- 1Information and Communication Branch of Hainan Power Grid Co., Ltd., Haikou, China
- 2Hainan Power Grid Co., Ltd., Haikou, China
The smart grid optimizes traditional power grids and provides more intelligent services for end users and utilities. However, due to the large number of unsafe devices in the smart grid, there are corresponding risks when implementing relevant solutions on these devices. Therefore, in this article, a security demand response management scheme based on blockchain is proposed to safely make energy trading decisions, thereby realizing the management of the overall load of users in the power grid. In this scheme, the miner node is the verifier. These nodes are responsible for verifying energy transactions in the smart grid (SG) and adding corresponding blocks to the blockchain. Successful energy transactions only occur in blocks in the blockchain. Here, the proposed method is validated through experiments on electric vehicles. The experimental results demonstrate the effectiveness of the proposed scheme in demand response management.
1 Introduction
With the rapid development and application of Distributed Energy Resources (DER), such as Rooftop Photovoltaics (PV) and Electric Vehicles (EVs), there is a new demand for coordinated management schemes for these distributed energy resources. Optimizing the management of distributed energy can enhance the flexibility of end users, reduce power costs, and provide key services to grid operators, achieving a match between demand and local renewable energy supply (Maharjan et al., 2017; Khan et al., 2018; Jindal et al., 2020; Zhang et al., 2021).
The development of the smart grid (SG) has led to incredible growth in the use of smart grid information and its related communication technology (ICT), and end users can obtain various related services within a specified time and range (Maharjan et al., 2017; Khan et al., 2018; Zhang et al., 2021). Smart energy trading, as one of the core components of smart grids, is closely related to users’ daily lives, involving various entities such as energy consumers (smart devices, SD) and service providers (power grids), and is achieved through daily energy operations. In addition, the popularity of EVs has also increased the load on the power grid as they require charging (Jindal et al., 2020). These entities form an energy network in smart cities, and it is necessary to optimize the management of energy resources to sustainably maintain energy supplies in smart cities. Therefore, energy management in smart cities has become an important task. However, due to limited power generation resources, it is necessary to manage the overall load situation of various departments in smart cities through energy trading (Wang et al., 2018; Li Q. et al., 2020; Gao et al., 2021). This can be achieved by using ICT and a cloud-based communication backend to manage the energy demand response of end users in residential, commercial, industrial, and transportation sectors (Fazio et al., 2016; Khoshkbarforoushha et al., 2017). Managing users’ energy needs in this way ensures that their energy utilization rate meets their needs. For example, a household that has excess energy at a certain moment can trade with EVs that require energy. Likewise, when EVs have excess energy, they can trade energy with industries that require more energy to operate.
Due to various energy management vulnerabilities in urban communication networks, energy trading can, however, be vulnerable to attacks. Therefore, to address these attacks and provide security and privacy for entities participating in energy transactions, a secure energy management scheme is needed that can ensure the overall security and privacy of users, even if the network is at risk (Cheng et al., 2022).
Blockchain technology ensures security constraints in a decentralized manner through distributed ledger systems (An et al., 2020; Cheng et al., 2020; Xu, 2020; Cheng et al., 2021), making it very difficult to disrupt this system as the disruption requires the destruction of all nodes (i.e., miner nodes), which are responsible for maintaining the security of the entire system. Therefore, blockchain can be successfully applied as part of security measures in smart cities to ensure the security of energy transaction requests. To date, some researchers have conducted relevant research. For example, Puthal (Puthal et al., 2018) proposed a blockchain-based energy trading solution that utilizes energy coins to achieve secure energy trading in intelligent transportation systems (ITS). Aujla (Aujla et al., 2018) proposed a localized peer-to-peer (P2P) electricity trading model for local electricity trading between plug-in hybrid vehicles (PHEVs) in smart grids. Wilson (2013) proposed a blockchain-based edge as a service framework for supporting secure energy trading in V2G environments of Software Defined Networks (SDNs). Kaur et al. (2018) proposed a new EV charging scheme for decentralized blockchain smart grid systems, aiming to minimize the level of power fluctuations in the grid and the overall charging cost for EV users. However, these methods all have some common problems, such as the inability to select miner nodes, the inability to select wallets, and a single application scenario. Therefore, this article proposes a scheme for applying blockchain to energy trading (Smart Secure Grid, SSG) to ensure the integrity and authenticity of energy trading requests. Once the transaction is authenticated, the energy transaction request will be used to manage the demand response, and after each successful transaction, the energy coin will be traded. In summary, the main contributions of this work are three-fold:
1. A miner node selection scheme is proposed based on the power capacity and processing capacity of intelligent devices in the smart grid.
2. A blockchain-based creation and verification scheme is proposed, which adds entries to the blockchain to ensure the security of energy transactions.
3. An energy transaction scheme for demand response management is designed to deal with energy transaction requests from different sources.
2 The proposed method
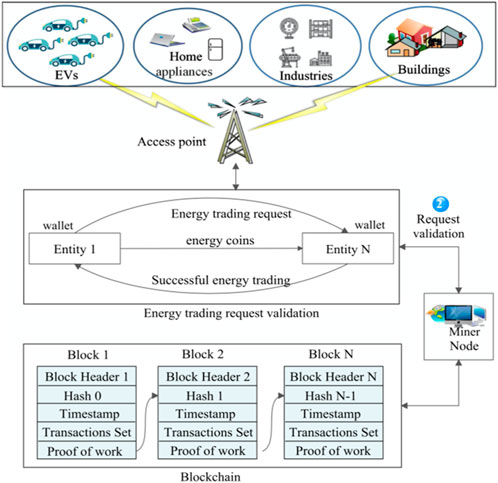
Here, we carefully discuss the general scenario where the SG ecosystem (SGE) is utilized for energy transactions. The proposed system consists of different entities such as residential, industrial, construction, and EVs. To maximize their benefits, their energy resources need to be shared with each other. As shown in Figure 1, these entities connect by using communication infrastructure based on ICT, while information about energy transactions between entities is delivered through access points. The details of an energy transaction among two various entities (seller and buyer) are stated as follows. First, energy-seeking entities initiate energy transaction requests in the SG ecosystem. Next, the system sends the requests to the access point. The verification requests are further sent by these access points to the miner nodes. The validation of energy transaction requests and relevant users’ privacy protection is performed by the miner nodes. The entity with superfluous energy will start trading with the energy-seeking entity after the request is validated by the miner node. The buyer transfers its energy coins to the seller at the value agreed by both parties once the energy trading succeeds. Note that in the system proposed in this paper, the initial value of energy coins owned by each participant is consistent; that is, the total amount of energy coins is constant. Figure 1 shows that two types of functional nodes (miner node and ordinary node) exist in our proposed system. Each node will be described in detail next.
2.1 Miner nodes
Miner nodes (MNs) are employed to authenticate, authorize, and audit energy-related transactions in the smart grid ecosystem. Each MN has its own limited storage capacity, where transaction data are temporarily stored before being added to the blockchain. The MN maintains a ledger for storing information related to received data blocks. The data block also includes block headers, hash values, timestamps, and transaction sets. For the block to be added to the blockchain, the MN calculates the proof of work based on the received information. If it matches the hash value received in the block, the MN will authenticate the block. It then sends information about the block to other MNs, and if all miner nodes agree on the authenticity of the block, the block is added to the blockchain. This step is repeated for each block received by an MN until its memory capacity is full, and then it sends the data to a centralized location with a large memory capacity.
The MN is employed to authenticate, authorize, and audit each energy-related trading in the SGE. The transaction data are temporarily stored in each MN’s limited storage area before they are added to the blockchain. A special ledger is maintained by the MN for storing information related to the data blocks received in the proposed system. Specifically, the complete data block also commonly includes a discriminative block header, a proof of work (PoW), a transaction set, one timestamp, and one hash value. The MNs calculate a PoW based on the received information for the newly added block. Next, once the calculated PoW matches the hash value received by the data block, the MN will authenticate the aforementioned new data block and send the block’s information to the other MNs. The new block will be added to the blockchain if all MNs reach a consensus on the authenticity of the block. These steps are repeated for each block received by a single MN until their memory capacity is exhausted, and then the data are sent to a centralized location that has a large memory capacity.
2.2 Ordinary nodes
In the smart grid ecosystem, nodes that are not miner nodes are referred to as ordinary nodes. The ordinary node maintains a limited-capacity ledger for storing its transaction logs. These ordinary nodes also have a wallet for energy coin payments between each other. The blockchain mechanism provides privacy protection for related entities by using encryption primitives to verify transactions between these modes. The blockchain is regarded as a chain of continuous data blocks that includes nodes’ related information. These nodes wish to execute transactions in a safe manner without relying on a centralized credible third-party system. In this system, each node has its own ledger to maintain transaction history. The ledgers of miner nodes are usually larger than the ledgers of ordinary nodes. The MNs are responsible for authenticating and authorizing transactions that users wish to execute in a secure manner.
The blocks in the blockchain contain a set of values used for authenticating transactions. These values include transaction blocks and hash value sets. The block header also includes the hash value of the previous block, which is used for verifying and authorizing transactions. It also contains sender information related to the transaction. The hash value is sent as part of the block to verify the identity of the sender. The ordinary nodes calculate this value and append it to blocks that are sent to miner nodes. The timestamp is the real-time information utilized by the miner node to calculate the PoW. The trading set or content consists of instructions based on which actual energy transactions are carried out. For example, the trading set can include the price of energy trading and the quantity of energy traded.
The PoW is not sent with the transaction, instead, it will be calculated by the miner node and used to add new blocks to the blockchain. This involves solving complex mathematical problems (similar to calculating hash values) and then matching the solution with the hash values received from ordinary nodes. If these two values match, then the block (and the transactions within it) is considered real and processed. In summary, the working steps of the blockchain mechanism are as follows:
1. Entity (such as Entity 1) sends energy transaction requests in the network.
2. The request is passed to the miner node for identity verification. If the calculated hash value matches the received hash value, the miner node adds the transaction to the blockchain.
3. If the request is verified to be true, the miner node sends energy trading requests to other entities. For entities that agree to participate in the transaction (such as entity N), the miner node notifies entity 1 and conducts actual energy transactions. If multiple entities are interested in energy trading, Entity 1 decides which entity to engage in energy trading with.
4. Blockchain is used to transfer energy coins from entity 1 to entity N. Entity 1’s wallet is deducted based on the agreed amount. Then, the miner node uses a similar method to verify the wallet address of entity N.
The schematic diagram of the entire blockchain is shown in Figure 2.
3 The principle of the SSG
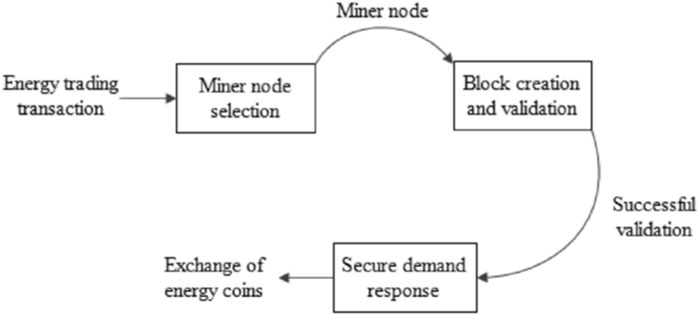
This section introduces the SSG scheme. First, the miner nodes are chosen to verify blocks created during the process of energy trading. Once the block verification is complete, the secure energy transactions are carried out according to the energy needs of the different entities. Figure 3 shows the complete algorithm process, and we will discuss the relevant stages in the following sections.
3.1 The selection of a miner node
The method of selecting an MN makes all entities in the SSG system miner nodes. Some previous studies have proposed MN selection methods (Chaudhary et al., 2019). For example, smart meters are utilized as miner nodes to access and store energy data for smart homes, or EVs are used as miner nodes to facilitate energy transactions in a smart transportation department, etc. The selection of a miner node depends on the types of available nodes and applications. Therefore, each MN selection method is unique to the problem. However, in this scheme, the miner nodes in our proposed method are chosen from various entities including family residences, industrial facilities, and buildings via analysis of the data associated with the entity’s processing capacity or electricity capacity. Algorithm 1 gives the MN selection process in detail.
Algorithm 1. Miner node selection.
Input:
Output: MNs
procedure SELECTION_of_MN (
/*Nodes in
Set
for
Get the power capacity
if
Put s in
end if
end for
/* Nodes in
Set
for
Obtain each b’s power capacity
if
Put b in
end if
end for
/* Nodes in
Set
for
Sort nodes in descending order based on processing power
Obtain
j
while (
temp
end while
if (
Put i in list
end if
end for
Select the top 50% nodes of
/* Nodes in
Set
for (
Obtain each e’s processing power
Ask e if it is possible to serve and store the protocol time in T (
Calculate
if (
Put e in
end if
end for
Calculate the amount of MNs
Randomly select MN from list
end procedure
First, the number of buildings, industries, smart homes (SHs), and EVs are taken as input for the algorithm and the output will be the selected MN. The algorithm utilizes different standards in order to select MNs from all existing entities. It is necessary to calculate the power capacity of SHs. SHs with power capacity greater than a threshold
The ratio of MNs to ordinary nodes (
3.2 The creation and validation of a block
After selecting the miner node, a block must be created and verified before it can be added to the blockchain. Therefore, the PoW of an ordinary node (such as entity E) is sent to the miner node. First, the first MN that resolves the PoW bootstraps the verification procedure by sending this PoW to the remaining nodes for review. The leading node adds blocks to the blockchain if the other results are consistent. Conversely, the blocks are abandoned, and the trade is invalid if the results mismatch. Algorithm 2 depicts the process of creating and validating the block. Table 1 explains the meanings of the symbols that appear in Algorithm 2.
Algorithm 2. The process of block creation and validation process between an ordinary node (E) and a miner node (MN).
Entity: (E)
Input:
Output: PoW
Calculate Wallet address:
Create Block Header:
Miner node: (MN)
Input:
Output: valid/Invalid transaction
Blockchain Validation
if (
return (valid)
else
return(invalid)
Send results for auditing to other miner nodes.
If consensus is reached, then accept the block
We explain entity E’s complete process of block creation as follows:
(a) The hash value
(b)
(c) Through merging the right and left sub-hash index pairs, we can compute the root’s hash in the Merkle hash tree, which is calculated together with the former
(d) The information of
(e) A 160-bit final hash value is generated by calculating a message digest (MD)
The process of verifying blocks (identifying whether they are real or tampered with) is performed by the miner node (MN). To this end, the miner node’s inputs are the PoW provided by
(a) First, the real trade received is computed by
(b) Next, the root node’s hash value of the Merkle hash tree is computed by
(c) Appending padding bits can generate a new fixed-length message. To provide an MD value (160-bit), the SHA-1 algorithm takes these padding bits as input. The provided value is actually a PoW (
(d) The
(e) The other MNs must agree on the block value and update it to put a block into an existing blockchain. To do this, the first miner node that solves the PoW will take the lead and broadcast its results to other miner nodes. If all of them reach an agreement, the algorithm adds the blocks to the blockchain and notifies all miner nodes. Otherwise, the block will be abandoned.
3.3 Management of safe demand response
This section describes how to trade energy from one entity to another. To trade energy, an EV will go to a buyer/seller (for example, an industry, home, or building) and then plug itself into the place to sell or buy energy. An energy transaction between one static entity and a mobile one occurs if it has been verified, as described in the previous section. Therefore, according to the energy demand of static entities, EVs trade energy from one place to another, as described in Aujla et al. (2018). There are two situations in this case. EVs are considered buyers if the static entities have additional energy, and EVs are considered energy providers when static entities need energy. We discuss these two cases in the following.
3.3.1 Electric vehicles act as buyers
EVs act as energy buyers if an entity, such as
The corresponding state-of-charge (SoC) level and an EV’s rated energy capacity (REC) determine the maximum amount of energy it can purchase. Therefore, given i-th EV’s maximum SoC level
The excess energy given by
where
Because the EV consumes energy in the process of driving from its position to
where
If entity
After the energy is sold to the EV,
It is possible that the value of
where
3.3.2 Electric vehicles act as providers
An EV can act as an energy supplier to provide a static entity
Because the required energy comes from EVs,
where
After
where
where
Another condition of a successful trade is that the EV owner’s announced price must be agreed to by
If the accessible energy is still smaller than
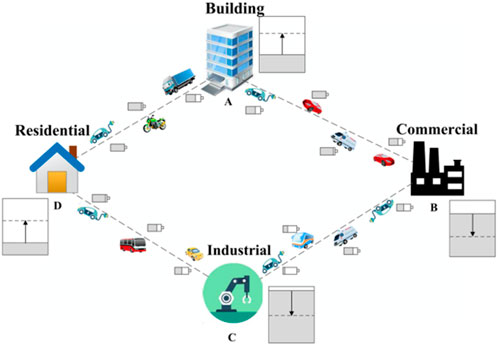
As previously described, once an energy transaction occurs, energy coins will be paid by the buyer to the seller (their wallets are updated synchronously) based on the blockchain. Figure 4 provides an example of such a transaction. Specifically, four different entities from various sectors, such as construction, commerce, industry, and residential, hope to perform energy trades with EVs to process their load requirements. In addition, different boxes denote the accessible energy of these entities. The dashed lines denote various entities’ LDs, and the solid black lines represent their total available energy. Therefore, as shown in Figure 4, EVs move to various entities, charging or discharging their batteries according to the energy needs of these entities and the energy available in the aforementioned EVs. Additionally, the blockchain transfers energy coins between various entities.
4 Experimental results and analysis
We discuss and analyze the experimental results in the following section.
4.1 The analysis of algorithm complexity
In this section, we evaluate the performance of the proposed method based on its communicational and computational costs.
4.1.1 Communicational cost
Given the two different entities named
(1) On entity €: If the bits of
(2) On the miner node (
4.1.2 Computational cost
When the blocks are created and validated, the involved computational operation mainly includes the add operation, hashing, and appending operation. The computational times for them need 1.0
(1) On entity (
(2) On the miner node (
4.2 The numerical results of the demand response process
Based on entity data from US Open Energy Information (Wilson, 2013), this paper simulates a scenario with 10 industrial buildings, 50 residences, and 30 commercial buildings. Subsequently, we use this scenario to test the proposed method for energy transactions. At the same time, in this scenario, 100 EVs (with energy capacity from 12 kWh to 36 kWh) are added, and their data are randomly assigned to simulate the real situation.
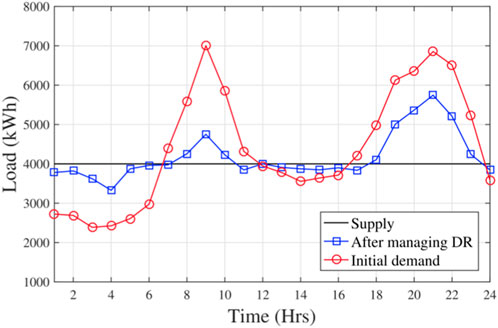
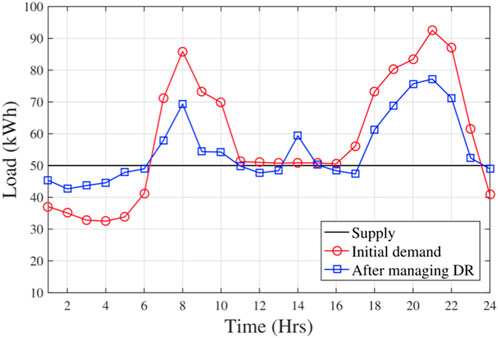
The entities’ demand responses need to be managed by the 4 MW fixed energy supply of the SG test scenario. From Figure 5, we can observe the total initial LD and the LD after managing the demand response and the supplied energy. We can infer from Figure 5 that the EV largely manages the LD of entities involved in transactions in some time gaps, which can help reduce their dependence on SG. Figure 7 shows an example of a negative LD of a building of commerce that provides 50 kWh of fixed energy. The building buys energy close to the EV from 0000 and 0600 hours and sells its energy to the EV from 0600 to 1100 hours and from 1600 to 2300 hours while this EV owns available energy after managing LD. EVs that need to purchase energy from an entity can be regarded as energy buyers. Figure 6 shows an example of a building for commercial selling its available energy to several EVs between 0800 and 1000 hours.
For an EV, the price charged by the EV is shown in Figure 7A, and the energy sold to the EV is shown in Figure 7B. The cost of an EV purchasing energy from commercial buildings is shown in Figure 7C. Likewise, when the LD management of an entity needs the energy of an EV, the EV serves as an energy supplier. For example, a building may require energy to manage its load from 0400 to 0600 hours in the case shown in Figure 6. The price charged by the EV for selling energy is shown in Figure 7A, and the related energy sold by an EV is shown in Figure 7B. The profitability of EVs is shown in Figure 7C.
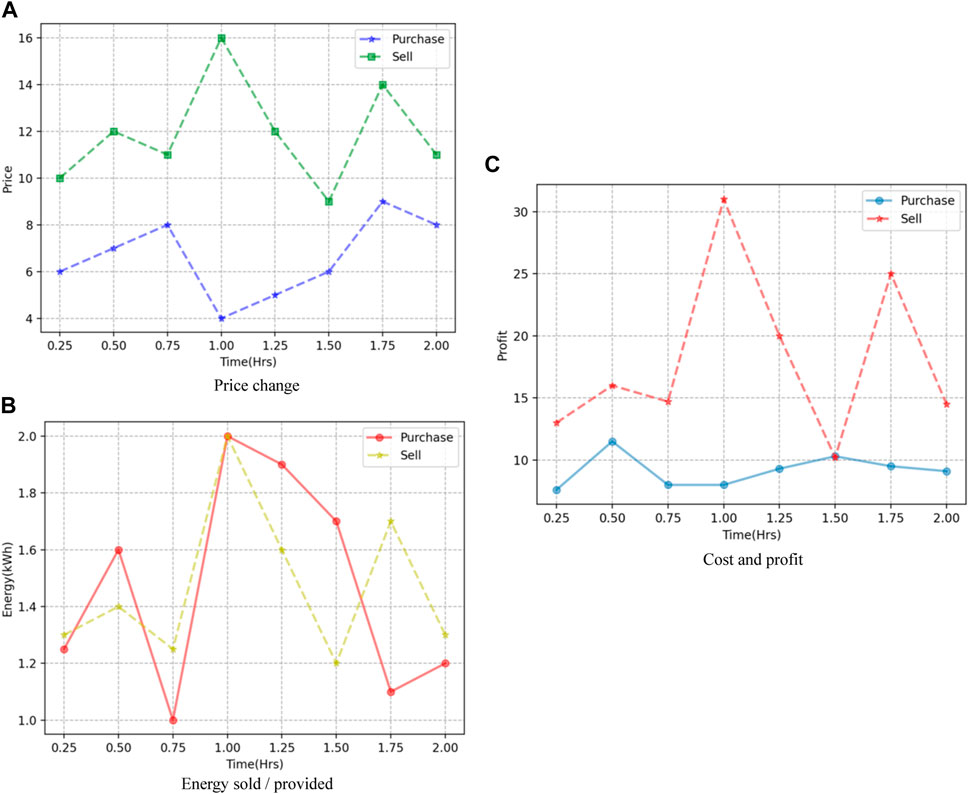
FIGURE 7. Comparison of energy consumers and providers. (A) Price change. (B) Energy sold/provided. (C) Cost and profit.
4.3 Safety assessment
We evaluate the security mechanism based on blockchain with several various metrics, that is, computational time, throughput, PoW generation time, and block preparation time, against changes in terms of the number of trades and nodes. Furthermore, we validate the security scheme on two datasets [one dataset from the literature (Kaur et al., 2018; Kumar et al., 2019), and the OEN (opening energy information) (Wilson, 2013)]. Specifically, from Figure 8A we can see the change in throughput as the total number of nodes is increasing. First, the quantity of trades every second is trending up and then further down without a major change. From Figure 8B, we can observe the consumed computation time as the number of nodes increases. It can be seen from the figure that after twelve nodes, the sharp increase trend of the initial level slows. The block preparation and proof-of-work generation times are also calculated. Figure 8C depicts the time of block preparation that appears to scale almost linearly with the increase in the number of trades. Interestingly, an analogous tendency of the proof-of-work generation curve with the increasing number of transactions can be seen in Figure 8D. Figures 8E, F show the higher throughput and lower computation time of the OEN dataset compared with that of the SG Lab dataset. The reason for this phenomenon lies in that compared with the data randomly generated in literature (Kaur et al., 2018; Kumar et al., 2019), the relevant datasets are structured.
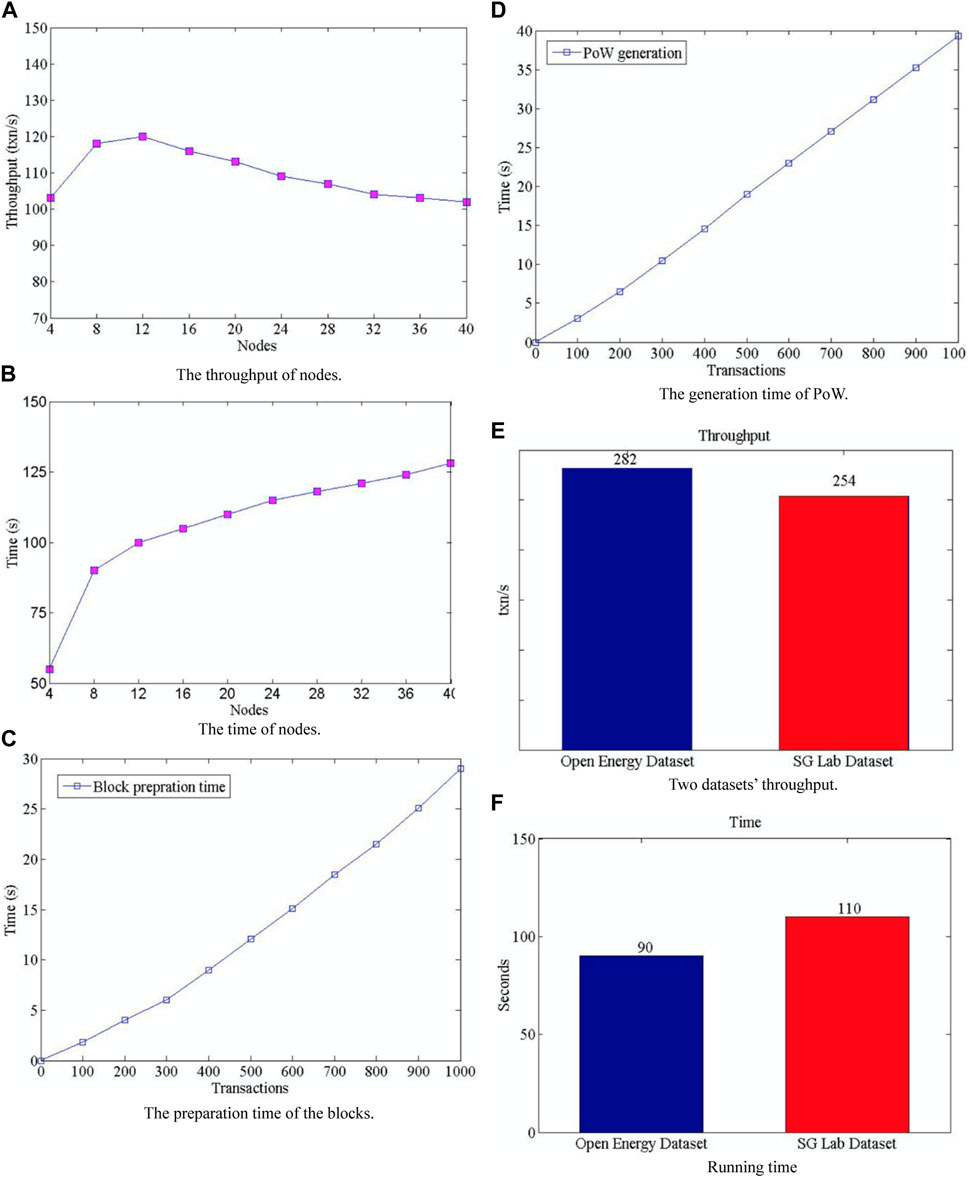
FIGURE 8. Safety assessment. (A) Node throughput. (B) Node time. (C) Block preparation time. (D) PoW generation time. (E) Throughput of the two datasets. (F) Running time.
4.4 Safety assessment
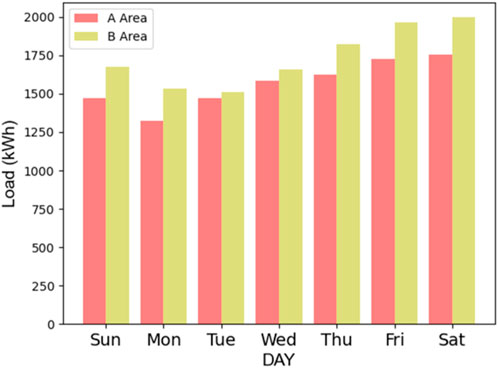
To better evaluate performance, we selected two approximate electricity consumption areas in Hangzhou, Zhejiang Province, China for comparison. The two areas consist of three commercial complexes and four residential areas with a total of 68 residential buildings. The method described in this article is deployed in Area A, while the traditional method is used as the control group in Area B. Each area has more than 120 EVs. We calculated a duration of 1 week, and the results are outlined below.
Figure 9 shows that compared to the traditional scheme, the method proposed in this article can reduce energy consumption by up to 18% and has good performance. At the same time, combined with energy sales, the method proposed in this paper has good economic benefits.
5 Conclusion
This paper proposes a demand response management method for smart grid ecosystem energy transaction security based on blockchain. The entities responsible for verifying energy trading are selected by the proposed method in the energy market. We can draw the following conclusions: 1) this scheme is capable of creating and validating blockchain blocks. If the validity of the data block is verified, energy transactions will be carried out. 2) The advantage of this method lies in the fact that even though a competitor participates in an energy transaction, the transaction cannot be tampered with because the transaction is added to the chain when all miner nodes have verified the transaction. 3) The experimental results show that the total communication and computational burden of this method are not high and that this method can effectively process the demand response of SGE.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material; further inquiries can be directed to the corresponding author.
Author contributions
WG, ZH, and LY contributed to the conception and design of the study. WG, LY, and ZD organized the database. YQ, LX, and GW performed the statistical analysis. ZH, WY, and YQ wrote the first draft of the manuscript. WY and LX wrote sections of the manuscript. All authors contributed to the article and approved the submitted version.
Funding
This research was funded by the National Natural Science Foundation of China (grant numbers 61862021 and 61662019).
Conflict of interest
Authors WG, ZH, YQ, ZD, LX, WY, and GW were employed by the Information and Communication Branch of Hainan Power Grid Co., Ltd. Author LY was employed by Hainan Power Grid Co., Ltd.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
An, D., Yang, Q., Li, D., Yu, W., Zhao, W., and Yan, C. B. (2020). Where Am I parking: Incentive online parking-space sharing mechanism with privacy protection. IEEE Trans. Automation Sci. Eng. 19 (1), 143–162. doi:10.1109/tase.2020.3024835
An, Q. (2017). Research and applications on the key techniques of decentralized transaction based on blockchain. Shanghai, China: Donghua University.
Aujla, G., Jindal, A., and Kumar, N. (2018). EVaaS: Electric vehicle-as-a-service for energy trading in SDN-enabled smart transportation system. Comput. Netw. 143 (10), 247–262. doi:10.1016/j.comnet.2018.07.008
Chaudhary, R., Jindal, A., Aujla, G., Aggarwal, S., Kumar, N., and Choo, K. K. R. (2019). Best: Blockchain-based secure energy trading in SDN-enabled intelligent transportation system. Comput. Secur. 85 (8), 288–299. doi:10.1016/j.cose.2019.05.006
Cheng, L., Chen, Y., and Liu, G. (2022). 2PnS-EG: A general two-population n-strategy evolutionary game for strategic long-term bidding in a deregulated market under different market clearing mechanisms. Int. J. Electr. Power & Energy Syst. 142, 108182. doi:10.1016/j.ijepes.2022.108182
Cheng, L., Liu, G., Huang, H., Wang, X., Chen, Y., Zhang, J., et al. (2020). Equilibrium analysis of general N-population multi-strategy games for generation-side long-term bidding: An evolutionary game perspective. J. Clean. Prod. 276, 124123. doi:10.1016/j.jclepro.2020.124123
Cheng, L., Yin, L., Wang, J., Shen, T., Chen, Y., Liu, G., et al. (2021). Behavioral decision-making in power demand-side response management: A multi-population evolutionary game dynamics perspective. Int. J. Electr. Power & Energy Syst. 129, 106743. doi:10.1016/j.ijepes.2020.106743
Fazio, M., Celesti, A., Ranjan, R., Liu, C., Chen, L., and Villari, M. (2016). Open issues in scheduling microservices in the cloud. IEEE Cloud Comput. 3 (5), 81–88. doi:10.1109/mcc.2016.112
Gao, Z., Peng, L., and Li, B. (2021). Research on the collaborative support of emerging new ICTs for power system automation. Power Syst. Prot. Control 49 (7), 160–166. doi:10.19783/j.cnki.pspc.200662
Jindal, A., Aujla, G., and Kumar, N. (2019). Survivor: A blockchain based edge-as-a-service framework for secure energy trading in SDN-enabled vehicle-to-grid environment. Comput. Netw. 153 (4), 36–48. doi:10.1016/j.comnet.2019.02.002
Jindal, A., Kumar, N., and Singh, M. (2020). Internet of energy-based demand response management scheme for smart homes and PHEVs using SVM. Future Gener. Comput. Syst. 108, 1058–1068. doi:10.1016/j.future.2018.04.003
Kang, J., Rong, Y., Huang, X., Maharjan, S., Zhang, Y., and Hossain, E. (2017). Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains. IEEE Trans. Industrial Inf. 13 (6), 3154–3164. doi:10.1109/tii.2017.2709784
Kaur, N., Aujla, G., Kumar, N., Zomaya, A. Y., Perera, C., and Ranjan, R. (2018). Tensor-based big data management scheme for dimensionality reduction problem in smart grid systems: SDN perspective. IEEE Trans. Knowl. Data Eng. 30 (10), 1985–1998. doi:10.1109/tkde.2018.2809747
Khan, O., Shah, M., Din, I., Kim, B. S., Khattak, H. A., and Rodrigues, J. J. P. C. (2018). Leveraging named data networking for fragmented networks in smart metropolitan cities. IEEE Access 6, 75899–75911. doi:10.1109/access.2018.2882811
Khoshkbarforoushha, A., Ranjan, R., Gaire, R., Abbasnejad, E., Wang, L., and Zomaya, A. Y. (2017). Distribution based workload modelling of continuous queries in clouds. IEEE Trans. Emerg. Top. Comput. 5 (1), 120–133. doi:10.1109/tetc.2016.2597546
Kumar, N., Aujla, G., Das, A., and Conti, M. (2019). ECCAuth: A secure authentication protocol for demand response management in a smart grid system. IEEE Trans. Industrial Inf. 15 (12), 6572–6582. doi:10.1109/tii.2019.2922697
Kurt, M., Yilmaz, Y., and Wang, X. (2020). Secure distributed dynamic state estimation in wide-area smart grids. IEEE Trans. Inf. Forensics Secur. 15, 800–815. doi:10.1109/tifs.2019.2928207
Li, Q., Wang, L., Zhang, Y., Liu, C. W., Yuan, Y. J., Lin, R., et al. (2020a). Anti-EGFR therapy in metastatic colorectal cancer: Mechanisms and potential regimens of drug resistance. Power Syst. Prot. Control 48 (19), 179–191. doi:10.1093/gastro/goaa026
Li, S., Wang, G., and Zhuang, L. (2020b). Reverse real-time model detection method for blockchain smart contract security. J. Chin. Comput. Syst. 41 (10), 2030–2035. doi:10.3969/j.issn.1000-1220.2020.10.003
Liu, C., Chai, K., and Zhang, X. (2018). Adaptive blockchain-based electric vehicle participation scheme in smart grid platform. IEEE Access 6, 25657–25665. doi:10.1109/ACCESS.2018.2835309
Liu, W., Wang, B., and Cao, Z. (2020). Design of shared charging pile platform of electric vehicle based on blockchain technology. Comput. Eng. Des. 41 (09), 2690–2696. doi:10.16208/j.issn1000-7024.2020.09.043
Maharjan, S., Zhang, Y., Gjessing, S., and Tsang, D. H. K. (2017). User-centric demand response management in the smart grid with multiple providers. IEEE Trans. Emerg. Top. Comput. 5 (4), 494–505. doi:10.1109/tetc.2014.2335541
Puthal, D., Malik, N., Mohanty, S., Kougianos, E., and Das, G. (2018). Everything you wanted to know about the blockchain: Its promise, components, processes, and problems. IEEE Consum. Electron. Mag. 7 (4), 6–14. doi:10.1109/mce.2018.2816299
Wang, K., Li, H., Maharjan, S., Zhang, Y., and Guo, S. (2018). Green energy scheduling for demand side management in the smart grid. IEEE Trans. Green Commun. Netw. 2 (2), 596–611. doi:10.1109/tgcn.2018.2797533
Wilson, E. (2013). Open energy information. Available: https://openei.org/datasets/dataset/commercial-and-residential-hourly-load-profiles-for-all-tmy3-locations-in-the-united-states.
Xu, Y. (2020). A review of cyber security risks of power systems: From static to dynamic false data attacks. Prot. Control Mod. Power Syst. 5 (1), 8–19. doi:10.1186/s41601-020-00164-w
Keywords: smart grid, blockchain, demand response management, network security, efficient
Citation: Guoshi W, Hairong Z, Ying L, Qing Y, Dazhi Z, Xiuli L, Yan W and Wei G (2023) A novel management scheme for power grid demand response based on blockchain. Front. Energy Res. 11:1183117. doi: 10.3389/fenrg.2023.1183117
Received: 09 March 2023; Accepted: 09 June 2023;
Published: 23 June 2023.
Edited by:
Xiaoyu Cao, Xi’an Jiaotong University, ChinaReviewed by:
Chunyu Chen, China University of Mining and Technology, ChinaShaoyan Li, North China Electric Power University, China
Copyright © 2023 Guoshi, Hairong, Ying, Qing, Dazhi, Xiuli, Yan and Wei. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Wang Guoshi, eWl6YXdlbjk3OTQyNTYyNTlAMTYzLmNvbQ==
 Wang Guoshi
Wang Guoshi Zhang Hairong1
Zhang Hairong1