- 1Research Laboratory SIME, ENSIT, University of Tunis, Tunis, Tunisia
- 2J-AP2S Laboratory, South University, Toulon, France
- 3NOCCS Research Laboratory, ENISo, ISITCOM, University of Sousse, Sousse, Tunisia
This research introduces a novel MOMENTS-SVD vector for fingerprint identification, combining invariant moments and SVD (Singular Value Decomposition), enhanced by a modified PCA (Principal Component Analysis). Our method extracts unique fingerprint features using SVD and invariant moments, followed by classification with Euclidean distance and neural networks. The MOMENTS-SVD vector reduces computational complexity by outperforming current models. Using the Equal Error Rate (EER) and ROC curve, a comparative study across databases (CASIA V5, FVC 2002, 2004, 2006) assesses our method against ResNet, VGG19, Neuro Fuzzy, DCT Features, and Invariant Moments, proving enhanced accuracy and robustness.
1 Introduction
Fingerprint is a key component of biometric identification, several systems highlight singularity features such as core and delta point detection. Balti introduced a fingerprint verification system utilizing a backpropagation neural network (Balti et al., 2013), although singularity-based methods faced challenges, particularly their sensitivity to noise due to the local nature of singularities. Fitz explored Fourier transform features for classification, but the global features extracted by the wedge-ring detector lacked discriminatory information (Fitz and Green, 1996). In addition, Singular Value Decomposition (SVD) was examined by Balti et al. (2012), Balti and Sayadi (2014), Balti et al. (2014) as a potential tool for fingerprint characterization and identification. Their work focuses on the efficient extraction of significant features from fingerprint images through dimensionality reduction, as well as the identification of underlying fingerprint patterns through SVD. The goal of this approach is to obtain the most important data for precise fingerprint identification (Balti and Sayadi, 2014). In 2012, they investigated the potential advantages of integrating invariant moment features, which are immune to image changes, with SVD. This combined method may increase fingerprint characterization accuracy.
In recent years, Convolutional Neural Networks (CNN) have been widely used, even in the field of fingerprint recognition. For instance, when I searched the literature, I found several significant studies in this area. These are some prominent instances, Militello et al. (2021) study to evaluate the efficacy of pre-trained convolutional neural networks (CNN) for fingerprint classification. Their study demonstrates how important classification is to reduce the quantity of comparisons required for large fingerprint databases. They tested the AlexNet, GoogLeNet, and ResNet architectures. They are noteworthy for being the first to thoroughly compare these popular CNN architectures for fingerprint classification.
By integrating multi-augmentation and inversion techniques into convolutional neural networks, Garg et al. (2024) have presented a novel approach to fingerprint recognition. They get around the issue of having little training data by creating new fingerprint images for each feature map using a variety of augmentation techniques and inversion. Using multiple CNN, the suggested method by Garg et al. (2024) extracts features from the augmented data. Significant improvements in accuracy were observed in their experiments with pre-trained models, such as VGG19. On the FVC2000_DB4 dataset, the VGG19 model outperformed other models with an accuracy of 97% thanks to multi-augmentation.
On the other hand, I discovered that researchers (Srivastava et al., 2022) have proposed a multimodal biometric framework for human identity validation using iris and finger-knuckle print (FKP) recognition. By combining multiple biometric traits (FKP and iris in this case), their method achieves higher accuracy. The framework extracts features from FKP images using SIFT and SURF, and extracts features from iris images using Log Gabor wavelets with PCA. Remarkably, they achieve 98.68% accuracy on the CASIA databases using a neuro-fuzzy classifier for match score level fusion.
To address these challenges, our work adopts Singular Value Decomposition (SVD) (Golshan and Mohammadi, 2013) and invariant moments (Hu, 1962) for fingerprint image verification. SVD, a well-established technique in digital image processing, efficiently reduces data volume, preserving essential features in a compact representation. Invariant moments, an effective image processing method, provide a thorough overview of texture with seven moments that are unaffected by translation, rotation, and adjustments to scale.
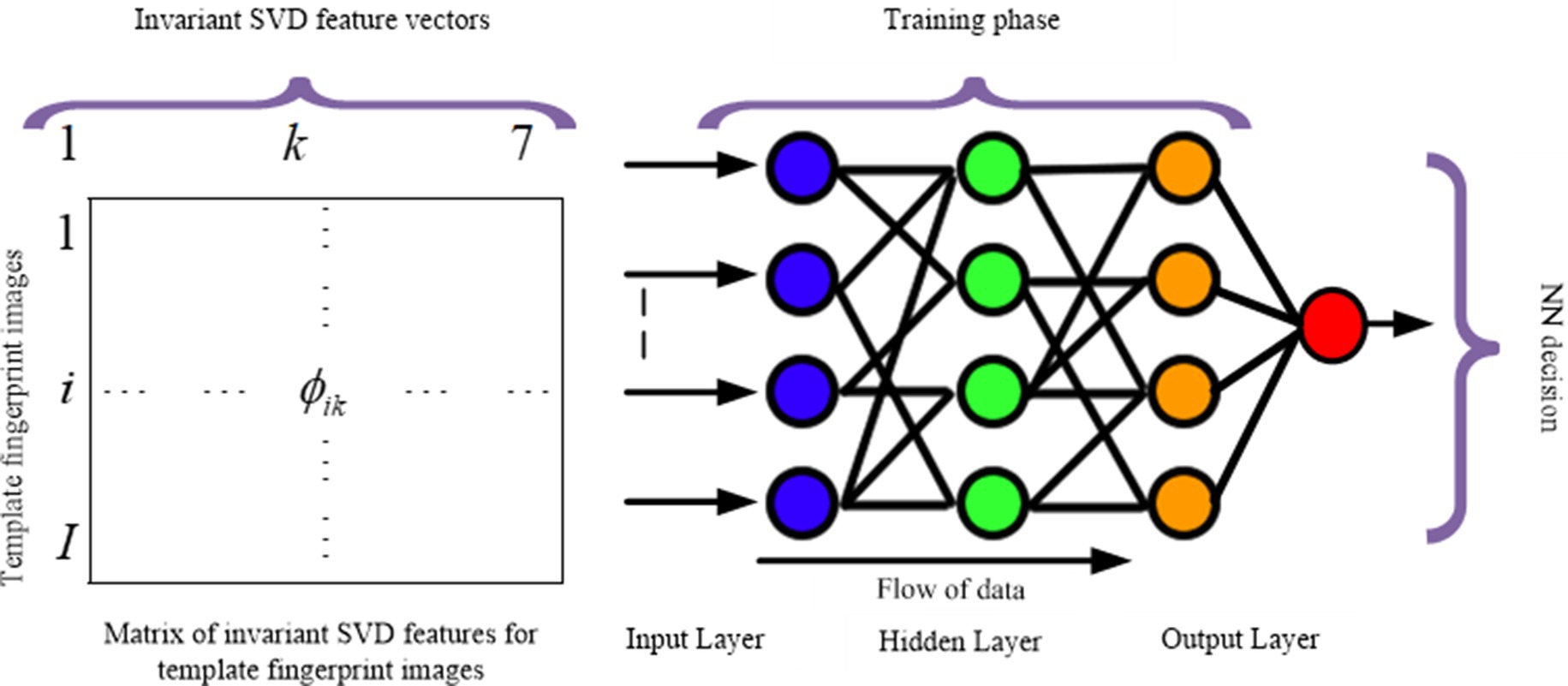
The proposed fully automatic matching approach relies on the fusion of seven invariant moments and SVD features for robust fingerprint identification. The process involves a neural network, as illustrated in Figure 1, outlining the fingerprint pattern identification and classification procedure. Verification between test and template fingerprint feature vectors is assessed using the absolute distance, the characterization degree and the Frobenuis norm as a similarity measure. This approach aims to overcome the limitations of traditional minutiae-based approaches by conducting extensive research, testing, and validating the effectiveness of modified Principal Component Analysis (PCA) with SVD and invariant moments.
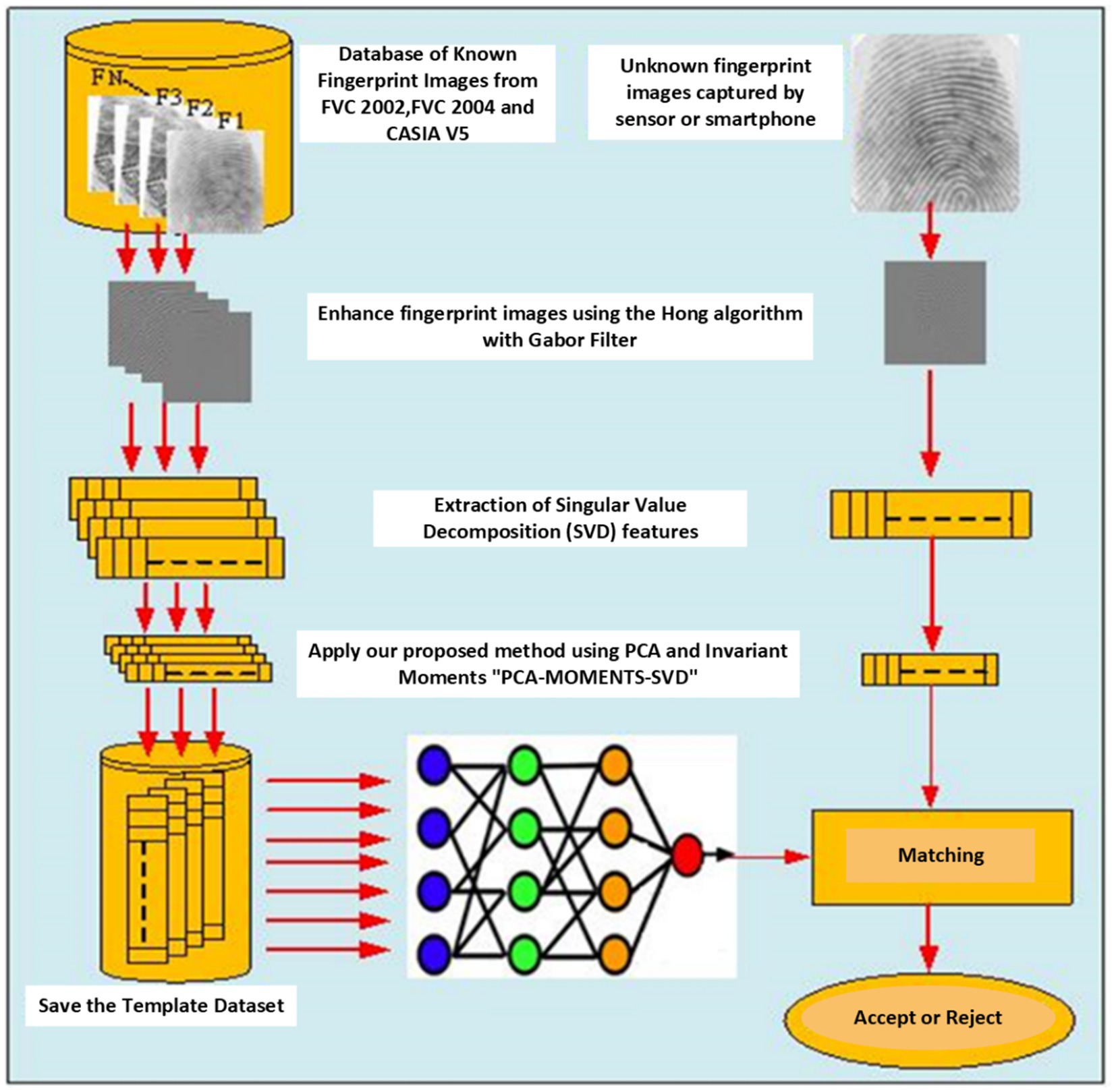
Figure 1. General process diagram for the proposed fingerprint recognition system (PCA-MOMENTS-SVD).
2 Theoretical foundations of SVD and invariant moments
SVD is a powerful approach to matrix analysis that has applications beyond square matrices (Loperfido, 2015). This method breaks down a matrix into three fundamental building blocks: U and V are two unitary matrices, and S is a diagonal matrix. These resulting matrices capture the most important information from the original data. SVD ability to extract this inherent structure has made it a cornerstone in various signal and image processing tasks. The SVD decomposition is represented by Equation (1).
Invariant moments are unique image features that remain constant even when the image is scaled, rotated, or moved (Tiwari and Srivastava, 2024). This makes them extremely useful in image processing tasks. In our approach, we use moment analysis, see Equation (2), to extract these valuable features from the SVD feature vectors. This section delves more deeply into the concept of invariant moments.
A moment of zero order corresponds to the object surface area and is expressed in the following form Equation (3):
The first-order moment is defined by the two expressions below (Equations 4 and 5):
They determine the centroid of the corresponding surface (Equations 6 and 7):
The central moments of order (p and q) can be declared as Equation (8):
The reduced and normalized central moments are defined as follows Equation (9):
with for
Several researchers have developed methods for extracting a specific set of seven features (Equations 10, 11), known as invariant moments, from an image (Hu, 1962; Yager and Amin, 2004; Liu et al., 2012; Monge-Alvarez et al., 2019; Hao et al., 2021). These features have a unique power: They remain constant even when the image is scaled, rotated, or moved around. This makes them extremely useful for tasks such as identifying patterns in images, which is exactly what our approach seeks to accomplish.
3 Modified PCA with SVD and invariant moments
This section introduces a ground breaking feature extraction approach that is specifically designed to address the complexities of fingerprint verification. This method employs a powerful set of techniques, including SVD for data analysis, invariant moments for capturing key features that are resistant to variations such as rotation and scale, and neural networks for classification. A comprehensive flowchart (Figure 1) details the entire process.
In this case, known fingerprints are treated as feature vectors, with invariant moments providing valuable information. This combined approach, including our proposed modified PCA with SVD and invariant moments, leverages the strengths of each technique to achieve accurate fingerprint verification.
3.1 Input: enhanced fingerprint images
Hong et al. (1998) used the Gabor filter to improve fingerprint images. We use the same algorithm as Hong et al. to improve the input fingerprint images. First, we create the matrix, which contains all of the identified fingerprints. Indeed, i represents the reference within the fingerprint database, while m and n represent the dimensions of matrix . Each image, assumed to have M pixels arranged in size m × n, is converted into a column vector of size M × 1. This vector contains the intensity values of all M pixels in a single column. Furthermore, set S containing N such fingerprint images can be represented as a matrix with dimensions M × N. Each column in this matrix corresponds to a single fingerprint vector ().
The mean features (Equation 18) of set S (Equation 17) are computed by taking the average of all vectors.
We arrange the data around zero by subtracting the average value from each element in the original features. This creates a new matrix T (Equation 19) with the same dimensions (M × N).
SVD of T is calculated, which results in singular values and left and right singular vectors, and , respectively. Matrix T (Equations 21 and 22) is represented as the sum of rank r components.
Calculating a scalar projection of allows us to determine how well each fingerprint matches the base images. This projection is represented by a set of values u assigned to each fingerprint. We build the general matrix (Equations 23 and 24). This matrix is created by multiplying the transpose of the base fingerprint image vectors with .
3.2 Feature extraction
For each row, seven moment features are extracted and stored in the database. These attributes will be used as inputs for a neural network classifier.
4 Results and discussion
4.1 Fingerprint databases
Abdul Cader et al. (2023) carried out a thorough examination of fingerprint recognition systems in their work, emphasizing current developments and difficulties. They draw attention to how sensor technology and image capture affect the accuracy of the system. Their analysis examines how sensor modalities and underlying physical principles can introduce distortions during image capture. It covers contact and contactless (2D and 3D) fingerprint systems. In order to close this gap, Abdul Cader et al. (2023) offers a cutting-edge analysis that covers sensors, image acquisition, and interoperability issues with different fingerprint systems.
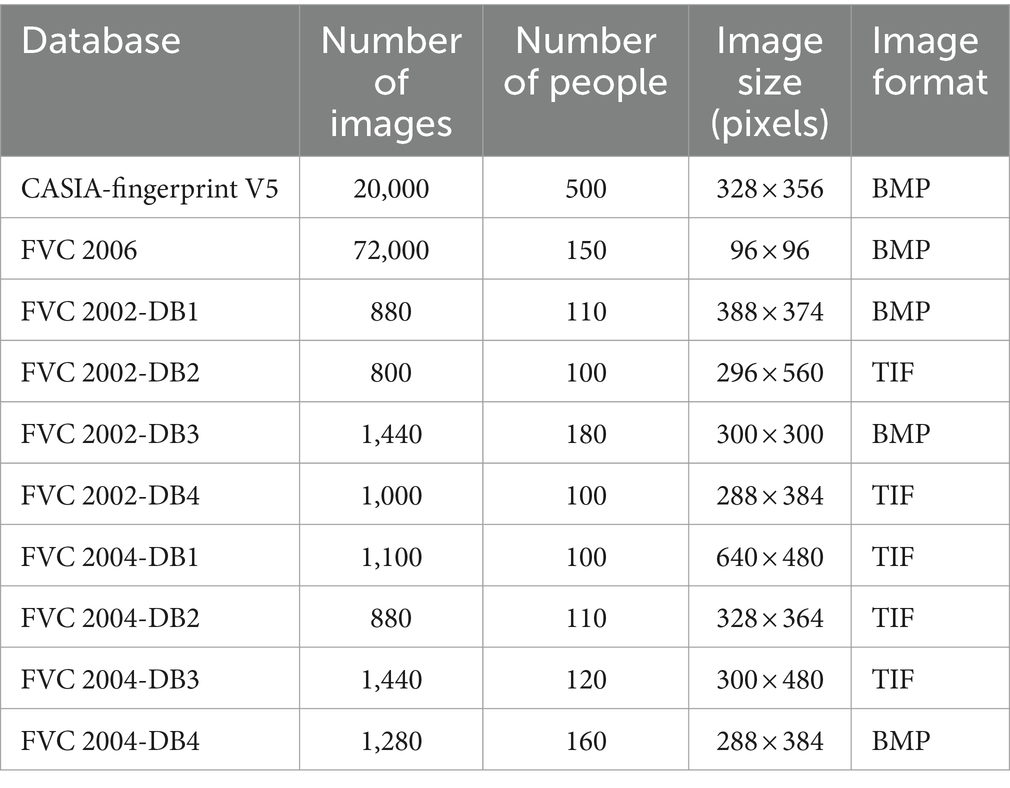
The FVC2002, FVC2004, FVC2006, and CASIA V5 fingerprint databases (Maio et al., 2000, 2002; Abdul Cader et al., 2023) provide a diverse set of fingerprint images for analysis, which we use in our experiment. Ten classes are available: four for FVC 2002 and 2004, one for FVC 2006, and one for CASIA V5. The following table provide a detailed description of the databases that were used in this work for the experimental study (Table 1).
The FVC2004 and FVC2006 were built with temperature differential sensors, which use pyroelectric materials to convert temperature changes into voltage (Abdul Cader et al., 2023). In many fingerprint data acquisition systems, such as the FVC2004, the Atmel FingerChip is a standard component. The development of biometric technologies and the Internet of Biometric Things (IoBT) depends on these sensors. In addition to using a variety of sensors, the CASIA Fingerprint databases also make use of optical, ultrasonic, and capacitive sensors (Abdul Cader et al., 2023). Thermal sensors make up the majority of these sensors.
4.2 Discrimination performance using characterization degree and Frobenius norm
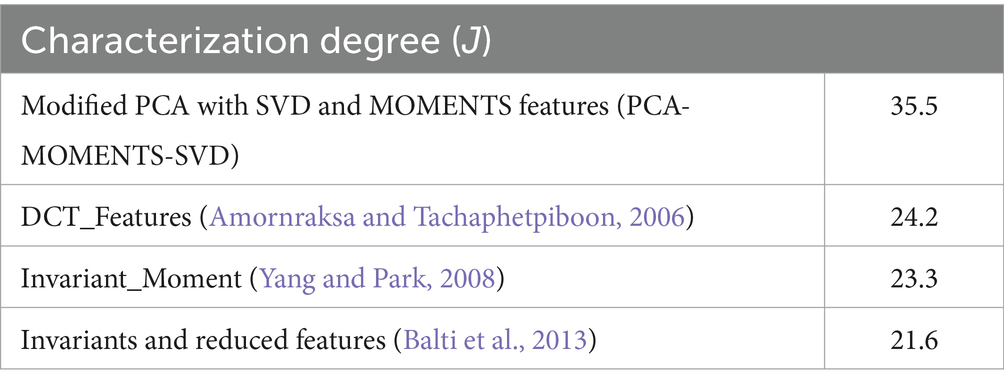
We choose 100 fingerprint images from each sub-database for analysis. Our goal is to determine whether enhanced fingerprint images improve the matching process over their original versions. To accomplish this, we propose a characterization degree, J, which will be computed for both sets of images (original and enhanced). This metric (J) is based on the ratio of variance between different fingerprints (inter-variance) to variance within a single fingerprint (intra-variance) (Amornraksa and Tachaphetpiboon, 2006; Balti et al., 2012, 2013).
A higher J value indicates a clearer distinction between different fingerprints, which can lead to better matching performance. For this evaluation, we use all 100 randomly selected fingerprint images from each sub-database, where is the estimated feature vector for each fingerprint image (1 ≤ k ≤ 100 and 1 ≤ n ≤ 25).
The average of the fingerprint feature vector class is shown in Equation (25):
The mean of all features’ vector classes is also noted in Equation (26):
The matrix represents the mean of intra-class (within-class) dispersion matrices (Equation 27):
This is the maximum likelihood estimate for the class covariance matrix. Additionally, the mean of between-class (inter-class) dispersion matrices describes the scattering of class sample means. The matrix computes this (Equation 28):
Finally, the characterization degree (J) is calculated as (Equation 29):
This method extracts a feature vector from each fingerprint image in the selected sets (original and enhanced). These feature vectors include both the mean and the variance, as well as higher-order moments up to the sixth order. The characterization degree (J), as previously described, is based on the ratio of inter-variance to intra-variance calculated from these features (Amornraksa and Tachaphetpiboon, 2006; Balti et al., 2012, 2013). A higher J value indicates a greater distinction between different fingerprints, which is desirable for a reliable fingerprint classification process. Table 2 compares the effectiveness of these features in achieving a high level of characterization.
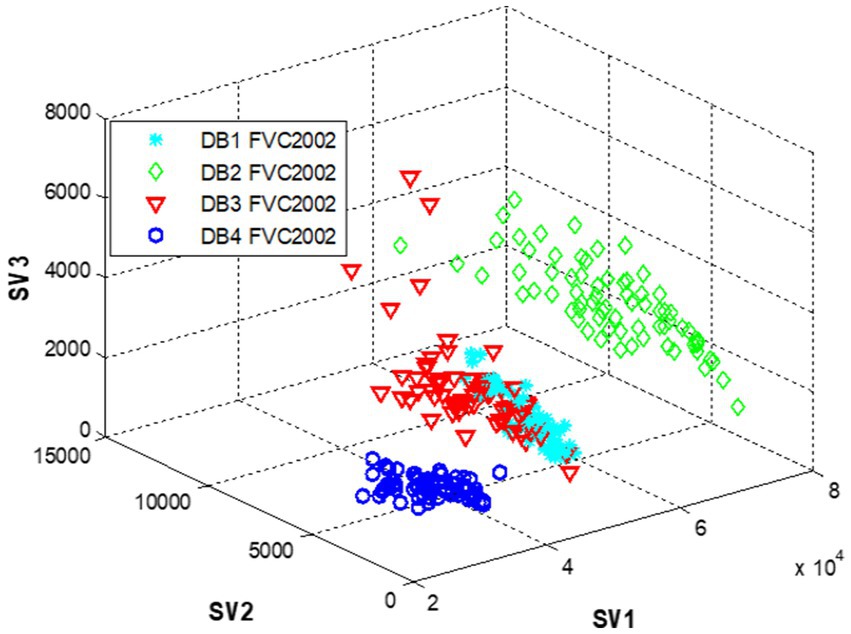
Figure 2 shows the discriminative 3D of singular values obtained using the modified PCA with SVD and MOMENTS features approach.
To determine the potential improvement in fingerprint characterization achieved by our MOMENTS-SVD feature approach, we propose to evaluate the extracted SVD feature vectors using the Frobenius norm (Equation 33) for each fingerprint image. The Frobenius norm is a popular metric in image processing that provides a consistent measure of errors. In our context, a lower Frobenius norm for the SVD features may indicate a better representation of the fingerprint than the original data, potentially leading to enhanced characterization. Applying (Equations 30−32) to our experimental data.
The singular value can be used to calculate the Frobenius norm, where represents the singular values of .
The suggested MOMENTS-SVD feature vectors are being evaluated. We generate the E projection vector, which is defined in equation (20) and apply it to the fingerprint images.
To assess the effectiveness of SVD features for fingerprint characterization, we examine 25 grayscale fingerprints from the FVC2002 (Figure 3). SVD features are especially useful because they remain consistent even when fingerprints are rotated.

Figure 3. Examples from fingerprint databases commonly used in fingerprint recognition research: (A) FVC-2002 DB1, (B) FVC-2002 DB2, (C) FVC-2002 DB3, (D) FVC-2002 DB4, (E) FVC-2004 DB1, (F) FVC-2004 DB2, (G) CASIA-fingerprint V5, (H) Critical case images from CASIA-fingerprint V5.
We conduct two controlled experiments to demonstrate the efficacy of our proposed SVD feature vectors in fingerprint matching.
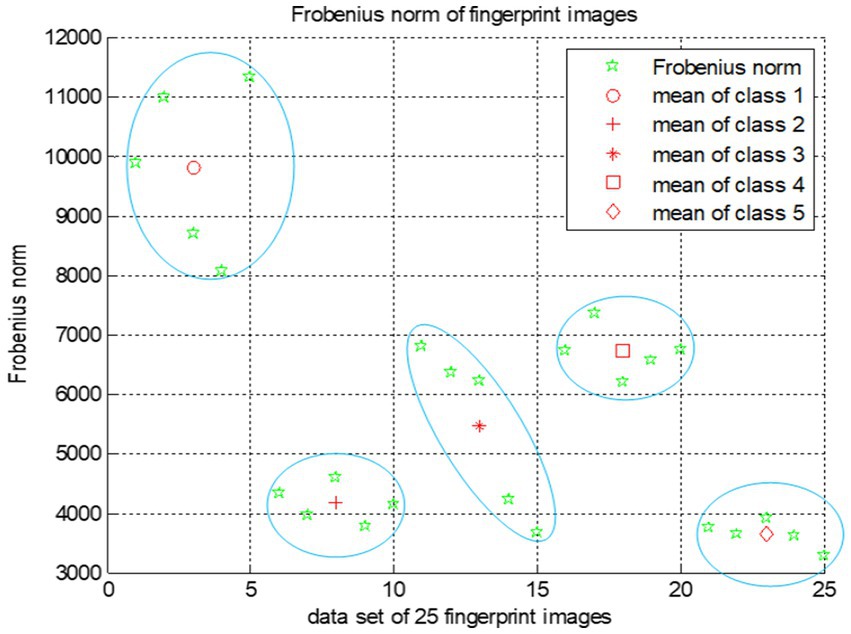
Experiment 1: Fingerprint clustering (Figure <bold>4</bold> ):
We choose a random set of fingerprints dataset (Figure 3). These fingerprints are then clustered using the proposed SVD feature extraction technique combined with the Frobenius norm. As shown in Figure 4, this approach effectively partitions fingerprints into distinct clusters (classes), demonstrating the SVD features ability to group similar fingerprints together.
Experiment 2 Fingerprint matching accuracy:
Our evaluation of the FVC fingerprint databases reveals a significant advantage of the proposed SVD-based representation for fingerprint indexing over the existing methods. The results highlight an important trade-off:
Accuracy: The suggested method with SVD feature matching provides superior verification accuracy.
Speed: Methods based on the Frobenius norm provide faster matching times, but at the potential cost of accuracy.
Furthermore, the proposed method has higher verification accuracy than other well-established techniques. These experiments show that SVD features outperform other techniques for matching fingerprints. They provide better verification system performance and greater resistance to variations in fingerprint image quality.
4.3 Performance evaluation
To assess the effectiveness of our fingerprint verification system, we use the standard protocol from the FVC2002, FVC2004, FVC2006, and CASIA V5 benchmark (Maio et al., 2000, 2002; Xie et al., 2020; Militello et al., 2021; Srivastava et al., 2022; Garg et al., 2024). This protocol is based on several key performance indicators:
False Acceptance Rate (FAR): This metric calculates the percentage of imposter fingerprints (those that do not match the claimed identity) which are mistakenly accepted as genuine. Having a lower FAR is desirable (Equation 34).
False Reject Rate (FRR): This metric measures the percentage of genuine fingerprints that the system incorrectly rejects. A lower FRR is also preferred (Equation 35).
Equal Error Rate (EER): This is the point at which FAR and FRR are equivalent. It serves as a common benchmark for comparing the performance of various fingerprint verification systems. A lower EER indicates improved overall performance.
Genuine Acceptance Rate (GAR): This metric measures the percentage of genuine fingerprints correctly accepted by the system. Having a higher GAR is desirable (Equation 36).
NAG (Number of Accepted Genuine Fingers): This metric measures the number of genuine fingerprints attempts correctly identified as belonging to authorized users. TNG (Total Number of Genuine Fingers): This metric measures the total number of attempts made with genuine fingerprints (authorized users). NAI (Number of Accepted Imposter Fingers): This metric measures the number of imposter fingerprint attempts incorrectly identified as belonging to authorized users (security failure).
TNI (Total Number of Imposter Fingers): This metric measures the total number of attempts made with imposter fingerprints (unauthorized users). NRG (Number of Rejected Genuine Fingers): This metric measures the number of genuine fingerprint attempts incorrectly rejected (causing user inconvenience).
We calculate EER, FRR and FAR for all databases using matched genuine and impostor fingerprint pairs. For genuine matches, each test fingerprint is compared to the corresponding template from the same person. Imposter matches, on the other hand, involve comparing each test fingerprint to templates created by different people. The following section describes our proposed method’s identification performance.
We compare the performance of our suggested SVD feature-based approach to five well-known fingerprint verification techniques in order to assess its efficacy. This research uses five different approaches. The method proposed by Invariant Moment (Yang and Park, 2008) combines BPNN and invariant moment features. Discrete Cosine Transform (DCT) features were utilized in the Second Method, DCT Features, developed by Amornraksa and Tachaphetpiboon (2006), to match fingerprints. The Third Method, Neuro Fuzzy method, was proposed by Srivastava et al. (2022), the Fourth Method, ResNet method, was proposed by Militello et al. (2021), and the Fifth Method, VGG19, was proposed by Garg et al. (2024).
The five methods were put into practice. In the framework of these well-known techniques, our experiment compares two matching strategies: absolute distance and neural network (Tables 3, 4).
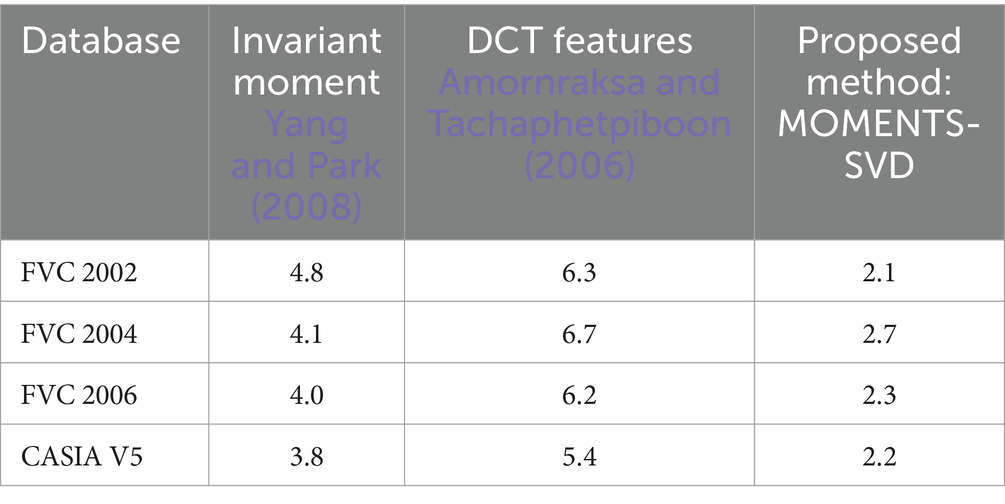
Table 3. Performance comparison of proposed method with the absolute distance (D_abs) for different databases and methods (EER %).
4.4 Role of absolute distance in fingerprint recognition
Absolute distance, also known as Euclidean distance, is used in fingerprint recognition systems to quantify the similarity between feature vectors extracted from captured fingerprints and the corresponding feature vectors of template fingerprints stored in a database.
Vectors refers to the invariant feature extracted from the input fingerprint, while is the feature vector obtained from the database for the template fingerprint. Added to that, (Equation 37) represents the difference vector computed from their respective feature vectors.
The absolute distance (Equation 38) between the two invariant feature vectors is defined as:
Table 3 compares the Equal Error Rate (EER) attained by various techniques using a variety of fingerprint verification databases, with an emphasis on the Absolute Distance (D_abs) metric. The proposed method, MOMENTS-SVD, is compared with Invariant Moment (Yang and Park, 2008), DCT Features (Amornraksa and Tachaphetpiboon, 2006), and the databases evaluated are FVC 2002, FVC 2004, FVC 2006, and CASIA V5. With values of 2.1, 2.7, 2.3, and 2.2% for FVC 2002, FVC 2004, FVC 2006, and CASIA V5, respectively. The results show that the suggested method consistently achieves the lowest EER across for all databases.
Compared to the Invariant Moment and DCT Features methods, which have higher EER values ranging from 3.8 to 6.7%, this performance is noticeably better.
5 Neural networks for fingerprint classification
This study expands on previous research in fingerprint verification with supervised neural networks (Yang and Park, 2008; Balti et al., 2013; Garg et al., 2024). However, our primary focus is on fingerprint identification, which entails categorizing fingerprints rather than determining whether they match a specific template. The neural network architecture has three layers (Figure 5): input, hidden, and output. For nonlinearity, we use sigmoid activation functions in the hidden layer, while for classification we use linear activation functions in the output layer (Figure 5).
After 893 epochs of experimentation, we find the optimal configuration with 60 hidden neurons and a mean squared error target of 10−20.
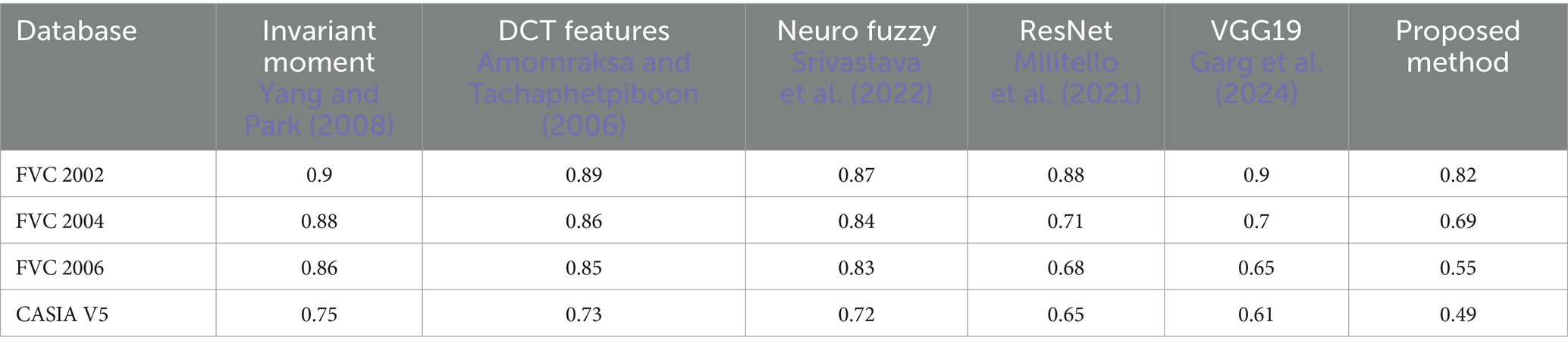
A comparative study of the Equal Error Rate (EER) attained by various feature extraction and classification techniques across multiple fingerprint verification databases is shown in Table 4. The databases that were examined are CASIA V5, FVC 2002, FVC 2004, and FVC 2006. The approaches that are compared are the following: ResNet (Militello et al., 2021), VGG19 (Garg et al., 2024), Neuro Fuzzy (Srivastava et al., 2022), DCT Features (Amornraksa and Tachaphetpiboon, 2006), and Invariant Moment (Yang and Park, 2008). The findings show that, for all databases, the suggested method consistently produces the lowest EER, with values for FVC 2002, FVC 2004, FVC 2006, and CASIA V5 of 0.82, 0.69, 0.55, and 0.49%, respectively.
This performance outperforms the other approaches, indicating the superior accuracy and robustness of the suggested method in fingerprint verification. The EER of the other methods, which highlight the consistent enhancement offered by the suggested approach, range from 0.87 to 0.9% for FVC 2002, 0.7–0.88% for FVC 2004, 0.65–0.86% for FVC 2006, and 0.61–0.75% for CASIA V5.
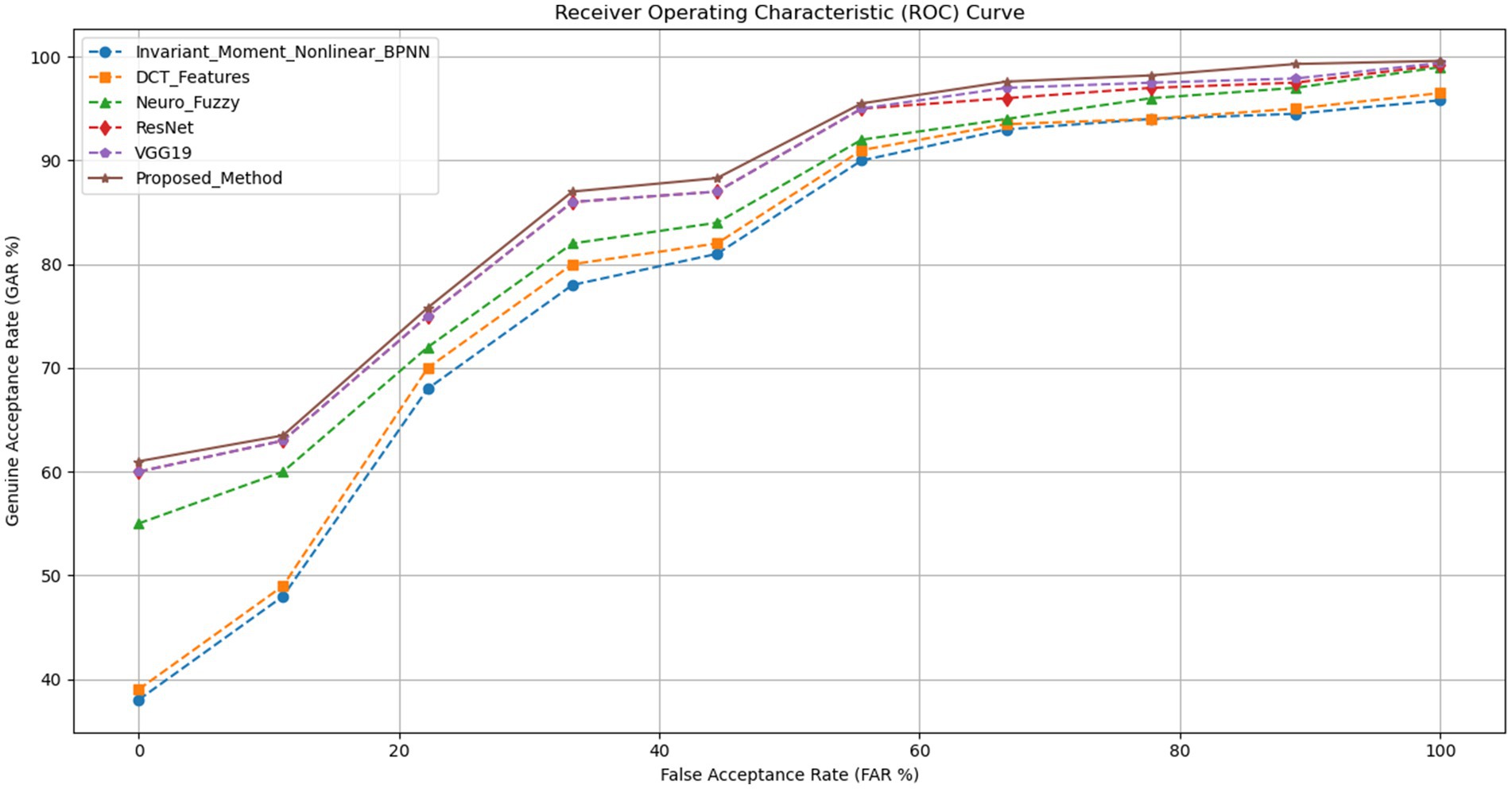
We also use the Receiver Operating Characteristic (ROC) curve (Figure 6), which compares the GAR to the FAR%, to assess these methods more effectively. Through graphical demonstration of maintaining a higher GAR for a lower FAR%, this analysis validates the superiority of the proposed method in biometric authentication technology. In order to improve security and user confidence in authentication procedures, these results demonstrate the usefulness of ROC analysis and GAR percentages in evaluating the precision and dependability of biometric recognition systems. A thorough assessment of the efficacy of various biometric recognition methods is made possible by the True Acceptance Rate (GAR) percentages for varying False Acceptance Rates (FAR). With GAR percentages ranging from 61 to 99.6%, the suggested method performs better than every other method that was tested. This performance improvement demonstrates the extent to which the proposed method can accurately identify real users at different security levels.
6 Conclusion
In conclusion, this paper presents a new fingerprint verification system that improves identification accuracy by utilizing SVD features and invariant moments. The matching engine of the system is a neural network that extracts and compares these features from captured fingerprints (tests) and database-stored templates. This method performs better in terms of flexibility, robustness against sensor noise, and achieving high matching accuracy when compared to conventional metrics like absolute distance and Frobenius norm. Neural network integration holds great promise for improving biometric authentication systems and providing a dependable solution for safe and effective identification procedures in a variety of applications. In the future, studies could focus on improving neural network architectures and diversifying datasets to improve the system’s functionality and applicability in real scenarios.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author contributions
AB: Conceptualization, Data curation, Formal analysis, Investigation, Methodology, Software, Supervision, Validation, Visualization, Writing – original draft, Writing – review & editing. AH: Conceptualization, Formal analysis, Methodology, Software, Validation, Writing – original draft, Writing – review & editing. SA: Formal analysis, Methodology, Supervision, Validation, Writing – review & editing. MB: Formal analysis, Methodology, Software, Supervision, Validation, Writing – review & editing. MS: Project administration, Supervision, Writing – review & editing.
Funding
The author(s) declare that no financial support was received for the research, authorship, and/or publication of this article.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abdul Cader, M., Banks, J., and Chandran, V. (2023). Fingerprint systems: sensors, image acquisition, interoperability and challenges. Sensors 23:6591.
Amornraksa, T., and Tachaphetpiboon, S. (2006). Fingerprint recognition using DCT features. Electron. Lett. 42, 522–523. doi: 10.1049/el:20064330
Balti, A., and Sayadi, M. (2014). “A new fingerprint identification approach based on SVD features” 2014 1st international conference on advanced technologies for signal and image processing (ATSIP), Sousse, Tunisia, pp. 301–304.
Balti, A., Sayadi, M., and Fnaiech, F. (2012). “Invariant and reduced features for Fingerprint Characterization,” in IECON 2012 - 38th Annual Conference on IEEE Industrial Electronics Society, Montreal, QC, Canada. 1530–1534.
Balti, A., Sayadi, M., and Fnaiech, F. (2013). Fingerprint verification based on back propagation neural network. J. Control Eng. Appl. Informat. 15, 53–60.
Balti, A., Sayadi, M., and Fnaiech, F. (2014). “Fingerprint characterization using SVD features” International image processing, applications and systems conference, Sfax, Tunisia, pp. 1–6.
Fitz, A. P., and Green, R. J. (1996). Fingerprint classification using a hexagonal fast Fourier transform. Pattern Recognition, 29, 1587–1597.
Garg, R., Singh, G., Singh, A., and Singh, M. P. (2024). Fingerprint recognition using convolution neural network with inversion and augmented techniques. Syst. Soft Comput. 6:200106. doi: 10.1016/j.sasc.2024.200106
Golshan, F., and Mohammadi, K. (2013). A hybrid intelligent SVD-based perceptual shaping of a digital image watermark in DCT and DWT domain. Imag. Sci. J. 61, 35–46. doi: 10.1179/1743131X11Y.0000000049
Hao, Y., Qiao, S., Zhang, L., Xu, T., Bai, Y., Hu, H., et al. (2021). Breast cancer histopathological images recognition based on low dimensional three-channel features. Front. Oncol. 11:657560. doi: 10.3389/fonc.2021.657560
Hong, L., Wan, Y., and Jain, A. (1998). Fingerprint image enhancement: algorithm and performance evaluation. IEEE Trans. Pattern Anal. Mach. Intell. 20, 777–789. doi: 10.1109/34.709565
Hu, M. K. (1962). Visual pattern recognition by moment invariants. IRE Trans. Inf. Theory 8, 179–187. doi: 10.1109/TIT.1962.1057692
Liu, Y., Yin, Y., and Zhang, S. (2012). Hand gesture recognition based on HU moments in interaction of virtual reality. In 2012 4th international conference on intelligent human-machine systems and cybernetics (1).
Loperfido, N. (2015). Singular value decomposition of the third multivariate moment. Linear Algebra Appl. 473, 202–216. doi: 10.1016/j.laa.2014.05.043
Maio, D., Maltoni, D., Cappelli, R., Wayman, J. L., and Jain, A. K. (2000). FVC2000: fingerprint verification competition. IEEE Trans. Pattern Anal. Mach. Intell. 24, 402–412. doi: 10.1109/34.990140
Maio, D., Maltoni, D., Cappelli, R., Wayman, J. L., and Jain, A. K. (2002). FVC2002: fingerprint verification competition. In Proc. Int. Conf. Pattern Recognition (ICPR) (pp. 744–747).
Militello, C., Rundo, L., Vitabile, S., and Conti, V. (2021). Fingerprint classification based on deep learning approaches: experimental findings and comparisons. Symmetry 13:750. doi: 10.3390/sym13050750
Monge-Alvarez, J., Hoyos-Barcelo, C., Lesso, P., and Casaseca-de-la-Higuera, P. (2019). Robust detection of audio-cough events using local hu moments. IEEE J. Biomed. Health Inform. 23, 184–196. doi: 10.1109/JBHI.2018.2800741
Srivastava, R., Bhardwaj, V. P., Othman, M. T. B., Pushkarna, M., Anushree,, Mangla, A., et al. (2022). Match-level fusion of finger-knuckle print and Iris for human identity validation using neuro-fuzzy classifier. Sensors 22:3620. doi: 10.3390/s22103620
Tiwari, A., and Srivastava, V. K. (2024). Image watermarking techniques based on Schur decomposition and various image invariant moments: a review. Multimed. Tools Appl. 83, 16447–16483. doi: 10.1007/s11042-023-16109-y
Xie, L., Xu, L., Kong, R., Chang, S., and Xu, X. (2020). Improvement of prediction performance with conjoint molecular fingerprint in deep learning. Front. Pharmacol. 11:606668. doi: 10.3389/fphar.2020.606668
Yager, N., and Amin, A. (2004). Fingerprint classification: a review. Pattern. Anal. Applic. 7, 77–93. doi: 10.1007/s10044-004-0204-7
Keywords: fingerprint classification, fingerprint features, invariant moments, PCA, recognition, SVD features
Citation: Balti A, Hamdi A, Abid S, Ben Khelifa MM and Sayadi M (2024) Enhanced fingerprint classification through modified PCA with SVD and invariant moments. Front. Artif. Intell. 7:1433494. doi: 10.3389/frai.2024.1433494
Edited by:
Jinwei Xing, Google, United StatesReviewed by:
Habib Hamam, Université de Moncton, CanadaMourad Moussa, National Institute of Applied Science and Technology, Tunisia
Copyright © 2024 Balti, Hamdi, Abid, Ben Khelifa and Sayadi. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Ala Balti, YWxhYS5iYWx0aUBlbmljYXIudWNhci50bg==
 Ala Balti
Ala Balti Abdelaziz Hamdi
Abdelaziz Hamdi Sabeur Abid1
Sabeur Abid1