
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Public Health , 19 November 2021
Sec. Public Health Policy
Volume 9 - 2021 | https://doi.org/10.3389/fpubh.2021.752112
This article is part of the Research Topic Key nutrition and hydration insights for Public Health and Policy View all 26 articles
Food fraud not only exacerbates human public health risks but also threatens the business development of food and related industries. Therefore, how to curb food fraud effectively becomes a crucial issue for governments, industries, and consumers. Previous studies have demonstrated that enterprise food fraud is subject to joint influences of factor at various hierarchical levels within a complex system of stakeholders. To address enterprise food fraud, it is necessary to identify the key such factors and elucidate the functional mechanisms, as well as systematic analysis of the interrelationships among clusters and factors. Hence, we grounded on a social co-governance perspective and investigated the food fraud key influencing factors and their interrelationships in an emerging food market – China, by using the DEMATEL-based analytic network process (DANP). Results showed that the identified key cluster was government regulation, social governance, and detection techniques. Four other key factors were also identified, including government regulatory capability and penalty intensity, expected economic benefits, maturity of market reputation mechanism, and transparency of supply chain. Policy implications from the social co-governance perspective for China and similar economies are discussed finally.
Food fraud is a collective term used to encompass the deliberate substitution, addition, tampering, or misrepresentation of food, food ingredients, or food packaging or false/misleading statements made about a product for economic gain (1–5). With the escalation in incidents, scope, and harm, research on food fraud has increased in recent years (6, 7). In recent years, food fraud has become a serious and challenging issue for worldwide society (8–10). Food fraud grows obstacles for food safety regulation and the food industry (11, 12). It also increases human health risks (13), hinders development of the food market/industries, and causes trust issues among stakeholders, including food producers and dealers, consumers, trading partners, and regulatory authorities (14). Food fraud can also be more difficult to expose and can carry greater threat than conventional food safety issues (15).
For example, one of the most notorious food fraud cases worldwide was the discovery in 2008 of the illegal addition of melamine, an industrial raw material, to infant milk powder in China, which negatively impacted 300,000 infants, six of whom died (16, 17). The company in question is a large enterprise group with a history of over 50 years and total assets of nearly RMB 2 billion (as of the end of 2007). In order to reduce costs, the enterprise involved used water and melamine in the milk to counterfeit. This is an example of food fraud as 'commercial enterprise crime' carried out by producers in the food supply chain. The discovery in 2013 of the addition of horsemeat to certain products in many European countries is another example of significant food fraud (18). Such incidents have led governments and relevant organizations in various countries to step up food safety regulation (19). For instance, In China, the government has repeatedly restructured its food safety regulatory bodies, reformed regulatory rules and practices, and promulgated the highly stringent Law on Food Safety protocols, which are targeted at effective regulation (20, 21).
Previous food safety regulations, however, are not designed to curb deliberate misconduct and are therefore not effective at addressing intentional food fraud (22, 23). Existing systems (and research on them) only focused on the compliance of food producers with food safety control systems, particularly the Hazard Analysis Critical Control Point (HACCP) system, to minimize the microbial, chemical, and physical risks incurred during food production (24, 25). Food fraud is a deliberate behavior of a food producer (generally) and will include attempts to evade supervision and regulation (11). Lord et al. (26) emphasizes that food fraud constitutes a crime and generally occurs along the supply chain of ordinary food, similar to other criminal activities.
Existing food fraud research is heavily weighted toward food science, packaging and labeling, and legal areas of knowledge discovery (27). Enterprise food fraud is a business behavior performed under certain conditions. Moving forward, this requires a business decision-making perspective to further study the problem of food fraud in food companies (13). So far, Van Ruth et al. (23), Levi et al. (28), Meerza et al. (29–31) and other studies have initially discussed how various factors affect the fraud behavior of food companies. We have a clearer understanding of the fraudulent decision-making behavior of food companies and laid the foundation. For instance, Meerza et al. (31) studied the Optimal Policy Response to Food Fraud and found that under different circumstances, strict monitoring and enforcement and increased certification costs will have different effects on companies' food fraud behaviors. However, the existing research only analyzes the influence of various factors on the fraud behavior of food companies. So, among these factors, which ones are the key factors? What are their interrelationships between factors? Existing research ignores these important issues. According to our knowledge, there is currently no literature report that identifies the key factors that affect the food fraud behavior of companies and analyzes the internal relationships between the factors.
In addition, enterprise food fraud is not only influenced by the action of certain individual factors, but also joint, organizational actions of a complicated system of clusters (cluster is a factor sets formed by different factors of the same class) at different hierarchical levels and among factors within a cluster (32). However, studies on the correlations among clusters and factors that motivate enterprise food fraud and how such clusters and factors jointly influence enterprise food fraud remain limited.
Heeding to such thoughts of the gaps in the literature, we argue that studies need to explore key factors of food fraud from more systematic and holistic theoretical lens and methodology, such as the social co-governance perspective and the DEMATEL-based analytic network process (DANP) method proposed here. Social co-governance theory for food safety emphasizes on “social participation for the collective pursuit of food safety” (33). As compared with traditional governance approaches for food issues, social co-governance stresses more on the wide and collective efforts from a diverse set of stakeholders, which ensures better informational transparency/symmetry, risk and cost sharing capacity, and resource richness (34). Such relationship also stresses social contract beyond economic ones (35). For methodological concern, Huang et al. (36) and Wu et al. (37) found the DANP to be an effective approach for studying the correlations among factors and (more usefully) the inter- and intra-clusters (factor sets) relationships at different hierarchical levels.
From the analysis of the development history of food fraud, the problem of food counterfeiting exists in any country in the world with varying degrees. And food fraud often occurs in the highly competitive food market. China has a highly competitive and relatively mature food market, which is similar to the food markets in the United States and the European Union. However, about 50% of food safety incidents in China are caused by food fraud, which is the result of the combination of complex factors such as the huge return from food consumption market, the large number of food enterprises with insufficient integrity, and the weakness of food supervision in China, etc., which might be different from the United States and the European Union but similar to most developing countries. Therefore, using China as the research object to study food fraud is reasonably significant and is of positive value in understanding the causes of food fraud/counterfeiting in similar economies' contexts with potential measures that might be taken by the whole society.
Information asymmetry between producers and consumers creates an adverse choice for oversupply of low-quality, unsafe products (38, 39). Traditional food regulation is dominated by the command-control type of intervention. In most developed countries, food safety regulation has focused on the imposition of standards that specify how food products should be produced and/or their final safety level (40). However, since the 1990s, food operators have frequently been given more responsibility to monitor food safety (41). For example, the UK Food Safety Act (1990) encourages food companies to establish private food safety control measures to ensure the quality and safety of food produced and sold (42). The EU Food Hygiene Regulations, implemented on January 1, 2006, require all food producers and operators to have food safety control measures to prove that they are managing food safety in their businesses. In United States, food safety control measures, such as HACCP, become a category of food safety regulation (43).
Food risks may be caused by malpractice of suppliers who exploit the fact that their production processes and resulting product properties cannot be directly observed by buyers (44). However, current food safety regulations aim to deal with unintentional food safety incidents such as microorganisms, physics and chemistry, rather than deliberately deceiving people. Besides, the design of food safety control measures from a production view could not take into account deliberate fraud. So, malicious intent is the blind spot of current food safety law (2). Food fraud often occurs outside the authorized supply chain and usually involves the addition of unsupervised substances (13). The fraudsters can design and manufacture adulterated materials based on the nature of the adulterated product, thereby escaping existing food safety controls (45). Therefore, existing food safety control measures are not effective against food fraud (22, 23).
Food fraud is crime-committed by producers and operators in the food supply chain to make full use of the opportunities of crime (26). In order to successfully implement food fraud, fraudsters actively seek for the opportunity and actively avoid detection using their technical expertise (46). In terms of the nature of food fraud, the collapse of the security of the entire food supply chain depends on a single factor, the criminal (45). Since food fraud is caused by conscious intelligent human opponents, food fraud is a crime and the crime prevention related theories have been applied in research (3, 4, 47, 48). The routine activity theory sees crime as the outcome of the convergence in time and place of (1) motivated offenders and (2) suitable targets in (3) the absence of capable guardians (23). Food fraud and other types of corporate crime have similar characteristics. In accordance with the routine activity theory, it is necessary to study the factors affecting the food fraud vulnerability from three aspects: opportunities, motivations and control measures, and develop a food fraud vulnerability assessment tool (23). From the view point of the Criminology, food fraud vulnerability assessment tools should be used, identify potential weaknesses of food systems, and to effectively prevent food fraud (49, 50). Nonetheless, if (as the present study does) the food fraud is defined as a commercial enterprise crime, then we need to extend such a crime prevention theory to designing organizational and institutional prevention strategies to enhance the integrity of the food system (26).
Based on the reviews above, we found that the production viewpoint does not take into account the deliberate characteristics of food fraud, so it is ineffective to control food fraud. Although the criminological viewpoint makes up for the above shortcomings of production viewpoint, and places its emphases on preventing food fraud through prevention. However, under the background of rapid development of food production technology and increasingly internationalization and complexity of food supply chain, it is far from enough to rely solely on the strength and resources of enterprises and governments to prevent food fraud. With the purpose to reduce costs and improve the effectiveness of food safety regulation, the new collaborations between public authorities and food operators in monitoring food safety has been developed (34, 40, 51). But, establishing a better food economy with sustainable development needs the efforts of all stakeholders and the integration of relevant resources. Involvement of all stakeholders to work together helps to improve the practicability of decision-making and reduce the burden on participants (33). Therefore, food safety risk governance must introduce the participation of consumers, non-governmental organizations and other social forces to guide the whole society to co-govern together (52).
In theory, social co-governance is rooted in the theory of cooperative governance. In the late 20th century, the role orientation of “super nanny” of the government in western countries' welfare systems resulted in many disadvantages, such as expansion of functions, overstaffed institutions and inefficiency, which caused public discontent due to inadequate governance of environmental protection, market monopoly, food safety and other issues (33). In order to solve the problems of fragmentation and decentralization of government governance, the theory of social governance, which emphasizes the multi-dispersed subjects to reach a multilateral interactive cooperative network, began to emerge at the end of the 20th century (53). As an important stakeholder of food safety, the media, employees, consumers and other social entities can also play an important role in preventing food safety risks. Social co-governance of food safety is a concept aimed at strengthening the partnership among the government, enterprises and social entities. The concept of social co-governance has become a practice in many countries. In the EU, governments, enterprises, social organizations, and citizens are actively involved in food safety governance. In China, the Food Safety Law of the People's Republic of China on October 1, 2015 established social co-governance as an important criterion for food safety risk governance. According to this, both theory and practice require that the discussion of the governance of food fraud be extended to the main constituents of a society.
In sum, the governance of food fraud with production and criminological views is mainly from the two main entities of the enterprise and the government, respectively. This paper expands the research scope to a pluralistic social groups (i.e., enterprise, government, consumers, and other stakeholders) based on the theory of social co-governance. A major reason is that the social co-governance theory suggests that stakeholders such as the consumers, social organizations or the other relatively neglected actors can also play an important role in ensuring food safety and in preventing fraud, posing a powerful complement to government governance and corporate self-discipline (33). To this end, based on our review of the perspective of social co-governance, this paper proposes five dimensions and 12 factors that may affect the corporate food fraud behavior (Table 1).
Enterprise food fraud is closely related to business scale, business ethics, and awareness of social responsibilities.
Enterprise scale refers to the number of employees and the size of assets. Though an enterprise may engage in food fraud regardless of its scale (47), a food enterprise of smaller scale has higher risk of deliberate crime as it may choose not to recall sold products suspected of authenticity or safety problems and may ignore consumer grievances (54). For instance, Wu et al. (55) reported that small-scale enterprises are more inclined to abuse food additives. Levi et al. (28) also revealed that smaller farms are more vulnerable to risks and may resort to food fraud when facing quality uncertainty or price pressure.
Business ethics refers to the integrity and ethical atmosphere within the enterprise. Business ethics are basic ethical codes that an enterprise complies with in all production and trade activities (56). Food fraud is unethical conduct (57), which is often closely related to business culture and the decision-maker's failure to stand behind the ethical bottom line (58). Business ethics is an important risk factor for corporate financial fraud (59, 60). Similarly, business ethics are key cultural factors leading to food fraud vulnerability (23). Enhancing an enterprise's business ethics imposes a positive influence on the enterprise from a cultural perspective and encourages the business to refrain from food fraud (61).
Manager awareness refers to the attitude of managers toward the social responsibility that the enterprise should take. Social responsibilities are fundamental duties related to environmental protection, justice, and equality that an enterprise assumes while striving for maximum benefits (62). Furthermore, ensuring food safety is the most important social responsibility of a food enterprise (63). Though most enterprises understand social responsibilities of food safety for the sake of a good public image (64), the concept of social responsibility originated and evolved to promote compliance with ethics and legislation among increasing cases of non-compliance (65). Illegal conduct will decrease if an enterprise strictly adheres to its social responsibilities. A manager's awareness of these social responsibilities also influences both willingness and performance. The stronger the manager's awareness of social responsibilities, the more responsible an enterprise is in regard to food safety and food fraud misconduct (66).
Food fraud is intrinsically subject to expected economic benefits and technical hardness.
Although food fraud may require an input of resources, it will also undoubtedly generate benefits (67). This is why fraudsters choose to misbehave in violation of social ethics and even with the risk of punishment (68, 69). For example, Levi et al. (28) found that enterprise food fraud aims to maximize the perceived quality of low-quality products to achieve higher economic benefits. Bitzios et al. (70) also determined that foods bearing geographical indication (GI) labels usually resulted in better quality foods and higher consumer acknowledgment; furthermore, when substantial economic benefits are expected from counterfeiting ordinary food into a GI product, the enterprise exhibits a higher probability of committing food fraud.
An enterprise will be more inclined to commit fraud when it is technically easy (71). The technical hardness of fraud can be measured from both knowledge and substance aspects. On the knowledge side, a fraudster is usually a technical expert with rich knowledge of production and knows how to perform the fraud and how to evade capture (46). Furthermore, it is relatively easy to acquire the knowledge and techniques necessary for food fraud (23). On the substance side, most food fraud does not necessitate complicated equipment or other substances and the required additives are often easily available (72). For example, the infant milk powder incident in China resulted from adding melamine to milk to conceal that it had been diluted with water (16). Melamine is an ordinary and easily accessible chemical and its addition to the milk did not require any complicated techniques.
Food fraud is subject to impact from government regulatory capability and penalty intensity, social supervision, and utility of detection techniques and methodologies.
Food fraud rampancy is closely related to inefficient government regulation (73). In China, the deficiency in food safety supervision and control, as well as the fragmentation of regulatory agencies, has resulted in poor regulation (47) as well as increased opportunities for fraudulent behavior. In addition, the government sampling inspection system is based on conventional empirical methodologies, information, and knowledge (i.e., what additives may be supplemented to food), and often cannot identify fraud based on the latest developments (74, 75). Furthermore, there is no punitive “joint examination” on similar enterprises. Therefore, the food quality sampling inspection system itself does not effectively deter food fraudsters (76). In addition, relatively moderate punishment coupled with high expected economic benefits does not constitute an effective deterrent, thus resulting in the high risk of food fraud (54).
Media, consumers, employees, and social organizations can help alleviate food fraud (33). For example, Peng et al. (77) found that food safety scandals disclosed by the media can lead to a decline in sales and damage to the brand's reputation, which might reversely help correct the misconducts of food producers. However, companies may be under the expectation that food fraud will not be discovered, which can induce enterprise misconduct. Traditionally, China is a institution-driven market economy with limited participation by civil society (78). If the general public identify and report fraud cases, those committing the fraud are exposed (69) and the enterprise manager's psychological expectations may change. The “whistler” inside the enterprise can help discover the fraudulent behavior (79). Waterhouse et al. (80) indicated that employees are more aware of hidden fraud and therefore whistle-blowing is a powerful tool to prevent fraudulent activities from inside food enterprises. Li et al. (81) stated that social organizations can help to avoid the dual failure of public government power and private market power and play an irreplaceable role in supervising the operation of food enterprises.
A fundamental reason why food fraud is rampant is the poor utility of food testing methodologies, which are unable to detect food fraud (11). Generally speaking, food testing methodologies are based on known additives and pollutants and whether such additives are excessive compared with the prescribed threshold values (82). However, the sophistication of food and raw materials complicates both analysis and detection (67), particularly when the testing institutes do not know the additives (6). Thus, in response to enterprise food fraud, it is important to combine targeted and non-targeted testing methods (19).
Food fraud is also subject to influence from the maturity of the market reputation mechanism and consumption behavior on the food market.
Good market reputation can enhance market sales (83) and can be the primary means by which an enterprise avoids market risks and achieves economic benefits (84). Therefore, market reputation constitutes a foundation of survival and benefits. Food fraud can result in severe damage to an enterprise's market reputation (85), not just for the enterprise committing the wrongdoing, but also for other enterprises in the same industry, causing heavy economic losses. For example, the 2008 melamine infant milk powder incident in China damaged the reputation of the company involved so badly that it went bankrupt in the same year. Therefore, reputation is a key market mechanism for preventing enterprise food fraud (54). For instance, a mature market reputation mechanism, whereby any enterprise food fraud is disclosed to the general public, can deter other enterprises from committing such misconduct.
Regulation of food systems exists to ensure safety and enhance consumer confidence in the food which they purchase and consume. However, food fraud scandals have caused consumers to be anxious and distrustful of local food products, and further stimulate distrust in food system. Consumers' awareness of food fraud incidents has reduced consumers' willingness to pay for products from companies and industries that have experienced food fraud scandals (86). Moreover, when consumers believe that there is a lack of regulatory protection, they will develop strategies to reduce the risk of food fraud to prevent the purchase and consumption of fraudulent food (54). The three main coping approaches include purchasing decision making, information searching & sharing and daily self-preservation strategies (87). These risk mitigation strategies of consumers (that is, consumer behavior) affect the food fraud behavior of companies.
Mutual constraints among stakeholders and transparency along the food supply chain are also key factors influencing enterprise food fraud.
Previous studies have demonstrated that downstream enterprises in the supply chain can constrain upstream enterprises by inspecting the safety and authenticity of foods or materials, thus preventing food fraud. Babich and Tang (88) and Cao et al. (89) showed that inspection and deferred payment mechanisms can prevent adulteration by suppliers and upstream enterprises. Nevertheless, deficiencies in the constraints mechanism by downstream enterprises can also increase the probability of enterprise food fraud. Levi et al. (28) revealed that, compared with concentrated supply chains, distributed supply chains entail difficulties for downstream enterprises to impose constraints on upstream enterprises, thus raising the probability of food fraud along the supply chain.
Increasing complexity of the supply chain network can result in less visibility of the operational management of suppliers and is a key cause of food fraud (70). For example, Waterhouse et al. (80) determined that adulterated wine can reach consumers due to the non-transparent chain of supply and distribution. The melamine infant milk powder scandal in China also provides evidence that non-transparency of the upstream supply chain can lead to food fraud (61). Ensuring transparency of the supply chain can enhance food safety and quality (90). The Safe Supply of Affordable Food Everywhere (91) organization states that efforts should be made to acquire and maintain enhanced traceability information to ensure high transparency of the supply chain and minimization of food fraud.
Based on the existing literature, this paper has summarized some factors and clusters that influence the counterfeiting decisions of food companies, so what is the interrelationship between clusters and factors? What are the intrinsic mechanisms upon which they can influence food counterfeiting? What are the key clusters and key factors? To answer the questions, based on Hsu et al. (92) and Huang et al. (36), we applied the DANP method as follows:
Step 1 – Calculated direct relationship average matrix A. Firstly, a direct relationship matrix was generated based on the assessment results of each expert member. The average matrix A = [aij]n×n, i, j = 1, 2, …, n was then obtained by calculating the average of the same factor of all direct relationship matrices.
Step 2 – Calculated initial direct influence matrix D.
Step 3 – Calculated total influence matrix T.
where, tij is the degree of the direct and indirect influences of factor i on factor j.
then
Step 4 – Calculated the sum of each line and each column of total influence matrix T.
where, ri is the total of the direct and indirect influences of factor i on other factors in the system and cj is the total of the direct and indirect influences that factor j receives from other factors in the system. When i = j, ri + ci is the sum of influence that factor i imposes on other factors and receives from other factors and ri − ci is the difference of influence that factor i imposes on other factors and receives from other factors. ri − ci > 0 indicates that factor i has influence on other factors and is the cause factor in the system. ri − ci < 0 indicates that factor i is influenced by other factors and is the result factor in the system.
Step 5 – Acquired the influential net relationship map.
Assuming each cluster has an equal degree of influence, ANP standardizes an unweighted supermatrix established by pair comparison between indicators into a weighted supermatrix. However, different clusters have different influences on enterprise food fraud. Therefore, DEMATEL can be used to determine the degree of influence of each cluster and thus normalize the ANP unweighted supermatrix to simulate real-world situations (92).
Step 1 – Acquired the unweighted supermatrix. We first divided the total influence matrix T into the TD matrix (by cluster) and TC matrix (by factor) based on clusters and factors in Table 1.
We then calculated the standardized total influence matrix .
Finally, we calculated the unweighted supermatrix W.
Step 2 – Calculated the weighted standardized supermatrix Wα.
Step 3 – Calculated the ultimate supermatrix W*.
Step 4 – Calculated the mixed weight as per the following formula:
where, Z is the mixed weight and W is the comprehensive weight of secondary indicators.
In order to ensure the data quality and quantity requirements of the DANP method, we have done following efforts. In terms of data quality, since sample's appropriateness and richness is very important (93), this paper selects qualified experts based on three criteria. First, experts are experienced and have at least 15 years of research or work experience in food safety areas. Second, experts must have an academic professorship, food industrial manager, or a government food safety governor background, in order to possess a more comprehensive knowledge structure. This determines the diversity, representativeness and breadth of the expert group, and can give a comprehensive evaluation based on the comprehensive consideration of the views and interests of different stakeholders related to food fraud. Third, experts all must be from China.
It should be noted that the research method used in this paper does not require a high number of experts to participate in the evaluation. For example, when Chiu and Tzeng (94) and Shen and Tzeng (95) used DANP (DEMATEL-based ANP) to conduct the study, the number of experts participating in the evaluation was only eight. Thus, our study refers to the literature of Chiu and Tzeng (94), Shen and Tzeng (95), Chuang and Chen (96), and Huang et al. (36), and uses the average deviation rate (or what is referred to as “errors of gap ratio”) to determine the number of experts, which satisfies the number of participating experts in the evaluation process as required by the DANP method. In terms of data quantity, according to Chiu et al. (94), Huang et al. (36), Chuang and Chen (96) and Shen and Tzeng (95), this paper uses the average deviation rate to assess whether the expert size reaches theoretical saturation . p is the number of experts, is the average effect of factor i on factor j, and n is the number of factors being affected. In this paper, a group of experts were invited to participate in the project, who come from China National Food Industry Association, China Agricultural University, Shandong Agricultural University, Jiangnan University, Jiangsu Academy of Agricultural Sciences and other institutions. Experts can express their opinions and discuss together before evaluating the relationship between the two factors. Since the opinions of the experts are expressed in terms of language rather than numerical values, when the evaluation results are finally collected, experts are required to score the pairwise relationship between the factors according to the corresponding integer values in Table 2.
Finally, regarding the theoretical saturation, we refer to Chuang and Chen (96) for our study. Using the average deviation rate (or “errors of gap ratio,” EGR) method, we calculated that the average deviation rate of the nine experts who participated in the evaluation was 4.25% <5% (see P24 of the revised paper). This indicates that we have more than 95% confidence that there is no significant difference between the results of 9 experts and 8 experts participating in the evaluation. According to Chuang and Chen (96), it is reasonable to assume that 9 experts are close to the theoretical saturation and meet the requirement of an appropriate number of experts.
By averaging the expert assessment results, we obtained the direct relationship average matrix A. By repeating the above step, we then obtained the initial direct relationship matrix D (Table 3), line sum and column sum (ri and ci) of total influence matrix T and of each cluster and factor (Table 4), and the mixed weights of the clusters and factors. Finally, we performed normalized sorting of the mixed weights to compile (Table 5).
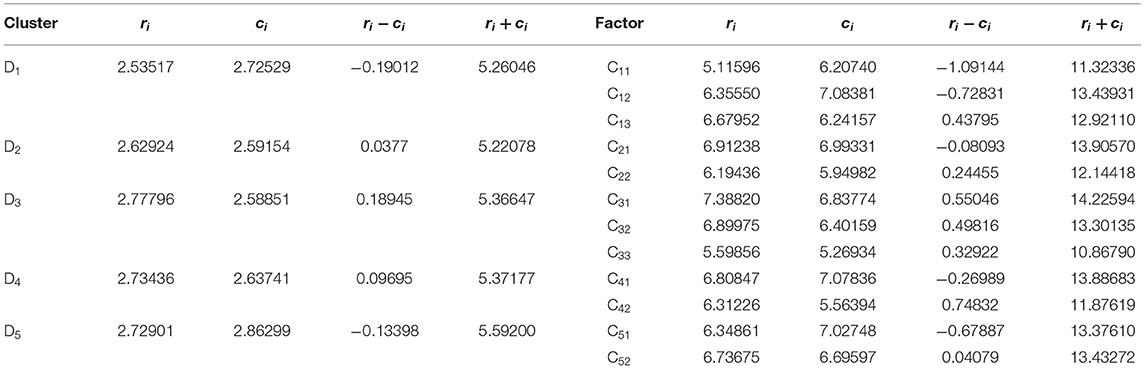
Table 4. Values of ri, ci, ri + ci, and ri − ci for clusters and factors influencing enterprise food fraud.
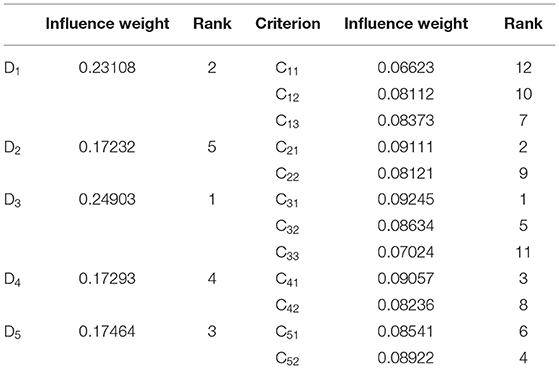
Table 5. Normalized rank of mixed weights of clusters and factors influencing enterprise food fraud.
Based on the calculation results obtained by the DANP method, this section identifies the interrelationships between Clusters and Factors that affect food counterfeiting and the intrinsic mechanisms that influence counterfeiting decisions of food companies, and identifies the key Clusters and key Factors from three aspects.
The ri − ci and ri + ci values of each cluster and factor obtained from DEMATEL analysis are shown in Table 4. With reference to the plotting methods of Yang and Tzeng (97) and by use of the (ri + ci, ri − ci) dataset, we obtained the influential net relationship map (Figure 1).
Figure 1 depicts the direct relationships among five clusters that influence enterprise food fraud, i.e., enterprise characteristics (D1), economic benefits and technical hardness of food fraud (D2), government regulation, social governance, and detection techniques (D3), market governance (D4), and internal relationship and transparency of food supply chain (D5). The direct influence of cluster D3 on D4, D2, D5, and D1 can be expressed as D3 → {D4, D2, D5, D1}. Similarly, the direct influence of cluster D4 on D2, D5, and D1 can be expressed as D4 → {D2, D5, D1}; the direct influence of cluster D2 on D5 and D1 can be expressed as D2 → {D5,D1}; and the direct influence of cluster D5 on D1 can be expressed as D5 → {D1}.
Figure 1 also shows the direct influence relationship among factors within the same cluster. For example, cluster D1 encompasses three interrelated factors, i.e., enterprise scale (C11), business ethics (C12), and manager's awareness of social responsibilities (C13). The direct influence of C13 on C12 and C11 can be expressed as C13 → {C12,C11} and the direct influence of C12 on C11 can be expressed as C12 → {C11}. The direct influence relationship among factors within each of the other four clusters can be expressed in the same way as cluster D1.
The ri − ci values in Table 4 were used to determine by what intrinsic mechanism the clusters and factors influence enterprise food fraud. Firstly, at the cluster level, D3, D4, and D2 were identified as cause clusters based on their positive ri − ci values, with each influencing other clusters in the system to a certain degree. In addition, D1 and D5 were identified as result clusters based on their negative ri − ci values, with both influenced significantly by other clusters in the system. Therefore, the five clusters interacted intrinsically, such that clusters D3, D4, and D2 directly and/or indirectly influenced clusters D1 and D5, and ultimately enterprise food fraud. This intrinsic mechanism can help us understand the causes of food fraud. In developed countries, the lack of detection technology is an important cause of food fraud (6). However, the Figure 1 shows that in China, the lack of government governance is highly related to insufficient supervision of social entities, but not for the reasons of governance approaches. This result might also apply to, and have implications for, other developing countries.
At the factor level, seven factors were identified as cause factors based on their positive ri − ci values, with each imposing significant influence on other factors in the system to varying degrees. These factors included consumption behavior on food market (C42), government regulatory capability and penalty intensity (C31), supervision by social forces (C32), manager's awareness of social responsibility (C13), technical hardness (C22), utility of detection techniques and methodologies (C33), and transparency of supply chain (C52). The other five factors were identified as result factors based on their negative ri − ci values, with each influenced significantly by other factors to varying degrees. These factors included enterprise scale (C11), business ethics (C12), constraints by downstream enterprises (C51), expected economic benefits (C21), and maturity of market reputation mechanism (C41). In summary, the factors interacted and influenced the fraudulent behavior of food enterprises intrinsically, with C42,C31, C32,C13,C22,C33, and C52 directly and/or indirectly influencing C11, C12, C51, C21, and C41, and ultimately enterprise food fraud. From a supply perspective, an in-depth understanding of the unethical behavior of companies pursuing profits in the supply chain can help us understand the food fraud behavior of companies (1). However, this intrinsic mechanism further reveals the particularity of the causes of Chinese food fraud from the perspective of demand. As in Table 4, C42′sri − ci value is the largest, indicating that the consumption behavior of the food market, especially the food literacy of consumers, provides a market space for food fraud. This may also be an important reason why food fraud in rural China is more serious than in urban areas.
In addition to the above, another major advantage of the DANP method is that when a result factor emerges, the decision-maker can determine what has caused the issue by examining the cause factors. Take the internal relationships and transparency of the food supply chain (D5) cluster as an example. Table 4 shows that constraints by downstream enterprises (C51) was the only result factor in this cluster, whereas transparency of supply chain (C52) was the cause factor. Loose constraints on upstream enterprises by downstream enterprises on the supply chain may be due to inadequacy of supply chain transparency. Similarly, low manager awareness of social responsibilities may be due to small scale or poor business ethics of the enterprise. High expected economic benefits from food fraud may be due to the low technical hardness of fraud. These inferences conform to what occur in the real world and may provide essential references for the government in stipulating and enforcing relevant policies.
Based on the internal relationships among clusters and factors and the intrinsic mechanism of how they influence enterprise food fraud, we used the mixed weights in Table 5 to further identify the key clusters and factors that influence enterprise food fraud.
Results demonstrated that the government regulation, social governance, and detection techniques (D3) cluster had an influence weight of 0.24903, and thus was a key cluster ranking first among the five clusters, as also seen in Figure 1. Furthermore, D3 had the maximum ri − ci value, which did not differ significantly from that of D5. This implies that, as a key cluster, D3 significantly influenced the other clusters and played a dominant role in the system. Therefore, based on the mixed weights, the DANP results were consistent with those obtained using DEMATEL. The results showed that the relationships between dimensions and real-world considerations are more significant than any single dimension. This also reveals the importance of establishing a system of social co-governance (implemented by improving all dimensions but not any single one) that is jointly supervised by the government and social entities in China.
Secondly, factors with a mixed weight > 0.09 in Table 5 were identified as key factors that influence the food fraud behavior of enterprises. Government regulation and penalty intensity (C31) was deemed a key factor based on its first-ranked mixed weight of 0.09245. This is consistent with the conclusions of Lord et al. (47) and Kendall et al. (54). The expected economic benefits (C21) and maturity of market reputation mechanism (C41) were also deemed as key factors with mixed weights of 0.09111 and 0.09057, ranking second and third, respectively. These findings are supported by Charlebois et al. (68). Transparency of supply chain (C52) was also determined to be a key factor, with a mixed weight of 0.08922 (close to 0.09), ranking fourth in the system. This result is supported by Bitzios et al. (70).
The key factors identified above are consistent with previous studies, thus providing preliminary proof that the DANP method is applicable and the conclusions of the study are reliable. Furthermore, to verify the applicability of the DANP method, we compared the key factors identified by DEMATEL and DANP analyses, which showed consistent conclusions. Previous studies have generally identified key factors by the magnitude of the ri+ci values obtained using DEMATEL (55). As seen in Table 4, the first four key factors ranked by the DEMATEL ri + ci values were government regulation and penalty intensity, expected economic benefits from fraud, maturity of market reputation mechanism, and transparency of supply chain. These results agree with the conclusions obtained using the mixed weight magnitudes from DANP (Table 5). Therefore, it is reasonable to believe that the four key factors proposed by this paper are accurate. Thus, we found the DANP method to be applicable in the identification of key factors that influence enterprise food fraud behavior.
In addition to the four key factors above, six other factors, namely supervision by social forces (C32), constraints by downstream enterprises (C51), manager's awareness of social responsibility (C13), consumption behavior on food market (C42), technical hardness of food fraud (C22), and enterprise business ethics (C12), had mid-rank mixed weights ranging from 0.8 to 0.9, and were thus deemed to be secondary key factors. Two further factors, namely utility of detecting techniques and methodologies (C33) and enterprise scale (C11), ranked last in the system and were therefore deemed to be non-key factors. As seen from most food safety incidents in China, food fraud is primarily uncovered by simple detection. Thus, the utility of detection methodologies is not directly related to enterprise food fraud. Furthermore, although it is generally recognized that enterprise scale can influence fraudulent behavior (28, 55), this was not supported in the current study. It is possible that food fraud occurs frequently in China and enterprises can commit food fraud regardless of enterprise scale. Therefore, food fraud may not be necessarily associated with enterprise scale.
In a complex system encompassing multiple stakeholders, we found that enterprise food fraud was subject to joint influences by multiple clusters. Government regulation, social governance, and detection techniques was the key cluster. Furthermore, government regulatory capability and penalty intensity, expected economic benefits from fraud, maturity of market reputation mechanism, and transparency of food supply chain were the four key factors. We further determined the intrinsic mechanism of fraudulent behaviors of food enterprises and demonstrated that the DANP method is effective at identifying key clusters and factors that influence enterprise food fraud.
The current research was based on participation of a group of experts and was conducted within the context in China's food systems. One common attribute is that all of the experts have deep care and understanding of policy making regarding food fraud. Thus, the results could have profound policy implications from the social co-governance perspective for China and similar economies. First, Fraudulent behavior depends not only on expected economic benefits but also on expected cost (i.e., probability of getting caught and the penalty if they are caught cheating). Among them, the probability of being caught is determined by factors such as the effectiveness of detection techniques and methods (i.e., utility of detection Techniques and methodologies), and the supervision of social forces. The punishment after being caught is determined by factors such as Government Penalty Intensity and Maturity of Market Reputation Mechanism. Due to the major attractive effect of expected economic benefits of committing food frauds for enterprises, the government should be increased penalty of getting caught, so that the economic costs of food fraud are increased to a level sufficient to change the psychological expectation for economic return of food fraud. From a social co-governance perspective, not only the government should exercise such a penalty system. Business partners (e.g., suppliers or buyers), for example, could exercise such penalty method by contract; while end consumers could exercise such penalty by collective actions of refusing purchases (98, 99). In addition, in addition to strengthening supervision and sampling and improving the level of detection technology, it is also necessary to actively promote internal employees to provide food fraud clues.
Second, a regulation mechanism based on individual person's and an enterprise's life-long, public credit should be established. Food enterprises should be rated by credit levels and regulation should differ for the different levels, including punitive measures and close-out mechanisms against credit-losing enterprises. With such system, all stakeholders could see the credit and collectively perceive the credibility of a food enterprise.
Third, priority should be given to criminal liabilities. In parallel with behavioral and property punishments, confinement should be stressed, i.e., administrative detention of the responsible persons. By eliminating no or weak enforcement and limited economic penalties in substitution for stronger criminal liabilities, a lasting system-based mechanism and legislative environment will be established to ensure that food enterprises are unable to or do not wish to commit food fraud.
Fourth, the market reputation mechanism should be leveraged to control food fraud by disclosing food fraud information in a widespread manner through public media.
Fifth, a food traceability system should be established, and the food supply chain should have due transparency. Government authorities should establish and popularize food traceability systems and ensure food enterprises maintain continuous records to create reliable information flow along the supply chain, thus allowing food production processes and destinations to be monitored, food fraud to be identified by tracking, and recall to be ordered when necessary. These measures will, in turn, encourage food enterprises to maintain compliance in business operation.
Sixth, although the food fraud vulnerability assessment tools are still in their infancy, its full impact remains to be seen. However, over time, food fraud vulnerability assessment tools can be used to ensure the food supply chain. Play an active role in integrity (100). China should also actively promote and encourage companies to implement food fraud vulnerability assessments. This is also an important part of social co-governance.
This paper adopts the DANP approach to make up for the deficiencies of existing studies that do not examine the key factors (cluster) and the interrelationships between factors (cluster) that influence food enterprises' food fraud decisions from the perspective of social co-governance and business decision making, thus contributing to an in-depth understanding of the causes of food fraud by food enterprises and to the formulation of targeted. The study contributes to the understanding of the causes of food fraud in food companies, and to the formulation of targeted measures to change the decisions of food companies and reduce food fraud at source.
Theoretically and practically, a social co-governance perspective extends the scope of governance to a multiple-agent level. That is, not just the producer enterprise is the focus of fraud prevention, but all stakeholders become the ones being governed by all of other social actors. The system design thinking of a food fraud governance should be a dominant logic to cover all government needs, whether which social actor is the one who is governing or governed.
What needs to be explained is the government regulatory capability and penalty intensity. Government has two instruments to control food fraud: (1) certification and (2) monitoring and enforcement system (31). The major reason for not discussing about the certification in the scope of the present study are: First, this paper is based on China's information. In China, the government's approach to countering food fraud is mainly government supervision and punishment, not certification. Second, in China, the government still needs to continuously improve the average product quality level in the market. When the government wants to increase the average product quality in the market while combating food adulteration, strict monitoring and enforcement is more effective than increasing certification costs (31). Therefore, this article will not discuss certification issues for the time being.
Additionally, in China, both legal food producers who have obtained food production licenses and a large number of illegal food producers who have not obtained licenses (such as illegal workshops) may engage in food fraud. The enterprise in this article refers to a legal food producer who has obtained a food production license. At the same time, we believe that the research conclusions are also applicable to illegal food producers who have not obtained a license to a certain extent.
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
This study was partially supported by the National Social Science Fund of China: Research on social co-governance of food safety risks and cross-border cooperative governance mechanism (20&ZD117).
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
1. McElwee G, Smith R, Lever J. Illegal activity in the UK halal sheep supply chain: towards greater understanding. Food Policy. (2017) 69:166–75. doi: 10.1016/j.foodpol.2017.04.006
2. Van der Meulen B. Is current EU food safety law geared up for fighting food fraud? Journal für Verbraucherschutz und Lebensmittelsicherheit. (2015) 101:19–23. doi: 10.1007/s00003-015-0992-2
3. Liu CY. Institutional isomorphism and food fraud: a longitudinal study of the mislabeling of rice in Taiwan. J Agric Environ Ethics. (2016) 29:607–30. doi: 10.1007/s10806-016-9623-x
4. Nöhle U. Food fraud, food crime oder kalter kaffee? J Consum Protect Food Saf. (2017) 12:197–9. doi: 10.1007/s00003-017-1115-z
5. Spink J, Moyer DC. Defining the public health threat of food fraud. J Food Sci. (2011) 76:157–63. doi: 10.1111/j.1750-3841.2011.02417.x
6. Manning L, Soon JM. Developing systems to control food adulteration. Food Policy. (2014) 49:23–32. doi: 10.1016/j.foodpol.2014.06.005
7. Bouzembrak Y, Steen B, Neslo R, Linge J, Mojtahed V, Marvin H. Development of food fraud media monitoring system based on text mining. Food Control. (2018) 93:283–96. doi: 10.1016/j.foodcont.2018.06.003
8. Zhang W, Xue J. Economically motivated food fraud and adulteration in China: an analysis based on 1,553 media reports. Food Control. (2016) 67:192–8. doi: 10.1016/j.foodcont.2016.03.004
9. Schaefer KA, Scheitrum D, Nes K. International sourcing decisions in the wake of a food scandal. Food Policy. (2018) 81:48–57. doi: 10.1016/j.foodpol.2018.10.002
10. Rocchi B, Romano D, Sadiddin A, Stefani G. Assessing the economy-wide impact of food fraud: a SAM-based counterfactual approach. Agribusiness. (2020) 36:167–91. doi: 10.1002/agr.21633
11. Everstine K, Spink J, Kennedy S. Economically motivated adulteration EMA of food: common characteristics of EMA incidents. J Food Prot. (2013) 76:723–35. doi: 10.4315/0362-028X.JFP-12-399
12. Yang Y, Huisman W, Hettinga KA, Liu N, Heck J, Schrijver GH, et al. Fraud vulnerability in the Dutch milk supply chain: assessments of farmers, processors and retailers. Food Control. (2019) 95:308–17. doi: 10.1016/j.foodcont.2018.08.019
13. Spink J, Ortega DL, Chen C, Wu F. Food fraud prevention shifts the food risk focus to vulnerability. Trends Food Sci Technol. (2017) 62:215–20. doi: 10.1016/j.tifs.2017.02.012
14. Spink J, Fortin ND, Moyer DC, Miao H, Wu Y. Food fraud prevention: policy, strategy, and decision-making-implementation steps for a government agency or industry. CHIMIA Int J Chem. (2016) 70:320–8. doi: 10.2533/chimia.2016.320
15. Tähkäpää S, Maijala R, Korkeala H, Nevas M. Patterns of food frauds and adulterations reported in the EU rapid alert system for food and feed and in Finland. Food Control. (2015) 47:175–84. doi: 10.1016/j.foodcont.2014.07.007
16. Pei X, Tandon A, Alldrick A, Giorgi L, Huang W, Yang R. The China melamine milk scandal and its implications for food safety regulation. Food Policy. (2011) 36:412–20. doi: 10.1016/j.foodpol.2011.03.008
17. Wu L, Chen X, Yin S. Safety of Every Bite of Food: Risk Management From Farm to Table. Beijing: China Agriculture Press (2019).
18. Barnett J, Begen F, Howes S, Regan A, McConnon A, Marcu A, et al. Consumers' confidence, reflections and response strategies following the horsemeat incident. Food Control. (2016) 59:721–30. doi: 10.1016/j.foodcont.2015.06.021
19. Mcgrath TF, Haughey SA, Patterson J, Fauhl-Hassek C, Donarski J, Alewijn M, et al. What are the scientific challenges in moving from targeted to non-targeted methods for food fraud testing and how can they be addressed? Spectroscopy case study. Trends Food Sci Technol. (2018) 76:38–55. doi: 10.1016/j.tifs.2018.04.001
20. Wu L, Zhu D. Food safety in China: a comprehensive review. Abingdon: CRC PRESS Taylor and Francis Group (2014).
21. Liu A, Shen L, Tan Y, Zeng Z, Liu Y, Li C. Food integrity in China: insights from the national food spot check data in 2016. Food Control. (2018) 84:403–7. doi: 10.1016/j.foodcont.2017.08.033
22. Curll J. The significance of food fraud in Australia. Aust Bus Law Rev. (2015) 43:270–302. Available online at: https://www.researchgate.net/publication/281366422
23. Van Ruth SM, Huisman W, Luning PA. Food fraud vulnerability and its key factors. Trends Food Sci Technol. (2017) 67:70–5. doi: 10.1016/j.tifs.2017.06.017
24. Kafetzopoulos DP, Psomas EL, Kafetzopoulos PD. Measuring the effectiveness of the HACCP food safety management system. Food Control. (2013) 33:505–13. doi: 10.1016/j.foodcont.2013.03.044
25. Djekic I, Kuzmanović J, Andelković A, Saračević M, Stojanović M, Tomašević I. Effects of HACCP on process hygiene in different types of Serbian food establishments. Food Control. (2016) 60:131–7. doi: 10.1016/j.foodcont.2015.07.028
26. Lord N, Flores Elizondo CJ, Spencer J. The dynamics of food fraud: the interactions between criminal opportunity and market dys functionality in legitimate business. Criminol Crim Just. (2017) 17:605–23. doi: 10.1177/1748895816684539
27. Ehmke MD, Bonanno A, Boys K, Smith TG. Food fraud: economic insights into the dark side of incentives. Aust J Agric Resource Econ. (2019) 63:685–700. doi: 10.1111/1467-8489.12346
28. Levi R, Singhvi S, Zheng Y. Economically motivated adulteration in farming supply chains. Manage Sci. (2020) 66:209–26. doi: 10.1287/mnsc.2018.3215
29. Meerza S, Giannakas K, Yiannaka A. Market and welfare effects of food fraud. Aust J Agric Resource Econ. (2019) 64:759–89. doi: 10.1111/1467-8489.12348
30. Meerza S, Gustafson CR. Consumers' response to food fraud: evidence from experimental auctions. J Agric Resource Econ. (2020) 45:219–31. doi: 10.22004/ag.econ.302451
31. Meerza S, Giannakas K, Yiannaka A. Optimal policy response to food fraud. J Agric Resource Econ. (2021) 46:343–60. doi: 10.22004/ag.econ.307459
32. Manning L, Smith R, Soon JM. Developing an organizational typology of criminals in the meat supply chain. Food Policy. (2016) 59:44–54. doi: 10.1016/j.foodpol.2015.12.003
33. Wu L, Liu P, Lv Y, Chen X. Social co-governance for food safety risks. Sustainability. (2018) 10:42–6. doi: 10.3390/su10114246
34. Martinez MG, Fearne A, Caswell JA, Henson S. Co-regulation as a possible model for food safety governance: opportunities for public-private partnerships. Food Policy. (2007) 32:299–314. doi: 10.1016/j.foodpol.2006.07.005
35. Russell CA, Russell DW, Honea H. Corporate social responsibility failures: how do consumers respond to corporate violations of implied social contracts? J Bus Ethics. (2016) 136:759–73. doi: 10.1007/s10551-015-2868-x
36. Huang CN, Liou JJ, Chuang YC. A method for exploring the interdependencies and importance of critical infrastructures. Knowledge Based Syst. (2014) 55:66–74. doi: 10.1016/j.knosys.2013.10.010
37. Wu L, Xu G, Wang X. Identifying critical factors influencing the disposal of dead pigs by farmers in China. Environ Sci Pollut Res. (2016) 23:661–72. doi: 10.1007/s11356-015-5284-y
38. Akerlof GA. The market for ‘lemons': quality uncertainty and the market mechanism. Q J Econ. (1970) 843:488–500. doi: 10.2307/1879431
39. Darby MR, Karni E. Free competition and the optimal amount of fraud. J Law Econ. (1973) 16:67–88. doi: 10.1086/466756
40. Rouvière E, Caswell JA. From punishment to prevention: a French case study of the introduction of co-regulation in enforcing food safety. Food Policy. (2012) 37:246–54. doi: 10.1016/j.foodpol.2012.02.009
41. Codron JM, Fares M, Rouviere E. From public to private safety regulation? The case of negotiated agreements in the French fresh produce import industry. Int J Agric Resources Governance Ecol. (2007) 6:415–27. doi: 10.1504/IJARGE.2007.012845
42. Hobbs JE, Fearne A, Spriggs J. Incentive structures for food safety and quality assurance: an international comparison. Food Control. (2002) 13:77–81. doi: 10.1016/S0956-7135(01)00103-7
43. Starbird SA. Designing food safety regulations: the effect of inspection policy and penalties for noncompliance on food processor behavior. J Agric Resource Econ. (2000) 25:616–35. doi: 10.22004/ag.econ.30898
44. Hirschauer N, Musshoff O. A game-theoretic approach to behavioral food risks: the case of grain producers. Food Policy. (2007) 32:246–65. doi: 10.1016/j.foodpol.2006.07.001
45. Moore JC, Spink J, Lipp M. Development and application of a database of food ingredient fraud and economically motivated adulteration from 1980 to 2010. J Food Sci. (2012) 77:118–26. doi: 10.1111/j.1750-3841.2012.02657.x
46. Primrose S, Woolfe M, Rollinson S. Food forensics: methods for determining the authenticity of foodstuffs. Trends Food Sci Technol. (2010) 21:582–90. doi: 10.1016/j.tifs.2010.09.006
47. Lord N, Spencer J, Albanese J, Elizondo CF. In pursuit of food system integrity: the situational prevention of food fraud enterprise. Eur J Crim Policy Res. (2017) 23:483–501. doi: 10.1007/s10610-017-9352-3
48. Manning L, Soon JM. Food safety, food fraud, and food defense: a fast evolving literature. J Food Sci. (2016) 81:823–34. doi: 10.1111/1750-3841.13256
49. Silvis ICJ, Van Ruth SM, Van Der Fels-klerx HJ, Luning PA. Assessment of food fraud vulnerability in the spices chain: an explorative study. Food Control. (2017) 81:80–7. doi: 10.1016/j.foodcont.2017.05.019
50. Yang Y, Huisman W, Hettinga KA, Zhang L, van Ruth S. The Chinese milk supply chain: a fraud perspective. Food Control. (2020) 113:107211. doi: 10.1016/j.foodcont.2020.107211
51. Rouviere E, Royer A. Public private partnerships in food industries: a road to success? Food Policy. (2017) 69:135–44. doi: 10.1016/j.foodpol.2017.04.003
52. Mutshewa A. The use of information by environmental planners: a qualitative study using grounded theory methodology. Inform Process Manage. (2010) 46:212–32. doi: 10.1016/j.ipm.2009.09.006
53. Commission on Global Governance. Our Global Neighbourhood: The Report of the Commission on Global Governance. London: Oxford University Press (1995).
54. Kendall H, Kuznesof S, Dean M, Chan MY, Clark B, Home R, et al. Chinese consumer's attitudes, perceptions and behavioural responses towards food fraud. Food Control. (2019) 95:339–51. doi: 10.1016/j.foodcont.2018.08.006
55. Wu L, Zhang Q, Shan L, Chen Z. Identifying critical factors influencing the use of additives by food enterprises in China. Food Control. (2013) 31:425–32. doi: 10.1016/j.foodcont.2012.10.028
56. Enderle G. How can business ethics strengthen the social cohesion of a society? J Bus Ethics. (2018) 150:619–29. doi: 10.1007/s10551-016-3196-5
57. El Darra N, Rajha HN, Saleh F, Al-Oweini R, Maroun RG, Louka N. Food fraud detection in commercial pomegranate molasses syrups by UV-VIS spectroscopy, ATR-FTIR spectroscopy and HPLC methods. Food Control. (2017) 78:132–7. doi: 10.1016/j.foodcont.2017.02.043
58. Cohen J, Ding Y, Lesage C, Stolowy H. Corporate fraud and managers' behavior: evidence from the press. J Bus Ethics. (2010) 95:271–315. doi: 10.1007/s10551-011-0857-2
59. Collins EJ. Food adulteration and food safety in Britain in the 19th and early 20th centuries. Food Policy. (1993) 18:95–109. doi: 10.1016/0306-9192(93)90018-7
60. Murphy PR, Dacin MT. Psychological pathways to fraud: understanding and preventing fraud in organizations. J Bus Ethics. (2011) 101:601–18. doi: 10.1007/s10551-011-0741-0
61. Dani S, Fassam L. The convergence of ethics and fraud: challenges facing procurement functions in food supply chains. In: Proceedings of 21st Logistics Research Network LRN Annual Conference 2016. Hull: University of Hull, (2016).
62. Freeman I, Hasnaoui A. The meaning of corporate social responsibility: the vision of four nations. J Bus Ethics. (2011) 100:419–43. doi: 10.1007/s10551-010-0688-6
63. Miller S, Tait P, Saunders C, Dalziel P, Rutherford P, Abell W. Estimation of consumer willingness-to-pay for social responsibility in fruit and vegetable products: a cross-country comparison using a choice experiment. J Consum Behav. (2017) 16:13–25. doi: 10.1002/cb.1650
64. Leon KS, Ken I. Food fraud and the partnership for a ‘healthier' America: a case study in state-corporate crime. Crit Criminol. (2017) 25:1–18. doi: 10.1007/s10612-017-9363-x
65. Donaldson J, Fafaliou I. Business ethics, corporate social responsibility and corporate governance: a review and summary critique. Eur Res Stud. (2003) 6:90–110. Available online at: https://www.um.edu.mt/library.oar//handle/123456789/30879
66. Zhang D, Gao Y, Morse S. Corporate social responsibility and food risk management in China: a management perspective. Food Control. (2015) 49:2–10. doi: 10.1016/j.foodcont.2013.01.030
67. Moyer DC, DeVries JW, Spink J. The economics of a food fraud incident: case studies and examples including Melamine in Wheat Gluten. Food Control. (2017) 71:358–64. doi: 10.1016/j.foodcont.2016.07.015
68. Charlebois S, Schwab A, Henn R, Huck CW. Food fraud: An exploratory study for measuring consumer perception towards mislabeled food products and influence on self-authentication intentions. Trends Food Sci Technol. (2016) 50:211–8. doi: 10.1016/j.tifs.2016.02.003
69. Zhao P, Zhang L, Hu S. Study on the behavior of counterfeiter and regulators based on Evolutionary Game. Econ Manage. (2018) 32:76–82. Available online at: en.cnki.com.cn/Article_en/CJFDTotal-JJGL201804014.htm
70. Bitzios M, Lisa J, Krzyzaniak SA, Mark XU. Country-of-origin labelling, food traceability drivers and food fraud: lessons from consumers' preferences and perceptions. Eur J Risk Regul. (2017) 8:541–58. doi: 10.1017/err.2017.27
71. Spink J. Safety of food and beverages: risks of food adulteration. Encyc Food Saf. (2014) 3:413–6. doi: 10.1016/B978-0-12-378612-8.00300-0
72. Álvarez BM, Pascual-Alonso M, Rusu A, Bogason SG. A review on existing databases relevant for food fraud and authenticity. Archivos de zootecnia. (2013) 62:73–91. doi: 10.21071/az.v62iREV.1958
73. Anita S, Bhatt SR, Bhatt SM. Food adulteration and practices in urban area of Varanasi. Food Sci Res J. (2010) 1:183–95. Available online at: www.researchgate.net/publication/230688059
74. Jack L. Risk Modelling of Food Fraud Motivation: “NSF Fraud Protection Model” Intelligent Risk Model Scoping Project FS 246004. NSF Safety and Quality UK Ltd. (2015). Available online at: https://core.ac.uk/download/pdf/29588958.pdf
75. Li D, Zang M, Li X, Zhang K, Wang S. A study on the food fraud of national food safety and sample inspection of China. Food Control. (2020) 116:107306. doi: 10.1016/j.foodcont.2020.107306
76. Wu Y, Cai H. Fraud propagations and containments: a study based on evolutionary game simulation model. Wuhan Univ J Phil Soc Sci. (2014) 67:112–8. doi: 10.14086/j.cnki.wujss.2014.0
77. Peng Y, Li J, Xia H, Qi S, Li J. The effects of food safety issues released by we media on consumers' awareness and purchasing behavior: a case study in China. Food Policy. (2015) 51:44–52. doi: 10.1016/j.foodpol.2014.12.010
78. Scott S, Si Z, Schumilas T, Chen A. Contradictions in state-and civil society-driven developments in China's ecological agriculture sector. Food Policy. (2014) 45:158–66. doi: 10.1016/j.foodpol.2013.08.002
79. Lee G, Fargher N. Companies' use of whistle-blowing to detect fraud: an examination of corporate whistle-blowing policies. J Bus Ethics. (2013) 114:283–95. doi: 10.1007/s10551-012-1348-9
80. Waterhouse AL, Sacks GL, Jeffery DW. Understanding Wine Chemistry. Chichester: John Wiley and Sons (2016).
81. Li Y, Wu L, Pu X, Lin M. Main factors affecting social organizations'capabilities of involving in food safety risk management in food industry. China Populat Resources Environ. (2016) 26:167–76. doi: 10.3969/j.issn.1002-2014.2016.08.022
82. Esslinger S, Riedl J, Fauhl-Hassek C. Potential and limitations of non-targeted fingerprinting for authentication of food in official control. Food Res Int. (2014) 60:189–204. doi: 10.1016/j.foodres.2013.10.015
83. Ryan J, Casidy R. The role of brand reputation in organic food consumption: a behavioral reasoning perspective. J Retail Consum Serv. (2018) 41:239–47. doi: 10.1016/j.jretconser.2018.01.002
84. Zhou X, Feng Z. Study on the relationship between repulation effects and the level of food safety: evidence from China famous trademarks. Res Econ Manage. (2014) 6:111–22. doi: 10.13502/j.cnki.issn10000-7636.2014.06.014
85. Wilkes E, Day M, Herderich M, Johnson D. AWRI reports: in vivo veritas-investigating technologies to fight wine fraud. Wine Viticulture J. (2016) 31:36–8.
86. Meerza S, Gustafson CR. Does prior knowledge of food fraud affect consumer behavior? Evidence from an incentivized economic experiment. PLoS ONE. (2019) 14:e0225113. doi: 10.1371/journal.pone.0225113
87. Soon JM, Liu X. Chinese consumers' risk mitigating strategies against food fraud. Food Control. (2020) 115:107298. doi: 10.1016/j.foodcont.2020.107298
88. Babich V, Tang CS. Managing opportunistic supplier product adulteration: deferred payments, inspection, and combined mechanisms. Manufact Serv Operat Manage. (2012) 14:301–14. doi: 10.1287/msom.1110.0366
89. Cao Y, Hu H, Wan G. Game analysis and mechanism choices of supplier product adulteration behavior. Operat Res Manage Sci. (2017) 7:54–63. doi: 10.12005/orms.2017.0162
90. Beulens AJ, Broens DF, Folstar P, Hofstede GJ. Food safety and transparency in food chains and networks relationships and challenges. Food Control. (2005) 16:481–6. doi: 10.1016/j.foodcont.2003.10.010
91. Safe Supply of Affordable Food Everywhere (2016). Food Fraud Vulnerability Assessment Tool. Available online at: http://www.ssafe-food.org/our-projects
92. Hsu CH, Wang FK, Tzeng GH. The best vendor selection for conducting the recycled material based on a hybrid MCDM model combining DANP with VIKOR. Resources Conserv Recycling. (2012) 66:95–111. doi: 10.1016/j.resconrec.2012.02.009
93. Denzin NK, Lincoln YS. The Landscape of Qualitative Research: Theories and Issues. Thousand Oaks, CA: Sage Publications (1998).
94. Chiu WY, Tzeng GH, Li HL. A new hybrid mcdm model combining danp with vikor to improve e-store business. Knowledge Based Syst. (2013) 37:48–61. doi: 10.1016/j.knosys.2012.06.017
95. Shen KY, Tzeng GH. Combining DRSA decision-rules with FCA-based DANP evaluation for financial performance improvements. Technol Econ Dev Econ. (2016) 22:685–714. doi: 10.3846/20294913.2015.1071295
96. Chuang HM, Chen YS. Identifying the value co-creation behavior of virtual customer environments using a hybrid expert-based DANP model in the bicycle industry. Human Centric Comput Inform Sci. (2015) 5:11. doi: 10.1186/s13673-015-0028-z
97. Yang JL, Tzeng GH. An integrated MCDM technique combined with DEMATEL for a novel cluster-weighted with ANP method. Expert Syst Appl. (2011) 38:1417–24. doi: 10.1016/j.eswa.2010.07.048
98. Burkhardt J. Agribusiness ethics: specifying the terms of the contract. J Bus Ethics. (1986) 54:333–45. doi: 10.1007/BF00383101
99. Kim Y. Consumer responses to the food industry's proactive and passive environmental CSR, factoring in price as CSR tradeoff. J Bus Ethics. (2017) 140:307–21. doi: 10.1007/s10551-015-2671-8
Keywords: food fraud, business ethics, social co-governance, safety and quality, DEMATEL-based ANP
Citation: Niu L, Chen M, Chen X, Wu L and Tsai F-S (2021) Enterprise Food Fraud in China: Key Factors Identification From Social Co-governance Perspective. Front. Public Health 9:752112. doi: 10.3389/fpubh.2021.752112
Received: 02 August 2021; Accepted: 22 October 2021;
Published: 19 November 2021.
Edited by:
Pauline Douglas, Ulster University, United KingdomReviewed by:
Guanghua Han, Shanghai Jiao Tong University, ChinaCopyright © 2021 Niu, Chen, Chen, Wu and Tsai. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Linhai Wu, d2xoNjc5OUBqaWFuZ25hbi5lZHUuY24=; Fu-Sheng Tsai, ZnVzaGVuZ190c2FpQGhvdG1haWwuY29t
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.