- 1Electrical Engineering Department, Faculty of Engineering, Lakehead University, Thunder Bay, ON, Canada
- 2Department of Electrical and Computer Engineering, University of Saskatchewan, Saskatoon, SK, Canada
This paper studies a two-user downlink non-orthogonal multiple access (NOMA) system that adopts an improper Gaussian signaling (IGS) strategy to compensate for the performance loss due to imperfect successive interference cancellation (SIC). Joint optimization problems are formulated to maximize the overall spectral efficiency and energy efficiency of a two-user NOMA system under minimum user-rate requirements and total power constraints. Sub-optimal solutions of IGS circularity coefficients and power allocation are obtained for the formulated problems. Furthermore, improper constellation diagrams are designed using widely linear transformation with predefined optimized IGS coefficients to study the impact of IGS on throughput and error performance. Simulation results show that the performance of IGS-based NOMA systems, where the IGS strategy is adopted by both users, outperforms that of the proper Gaussian signal (PGS)-based NOMA system under imperfect SIC.
1 Introduction
Proper Gaussian Signaling (PGS) has been widely adopted in communication systems due to its attractive entropy-maximizing property, which is proved to achieve the maximum spectral efficiency in additive white Gaussian noise (AWGN) channels but not in the case of an interference channel (Zeng et al., 2013a; Zeng et al., 2013b; Lameiro et al., 2017). Moreover, the majority of the wireless products assume a proper signal model for the underlying circularly symmetric complex Gaussian (CSCG) signals, which is in contrast with many of the real-world applications. As a definition, a proper complex random variable has equal energy and uncorrelated real and imaginary components of a complex random entity, whereas any correlation between the two components results in an improper complex random variable. The improper characteristics with non-identical variance on the real and imaginary components are known to exist in some well-known constellation diagrams such as binary phase-shift keying and continuous phase modulation (CPM) (Javed et al., 2020).
The traditional complex-valued signal processing assumes a vanishing pseudo-covariance, i.e., equals zero, which is not accurate for many real-world scenarios where the concerned signals are frequently improper (Javed et al., 2020). Such simplified assumption not only results in misleading analysis and inaccurate results but also prohibits us from investigating the potential benefit of the additional degree of the freedom offered by improper signaling. By relaxing the constraints of PGS, i.e., equal power and uncorrelated real and imaginary components, we have what is called improper Gaussian signaling (IGS) (Schreier and Scharf, 2010; Javed et al., 2020). In practical systems, improper signaling techniques have already existed in linear receivers for Global System for Mobile communication and third Generation Partnership Project systems (Kurniawan and Sun, 2015). It has been shown that IGS attains higher degrees of freedom than PGS due to its ability to identify the interference signal dimension. In fact, it can be described as a kind of interference alignment technique since it mitigates interference by using its alignment in only one orthogonal signal space dimension, and by extracting the desired signal from the other orthogonal space (Cadambe et al., 2010). Due to these impropriety characteristics, IGS has been identified as a potential candidate for improving the spectral efficiency in interference-limited systems (Schreier and Scharf, 2010; Javed et al., 2020).
Non-orthogonal multiple access (NOMA) has been introduced as a potential candidate for enabling heavily-loaded systems using limited resources while improving the spectral efficiency (Islam et al., 2017). In that sense, in the downlink of NOMA systems, multiple users can be served simultaneously on one resource block by implementing superposition coding at the base-station side and successive interference cancellation (SIC) at the users’ side (Ding et al., 2014). This leads to spectrally-efficient systems provided that perfect SIC is performed, which is not a realistic assumption. In practice, detectors suffer from imperfect SIC, which leads to an interference-limited NOMA system (Yue et al., 2018). This encourages us to consider IGS as a promising solution to recompense for the SIC imperfections in such interference-limited scenarios.
In orthogonal multiple access (OMA) schemes, IGS has been investigated in interference Z-channel models (Zeng et al., 2013a; Zeng et al., 2013b; Lameiro et al., 2017), multiple-input multiple-output interference-limited systems (Nguyen et al., 2021), and broadcast channels (Shin et al., 2012; Nasir et al., 2019), where the achievable throughout regions and degrees of freedom were derived. IGS was also considered in Z-channel cognitive radio (CR) networks, where IGS was proven to be beneficial in reducing the interference to primary users in various unlicensed spectrum-sharing models (Lameiro et al., 2019). IGS was also evaluated in cooperative full-duplex relaying (CR) systems (Gaafar et al., 2017), where IGS was used to help the secondary user access the spectrum. Similar work in (Gaafar et al., 2018) was investigated in non-CR systems under Nakagami-m fading, where it was concluded that using IGS can eliminate the impact of residual self-interference by revising the signal impropriety.
Recent works considered IGS in NOMA interference-limited systems. The authors in (Hong and Bahk, 2020) investigated the performance of a two-user downlink NOMA system using IGS, by deriving the outage probability and the ergodic capacity expressions. In (Tuan et al., 2019), transmit precoding schemes were designed for a multi-cell network in order to maximize the users’ minimum rates under various power budget constraints. In (Yu et al., 2020), IGS scheme was generated for signal beamforming with the goal of improving the spectral efficiency of a multi-cell network and protecting the users’ secrecy. Our previous works in (Abu Mahady et al., 2019; Mahady et al., 2021) studied a two-user downlink point-to-point NOMA system with IGS under imperfect SIC, where sum-rate was maximized under user rate constraints in the cases of one user and two users employing IGS, respectively. Compared with these previous works, this work also considers the maximization of the system energy efficiency given the QoS and power budget requirements. In addition, this work designs IGS constellation diagrams using optimized IGS coefficients found through the spectral efficiency maximization problem. Moreover, error performance is simulated using the optimized constellation diagrams.
In particular, in this work, we investigate the potential merits of using IGS in a downlink two-user NOMA systems under SIC imperfection, where a BS serves two users in a near-far setup. In particular, the user closer to the BS (user 1) employs imperfect SIC to extract and forward user 2’s signal in addition to detecting its own signal. We first derive the exact expressions for each user’s rate when using IGS at both users. Due to the superiority of IGS over PGS in terms of spectral and energy efficiencies in interference-limited scenarios, we formulate two optimization problems for spectral efficiency and energy efficiency. In each formulated problem, we jointly optimize the BS transmit power and the transmit signal’s circularity coefficients. We propose iterative algorithms to find sub-optimal solutions to the developed non-convex optimization problems based on the Karush-Kuhn-Tucker (KKT) conditions. Additionally, we show the efficacy of the optimized circularity coefficient on the transmit constellations at the BS and the system error performance, where improper constellation diagrams are designed using widely linear transformation (WLT) based on the optimized IGS circularity coefficients. Simulation results demonstrate the vital impact of IGS over PGS in the context of NOMA systems under imperfect SIC.
Organization: The remainder of this paper is organized as follows: Preliminary IGS definition and generation are given in Section 2. The system and channel models are introduced in Section 3. The optimization problems are solved in Section 4. Simulation results are presented in Section 5. Finally, the conclusion is given in Section 6.
2 Preliminary: Improper Gaussian Signaling Definition and Generation
2.1 Improper Random Variables
Let Ωx and
Definition 1: A signal is called proper if it is uncorrelated with its complex conjugate and has a zero pseudo-variance, i.e.,
Definition 2. : The impropriety degree (or the IGS coefficient) of x is given as
2.2 Improper Constellation Design
WLT is known as one of the most common ways of transforming proper signals into improper ones. In (Santamaria et al., 2018; Lopez-Fernandez et al., 2019; Javed et al., 2021), an easy design involving the generation of improper discrete constellations was considered, where a WLT of a standard unit energy proper M-quadrature amplitude modulation (QAM) constellation was used. In these works, the WLT was designed to maximize the minimum Euclidean distance between the improper constellation points, while keeping the signal energy the same.
Specifically, an improper constellation design, with a complex symbol x and predefined circularity coefficient κx, can be obtained from a proper constellation design with complex symbol s with a unit power
where the superscript (⋅)* refers to the complex conjugation operation, ϵ and ɛ are complex-valued quantities such that |ϵ|2 + |ɛ|2 = 1 (to maintain unit transmit power),
3 Channel and System Models
3.1 Channel Model
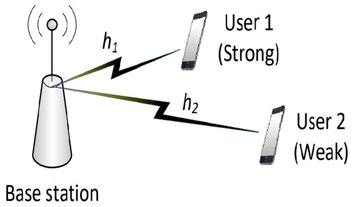
A downlink two-user NOMA system model with a base station (BS) is considered in this work as shown in Figure 1. The Rayleigh model is considered for the channels between the BS and users. We denote hi, ∀i = 1, 2, as the channel variables with zero-mean and variance
As per power-domain NOMA basics, users experience different channel conditions with the assumption of |h1|2 > |h2|2 and P2 > P1. Consequently, user 1, which has a better channel condition, can decode its own signal after removing the signal of user 2, which has worse channel condition, through SIC processing (Zeng et al., 2017). Meanwhile, user 2 can decode its own signal assuming the interference inflicted by user 1 is negligible and can thus be dealt with as noise. Since user 1’s receiver has imperfect SIC, there exists a residual interference as an outcome from this imperfection. Generally, the residual interference resulting from imperfect SIC is a complicated function of multiple factors, e.g., coding/modulation related parameters, channel related issues (fading and shadowing), device/hardware/battery related restrictions, etc. Furthermore, due to the characteristics of error propagation due to imperfect SIC, it is hard to model its impact. It is stated in (Sun et al., 2016a) and (Chen et al., 2018) that a linear model can effectively demonstrate the relationship between the residual interference and the received signal power. To introduce the impact of imperfect SIC, we adopt this linear model here. Under such a model of imperfect SIC, the received signal after SIC at user 1 is given in (Eq. 2), where η denotes the coefficient of imperfect SIC at user 1. Note that η = 0, corresponds to perfect SIC, and η = 1, corresponds to no interference cancellation.
3.2 Spectral Efficiency Analysis
Since IGS is considered at both users, i.e., x1 and x2 are improper, and imperfect SIC is assumed, we first need to find the new expressions for the users’ information rates. Hence, closed-form expressions are obtained for the spectral efficiency for each user in the considered system model. To do so, we characterize the received signals at each user as follows
where xi, ∀i = 1, 2, is the signal for the ith user and ni is additive white Gaussian noise (AWGN) at the ith user’s receiver. The component
To continue, based on (Zeng et al., 2013b), the user’s rate definition in the case of IGS is given as
where
After a few mathematical manipulations and assuming, for simplicity, that
In the same way, the rate of user 2,
It is worth-note that each
4 Optimization Problems
In this section, two optimization problems are formulated to maximize both the overall spectral efficiency and the energy efficiency under the constraints of each user’s minimum rate requirements and power budget.
4.1 Spectral Efficiency Maximization
Maximizing the overall spectral efficiency is a common objective in wireless systems. However, to avoid having all resources taken by one user, the quality of service (QoS) constraints are often enforced when formulating the overall spectral efficiency maximization. A joint optimization problem is developed to optimize both the IGS circularity coefficients
In this optimization problem, we assume that the BS uses the total available power. For simplicity, we denote α1 = α and α2 = 1 − α. Based on the analysis of the rate expressions in Section 3.2., we can improve the overall sum rate in the case both users are employing IGS. That mentioned, the joint optimization problem can be developed as
where
The objective and rate constraints in the formulated optimization (Eqs 7a–7e) are non-convex which lead to a non-convex problem. To tackle this issue, the formulated problem can be optimized by using the necessary but not sufficient Karush-Kuhn-Tucker (KKT) conditions to find sub-optimal solutions for the circularity coefficient
The Lagrangian function corresponding to (Eqs 7a–7e) can be outlined as
where λ1 ≥ 0 and λ2 ≥ 0 are the Lagrange multipliers associated with the minimum rates constraints of user 1 and user 2, respectively. Based on the above, the KKT conditions can be described as follows (Boyd et al., 2003).
The results of (Eqs 9a–9c) are found as in (Eq. 10), (Eq. 11), and (Eq. 12) at the top of the next page, where
Algorithm 1. : Spectral efficiency maximization algorithm.
From the KKT conditions mentioned earlier, we need to check all alternatives of λi, ∀i = 1, 2. As can be seen from (Eqs 9d, 9e), it is either we have λ1 = 0 or
Case 1. :Inactive QoS constraints, when both λ1 = λ2 = 0.
Case 2. : The sub-optimal solutions of
Case 3. : The sub-optimal solutions of
Case 4. : The sub-optimal solutions of
• Step 3: the proposed algorithm starts by assuming that both the minimum user rate constraints are inactive. Then, we find the optimal solution based on this assumption. If the inactive constraints are satisfied, then the optimal solution is reached.
• Step 4: based on the assumption that solution belongs to Case 1 (inactive constraints), the user 1 minimum rate constraint may be not inactive. This means that initial solution from step 3 is infeasible and the proposed algorithm finds the Lagrangian multipliers that enforce the solution to be in the feasible region. More specifically, the proposed algorithm finds the non-negative Lagrangian multiplier λ1 that makes user 1 minimum rate constraint active (i.e., satisfied with equal sign)-Case 2.
• Step 5: based on the assumption that solution belongs to Case 1 (inactive constraints), the user 2 minimum rate constraint may be not inactive. This means that initial solution from step 3 is infeasible and the proposed algorithm finds the Lagrangian multipliers that enforce the solution to be in the feasible region. More specifically, the proposed algorithm finds the non-negative Lagrangian multiplier λ2 that makes user 2 minimum rate constraint active (i.e., satisfied with equal sign)-Case 3.
• Step 6: based on the assumption that solution belongs to Case 1 (inactive constraints), both minimum rate constraints may be not inactive. This means that initial solution from step 3 is infeasible, and the proposed algorithm finds the Lagrangian multipliers that enforce the solution to be in the feasible region. More specifically, the proposed algorithm finds the non-negative Lagrangian multiplier λ1, λ2 that makes both minimum rate constraints active (i.e., satisfied with equal sign)-Case 4.
• At the end, the optimal IGS circularity coefficients and power allocation parameter are obtained and the corresponding maximum sum-rate can be computed.
4.2 Energy Efficiency Maximization
In this subsection, we maximize the energy efficiency of the two-user system considering both QoS and BS power constraints.
where Pc is the BS’s circuitry power consumption. The optimization problem in (Eq. 14a) is equivalent to the following minimization problem
The objective function of (Eq. 15) and rate constraints are non-convex; hence, the overall problem is non-convex, and the global optimal solution cannot be ensured.
The fractional non-convex optimization problem in (Eq. 15) can be converted to an equivalent parametric optimization problem using concepts from fractional programming, namely the Dinkelbach approach (Dinkelbach, 1967). Using this conversion, a new objective function can be found as
where
It was proved in (Dinkelbach, 1967) that at a certain value of
To find the sub-optimal solutions, we solve
where λ1, λ2 and λ3 are the Lagrange multipliers connected with the QoS conditions of user 1, user 2, and power allocation at the BS, respectively. The impact of the constraints
From (Eq. 19a), we obtain
and
To find the sub-optimal solution in case of energy efficiency maximization, we follow similar steps to the previous analysis of KKT conditions in the spectral efficiency maximization algorithm. From (Eqs 19c–19e), we either have λ1 = 0 or
Description of Step 3 in the Algorithm 2: We assume the optimal solution belongs to the case where the QoS and power allocation constraints are inactive. We initially find the sub-optimal solution when assuming all constraints are satisfied (inactive constraints), and then for those constraints that are not satisfied, we find their Lagrange multipliers to make them satisfied with equal sign. We initially set λ1 = λ2 = λ3 = 0 and find initial
If
If
If
If
If
If
If
The energy efficiency solution is found at
The complexity analysis of Algorithm 2 can be described as follows.
• Step 3: the complexity order of this step is the complexity of Algorithm 1. Let us assume that the maximum number of iterations needed for the subgradient method to converge is T, then the number of operations is of a complexity order equal to
• Thus, the complexity order up to Step 4 (of Algorithm 2) is
• Accordingly, the complexity order of the proposed Algorithm 2 is
Algorithm 2. : Energy efficiency maximization algorithm.
5 Simulation Results
In this section, we evaluate the proposed solutions of the formulated optimization problems. A comparison in terms of the overall spectral efficiency and energy efficiency of the system with its counterpart of a NOMA system employing traditional PGS at both users is performed. We also compare the proposed solution with (Abu Mahady et al., 2019) that considers IGS only at the strong user. We consider the distance-dependent path-loss model as a form of large-scale fading, and the Rayleigh fading model as small-scale multi-path fading. The channel from the BS to user i, ∀i = 1, 2, at a distance of di meters is generated as
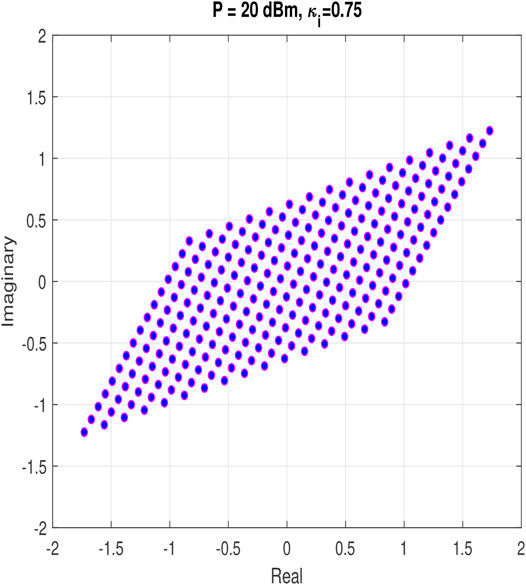
Figures 2, 3 show two examples of the improper constellation diagrams with 64-QAM and 256-QAM, respectively, which are designed based on WLT as described in Section 2. We generate unit average energy standard 64-QAM and 256-QAM constellations. Next, we find the optimized
In Figure 4, the overall spectral efficiency of the system is depicted as a function of PT, at different levels of the SIC imperfections η. The performance of the modified proposed Algorithm 1 (jointly optimizing IGS circularity coefficients
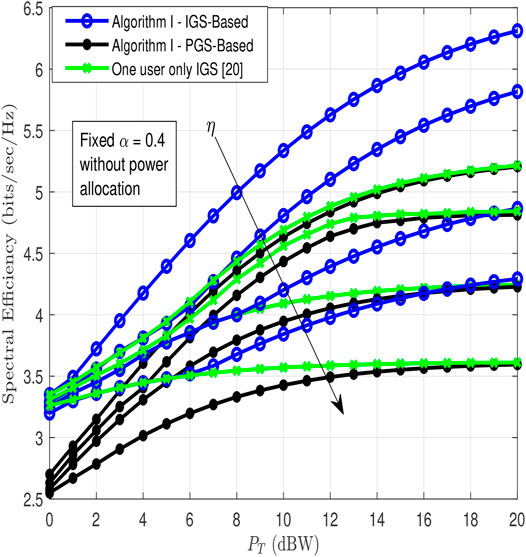
FIGURE 4. Spectral efficiency comparison between IGS-based and PGS-based (Abu Mahady et al., 2019) for various η = 0.1, 0.2, 0.3, 0.4, and fixed α = 0.4.
A spectral efficiency of about 4 bits/s/Hz can be attained by the modified proposed algorithm at 3 dBW power at η = 0.1 and α = 0.4. To achieve the same spectral efficiency of 4 bits/s/Hz using only one user IGS-based and PGS-based schemes, nearly 2 to 2.5 dBW power are needed, respectively. It is also observed that as the SIC becomes worse, i.e., from η = 0.1 to η = 0.4, the performance of all schemes gets worse. However, the PGS-based scheme is the most impacted scheme.
While Figure 4 assumes the fixed power allocation, i.e., (α = 0.4) scenario, Figure 5 presents the optimized power allocation scenario. In particular, Figure 5 shows the behaviour of the proposed spectral efficiency algorithm (IGS-based with optimized power allocation) and its counterpart PGS-based NOMA system. It is clear that there is a further gain improvement for IGS-based scheme over the PGS-based one at different values of η. In overall, the results reveal the positive influence of jointly optimizing both IGS coefficients and power allocation parameter to enhance the NOMA system’s spectral efficiency under imperfect SIC.
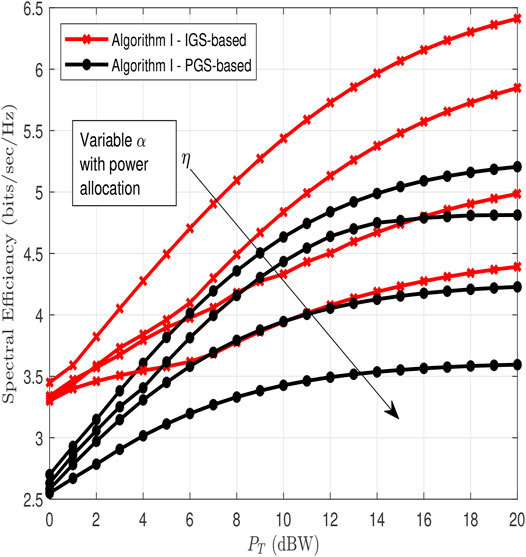
FIGURE 5. Spectral efficiency comparison between IGS-based and PGS-based for various values of η = 0.1, 0.2, 0.3, 0.4 and optimized α.
In Figure 6, the convergence of the proposed spectral efficiency algorithm is compared with the proposed algorithm for the one user only IGS-based scheme in (Abu Mahady et al., 2019) at η = 0.1. The number of iterations required for IGS in the proposed algorithm is approximately double the number of iterations required for the algorithm in (Abu Mahady et al., 2019) but it is still relatively low.
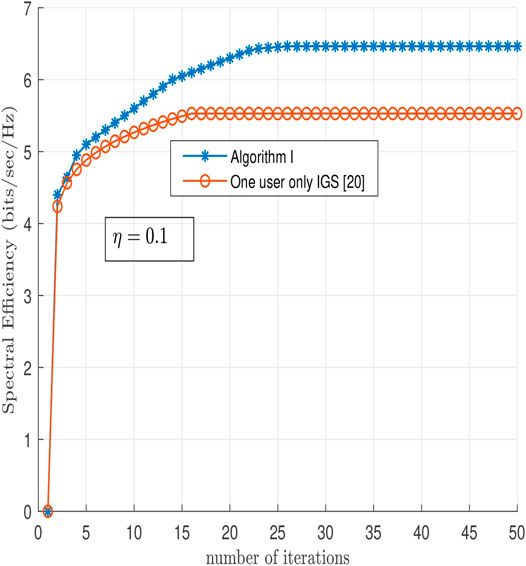
FIGURE 6. Comparison between the convergence of the Algorithm 1 and the Algorithm in (Abu Mahady et al., 2019) in terms of number of iterations at η = 0.1.
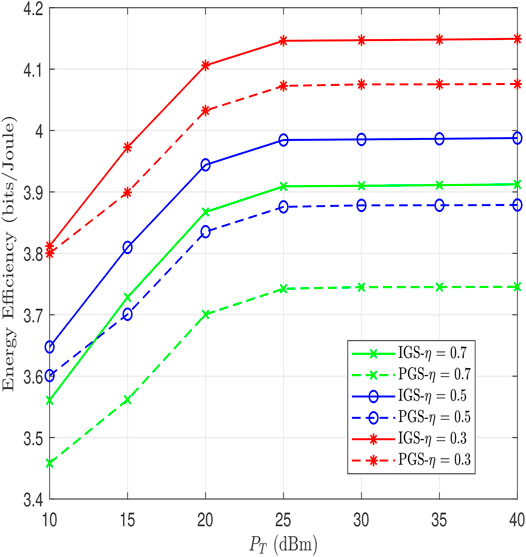
In Figure 7, the performance of the energy efficiency algorithm (in bits/joule) is plotted against PT (dBm) at Pc = 20, 25 dBm. This figure shows that IGS enhances the energy efficiency performance in the proposed system by transmitting around 0.3 bits/joule more than PGS in all BS power regions. It is also observed that as the BS’s power increases from low to medium, the energy efficiency performance improves. However, the energy efficiency saturates when the BS’s transmit power increases which means that increasing the transmit power does not necessarily enhance the energy efficiency.
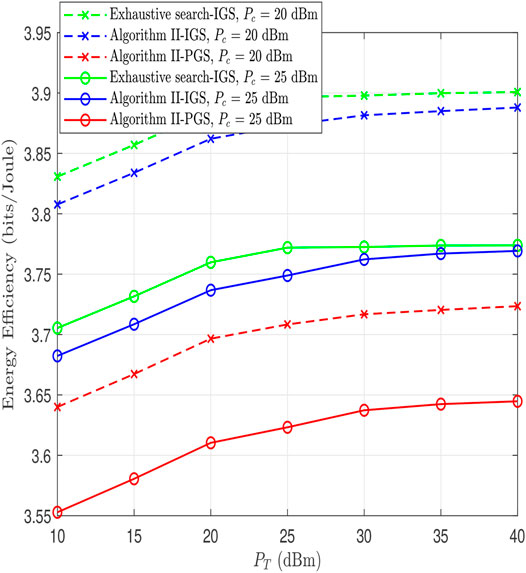
FIGURE 7. Energy efficiency vs. P (dBm) at different values of Pc for proposed Algorithm 2 and exhaustive search.
To demonstrate how closes it is to the optimal solution, we compared the proposed sub-optimal solution with optimal solution through an exhaustive search, where the latter is performed through three nested loops with a step size of 0.05 (the three optimization variables are all bounded between 0 and 1). The result is a gap of around of 0.1 dB, which is acceptable performance loss given the high computational complexity of the exhaustive search solution.
Figure 8 shows the energy efficiency performance against PT dBm at different levels of SIC and at fixed Pc = 20 dBm. The figure shows the effectiveness of using IGS in the case of SIC imperfections when compared to the PGS case, especially at higher levels of η. As η increases, the gain due to using IGS becomes greater.
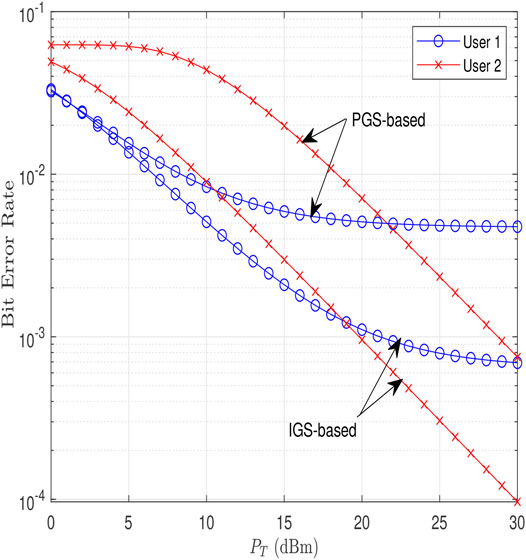
Figure 9 shows the bit error rate (BER) through simulations versus PT for both users in case of IGS and PGS at 16-QAM at η = 0.1. For each channel realization, we find the optimal improper coefficients, then we find the corresponding improper constellation diagram, simulate the error rate, and repeat. For a given optimal IGS circularity coefficients, we study the BER performance of the new improper constellations, by means of 104 simulations, where each simulation considering the decoding of 104 symbols. The optimal maximum likelihood detector is applied at the receiver side for this problem, which aims to finding the closest constellation point to a given noisy received signal. It should be noted that this approach may not result in the optimal BER performance since the decision variables κi and αi are optimized to maximize the transmission rates (to approach Shannon capacity).
As can be seen in the figure, error performance in case of using improper constellation diagrams outperforms that of the proper constellation. The reason behind this is that since the improper constellation is designed based on WLT which relies on maximizing the minimum Euclidean distance, and hence achieves a better BER. Another observation is that as PT increases, error performance improves as expected. However, error floor occurs at high PT in case of user 1 due to residual interference resulting from the imperfect SIC.
6 Conclusion
In this work, the system spectral and energy efficiencies of a two-user NOMA system adopting IGS at both users are maximized such that the minimum rate requirements and power budget constraints are met under imperfect SIC. In addition, to study the system performance, improper constellations are designed using WLT based on predefined optimized IGS coefficients. Results showed that system spectral and energy efficiencies of the IGS-based NOMA systems are further improved by jointly optimizing the circularity coefficients at both users compared to the case of optimizing the circularity coefficient of the single user IGS-based systems and PGS-based NOMA systems. In contrast to PGS-based NOMA systems, results revealed that IGS can save around 0.2 dB of the transmit power, and hence, can be identified as an energy efficient signaling scheme. Furthermore, the results demonstrate that the error performance of the IGS-based system outperforms its counterpart PGS-based system due to impropriety characteristics of the constellation.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author Contributions
IA: Sole author, idea, proposed algorithm, simulations, and writing up. EB: Technical supervision, contribute to the idea, discussion, and writing revision. SI: Technical supervision, contribute to the idea, discussion, and writing revision.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abu Mahady, I., Bedeer, E., Ikki, S., and Yanikomeroglu, H. (2019). Sum-rate Maximization of NOMA Systems under Imperfect Successive Interference Cancellation. IEEE Commun. Lett. 23 (3), 474–477. doi:10.1109/LCOMM.2019.2893195
Boyd, S., Xiao, L., and Mutapcic, A. (2003). “Subgradient Methods,” in Lecture Notes of EE392o (Autumn Quarter: Stanford University).
Cadambe, V. R., Jafar, S. A., and Wang, C. (2010). Interference Alignment with Asymmetric Complex Signaling-Settling the Høst-Madsen-Nosratinia Conjecture. IEEE Trans. Inform. Theor. 56 (9), 4552–4565. doi:10.1109/tit.2010.2053895
Chen, X., Zhang, Z., Zhong, C., Jia, R., and Ng, D. W. K. (2018). Fully Non-orthogonal Communication for Massive Access. IEEE Trans. Commun. 66 (4), 1717–1731. doi:10.1109/tcomm.2017.2779150
Ding, Z., Yang, Z., Fan, P., and Poor, H. V. (2014). On the Performance of Non-orthogonal Multiple Access in 5G Systems with Randomly Deployed Users. IEEE Signal. Process. Lett. 21 (12), 1501–1505. doi:10.1109/lsp.2014.2343971
Dinkelbach, W. (1967). On Nonlinear Fractional Programming. Manage. Sci. 13 (7), 492–498. doi:10.1287/mnsc.13.7.492
Gaafar, M., Amin, O., Abediseid, W., and Alouini, M.-S. (2017). Underlay Spectrum Sharing Techniques with In-Band Full-Duplex Systems Using Improper Gaussian Signaling. IEEE Trans. Wireless Commun. 16 (1), 235–249. doi:10.1109/twc.2016.2621767
Gaafar, M., Khafagy, M. G., Amin, O., Schaefer, R. F., and Alouini, M.-S. (2018). Full-Duplex Relaying with Improper Gaussian Signaling over Nakagami- $m$ Fading Channels. IEEE Trans. Commun. 66 (1), 64–78. doi:10.1109/tcomm.2017.2759109
Hong, S. G., and Bahk, S. (2020). Performance Analysis and Fairness Maximization in NOMA Systems with Improper Gaussian Signaling under Imperfect Successive Interference Cancellation. IEEE Access 8, 50439–50451. doi:10.1109/access.2020.2980167
Islam, S. M. R., Avazov, N., Dobre, O. A., and Kwak, K.-s. (2017). Power-domain Non-orthogonal Multiple Access (NOMA) in 5G Systems: Potentials and Challenges. IEEE Commun. Surv. Tutorials 19 (2), 721–742. doi:10.1109/comst.2016.2621116
Javed, S., Amin, O., Shihada, B., and Alouini, M.-S. (2020). A Journey from Improper Gaussian Signaling to Asymmetric Signaling. IEEE Commun. Surv. Tutorials 22 (3), 1539–1591. doi:10.1109/comst.2020.2989626
Javed, S., Elzanaty, A., Amin, O., Shihada, B., and Alouini, M.-S. (2021). When Probabilistic Shaping Realizes Improper Signaling for Hardware Distortion Mitigation. IEEE Trans. Commun. 69 (8), 5028–5042. doi:10.1109/tcomm.2021.3074978
Kurniawan, E., and Sun, S. (2015). Improper Gaussian Signaling Scheme for the Z-Interference Channel. IEEE Trans. Wireless Commun. 14 (7), 3912–3923. doi:10.1109/twc.2015.2414913
Lameiro, C., Santamaria, I., and Schreier, P. J. (2019). Improper Gaussian Signaling for Multiple-Access Channels in Underlay Cognitive Radio. IEEE Trans. Commun. 67 (3), 1817–1830. doi:10.1109/TCOMM.2018.2880765
Lameiro, C., Santamaría, I., and Schreier, P. J. (2017). Rate Region Boundary of the SISO Z-Interference Channel with Improper Signaling. IEEE Trans. Commun. 65 (3), 1022–1034. doi:10.1109/TCOMM.2016.2641948
Lopez-Fernandez, J. A., Ayestaran, R. G., Santamaria, I., and Lameiro, C. (2019). Design of Asymptotically Optimal Improper Constellations with Hexagonal Packing. IEEE Trans. Commun. 67 (8), 5445–5457. doi:10.1109/tcomm.2019.2916857
Mahady, I., Bedeer, E., Ikki, S., and Yanikomeroglu, H. (2021). “NOMA Spectral Efficiency Maximization with Improper Gaussian Signaling and SIC Imperfection,” in ICC 2021 - IEEE International Conference on Communications, Montreal, QC, 14-23 June 2021, 1–6. doi:10.1109/icc42927.2021.9500779
Moré, J. J. M. Y., and Cosnard, M. (1979). Numerical Solution of Nonlinear Equations. ACM Trans. Math. Softw. 5 (1), 64–85. doi:10.1145/355815.355820
Nasir, A. A., Tuan, H. D., Duong, T. Q., and Poor, H. V. (2019). Improper Gaussian Signaling for Broadcast Interference Networks. IEEE Signal. Process. Lett. 26 (6), 808–812. doi:10.1109/lsp.2019.2905959
Nguyen, H. T., Tuan, H. D., Niyato, D., Kim, D. I., and Vincent Poor, H. (2021). Improper Gaussian Signaling for D2D Communication Coexisting MISO Cellular Networks. IEEE Trans. Wireless Commun. 20 (8), 5186–5198. doi:10.1109/twc.2021.3065961
Santamaria, I., Crespo, P. M., Lameiro, C., and Schreier, P. J. (2018). Information-theoretic Analysis of a Family of Improper Discrete Constellations. Entropy (Basel) 20 (1), 1–22. doi:10.3390/e20010045
Schreier, P. J., and Scharf, L. L. (2010). Statistical Signal Processing of Complex-Valued Data: The Theory of Improper and Noncircular Signals. Cambridge, U.K.: Cambridge Univ. Press.
Shin, H.-Y., Park, S.-H., Park, H., and Lee, I. (2012). A New Approach of Interference Alignment through Asymmetric Complex Signaling and Multiuser Diversity. IEEE Trans. Wireless Commun. 11 (3), 880–884. doi:10.1109/twc.2012.010312.102034
Sun, H., Xie, B., Hu, R. Q., and Wu, G. (2016). “Non-orthogonal Multiple Access with SIC Error Propagation in Downlink Wireless MIMO Networks,” in 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18-21 Sept. 2016, 1–5. doi:10.1109/vtcfall.2016.7881111
Sun, S., Rappaport, T. S., Rangan, S., Thomas, T. A., Ghosh, A., Kovacs, I. Z., et al. (2016). “Propagation Path Loss Models for 5G Urban Micro- and Macro-Cellular Scenarios,” in 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15-18 May 2016, 1–6. doi:10.1109/vtcspring.2016.7504435
Tuan, H. D., Nasir, A. A., Nguyen, H. H., Duong, T. Q., and Poor, H. V. (2019). Non-orthogonal Multiple Access with Improper Gaussian Signaling. IEEE J. Sel. Top. Signal. Process. 13 (3), 496–507. doi:10.1109/jstsp.2019.2901993
Yu, H., Tuan, H. D., Duong, T. Q., Fang, Y., and Hanzo, L. (2020). Improper Gaussian Signaling for Integrated Data and Energy Networking. IEEE Trans. Commun. 68 (6), 3922–3934. doi:10.1109/tcomm.2020.2981332
Yue, X., Qin, Z., Liu, Y., Kang, S., and Chen, Y. (2018). A Unified Framework for Non-orthogonal Multiple Access. IEEE Trans. Commun. 66 (11), 5346–5359. doi:10.1109/tcomm.2018.2842217
Zeng, M., Yadav, A., Dobre, O. A., Tsiropoulos, G. I., and Poor, H. V. (2017). Capacity Comparison between MIMO-NOMA and MIMO-OMA with Multiple Users in a Cluster. IEEE J. Select. Areas Commun. 35 (10), 2413–2424. doi:10.1109/jsac.2017.2725879
Zeng, Y., Yetis, C. M., Gunawan, E., Guan, Y. L., and Zhang, R. (2013). Transmit Optimization with Improper Gaussian Signaling for Interference Channels. IEEE Trans. Signal. Process. 61 (11), 2899–2913. doi:10.1109/tsp.2013.2254480
Keywords: improper Gaussian signaling, non-orthogonal multiple access, spectral efficiency, successive interference cancellation, error probability
Citation: Abu Mahady I, Bedeer E and Ikki S (2022) Non-Orthogonal Multiple Access: The Case of Improper Gaussian Signaling and Imperfect Successive Interference Cancellation. Front. Comms. Net 3:821037. doi: 10.3389/frcmn.2022.821037
Received: 23 November 2021; Accepted: 17 February 2022;
Published: 22 March 2022.
Edited by:
Mohamed Saad, University of Sharjah, United Arab EmiratesReviewed by:
Saeed Abdallah, University of Sharjah, United Arab EmiratesAlister Burr, University of York, United Kingdom
Copyright © 2022 Abu Mahady, Bedeer and Ikki. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Islam Abu Mahady, aWFidW1haEBsYWtlaGVhZHUuY2E=
 Islam Abu Mahady
Islam Abu Mahady Ebrahim Bedeer
Ebrahim Bedeer Salama Ikki
Salama Ikki