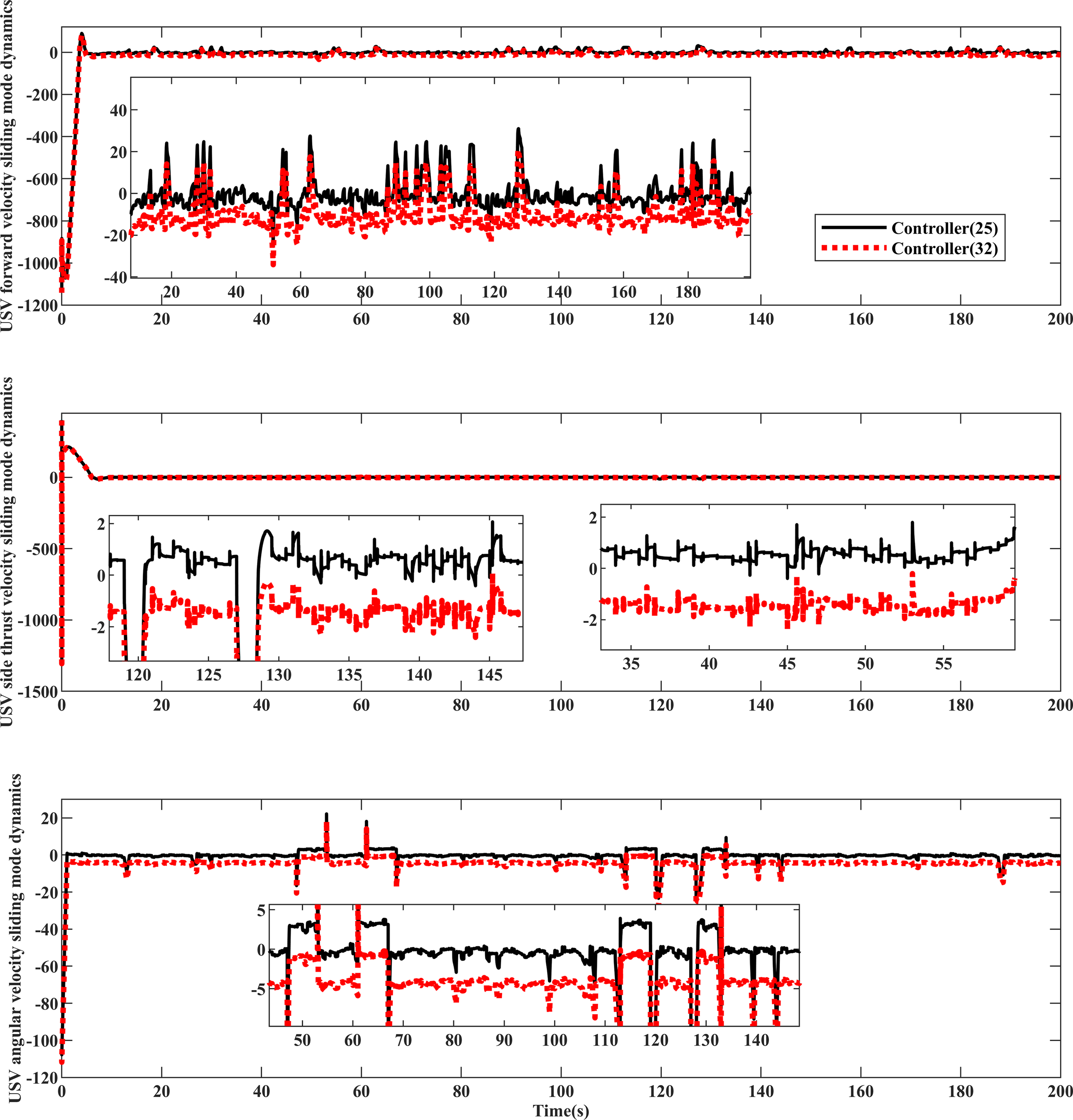
Dynamic comparison of sliding mode of USV equipment .
Figure 10
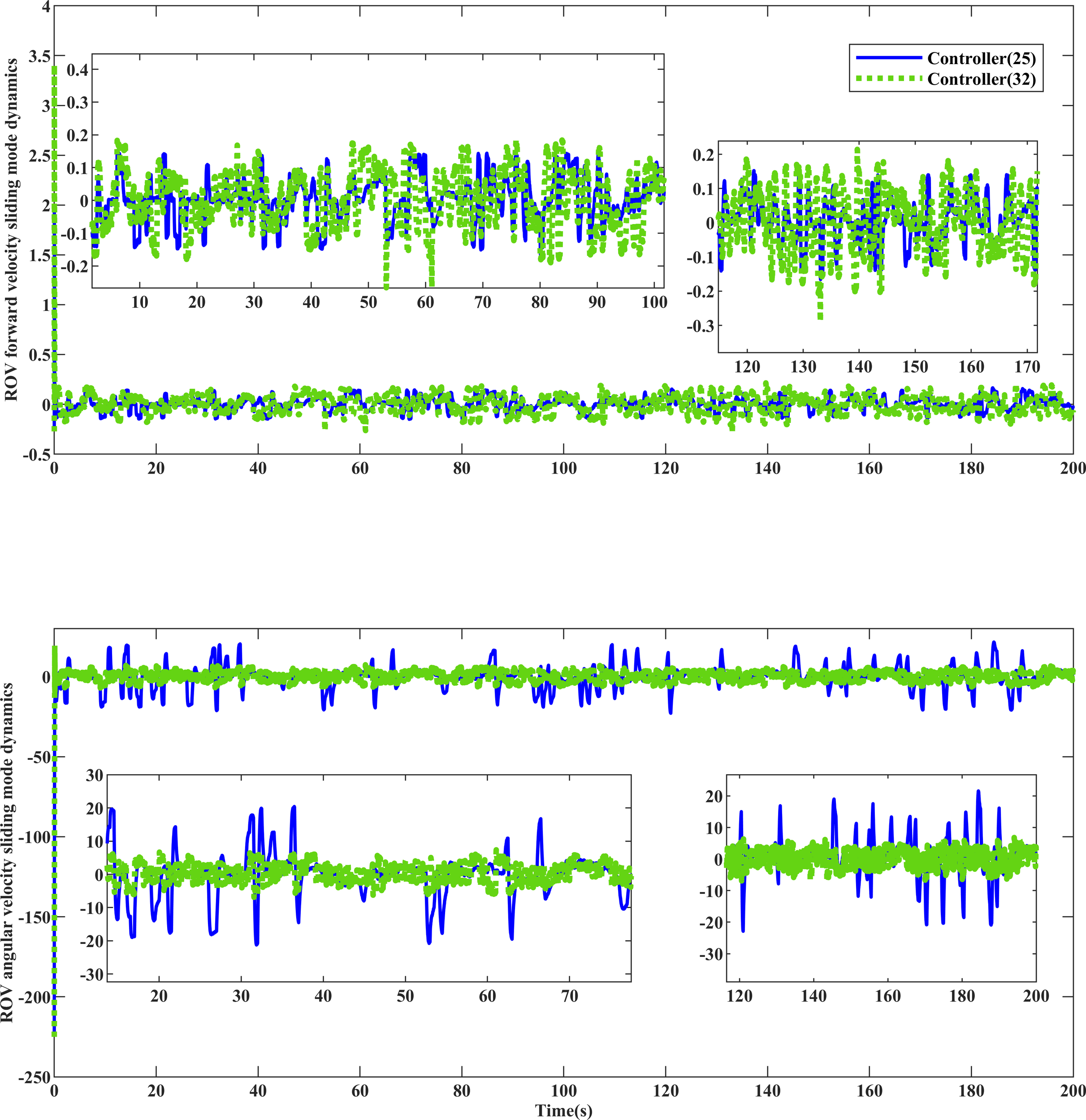
Dynamic comparison of sliding mode of ROV equipment .
Figure 11
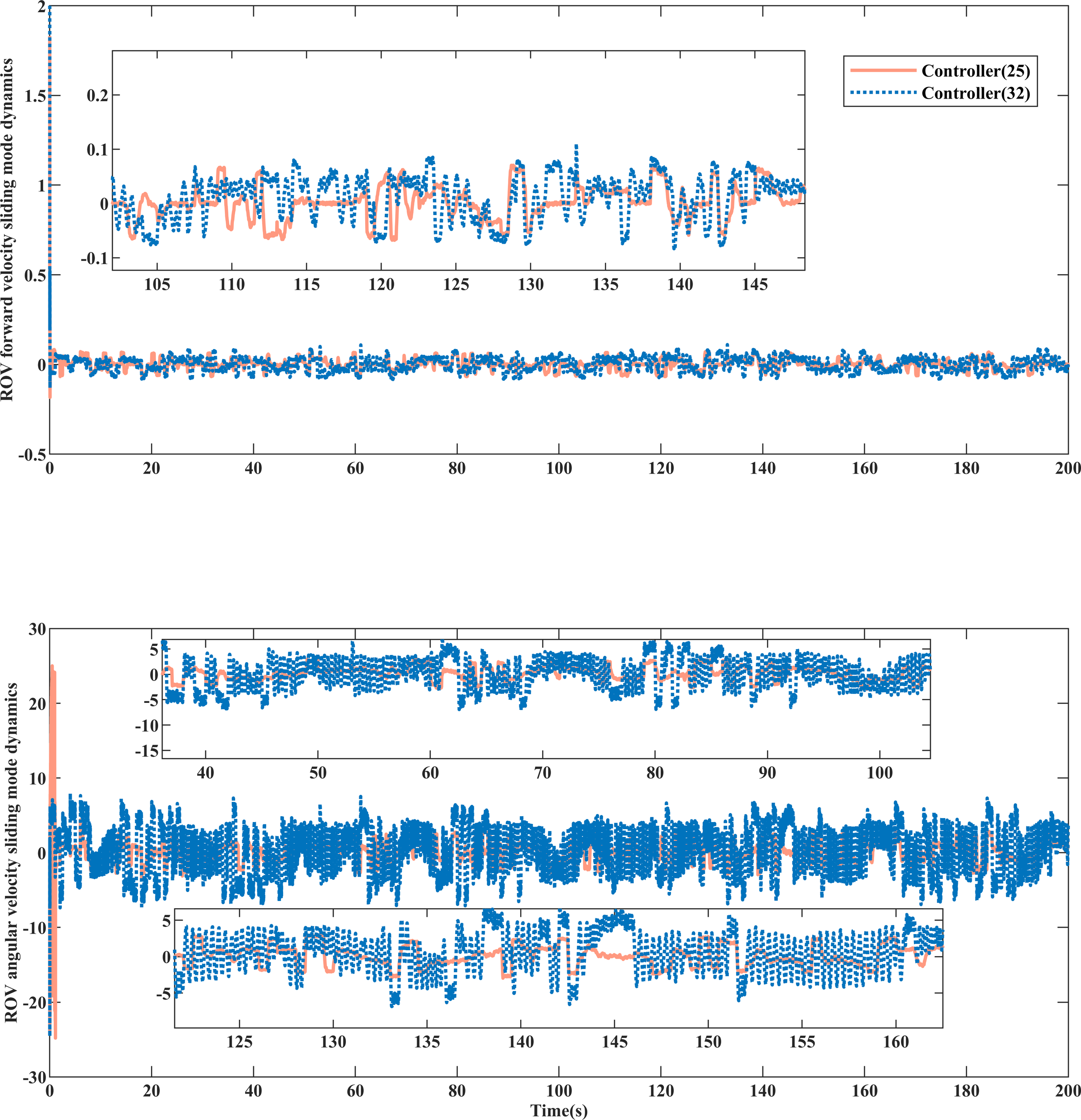
Dynamic comparison of sliding mode of ROV equipment .
Figure 12
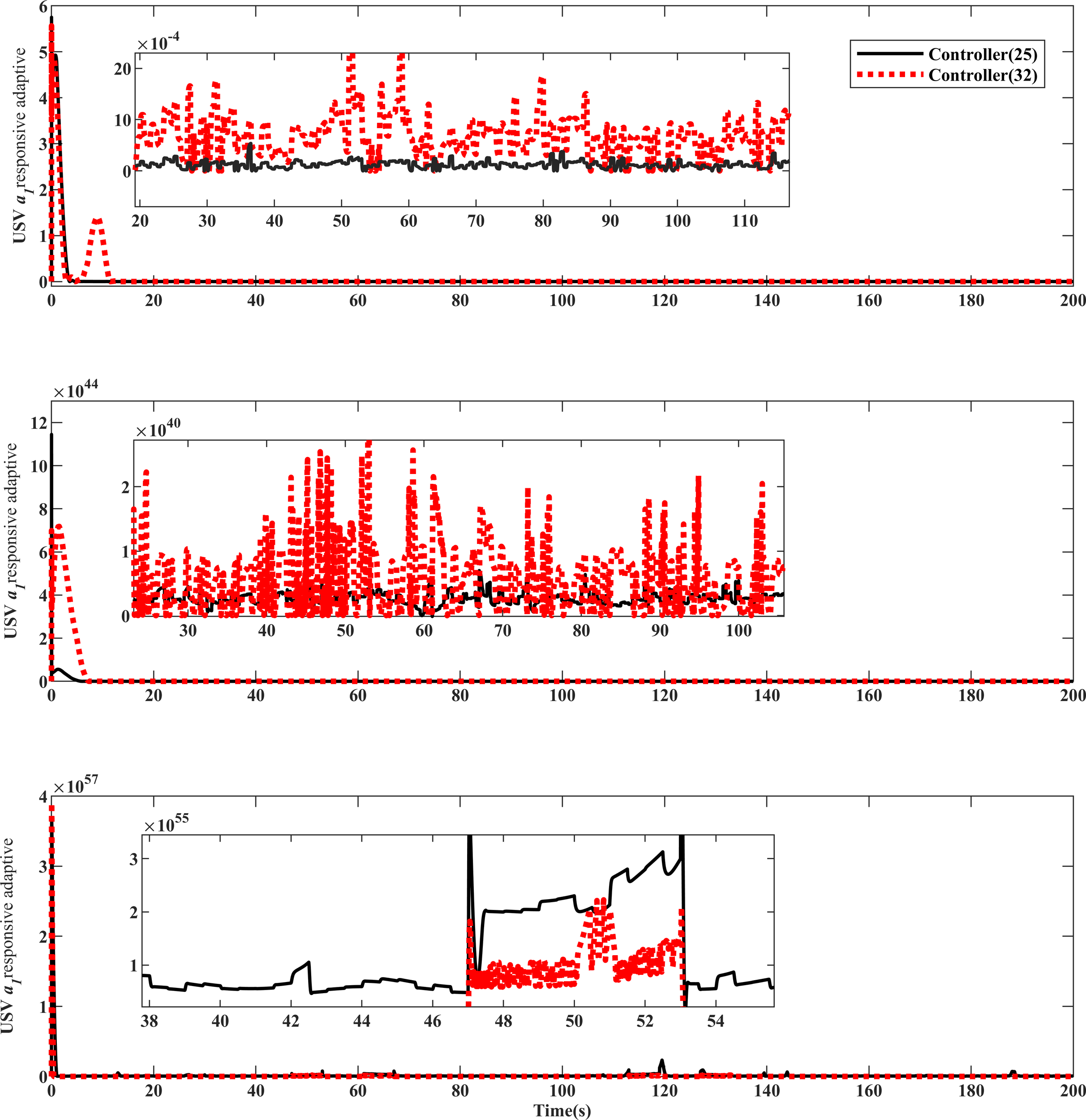
Comparison of adaptive approximation response of USV equipment .
Figures 12 , 13 illustrate that, in contrast to controller (32), controller (25) integrates the adaptive parameter estimator (26) designed by the RBF neural network with the influence of the minimum learning parameter. This integration establishes a virtual model for deceptive attacks and external disturbances, allowing for effective compensation of input anomalies. Controller (25) exhibits resistance against the continuous excitation of state changes, thereby countering the effects of deceptive attacks and disturbances.
Figure 13
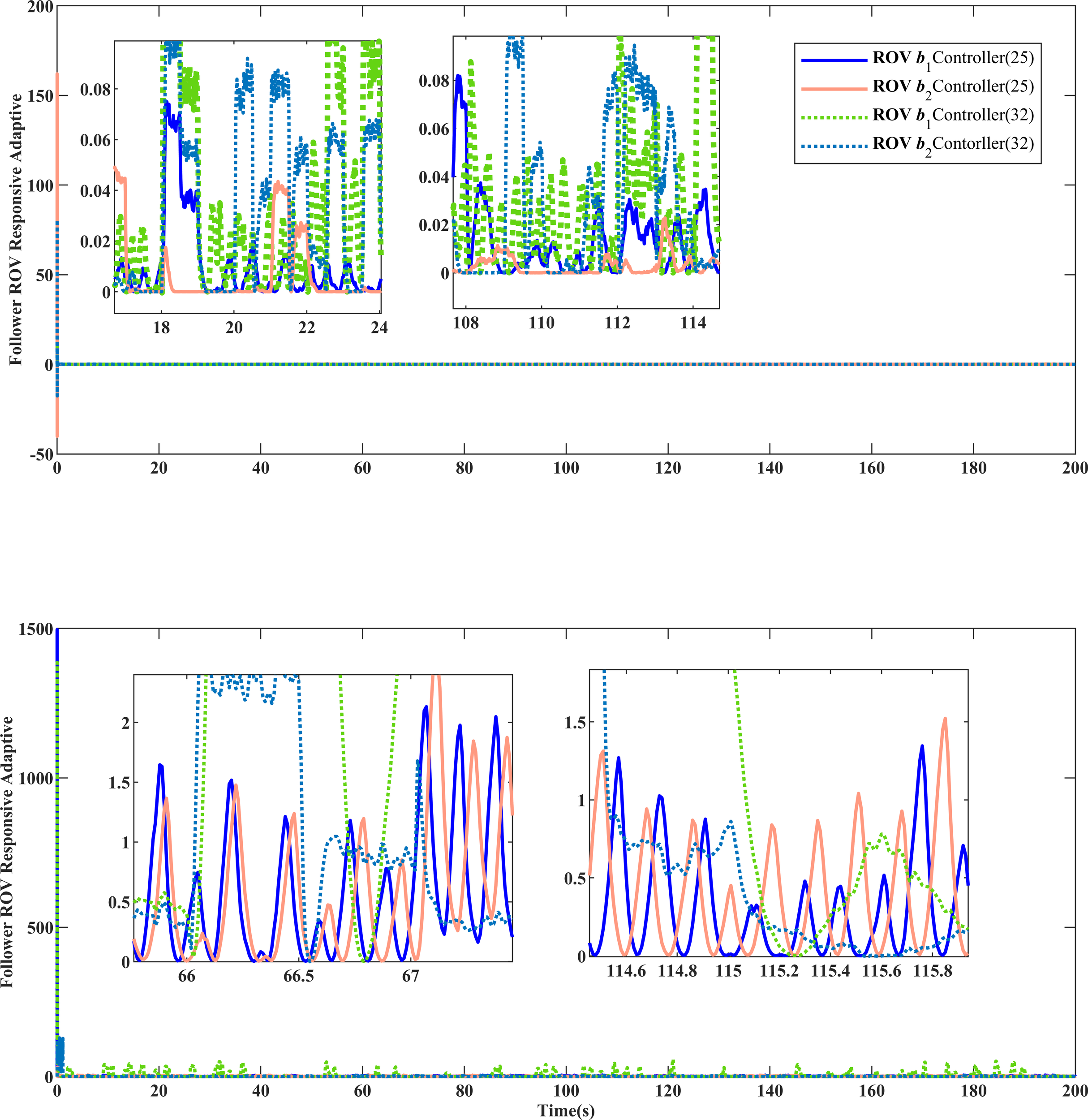
Comparison of adaptive approach response of ROV equipment.
Examining Figures 14–16 and the MIAC in Tables 2 and 3, let us consider the time interval of 50-100s. In comparison to controller (32), the input of the controller (25) proposed in this paper, despite being exposed to deceptive attacks, exhibits a smaller jitter range, fewer high-frequency spikes, conserves more control resources, and demonstrates superior control dynamics.
Figure 14
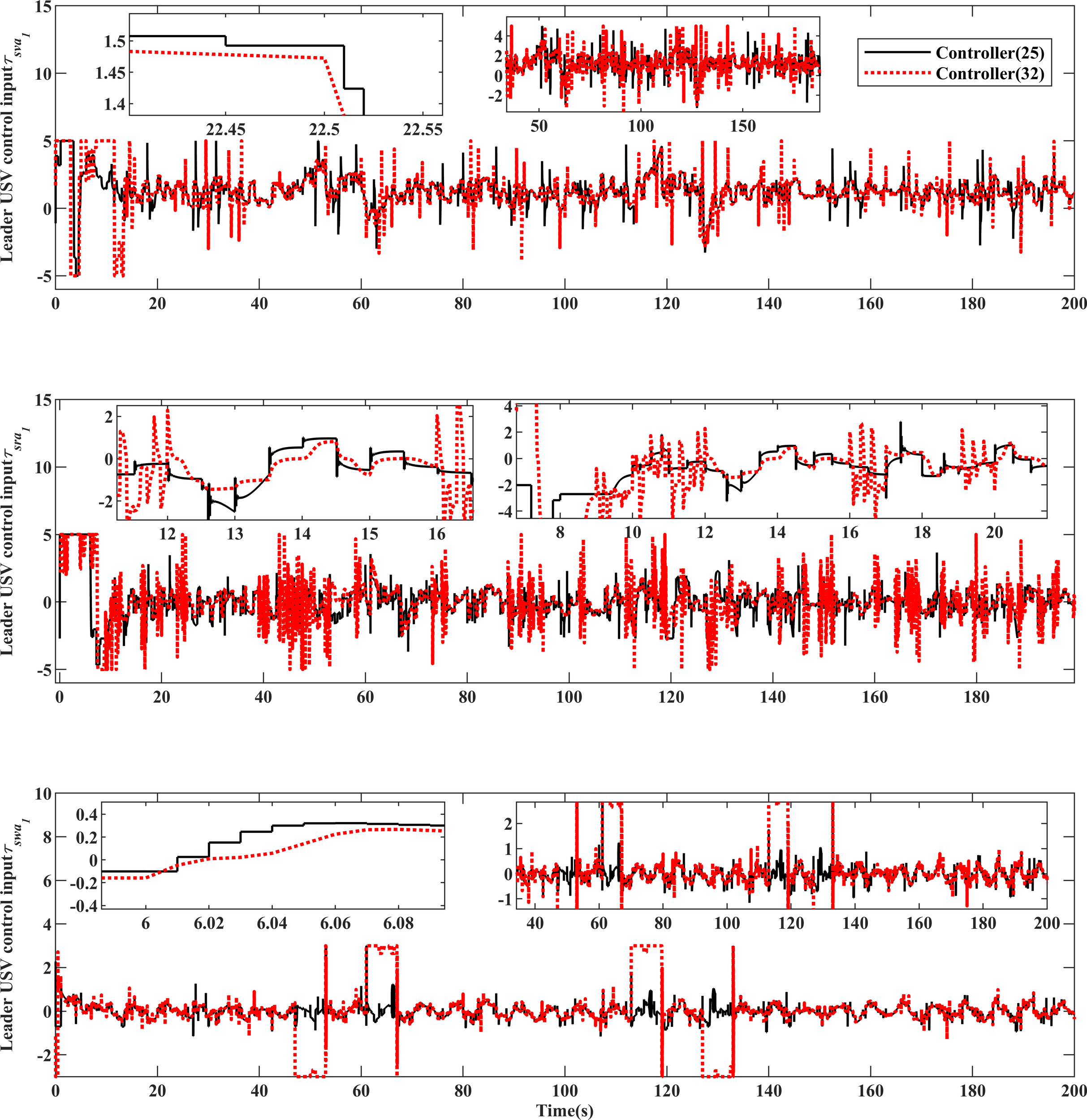
USV equipment system input comparison.
Figure 15

ROV equipment system input comparison.
Figure 16
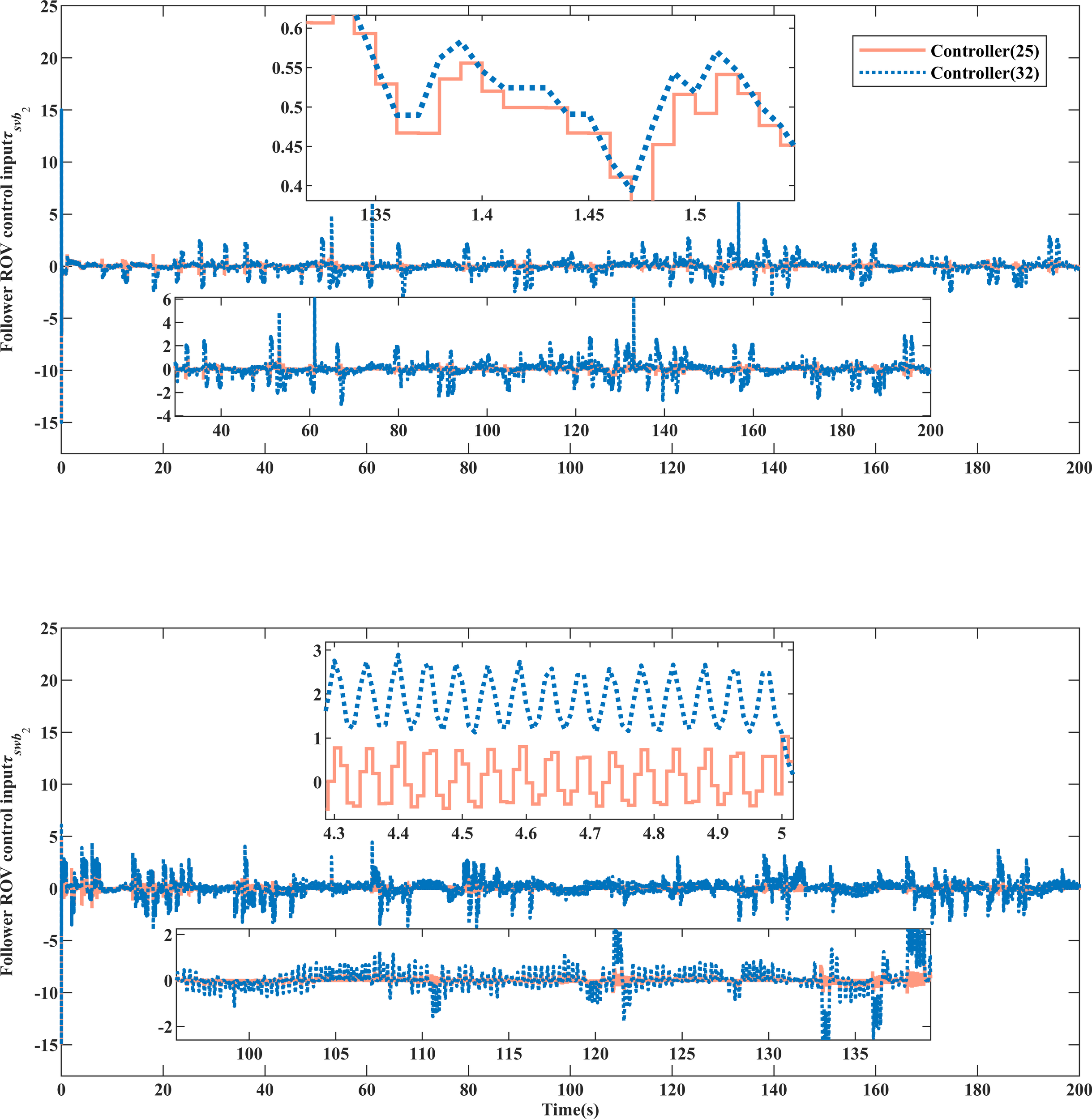
ROV equipment system input comparison.
Observing the MITV and transfer times in Tables 2 and 3, it is evident that controller (25), in contrast to controller (32), employs an event triggering mechanism with saturation characteristics to govern the controller output. This approach conserves approximately of control resources, enhancing control robustness within the rated power limit. Simultaneously, it improves transfer regulation performance, achieving superior control efficacy under deceptive attacks.
5 Conclusion
This paper addresses the control of USV-ROVs formation systems in the presence of deceptive data injection. A controller is designed considering dynamic uncertainties, deceptive attacks, unknown time-varying environmental disturbances, equipment matching disturbances, and input saturation constraints. First, a formation control scheme is designed to successfully realize the desired operational formation through geometric transformations. Then, a new terminal sliding mode surface is designed to solve the singularity problem of the terminal sliding mode surface while achieving global finite time convergence. After that, a new dynamic convergence law is designed to speed up the convergence response, optimize the sliding mode jitter problem, and ensure robustness under deceptive attacks. Finally, a new controller is designed using an event-triggered mechanism, RBF neural networks, and adaptive techniques to avoid the effects of deceptive attacks and uncertainty, save control resources, and enhance robustness. To verify the control stability of the algorithm under the influence of deceptive attacks, experiments were conducted using single USV and dual ROVs formation configurations. These results were then compared with the performance of a conventional sliding mode control algorithm. The experiments confirm the feasibility and superiority of the method proposed in this paper and ultimately demonstrate the effectiveness of the robust adaptive compensation mechanism against deceptive attacks.
Statements
Data availability statement
The original contributions presented in the study are included in the article/supplementary material. Further inquiries can be directed to the corresponding author.
Author contributions
QZ: Writing – review & editing. SZ: Writing – original draft. YL: Writing – review & editing. YZ: Writing – review & editing. YH: Writing – review & editing.
Funding
The author(s) declare financial support was received for the research, authorship, and/or publication of this article. The research carried out in this paper was mainly supported by the Shandong Provincial Natural Science Foundation grant (No. ZR2022ME087) and partly supported by the Shandong Provincial Science and Technology Department of Science and Technology Small and Medium-sized Enterprises Innovation Capacity Enhancement Project (No. 2021TSGC1394), as well as being partly supported by the project (No. 2022KJ210) in the Shandong province colleges and universities “Youth Innovation Team Plan”.
Acknowledgments
The authors would like to express their sincere gratitude to Qiyu Chen and Gaoyang Guo for their valuable comments during the writing of the paper, and to the reviewers for their positive and constructive comments.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1
Chen Q. Zhang Q. Hu Y. Liu Y. Wu H. (2023). Euclidean distance damping–based adaptive sliding mode fault-tolerant event-triggered trajectory-tracking control. Proc. Institution Mechanical Engineers Part I: J. Syst. Control Eng.237 (3), 551–567. doi: 10.1177/09596518221126584
2
Chen W. Ding D. Dong H. Wei G. (2019). Distributed resilient filtering for power systems subject to denial-of-service attacks. IEEE Trans. Systems Man Cybernetics: Syst.49 (8), 1688–1697. doi: 10.1109/TSMC.2019.2905253
3
Ding L. Guo G. (2012). Formation control for ship fleet based on backstepping. Control Decision27 (2), 299–303.
4
Ding D. Wang Z. Ho D. W. Wei G. (2016). Observer-based event-triggering consensus control for multiagent systems with lossy sensors and cyber-attacks. IEEE Trans. cybernetics47 (8), 1936–1947. doi: 10.1109/TCYB.2016.2582802
5
Fan Y. Liu B. Wang G. Mu D. (2021). Adaptive fast non-singular terminal sliding mode path following control for an underactuated unmanned surface vehicle with uncertainties and unknown disturbances. Sensors21 (22), 7454. doi: 10.3390/s21227454
6
Fu M. Y. Wang D. S. Wang C. L. (2018). Formation control for water-jet USV based on bio-inspired method. China Ocean Engineering. 32, 117–122. doi: 10.1007/s13344-018-0013-1
7
Gao H. Song Y. Wen C. (2016). Backstepping design of adaptive neural fault-tolerant control for MIMO nonlinear systems. IEEE Trans. Neural Networks Learn. Syst.28 (11), 2605–2613. doi: 10.1109/TNNLS.2016.2599009
8
Huang X. Dong J. (2019). Reliable control of cyber-physical systems under sensor and actuator attacks: An identifier-critic based integral sliding-mode control approach. Neurocomputing361, 229–242. doi: 10.1016/j.neucom.2019.06.069
9
Ito T. Takanami I. (1997). “On fault injection approaches for fault tolerance of feedforward neural networks,” in Proceedings sixth asian test symposium (ATS'97). 88–93 (IEEE).
10
Jin X. (2018). Fault-tolerant iterative learning control for mobile robots non-repetitive trajectory tracking with output constraints. Automatica94, 63–71. doi: 10.1016/j.automatica.2018.04.011
11
Kang Z. Yu H. Li C. (2020). Variable-parameter double-power reaching law sliding mode control method. Automatika61 (3), 345–351. doi: 10.1080/00051144.2020.1757965
12
Li X. Wen C. Wang J. Xing L. Li X. (2022). Jamming-resilient synchronization of networked lagrangian systems with quantized sampling data. IEEE Trans. Ind. Inf.18 (12), 8724–8734. doi: 10.1109/TII.2022.3148395
13
Li J. Zhang G. Shan Q. Zhang W . (2023a). A novel cooperative design for USV-UAV systems: 3-D mapping guidance and adaptive fuzzy control. IEEE Trans. Control Network Systems.10 (2), 564–574. doi: 10.1109/TCNS.2022.3220705
14
Li J. Zhang G. Zhang W. Shan Q. Zhang W . (2023b). Cooperative path following control of USV-UAVs considering low design complexity and command transmission requirements. IEEE Trans. Intelligent Vehicles. doi: 10.1109/TIV.2023.3317336
15
Lin A. Jiang D. Zeng J. (2018). Underactuated ship formation control with input saturation. Acta Autom. Sin.33, 1496–1504.
16
Liu J. Wang Y. Cao J. Yue D. Xie X. (2020). Secure adaptive-event-triggered filter design with input constraint and hybrid cyber attack. IEEE Trans. Cybernetics51 (8), 4000–4010. doi: 10.1109/TCYB.2020.3003752
17
Min H. Xu S. Zhang Z. (2020). Adaptive finite-time stabilization of stochastic nonlinear systems subject to full-state constraints and input saturation. IEEE Trans. Automatic Control66 (3), 1306–1313. doi: 10.1109/TAC.2020.2990173
18
Saihi L. Ferroudji F. Berbaoui B. Bakou Y. Koussa K. Meguellati F. et al . (2019). “Hybrid control based on sliding mode fuzzy of DFIG power associated WECS,” in AIP conference proceedings, vol. 2123, No. 1). (AIP Publishing).
19
Sandberg H. Amin S. Johansson K. H. (2015). Cyberphysical security in networked control systems: An introduction to the issue. IEEE Control Syst. Magazine35 (1), 20–23. doi: 10.1109/MCS.2014.2364708
20
Shi J. Zhou D. Yang Y. Sun J. (2018a). Fault tolerant multivehicle formation control framework with applications in multiquadrotor systems. Sci. China Inf. Sci.61, 1–3. doi: 10.1007/s11432-018-9486-3
21
Shi J. Zhou D. Yang Y. Sun J. (2018b). Fault tolerant multivehicle formation control framework with applications in multiquadrotor systems. Sci. China Inf. Sci.61, 1–3. doi: 10.1007/s11432-018-9486-3
22
Skjetne R. Fossen T. I. Kokotović P. V. (2005). Adaptive maneuvering, with experiments, for a model ship in a marine control laboratory. Automatica41 (2), 289–298. doi: 10.1016/j.automatica.2004.10.006
23
Sun R. Wang J. Zhang D. Shao X. (2018). Neural network-based sliding mode control for atmospheric-actuated spacecraft formation using switching strategy. Adv. Space Res.61 (3), 914–926. doi: 10.1016/j.asr.2017.11.011
24
Swaszek P. F. Hartnett R. J. Kempe M. V. Johnson G. W. (2013). “Analysis of a simple, multi-receiver GPS spoof detector,” in Proceedings of the 2013 international technical meeting of the institute of navigation, 884–892.
25
Tian Y. Cai Y. Deng Y. (2020). A fast nonsingular terminal sliding mode control method for nonlinear systems with fixed-time stability guarantees. IEEE Access8, 60444–60454. doi: 10.1109/ACCESS.2020.2980044
26
Wang W. Han Z. Liu K. Lü J. (2021). Distributed adaptive resilient formation control of uncertain nonholonomic mobile robots under deception attacks. IEEE Trans. Circuits Syst. I: Regular Papers68 (9), 3822–3835. doi: 10.1109/TCSI.2021.3096937
27
Wu Y. Wang Y. (2020). Asymptotic tracking control of uncertain nonholonomic wheeled mobile robot with actuator saturation and external disturbances. Neural Computing Appl.32 (12), 8735–8745. doi: 10.1007/s00521-019-04373-9
28
Wu C. Wu L. Liu J. Jiang Z. P. (2019). Active defense-based resilient sliding mode control under denial-of-service attacks. IEEE Trans. Inf. Forensics Secur.15, 237–249. doi: 10.1109/TIFS.2019.2917373
29
Xu H. Cui G. Ma Q. Li Z. Hao W. (2023). Fixed-time disturbance observer-based distributed formation control for multiple QUAVs. IEEE Trans. Circuits Syst. II: Express Briefs. doi: 10.1109/TCSII.2022.3233438
30
Xu X. P. Yan X. T. Yang W. Y. An K. Huang W. Wang Y. (2022). Algorithms and applications of intelligent swarm cooperative control: A comprehensive survey. Prog. Aerospace Sci.135, 100869. doi: 10.1016/j.paerosci.2022.100869
31
Yang G. Y. Chen S. Y. (2020). Piecewise fast multi-power reaching law: Basis for sliding mode control algorithm. Measurement Control53 (9-10), 1929–1942. doi: 10.1177/0020294020964246
32
Yin T. Gu Z. Park J. H. (2022). Event-based intermittent formation control of multi-UAV systems under deception attacks. IEEE Trans. Neural Networks Learn. Systems. doi: 10.1109/TNNLS.2022.3227101
33
Yun L. Ying J. (2016). Combination of leader-follower method and potential function about ship formation control. Control Theory Appl. 33, 1259–1264.
34
Zhang G. Zhang X. (2015). A novel DVS guidance principle and robust adaptive path-following control for underactuated ships using low frequency gain-learning. ISA Trans.56, 75–85. doi: 10.1016/j.isatra.2014.12.002
35
Zhang G. Liu S. Zhang X. (2022). Adaptive distributed fault-tolerant control for underactuated surface vehicles with bridge-to-bridge event-triggered mechanism. Ocean Eng.262, 112205. doi: 10.1016/j.oceaneng.2022.112205
36
Zhang D. W. Liu G. P. (2023). Predictive sliding-mode control for networked high-order fully actuated multiagents under random deception attacks. IEEE Trans. Systems Man Cybernetics: Systems. doi: 10.1109/TSMC.2023.3311438
37
Zhu G. Du J. (2018). Global robust adaptive trajectory tracking control for surface ships under input saturation. IEEE J. Oceanic Eng.45 (2), 442–450. doi: 10.1109/JOE.2018.2877895
Summary
Keywords
cooperative formation, USV, ROVs, deceptive attack, sliding mode control
Citation
Zhang Q, Zhang S, Liu Y, Zhang Y and Hu Y (2024) Adaptive terminal sliding mode control for USV-ROVs formation under deceptive attacks. Front. Mar. Sci. 11:1320361. doi: 10.3389/fmars.2024.1320361
Received
12 October 2023
Accepted
16 January 2024
Published
08 February 2024
Volume
11 - 2024
Edited by
Xinyu Zhang, Dalian Maritime University, China
Reviewed by
Yong Ma, Wuhan University of Technology, China
Nitin Agarwala, National Maritime Foundation, India
Zhang Guichen, Shanghai Maritime University, China
Guoqing Zhang, Dalian Maritime University, China
Updates
Copyright
© 2024 Zhang, Zhang, Liu, Zhang and Hu.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Yang Liu, godkissyou@126.com
Disclaimer
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.