- Tianhe Power Supply Bureau of Guangzhou Power Supply Bureau, Guangdong Power Co., Ltd., Guangzhou, China
In order to avoid safety problems caused by foreign bodies such as mice that may appear in the power distribution room and by demarcating the electronic fence area for key monitoring in the video surveillance screen, a foreign body intrusion monitoring and recognition approach in a power distribution room based on the improved YOLOv4 deep learning network is proposed. To optimize the detection effects, the YOLOv4 algorithm is improved from the aspects of network structure, frame detection, and loss function. At the same time, the channel pruning algorithm is used to prune the model to simplify the model structure. The experimental results show the effectiveness of the improved YOLOv4 deep learning network, which has high detection accuracy, fast detection speed, and takes up less space after pruning.
1 Introduction
With the deepening of the reform of the power system and the formation of the new normal of the macro economy, the competition in the energy consumption market has become increasingly fierce, and the external environment has gradually increased the service requirements of power grid operators and power supply companies (Kaur et al., 2020; Yuan et al., 2022; Liu et al., 2023). The existing management and monitoring mode of the power room is based on sensors, video monitoring, manual analysis, robot inspection, etc. (Dhiman and Kaur, 2019; Kumar and Dhiman, 2021; Yang et al., 2021). Artificial intelligence can be used to improve the level of automation management and monitoring of power rooms so as to provide customers with better power supply services (Jacob and Darney, 2021; Kiruthika et al., 2021; Liu et al., 2021). At present, equipment and security monitoring methods of some power distribution rooms are relatively backward, so they may not be able to timely and accurately reflect information about abnormal situations (Gangolells et al., 2010; Mroszczyk, 2015). Research studies on the intelligent identification technology of video surveillance based on deep learning can realize the real-time monitoring and identification of foreign body intrusion in the power room.
Target detection technology has been applied in this field for decades (Anastasiadou et al., 2021; Ren et al., 2021a; Chen et al., 2022; Qin et al., 2022; Yang et al., 2022). Traditional target detection can be divided into three steps: one is to select some candidate regions on a given image; the second step is to characterize these regions’ extraction; and the third step is to use the trained classifier for classification, generally selecting Bagging, AdaBoost, and support vector machine (SVM) (Tang et al., 2020; Wang et al., 2020; Yang et al., 2020). When the selected feature descriptor has good robustness, the performance of the traditional object detection algorithm is also acceptable. However, the traditional target detection has the problem that the artificially designed sliding window leads to an unsatisfactory detection effect (Ramcharan et al., 2017; Li et al., 2019). Now, deep learning techniques which are a powerful class of methods that can automatically learn feature representations from data, have developed rapidly, (Ker et al., 2017; Mezgec et al., 2019). In terms of foreign body detection, according to the low environmental adaptability of the existing foreign body detection and identification model, foreign body intrusion detection and the identification model for urban rail transit lines is constructed in the literature (Bashar, 2019). Singamaneni et al. (2022) proposed an improved YOLOv3 foreign body detection method for transmission lines, which has certain advantages in performance. One of the main problems it aimed to solve was that the image is prone to distortion during the insulator detection process and the model is greatly affected by the external environment. The algorithm in the literature (Aggarwal, 2019) first adopts adaptive gamma transform to automatically adjust the brightness of the insulator image, and YOLOv4 is used to learn the feature representation of different levels of the insulator. In order to simplify the complex structure of YOLOv4 target detection network, many parameters, high configuration required for training, and low number of transmission frames of real-time detection pictures, it is difficult to achieve industrial application popularization. The study by Sharma (2018) proposes an improved light-weight network based on the YOLOv4 quantization algorithm. The original YOLOv4 network is improved and optimized, the ShuffleNetv2 light-weight network is used to replace the original YOLOv4 backbone network, and the SENet module is integrated into ShuffleNetv2 to make the model converge better.
To bring a new and higher level of foreign body intrusion into the power distribution room, a foreign body intrusion monitoring and recognition approach in the power distribution room based on the improved YOLOv4 deep learning network is proposed. To optimize the detection effects, the YOLOv4 algorithm is improved from the aspects of the network structure, frame detection, and loss function. The main contributions of the study are summarized as follows:
(1) The YOLOv4 algorithm is improved from the aspects of the network structure, frame detection, and loss function.
(2) The channel pruning algorithm is used to prune the model to simplify the model structure and reduce the amount of calculation.
This paper is organized as follows: the first section establishes the design framework for foreign body intrusion recognition in power distribution rooms, the second section introduces the identification method of foreign body intrusion in power distribution rooms based on improved YOLOv4, the third section is experimental verification and analysis, and the fourth section is the conclusion.
2 Design framework for foreign body intrusion identification in a power distribution room
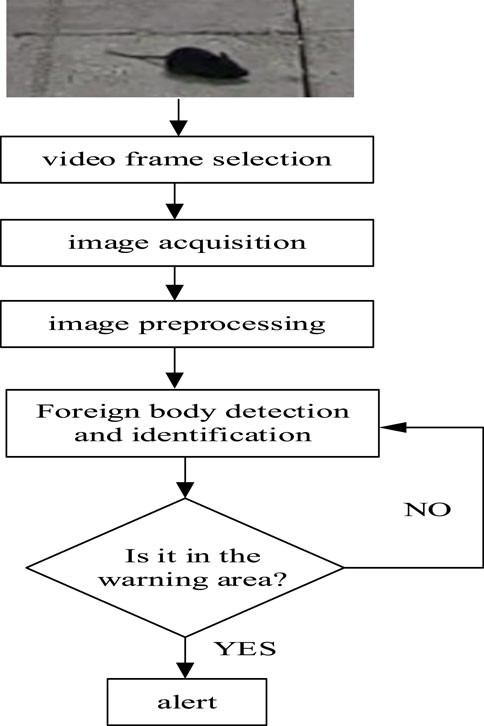
For the intrusion of foreign objects, the video frame is selected for frame selection, small target detection, classification, and identification. When abnormal intrusion is detected, its shape is captured through images, a general category judgment is made, and then corresponding alarms are sent to the duty personnel This would reduce the safety accidents caused by mice and other small animals entering the electric room by mistake. The detection steps are as follows:
Step 1 Video frame selection and format processing. According to the comprehensive consideration of the scene, demand, and performance, a reasonable video frame selection interval is designed, and the captured single frame picture is converted into a JPG format picture.
Step 2 Image preprocessing. Image preprocessing is performed on the format-converted image to remove some noise interference in the image and ensure that the training and inference data preprocessing operations are consistent.
Step 3 Small mouse detection and identification. According to the preprocessing result, the image is preprocessed before recognition, and then it is input into the foreign body detection model to determine whether a mouse is detected.
Step 4 Judgment results and output alarm information. According to the recognition result, if no mouse is detected, it will directly return to none to continue the detection. If detected, it will output alarm information. The identification process of foreign body intrusion in the power distribution room is shown in Figure 1.
3 Identification method of foreign body intrusion in a power distribution room based on improved YOLOv4
3.1 Data preprocessing
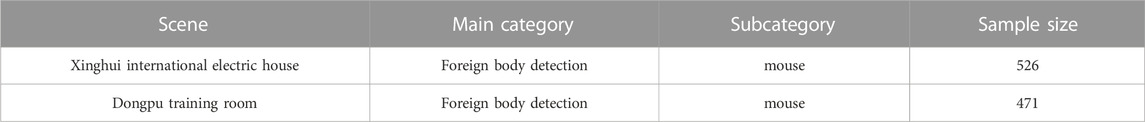
Based on the samples in the pilot electric room scene, labellum is used in this study to manually label foreign bodies such as mice in each image, and the minimum circumscribed rectangle of the target is used as the real frame during labeling. The number of annotations is shown in Table 1.
3.2 The improvement strategy of the YOLOv4 model
The YOLOv4 target detection algorithm is an improved version of the YOLOv3. Compared with YOLOv3, YOLOv4 implements feature extraction of input images through the backbone feature extraction network CSPDarknet53, and Path aggregation network (PANet) is used to achieve feature fusion between different output layers (Hu, 2022; Zhang et al., 2022).
In this study, the foreign body detection and recognition model in the distribution room based on the YOLOv4 algorithm is mainly composed of the following four modules: the center and scale prediction (CSP) module divides the stacking of the original residual blocks into two parts, one part continues the stacking of the residual blocks, the other part is connected to the output only after a small amount of processing (Ren et al., 2021b; Ahmad et al., 2022; Liang and Pei, 2022). The batch normalization and Mish (CBM) module is used to extract input image features. The spatial pyramid pooling (SPP) module uses the maximum pooling of different scales to pool the input feature layers and then stack them, which can greatly increase the receptive field.
3.2.1 The improvement of the network structure
The input image is scaled to a pixel size of 608 × 608 as the input of the network, and local features are extracted by convolution in three different scales. The three output feature maps of different sizes, 19 × 19, 38 × 38, and 76 × 76, correspond to scale 1, scale 2, and scale 3, respectively. Among them, the scale 19 × 19 adds some convolution blocks and then convolve the output detection frame information after the auxiliary basic network, the scale 38 × 38 introduces a new round of convolution based on the convolution before the end of scale 1 after block and up-sampling, and the CSPDarknet53 network is combined to perform the final convolution. Then, the regression judgment of the category and location is performed. To avoid problems such as label overlap, binary cross-sections perform category prediction, which is used to improve accuracy.
3.2.2 The optimization of border detection
In the process of dividing the input photo into M × M blocks, each of the detection boxes contains five parameters, which are the abscissa x of the object center position, the ordinate y, the confidence score Cobjec, the height h, and width w of the detection frame. It effectively reduces the influence of the bounding box regression dislocation caused by the fixed detection bounding box scale. As an improved YOLOv4 algorithm, the difference is that the offset of x and y is used as the linear expression of the length and width of the detection frame, as shown in Eqs. 1–4:
where Rx, Ry, Rw, and Rh are the estimated values of the four position coordinates on the feature map, respectively, and Px and Py represent the coordinate values of the center point. Then, the abscissa, ordinate, width, and height of the available frame information are studied, and the formulas for solving the values are as follows:
where bx, by, bw, and bh are the information of the obtained frame, cx and cy indicate the offset of the frame coordinates, and the width and sum of the preset anchor frame height are represented by Pw and Ph, respectively. On this basis, the mathematical expressions of confidence and intersection ratio are as follows:
where Pobject represents the probability that the target exists in the cell,
3.2.3 The optimization of loss function
Considering the contribution rate of each loss and the weight in training, the loss function of the improved YOLOv4 algorithm is as follows:
where Vi indicates whether there is a foreign body intrusion in the grid i; if there is an object, Vi = 1, otherwise it is 0.
3.2.4 YOLOv4 model simplification based on the channel pruning algorithm
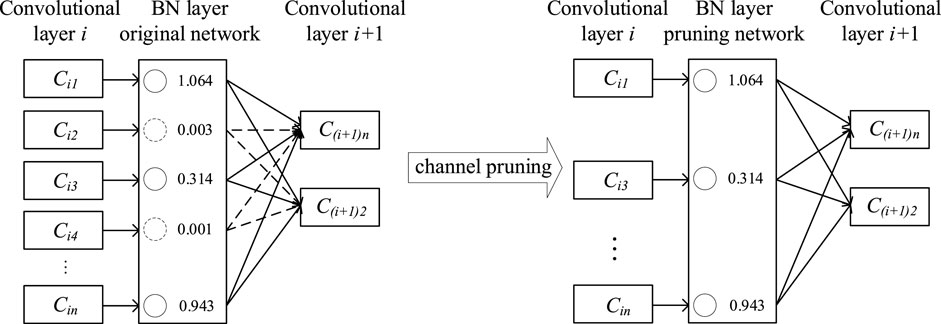
To improve the practicability of the detection model and reduce the calculation of the model amount, it is necessary to prune the model. The channel pruning algorithm is used in this study to prune the YOLOv4 model while ensuring accuracy. The channel pruning algorithm realizing the principle is shown in Figure 2.
During model training, the contribution rate of each input channel is scored using the coefficients of batch normalization (BN) layers in the network. The channel with a high contribution rate is retained, the channel with low contribution rate is pruned, and the pruned model structure is more compact.
3.3 Evaluation indicators
To evaluate the recognition effect, the average accuracy index is used to measure the matching accuracy of the detection frame to the target object; it can be expressed as:
where
The average precision metric is
4 Experimental verification and analysis
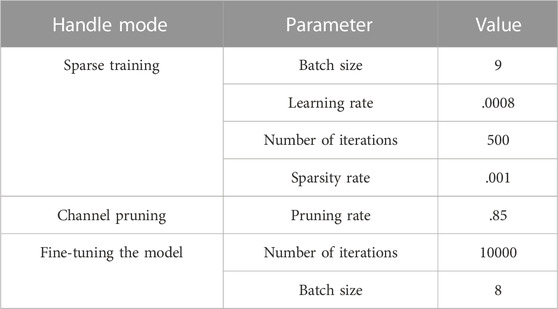
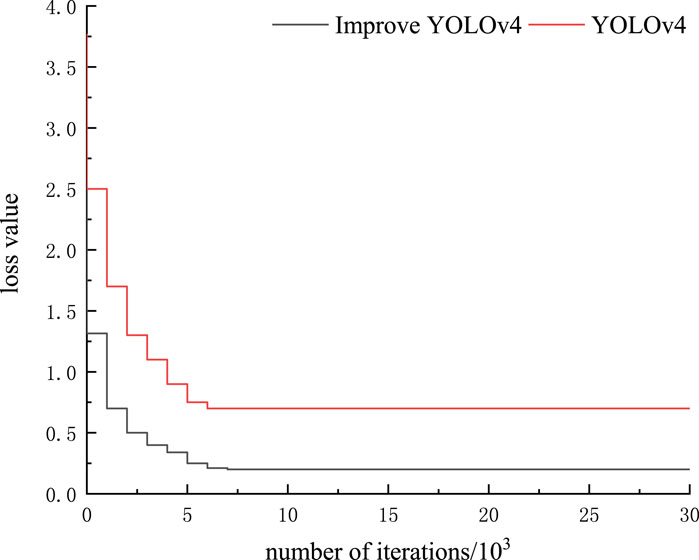
The experimental parameters are shown in Table 2 and Table 3. The identification object is a mouse in the power distribution room. The scene locations are the pilot power room and the Dongpu training room. The site is characterized by no light in the room, and the infrared white-light function of the camera needs to be automatically turned on. The camera deployment requirement is that in the pilot power room, at least one camera will monitor the entire power room. The height of the camera stand is 1 m and 2.3 m, respectively, and the angle is 15° downward. The experimental data can be referred to in the reference (Dhiman and Kumar, 2017; Li et al., 2021; Traoré and Pauwels, 2021; Xu et al., 2021). During the training phase, the base learning rate was .00001, the weight decay was .00005, the batch size was 64, and the momentum was .9. In this parameter setting, the change in the loss value in the training process of traditional YOLOv4 and improved YOLOv4 used is compared, and the results are shown in Figure 3.
In Figure 3, the loss values of the two networks decrease rapidly with the iterations, but it is evident that the loss value of the improved YOLO converges to a lower value of about .2, while the unimproved loss value is significantly higher at .5. Therefore, the loss value can directly reflect that the model of the improved YOLOv4 algorithm is more ideal, and the detection accuracy and speed are more in line with the experimental requirements.
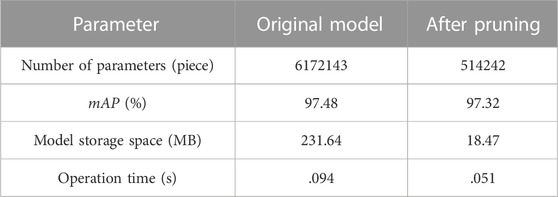
Table 4 shows the pruning result. After pruning, the number of parameters of the model is reduced by 91.67%, the storage space of the model is reduced by 213.17 MB, and the forward operation time is shortened by .043 s. After fine tuning, the model parameters and occupied space increased slightly, but the accuracy was still similar to that before pruning, and the forward propagation time did not change significantly. The results show that the pruning process can simplify the model while ensuring the original accuracy of the model.
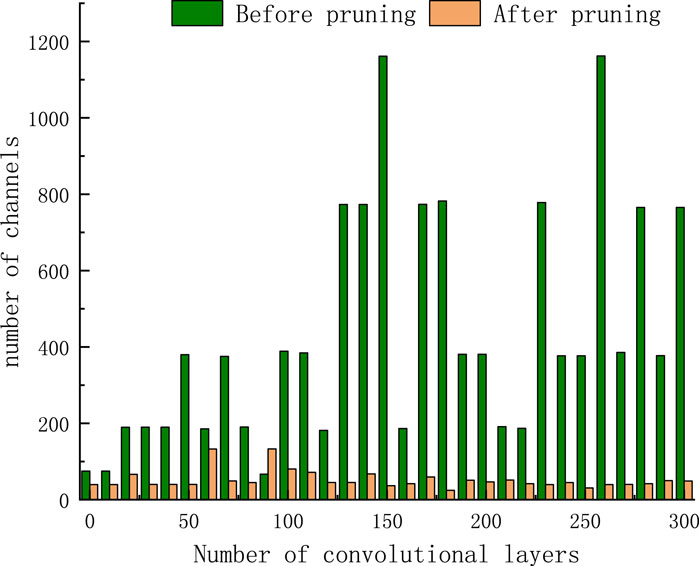
The number of channels in each layer after pruning is shown in Figure 4. As can be seen from Figure 4, the number of channels in each convolutional layer has been greatly reduced, which proves that the pruning algorithm is effective.
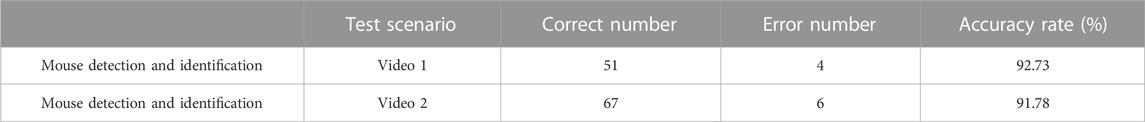
When the network training is performed for about 15,000 times, the loss value stabilizes around .2. At this time, the images in the test set are sent to the trained network for testing and verification, and the performance of foreign body recognition in various scenarios is shown in Table 5.
In Table 5, the result shows the good recognition performance, which can accurately identify the foreign body in different scenarios, showing good recognition performance.
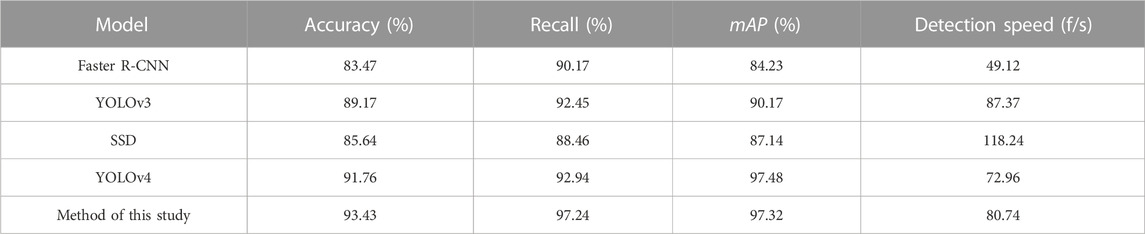
To reflect the superiority, the faster R-CNN (Stanford et al., 2017), YOLOv3 (Chen and Zhao, 2021), SSD (Dhiman and Kumar, 2018), and the YOLOv4 model are tested (Ma et al., 2021). After training, the test set data are used to evaluate the performance of these five algorithms. The evaluation results are shown in Table 6.
In Table 5, compared with the other four models, the accuracy of the method in this study is higher. The mAP of the YOLOv4 model after pruning is 1.6% lower than that of the YOLOv4 model before pruning, and the accuracy of the model after fine tuning is still similar to that before pruning. In terms of detection speed, although YOLOv3 and SSD are faster than the method proposed, their mAP is 7.3% and 10.5% lower than the method proposed in this study, respectively. In summary, compared with the other four models, the method in this study has higher mAP and higher detection speed, among which mAP is 13.5%, 7.3%, and 10.5% higher than faster R-CNN, YOLOv3, and SSD, respectively. The detection speed is 39.2% and 9.6% higher than faster R-CNN and YOLOv4, respectively. The detection accuracy of the method is high, the detection speed is fast, and the space occupied after pruning processing is small, which proves that the YOLOv4 detection model based on the pruning algorithm has high practicability and can be used for the detection of foreign bodies in power distribution rooms, thereby ensuring power distribution safety.
5 Conclusion
In this paper, a foreign body intrusion monitoring and recognition approach in the power distribution room based on the improved YOLOv4 deep learning network is proposed. To optimize the detection effect, the YOLOv4 algorithm is improved from the aspects of network structure, frame detection, and loss function. The results show that the proposed approach has higher mAP and higher detection speed. The mAP index is 13.5%, 7.3%, and 10.5% higher than faster R-CNN, YOLOv3, and SSD algorithm, respectively. The detection speed is, respectively, 39.2% and 9.6% higher than the faster R-CNN and YOLOv4 algorithms. The improved YOLOv4 has high detection accuracy, fast detection speed, and takes up less space after pruning. It can be used for the detection of foreign bodies in the power distribution room so as to ensure the safety of power distribution. However, it still needs to be pointed out that the model is based on the results of static image processing, and how to detect dynamic videos will be the main research direction in the future.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Funding
I and my fellow co-authors are fully aware of and agree with the payment of the listed article’s processing fee should the manuscript be accepted for publication.
Conflict of interest
SC, XD, ZW, PZ, and ZC were employed by Tianhe Power Supply Bureau of Guangzhou Power Supply Bureau, Guangdong Power Co. Ltd.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Aggarwal, L. P. (2019). Data augmentation in dermatology image recognition using machine learning. Skin Res. Technol. 25 (6), 815–820. doi:10.1111/srt.12726
Ahmad, F., Shahid, M., Alam, M., Ashraf, Z., Sajid, M., Kotecha, K., et al. (2022). Levelized multiple workflow allocation strategy under precedence constraints with task merging in IaaS cloud environment. IEEE Access 10, 92809–92827. doi:10.1109/access.2022.3202651
Anastasiadou, K., Gavanas, N., Pitsiava-Latinopoulou, M., and Bekiaris, E. (2021). Infrastructure planning for autonomous electric vehicles, integrating safety and sustainability aspects: A multi-criteria analysis approach. Energies 14 (17), 5269–5274. doi:10.3390/en14175269
Bashar, A. (2019). Survey on evolving deep learning neural network architectures. J. Artif. Intell. 1 (2), 73–82. doi:10.36548/jaicn.2019.2.003
Chen, Y., and Zhao, Q. (2021). Mineral exploration targeting by combination of recursive indicator elimination with the ℓ2-regularization logistic regression based on geochemical data. Ore Geol. Rev. 135 (2), 104213. doi:10.1016/j.oregeorev.2021.104213
Chen, Z., Yang, H., Bai, X., Gao, P., and Han, H. (2022). Image recognition method of power equipment based on deep learning. Electr. Technol. 9, 34–36.
Dhiman, G., and Kaur, A. (2019). Stoa: A bio-inspired based optimization algorithm for industrial engineering problems. Eng. Appl. Artif. Intell. 82, 148–174. doi:10.1016/j.engappai.2019.03.021
Dhiman, G., and Kumar, V. (2018). Emperor penguin optimizer: A bio-inspired algorithm for engineering problems. Knowledge-Based Syst. 159, 20–50. doi:10.1016/j.knosys.2018.06.001
Dhiman, G., and Kumar, V. (2017). Spotted hyena optimizer: A novel bio-inspired based metaheuristic technique for engineering applications. Adv. Eng. Softw. 114, 48–70. doi:10.1016/j.advengsoft.2017.05.014
Gangolells, M., Casals, M., Forcada, N., Roca, X., and Fuertes, A. (2010). Mitigating construction safety risks using prevention through design. J. Saf. Res. 41 (2), 107–122. doi:10.1016/j.jsr.2009.10.007
Hu, P. (2022). Detection and identification of foreign bodys in urban rail transit lines based on image processing. Automation Instrum. 9 (7), 86–90.
Jacob, I. J., and Darney, P. E. (2021). Design of deep learning algorithm for IoT application by image based recognition. J. ISMAC 3 (3), 276–290. doi:10.36548/jismac.2021.3.008
Kaur, S., Awasthi, L. K., Sangal, A. L., and Dhiman, G. (2020). Tunicate swarm algorithm: A new bio-inspired based metaheuristic paradigm for global optimization. Eng. Appl. Artif. Intell. 90, 103541. doi:10.1016/j.engappai.2020.103541
Ker, J., Wang, L., Rao, J., and Lim, T. (2017). Deep learning applications in medical image analysis. IEEE Access 6 (13), 9375–9389. doi:10.1109/access.2017.2788044
Kiruthika, S., Sakthi, P., Kaviya, M., and Vishnupriya, S. (2021). Blood bank monitoring and blood identification system using IoT device. Ann. Romanian Soc. Cell. Biol. 25 (6), 182–192.
Kumar, R., and Dhiman, G. (2021). A comparative study of fuzzy optimization through fuzzy number. Int. J. Mod. Res. 1, 1–14.
Li, B., Coutiño, M., Giannakis, G. B., and Leus, G. (2021). A momentum-guided frank-wolfe algorithm. IEEE Trans. Signal Process. 69 (12), 3597–3611. doi:10.1109/tsp.2021.3087910
Li, Y., Li, J., and Pan, J. S. (2019). Hyperspectral image recognition using SVM combined deep learning. J. Internet Technol. 20 (3), 851–859.
Liang, Liming, and Pei, Zou (2022). Insulator detection algorithm based on YOLOv4. Softw. Guide 21 (08), 132–137.
Liu, Y., Jin, T., Mohamed, M. A., and Wang, Q. (2021). A novel three-step classification approach based on time-dependent spectral features for complex power quality disturbances. IEEE Trans. Instrum. Meas. 70, 1–14. doi:10.1109/tim.2021.3050187
Liu, Y., Yuan, D., Gong, Z., Jin, T., and Mohamed, M. A. (2023). Adaptive spectral trend based optimized EWT for monitoring the parameters of multiple power quality disturbances. Int. J. Electr. Power and Energy Syst. 146, 108797. doi:10.1016/j.ijepes.2022.108797
Ma, F., Wang, B., Zhou, J., Jia, R., Luo, P., Wang, H., et al. (2021). An effective risk identification method for power fence operation based on neighborhood correlation network and vector calculation. Energy Rep. 7, 6995–7003. doi:10.1016/j.egyr.2021.10.061
Mezgec, S., Eftimov, T., Bucher, T., and Korousic Seljak, B. (2019). Mixed deep learning and natural language processing method for fake-food image recognition and standardization to help automated dietary assessment. Public health Nutr. 22 (7), 1193–1202. doi:10.1017/S1368980018000708
Qin, Z., Ming, L., Song, W., and Zhang, W. (2022). Helmet detection method based on lightweight deep learning model. Sci. Technol. Eng. 22 (14), 5659–5665.
Ramcharan, A., Baranowski, K., McCloskey, P., Ahmed, B., Legg, J., and Hughes, D. P. (2017). Deep learning for image-based cassava disease detection. Front. plant Sci. 8 (14), 1852–2201. doi:10.3389/fpls.2017.01852
Ren, G., Han, H., and Li, C. (2021). Detection of foreign bodys in coal mine belt transportation based on Fast_YOLOv3 algorithm [J]. Industrial Min. Automation 47 (12), 128–133.
Ren, X., Yue, C., Ma, T., Wang, J., Wang, J., Wu, Y., et al. (2021). Adaptive parameters optimization model with 3D information extraction for infrared small target detection based on particle swarm optimization algorithm. Infrared Phys. Technol. 117 (3), 103838–103847. doi:10.1016/j.infrared.2021.103838
Sharma, A. (2018). Guided stochastic gradient descent algorithm for inconsistent datasets. Appl. Soft Comput. 73 (5), 1068–1080. doi:10.1016/j.asoc.2018.09.038
Singamaneni, K. K., Dhiman, G., Juneja, S., Muhammad, G., AlQahtani, S. A., and Zaki, J. (2022). A novel QKD approach to enhance IIOT privacy and computational knacks. Sensors 22 (18), 6741. doi:10.3390/s22186741
Stanford, F. C., Alfaris, N., Gomez, G., Ricks, E. T., Shukla, A. P., Corey, K. E., et al. (2017). The utility of weight loss medications after bariatric surgery for weight regain or inadequate weight loss: A multi-center study. Surg. Obes. Relat. Dis. 13 (3), 491–500. doi:10.1016/j.soard.2016.10.018
Tang, H., Liu, H., Xiao, W., and Sebe, N. (2020). When dictionary learning meets deep learning: Deep dictionary learning and coding network for image recognition with limited data. IEEE Trans. neural Netw. Learn. Syst. 32 (5), 2129–2141. doi:10.1109/tnnls.2020.2997289
Traoré, C., and Pauwels, E. (2021). Sequential convergence of AdaGrad algorithm for smooth convex optimization. Operations Res. Lett. 49 (4), 452–458. doi:10.1016/j.orl.2021.04.011
Wang, J., Luo, J., Liu, B., Feng, R., Lu, L., and Zou, H. (2020). Automated diabetic retinopathy grading and lesion detection based on the modified R-FCN object-detection algorithm. IET Comput. Vis. 14 (1), 1–8. doi:10.1049/iet-cvi.2018.5508
Xu, D., Zhang, S., Zhang, H., and Mandic, D. P. (2021). Convergence of the RMSProp deep learning method with penalty for nonconvex optimization. Neural Netw. 139, 17–23. doi:10.1016/j.neunet.2021.02.011
Yang, J., Zhang, Y., and Mao, X. (2020). Deep learning detection method for safety helmets on construction work surfaces. Comput. Appl. 40 (S2), 178–182. doi:10.1002/cpe.6234
Yang, T., Xu, G., and Yan, J. (2022). Design of safety helmet and mask detection system based on deep learning. Comput. Knowl. Technol. 18 (10), 15–18.
Yang, X., Zhang, Y., Lv, W., and Wang, D. (2021). Image recognition of wind turbine blade damage based on a deep learning model with transfer learning and an ensemble learning classifier. Renew. Energy 163 (5), 386–397. doi:10.1016/j.renene.2020.08.125
Yuan, D., Liu, Y., Lan, M., Jin, T., and Mohamed, M. A. (2022). A novel recognition method for complex power quality disturbances based on visualization trajectory circle and machine vision. IEEE Trans. Instrum. Meas. 71, 1–13. doi:10.1109/tim.2022.3204985
Keywords: power distribution room, foreign body intrusion monitoring, improved YOLOv4, channel pruning algorithm, monitoring-highway hazard
Citation: Chen S, Dai X, Wang Z, Zhang P and Chen Z (2023) Foreign body intrusion monitoring and recognition approach in a power distribution room based on the improved YOLOv4 deep learning network. Front. Energy Res. 10:1090033. doi: 10.3389/fenrg.2022.1090033
Received: 04 November 2022; Accepted: 30 December 2022;
Published: 12 January 2023.
Edited by:
Amrit Mukherjee, University of South Bohemia in České Budějovice, CzechiaReviewed by:
Gaurav Dhiman, Government Bikram College of Commerce Patiala, IndiaRamin Ranjbarzadeh, Dublin City University, Ireland
Copyright © 2023 Chen, Dai, Wang, Zhang and Chen. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zengyu Wang, d2FuZ3plbmd5dWd6cHNAZ21haWwuY29t
 Shenyu Chen
Shenyu Chen Zengyu Wang
Zengyu Wang