- 1Department of Mathematical Sciences, Faculty of Science and Technology, Fatima Jinnah Women University, Rawalpindi, Pakistan
- 2Capital University of Science and Technology, Islamabad, Pakistan
- 3CES Laboratory, National School of Engineers of Sfax, University of Sfax, Sfax, Tunisia
- 4Computer Science Department, Prince Sultan University, Riyadh, Saudi Arabia
Network communications are expanding rapidly in many fields, including telecommunications, the Internet of Things, space, consumer electronics, and the military, with different privacy and security issues at stake in each of these areas. The Internet of Things (IoT) has drawn increased attention from academic and industrial researchers over the last few decades. In this environment, keys are routinely exchanged through a public protocol to support the highly secure IoT domain and thwart security threats from unauthorized parties. The environment for IoT devices is subject to numerous limitations, including those related to processing, memory, and energy. These devices need to pass through a gateway or sink to connect to the network. Additionally, the environment must enable secure communication between gateways and IoT devices, even when the devices are disconnected from the rest of the network. In this paper, a lightweight key exchange protocol for IoT environments is presented, allowing the gateway and the IoT device to communicate over an open channel. Our proposed protocol improves security by utilizing noncommutative structures and polynomials over noncommutative rings. The underlying idea is to use the generalized decomposition problem associated with noncommutative rings. Furthermore, how the suggested protocol can achieve key certification and perfect onward secrecy is addressed. Results show this protocol is a strong candidate for key sharing and secure communication between IoT devices. We put our methodology into practice and the results of our experiments demonstrate enhancement of security levels. Finally, the performance analysis of the suggested protocol is compared with some other protocols, in terms of security, communication, and computing overhead.
1 Introduction
The Internet-of-Things (IoT) is an environment that enables interconnected devices and human beings to communicate and send one another information. The use of the IoT environment is growing and is increasingly prevalent in our lives. Many applications depend on functionalities that use information collected from IoT devices: monitoring patient health records, for example. Sometimes it is necessary to send large amounts of data over open wireless channels, such as heavy videos or large image files. In all these situations, the communication of data must be secured and authenticated.
In the IoT environment, the gateway/sink is the main object through which the rest of the environment’s devices communicate. We thus require secure and authenticated communication between the IoT device and the gateway/sink. However, traditional key exchange protocols cannot be employed for this purpose due to several constraints. These constraints involve dependence on a trusted third party (TTP) and high processing requirements. It is also essential for IoT environments to be capable of operating even in disconnected mode, without access to a TTP.
The authentication and key exchange processes between two entities without a TTP requires a prior shared secret. Additionally, it is important to eradicate the chance of disclosure of that secret in the environment. We therefore look for more than one secret key, each of which is used for a different purpose. The most important requirement for the implementation of a protocol is to have Perfect Forward Secrecy (PFS). PFS is a feature of a key exchange protocol that ensures the secrecy of all previous session communications in the event of any leakage of a long-term private key. This situation can be controlled by using a different key for every session. If the cryptanalyst can somehow extract the session key, that key does not contain any information about further sessions. This is one of the motivations for our proposed key exchange protocol for the IoT environment. The digital certification of IoT devices depicting the authentication is another salient feature of the IoT environment, which our proposal also addresses.
There is a vast literature suggesting various new techniques, as well as case studies of new technologies and solutions (Ko et al., 2000; Sakalauskas and Burba, 2003; Cheikhrouhou et al., 2020; Zhongjun et al., 2022). In 2017, the National Institute of Standards and Technology (NIST) started an evaluation procedure of cryptographic techniques that can resist quantum attacks. Most of today’s cryptosystems currently relying on integer factorization (Rivest et al., 1978) and discrete logarithms (ElGamal, 1985) will become obsolete because of the Shor algorithm (Shor, 1997). Given the quantum threats, there is an increasing trend toward developing new technologies known as quantum key distribution (QKD) (Bennett and Brassard, 1984; Center, 2021; Lizama-P´erez et al., 2021). Seven algorithms have been selected by NIST: four are public key cryptosystems and concern key establishment, and three are related to digital signature algorithms. That is why the active area of research is now noncommutative algebraic cryptography (Anshel et al., 1999; Ko et al., 2000; Paeng et al., 2001; Sakalauskas and Burba, 2003; Inam and Ali, 2016; Kanwal and Ali, 2016). The main focus of this area is to develop and analyze cryptographic protocols over noncommutative structures.
The use of noncommutative structures for public key exchange has been examined by several authors. Here we provide a brief overview of these protocols. In their proposals, Anshel et al. (1999) and Ko et al. (2000) suggested using braid groups as the underlying structure for achieving a good level of security. Thomas and Lal (2008) then proposed a public key cryptographic protocol whose security depends on the discrete log problem (DLP) of the inner automorphism. The main strength of this protocol is the difficulty of finding the conjugate element in a noncommutative group.
The use of a public key cryptographic model was highlighted by Shpilrain and Ushakov (2006), who introduced the difficulty of solving the symmetrical decomposition problem. Thomas and Lal (2008) then proposed a cryptosystem based on the symmetric decomposition problem and conjugacy search problems over a noncommutative structure. For their part, Anjaneyulu and Sanyasirao (2014) generated a common key or group key using the polynomial symmetric decomposition problem. Their proposal was based on the polynomial symmetric decomposition problem over noncommutative division semi-rings.
Furthermore, Meshram et al. (2017) proposed a new IND-CCA2 secure public-key cryptographic protocol. They used the integral coefficient ring polynomial concept with the Suzuki 2-group as the underlying work structure. Odoni et al. (1984) previously discussed the DLP for the ring of matrices. Similarly, the Diffie-Hellman protocol for different matrix rings was presented in Stickel (2005) and Alvarez et al. (2009). In 2004, Stickel (2005) proposed a public key exchange scheme using matrices in a particular subgroup. However, Sramka (2022) highlighted some weaknesses in the scheme, and Shpilrain (2008) provided a cryptanalysis of the scheme, suggesting that it would be more secure to work with a semigroup of all matrices over some finite ring as a platform for the scheme. He also provided a modified method for exchanging a shared secret key. However, Mullan (2012) successfully mounted a linear algebra attack against Shpilrain’s modifications of Stickel’s scheme.
A broad literature is available concerning key exchange protocols for IoT and their weaknesses (Mano et al., 2016; Khan and Salah, 2018; Mutlag et al., 2019; Lizama-Perez and López, 2021). The first public key exchange was proposed by Diffie and Hellman (1976). After that, there followed an extensive list of public key exchange protocols, which can be found in the literature: for example, Menezes et al. (1996); Schneier (1996); Singh et al. (2017); and the references therein. Abdalla et al. (2005) proposed a three-party password-authenticated key exchange (3PAKE) protocol for wireless mobile communications. Lu and Cao (2007) modified the 3PAKE protocol, and Chung and Ku (2008) consequently indicated that these protocols were vulnerable to attack by impersonation.
Further, Guo et al. (2008) proved that Anjaneyulu and Sanyasirao (2014)’s improvement of the protocol of Chang et al. (2011) had no security against the replay attack. Chang et al. (2011) and Yoon and Yoo (2011) developed a protocol independent of a symmetrical type of algorithm. In this present study, an improved public key exchange protocol is proposed over the noncommutative ring for IoT devices. The main idea of our proposal is to take polynomials over a given noncommutative ring as useful for secure communication in the pre-and post-quantum age. It is also shown that the brute force attack leads to the solution of the generalized decomposition problem, rendering it infeasible. The rest of this manuscript is organized as follows:
Section 2 provides a brief overview of the security challenges and requirements of the IoT environment. Section 3 gives the basic definitions of related cryptographic problems over noncommutative structures. The proposed protocol is presented in Section 4. We also discuss security aspects of the proposed protocols. The guaranteed secrecy of the new session keys achieved by the perfect forward security method is described in Section 5. Section 6 describes a procedure to certify the public keys across inter-domain certificates. The experimental results and discussion of computational cost are covered in Section 7. Finally, the conclusion of the work is drawn in Section 8.
2 Security challenges of IoT environments
It is a highly challenging task to achieve proper levels of security in an IoT environment. These environments are vulnerable to potential attacks, such as user privacy and data integrity attacks. The physical failure of IoT devices and malicious invasions are other potential issues involved. The interconnected devices are usually resource-limited, with inadequate storage capability and energy, which is why IoT environments are sensitive to various threats. Thus, critical IoT data may be blocked and changed, with unrecoverable financial and security consequences. To protect the IoT against attacks, while keeping in mind the memory size and computation power of devices (Alohali and Vassialkis, 2015) in IoT environments, advanced protocols and algorithms need to be evolved. For robust security of the IoT environment, data integrity is also necessary, because a large amount of data has to be processed and managed, and therefore the security of data exposure is essential.
2.1 Security risks and secure design requirements for the IoT environment
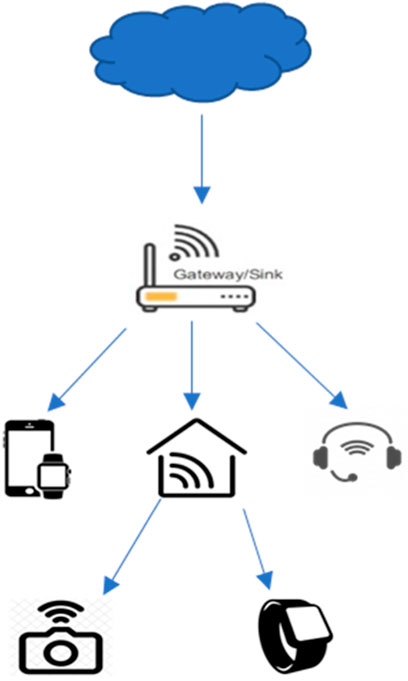
The environment under consideration consists of a collection of wireless nodes (devices) having sensing elements. These devices, known as things, are structured into groups. There is a node called a gateway in each group responsible for connecting to the rest of the network. The gateway (GW) may connect with other gateways in the network, and all gateways may be connected to the main server. The data generated by different things are deposited on the main server. There are two main related risks. First, there is the risk of someone eavesdropping on the traffic of the data and of traffic analysis, which may result in the disruption of the whole network. To overcome this risk, secure communication is needed between the nodes. Second, there is always the risk of the physical destruction or imprisonment of nodes. Given these risks, the following security requirements are essential:
• The things should be authenticated when they request to join the network.
• The gateways should forward data only from authenticated things.
• There should be complete privacy of communication between the things and the server.
• If possible, confidential information should not be put on any one individual thing.
Figure 1 shows a simple example of an IoT environment. Note that a thing may connect or leave the network at any time. Our proposal is based on the needs described above. The main aim is to guarantee the authentication of a thing without significant effect on the network and the provided facilities.
3 Background definitions
This section describes different problems involved in the security of noncommutative group-based cryptography. For instance, Diffie and Hellman (1976) and the Birman et al. (1998) used the conjugator search problem in braid groups to develop their approach. A new Diffie-Hellman-like protocol and ElGamal-like cryptosystem were proposed in Cao et al. (2007). These proposals are based on the symmetric decomposition and generalized symmetric decomposition problems over noncommutative groups. The details of these problems are given as follows.
3.1 Definition 1: Conjugator search problem (CSP)
Let
is known as the conjugator search problem.
3.2 Definition 2: Decomposition problem (DP)
Let
is known as the decomposition problem (Cao et al., 2007).
Generally, for a noncommutative group, the two problems CSP and DP are considered difficult enough given the cryptographic assumptions. More specifically, the DP is intractable, meaning that no probabilistic polynomial-time algorithm is used to solve the DP with nonnegligible accuracy.
3.3 Definition 3: Symmetric decomposition problem (SDP)
Let
is known as the symmetric decomposition problem.
3.4 Definition 4: Generalized symmetric decomposition problem (GSDP)
Let
is known as the generalized symmetric decomposition problem.
Given these problems, we now define the following cryptographic problem over a noncommutative group
3.5 Definition 5: Generalized decomposition problem (GDP)
Let
is called the generalized decomposition problem.
Note that the GDP can be considered a special form of a constrained DP. If the size of sets
We now give a variant of the GDP over a noncommutative ring R and name it as the polynomial generalized decomposition problem (PGDP).
3.6 Definition 6: Polynomial generalized decomposition problem (PGDP)
Let
Let
is known as the polynomial generalized decomposition problem.
So, the PGD (polynomial generalized decomposition) cryptographic assumption states that the PGDP over R is intractable, which means there is no probabilistic polynomial-time algorithm that can solve the PGDP with nonnegligible accuracy.
We are going to use the PGDP in our proposed key exchange protocols as described in the following section.
4 Proposed protocol for generation and distribution of keys
In order to increase security, we present a protocol that offers a novel authentication mechanism. It is more efficient and cost effective. The performance analysis of the suggested work is validated and compared with the current protocols in terms of security, communication, and computing overhead.
We now demonstrate the main structure of the proposed protocol for a group
It selects a noncommutative ring
• A random polynomial
• Small numbers (for instance, less than 10 (Cao et al., 2007))
• The gateway generates the key for each device as follows:
• The
The following steps would be executed for sharing a secret key between
•
• j
The correctness of the proposed protocol is shown in Theorem 1.
Theorem 1:. Keeping in mind the specified notation, it follows that the shared secret keys obtained by both entities are the same, that is
Proof
First, consider the expression
that becomes by using (1),
Expression (3) gives
Since the coefficients of the polynomials are from the center
Using this property successively, we have
Given property (6), expressions (5) and (6) are the same.
It is obvious that for the proposed public key exchange protocol, the passive attack can be resisted with the PGD assumption over the noncommutative ring.
4.1 Device authentication
After getting the key by the gateway, the
• A random polynomial
• Small numbers (for instance, less than 10 [9])
• The device generates the key
If
wants to communicate with the
• The sender device
to the device
• The device
where
If
then device
4.2 Choice of parameters
Suppose we take the ring of matrices of order 2 over
For a brute force attack, one has to check all the polynomials whose coefficients come from the set
The values of
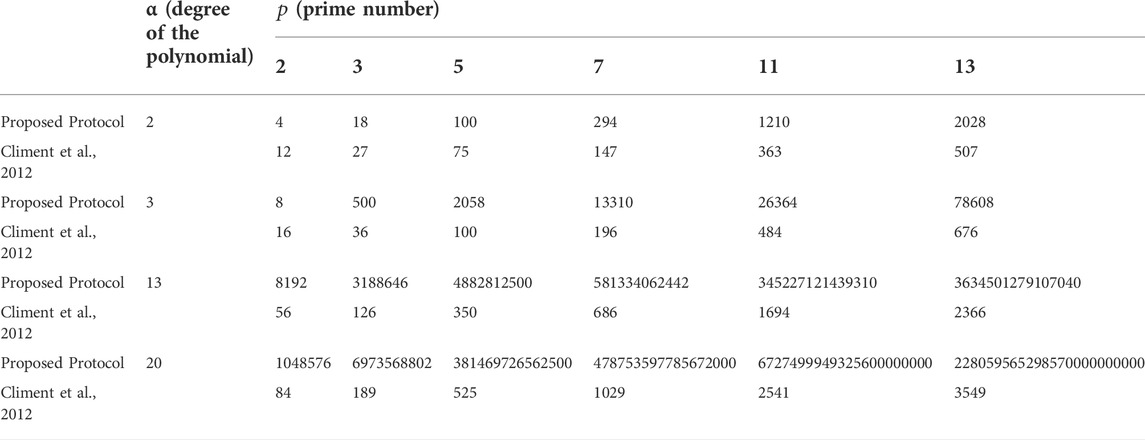
TABLE 1. The size of the set of polynomials of different degrees
If the degrees of the two polynomials are
4.3 Security aspects of the proposed protocols
This section discusses the security analysis of the protocols proposed in Section 3. The security of the protocols depends on the solution of the generalized decomposition problem. For solving such a problem in a noncommutative ring, no polynomial-time algorithm is known. An adversary has to find the solution to the decomposition problems, which are expressed as the following system of equations:
The adversary also knows the elements
One can then guarantee conditions (12) and (13). We note that the size of the space of the polynomials over
4.3.1 Man-in-the-middle attack
In this attack scenario, the adversary has a man-in-the-middle position. He can breach the security of the key exchange protocol by intercepting the communication between Alice (ith device) and Bob (jth). The attacker manipulates the public keys of both parties and blocks the transmission of actual messages on either side. The proposed protocol can be immunized against this type of attack in the following way.
The gateway can use hashes and encrypt the private keys
When the devices calculate their secret shared keys, the gateway calculates the same. The gateway then hashes the shared key and keeps it in the device hash table. Alice (ith device) and Bob (jth) then hash their shared keys and ask the gateway for verification. The gateway checks the hashed shared keys with the hash table. If the hash value of the shared key matches, then communication may be allowed. Otherwise, the shared key is assumed to have been intercepted and manipulated by the attacker.
For authentication of the gateway, the device authentication mechanism described in Section 4.1 can also be implemented between an IoT device and gateway. Each IoT device and gateway pair can have a unique pair of keys specifically for authentication. Further, IoT devices and the gateway are authenticated using encryption and a hash of the keys during a session.
4.3.2 Privileged insider attack
To prevent this type of attack, the passwords can be managed at the time of registration of the users in the following way.
Each user chooses a username and password and provides this information to the web browser. The passwords can be encrypted by the public key, and their hashes can be stored in a password management table. The users are authenticated by their usernames and passwords. It is hard to get passwords because they are encrypted by public keys. The protocol’s security depends on the solution of Eqs 12–15 describing the generalized decomposition problem in a noncommutative ring. The insider finds it hard to guess a password.
4.3.3 Impersonation attack
It is difficult to detect an impersonation attack. In our case, if the attacker impersonates the authenticated user and launches a login request, it is not easy to extract the user id and password because they are encrypted, as discussed in the previous section. Inverting the hash function and decrypting it without knowing the key that generalizes the decomposition problem of the polynomials over the noncommutative ring is computationally hard. The user-impersonation attack is thus resisted by our proposed protocol.
5 Perfect forward secrecy (PFS)
Based on the already shared secret key
Stickel (2005) proposed that the order of matrices
Shpilrain modified Stickel’s scheme to prevent his linear algebra attack, suggesting that the publicly announced elements
Mullan (2012) called Shpilrain’s modification the polynomial version of Stickel’s scheme. He offered a cryptanalysis of Shpilrain’s polynomial variant of Stickel’s scheme to discover the shared key. Cao et al. (2007) proposed a new scheme for devising a public key cryptosystem based on noncommutative rings. The main idea of their proposal was that for a noncommutative ring, the set of polynomials can be considered the underlying work structure. The Diffie-Helman-like key exchange protocol and consequently ElGamal-like cryptosystems were constructed using polynomials over the noncommutative ring. The authors also showed how to extend their method to noncommutative groups (or semi-groups). The main difference between Shpilrain’s polynomial version of the Stickel scheme and the key exchange protocol proposed by Cao et al. (2007) was in the use of the underlying structures. Shpilrain’s proposal was for commutative structures, whereas Cao et al. (2007) proposed the use of noncommutative structures.
The protocol proposed by Cao et al. (2007) deals with the polynomials having coefficients from the set of positive integers. In our proposal, polynomials with coefficients from the center of the respective underlying noncommutative structure are used. The advantage of using the coefficients from the center over integer coefficients is that these coefficients depend on the nature of the noncommutative structure used as a platform. That is why determining the values of coefficients is difficult when choosing a complex platform.
A random choice of the polynomial
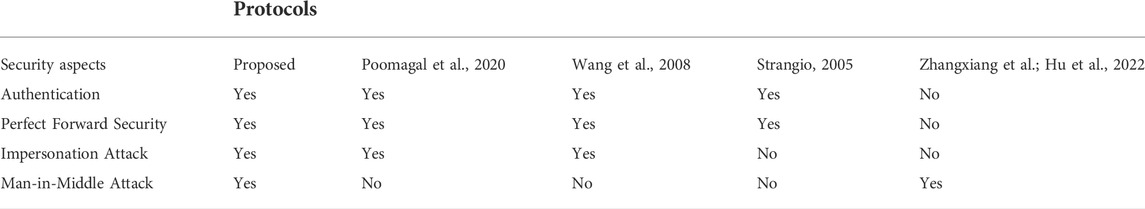
The proposed protocol meets the different kinds of requirements of lightweight mechanisms. As it is based on polynomials, it requires fewer bytes for manipulation over the network. Also, the computations involved in key exchange and authentication are fast and space efficient, which makes the protocol suitable for implementation in a lightweight scenario. The protocol can also resist various attacks. Table 2 summarizes the overall strengths of the proposal.
6 Certified keys
A vital characteristic of public keys is authentication by a certification authority (CA). The keys of the proposed key exchange protocol can be certified using the CA’s private key
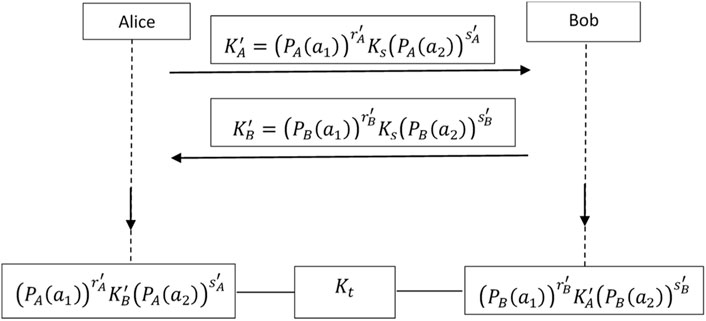
After getting their public certified keys from the web service, ith and jth device find the shared secret key as
7 Experimental results and performance analysis
For the implementation of our protocol, Python 3.6.9 with cryptography library Pycrpto 2.6.1 is used. The Mininet platform (Hu et al., 2022) is used for creating the networking environment. The communication cost of a protocol is affected by different attributes. By analyzing these attributes, the effects of the implementation of the protocol can be studied. The following are some parameters to be studied in this regard:
7.1 Passes overhead
The number of messages exchanged in the execution of the protocol is known as the number of passes. A key exchange protocol with a significant number of passes is considered more costly. The proposed protocol costs three passes in distributing and sharing keys, with the choice of parameters suggested in Section 4.2. Practically, the ith and jth nodes can generate their shared key simultaneously and need only one communication pass from either node without any further communications.
7.2 Communication cost
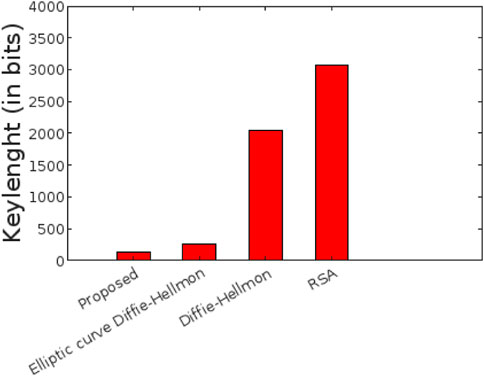
The total number of transmitted bits for optimized performance is known as communication overhead or communication cost. A protocol with a low communication overhead is considered more efficient. We take the key length of our key exchange protocol to be 128-bits, whereas the equivalent key lengths of the state-of-the-art protocols of RSA, Diffie-Hellman, and elliptic curve Diffie-Hellman are 3072-bits, 2048-bits, and 256-bits, respectively. Our proposed protocol performs better than these protocols because it uses polynomials over the noncommutative ring. When compared to the exponential operations used in RSA and Deffie-Hellman, and the elliptic curve operations used in elliptic curve based protocols, operations based on polynomials use less processing space and power. Figure 3 shows the comparison of the key lengths of the protocols.
7.3 Computational time
The total time consumed by the protocol is known as computation time. Some of the attributes of the computational cost are as follows:
For the execution of an algorithm, it is preferred that the total number of arithmetical operations is as low as possible, so as to enhance efficiency and reduce the computational cost. With the increase in the number of operations, the energy and running time of the algorithm may be compromised. The calculation of the computational time of the proposed protocol is based on the ring scalar multiplication, hash operation, and exponentiation operation. The calculated result is then compared with some recent protocols.
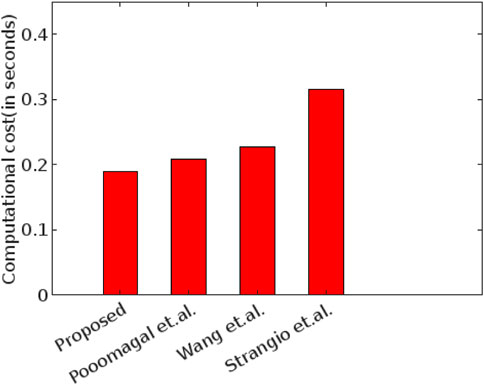
With the choice of parameters suggested in Section 4.2, the scalar multiplication involved in our proposed protocol requires 0.003432 s, the hash needs 0.00025 s, and the modular exponentiation operation takes 0.016121 s. The gateway performs six scalar multiplications and eight exponentiations, while three scalar multiplications, two exponentiation operations, and a hash function calculation are involved in the calculation of the key at each IoT device end. Therefore, 0.14956 and 0.042788 s are required for calculations on the gateway and each device, respectively. The total time cost is 0.192348.
The time for simple addition and multiplication operations can be neglected because it is negligible compared to other operations. Table 4; Figure 4 show the comprehensive result of the total computation time for all the operations of our protocols and other protocols. Notations
8 Conclusion
A lightweight, efficient, and secure key exchange protocol for secret communication in IoT environments is presented. The related features of key exchange protocol, such as PFS and key certification, are addressed in the proposal. The security aspects of the new protocol are discussed in detail. For the scheme’s implementation, the values of related parameters are suggested. It is shown that the proposed protocol enables secure communication between IoT devices in the future regime. Further, an ElGamal-like cryptosystem can also be constructed based on the proposed protocol.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author contributions
SK designed the model and the computational framework and analysed the data. SI and RA assisted with the measurements and wrote the paper with input from all authors. OC and AK contributed to the interpretation of the experimental results. AK provided critical feedback and helped shape the overall structure of the revised manuscript.
Acknowledgments
The authors would like to acknowledge the support of Prince Sultan University for paying the Article Processing Charges (APC) of this publication.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abdalla, M., Fouque, P. A., and Pointcheval, D. (2005). “Password-based authenticated key exchange in the three-party setting,” in International Workshop on Public Key Cryptography, 2005 Jan 23 (Berlin, Heidelberg: Springer), 65–84.
Alohali, B. A., and Vassialkis, V. G. (2015). “Secure and energy-efficient multicast routing in smart grids,” in 2015 IEEE Tenth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), 2015 Apr 7 (Singapore: IEEE), 1–6.
Alvarez, R., Tortosa, L., Vicent, J. F., and Zamora, A. (2009). Analysis and design of a secure key exchange scheme. Inf. Sci. 179, 2014–2021. doi:10.1016/j.ins.2009.02.008
Anjaneyulu, G. S. G. N., and Sanyasirao, A. (2014). Distributed group key management protocol over non-commutative division semirings. Indian J. Sci. Technol. 7 (6), 871–876. doi:10.17485/ijst/2014/v7i6.18
Anshel, I., Anshel, M., and Goldfeld, D. (1999). An algebraic method for public-key cryptography. Math. Res. Lett. 6, 287–291. doi:10.4310/mrl.1999.v6.n3.a3
Bennett, H., and Brassard, G. (1984). “Quantum cryptography: Public key distribution and coin tossing,” in Int. Conf. on Computers, Systems and Signal Processing, Bangalore, India, Dec. 1984, 175–179.
Birman, J., Ko, K., and Lee, S. J. (1998). A new approach to the word and conjugacy problems in the braid groups. Adv. Math. (N. Y). 139, 322–353. doi:10.1006/aima.1998.1761
Cao, Z., Dong, X., and Wang, L. (2007). New public key cryptosystems using polynomials over non-commutative rings. Cryptology e-print Archive.
Center, C. S. R. (2021). Post-quantum cryptography standardization conference. Online; Accessed May 17, 2021.
Chang, T. Y., Hwang, M. S., and Yang, W. P. (2011). A communication-efficient three-party password authenticated key exchange protocol. Inf. Sci. 181 (1), 217–226. doi:10.1016/j.ins.2010.08.032
Cheikhrouhou, O., Koubâa, A., and Zarrad, A. (2020). A cloud based disaster management system. J. Sens. Actuator Netw. 9, 6. doi:10.3390/jsan9010006
Chung, H. R., and Ku, W. C. (2008). Three weaknesses in a simple three-party key exchange protocol. Inf. Sci. 178 (1), 220–229. doi:10.1016/j.ins.2007.08.004
Climent, J. J., Navarro, P. R., and Tortosa, L. (2012). Key exchange protocols over noncommutative rings. The case of End (Zp×Zp2). Int. J. Comput. Math. 89 (13-14), 1753–1763. doi:10.1080/00207160.2012.696105
Diffie, W. D., and Hellman, M. E. (1976). New directions in cryptography. IEEE Trans. Inf. Theory 22 (6), 644–654. doi:10.1109/tit.1976.1055638
ElGamal, T. (1985). A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 31 (4), 469–472. doi:10.1109/tit.1985.1057074
Guo, H., Li, Z., Mu, Y., and Zhang, X. (2008). Cryptanalysis of simple three-party key exchange protocol. Comput. Secur. 27 (1-2), 16–21. doi:10.1016/j.cose.2008.03.001
Hu, Z., Li, J., Mergendahl, S., and Wilson, C. (2022). “Toward a resilient key exchange protocol for IoT,” in Proceedings of the Twelfth ACM Conference on Data and Application Security and Privacy (CODASPY '22), April 2022, 214–225.
Inam, S., and Ali, R. (2016). A new ElGamal-like cryptosystem based on matrices over groupring. Neural Comput. Appl. doi:10.1007/s00521-016-2745-2
Kanwal, S., and Ali, R. (2016). A cryptosystem with noncommutative platform groups. Neural comput. Appl. 29, 1273–1278. doi:10.1007/s00521-016-2723-8
Khan, M. A., and Salah, K. (2018). IoT security: Review, blockchain solutions, and open challenges. Future gener. Comput. Syst. 82, 395–411. doi:10.1016/j.future.2017.11.022
Ko, K. H. S., Lee, J., Cheon, J. H., Han, J. W., Kang, J. S., and Park, C. (2000). “New public-key cryptosystem using braid groups,” in Advances in cryptology - crypto 2000, 1880. Lecture notes in computer science (Berlin: Springer-Verlag), 166–183.
Lizama-Perez, L. A., and López, R., J. M. (2021). Non-invertible public key certificates. Entropy 23, 226. doi:10.3390/e23020226
Lizama-P´erez, L. A., L´opez, R. J. M., and Samperio, E. H. (2021). Beyond the limits of shannon’s information in quantum key distribution. Entropy 23, 229. doi:10.3390/e23020229
Lu, R., and Cao, Z. (2007). Simple three-party key exchange protocol. Comput. Secur. 26 (1), 94–97. doi:10.1016/j.cose.2006.08.005
Mano, L. Y., Faiçal, B. S., Nakamura, L. H., Gomes, P. H., Libralon, G. L., Meneguete, R. I., et al. (2016). Exploiting IoT technologies for enhancing Health Smart Homes through patient identification and emotion recognition. Comput. Commun. 89, 178–190. doi:10.1016/j.comcom.2016.03.010
Menezes, A. J., Van Oorschot, P. C., and Vanstone, S. A. (1996). Handbook of applied cryptography. Boca Raton, FL: CRC Press.
Meshram, A., Meshram, C., and Khobragade, N. W. (2017). An IND-CCA2 secure public key cryptographic protocol using Suzuki 2-group. Indian J. Sci. Technol. 10 (12), 1–8. doi:10.17485/ijst/2017/v10i12/111588
Mullan, C. (2012). Some results in group-based cryptography. Technical report. London: Department of Mathematics, Royal Holloway, University of London.
Mutlag, A. A., Abd Ghani, M. K., Arunkumar, N. A., Mohammed, M. A., and Mohd, O. (2019). Enabling technologies for fog computing in healthcare IoT systems. Future Gener. Comput. Syst. 90, 62–78. doi:10.1016/j.future.2018.07.049
Odoni, R. K., Varadharajan, V., and Sanders, P. W. (1984). Public key distribution in matrix rings. Electron. Lett. 20, 386–387. doi:10.1049/el:19840267
Paeng, S. H., Ha, K. C., Kim, J. H., Chee, S., and Park, C. (2001). “New public key cryptosystem using finite non abelian groups,” in Advances in cryptology - crypto 2001, 2139. Lecture notes in computer science (Berlin: Springer-Verlag), 470–485.
Poomagal, C. T., S. Kumar, G. A., and Mehta, D. (2020). Multi level key exchange and encryption protocol for internet of things (iot). Comput. Syst. Sci. Eng. 35 (1), 51–63. doi:10.32604/csse.2020.35.051
Rivest, R. L., Shamir, A., and Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21 (2), 120–126. doi:10.1145/359340.359342
Sakalauskas, E., and Burba, T. (2003). Basic semigroup primitive for cryptographic session key exchange protocol. Inf. Technol. Control 28 (3), 76–80.
Shor, P. W. (1997). Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26 (5), 1484–1509. doi:10.1137/s0097539795293172
Shpilrain, V. (2008). Cryptanalysis of Stickel’s key exchange scheme. Proc. Comput. Sci. Russ. 5010, 283–288.
Shpilrain, V., and Ushakov, A. (2006). A new key exchange protocol based on the decomposition problem. Contemp. Math. 418, 161–167.
Singh, S. R., Khan, A. K., and Singh, T. S. (2017). A new key management scheme for wireless sensor networks using an elliptic curve. Indian J. Sci. Technol. 10 (13), 1–7. doi:10.17485/ijst/2017/v10i13/108661
Sramka, M. (2022). On the security of Stickels key exchange scheme. Available at: http://crisesdeim.urv.cat/msramka/pubs/sramka-stickelkesecurity.pdf.
Stickel, E. (2005). “A new method for exchanging secret key,” in Proceedings of the Third International Conference on Information Technology and Applications (ICITA’05), Sidney, Australia, 426–430.
Strangio, M. A. (2005). “Efficient Diffie–Hellmann two-party key agreement protocols based on elliptic curves,” in Proc. 20th ACM Symposium on Applied Computing (SAC), 324–331.
Thomas, T., and Lal, A. K. (2008). A zero-knowledge undeniable signature scheme in nonabelian group setting. Int. J. Netw. Secur. 6 (3), 265–269.
Wang, S., Cao, Z., Strangio, M. A., and Wang, L. (2008). Cryptanalysis and improvement of an elliptic curve diffie-hellman key agreement protocol. IEEE Commun. Lett. 12 (2), 149–151. doi:10.1109/lcomm.2008.071307
Yoon, E. J., and Yoo, K. Y. (2011). Cryptanalysis of a simple three-party password-based key exchange protocol. Int. J. Commun. Syst. 24 (4), 532–542. doi:10.1002/dac.1168
Keywords: discrete log problem, public key exchange protocol, public key cryptography, noncommutative ring, polynomial, Internet of Things (IoT)
Citation: Kanwal S, Inam S, Ali R, Cheikhrouhou O and Koubaa A (2022) Lightweight noncommutative key exchange protocol for IoT environments. Front. Environ. Sci. 10:996296. doi: 10.3389/fenvs.2022.996296
Received: 17 July 2022; Accepted: 31 August 2022;
Published: 23 September 2022.
Edited by:
Muhammad Tayyab Sohail, Xiangtan University, ChinaReviewed by:
Aamir Akbar, Abdul Wali Khan University Mardan, PakistanTengyue Hao, University of Malaya, Malaysia
Copyright © 2022 Kanwal, Inam, Ali, Cheikhrouhou and Koubaa. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Shamsa Kanwal, c2hhbXNfa2Fud2FsQGhvdG1haWwuY29t
 Shamsa Kanwal
Shamsa Kanwal Saba Inam
Saba Inam Rashid Ali
Rashid Ali Omar Cheikhrouhou
Omar Cheikhrouhou Anis Koubaa
Anis Koubaa