
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
SYSTEMATIC REVIEW article
Front. Public Health, 03 October 2022
Sec. Digital Public Health
Volume 10 - 2022 | https://doi.org/10.3389/fpubh.2022.965017
This article is part of the Research TopicPositive or Negative? The Effect of Emerging Technologies and Products on Mental HealthView all 10 articles
 Sobana Jeyagobi1
Sobana Jeyagobi1 Shalini Munusamy1,2
Shalini Munusamy1,2 Mohammad Rahim Kamaluddin1*
Mohammad Rahim Kamaluddin1* Abdul Rahman Ahmad Badayai1
Abdul Rahman Ahmad Badayai1 Jaya Kumar3
Jaya Kumar3Cyber-aggression is global epidemic affecting citizens of cyberspace, without regards to physical, geographical and time constraints. Recent research has identified the significant role of cyber-bystanders in exacerbating and de-escalating incidents on cyber-aggression they come across. Additionally, frequent exposure to cyber-aggression is found to have been associated with negative effects on participants of cyber-aggression, ranging from self-esteem problems to mental health disorders such as depression and anxiety, and in the worst cases even suicidal behaviors and ideation. Moreover, past research had also identified that negative bystanders could potentially become aggressors themselves. Therefore, the current review is aimed at uncovering the common themes and factors that drive individuals to resort to negative bystander behavior. Hence, a systematic literature review using the PRISMA framework was carried out, involving articles published between January 2012 to March 2022, on online databases such as SCOPUS, Science Direct, SAGE Journals, Web of Science, and Springer Link. Results obtained through the synthesis of 27 selected articles, were grouped into three categories, namely situational factors, personal factors and social influence. Upon further synthesis of the results, it was noted that many of the factors had interacted with each other. Thus, practical suggestion for prevention and future research would include addressing these interactions in preventative methodologies and research interests.
The introduction of handheld supercomputers such as tablet computers and smartphones has not only made the internet and its affordances increasingly accessible but has also made one's exposure to cyberspace and the digital landscape as inevitable as it is essential. Aside from improving one's quality of life, the increased reliance and almost constant exposure to cyberspace can not only turn into dependence and subsequent addiction, but can also decrease one's quality of life in various aspects [e.g.,: (1–4)], including by exposing individuals to phenomena such as cyber-aggression (5, 6). According to past literature, rates at which cyber-aggression is perpetrated or victimizes an individual, fall between 1 to 41% and 3 to 72%, respectively (7).
Similarly to problematic internet use, it is associated with a host of negative thought patterns and behaviors ranging from mental health problems such as depression and suicide (8), to behavioral problems such as consequent or past involvement in bullying or aggressive behavior (8–11). Despite that, those who experience the fear of missing out (FOMO) tend to refrain from reporting the incident to others due to the fear of losing access to the internet or their phones which keep them connected in ways they desire (12), suggesting that the dependence on the digital world can potentially keep people in a loop of negative experiences.
Given the multifaceted nature of cyberaggression and the need to improve general understanding and intervention efforts associated with it, researchers from various fields have investigated the phenomenon from a variety of angles. These include identifying risk factors associated with cyber-aggressors (8, 10, 13), building standardizable research instruments [e.g.,: (11, 14, 15)], studying the efficacy of intervention strategies (16, 17), improving detection of aggression online (18–20), and more recently, cyber-bystander behavior, among others. The improved understanding of the role of cyber-bystanders in an incident of cyber-aggression has assisted in improving the understanding of the unique mechanism of cyber-aggression, and subsequently, the way it is defined, as well as the way intervention efforts are approached.
For instance, the presence and influence of cyber-bystanders are one of the reasons which prompted researchers to call for cyber-aggression to be distinguished from face-to-face aggression, defining it simply as being an act that is carried out using Information and Communications Technology (ICT), with the intent to cause harm to an individual (or individuals) who would have rather avoided it, omitting factors such as repetition and power imbalance which characterize traditional bullying or aggression (21, 22). This not only acknowledges the significant impact of other factors that mediate and exacerbate or merely influence cyber-aggression such as the presence and actions of cyber-bystanders but also allows for the inclusion of other singular but harmful acts such as happy slapping and outing (22, 23).
Cyber-bystanders, in simple terms, make up the audience who not only witness incidents of cyber-aggression but also have the capacity to either escalate or de-escalate the severity of the incident they have witnessed through their own response or even lack of response (21, 22). While many cyber-bystanders do utilize the opportunity to intervene positively and defend and/or comfort the victim, or even confront the aggressor constructively in order to de-escalate the situation, a non-negligible number of individuals engage in bystander behavior which reinforces the act of aggression against the victim or may even become hostile toward the aggressors (24). Moreover, cyber-bystanders are also at risk of becoming primary aggressors themselves (24).
Additionally, past research has identified that their impact on cyber-victims is no different than that of a primary aggressor. For instance, victims become warier of their social environment or experience fear and worry about being revictimized and having to revisit the incident and the pain it elicits whenever someone shows support for the aggressor by interacting with the victimizing post (12). Additionally, young people express that they do not receive the necessary support from their environment and admit to being unequipped to aid their peers manage and resolve these experiences (12). Hence, it is no wonder that feelings of loneliness, mistrust, embarrassment, fear, sadness and helplessness, and depressive symptoms as well as suicidal ideation, were associated with these revictimized individuals (25).
Furthermore, having to face incidents of cyber-aggression even as a bystander, was found to be associated with depression and/or anxiety due to the fear of being victimized, feeling empathic concern for the victimized individuals followed by the helplessness that results from not knowing how to navigate through the situation (26). In addition to that, frequent and long-term exposure to cyber-aggression on the internet could also result in individuals having lesser levels of empathic responses toward distressed individuals over time (27), and if bystanders were to perceive cyber-aggression as being a norm or expectation within their social circle, they are more likely to reinforce such acts (28).
Therein lies the importance of addressing what drives the behavior of bystanders, particularly those individuals who choose to engage in behavior that explicitly exacerbates a cyber-aggressive act, in addition to individuals whose passive behavior can act as silent approval of an instance of cyber-aggression. Therefore, the aim of the current review is to identify and synthesize results from past studies which have pinpointed the factors that influence an individual's decision to resort to negative bystander behavior. Additionally, the types and the frequencies of negative bystander behaviors addressed in the selected studies will also be highlighted for context and a better understanding of the phenomenon.
Literature was sourced using five different online databases, namely Scopus, Science Direct, Web of Science, Springer Link, and SAGE Journals. The search was conducted during the last week of February 2022 up to mid-March 2022, targeting articles published in the past decade and throughout the search period.
Keywords to be used were identified by reviewing past literature addressing negative cyber-bystander behavior—words associated with the term “bystander” and the various forms of negative bystander behavior were sourced. The search resulted in the finding that cyber bystander was used interchangeably with the words “cyber observer” and “cyber witness”, and the types of negative bystander behavior can be summarized as being behaviors that reinforce the aggressor or act of aggression, aggressive behaviors, or passivity. Additionally, before identifying the keyword string to be used, the search features of the selected online literature databases were investigated. Special symbols to promote truncation of used keywords were omitted as they were already built into the database search engines.
The final string of keywords used was “((cyber bystander) OR (cyber witness) OR (cyber observer)) AND (aggressive OR passive OR reinforce)”, whereby the keyword string was divided into two halves, containing the synonyms of “cyber-bystander” in the first half and keywords associated with negative bystander behavior for specification and focus in the second half.
Literature was screened in multiple stages, beginning from the inspection of the title and abstract to select suitable articles from the databases, followed by the close examination of the full-text of the article to determine whether they qualify to be included in the review. Inclusion and exclusion criteria were set as parameters to aid these processes, to ensure that a coherent set of articles are selected to be included in the review, allowing the researcher to fulfill the purpose of the study as accurately as possible.
Firstly, in order to ease the process of reviewing the articles, and to avoid misinterpretation of the contents of the articles due to flaws in translation, the articles screened were limited to those written in the English language. Secondly, a timeline spanning a decade, from 2012 to the current year, was set, taking into account the development of the technological scene which may have differed too vastly in the previous decade given how rapidly technology has evolved, possibly affecting the findings regarding individuals' behavior online. In addition to that, only research articles that discuss and elaborate on negative cyber-bystander behavior, which includes behaviors such as assisting the bully, aggressive intervention, and even the absence of intervention entirely, were included.
In the current review, negative bystander behavior was characterized as any response to cyberbullying which encourages bullying, including the absence of intervention as it is viewed as silent approval and reinforcement of the act of bullying, and “aggressive defending” through which a bystander defends the victim via acts of aggression against the bully. Other such acts include reinforcing the bully by assisting them, encouraging them through laughing along or sharing the content with others, and the like. This would indefinitely exclude articles which only address positive and constructive bystander behavior which express support toward the victim and disapproval of cyberaggression without the use of excessive aggression.
Additionally, articles which do not clearly identify the relationship between identified factors and negative bystander behavior and approach the topic through the lens positive bystander behavior will also be excluded to avoid misinterpretation of the results. The criteria are better presented in Table 1.
The literature search was split into two sections, whereby the first part of the search involved using search engines of literature databases to recall articles relevant to the keyword string input, and the second part involved a backwards and forwards search using relevant articles.
Through the preliminary literature search using the literature databases, 4,410 articles were identified and were screened based on their abstract and title. This preliminary screening resulted in 132 articles being identified and selected for further screening. On the other hand, as for the backwards and forwards search, a randomly selected article published in 2020 and 2013, respectively, were used to fill timeline gaps. The literature database “Web of Science” was used for these processes, which resulted in 25 most relevant articles being identified through the screening of their title and abstract alone. Next, upon the removal of articles that could not be accessed, were not written in English and were duplicates, authors were left with 116 articles to be screened. These articles were screened based on their full-texts to determine whether or not they met the inclusion criteria set. This resulted in 27 relevant articles being selected as the most suitable to be included in systematic review and fulfill the research objective of identifying the factors associated with negative bystander behavior. The process is presented in the PRISMA (Preferred Reporting Items for Systematic Reviews) flow-diagram (Figure 1).
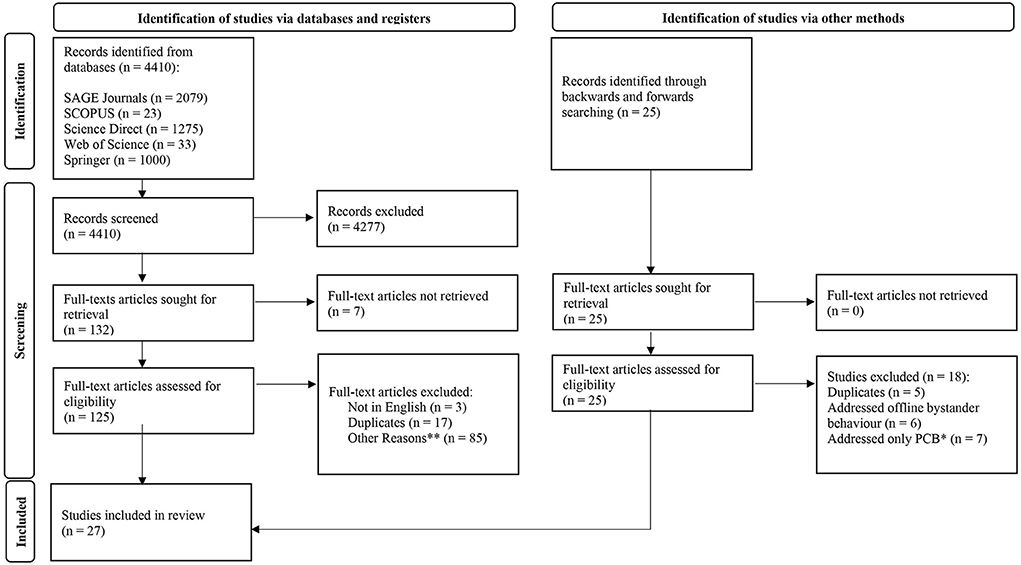
Figure 1. PRISMA flow-diagram. Source: Page et al. (29).
Selected articles were then screened for author names, age range of participants, study design, types and prevalence rates of negative cyber-bystander behavior, and lastly the factors that contribute to negative cyber-bystander behavior. The data extracted are presented in Table 2 and discussed in the following section.
Some of the reasons articles were excluded include the fact that they did not discuss negative cyber-bystander behavior, and discussed positive cyber-bystander behavior [e.g.,: (30–33)], addressed bystander behavior in offline settings [e.g.,: (34, 35)], addressed cyberaggression rather than reinforcement of the act through negative cyber-bystander behavior [e.g.,: (36–38)], how people protect themselves [e.g.,: (39)], and the like instead.
The analysis of included studies reveal that there are four different types of negative cyber-bystanders—passive bystanders, assistants, reinforcers and aggressive defenders. These bystanders, remain passive, join in on the aggression, show support for the aggressor, and aggress against the aggressor, respectively. “Showing support for the aggressor” within this review, was found to be limited to behaviors such as sharing the incident with others with the intent of making fun of the victim, laughing at the incident, telling the aggressor that they found the situation funny, and cheering on the bully. On the other hand, “aggressive defending” included behaviors such as threatening the aggressor, spreading rumors about the aggressor, or releasing their private information online, saying mean things about the aggressor and lastly, asking the aggressor to “back off”.
Out of the twenty seven studies included in this review, only eleven studies reported prevalence rates of negative cyber-bystander behavior, and these rates fell between the ranges of 1.8–55.4%, depending on the type of behavior measured. The most common negative cyber-bystander behavior was passive bystander behavior, with prevalence rates ranging from 10.55 to 55.4%, followed by reinforcers, assistants, and aggressive defenders with rates as low as 1.8% and a maximum of 26.3% overall. While the prevalence of the latter types of negative cyber-bystander behaviors are much less common, they have a more direct effect on the victim, and the severity and/or direction of an incident.
In terms of the factors that were associated with these behaviors on the other hand, the analysis of the results indicates that the most studied variables were what the current review categorizes as “personal factors”, and the least commonly addressed variables were associated with social influences. Moreover, there are a noteworthy number of studies which both, studied and loosely addressed “mediating” variables to explain the motivation behind negative cyber-bystander behaviors. Additionally, many studies had discussed certain parts of their findings (i.e.,: the relationship between the variables studied and cyber-bystander behavior) in relation to constructive cyber-bystander behavior without clarifying how or if said variables influence or are associated with negative cyber-bystander behaviors. Hence, only certain variables from these studies can be reported within the current review, and are reported alongside other details of the study in Table 2. Following that, the factors associated with negative cyber-bystander behavior which were identified through the review process were then grouped into three categories, namely (a) personal factors, (b) situational factors, and (c) social influence, and are presented in Table 3, and discussed in the sections below.
These factors address qualities unique to an individual, such as their demographic backgrounds, their past experiences, levels and usage of moral disengagement strategies, empathy levels, skills and beliefs pertaining the efficacy of their capacity.
While various demographic factors were addressed, age and gender were the most commonly studied across the articles included in this review and were the only demographic factors identified as being significantly associated with negative cyber-bystander behavior, with some exceptions which provided contradicting results by Schultze-Krumbholz et al. (40), Erreygers et al. (41), and Barlinska et al. (42).
With regards to age, it was noticed that older individuals expressed more reluctance to intervene (41), and were more likely to remain passive as a bystander (43) or join in on the aggression (43, 44). The lack of constructive intervention and higher negative cyber-bystander behavior among older individuals in the sample populations were rationalized using low empathy scores (45), the increase in anti-social tendencies in older adolescents (44) and social influence such as the fear of judgment by peers (41).
Gender differences reported by the studies included in the review, on the other hand, seemed to consistently indicate that male individuals were more prone to negative cyber-bystander behavior, in comparison to their counterparts. Not only was it identified that boys had a higher likelihood of being passive (45, 46) and possessing higher behavioral intention to reinforce the aggressor (31), being male could also significantly predict an individual's involvement as an assistant (47). However, variables such as moral disengagement strategies which distort the consequences of their behaviors, as well as perceived severity were found to moderate the relationship between gender and pro-aggressor behaviors in the study by Schultze-Krumbholz et al. (47), suggesting that the relationship between gender and negative cyber-bystander behavior might not be very straight-forward and will require further analysis.
Unsurprisingly, studies found that individuals with past experience as an aggressor were more likely to be associated with negative cyber-bystander behavior (28, 42–44). This was true for both traditional aggressors who engaged in face-to-face aggression, as well as cyber-aggressors who were bullies in cyberspace (43). Panumaporn et al. (44) elaborated on these results, stating that individuals who were bullies tend to hold positive beliefs pertaining to the use of aggression and that this attitude is likely to be reflected in their behavior as cyber-bystanders as well. Moreover, individuals who were aggressors did not feel pressured into joining in on the aggression as cyber-bystanders (28). On the other hand, it was identified that aggressive defenders were also more likely to have had experiences of being cyber-victims in the past, in comparison to their peers who engaged in more prosocial behaviors (47).
Seven different studies identified differing normative believes, outcome expectations and attitudes pertaining to cyber-aggression or bystander behavior. Put simply, the findings of these studies indicate that individuals tend to engage in behaviors that they perceive would result in either a reward or the avoidance of harm. For example, individuals stated that they remained passive for safety reasons (48) or the fear of being victimized in the process of defending a victim (43, 49–51). On the other hand, DeSmet et al. (52) found that individuals were also prone to remaining passive or reinforcing the aggressor if they expected to be rewarded with a rise in social status, the possibility to gain new friends, for self-protection or if they held positive beliefs about their choice of response as a bystander. Additionally, it was also noticed that individuals who believed that aggression was a valid response to provocation, as well as those who had lower levels of defending normative beliefs were moe likely to resort to pro-bullying behavior that reinforces aggression (53).
Whether or not individuals possessed the skill or the belief that they were capable of effectively handling an incident of cyber-aggression as a bystander, was found to be associated with negative bystander behavior. In essence, individuals who lacked self-efficacy or the skills to intervene, had a higher tendency to become negative bystanders (43). While participants in the study by Bauman et al. (50) simply stated that the “did not know what to do” in response to why they remained passive, more specific factors such as the lack of defending self-efficacy (54), social self-efficacy and knowledge (55), as well as low socio-emotional skills (47), self-reliance, and problem-solving strategies) were linked to the increased tendency to resort to negative cyber-bystander behavior. Van Cleemput et al. (43) suggested that the lack of control individuals have over an incident of cyber-aggression, such as the inability to prevent something from going viral given the public nature of cyber-space as well as the speed through which information spreads digitally, could contribute to the perceived lack of skills (i.e.,: low self-efficacy) among individuals. It is important to note, however, that the adolescents in the study by Bussey et al. (54) neither remained passive nor reinforced the aggressor, but instead resorted to aggressive defending styles by redirecting the aggression toward the aggressor when they lacked the self-efficacy to defend individuals in more constructive ways.
Cross-sectional studies show that lower levels of empathy was able to predict individuals' negative bystander behavior (43, 47). Additionally, an empathic reaction was found to be the only differentiating factor between bystanders who respond in supportive ways and those who chose to remain passive (46). Lastly, a noteworthy finding by Machackova et al. (46) indicates that it's likely that empathic reactions could be reliant on contextual factors that might play a more crucial role in determining the final response.
Without surprise, studies found that more aggressive individuals had a higher tendency to assist aggressors (47). Schultze-Krumbholz et al. (47) highlighted reactive aggression in particular and suggested that the behavior is likely influenced by impulsivity and identified this group of individuals as being at a higher risk of becoming aggressors, in comparison to their peers.
Moral disengagement was found to be one of the more prominent theme and variable in this review, with seven different studies highlighting its link to negative bystander behavior. It is defined as a mechanism that allows an individual to reconstruct their beliefs about negative and harmful behaviors by either minimizing or distorting the consequences of said behaviors, or shifting the blame and/or responsibility away from themselves or onto others, allowing them to justify engaging in such behaviors (56). The results presented by the studies indicate that individuals who were more morally disengaged were also more prone to engaging in aggressive defending (54, 57), as well as positive bystanding (49, 58). This is likely because moral disengagement processes provide individuals with the tools to justify their behavior (49), even in the event that they behave in ways that contradict their own values (58).
Van Cleemput et al. (43) who studied the influence of various aspects moral disengagement mechanisms identified that diffusion of responsibility, attribution of blame, and distortion of consequences as well as displacement of responsibility as being factors that are positively linked to negative cyber-bystander behavior. Similar patterns can be found in other studies as well, where individuals who had low levels of moral responsibility (58) or believed that it was “not their problem” (48, 50, 51, 55) were more likely to be negative bystanders. DeSmet et al. (52) on the other hand, found contradicting evidence pertaining the mechanism of attribution of blame, whereby lower victim blaming tendencies were associated with passive bystander behavior, suggesting that it is possible that individuals were behaving in ways that go against their own beliefs.
Three different characteristics of computer mediated communication (CMC) were identified through this study. The first being the absence of physical aggression which diminishes the severity of the event in the eyes of cyber-bystanders (59). Secondly, student's suggested that the lack of rules and authority figures present in online spaces, to provide guidance, led them to remain passive when they witnessed incidents of cyber-aggression (59). Lastly, it was noticed that the increase in tendency to be a passive bystander was contributed by the bystanders' delayed exposure to the incident of cyber-aggression (43).
Participants in a study by Barlinska et al. (42) were found to be more likely to remain passive as a bystander when the incident they had witnessed was private in the nature. The researchers theorized that it was the result of the lack of social pressure to conform to social norms, which is present in situations where there is a large audience.
In the study by You and Lee (60), it was identified that the intention to intervene was more influenced by their own anonymity or lack thereof, rather than the number of cyber-bystanders present.
In most of the reported findings addressed in the studies included in the current review, it was noticed that individuals were more likely to remain passive if they perceived a situation as being not severe enough to require intervention (49, 50, 55, 59, 61). This falls in line with the Bystander Theory by Latane and Darley (62), which states that individuals need to perceive the situation as being an emergency that requires their intervention in order to engage in proactive and constructive bystander behavior. Additionally, it was also identified that individuals remained passive if they assumed that the victim had the capacity to handle the situation themselves, or if they found enjoyment in witnessing the incident (50)—it seems reasonable to assume that that this would have made a situation seem less like an emergency that requires their intervention.
In addition to the perceptions about the severity of the incident, two studies found that bystanders also remained passive when they experienced difficulty in interpreting the nature of the incident they are witnessing (43, 63) and/or were uncertain about who was responsible for the incident (43). On the other hand, they were more likely to engage in behaviors that reinforce the aggression and aggressor if they believed that the event they were witnessing was a joke between parties involved (63).
Cyber-bystanders' behavior was found to be influenced by not just the behavior of other bystanders (31, 49, 50) but also the number of bystanders present (60, 64), as well as the gender of the protagonist (63) involved in an incident of cyber-aggression. Through this review, it was noticed that bystanders were likely to reinforce aggressor (31) or remain passive (50), if other bystanders, especially close friends were to engage in such behaviors (31). Additionally, the “bystander effect” which states that individuals are less likely to intervene in the presence of a large audience, was present in reports by Song and Oh (64) as well as You and Lee (60). However, it was reported that passive bystander behavior was possible even in the absence of other bystanders, in the event that these bystanders had a positive relationship with the aggressor(s), likely to preserve their relationship with the aggressor (64), suggesting that there are other important contextual factors that need to be taken into account when addressing the number of bystanders and its relationship with the behavior of bystanders.
Lastly, a lone study by Patterson et al. (63), in which adolescents were allowed to freely state their reasons for passive behavior, it was identified that individuals did not want to intervene in situations where the protagonists were female as they believed that the situation was less controllable than when the protagonists were male.
As addressed in an above-mentioned section, bystanders' behavior was also found to be influenced by their relationship with the participants involved in an incident they had witnessed. For example, if they were friends with aggressor, they were more likely to reinforce or ignore the incident and disregard the plight of the victim (50, 64) in order to maintain their relationship with the aggressor (64). However, Song and Oh (64) clarified that this behavior was context dependent and relied on the absence of other bystanders, as the presence of other bystanders would lead to defending behaviors.
Additionally, bystanders were also found to remain passive when they were not closely acquainted with or had a bad relationship with the victim (46, 50, 55), or in the event that they did not have a close relationship with any participant involved in the incident of cyber-aggression they witnessed (44, 63). It could be because individuals perceived levels of responsibility based on the closeness of their relationship with the victim (55)—the closer they were, the more responsibility they had to intervene and defend the victim, and vice versa (44). It could possibly be explained by how people tend to view individuals from their in-group and their out-group as most people tend to prioritize their in-group (i.e.,: individuals they identify with, and are close to) in comparison to those who are more distant to them (44). Machackova et al. (46) on the other hand, theorized that an individual's relationship with the victim could influence their perception of the severity of the event they are witnessing, meaning the closer they were to the victim, the more severe they would perceive an incident to be. According to the “bystander effect” theory and the bystander intervention model, a lower perception of severity would lead to passivity in the face of aggression as a bystander.
The popularity of the aggressor was stated as a reason why 16% of the bystanders in the study by Bauman et al. (50) had refrained from intervening and had chosen to remain as passive bystanders. It could be that going against a popular individual who holds a higher social status costs a lot more than individuals are willing to deal with.
In the event that individuals held the perception that their peer would support or expect them to join in on the bullying, they were more likely to join in on the bullying and reinforce the aggression against the victim, to maintain their relationships and social status (28, 31).
Only Levy (65) addressed the influence of parental monitoring. It was noticed that higher aggressor-supporter scores were positively associated with the behavior of reinforcing and supporting aggressors. However, it was not expressed as a causal relationship and authors suggest that restrictions could be the consequence of aggressor-supporter behaviors and questioned the efficacy of such measures if it were the case.
Schultze-Krumbholz et al. (40) found that lower levels of positive peer interactions in class was associated with assistant behavior cyber-aggression situations. Additionally, they also stated that classrooms that contained a higher number of offline-aggressors tend to promote more negative cyber-bystander behavior—likely due to social norms and pressure.
The acknowledgment of the influence of cyber-bystanders in influencing incidents of cyber-aggression has allowed for a more complete understanding of the mechanism of cyber-aggression, which in turn allows for the identification of crucial risk factors that contribute to the reinforcement and/or prevalence of the phenomenon. While these individuals known as negative cyber-bystanders, in contrast to the more constructive cyber-bystanders, have been studied for a while now, the data obtained are scattered and lacking. Hence the current review aims to compile, present and discuss existing findings from journal articles published in the past decade, to provide a more coherent look at the data, and highlight potential findings of interest that may aid in the identification of future research questions. The discussion will be broken into several sections which will discuss the factors associated with negative cyber-bystander behavior, as well as directions for future studies and limitations of the current review.
Based on the review of the results and discussions produced by the studies included, it appears evident that negative cyber-bystander behavior is the result of the interaction of multiple factors, and that mediating and moderating factors should be of focus and rigorously studied to better understand the phenomenon. Despite the complexity of the associations between the variables of interest, several notable themes were identified. Firstly, the review indicates that the Bystander Intervention Model introduced by Latane and Darley in 1970 (61) was a relatively simple yet useful model that identified noteworthy precursors to negative cyber-bystander behavior.
Latane and Darley's (62) Bystander Intervention Model posits that (a) the perception of the severity of an incident and need for intervention, (b) accepting responsibility to intervene and (c) having the capacity to intervene were important precursors to bystander behavior (61). The findings identified through the review echoed this, as those who (a) minimized the severity of the event (49, 50, 55, 59, 61), (b) did not think that it was their responsibility to intervene (43, 48, 50, 51, 55), and those who had neither the necessary skills and knowledge (43, 50) nor the self-efficacy to intervene (54), had consequently resorted to negative cyber-bystander behavior.
The need for intervention appears to be assessed in two ways; based on (a) the severity of the incident and (b) the capacity of the individuals involved to manage the situation without additional intervention. Evidently, those who believed that victims (50) or other bystanders (49) would accept the responsibility and have the capacity to effectively resolve or handle the situation were more likely to detach themselves from the situation and remain as passive bystanders. Those who had the tendency to minimize the severity of a situation, however, did not consistently adopt the role of a passive bystander as a result. For instance, individuals consistently ignored the incident when they perceived the absence of physical aggression to mean that the situation was not severe enough (59), or because they perceived the inaction of other bystanders as a sign that there was no need for intervention (49). On the other hand, while some individuals remained passive when they perceived the incident as being mere banter among peers (63), others had chosen to reinforce it (49, 63). This implies that there may be two stages in the process leading to a behavioral response, whereby the initial step involves factors that first influence the perception of the severity of the event, followed by the second step which includes an additional variable that subsequently influences the resulting type of negative cyber-bystander behavior.
An individual's perception regarding their responsibility to intervene, on the other hand, was in many instances associated with the nature of their relationship with participants involved in the incident, as individuals only felt more responsible to intervene when they were close to the victims (44, 55), hence were less likely to intervene when they had neither a close nor positive relationship with the victim (43, 46, 50, 55) or any other participant in general (44, 63). Moreover, when faced with ambiguous situations that make it difficult for individuals to even identify whether intervention is necessary, a close relationship with other participants would allow them to directly request for further context or clarification, and subsequently determine whether they must or want to intervene (63). Whereas, those with a weaker relationship with other participants would be deprived of this opportunity. Given the lack of contextual information present online, and the fact that the ambiguity of a situation leads individuals to remain passive, this presents as a vital finding (43, 63).
Regarding the lack of skills that were associated with negative bystander behavior, as mentioned in the result section, both the lack of problem-solving (52) as well as socio-emotional skills (47) resulted in negative cyber-bystander behavior. Similarly, factors like the lack of self-reliance (52), defending self-efficacy (50, 54), general self-efficacy (43), social self-efficacy (55) and components of empathy (43, 47), which are associated with these skills, were also associated with an increased likelihood that individuals would resort to negative cyber-bystander behavior. Building these skills and improving one's self-efficacy, which could promote later positive cyber-bystander behavior, requires both, the opportunity to learn and to practice those skills. One of the reasons that hinder these possibilities is the reliance on others, like authority figures, when faced with incidents of cyber-aggression, rather than relying on themselves, as it would likely decrease the opportunities to build these necessary intervention skills (59). Therefore, although teaching individuals to reach out to authorities or others who may be able to help or guide them is necessary, it is also important to create opportunities for them to develop these crucial skills.
Moreover, one's environment needs to promote these behaviors as being desirable behavior in order to further encourage it as the review indicates that individuals tend to engage in these behaviors if they believe that their peers expect (28) or will reward such behaviors (52), or that it would keep them safe (43, 49–51). This includes efforts to discourage both face to face and online cyber-aggression as those who were in classrooms with a higher number of aggressors were more likely to reinforce aggression (40). In addition to that, efforts to improve poor peer relationships and peer support also seem vital as factors such as self-efficacy were found to be associated with these variables (51), and it might also increase one's sense of safety when they have adequate social support. Based on the above-mentioned section, it also seems reasonable to believe that good peer relationships have the potential to promote a higher sense of responsibility (44) to engage in incidents of aggression as constructive cyber-bystanders.
It shouldn't go unnoticed that some individuals who lack defending self-efficacy may still assist the victim, albeit resorting to aggressive behaviors directed at the aggressor (54). This indicates that some individuals may have the correct intention, the ability to understand that intervention is required, and subsequently choose to intervene, but choose retaliatory acts similar to that of cyber-aggressors rather than more constructive ways of intervening. Schultze-Krumbholz et al. (47) identified that factors such as past experience as either a cyber-victims or cyber-aggressors, lower socio-emotional skills, as well as higher reactive-aggression, and possibly also impulsivity as being associated with these individuals. Bussey et al. (54) and Luo and Bussey (57) on the other hand, caution that these individuals are more closely linked to aggressors rather than defenders, making it necessary to clearly differentiate the various types of negative cyber-bystander behavior rather than grouping them together.
Another important theme that was identified through the review was the fact that there seemed to be notable distinctions between factors associated with aggressive and passive types of negative cyber-bystander behavior, despite there being some overlapping variables. For instance, aggression, whether it's their own past experience as aggressors (28, 42–44), increased exposure to aggressors in their environment (40), or their belief that aggression can be a valid response (53), was naturally more likely to be associated with aggressive forms of cyber-bystander behavior. Moreover, these behaviors were also associated with the belief that it would result in favorable responses such as an improvement in social status or opportunity for new friendships (52). On the other hand, passive bystanders were associated with factors which were related to avoidance of undesirable consequences like a threat to their safety (48), potential victimization (43, 49–51), loss of friendships (43) and etc. As highlighted above, it also has to do with not accepting responsibility to intervene, as well. However, this should be interpreted with caution given that studies had rarely addressed or compared the different types of negative cyber-bystander behavior.
In addition to above-mentioned themes, moral disengagement strategies, whether or not explicitly studied, were observed to be present in many of the situations that were discussed in the findings of the study. Simply put, moral disengagement is a mechanism of thought through which individuals rationalize and justify their harmful or generally negative behaviors (56), which in the case of the study would subsequently lead to or is simply positively associated with negative cyber-bystander behavior (49, 54, 57, 58). It involves the use of strategies such as the attribution of blame, the displacement or diffusion of responsibility, cognitive restructuring, distorting consequences of an action and etc. (56), most of which can be identified within the current review even in studies outside of those that had provided empirical evidence pertaining to their relationship with negative cyber-bystander behavior.
Some of the examples include the diffusion of responsibility experienced by individuals in a large crowd (60), placing blame and the responsibility to handle the situation on the victim (43), detaching themselves from their aggressive friends and the consequences of their behaviors (64), trivializing their reinforcement of aggression and reframing it as mere banter (49) or just the minimization of the severity of the incident in general (43), among other things. Moreover, aside from reinforcer and passive bystanders, both empirical evidence and simple deduction suggest that aggressive defending, was associated with moral disengagement strategies (54, 57), as it requires individuals to justify why their use of aggression is morally correct while the aggressor's use of aggression was not. These findings suggest that individuals resort to moral disengagement strategies in order to simultaneously maintain their own moral identities while also engaging in negative cyber-bystander behavior without feelings such as guilt. Additionally, moral disengagement was found to moderate the relationship between gender and pro-aggressive bystander behavior, further implying that it might be the factor that distinguishes between individuals that resort to such behaviors and those who don't (47).
Similarly, the bystander effect, as introduced by Latane and Darley (62), which suggests that individuals tend to resort to being passive in the presence of other bystanders (60), was proven by Chan et al. (49) and You and Lee (60) but contradicted by Song and Oh (64). This indicates that even the presence or absence of other bystanders did not consistently predict the way in which individuals will react to an incident of cyber-aggression, as some bystanders were more constructive in private situations where no or very few bystanders were present (64) while others were more likely to remain passive in a similar situation (42), and some others were passive in the presence, not absence of other bystanders (60). Therefore, it seems likely that a larger crowd, in some situations would increase the social pressure an individual experiences to behave in socially acceptable ways (42), while it encourages the diffusion of responsibility in others (60), and that other contextual factors should be taken into account. For instance, individuals with a close relationship with the aggressor were more likely to remain passive in the absence of other cyber-bystanders but were more likely to behave constructively in the presence of other bystanders (64), possibly because they found safety in numbers.
Lastly, although this phenomenon is one that occurs in cyber-space, there were very few papers which identified or acknowledged the influence of the characteristics of cyber-space and computer mediated communication on leading individuals to resort to negative cyber-bystander behavior. From what was reported, however, it can be gathered that the lack of context cues can complicate matters relating to the interpretation of the event and subsequently one's response as a cyber-bystander. Additionally, it seems as though individuals have the tendency to perceive cyber-aggression as being less severe than face-to-face aggression, solely due to the absence of physical aggression in the former, suggesting that there is a lack of awareness regarding the effects of cyber-aggression due to these differences. Moreover, asynchronicity which can cause a delay between when the incident had occurred and when the cyber-bystander witnesses it may leave individuals believing that there is no other response other than ignoring the incident as there is neither a need nor value in intervening in a situation that has already passed and might have been resolved (43). Besides that, in You and Lee (60), it was discussed that individuals are less likely to choose more constructive cyber-bystanders behavior, likely due to the fact that they fear negative judgments a lot less in such situations. Other than that, there seems to be very little empirical evidence and the discussion it fueled, regarding the ways in which the characteristics of cyberspace and the pattern of communication in such platforms influence negative cyber-bystander behavior.
Based on the review of demographic factors associated with the participants included in the studies reviewed, it is evident that the focus was largely on the pre-teen and adolescent population, aged between 12 and 16, with only six out of 27 studies addressing the adult population, and even fewer studies which included children ages 8–10. Hence, future studies should consider investigating negative cyber-bystander behavior among the adult population as well as well as younger children considering that the age at which individuals are exposed to the internet and technological devices seems to be decreasing. Moreover, various factors such as empathy, technological savviness, the need for external guidance and others might manifest differently among different age groups.
Secondly, most of the studies were carried out in the United States of America (USA) or European countries with very few addressing countries from other regions with differing cultures and norms. Given that these differences can subsequently influence thought and behavioral outcomes, it seems necessary to widen the scope of the study in terms of geographical locations, to account for cross-cultural differences. Additionally, most studies were cross-sectional surveys, more longitudinal studies as well experimental designs should be explored. In addition to that, there was a great benefit in collecting qualitative data from participants, hence, this practice should be encouraged even in the smallest ways in future studies.
Future studies could also go beyond the biological binary when discussion gender differences and account for more personal differences. The differences can include factors such as normative beliefs associated with gender, particularly with regards to aggression, empathy, outcome expectations, feelings of guilt and shame associated with negative cyber-bystander behavior, and the like. Moreover, difference in personality traits may also be worth exploring to identify variables that directly or indirectly influence an individual's choice of negative cyber-bystander behavior on a more personal level. In addition to that, factors such as moral disengagement, on the other hand, could potentially prove to be a vital moderating factor in future studies.
Future studies could also benefit from a more uniform way of measuring different types of cyber-bystander behavior to ensure some consistency across different studies. Most importantly, as identified above, more studies should address the ways in which the characteristics of cyberspace as well as computer mediated communication would influence an individual's decision to resort to negative cyber-bystander behavior. Various existing models and theories such as the online disinhibition theory by Suler (66) and the Barlett and Gentile Cyberbullying Model would be of use in doing so as they do indeed support findings presented by studies such as You and Lee (60) and Van Cleemput et al. (43).
There are a number of limitations and shortcomings in several aspects of the study ranging from the literature search, data analysis to the determination of the quality of the study. Firstly, although the choice of keywords used, as well as the strict inclusion criteria were selected and employed in order to ensure that only relevant data would be retrieved, it could have inadvertently excluded other significant literature which could have further enriched the current review. For instance, while the peer-reviewed articles published in the past ten (10) years might be able to better capture dynamics of the phenomenon in the current cyber landscape, it is likely that literature published prior to the past decade might contain important information that the current review may have benefitted from. The omission of gray literature would have impacted the review in similar ways. Moreover, limiting the literature search to five databases might have lead to the omission of important literature that could be found on other online databases or registers. Lastly, it should be taken into account the screening process could have been impacted by human errors. However, the review has managed to fulfill the aim of compiling, presenting and discussing important findings that provide a simple overview of negative cyber-bystander behavior.
Moreover, the reproducibility or the replicability of the search can be affected by things out of the control of the authors, such as the changes made in the literature databases in terms of search retrieval systems, the addition or elimination of journals or articles and etc. (67). Additionally, the quality of the review is difficult to assess given that the extraction and analysis of data could be influenced by bias as they rely on the reviewers' and authors' interpretations and ideas, and the fact that the review consists of studies of varying designs (68).
Despite the flaws, the review, like any other has managed to compile, and present a comprehensive set of literature and discussion highlighting factors associated with negative bystander behavior, in addition to the possible interactions between them, as well as possible gaps to address in the future. Moreover, the review can be used as a point of reference through which further questions can be identified, in order to extend the scope of research.
Through the synthesis of literature included in this review, it is evident that is not only crucial to create an environment that facilitates and encourages positive bystander behavior, but also an environment that discourages and disincentivizes negative bystander behavior. This is especially true in the case of aggressive bystander behavior, as it would aid in not just preventing the reinforcement and/or exacerbation of an act of aggression by primary aggressors but could possibly prevent bystanders' potential future participation in acts of cyber-aggression. Moreover, the review indicates the necessity to take into consideration and further study in detail the interaction between multiple variables, as well as contextual factors, as a catalyst for negative bystander behavior as many of the studies have either theorized or proven that these are relevant in uncovering a clearer picture regarding this phenomenon. Lastly, the influence of technology on human behavior and interaction, in addition to the role of personal characteristics rather than a categorical approach to demographic differences may also prove to be useful directions for future studies to take.
The original contributions presented in the study are included in the article/Supplementary material, further inquiries can be directed to the corresponding author/s.
The study and its design were conceptualized by SJ and MK. The literature search was carried out in two steps, whereby the preliminary screening was conducted by SJ and the subsequent screening to select studies to be included was a joint effort between SJ, MK, SM, JK, and AA. Data organization and analysis, in addition to the writing of the first draft was carried out by SJ under the direction and supervision of MK. Lastly, the collective effort and agreement of all authors were involved in the process of proofreading and editing of subsequent drafts, as well as the approval of the final submitted manuscript.
We extend our sincere gratitude to the Faculty of Social Sciences and Humanities, Universiti Kebangsaan Malaysia, for sponsoring the APC of this manuscript. Additionally, we would also like to thank Dr. Isa Naina Mohamed for their valuable feedback and guidance during the process of writing the manuscript.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fpubh.2022.965017/full#supplementary-material
1. Alonzo R, Hussain J, Stranges S, Anderson KK. Interplay between social media use, sleep quality, and mental health in youth: A systematic review. Sleep Med Rev. (2021) 56:101414. doi: 10.1016/j.smrv.2020.101414
2. Güzel N, Kahveci I, Solak N, Cömert M, Turan FN. Internet addiction and its impact on physical health. Turkish Med Student J. (2018) 5:32–6. doi: 10.4274/tmsj.2018.05.03.0002
3. Rathakrishnan B, Singh SSB, Kamaluddin MR, Yahaya A, Nasir MAM, Ibrahim F, et al. Smartphone addiction and sleep quality on academic performance of university students: An exploratory research. Int J Environ Res Public Health. (2021) 18:8291. doi: 10.3390/ijerph18168291
4. Tateno M, Teo AR, Ukai W, Kanazawa J, Katsuki R, Kubo H, et al. Internet addiction, smartphone addiction, and hikikomori trait in japanese young adult: Social isolation and social network. Front Psychiatry. (2019) 10:1–11. doi: 10.3389/fpsyt.2019.00455
5. Lin L, Liu J, Cao X, Wen S, Xu J, Xue Z, et al. Internet addiction mediates the association between cyber victimization and psychological and physical symptoms:moderation by physical exercise. BMC Psychiatry. (2020) 20:1–8. doi: 10.1186/s12888-020-02548-6
6. Craig W, Boniel-Nissim M, King N, Walsh SD, Boer M, Donnelly PD, et al. Social media use and cyber-bullying: a cross-national analysis of young people in 42 countries. J Adolesc Heal. (2020) 66:S100–8. doi: 10.1016/j.jadohealth.2020.03.006
7. Jenaro C, Flores N, Frías CP. Systematic review of empirical studies on cyberbullying in adults: what we know and what we should investigate. Aggress Violent Behav. (2017) 38:113–22. doi: 10.1016/j.avb.2017.12.003
8. Guo SA. Meta-analysis of the predictors of cyberbullying perpetration and victimization. Psychol Sch. (2016) 53:432–53. doi: 10.1002/pits.21914
9. Hua TK, Hwa NSH, Chong ST. Cyberbullying victimization and cyberbullying perpetration with self-esteem as the moderator. Int J Recent Technol Eng. (2019) 8:88–92. doi: 10.35940/ijrte.B1014.0982S1019
10. Zhu C, Huang S, Evans R, Zhang W. Cyberbullying among adolescents and children: A comprehensive review of the global situation, risk factors, and preventive measures. Front Public Health. (2021) 9:1–12. doi: 10.3389/fpubh.2021.634909
11. Sabramani V, Idris IB, Ismail H, Nadarajaw T, Zakaria E, Kamaluddin MR. Bullying and its associated individual, peer, family and school factors: Evidence from Malaysian National Secondary School Students. Int J Environ Res Public Health. (2021) 18:7208. doi: 10.3390/ijerph18137208
12. Dennehy R, Meaney S, Cronin M, Arensman E. The psychosocial impacts of cybervictimisation and barriers to seeking social support: Young people's perspectives. Child Youth Serv Rev. (2021) 111:104872. doi: 10.1016/j.childyouth.2020.104872
13. Balakrishnan V, Norman AA. Psychological motives of cyberbullying among Malaysian young adults. Asia Pacific J Soc Work Dev. (2020) 30:181–94. doi: 10.1080/02185385.2020.1772101
14. Del Rey R, Casas JA, Ortega-Ruiz R, Schultze-Krumbholz A, Scheithauer H, Smith P, et al. Structural validation and cross-cultural robustness of the European Cyberbullying Intervention Project Questionnaire. Comput Human Behav. (2015) 50:141–7. doi: 10.1016/j.chb.2015.03.065
15. Ahmad Ghazali AH, Abu Samah A, Omar SZ, Abdullah H, Ahmad A, Mohamed Shaffril HA, et al. Development and validation of an instrument measuring cyberbullying among Malaysian youths. J Cogn Sci Hum Dev. (2019) 5:78–91. doi: 10.33736/jcshd.1921.2019
16. Aizenkot D, Kashy-Rosenbaum G. The effectiveness of safe surfing, an anti-cyberbullying intervention program in reducing online and offline bullying and improving perceived popularity and self-esteem. Cyberpsychology. (2020) 14:1–23. doi: 10.5817/CP2020-3-6
17. Gaffney H, Farrington DP, Espelage DL, Ttofi MM. Are cyberbullying intervention and prevention programs effective? A systematic and meta-analytical review. Aggress Violent Behav. (2019) 45:134–53. doi: 10.1016/j.avb.2018.07.002
18. Fortunatus M, Anthony P, Charters S. Combining textual features to detect cyberbullying in social media posts. Proc Comput Sci. (2020) 176:612–21. doi: 10.1016/j.procs.2020.08.063
19. Ali WNHW, Mohd M, Fauzi F. Identification of profane words in cyberbullying incidents within social networks. J Infm Sci Theor Pract. (2021) 9:24–34. doi: 10.1633/JISTaP.2021.9.1.2
20. Hua TK, So'od SMM, Hamid BA. Communicating insults in cyberbullying. Search. (2019) 11:91−109. Available online at: https://fslmjournals.taylors.edu.my/communicating-insults-in-cyberbullying/
21. Grigg DW. Cyber-aggression: definition and concept of cyberbullying. Aust J Guid Couns. (2010) 20:143–56. doi: 10.1375/ajgc.20.2.143
22. Corcoran L, Guckin C, Prentice G. Cyberbullying or cyber aggression?: a review of existing definitions of cyber-based peer-to-peer aggression. Societies. (2015) 5:245–55. doi: 10.3390/soc5020245
23. Hyland JM, Hyland PK, Corcoran L. Cyber aggression and cyberbullying: Widening the net. Adv Sci Technol Secur Appl. (2018) 5:245–55. doi: 10.1007/978-3-319-97181-0_3
24. Shultz E, Heilman R, Hart KJ. Cyber-bullying: An exploration of bystander behavior and motivation. Cyberpsychology. (2014) 8. doi: 10.5817/CP2014-4-3
25. DeSmet A, De Bourdeaudhuij I, Walrave M, Vandebosch H. Associations between bystander reactions to cyberbullying and victims' emotional experiences and mental health. Cyberpsychol. Behav Soc Netw. (2019) 22:648–56. doi: 10.1089/cyber.2019.0031
26. Wright MF, Wachs S, Harper BD. The moderation of empathy in the longitudinal association between witnessing cyberbullying, depression, and anxiety. Cyberpsychology. (2018) 12. doi: 10.5817/CP2018-4-6
27. Pabian S, Vandebosch H, Poels K, Van Cleemput K, Bastiaensens S. Exposure to cyberbullying as a bystander: an investigation of desensitization effects among early adolescents. Comput Human Behav. (2016) 62:480–7. doi: 10.1016/j.chb.2016.04.022
28. Bastiaensens S, Pabian S, Vandebosch H, Poels K, Van Cleemput K, Desmet A. From normative influence to social pressure : how relevant others affect whether bystanders join in cyberbullying Soc Dev. (2016) 25:193–211. doi: 10.1111/sode.12134
29. Page MJ, McKenzie JE, Bossuyt PM, Boutron I, Hoffmann TC, Mulrow CD, et al. The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. BMJ. (2021) 372:n71. doi: 10.1136/bmj.n71
30. Desmet A, Bastiaensens S, Cleemput Van K, Poels K, Vandebosch H. The efficacy of the Friendly Attac serious digital game to promote prosocial bystander behavior in cyberbullying among young adolescents: a cluster-randomized controlled trial. Comput Human Behav. (2018) 78:336–47. doi: 10.1016/j.chb.2017.10.011
31. Bastiaensens S, Vandebosch H, Poels K, Van Cleemput K, DeSmet A, De Bourdeaudhuij I. Cyberbullying on social network sites: An experimental study into bystanders' behavioural intentions to help the victim or reinforce the bully. Comput Hum Behav. (2014) 31:259–71. doi: 10.1016/j.chb.2013.10.036
32. Bastiaensens S, Vandebosch H, Poels K, Van Cleemput K, Desmet A, Bourdeaudhuij D, et al. I afford to help? How affordances of communication modalities guide bystanders' helping intentions towards harassment on social network sites. Behav Inf Technol. (2015) 34:425–35. doi: 10.1080/0144929X.2014.983979
33. Liu C-H, Yin X-R, Huang P-S. Cyberbullying: Effect of emergency perception on the helping tendencies of bystanders. Telemat Informatics. (2021) 62:101627. doi: 10.1016/j.tele.2021.101627
34. Jungert T, Holm K, Iotti NO, Longobardi C. Profiles of bystanders ' motivation to defend school bully victims from a self - determination perspective. Aggress Behav. (2020) 47:78–88. doi: 10.1002/ab.21929
35. Jungert T, Perrin S. Trait anxiety and bystander motivation to defend victims of school bullying. J Adolesc. (2019) 77:1–10. doi: 10.1016/j.adolescence.2019.10.001
36. Ouvrein G, Pabian S, Machimbarrena JM, Erreygers S, De Backer CJ, Vandebosch H. Setting a bad example: Peer, parental, and celebrity norms predict celebrity bashing. J Early Adolesc. (2018) 39:937–61. doi: 10.1177/0272431618797010
37. Law DM, Shapka JD, Hymel S, Olson BF, Waterhouse T. The changing face of bullying : an empirical comparison between traditional and internet bullying and victimization. Comput Human Behav. (2012) 28:226–32. doi: 10.1016/j.chb.2011.09.004
38. Royen KV, Poels K, Vandebosch H, Zaman B. Think twice to be nice? A user experience study on a reflective interface to reduce cyber harassment on social networking sites. Int J Bully Prevent. (2021) 4:23–34. doi: 10.1007/s42380-021-00101-x
39. Vandoninck S, d'Haenens, L. Children's online coping strategies: Rethinking coping typologies in a risk-specific approach. J Adolesc. (2015) 45:225–36. doi: 10.1016/j.adolescence.2015.10.007
40. Schultze-Krumbholz A, Zagorscak P, Hess M, Scheithauer H. The influence of school climate and empathy on cyberbystanders' intention to assist or Defend in cyberbullying. Int J Bully Prevent. (2019) 2:16–28. doi: 10.1007/s42380-019-00040-8
41. Erreygers S, Pabian S, Vandebosch H, Baillien E. Helping behavior among adolescent bystanders of cyberbullying: The role of impulsivity. Learn Individ Differ. (2016) 48:61–7. doi: 10.1016/j.lindif.2016.03.003
42. Barlińska J, Szuster A, Winiewski M. Cyberbullying among adolescent bystanders: Role of the communication medium, form of violence, and empathy. J Commun Appl Soc Psychol. (2012) 23:37–51. doi: 10.1002/casp.2137
43. Van Cleemput K, Vandebosch H, Pabian S. Personal characteristics and contextual factors that determine “helping,” “joining in,” and “doing nothing” when witnessing cyberbullying. Aggress Behav. (2014) 40:383–96. doi: 10.1002/ab.21534
44. Panumaporn J, Hongsanguansri S, Atsariyasing W, et al. Bystanders' behaviours and associated factors in cyberbullying. Gen Psychiatry. (2020) 33:e100187. doi: 10.1136/gpsych-2019-100187
45. Wang S, Kim KJ. Effects of victimization experience, gender, and empathic distress on bystanders' intervening behavior in cyberbullying. Soc Sci J. (2021) 1–10. doi: 10.1080/03623319.2020.1861826
46. Machackova H, Dedkova L, Sevcikova A, Cerna A. Bystanders' supportive and passive responses to cyberaggression. J Sch Violence. (2018) 17:99–110. doi: 10.1080/15388220.2016.1222499
47. Schultze-Krumbholz A, Hess M, Pfetsch J, Scheithauer H. Who is involved in cyberbullying? Latent class analysis of cyberbullying roles and their associations with aggression, self-esteem, and empathy. Cyberpsychology. (2018) 12. doi: 10.5817/CP2018-4-2
48. Balakrishnan V. Actions, emotional reactions and cyberbullying – From the lens of bullies, victims, bully-victims and bystanders among Malaysian young adults. Telemat Informat. (2018) 35:1190–200. doi: 10.1016/j.tele.2018.02.002
49. Chan NN, Ahrumugam P, Scheithauer H, Schultze-Krumbholz A, Ooi PBA. hermeneutic phenomenological study of students' and school counsellors' “lived experiences” of cyberbullying and bullying. Comput Educ. (2020) 146:103755. doi: 10.1016/j.compedu.2019.103755
50. Bauman S, Yoon J, Iurino C, Hackett L. Experiences of adolescent witnesses to peer victimization: the bystander effect. (2020) 80:1–14. doi: 10.1016/j.jsp.2020.03.002
51. Olenik-Shemesh D, Heiman T, Eden S. Bystanders' behavior in cyberbullying episodes: active and passive patterns in the context of personal–socio-emotional factors. J Interpers Violence. (2017) 32:23–48. doi: 10.1177/0886260515585531
52. DeSmet A, Bastiaensens S, Van Cleemput K, Poels K, Vandebosch H, Cardon G, et al. whether to look after them, to like it, or leave it: a multidimensional analysis of predictors of positive and negative bystander behavior in cyberbullying among adolescents. Comput Human Behav. (2016) 57:398–415. doi: 10.1016/j.chb.2015.12.051
53. Machackova H, Pfetsch J. Bystanders ' responses to offline bullying and cyberbullying : the role of empathy and normative beliefs about aggression. Scand J Psychol. (2016) 57:169–76. doi: 10.1111/sjop.12277
54. Bussey K, Luo A, Fitzpatrick S, Allison K. Defending victims of cyberbullying : the role of self-efficacy and moral disengagement. J Sch Psychol. (2020) 78:1–12. doi: 10.1016/j.jsp.2019.11.006
55. Gahagan K, Vaterlaus JM, Frost LR. College student cyberbullying on social networking sites : conceptualization, prevalence, and perceived bystander responsibility. Comput Human Behav. (2016) 55:1097–105. doi: 10.1016/j.chb.2015.11.019
56. Bandura A. Moral Disengagement: The Encyclopedia of Peace Psychology. Hoboken, NJ: Blackwell Publishing Ltd. (2011). doi: 10.1002/9780470672532.wbepp165
57. Luo A, Bussey K. The selectivity of moral disengagement in defenders of cyberbullying : contextual moral disengagement. Comput Human Behav. (2019) 93:318–25. doi: 10.1016/j.chb.2018.12.038
58. Tong D, Talwar V. Students' moral emotions and judgments of cyberbullying: The influence of previous cyberbullying experiences. Curr Psychol. (2020) 41:4200–9. doi: 10.1007/s12144-020-00916-9
59. Patterson LJ, Allan A, Cross D. Adolescent bystanders ' perspectives of aggression in the online versus school environments *. J Adolesc. (2016) 49:60–7. doi: 10.1016/j.adolescence.2016.02.003
60. You L, Lee YH. The bystander effect in cyberbullying on social network sites: anonymity, group size, and intervention intentions. Telemat Informatics. (2019) 45:101284. doi: 10.1016/j.tele.2019.101284
61. Koehler C, Weber M. “Do I really need to help?!” Perceived severity of cyberbullying, victim blaming,and bystanders' willingness to help the victim. Cyberpsychology. (2018) 12. doi: 10.5817/CP2018-4-4
62. Latané B, Darley JM. The Unresponsive Bystander: Why Doesn't He Help? New York, NY: Appleton-Century- Croft (1970).
63. Patterson LJ, Allan A, Cross D. Adolescent perceptions of bystanders' responses to cyberbullying. New Media Soc. (2017) 19:366–83. doi: 10.1177/1461444815606369
64. Song J, Oh I. Factors influencing bystanders' behavioral reactions in cyberbullying situations. Comput Human Behav. (2018) 78:273–82. doi: 10.1016/j.chb.2017.10.008
65. Levy M, Sela-Shayovitz R. Cyberaggression: The effect of parental monitoring on bystander roles. Int J Child Youth Fam Stud. (2020) 11:13–36. doi: 10.18357/ijcyfs114.2202019986
66. Suler J. The online disinhibition effect. Cyberpsychol Behav. (2004) 7:321–6. doi: 10.1089/1094931041291295
67. Cram WA, Templier M, Paré G. (Re)considering the concept of literature review reproducibility. J Assoc Inf Syst. (2020) 21:1103–14. doi: 10.17705/1jais.00630
68. Costa-Cordella S, Arevalo-Romero C, Parada FJ, Rossi A. Social support and cognition: a systematic review. Front Psychol. (2021) 12:1–22. doi: 10.3389/fpsyg.2021.637060
Keywords: bystander intervention, systematic review, cyberaggression, cyberbullying, cyber-bystander
Citation: Jeyagobi S, Munusamy S, Kamaluddin MR, Ahmad Badayai AR and Kumar J (2022) Factors influencing negative cyber-bystander behavior: A systematic literature review. Front. Public Health 10:965017. doi: 10.3389/fpubh.2022.965017
Received: 23 June 2022; Accepted: 06 September 2022;
Published: 03 October 2022.
Edited by:
Chao Guo, Peking University, ChinaCopyright © 2022 Jeyagobi, Munusamy, Kamaluddin, Ahmad Badayai and Kumar. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Mohammad Rahim Kamaluddin, cmFoaW1rQHVrbS5lZHUubXk=
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.