- School of Information Engineering, Jiangxi University of Science and Technology, Ganzhou, Jiangxi, China
Introduction: Blockchain technology has attracted much attention due to its decentralization, transparency and security. Initially applied in the financial field, it has now expanded to various fields such as Internet of Things (IoT), electronic cash and healthcare. However, the open nature of blockchain has raised potential security concerns about sensitive transaction data, and the increasing number of transactions requires low-latency solutions. Most blockchain applications still rely on the lightweight Elliptic Curve Digital Signature Algorithm (ECDSA). Due to complex operations such as vectorized multiplication and modular inversion, this may introduce significant additional overhead.
Methods: To address these issues, a new scheme named KTP-ECDSA is proposed. This scheme is based on the improved two-parameter Elliptic Curve Digital Signature Algorithm (TP-ECDSA) and the KGLP algorithm. In both the signing and verification processes, this scheme eliminates modular inverse operations and reduces scalar multiplications during the verification stage by using batch verification.
Result: The experimental results show that, compared with the traditional ECDSA, KTP-ECDSA has achieved a speed increase of over 50% in both independent verification and batch verification, significantly improving the efficiency of signature verification.
Discussion: By adopting the KTP-ECDSA algorithm and using the digital signature batch verification method, multiple signatures can be verified simultaneously, thus reducing the computational burden of the traditional single-verification method. This greatly increases the overall transaction throughput and improves resource utilization efficiency.
1 Introduction
Blockchain is essentially a new type of distributed database that integrates a series of emerging information technologies (Lin, 2023), including consensus mechanisms, encryption algorithms, network communication, and smart contracts. These technologies also contribute to the decentralization, transparency, traceability, and immutability of blockchain, which plays a significant role in finance (Puthiyidam et al., 2023; Wang et al., 2020), electronic cash (Jiarui et al., 2023), and the Internet of Things (IoT) (Mahajan and Junnarkar, 2023). In particular, the development of blockchain in cryptocurrency has made it a modern network technology (Zhang et al., 2022). As Blockchain 1.0, Bitcoin has received widespread attention for its successful deployment and application of ECDSA. ECDSA is gradually becoming the default signature mechanism for the current mainstream blockchain platforms and projects. The efficient development of any network technology must consider its cybersecurity factors (Khizar et al., 2022; Marcos et al., 2023), and digital signature technology in cryptography can effectively solve some security problems in blockchain.
The digital signature algorithm (DSA) uses asymmetric encryption technology to achieve information identity authentication, data integrity verification, and tamper resistance (Fang et al., 2020). In blockchain, each transaction needs to be verified by a digital signature before being added to the block. However, blockchain faces the challenge of large-scale data transactions in electronic cash applications. With the rapid development of the electronic cash market, the number of transactions and the scale of transaction data are increasing. In order to obtain real-time results, it is important to verify multiple signatures at any given point in time, and the signature verification of large-scale transaction tasks can cause cumbersome overhead to nodes (Rahman Taleb and Vergnaud, 2021). Therefore, finding a way to improve the efficiency and security of ECDSA signature verification has become a key issue. Currently, ECDSA remains one of the mainstream algorithms in the blockchain field (Yehuda, , 2021). Nevertheless, the implementation of this algorithm presents two significant mathematical challenges. The first is modular inversion, which is 10 times slower than multiplication (Kittur et al., 2017). The second is ECC scalar multiplication (Binbin et al., 2024), which is performed in both the signature and verification stages, making it a crucial factor influencing the efficiency of ECDSA.
In response to the above two problems, various schemes have been proposed to improve the ECDSA modular inversion and scalar multiplication operations. Zhang et al. (2008) proposed a fast verification ECDSA scheme that only performs scalar multiplication and modular multiplication operations to increase the operation speed. The limitations to the above scheme are that although the computational efficiency is improved, simply increasing the efficiency of signatures by reducing the number of inverse operations can lead to security issues with forged signatures, and forward security cannot be guaranteed. Therefore, Xiao et al. (2020) proposed an ECDSA scheme without modular inversion, which introduces two random parameters to improve efficiency while effectively ensuring the security of the scheme. Cao and Wei (2018) proposed an improved ECDSA protocol that effectively avoids modular inversion operations by using the SHA-256 algorithm to improve efficiency.
However, the above solutions are all based on independent verification methods. In the face of the signature verification task of large-scale transactions, using independent verification schemes is not sufficient to meet strict low-latency requirements (Liu et al., 2021). In 1994, Fiat (1997) introduced the concept of batch verification, a method that verifies multiple signatures simultaneously, reduces repetitive computation operations, and greatly saves the verifier’s computational resources and verification latency. In signature schemes such as DSA and RSA, batch verification has been widely applied (Lim and Lee, 1994; Bao et al., 2006). For ECDSA, researchers have proposed various batch verification schemes (Karati et al., 2014). Although there are technologies for batch verification of multiple ECDSA signatures, many of them have a major drawback that they are not efficient for larger batch verification. Therefore, in real-time scenarios, where a large number of signatures need to be verified at once, it is important to have a performance solution that can perform well, regardless of the signature size without compromising security. Kittur and Pais (2017) introduced a batch verification scheme for multiple ECDSA signatures. This scheme introduces batch verification technology, which combines multiple signature verification steps into one step, thereby reducing the computational and communication overhead and improving the efficiency of signature verification while ensuring security. Xiong et al. introduced an ECDSA signature scheme based on blockchain with fault-tolerant batch verification. Using batch verification technology, the verification of multiple signatures is combined into a set operation, thereby improving the efficiency of verification.
Although existing technologies attempt to reduce the overhead of verification time, for large-scale signature verification, the verification efficiency of most batch verification schemes is not high (Yu et al., 2023). To improve the efficiency of large-scale verification tasks, this paper proposes a blockchain-based dual-parameter ECDSA batch verification scheme based on the improvement of ECDSA. The scheme can verify multiple signatures at once based on the modulo inversion algorithm, and it introduces the KGLP algorithm to accelerate the scalar multiplication operation, thus greatly reducing the verification time and significantly improving the efficiency of the scheme. It can also prevent digital signature forgery attacks.
The rest of this paper is organized as follows: Section 2 introduces the basics of ECDSA and cryptography in blockchain. Section 3 proposes a signature algorithm based on two-parameter ECDSA using the KGLP algorithm and batch verification technique. Section 4 analyzes the scheme in terms of security. Section 5 analyzes the performance of the scheme. Finally, Section 6 summarizes the paper.
2 Preliminaries
2.1 Scheme parameters and interpretation instructions
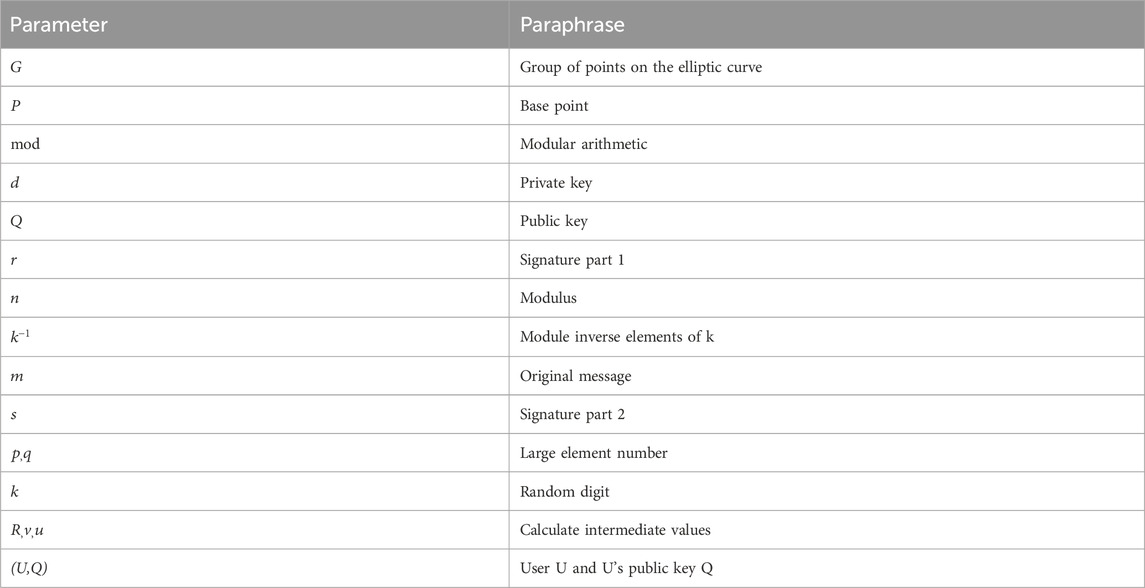
The symbols and definitions of the parameters involved in this scheme description are shown in Table 1.
2.2 Elliptic curve
Elliptic curve cryptography (ECC) is an algebraic structure defined over a finite field, which is commonly used in cryptography such as encryption and digital signatures. With it set as an elliptic curve,
where
2.3 Elliptic curve digital signature algorithm
ECDSA is a digital signature algorithm based on elliptic curves, which can be used to verify the integrity and non-repudiation of messages. The key pair of ECDSA
2.3.1 Key generation stage
Given the main parameters
Step 1: select a base point
Step 2: select a random integer
Step 3: calculate
2.3.2 Signature stage
The signer generates an ECDSA signature
Step 1: the signer randomly selects a temporary secret value
Step 2: calculate
Step 3: calculate
Step 4: the signer generates the signature
2.3.3 Verification stage
After receiving the signature
Step 1: the verifier first checks whether
Step 2: calculate
Step 3: compute
Step 4: the verifier verifies whether
In ECDSA, one modulo-inverse operation is required for each of the signature and verification phases. If the data size is
2.4 Elliptic curve discrete logarithm problem
The elliptic curve discrete logarithmic problem (ECDLP) is recognized as a difficult mathematical problem, and its intractability is based on the inability of the current computational power of computers to solve large-scale elliptic curve discrete logarithmic problems in a reasonable amount of time. The ECDLP takes the specific form of solving an elliptic curve
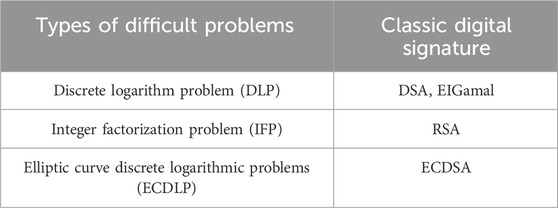
Three common types of difficult problems in current public key cryptosystem-based digital signatures are given in Table 2, among which, ECDLP is the most difficult to solve (Abdelkrim et al., 2022).
2.5 Batch validation for ECDSA
Batch verification is a technology that can verify multiple signatures at the same time, which is applicable to ECDSA. In the large-scale transaction of blockchain systems, there are many message signatures to be verified, and a lot of time and computational resources will be consumed if they are verified one by one. Batch verification technology can verify multiple message signatures at the same time, which can effectively improve the verification efficiency of signatures and also reduce the computational cost of verification. The standard methods for batch verification of ECDSA signatures generated by multiple or single signers are shown in Equations 2, 3.
The standard ECDSA signature verification equation is R = uP + vQ. When verifying the ECDSA signature
In the event that all signatures originate from a single signer, the public key utilized in the verification process is identical,
The ECDSA batch verification scheme can reduce the scalar multiplication operation in the verification phase from 2t to [2, t+1], which greatly reduces the time overhead of signature verification. To detect the equivalence of Equations 2, 3, Karati et al. proposed the plain batch verification algorithm and the symbolic batch verification algorithm.
2.6 Blockchain cryptography
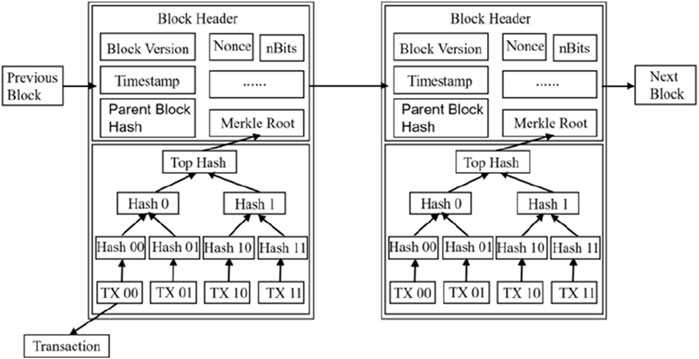
Blockchain is a distributed ledger technology that originated with the digital cryptocurrency Bitcoin. In a blockchain, each block consists of two main parts, the block header and the block body, where the block header contains a unique hash value as the block address. By recording the hash value of the previous block, the blockchain links each block into a chain structure, the specific structure of which is shown in Figure 1. Each transaction consists of a list of “inputs” and “outputs,” and the “inputs” of a transaction contain digitally signed data, ensuring that the transaction data cannot be tampered with or forged.
In the Bitcoin trading system, ECDSA is used to verify the identity of the account holder and prevent misuse of the account. To ensure the validity of transactions, each transaction must be verified with a digital signature. When a node receives a transaction, it first verifies the correctness of the digital signature to ensure that the transaction was initiated by the account holder. Only after verifying the digital signature will the node broadcast the transaction to other nodes and join the blockchain. Therefore, ECDSA is an important guarantee for the security of Bitcoin transactions, making transactions safe and efficient in a decentralized blockchain system. However, with the increasing volume of transactions, the verification efficiency of ECDSA has gradually become a challenge. To address this challenge, several optimization measures can be taken to reduce the latency of transaction broadcasting and verification while ensuring the security and reliability of transactions.
3 Proposed scheme
3.1 The KTP-ECDSA digital signature algorithm
The traditional ECDSA scheme has time-consuming mode reversal operations in both the signature phase and the verification phase, and its computation time overhead is 10 times that of the dot product operation. In order to improve the efficiency of the ECDSA scheme, an improved elliptic curve digital signature algorithm (KTP-ECDSA) is proposed, which introduces the KGLP algorithm under the premise of the TP-ECDSA (Guang-fu et al., 2024) scheme and uses Hamming weights instead of message hash to avoid the mode reversal operation. The KTP-ECDSA algorithm is mainly divided into key generation, signature, and verification stages, and the specific process is as follows.
3.1.1 Key generation stage
Given the main parameters
Step 1: select a base point
Step 2: select a random integer
Step 3: calculate
3.1.2 Signature stage
The signer generates an ECDSA signature
Step 1: the signer randomly selects a temporary secret value
Step 2: calculate
Step 3: the signer uses a random number generator to generate two numbers
Step 4: calculate
Step 5: calculate
Step 6: the signer generates the signature
3.1.3 Verification stage
Any verifier can test the validity of a sign
Step 1: the verifier first tests whether
Step 2: compute
Step 3: compute
Step 4: calculate
Step 5: the verifier checks whether
3.2 KGLP algorithms
The KGLP algorithm is a fast scalar multiplication algorithm for elliptic curve cryptography, which is widely used in scenarios such as digital signature and public key encryption. Compared with the traditional scalar multiplication algorithm, the KGLP algorithm has higher computational efficiency and better performance. The KGLP algorithm transforms the original scalar multiplication operation into multiple sub-operations based on the addition and multiplication of elliptic curve points and improves the execution speed of the whole algorithm through parallel processing. In practice, the KGLP algorithm can significantly improve the security and efficiency of elliptic curve cryptography, especially when dealing with large data and performing high-strength encryption.
In general, the most time-consuming operations in the ECDSA batch verification scheme are scalar multiplication and the modulo inverse operation. In contrast, the TP-ECDSA scheme does not require the latter, with the former, therefore, representing the most time-consuming operation in this scheme. In order to enhance the efficiency of the TP-ECDSA batch verification scheme, we employ the KGLP algorithm to accelerate the scalar multiplication operation, thereby improving the overall verification efficiency. The KGLP algorithm can calculate scalar multiplications of multiple points at the same time, which reduces the number of doubling operations and improves the computational efficiency. For example, in batch verification of t TP-ECDSA signatures, the KGLP algorithm can calculate and sum the scalar multiplications of t points simultaneously, i.e.,
Algorithm 1.KGLP algorithm.
Input: ui = (ui,l,ui,l−1, … ,ui,1), Qi∈E (FP), i∈[1,t]
Output: R = ∑uiQi
1. QQj = jtQt + jt−1Qt−1 + … + j1Q1, j=(jt, … ,j1)2, j∈[0,2t−1]; //pre-calculated results for any combination of t-point scalar summation
2. R = ∞;
3. for i = t; i ≥ 0;i--do
4. R = 2R;
5. for j = t; j ≥ 0; j--do
6. bit = uj,i ≪ j;
7. R = R + QQbit;
8. return R;
3.3 KTP-ECDSA batch verification scheme
ECDSA batch verification schemes are good at checking lots of signatures at once, but they get slower as the number of signatures in a batch gets bigger. Blockchain transactions are large, so existing schemes may not work. Our scheme is fast for all sizes of message signature verification with few modulo and scalar multiplication operations. The main time-consuming operation in the KTP-ECDSA batch verification scheme is the scalar multiplication operation. We propose a KTP-ECDSA batch verification scheme using the KGLP algorithm to reduce this operation and the time overhead of signature verification. The KTP-ECDSA batch verification scheme is given below from the perspective of the same signer and different signers.
3.3.1 KTP-ECDSA batch verification scheme for same signers
For batch verification of same signers, we can utilize the same public key and different messages and signatures. The public key of the same signer is the same; when verifying t message signatures
Step 1: the verifier first tests whether
Step 2: compute
Step 3: compute
Step 4: calculate
Step 5: calculate
Step 6: based on the equations in steps 3 and 4, the KGLP algorithm is applied to perform scalar multiplication to calculate
Step 7: the verifier computes
3.3.2 KTP-ECDSA batch verification scheme for different signers
For batch verification of different signers, there are varying public keys and message signatures to be verified. It is assumed that there are t signers whose key pairs are
Step 1: the verifier first tests whether
Step 2: tor t different signers, have
Step 3: compute
Step 4: compute
Step 5: calculate
Step 6: calculate
Step 7: based on the above equation, the KGLP algorithm is applied to calculate the scalar multiplication operation to compute
Step 8: the verifier computes
Our scheme uses the TP-EDCSA implementation, which uses the KGLP algorithm to further reduce the time overhead of the scalar multiplication operation. As the number of signatures increases, the time spent verifying them decreases. The KTP-ECDSA scheme uses the KGLP algorithm to reduce the time spent on verification. It can verify large numbers of transactions in the blockchain efficiently and reduces the time spent on signature verification.
3.4 Correctness
The signature verification phase of the TP-ECDSA scheme meets the computational correctness of individual verification processes and batch verification processes, as shown in Equations 4–6.
3.4.1 Individual verification
3.4.2 Batch verification
For batch verification of different signers, there are
Then, the following equation holds:
4 Security analysis
4.1 Security formalism analysis
This section shows how the security model works in a game between a challenger
Attacker
4.1.1 Game
Super type I and type II attackers
Theorem 1:. Under the intractability assumption based on the elliptic curve discrete logarithmic problem, the proposed scheme suffers from unforgeability under the adaptive choice of message attack against the super type I attacker
4.1.2 Proof
Under the stochastic predicate machine model, a legitimate signature can be forged assuming that in polynomial time, the attacker
4.1.3 Initialization phase
Challenger
4.1.4 Query phase
User creation query: challenger
Hash query: challenger
Secret value query: challenger
Public key query: when
Signature query: when challenger
4.1.5 Forging phase
Based on the above two equations,
Challenger
Theorem 2:. Under the intractability assumption based on the elliptic curve discrete logarithmic problem, the proposed scheme suffers from unforgeability under the adaptive choice of message attack against the super type II attacker
The proof of Theorem 2 has the same idea and method as Theorem 1, so the proof process will not be repeated in this paper.
4.2 Security analysis
1) Message integrity: Message integrity is achieved through hash functions and Hamming weights. A hash function is a function that maps the data on arbitrary length to a fixed length hash value, which is unique and irreversible. Any minor changes to the message will result in a completely different hash digest. Hamming weights can further verify the integrity of the message. When the data are tampered with, the Hamming weight gives different results. Therefore, the scheme in this paper has message integrity and can effectively prevent data tampering. In the event that a signature is identified as being fraudulent as a result of the injection of a fictitious signature, the verification process will be unsuccessful.
2) Non-repudiation: in the scheme of this paper, the sender of the message signs the message using its own private key. Since the private key is owned only by the sender, no one else can forge the sender’s signature. Therefore, once the signature of a message has been verified, it can be determined that the message was indeed sent by the sender, and the sender cannot deny that it sent the message.
3) Forward security: assume that an illegal user can get the public key of U. Due to
4) Resistant weak randomness: after taking the first random number
5) Anti man-in-the-middle attack: if the two communicating parties do not know each other’s identity, the establishment of a critical session is vulnerable to man-in-the-middle attack. This solution realizes two-way authentication through digital signature technology so that illegal users cannot impersonate either party and can effectively prevent man-in-the-middle attacks.
5 Efficiency analysis
We compare ECDSA with KTP-ECDSA for verification to check how well they work. The computer-based experimental runtime environment is Windows 11, 64-bit CPU. Intel Core i5 CPU @ 1.60 GHz; 8 GB RAM.
We use C to implement the schemes in this paper, calling the parameters of the security curve in the OpenSSL source code (OpenSSL is an open-source cryptographic library that provides a large number of cryptographic algorithms and key protocols) and programmed in Visual Studio 2021. The OpenSSL Development Kit program is used to verify ECDSA and KTP-ECDSA for large prime number domains.
The current mainstream batch algorithms include Schnorr and SM2. However, Schnorr has not been widely adopted by all mainstream blockchains, and the international adoption rate of SM2 is lower than that of ECDSA and Schnorr. Consequently, in the experimental efficiency analysis, we primarily compared with the ECDSA algorithm.
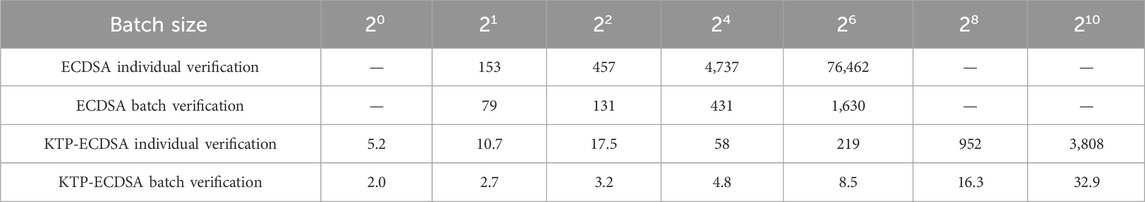
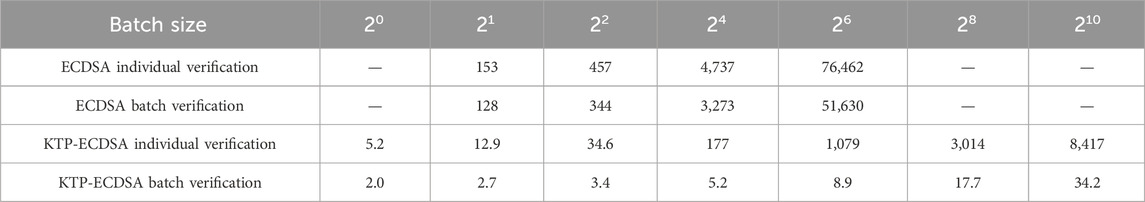
The ECDSA is employed in conjunction with KTP-ECDSA, as detailed in this paper, to facilitate the individual and batch verification of a single signatory and multiple signatories. Each scheme is executed 100 times, and the resulting data are averaged. The time required for the key generation phase differs between the same-signer and different-signer signature verification schemes. This is due to the fact that the same-signer scheme necessitates the generation of a single set of key pairs but the different-signer scheme requires the generation of multiple sets of key pairs. Furthermore, the time required for each stage of the signature verification process is almost identical. Table 3 presents the runtime overhead of independent and bulk verification by the same signers for varying message signature sizes. Table 4 presents the runtime overhead of independent and bulk verification by different signers. The use of a hyphen in tables III and IV indicates the absence of pertinent data. As can be seen from table III, when verifying 16 message signatures, ECDSA consumes 4,737 ms for individual verification and 431 ms for batch verification, while KTP-EDCSA consumes 58 ms for individual verification and only 4.8 ms for batch verification. It is evident from tables III and IV that the batch verification can markedly reduce the time overhead of verification in comparison to individual verification. In particular, the KTP-ECDSA batch verification scheme proposed in this paper requires even less time for the verification of signatures.
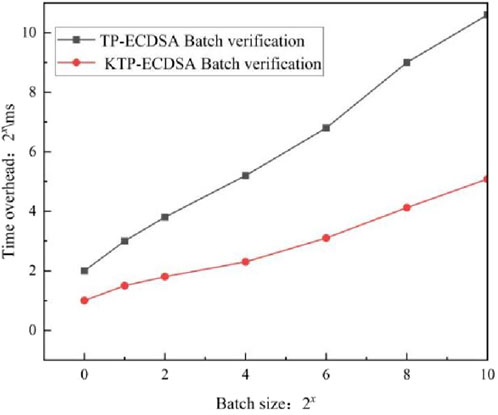
In Figure 2, we show whether the TP-ECDSA batch verification scheme uses the KGLP algorithm to accelerate the time overhead of the verification algorithm, i.e., comparing the time overhead of TP-ECDSA and KTP-ECDSA batch verification, which can be shorter and more efficient in the latter. The horizontal coordinate
6 Conclusion
The present study proposes a batch verification scheme with the objective of enhancing the efficiency of large-scale message signature verification in blockchain. The proposed scheme builds upon the TP-ECDSA scheme with a modeless inverse operation, employing the KGLP algorithm in a dual-parameter elliptic curve digital signature for batch verification. In comparison to independent verification, the TP-ECDSA batch verification scheme reduces the number of scalar multiplications and utilizes the KGLP algorithm to accelerate the time-consuming scalar multiplication operation, thereby significantly improving the verification speed. A security analysis indicates that the proposed scheme ensures data security, possesses non-forgeability, and can resist weak randomness attacks on ECDSA. Experimental analysis demonstrates that in comparison to existing schemes, the proposed scheme has a significant advantage in terms of verification time costs and can achieve the final verification result with fewer computational operations. It is our belief that this scheme will prove to be a valuable addition to blockchain systems in the future.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material; further inquiries can be directed to the corresponding author.
Author contributions
GW: writing–original draft. JZ: writing–review and editing. XF: writing–review and editing.
Funding
The author(s) declare that no financial support was received for the research, authorship, and/or publication of this article.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abdelkrim, I., Ahmed, E., and Fouzia, O. (2022). ECDSA-based certificateless conditional privacy-preserving authentication scheme in Vehicular ad hoc Network. Veh. Commun. 37, 100504. doi:10.1016/j.vehcom.2022.100504
Bao, F., Lee, C. C., and Hwang, M. S. (2006). Cryptanalysis and improvement on batch verifying multiple RSA digital signatures. Appl. Math. Comput. 172 (2), 1195–1200. doi:10.1016/j.amc.2005.03.016
Binbin, T., Chen, Y., Cui, H., and Wang, X. (2024). Fast two-party signature for upgrading ECDSA to two-party scenario easily. Theor. Comput. Sci. 986, 114325. doi:10.1016/j.tcs.2023.114325
Cao, X., and Wei, S. M. (2018). Improved elliptic curve digital signature algorithm. J. Huaibei Normal Univ. Nat. Sci. Ed. 34 (2), 1–3.
Fang, W., Chen, W., Zhang, W., Pei, J., Gao, W., Wang, G., et al. (2020). Digital signature scheme for information non-repudiation in blockchain: a state of the art review. EURASIP J. Wirel. Commun. Netw. 10, 1366–1385. doi:10.1186/s13638-020-01665-w
Guang-fu, W., Xiao-yan, F., and Jian-dong, Z. (2024). An efficient and lightweight two-parameter ECDSA batch verification scheme. J. Jiamusi Univ. Nat. Sci. Ed. 42 (01), 1–5.
Jiarui, Y., Cui, J., Tu, H., Yu, C., and Zhou, M. (2023). A SM2 based efficient and lightweight batch verification approach for IC cards. J. Inf. Secur. Appl. 73, 103409. doi:10.1016/j.jisa.2022.103409
Karati, S., Das, A., Roychowdhury, D., Bellur, B., Bhattacharya, D., and Iyer, A. (2014). New algorithms for batch verification of standard ECDSA signatures. J. Cryptogr. Eng. 4 (4), 237–258. doi:10.1007/s13389-014-0082-x
Khizar, H., Garg, S., Amin, M. B., Kang, B., and Khan, A. (2022). A context-aware information-based clone node attack detection scheme in Internet of Things. J. Netw. Comput. Appl. 197, 103271. doi:10.1016/j.jnca.2021.103271
Kittur, A. S., and Roshan Pais, A. (2017). Batch verification of digital signatures: approaches and challenges. J. Inf. Secur. Appl. 37, 15–27. doi:10.1016/j.jisa.2017.09.005
Kittur, A. S., and Pais, A. R. (2017). Batch verification of digital signatures: approaches and challenges. J. Inf. Secur. Appl. 37, 15–27. doi:10.1016/j.jisa.2017.09.005
Lim, C. H., and Lee, P. J. (1994). Security of interactive DSA batch verification. Electron. Lett. 30 (19), 1592–1593. doi:10.1049/el:19941112
Lin, H.Yi (2023). Secure data transfer based on a multi-level blockchain for Internet of vehicles. Sensors 23 (5), 2664. doi:10.3390/s23052664
Liu, S. G., Chen, W. Q., and Liu, J. L. (2021). An efficient double parameter elliptic curve digital signature algorithm for blockchain. IEEE Access 9, 77058–77066. doi:10.1109/access.2021.3082704
Mahajan, H. B., and Junnarkar, A. A. (2023). Smart healthcare system using integrated and lightweight ECC with private blockchain for multimedia medical data processing. Multimedia tools Appl. 82 (28), 44335–44358. doi:10.1007/s11042-023-15204-4
Marcos, A., León, D. L., Cerón, S., Pareja, A., Pacheco, E., Leal, A., et al. (2023). Quantum-resistance in blockchain networks. Sci. Rep. 13 (1), 5664. doi:10.1038/s41598-023-32701-6
Na, J., Kim, Y. H., Park, N., and Seo, B. (2022). Comparative analysis of Schnorr digital signature and ECDSA for efficiency using private ethereum network. IEIE Trans. Smart Process. and Comput. 11 (3), 231–239. doi:10.5573/ieiespc.2022.11.3.231
Puthiyidam, J. J., Shelbi, J., and Bharat, B. (2023). Enhanced authentication security for IoT client nodes through T-ECDSA integrated into MQTT broker. J. Supercomput. 80 (7), 8898–8932. doi:10.1007/s11227-023-05789-w
Rahman Taleb, A., and Vergnaud, D. (2021). Speeding-up verification of digital signatures. J. Comput. Syst. Sci. 116, 22–39. doi:10.1016/j.jcss.2020.08.005
Wang, Z., Yu, H., Zhang, Z., Piao, J., and Liu, J. (2020). ECDSA weak randomness in Bitcoin. Future Gener. Comput. Syst. 102, 507–513. doi:10.1016/j.future.2019.08.034
Xiao, S., Wang, X. A., and Pan, F. (2020). Elliptic curve digital signature algorithm for modeless inverse operations. Comput. Eng. Appl. 56 (11), 118–123.
Yehuda, L. (2021). Fast secure two-party ECDSA signing. J. Cryptol. 34 (4), 44. doi:10.1007/s00145-021-09409-9
Yu, J., Cui, J., Tu, H., Yu, C., and Zhou, M. (2023). A SM2 based efficient and lightweight batch verification approach for IC cards. J. Inf. Secur. Appl. 73 (C), 103409. doi:10.1016/j.jisa.2022.103409
Zhang, P., Li, Y., Liu, M., Shang, Y., and Fu, Z. (2022). An ECC-based digital signature scheme for privacy protection in wireless communication network. Wirel. Commun. Mob. Comput. 2022, 1–9. doi:10.1155/2022/1977798
Keywords: ECDSA, batch verification, blockchain, KGLP algorithm, scalar multiplication
Citation: Wu G, Zhou J and Fu X (2025) Improved blockchain-based ECDSA batch verification scheme. Front. Blockchain 8:1495984. doi: 10.3389/fbloc.2025.1495984
Received: 13 September 2024; Accepted: 13 January 2025;
Published: 13 February 2025.
Edited by:
Alex Zarifis, University of Southampton, United KingdomReviewed by:
Hariprasath Manoharan, Panimalar Institute of Technology, IndiaMohd Sameen Chishti, Norwegian University of Science and Technology, Norway
Copyright © 2025 Wu, Zhou and Fu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Jiandong Zhou, MTczNjM0Njc1NUBxcS5jb20=
 Guangfu Wu
Guangfu Wu Jiandong Zhou
Jiandong Zhou Xiaoyan Fu
Xiaoyan Fu