- Department of Mathematics, Dilla University, Dilla, Ethiopia
This study constructs a robust higher-order fitted operator finite difference method for a two-parameter singularly perturbed boundary value problem. The derivatives in the governing ordinary differential equation are substituted by second-order central finite difference approximations, after which the fitting parameter is introduced and determined. The resulting system of linear equations may then be solved using the Thomas method. The stability, consistency, and convergence of the current method have been thoroughly validated. To enhance accuracy and achieve a higher-order numerical solution, a post-processing technique was employed to upgrade the method from second-order to fourth-order convergence. Finally, three test examples were used to confirm the method's appropriateness. The numerical results demonstrate that the proposed technique is stable, consistent, and produces a higher-order numerical solution than the existing ones in the literature.
1 Introduction
Singularly perturbed differential equations involve the highest-order derivative term being multiplied by a small perturbation parameter, ε. In the context of singularly perturbed problems, differential equations with two small parameters affecting the diffusion and convection terms are intriguing areas of research. The main purpose of this study is to obtain a robust higher-order numerical method to solve a two-parameter singularly perturbed boundary value problem. Find Υ such that
subject to the boundary conditions
where ε(0 < ε ≪ 1) and μ(0 < μ ≪ 1) are the small parameters that make the differential equation singularly perturbed. Let us assume the functions a(θ), b(θ) and f(θ) are sufficiently smooth and bounded to ensure the existence of a unique solution. Assume that there exist constants α, β and ζ independent of ε and μ such that for any θ = [0, 1] the conditions,
hold for some constant α, β and ζ. Assume . When μ = 1, Equation 1 is reduced to the singularly perturbed convection-diffusion boundary value problem. When μ = 0, Equation 1 reduces to a well-known singularly perturbed reaction-diffusion boundary value problem. The mathematical model for the kind of Equation 1 often arises in chemical reactor theory [1], transport phenomena in chemistry and biology [2], and lubrication theory [3]. The nature of the two-parameter problem was asymptotically examined by O'Malley [4], where the ratio of μ to ε has significant role in the solution. For this problem, two boundary layers occur at θ = 0 and θ = 1. Because of the presence of these layers, some standard numerical methods in Lodhi et al. [5], Kambampati et al. [6], Pandit and Kumar [7], Khandelwal and Khan [8] are applied to a uniform mesh, which provides an oscillatory numerical solution. Consequently, considerable attention has been devoted to using non-uniform meshes to solve two-parameter singularly perturbed boundary value problems, as discussed in works by O'Riordan and Pickett [9], Roos and Uzelac [10], Kadalbajoo and Yadaw [11], Kadalbajoo and Jha [12], Brdar and Zarin [13], Luo et al. [14], Brdar and Zarin [15, 16], Padmaja et al. [17], Andisso and Duressa [18], Linß and Roos [19], Cheng [20], Zhang and Lv [21], Valarmathi and Ramanujam [22], Patidar [23] to solve two-parameter singularly perturbed boundary value problems. The majority of the previously developed methods to solve the problem at hand are less accurate and of lower order. Inspired by this, the goal of this study is to offer a high order and more accurate fitted operator method with the help of post-processing technique to solve the considered problem. Because of the presence of boundary layer in the solution of Equation 1, devising a higher-order convergent numerical method is a big challenge. In this study, we apply the well-known post-processing technique of Richardson extrapolation method to obtain fourth order uniformly convergent numerical solution of Equation 1. The present approach yields a more accurate solution in terms of maximum absolute errors than previous approaches found in the literature.
Some robust numerical methods for one-parameter and two-parameter singularly perturbed problems in studies by Hassen and Duressa [24], Mohye et al. [25], Tesfaye et al. [26], Cheru et al. [27], Daba et al. [28], Gupta et al. [29], singularly perturbed turning point problem in Gupta et al. [30], time-fractional singularly perturbed convection-diffusion problem [31], singularly perturbed problems with spatio-time delays the study by Ejere et al. [32] and singularly perturbed problems Burger-Huxley problem in the study by Daba and Duressa [33] and Derzie et al. [34]. Some methods are employed studies by Li et al. [35], El Ahmadi et al. [36], Nachaoui [37], Mardanov et al. [38] to solve different types of differential equations.
The remaining part of the article is arranged as follows: In Section 2, we have provided a brief description of the present method for the numerical solution of Equations 1, 2. The convergence analysis of the method is presented in Section 3. Section 4 presents the numerical results, and comparisons are made with other existing methods. Finally, the conclusion is provided at the end of the article in Section 5.
2 The continuous problem
In this section, we provide a priori bounds for the solution and its corresponding derivatives. The governing problem in Equations 1, 2 exhibits twin boundary layers with different layer widths depending on the relation between the values of ε and μ. If αμ2 ≤ δε, then the reduced problem corresponding to Equations 1, 2 is given by
Thus, the boundary layers are expected near θ = 0 and θ = 1, with a width of if Υ0(0) ≠ γ0 and Υ0(1) ≠ γ1. If αμ2 ≥ δε, then the reduced problem corresponding to Equations 1, 2 is given by
Thus, the boundary layer of width O(ε/μ) is expected in the right neighborhood of θ = 0 if Υμ(0) ≠ γ0 and the boundary layer of width O(μ) is expected in the left neighborhood of θ = 1 if Υμ(1) ≠ γ1. The assumptions given for Equations 1, 2 ensure that the differential operator Πε, μ satisfies the following maximum principle.
Lemma 1. Let ϖ(θ) be a smooth function such that ϖ(0) ≥ 0 and ϖ(1) ≥ 0. If Πε,μ ϖ(θ) ≥ 0, for θ ∈ Ω, then ϖ(θ) ≥ 0, for .
Proof. Assume θ* be such that and ϖ(θ*) < 0. Then, it is obvious that θ* ∉ {0, 1}. Hence, ϖ′(θ*) = 0 and ϖ′′(θ*) ≥ 0. Now, , which is contradiction. Hence, we conclude that ϖ(θ) ≥ 0 for all θ ∈ [0, 1]. □
The following lemma proves the stability estimate to obtain a unique solution.
Lemma 2. On , the solution Υ(θ) to the problem in Equations 1, 2 satisfy the bound
Proof. Defining two functions ζ±(θ) such that
It is straightforward that ζ±(0) ≥ 0 and ζ±(1) ≥ 0. Now, for θ ∈ Ω,
Therefore, the desired result follows by applying Lemma (1). □
The solution to the reduced problem μa(θ)Υ′(θ)+b(θ)Υ(θ) = f(θ), in general, does not satisfy both the boundary conditions; therefore, there exist boundary layers at both the boundaries, θ = 0 and θ = 1 [10]. To describe these boundary layers, the characteristic equation for the homogeneous part of Equation 1 with constant coefficients that are the minimum values of the corresponding variable coefficients is considered as
The characteristic equation in Equation 3 has two real solutions
The solution Ψ0(θ) < 0 describes the boundary layer at θ = 0, whereas Ψ1(θ) > 0 describes the boundary layer at θ = 1. To bound the solution and its derivatives, we define
The two real solutions Ψ0(θ) < 0 and Ψ1(θ) < 0 describing the boundary layers, respectively, at θ = 0 and θ = 1 are based on the two cases below.
Case 1. If as ε → 0, then
The governing Equation 1 has two boundary layers that behave like the reaction-diffusion case (μ≈0) with each of width at θ = 1 and θ = 0. The complementary function of Equation 1 may be expressed as
where A1 and B1 are real constant numbers.
Case 2. If as μ → 0, then
In this case, the governing Equation 1 has two boundary layers near θ = 0 and θ = 1 with different layer widths O(ε/μ) and O(μ), respectively. Now, the complementary function of Equation 1 can be given as
where A2 and B2 are real constant numbers. Note that most numerical methods give an accurate numerical solution for case 1, since μ≈0 behaves like a reaction-diffusion problem. For case 2, it is challenging to produce an accurate numerical solution. Therefore, in this study, we focus on case 2.
Theorem 1. For any 0 < p < 1, we have up to a certain order q that depends on the smoothness of the data. If , then the solution u(θ) satisfies
Proof. The details of the proof is well established in studies by Roos and Uzelac [10]. □
3 The discrete problem
Let N be a positive integer and [0,1] be the closed domain, where N is the subinterval such that 0 = θ0 < θ1 < ⋯ < θN = 1 and i = 0, 1, ⋯ , N. Using the notation Υi as a numerical approximation to the analytical solution Υ(θi) and second-order central finite difference approximations for the second- and first derivatives, we have the discrete problem as
with the discrete boundary conditions
where . In order to regulate the solution behavior of the singular perturbation parameter ε, we have introduced the fitting factor η on the homogeneous part of Equation 4.
The discrete problem in Equation 6 can be written as the three-term recurrence relation of the form
with the discrete boundary conditions in Equation 5 and where the coefficients are given by
The developed method is considered as an exponentially fitted operator finite difference method to solve the problem in Equations 1, 2. The coefficients Li, Mi, and Ri are given to satisfy the conditions |Li| > 0, |Mi| > 0, |Ri| > 0 and |Mi| ≥ |Li|+|Ri|. These conditions guarantee that the linear system is diagonally dominant and can be solved by a tri-diagonal solver, which is the Thomas algorithm.
3.1 Determination of fitting factor
It is possible to rewrite the equation in the following form to determine the fitting factor.
Multiplying Equation 9 by ℓ and taking the limit on both sides as h → 0 yields
where . To determine the fitting factor in Equation 10, the theory of singular perturbations have been applied. Based on O'Malley's [39] theory of singular perturbations, the asymptotic solution of Equation 10 for the left boundary layer is as follows
where Υ0(θ) represents the solution of the reduced problem
Taking the Taylor series expansion for a(θ) restricted to the first term about the point θ = 0 and also evaluating the limit as ℓ → 0 for θi = iℓ, we get
where Similarly,
Substituting Equations 12 and 13 into Equation 10 and simplifying gives the following fitting factor:
For the right boundary layer, consider the asymptotic solution of the form
Using Taylor's series expansion for a(θ) restricting to the first term about θ = 1 and also taking the limit as ℓ → 0, we obtain
Similarly, we have
Substituting Equations 16 and 17 into Equation 10 and simplifying gives the following fitting factor:
Combining Equations 14 and 18 gives variable fitting factor as follows
4 Convergence analysis
In this section, we prove the stability and convergence analysis of the discrete problem. First, we want to prove the discrete comparison principle for the discrete scheme in Equation 12.
Theorem 2. Assume be discrete operator and Θi be comparison function such that . If Υ0 ≤ Θ0 and ΥN ≤ ΘN, then Υi ≤ Θi ∀i = 0, ⋯ , N.
Proof. The matrix associated with operator is of size (N − 1) × (N − 1) and satisfies the property of M-matrix. That is, the inverse matrix exists, and it is nonnegative. See the detailed proof in Kellogg and Tsan [40]. This guarantees the existence and uniqueness of the discrete solution. □
Lemma 3. Let Υi be the discrete solution. Then, we have the following bound
Proof. Let and define the two barrier functions by At the boundary points, we have , and On the discretized domain 1 ≤ i ≤ N − 1, we have
where bi ≥ β > 0 and from Theorem (2), we get , for □
We use the truncation error given in Equation 5 to show the convergence analysis of the present method as follows:
Theorem 3. Let Υ(θi) be the continuous solution and Υi be the discrete solution. Then, the error bound satisfies
where C is a constant independent of ε, μ and the mesh lengths h.
The above theorem shows that the present method is second-order convergent, independent of the parameters ε and μ. Next, we develop the post-processing technique to improve the accuracy of the present method and order of convergence.
4.1 Post-processing technique
To improve the accuracy of the numerical solution ΥN by the post-processing technique, we solve the discrete scheme in Equation 7 on the fine mesh with 2N mesh intervals. From Equation 20, we have
where Υ(θi) and Υi are continuous and numerical solutions, respectively, and C is a constant independent of the perturbation parameters ε, μ and mesh size ℓ and . Assume ΩN ⊂ Ω2N, where ΩN is the mesh obtained from the mesh interval ℓ, and Ω2N is the mesh obtained by bisecting the mesh interval ℓ. Denoting the numerical solution obtained with the mesh points Ω2N by . Consider the mesh and Equation 21 works for any ℓ ≠ 0 which implies
where RN is the remainder term of the truncation error with O(ℓ2). Now, we construct another mesh which is obtained by bisecting the mesh ΩN. Let us define the step size as . Then, for . For the mesh , we have
where R2N is the remainder term of the truncation error with O(ℓ4). Multiplying Equation 23 by four and subtracting the result obtained from Equation 22 yields
Dropping the error term in Equation 24 and rearranging, we have
from which the following extrapolation formula is developed
which is also the numerical solution for Υ(θi). The error bound for after post-processing technique can now be stated in the theorem below.
Theorem 4. Let Υ(θi) be the solution to the continuous problem and be the post-processed solution. Then, the new error bound takes the form
where C is a constant independent of ε, μ and the mesh length h.
As a result, the post-processing technique enhances the second-order parameter-uniformly convergent method to achieve fourth-order parameter-uniform convergence. Consequently, the current approach is fourth-order convergent and more efficient. We now implement the theoretical findings from the preceding sections through computerized calculations.
5 Numerical computations and discussions
In this section, we undertake computerized calculations to validate the efficacy of the proposed method against the theoretical results described in previous sections.
Example 1. Consider variable coefficient two parameter singularly perturbed problem
Example 2. Consider variable coefficient two parameter singularly perturbed problem
Since the exact solutions for each example are not available, the double mesh principle was employed to compute the maximum absolute errors for each (ε, μ):
where is the numerical solution with N mesh points and is the numerical solution at the finer mesh with 2N mesh points.
Example 3. Consider constant coefficient two parameter singularly perturbed problem
for which the analytical solution is given by
where
The maximum absolute errors for each (ε, μ) may be determined using the following formula, as the exact solution for Example (3) is known.
where is the numerical solution with N mesh points and is the analytical solution. The (ε, μ)-maximum errors for all the Examples are calculated using the following formula
Furthermore, we compute the numerical rate of convergence before and after post-processing technique with the following formulas, respectively:
The (ε, μ)−maximum rates of convergence before and after post-processing techniques were calculated using the following formulas, respectively
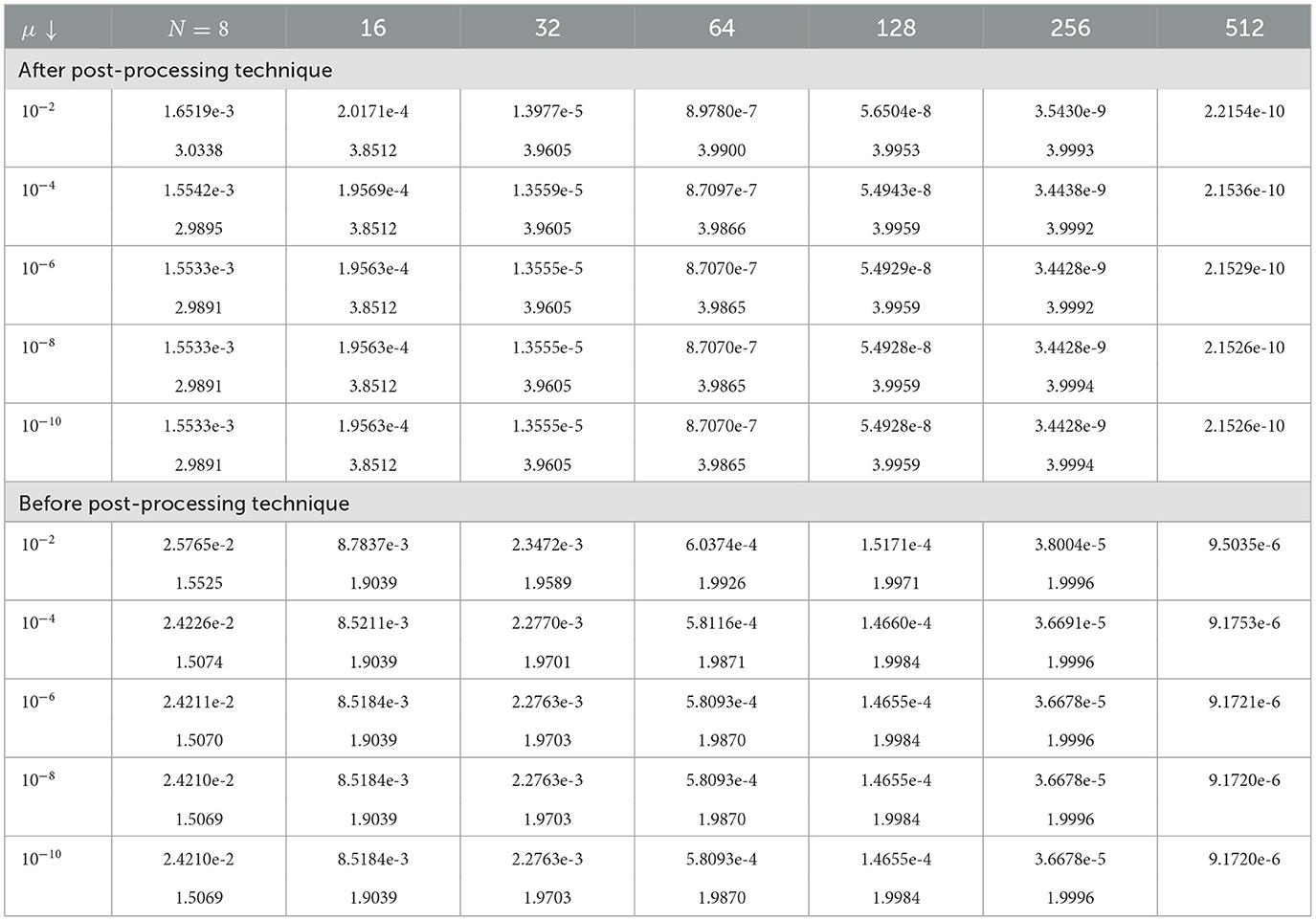
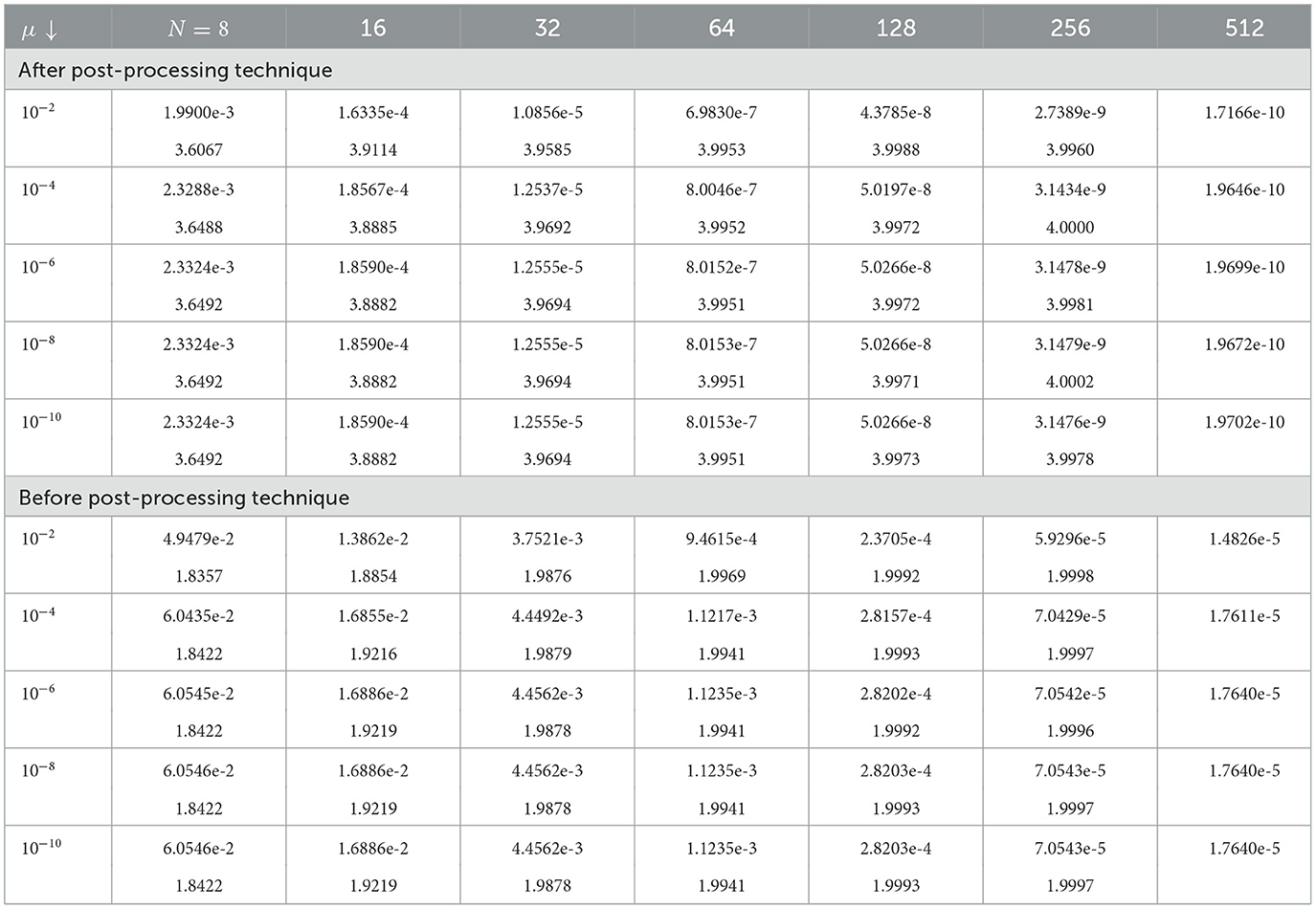
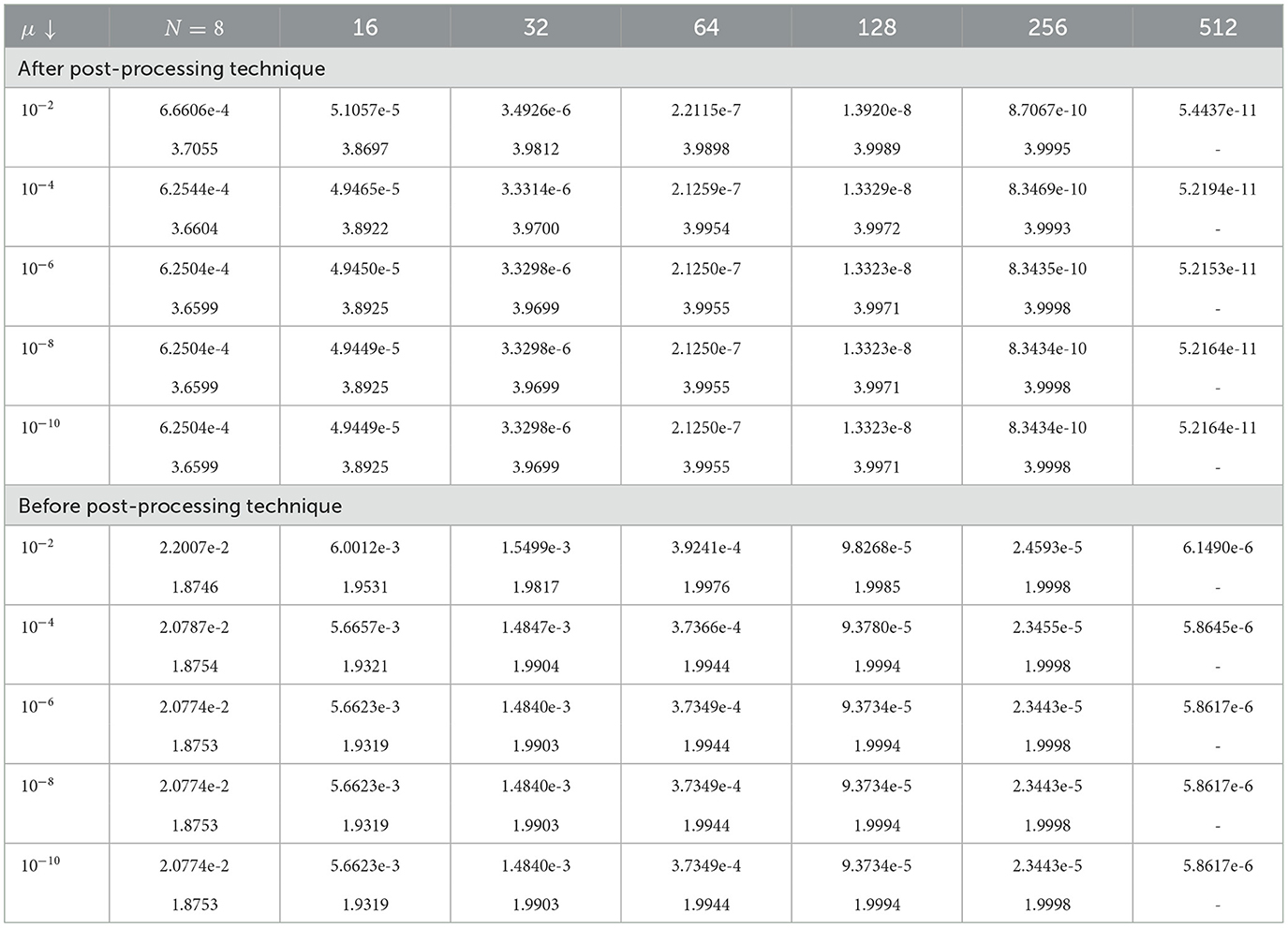
Tables 1–3 show the calculated maximum errors and the parameter-uniform errors eN for Examples (1)–(3), respectively. These findings demonstrate that the current approach provides parameter-uniform convergence for both the before and after post-processing technique. Figures 1–3 display the plots of the numerical simulations for Examples (1)–(3). Figures 1–3 illustrate the plots of the numerical solution profile for Examples (1)–(3) for fixed μ and varying ε. From these figures, we observe that for fixed μ as ε → 0, strong layers are formed. Figures 4–6, respectively, show the log–log scale plots of the maximum errors for Examples (1), (2), and (3). The numerical findings show that the current higher-order fitted operator finite difference technique provides a numerical solution with more accuracy. The application of post-processing approach improves the accuracy of the numerical solution and speeds up the rate of convergence, as demonstrated by the numerical findings in all of the Tables.
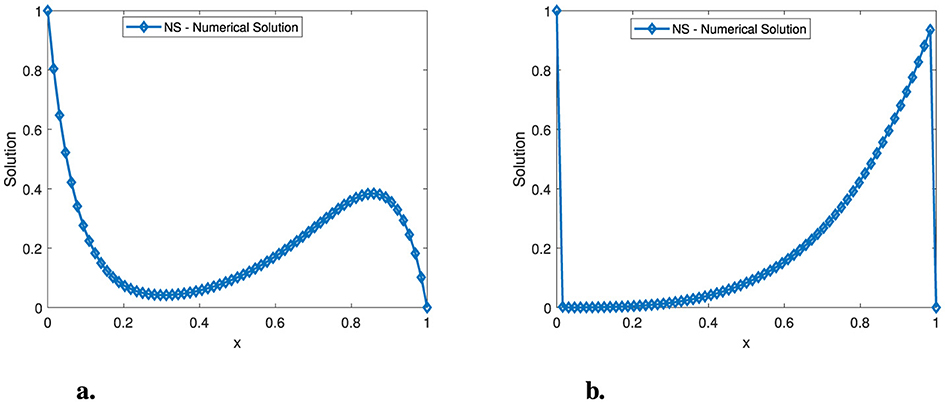
Figure 1. A plot of the numerical solution for Example (1) at N = 64 and μ = 10−6. (A) ε = 10−2. (B) ε = 10−6.
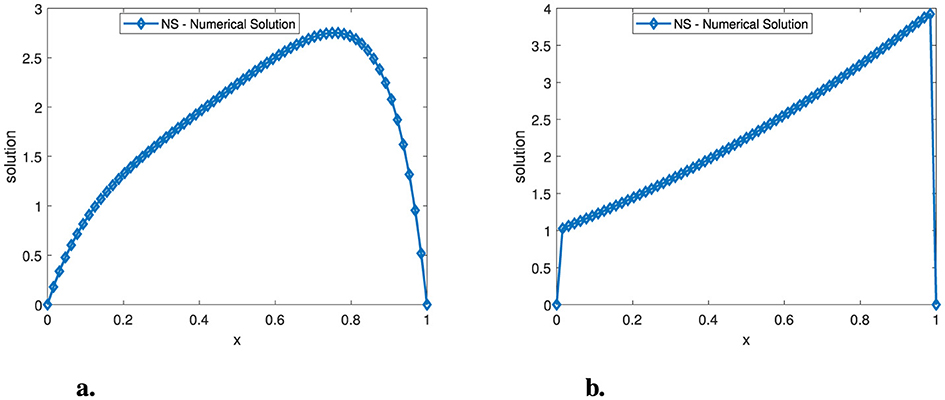
Figure 2. A plot of the numerical solution for Example (2) at N = 64 and μ = 10−6. (A) ε = 10−2. (B) ε = 10−6.
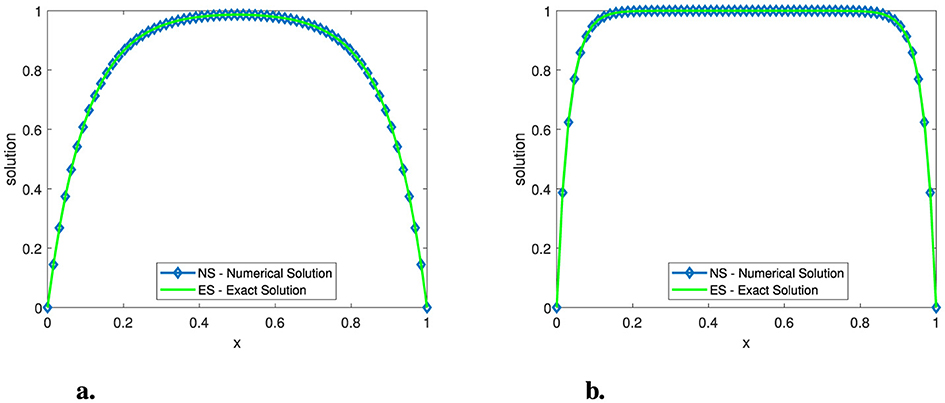
Figure 3. Plot of the numerical solution for Example (3) at N = 64 and μ = 10−6. (A) ε = 10−2. (B) ε = 10−3.
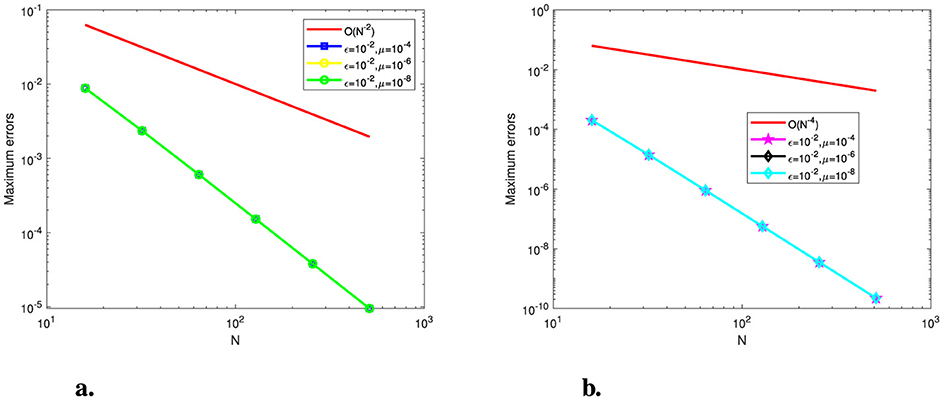
Figure 4. Log-log plot of the maximum point-wise errors for Example (1). (A) Before post-processing. (B) After post-processing.
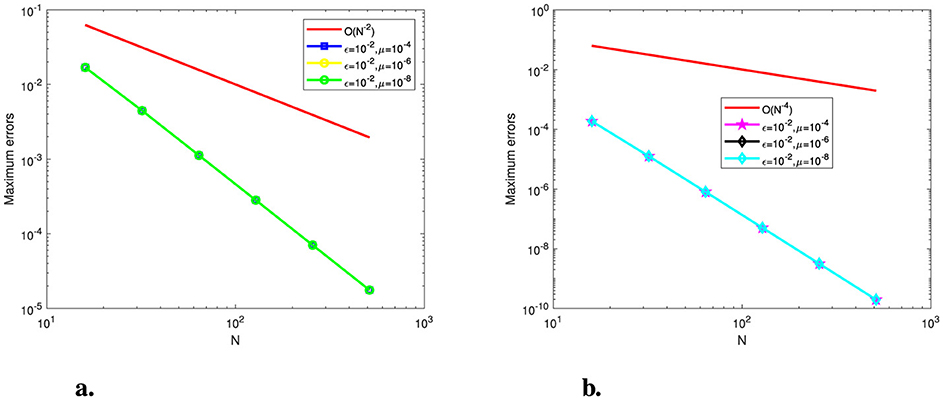
Figure 5. Log-log plot of the maximum point-wise errors for Example (2). (A) Before post-processing. (B) After post-processing.
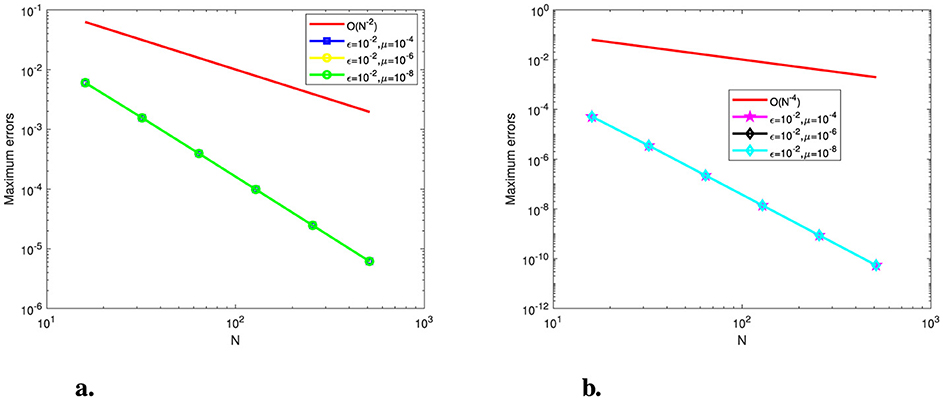
Figure 6. Log-log plot of the maximum point-wise errors for Example (3). (A) Before post-processing. (B) After post-processing.
6 Conclusion
A higher-order exponentially fitted operator finite difference method for two parameter singularly perturbed boundary value problems is presented in this study. The stability and uniform convergence of the current method are well established, ensuring second-order convergence. The post-processing technique is then applied to enhance the convergence order of the method and improve accuracy in terms of maximum errors. Theoretically, we have proven that the post-processing technique provides fourth-order parameter-uniform convergence. Three numerical examples are computed for various perturbation parameter values in order to verify the applicability of the current method. The present method can be applied to singularly perturbed parabolic problem with or without delay.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author/s.
Author contributions
AA: Conceptualization, Formal analysis, Investigation, Methodology, Software, Validation, Writing – original draft, Writing – review & editing, Supervision. FG: Conceptualization, Formal analysis, Investigation, Methodology, Software, Supervision, Validation, Writing – original draft, Writing – review & editing. MF: Conceptualization, Investigation, Methodology, Writing – original draft, Writing – review & editing, Software, Supervision.
Funding
The author(s) declare that no financial support was received for the research, authorship, and/or publication of this article.
Acknowledgments
The authors appreciate valuable comments and suggestions of the reviewers.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Chen J, O'Malley R Jr. On the asymptotic solution of a two-parameter boundary value problem of chemical reactor theory. SIAM J Appl Math. (1974) 26:717–29. doi: 10.1137/0126064
2. Bigge J, Bohl E. Deformations of the bifurcation diagram due to discretization. Mathem. Comput. (1985) 45:393–403. doi: 10.1090/S0025-5718-1985-0804931-X
3. DiPrima RC. Asymptotic methods for an infinitely long slider squeeze-film bearing. J Lubr Technol. (1968) 90:173–83. doi: 10.1115/1.3601534
4. O'Malley R. Two-parameter singular perturbation problems for second-order equations. J. Math. Mech. (1967) 16:1143–64.
5. Lodhi RK, Jaiswal BR, Nandan D, Ramesh K. Numerical Solution of two-parameter singularly perturbed convection-diffusion boundary value problems via fourth order compact finite difference method. Math Modell Eng Probl. (2021) 8:819–25. doi: 10.18280/mmep.080519
6. Kambampati S, Emineni SP, Reddy M, Kolloju P. Fourth order computational spline method for two-parameter singularly perturbed boundary value problem. Int J Appl Mech Eng. (2023) 28:79–93. doi: 10.59441/ijame/176516
7. Pandit S, Kumar M. Haar wavelet approach for numerical solution of two parameters singularly perturbed boundary value problems. Appl Math Inf Sci. (2014) 8:2965. doi: 10.12785/amis/080634
8. Khandelwal P, Khan A. Singularly perturbed convection-diffusion boundary value problems with two small parameters using nonpolynomial spline technique. Math Sci. (2017) 11:119–26. doi: 10.1007/s40096-017-0215-3
9. O'Riordan E, Pickett M. Numerical approximations to the scaled first derivatives of the solution to a two parameter singularly perturbed problem. J Comput Appl Math. (2019) 347:128–49. doi: 10.1016/j.cam.2018.08.004
10. Roos HG, Uzelac Z. The SDFEM for a convection-diffusion problem with two small parameters. Comput Methods Appl Math. (2003) 3:443–58. doi: 10.2478/cmam-2003-0029
11. Kadalbajoo MK, Yadaw AS. B-Spline collocation method for a two-parameter singularly perturbed convection-diffusion boundary value problems. Appl Math Comput. (2008) 201:504–13. doi: 10.1016/j.amc.2007.12.038
12. Kadalbajoo MK, Jha A. Exponentially fitted cubic spline for two-parameter singularly perturbed boundary value problems. Int J Comput Math. (2012) 89:836–50. doi: 10.1080/00207160.2012.663492
13. Brdar M, Zarin H. Convection-diffusion-reaction problems on a B-type mesh. PAMM. (2013) 13:423–4. doi: 10.1002/pamm.201310207
14. Luo XQ, Liu LB, Ouyang A, Long G. B-spline collocation and self-adapting differential evolution (jDE) algorithm for a singularly perturbed convection-diffusion problem. Soft Computing. (2018) 22:2683–93. doi: 10.1007/s00500-017-2523-9
15. Brdar M, Zarin H. On graded meshes for a two-parameter singularly perturbed problem. Appl Math Comput. (2016) 282:97–107. doi: 10.1016/j.amc.2016.01.060
16. Brdar M, Zarin H. A singularly perturbed problem with two parameters on a Bakhvalov-type mesh. J Comput Appl Math. (2016) 292:307–19. doi: 10.1016/j.cam.2015.07.011
17. Padmaja P, Aparna P, Gorla RSR, Pothanna N. Numerical solution of singularly perturbed two parameter problems using exponential splines. Int J Appl Mech Eng. (2021) 26:160–72. doi: 10.2478/ijame-2021-0025
18. Andisso FS, Duressa GF. Graded mesh B-spline collocation method for two parameters singularly perturbed boundary value problems. MethodsX. (2023) 11:102336. doi: 10.1016/j.mex.2023.102336
19. Linß T, Roos HG. Analysis of a finite-difference scheme for a singularly perturbed problem with two small parameters. J Math Anal Appl. (2004) 289:355–66. doi: 10.1016/j.jmaa.2003.08.017
20. Cheng Y. On the local discontinuous Galerkin method for singularly perturbed problem with two parameters. J Comput Appl Math. (2021) 392:113485. doi: 10.1016/j.cam.2021.113485
21. Zhang J, Lv Y. High-order finite element method on a Bakhvalov-type mesh for a singularly perturbed convection-diffusion problem with two parameters. Appl Math Comput. (2021) 397:125953. doi: 10.1016/j.amc.2021.125953
22. Valarmathi S, Ramanujam N. Computational methods for solving two-parameter singularly perturbed boundary value problems for second-order ordinary differential equations. Appl Math Comput. (2003) 136:415–41. doi: 10.1016/S0096-3003(02)00053-X
23. Patidar KC. A robust fitted operator finite difference method for a two-parameter singular perturbation problem1. J Diff Equ Appl. (2008) 14:1197–214. doi: 10.1080/10236190701817383
24. Hassen ZI, Duressa GF. Parameter-uniformly convergent numerical scheme for singularly perturbed delay parabolic differential equation via extended B-spline collocation. Front Appl Math Stat. (2023) 9:1255672. doi: 10.3389/fams.2023.1255672
25. Mohye MA, Munyakazi JB, Dinka TG. A nonstandard fitted operator finite difference method for two-parameter singularly perturbed time-delay parabolic problems. Front Appl Math Stat. (2023) 9:1222162. doi: 10.3389/fams.2023.1222162
26. Tesfaye SK, Duressa GF, Woldaregay MM, Dinka TG. Fitted computational method for singularly perturbed convection-diffusion equation with time delay. Front Appl Math Stat. (2023) 9:1244490. doi: 10.3389/fams.2023.1244490
27. Cheru SL, Duressa GF, Mekonnen TB. Numerical integration method for two-parameter singularly perturbed time delay parabolic problem. Front Appl Math Stat. (2024) 10:1414899. doi: 10.3389/fams.2024.1414899
28. Daba IT, Melesse WG, Kebede GD. Third-degree B-spline collocation method for singularly perturbed time delay parabolic problem with two parameters. Front Appl Math Stat. (2024) 9:1260651. doi: 10.3389/fams.2023.1260651
29. Gupta V, Kadalbajoo MK, Dubey RK. A parameter-uniform higher order finite difference scheme for singularly perturbed time-dependent parabolic problem with two small parameters. Int J Comput Math. (2019) 96:474–99. doi: 10.1080/00207160.2018.1432856
30. Gupta V, Sahoo SK, Dubey RK. Robust higher order finite difference scheme for singularly perturbed turning point problem with two outflow boundary layers. Comput Appl Math. (2021) 40:1–23. doi: 10.1007/s40314-021-01564-w
31. Sahoo SK, Gupta V. A robust uniformly convergent finite difference scheme for the time-fractional singularly perturbed convection-diffusion problem. Comput Math Appli. (2023) 137:126–46. doi: 10.1016/j.camwa.2023.02.016
32. Ejere AH, Duressa GF, Woldaregay MM, Dinka TG. A robust numerical scheme for singularly perturbed differential equations with spatio-temporal delays. Front Appl Math Stat. (2023) 9:1125347. doi: 10.3389/fams.2023.1125347
33. Daba IT, Duressa GF. Numerical treatment of singularly perturbed unsteady Burger-Huxley equation. Front Appl Math Stat. (2023) 8:1061245. doi: 10.3389/fams.2022.1061245
34. Derzie EB, Munyakazi JB, Dinka TG. A NSFD method for the singularly perturbed Burgers-Huxley equation. Front Appl Math Stat. (2023) 9:1068890. doi: 10.3389/fams.2023.1068890
35. Li J, Singh G, Ilhan OA, Manafian J, Gasimov YS. Modulational instability, multiple Exp-function method, SIVP, solitary and cross-kink solutions for the generalized KP equation. AIMS Math. (2021) 6:7555–84. doi: 10.3934/math.2021441
36. El Ahmadi M, Ayoujil A, Berrajaa M. Existence and multiplicity of solutions for a class of double phase variable exponent problems with nonlinear boundary condition. Adv Math Models Appl. (2023) 8:401–14.
37. Nachaoui A. An iterative method for cauchy problems subject to the convection-diffusion equation. Adv Math Models Appl. (2023) 8:327–38.
38. Mardanov MJ, Sharifov YA, Gasimov YS, Cattani C. Non-linear first-order differential boundary problems with multipoint and integral conditions. Fractal Fract. (2021) 5:15. doi: 10.3390/fractalfract5010015
Keywords: an exponentially fitted, higher order method, two parameters, post-processing technique, twin boundary layers
Citation: Agmas AF, Gelu FW and Fino MC (2025) A robust, exponentially fitted higher-order numerical method for a two-parameter singularly perturbed boundary value problem. Front. Appl. Math. Stat. 10:1501271. doi: 10.3389/fams.2024.1501271
Received: 24 September 2024; Accepted: 04 December 2024;
Published: 07 January 2025.
Edited by:
Tariku Birabasa Mekonnen, Wollega University, EthiopiaReviewed by:
Yusif Gasimov, Azerbaijan University, AzerbaijanVikas Gupta, LNM Institute of Information Technology, India
Copyright © 2025 Agmas, Gelu and Fino. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Fasika Wondimu Gelu, UnVoYW1hdGFkdWZhc2kyMkBnbWFpbC5jb20=
 Adisie Fenta Agmas
Adisie Fenta Agmas Fasika Wondimu Gelu
Fasika Wondimu Gelu