- Economic & Technology Research Institute of State Grid Shandong Electric Power Company, Jinan, China
With the gradual increase in the grid-connected capacity of renewable energy sources, the uncertainty in the operation of power systems has increased, posing challenges to static security assessment considering N-1 contingency scanning. To address this, this article first establishes a static security calculation model based on stochastic power flow. Then, it proposes stochastic component-level safety indexes and system-level safety indexes. Finally, using the analytic hierarchy process to analyze the obtained weighting coefficients, the article establishes a system of static security assessment indexes for power systems. A data-driven simulation method based on extreme gradient boosting (XGBoost) is proposed to tackle the high time consumption of multi-scenario static security assessment, which brings difficulties in model debugging and application. Case studies based on the IEEE 39-bus system demonstrate the effectiveness of the proposed model and the rapidity of the data-driven approach.
1 Introduction
As the operational environment of the power grid evolves, the system faces increasing random disturbances, leading to more complex and variable conditions. However, the traditional static security assessment (SSA) for N-1 contingency scanning has difficulty dealing with the increasing uncertainties (Čepin, 2011; Chen et al., 2015; Meegahapola et al., 2020; Qian et al., 2022). To ensure the system’s safety and stability, it is crucial to develop a stochastic-based SSA method.
The primary feature of an electrical power system is to ensure the reliability, cost-effectiveness, and quality of the power supply, providing continuous and uninterrupted energy to users (Das, 2007; Schavemaker and Van der Sluis, 2017). Power system safety analysis is categorized into static and dynamic safety analyses. SSA assumes that the power system transitions directly from a pre-disturbance static state to a post-disturbance static state without considering the intermediate transient processes. This analysis is used to verify whether various constraints are satisfied following a disturbance (Prabhakar et al., 2022). Dynamic safety analysis, on the other hand, examines the power system’s ability to maintain stability during the transient process from a pre-disturbance static state to a post-disturbance static state (Rao et al., 2009).
By considering the randomness of wind power and PV power generation, the accuracy of the static safety evaluation method can be improved, thereby providing a more reliable safety reference and ensuring that the system can cope with emergencies and failures. Accurate static safety evaluation can assist decision makers in formulating more effective scheduling strategies and emergency plans to improve the reliability and safety of the power system. Power system static security assessments have been widely investigated in previous studies. The existing methods can be classified as i) model based, ii) signal-based, and iii) artificial intelligence (AI) (Wu, 2015). The model-based methods use a mathematical expression of the power system to analyze the security status (Jing, 2014). The main disadvantages of model-based methods are that it is difficult to provide an accurate model for the power system in most cases, and models are unsuitable for real-time assessment based on accurate modeling. Signal-based methods have better calculation accuracy, but they depend on a predefined threshold and are notably sensitive to the completeness of the information about the power system’s status. AI-based methods require historical data to assess the power system security status. The main methods include random forest (Wang et al., 2016), multi-class support vector machine (SVM) (Meegahapola et al., 2020), core vector machine (Mohammadi et al., 2010), etc. These methods are restricted in terms of extracting the comprehensive features in complex and nonlinear systems such as power networks.
Load flow analysis is crucial for power system SSA; it can address the load uncertainties from forecasting errors and operational conditions, particularly with renewable energy integration (Kalyani and Swarup, 2010; Afrasiabi et al., 2019). Stochastic load flow offers statistical insights into node voltages and branch powers, facilitating the evaluation of random factors and probability distributions at specific operational points (Shirasaki and Uchida, 2010). There are three general methods used for stochastic power flow calculation: simulation, analytical, and approximate approaches (Su, 2005; Wang et al., 2008; Ghiasi, 2018). Monte Carlo simulation generates a stochastic process to approximate solutions by analyzing statistical properties (Binder et al., 1992; Conti and Raiti, 2007; Thomopoulos, 2012; Graham and Talay, 2013). The analytical method uses simplified DC and AC load flow equations with convolution techniques to calculate output distributions based on input variables, effectively modeling stochastic behavior under varying conditions (Hu and Wang, 2007; Kiruthika and Bindu, 2020; Han et al., 2021). The approximate method estimates system state variables’ statistical characteristics from input variables’ statistical features, reducing computational demands. It is ideal for quick assessments (Morales and Perez-Ruiz, 2007). These methods are essential for power generation planning, network planning, SSA, real-time operational state analysis, optimal load flow calculations, and risk assessments, especially as power systems face rising uncertainties.
In summary, the prevailing research on N-1 security scanning predominantly utilizes deterministic load flow analysis, which does not adequately account for the stochastic variations introduced by wind and solar energy sources. By taking uncertainties into account, the article proposes a novel static security assessment methodology that leverages stochastic load flow simulation and incorporates a data-driven acceleration algorithm, addressing the complexities of static security assessment in the face of stochastic variations effectively.
The organization of the subsequent sections of this article is as follows: Section 2 establishes a static security index system that considers stochasticity and develops a stochastic load flow model based on simulation methods. Section 3 introduces a data-driven method for stochastic static security assessment. Section 4 provides a case study analysis based on the IEEE 39-bus system. Section 5 concludes the article.
2 Model formulation
The model formulation process is as follows: Initially, it establishes probability distribution models for load, photovoltaic (PV), and wind power, generating random scenarios with uncertainty. Then, it calculates the DC optimal power flow, using the result as the base case for power flow. Following the base case flow, the Newton–Raphson method is employed to compute the stochastic load flow for the generated probability distribution scenarios. Finally, it utilizes a kernel density estimation (KDE) algorithm to fit the results of the stochastic load flow calculations.
2.1 Stochastic power flow model
2.1.1 Model for uncertainty sources
(1) Load Probability Model
In most stochastic load flow studies, load uncertainty is assumed to be normally distributed, with the power injections at nodes being either independent or linearly related (Tuinema et al., 2020). Based on this, this article develops a stochastic model for the active and reactive power of system loads that adhere to a normal distribution.
There is always a deviation in load forecasting, expressed as:
The probability density function of the load forecast error random variable as follows:
where
(2) Photovoltaic and Wind Power Plant Probability Model
We can describe the uncertainty of PV and wind power output by superimposing the forecast error
The standard deviation of power forecast error
where
2.1.2 Stochastic power flow model
The article initially addresses the solution of the DC optimal power flow, employing the outcome as the base case for power flow. Thereafter, the Newton–Raphson method is utilized to compute the system’s stochastic load flow, establishing the stochastic power flow model.
For a combined generation and transmission system with
The following constraints should be satisfied:
where
The stochastic load flows have been calculated based on the solved DC base case power flow. The probability distribution models for node voltage
where
Subsequently, the Newton–Raphson method is used to solve the stochastic load flow based on the generated probability distribution models. This approach yields the system power flow distribution results for each random case. Further, the KDE algorithm is used to fit the probability distribution of output data.
Given
where
2.2 N-1 static security assessment indexes
The impact of random disturbances or faults on power systems primarily manifests as branch overloads and node voltage violations: branch overloads may trigger cascading failures, while node voltage violations may lead to voltage collapse (De La Ree et al., 2005; Ibrahim, 2011). Therefore, the SSA of the system is conducted mainly from two aspects: branch overloads and node voltage violations. The assessment perspective involves two levels: safety risk and safety probability.
2.2.1 Component-level safety index
(1) Severity Index
The load flow percentage of each line determines the degree of overload.
where
The node voltage severity function typically defines the percentage deviation of each node voltage magnitude from its normal magnitude limit.
(2) Component failure probability
The probability that the network operation fails to meet the power flow security constraints after a specific anticipated event occurs can be determined as follows:
where
The probability that branch
where
2.2.2 System-level safety indexes
The system risk or insecurity probability is a comprehensive reflection of the risks or insecurity probabilities of individual components.
(1) System Risk Index
The system overload severity index is defined as:
where
The system voltage violation severity index is defined as:
(2) System probability indexes
The failure of component
where
Furthermore, the probability that the system satisfies power flow security constraints after an anticipated event occurs is given by:
The probability that the system does not satisfy power flow security constraints is given by:
where
Assuming the probability of component
where
Then, the probability of power flow security for the system is obtained as:
The probability of power flow insecurity for the system is given by:
In this subsection, this article integrates the subjective weighting model constructed using the analytic hierarchy process (AHP) (Chatzimouratidis and Pilavachi, 2007) and the objective weighting model constructed using the entropy method using the additive integration method.
First, the proportions of each weight are determined in the comprehensive weights:
where
Next, the formula for calculating the comprehensive weight coefficient of the ith index is given as follows:
The overall system static security assessment index S0 is obtained as follows:
3 Data-driven static security assessment algorithm
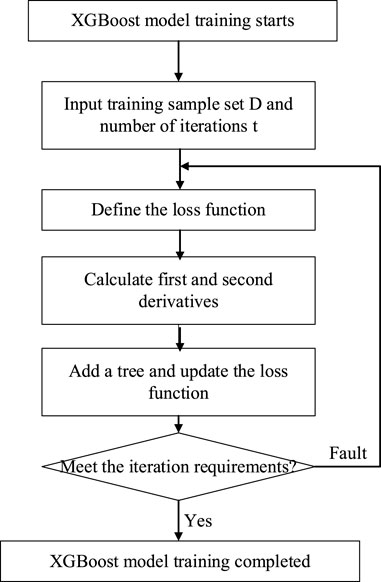
Considering the issues of long training times and the difficulty of extracting features from data in data-driven models, this article employs the XGBoost method to reduce the simulation time and application complexity in the safety assessment of power systems.
Initially, this article uses the Monte Carlo simulation method to construct random scenarios reflecting the stochastic fluctuations in load, PV, and wind output values. Following this, an iteration through all fault conditions of lines and generators is conducted. The method can solve the corresponding random scenarios for each fault condition. Subsequently, the static unsafety indexes for the system under the respective fault conditions are calculated, applying the method detailed in Section 2.2.
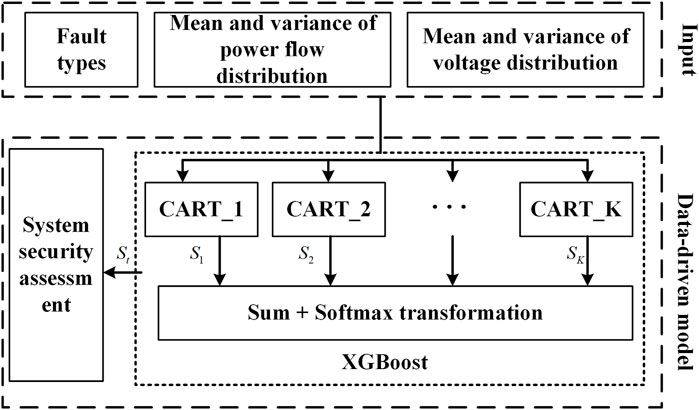
XGBoost is a machine learning algorithm based on tree models (Chen and Guestrin, 2016), which automatically selects appropriate splitting directions when samples are missing, making it suitable for processing tabular data. First, the system safety assessment scenario is designed, the fault set and data collection points are selected, and the sample set that characterizes the random power flow input and output changes under normal operation and fault conditions is constructed as follows:
where N represents the number of samples, that is, N safety assessment scenarios, and M represents the dimension of each sample feature vector. The input feature vector of sample
Based on the new energy power system safety assessment data set established, K classification and regression trees are selected as base learners; further, based on the regression idea of the boosting method, the sample data is input into the XGBoost model, and the output vectors of multiple base learners are continuously added as the tree model of XGBoost. Finally, the learned system insecurity probability can be obtained by using the
Based on the renewable energy power system static security assessment dataset established, K classification and regression trees are chosen as base learners. The learned system insecurity probability can be obtained by utilizing the cumulative function. The system static security assessment framework is illustrated in Figure 1, and for a given dataset
In the equation,
The objective function trained by XGBoost can be represented as:
where
In the XGBoost algorithm, the model complexity of a single base learner is defined as:
where
Based on the established dataset for assessing the security of new energy power systems (shown in Figure 2), CART base learners are continuously trained to fit the residuals of the previous model and then integrated into the XGBoost model. Iteration continues until either the preset number of base learners is trained or the model residuals are smaller than the set threshold.
where
4 Case study
In the case study, the SSA indexes for a system postulated are assessed with accidents detailed. This includes evaluating the likelihood that voltage and power flow limits are not exceeded after each accident, considering uncertainties in power injections and line failures. The study calculates the overall system safety by integrating these probabilities with the frequency of each pre-planned accident.
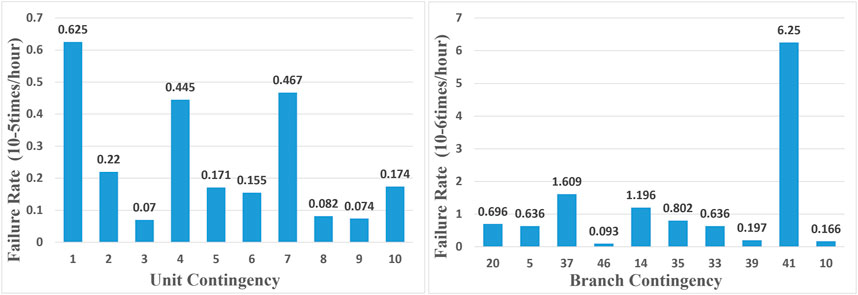
Then, fault scenarios for the case are constructed. The average failure probability for units is 1×10−4 times/hour, with the range from 5 × 10−5∼2 × 10−4. The average failure probability for branches is 1.2 × 10−4 times/hour, with the range from 2 × 10−5∼2 × 10−4. The transmission capacity of all branches is consistent with the IEEE 39-bus case, and the transmission capacity limit during emergencies is 2.5 times that of normal conditions.
4.1 Model-driven analysis
(1) Component and System Safety Index Ranking Analysis
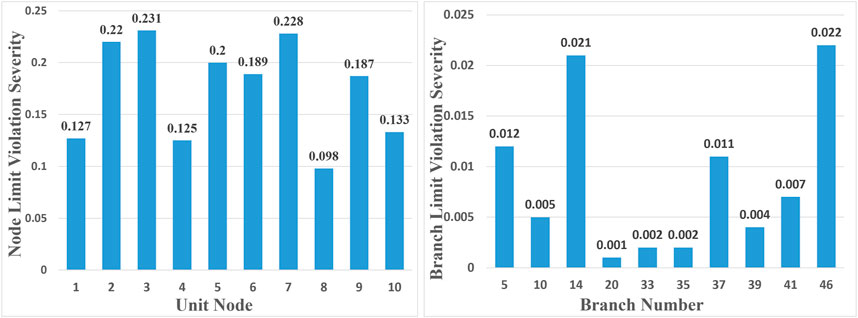
By ranking the items in the safety function according to the calculation results, the links that contribute significantly to the overall probability of system unsafety can be identified, drawing attention to them. Figure 3 provides risk indexes for each component in the system under various fault occurrence probabilities. For each unit, this reflects the risk of a voltage limit violation at the node where the unit is located. For each branch, it reflects the risk of a power flow limit violation on that branch. The higher the risk index, the greater the threat to the system in the event of a fault at that node or on that branch.
Additionally, by ranking the probabilities of the system not meeting power flow safety constraints for each pre-planned accident, the fault items that most affect the probability of system power flow can be identified. More targeted preventive measures can be implemented. Figure 4 provides the probabilities of system unsafety caused by the failure of each component, considering the failures of various components.
(2) System Safety Assessment Simulation Analysis
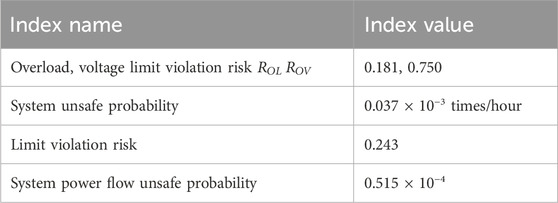
When assessing the system risk indexes, the system overload risk index
First, use the additive aggregation method to calculate the undetermined constants for the subjective and objective weights, resulting in the undetermined constant
4.2 Data-driven analysis
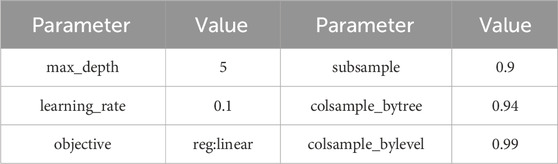
In XGBoost, there are three methods for calculating variable importance: using the frequency of variable splitting in trees as a measure of importance, using the average gain after variable splitting as a measure of profit, and using the coverage range of samples after variable splitting as a measure of coverage. In this section, the XGBRegressor function is used to train and learn from sample data. The number of iterations is set to 300, and other parameters are set, as shown in Table 2.
The importance of variables in the model is analyzed. The analysis results are shown in Figure 5.
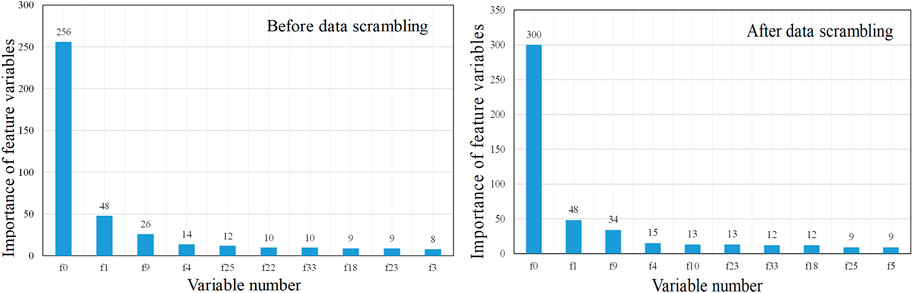
Figure 5. Before and after data scrambling importance analysis of feature variables based on XGBoost.
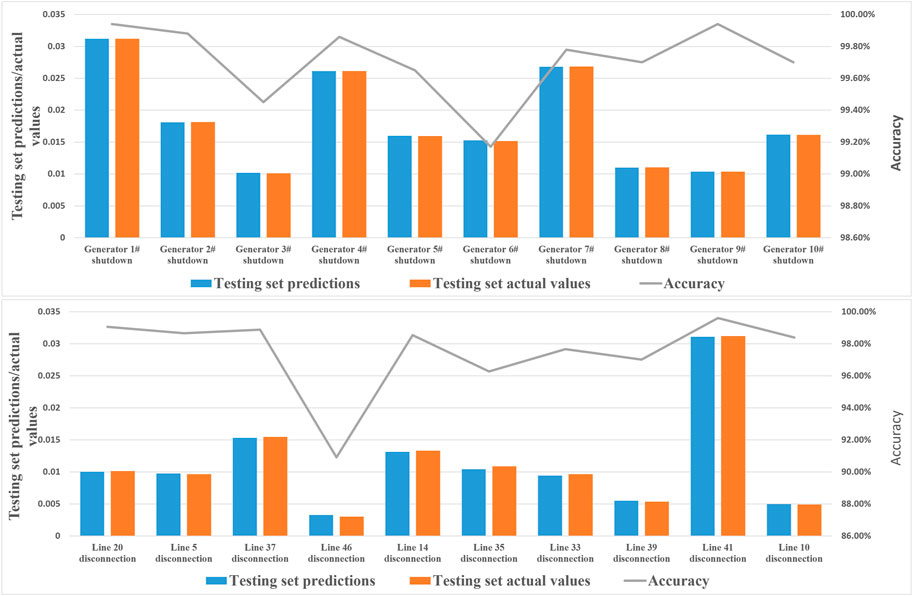
The specific SSA values and their accuracy rates for different operating scenarios of the system are shown in Figure 6 the average static security assessment values of prediction and actual are 1.470% and 1.472%.
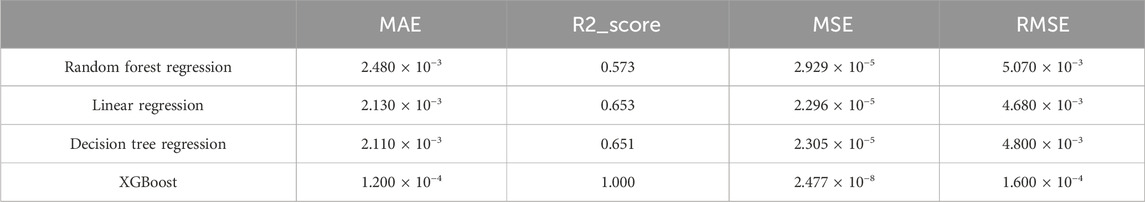
To provide a more intuitive analysis of the effectiveness of the strategies learned by the static assessment model based on the XGBoost algorithm, it will be compared to three methods: random forest regression, linear regression, and decision tree. Mean absolute error (MAE), R-squared score (R2_score), mean squared error (MSE), and root mean squared error (RMSE) are used as evaluation metrics. In all experiments, 80% of randomly sampled input data is used to build the model (training set), while 20% of the data is used for evaluation (testing set). The experimental results are shown in Table 3.
The experimental results indicate that the data-driven model used in this article has higher prediction accuracy than other comparative algorithms, demonstrating the better applicability of the XGBoost algorithm. The inference speed of the XGBoost algorithm is 7.58 × 10−6 s per item, showing a significant speed improvement compared to traditional evaluation methods.
5 Conclusion
This article outlines a static security assessment index system that accommodates stochastic variations, introduces a method based on stochastic load flow simulations, and develops a data-driven acceleration algorithm to enhance static security assessments in the face of stochastic variations.
First, based on simulation techniques, a calculation method for stochastic load flow is proposed, which can then provide the necessary indices for static security assessment considering uncertainties.
Second, by integrating the outcomes derived from stochastic load flow analyses, a comprehensive approach to static security assessments is adopted, focusing on two primary factors: the potential for branch overloading and the adherence to node voltage limits, evaluated specifically for each branch and node. The system indices are weighted considering both subjective and objective perspectives, and the safety assessment indices for new energy systems are ultimately obtained.
Third, for acceleration, the article utilizes data from various fault scenarios to create samples that are suitable for data-driven models, capturing the system’s stochastic load flow and voltage amplitude under both normal and fault conditions. An XGBoost-based data-driven model was developed using this dataset, specifically for safety assessment in new energy power systems. The XGBoost showed strong predictive accuracy in assessing the safety of these power systems in case studies.
The article effectively evaluates system safety under the influence of randomness, providing theoretical support and technical guidance for the stable operation of renewable power systems.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author contributions
YZ: writing–original draft, writing–review and editing. XT: writing–original draft, writing–review and editing. LZ: writing–original draft, writing–review and editing.
Funding
The author(s) declare that financial support was received for the research, authorship, and/or publication of this article. This work is sponsored by the Science and Technology Project of the State Grid Shandong Electric Power Company, Grant/Award Number: 520625210007.
Conflict of interest
Authors YZ, XT, and LZ were employed by the Economic & Technology Research Institute of the State Grid Shandong Electric Power Company.
The authors declare that this study received funding from State Grid Shandong Electric Power Company. The funder had the following involvement in the study: the collection of data work in this paper.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Afrasiabi, S., Afrasiabi, M., Parang, B., and Mohammadi, M. (2019). Integration of accelerated deep neural network into power transformer differential protection. IEEE Trans. Industrial Inf. 16, 865–876. doi:10.1109/tii.2019.2929744
Al-Sumaiti, A. S., Ahmed, M. H., Rivera, S., El Moursi, M. S., Salama, M. M., and Alsumaiti, T. (2019). Stochastic PV model for power system planning applications. IET Renew. Power Gener. 13, 3168–3179. doi:10.1049/iet-rpg.2019.0345
Binder, K., Heermann, D. W., and Binder, K. (1992). Monte Carlo simulation in statistical physics. Springer.
Čepin, M. (2011). Assessment of power system reliability: methods and applications. Springer Science & Business Media.
Chatzimouratidis, A. I., and Pilavachi, P. A. (2007). Objective and subjective evaluation of power plants and their non-radioactive emissions using the analytic hierarchy process. Energy policy 35, 4027–4038. doi:10.1016/j.enpol.2007.02.003
Chen, S., Chen, Q., Xia, Q., Zhong, H., and Kang, C. (2015). N 1 security assessment approach based on the steady-state security distance, 9. London, United Kingdom: Generation Transmission & Distribution Iet, 2419–2426.
Chen, T., and Guestrin, C. (2016). “Xgboost: a scalable tree boosting system,” in Proceedings of the 22nd acm sigkdd international conference on knowledge discovery and data mining, 785–794.
Conti, S., and Raiti, S. (2007). Probabilistic load flow using Monte Carlo techniques for distribution networks with photovoltaic generators. Sol. Energy 81, 1473–1481. doi:10.1016/j.solener.2007.02.007
De La Ree, J., Liu, Y., Mili, L., Phadke, A. G., and Dasilva, L. (2005). Catastrophic failures in power systems: causes, analyses, and countermeasures. Proc. IEEE 93, 956–964. doi:10.1109/jproc.2005.847246
Ghiasi, M. (2018). A detailed study for load flow analysis in distributed power system. Int. J. Industrial Electron. Control Optim. 1, 153–160. doi:10.22111/IECO.2018.24423.1027
Graham, C., and Talay, D. (2013). Stochastic simulation and Monte Carlo methods: mathematical foundations of stochastic simulation. Springer Science and Business Media.
Han, J., Miao, S., Li, Y., Yang, W., and Yin, H. (2021). Fault diagnosis of power systems using visualized similarity images and improved convolution neural networks. IEEE Syst. J. 16, 185–196. doi:10.1109/jsyst.2021.3056536
Hu, Z., and Wang, X. (2007). Stochastic optimal load flow method considering load probability distribution. Automation Electr. Power Syst. (16), 14–18+44. doi:10.3321/j.issn:1000-1026.2007.16.003
Jing, W. (2014). Functional modeling methodology of complex system and its application in safety assessment. Beijing: China University of Petroleum.
Kalyani, S., and Swarup, K. S. (2010). Classification and assessment of power system security using multiclass SVM. IEEE Trans. Syst. Man, Cybern. Part C Appl. Rev. 41, 753–758. doi:10.1109/tsmcc.2010.2091630
Kiruthika, M., and Bindu, S. (2020). Classification of electrical power system conditions with convolutional neural networks. Eng. Technol. Appl. Sci. Res. 10, 5759–5768. doi:10.48084/etasr.3512
Meegahapola, L. G., Bu, S., Wadduwage, D. P., Chung, C. Y., and Yu, X. (2020). Review on oscillatory stability in power grids with renewable energy sources: monitoring, analysis, and control using synchrophasor technology. IEEE Trans. Industrial Electron. 68, 519–531. doi:10.1109/tie.2020.2965455
Mohammadi, M., Gharehpetian, G., and Niknam, T. (2010). On-line small-signal stability assessment of power systems using ball vector machines. Electr. Power Components Syst. 38, 1427–1445. doi:10.1080/15325001003735150
Morales, J. M., and Perez-Ruiz, J. (2007). Point estimate schemes to solve the probabilistic power flow. IEEE Trans. power Syst. 22, 1594–1601. doi:10.1109/tpwrs.2007.907515
Prabhakar, P., Krishan, R., and Pullaguram, D. R. (2022). “Static security assessment of large power systems under n-1-1 contingency,” in 2022 22nd national power systems conference (NPSC). IEEE, 35–40.
Qian, T., Shi, F., Wang, K., Yang, S., Geng, J., Li, Y., et al. (2022). N-1 static security assessment method for power grids with high penetration rate of renewable energy generation. Electr. Power Syst. Res. 211, 108200. doi:10.1016/j.epsr.2022.108200
Rao, K. D., Gopika, V., Rao, V. S., Kushwaha, H., Verma, A. K., and Srividya, A. (2009). Dynamic fault tree analysis using Monte Carlo simulation in probabilistic safety assessment. Reliab. Eng. Syst. Saf. 94, 872–883. doi:10.1016/j.ress.2008.09.007
Schavemaker, P., and Van Der Sluis, L. (2017). Electrical power system essentials. John Wiley & Sons.
Shirasaki, K., and Uchida, N. (2010). Fast computation and stable convergence technique for unbalanced load flow calculation in the large scale system. IEEJ Trans. Power Energy 128, 1329–1334. doi:10.1541/ieejpes.128.1329
Su, C.-L. (2005). Probabilistic load-flow computation using point estimate method. IEEE Trans. Power Syst. 20, 1843–1851. doi:10.1109/tpwrs.2005.857921
Thomopoulos, N. T. (2012). Essentials of Monte Carlo simulation: statistical methods for building simulation models. Springer Science & Business Media.
Tuinema, B. W., Tuinema, B. W., Rueda Torres, J. L., Stefanov, A. I., Gonzalez-Longatt, F. M., and Van Der Meijden, M. A. (2020). “Probabilistic power flow analysis,” in Probabilistic reliability analysis of power systems: a student’s introduction, 179–208.
Wang, L., Lin, X., Howell, F., and Morison, K. (2016). Dynamic security assessment. Smart grid handbook, 1–24.
Keywords: stochastic power flow, static security assessment, uncertain scenarios assessment, analytic hierarchy process, Xgboost algorithm
Citation: Zhang Y, Tian X and Zhang L (2024) A stochastic power flow-based static security assessment under uncertain scenarios. Front. Energy Res. 12:1429160. doi: 10.3389/fenrg.2024.1429160
Received: 07 May 2024; Accepted: 26 June 2024;
Published: 08 August 2024.
Edited by:
Chaojie Li, University of New South Wales, AustraliaReviewed by:
Chenchen Li, The University of Tennessee, United StatesPeng Zhang, University of Washington, United States
Houqi Dong, Tsinghua University, China
Copyright © 2024 Zhang, Tian and Zhang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Yuyue Zhang, MTUxMTcwODIwN0BxcS5jb20=
 Yuyue Zhang
Yuyue Zhang Xin Tian
Xin Tian Lina Zhang
Lina Zhang