
95% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Phys. , 06 November 2024
Sec. Quantum Engineering and Technology
Volume 12 - 2024 | https://doi.org/10.3389/fphy.2024.1434095
In the development of quantum technologies, a reliable means for characterizing quantum devices, be it a measurement device, a state-preparation device, or a transformation device, is crucial. However, the conventional approach based on, for example, quantum state tomography or process tomography relies on assumptions that are often not necessarily justifiable in a realistic experimental setting. Although the device-independent (DI) approach to this problem bypasses the shortcomings above by making only minimal, justifiable assumptions, most of the theoretical proposals to date only work in the idealized setting where independent and identically distributed (i.i.d.) trials are assumed. Here, we provide a versatile solution for rigorous device-independent certification that does not rely on the i.i.d. assumption. Specifically, we describe how the prediction-based ratio (PBR) protocol and martingale-based protocol developed for hypothesis testing can be applied in the present context to achieve a device-independent certification of desirable properties with confidence interval (CI). To illustrate the versatility of these methods, we demonstrate how we can use them to certify—with finite data—the underlying negativity, Hilbert space dimension, entanglement depth, and fidelity to some target pure state. In particular, we provide examples showing how the amount of certifiable negativity and fidelity scales with the number of trials and how many experimental trials one needs to certify a qutrit state space or the presence of genuine tripartite entanglement. Overall, we have found that the PBR protocol and the martingale-based protocol often offer similar performance, even though the latter does have to presuppose any witness (Bell-like inequality). In contrast, our findings also show that the performance of the martingale-based protocol may be severely affected by one’s choice of Bell-like inequality. Intriguingly, a Bell function useful for self-testing does not necessarily give the optimal confidence-gain rate for certifying the fidelity to the corresponding target state.
The proper analysis of quantum experiments is an indispensable part in the development of quantum technologies. However, it is not trivial to reliably characterize a quantum setup, which may include, e.g., measurement and state-preparation devices. Moreover, imperfections in the experimental setup can easily result in a mismatch [1–3] between the characterization tools developed for an idealized situation and an actual experimental situation. However, we can circumvent this problem by the so-called “device-independent approach” [4, 5]. In quantum information, the term “device-independent” (DI) was first coined [6] in the task of quantum key distribution [7–9], even though the idea was already perceived independently but implicitly in [10, 11].
In a nutshell, the DI approach is a framework for analyzing physical systems without relying on any assumption about the degrees of freedom measured. Its basis is Bell nonlocality [5, 12], which shows that no local-hidden-variable (LHV) theory can reproduce all quantum predictions, even though no further assumption is made about the details of such a theory. For example, it is known that the violation of Bell inequalities [12] obtained by locally measuring a shared state implies [13] shared entanglement [14], which is a powerful resource in many quantum information processing tasks. More generally, many other desirable properties of the underlying state [15–23], measurements [22–28], and channel [21, 29, 30] may be derived directly from the observation of a Bell inequality-violating correlation between measurement outcomes. Recently, the DI approach has also been incorporated into the security analysis of quantum secure direct communication; see, for example, [31] and references therein.
However, due to statistical fluctuations, even when the experimental trials are independent and identically distributed (i.i.d.), relative frequencies of the measurement outcomes obtained from a Bell experiment do not faithfully represent the underlying distribution. In particular, such raw distributions estimated from the experimental results typically [32–34] lead to a violation of the nonsignaling conditions [35, 36], which is a prerequisite for the analysis shown in [16–30]. In other words, statistical fluctuations render many theoretical tools developed for such a purpose inapplicable. To address this issue, some ad hoc methods [32–34] have been proposed to regularize the relative frequencies obtained to ensure that the resulting distribution satisfy the nonsignaling conditions. In [37], a more in-depth discussion was provided, and two better-motivated regularization methods were proposed.
Although these more recent attempts do provide a point estimator that fits within the framework of the usual DI analysis, they are still problematic in two aspects. First, they do not provide any confidence region associated with the estimate. However, any real experiment necessarily involves only a finite number of experimental trials. Therefore a useful analysis should provide not only an estimate but also an indication of the reliability of such an estimate. In many of the Bell experiments reported [38–41], this is achieved by reporting the standard deviations of Bell violations. However, for finite, especially relatively small numbers of trials, the central limit theorem is not warranted, so the usual interpretation of standard deviations may become dubious. Second, these usual approaches and those that provide a DI point estimator [32–34, 37] implicitly assume that the experimental trials are i.i.d. and hence free of the memory effect [42, 43] (see more discussions in [5, 44–46]). Again, in a realistic experimental setting, the i.i.d. assumption may be difficult to justify.
For the tasks of DI randomness expansion [47, 48] and DI quantum key distribution [49, 50], specific tools [51–59] have been developed to overcome the abovementioned problems. Here, we are interested in providing a general solution to other device-independent certification tasks1 that 1) can provide a confidence region and two) does not a priori require the i.i.d. assumption. Our approach is inspired by the prediction-based ratio (PBR) protocol developed in [60] and the martingale-based method proposed by Gill [43, 61] for performing a hypothesis testing against the assumption of Bell locality. Following [62], we further adapt these earlier methods and illustrate how they can be used for the device-independent certification of various properties of interest, including the underlying amount of entanglement and its fidelity with respect to some target quantum state.
To this end, we structure the rest of this paper as follows. In Section 2.1, we explain the basic concepts relevant to the understanding of DI certification in the ideal setting. After that, we introduce in Section 2.2 our adapted statistical tools for performing a rigorous device-independent certification. Results obtained from these tools are then presented in Section 3.1. Finally, we provide some concluding remarks and future directions in Section 4.
The starting point of the DI approach is a Bell test. To this end, a bipartite Bell scenario was considered, where two observers, Alice and Bob, can choose, respectively, their measurements labeled by
For example, correlations that can be produced in an LHV theory have to satisfy a Bell inequality:
where the Bell coefficients
where
In an actual Bell test, the measurement settings ought to be chosen randomly according to some predetermined distributions
where
or equivalently, in terms of the correlator
where
In contrast, quantum theory allows correlations that cannot be cast in the form of Equation 2. In fact, in a bipartite Bell test, general quantum correlations read as
where
For the CHSH Bell function, cf. Equation 4, quantum theory dictates the upper bound as
which can be seen as a Bell-like inequality. Other Bell and Bell-like inequalities relevant to this work will be presented in the corresponding sections below.
As mentioned above, with local measurements on a quantum system, a Bell inequality-violating correlation
For a bipartite density operator
where
As an explicit example, note that an observed violation of the CHSH Bell inequality of Equation 5 gives the following nontrivial negativity lower bound of the underlying state
In addition, it is worth noting that if
From Equations 5, 8 and 10, nonetheless, we see that a violation of the CHSH Bell inequality can never witness a local Hilbert space dimension
where
In a many-body system, entanglement can occur in various forms or structures [73]. In particular, an
For illustration, consider the expectation value of the Mermin Bell function [78]
where
Then, it is known [19] that the following Bell-like inequalities hold, respectively, for fully separable states, 2-producible [76] tripartite quantum states (i.e., quantum states that can be generated using only two-body entanglement), and general tripartite quantum states:
The strongest form of device certification one can hope for within a DI paradigm is called self-testing [79], which was first proposed in [10]. The key observation behind this feat is that the quantum strategy compatible with certain extremal quantum correlations
For instance, it is long known [82–85] that the maximal CHSH Bell-inequality violation of
where the respective POVM elements (with
Moreover, to obtain the maximal CHSH Bell-inequality violation for a partially entangled two-qubit state,
it suffices [72] to consider
thereby giving
Interestingly, the resulting correlation also self-tests [86, 87] the corresponding quantum strategy of Equation 17a, b and maximally violate the family of tilted CHSH Bell inequalities for
giving
In practice, however, due to various imperfections, one can, at best, attain a correlation close to the ideal correlation
with the help of an SDP outer approximation of the quantum set
which is extracted from the underlying quantum state
At this point, it is worth noting that for all the three properties
we obtain an SDP that characterizes the set of correlations attainable by quantum states having a negativity upper-bound by
On the other hand, if we drop the constraint of Equation 9b, but imposes additional positive-partial-transposition constraints, then we obtain an SDP characterization of the set
Having understood how DI certification can be achieved from a given correlation
Null Hypothesis 1.
Since such a hypothesis involves a set of (rather than a single) compatible distribution
Then, we apply appropriate methods for this kind of hypothesis testing on the collected data to determine an upper bound
Of course, one may also be interested to understand how quickly statistical evidence (against a hypothesis
where
We shall start with the martingale-based protocol, pioneered by Gill in [43, 61], for testing against LHV theories, and further developed in [60, 90]. The protocol relies on the observation of the (super)martingale structure in some random variables of interest. To employ the martingale-based protocol, one has to fix a Bell function
may be violated by some quantum correlation
Let
where, for simplicity, we have suppressed the dependency of
It is worth noting that the martingale-based
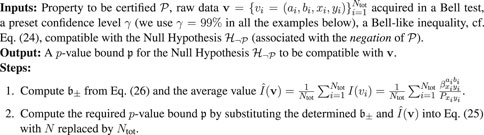
Figure 1. Pseudocode associated with the martingale-based protocol for DI certification. If the
Let
The other hypothesis-testing protocol that we consider in this work is based on the so-called PBR protocol proposed in [60] (see also [90]). In contrast with a martingale-based protocol, the PBR protocol does not need to presuppose any Bell-like inequality for determining a
where
The key idea of the PBR protocol is to use this relative frequency
An important point to note now is that if the composite null hypothesis
The unique [37] minimizer
which gives the optimized Bell-like inequality
where the product is only carried out over the remaining
Several remarks are now in order. First, if none of the entries in
Next, notice that
Another important feature of the PBR protocol is that the optimized inequality characterized by
where
where

Figure 3. Pseudocode associated with the PBR protocol for DI certification. If the
Finally, note that for an ideal Bell test giving the correlation
which may be obtained by solving Equation 29 with
We are now ready to present our simulations results involving a finite number of trials. Throughout this section, the results presented for finite trials consist of an average over 30 complete Bell tests, each involving
Our first example consists of a Bell test based on the quantum strategy presented in Equations 15a, b, c, which leads to a CHSH Bell value of
Specifically, for the martingale-based protocol, we use Equation 25 with the CHSH Bell expression of Equation 4. In this case,
On the other hand, for the PBR protocol, the optimizing distribution
where
Figure 4 shows the average amount of certifiable negativity from these two methods as a function of the number of trials
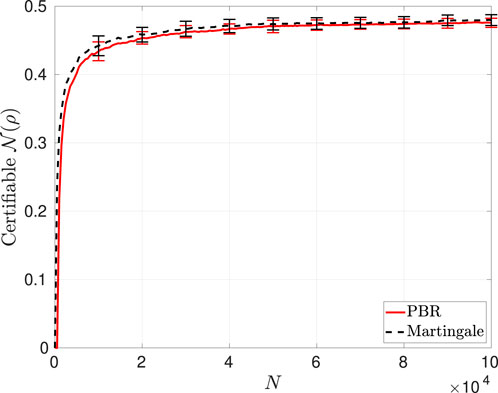
Figure 4. Negativity certifiable from the data observed in a Bell test generating
These results clearly suggest that the CHSH Bell function of Equation 4 is optimal for certifying the underlying negativity of
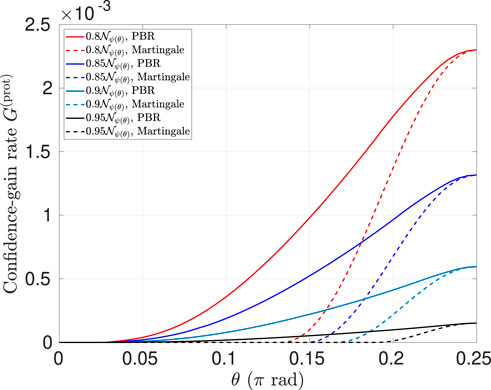
Figure 5. Asymptotic confidence-gain rate
As mentioned in Section 2.1.2.1, the correlation
with the local measurements
where
Next, we use the data numerically simulated from
where the CGLMP Bell coefficients
Figure 6 shows that with approximately
and numerically maximize their CGLMP Bell-inequality violation using the heuristic algorithm given in [94]. We denote the corresponding correlation by
Figure 6. Negativity certifiable from the data observed in a Bell test generating
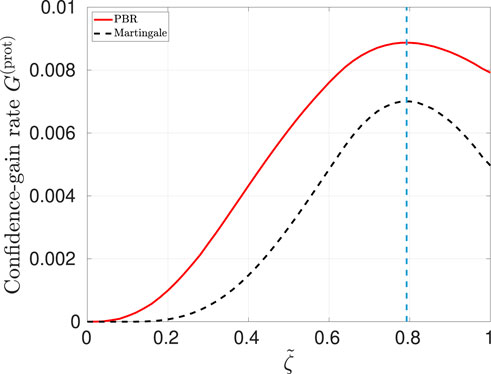
Figure 7. Asymptotic confidence-gain rate
Interestingly, even though Figure 6 suggests that the CGLMP Bell function is very effective in providing a good
Next, we consider the tripartite correlation
on the Greenberger–Horne–Zeilinger (GHZ) state [95, 96]:
It is easy to verify that
Null Hypothesis 2.
Null Hypothesis 3.
For the martingale-based method, we use Equation 25 with the Mermin Bell expression of Equation 12 and the bounds given in Equation 14, i.e.,
where
On the other hand, notice that 2-producibility [76] is equivalent to biseparability [14] in the tripartite scenario. Hence, for Null Hypothesis 3, we obtain the corresponding optimizing distribution by solving
where
for the computation of the test statistic
For
for the separable hypothesis
for the 2-producible hypothesis
Our last examples concern the DI certification of a lower bound on the fidelity of the swapped state
Null Hypothesis 4.
Then, for any given
where the left-hand side of the last inequality in Equation 51b consists of some specific linear combination of entries of
to determine
Let us start with the self-testing of a Bell state, corresponding to
Interestingly, our results show that the martingale-based protocol with the CHSH Bell function of Equation 4 again performs very well for the self-testing of a Bell state with finite statistics, even though our computation of the corresponding asymptotic confidence-gain rate for
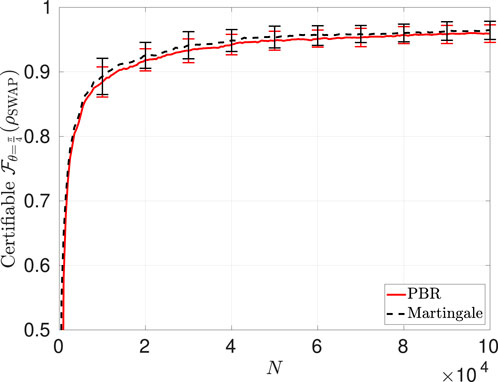
Figure 8. Certifiable fidelity
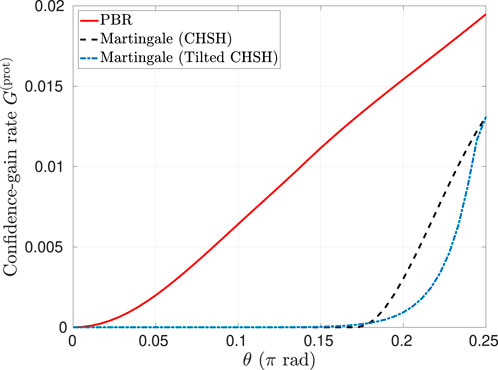
Figure 9. Asymptotic confidence-gain rate
The advantage of a fidelity certification based on the SWAP method [86, 88] is that the technique is applicable to a general Bell scenario. However, in the simplest CHSH Bell scenario, it is known that a much tighter lower bound on the Bell-state fidelity can be obtained by considering a more general extraction map. Specifically, Kaniewski showed in [97] that
where
To take the advantage of Equation 53, we can first perform hypothesis testing based on the following null hypothesis.
Null Hypothesis 5.
Specifically, using the same set of data generated for the analysis in Sections 3.1.1.1 and 3.1.3, we perform composite hypothesis testing for Null Hypothesis 5 with
In particular, for the martingale-based protocol, we can simply use Equation 25 with
with or without imposing the SDP constraints of Equation 9c. The results obtained from these tests are shown in Figure 10.
Using each lower bound on
It is also worth noting that in computing these PBR bounds, the computation may be further simplified by regularizing the relative frequency
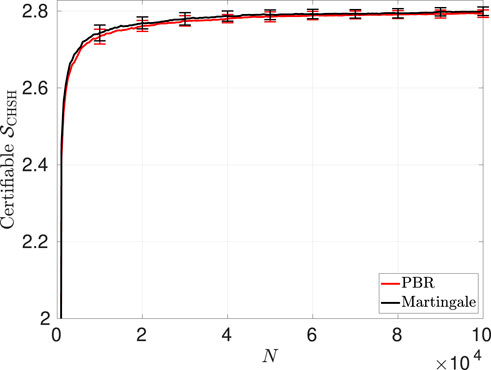
Figure 10. Certifiable Bell-CHSH violation
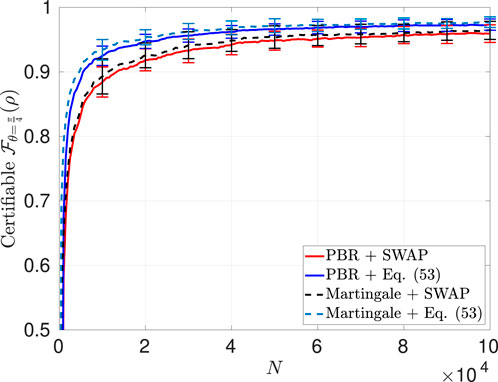
Figure 11. Comparison of the Bell-state fidelity certifiable via the SWAP-based approach presented in Section 3.1.3 and that using Equations 54a, b and
Tomography and witnesses are two commonly employed toolkits for certifying the desirable properties of quantum devices [98]. In recent years, the device-independent paradigm has offered an appealing alternative to these conventional means as it involves only a minimal set of assumptions. Nonetheless, many DI certification schemes, e.g., [16–19, 21–27, 29, 30], implicitly assumes that the underlying quantum correlation
To this end, very specialized tools have been developed for the task of randomness generation, quantum key distributions, and the self-testing [86, 99, 100] of quantum states. Among them, the possibility of using hypothesis testing (based on the PBR protocol [60]) for self-testing with finite data was first discussed in [86] (see also [99] for a different approach). Meanwhile, it is long known [43, 61, 90] that hypothesis testing in a Bell test can also be carried out using a martingale-based protocol. Here, we demonstrate the viability and versatility of such hypothesis-testing-based approaches for the general problem of DI certification.
Central to our finding is the observation that many desirable quantum properties
In this paper, we explain in detail how the two aforementioned hypothesis-testing protocols can be adapted for the DI certification of desirable properties. Specifically, we illustrate how we can use them to perform the DI certification of the underlying negativity [64], local Hilbert space dimension [15], entanglement depth [76]; [77], and fidelity to some target two-qubit entangled pure state
In the i.i.d. setting, the PBR protocol is known to be asymptotically optimal (in terms of its confidence-gain rate). However, we see from Figures 4, 6, 8 that for a relatively small number of trials and with the right choice of the Bell function, the martingale-based protocol performs equally well, if not better. A similar observation was also noted in [101] where the authors therein compare the PBR method with the Chernoff–Hoeffding bound in determining the success probability of Bernoulli trials. In our case, this is not surprising as the PBR method does not presuppose a Bell-like inequality but rather sacrifices some of the data to determine one. Indeed, if we equip the PBR protocol with the optimized Bell-like inequality right from the beginning, its performance is, as expected, no worse than the martingale-based protocol; see Supplementary Figures S1, S2, S4-S7 for some explicit examples.
Meanwhile, we also see from Figures 5, 7, 9 that for several cases that we have investigated, one’s intuitive choice of the Bell function for the martingale-based method can lead to a relatively poor confidence-gain rate and hence impairs its efficiency to produce a good
Several research directions naturally follow from the present work. First, there are the scalability questions: 1) how do the number of measurement bases and 2) the number of samples scale with the complexity (say, dimension) of the measured system? The former is again closely related to the general viability of the device-independent certification approach, where our understanding is far from complete. As for the latter, we remark that it is indeed one of the goals of the present work to shed light on the sample complexity of our hypothesis-testing-based approaches. In some cases, such as the certification from the GHZ correlation, we see that hundreds of trials suffice, but in some others, several tens of thousands may be required to give a satisfactory level of certification. Still, some general understanding of how the sample size scales with the properties to be certified and the confidence level will be surely welcome.
Second, for experimental trials expected to deviate significantly from being i.i.d., one should choose a much smaller block size
Given that self-testing with a high fidelity is technically challenging, it is still of interest to devise a general recipe for certifying the average behavior of other more specific properties (such as entanglement and steerability), which may already be sufficient for the specific information processing task at hand. However, note that the rejection of a null hypothesis on the average behavior (e.g., average negativity
In addition, it is worth noting that if the i.i.d. assumption is somehow granted, then our protocols also certify the quality of the setup for every single runs, including those that have not been measured. In this case, once a sufficiently small
The raw data supporting the conclusions of this article are available in the Supplementary Material.
W-GC: data curation, investigation, software, writing–original draft, and writing–review and editing. K-CC: data curation, investigation, software, and writing–original draft. K-SC: data curation, investigation, software, validation, and writing–review and editing. S-LC: investigation, validation, writing–review and editing, formal analysis, and software. Y-CL: conceptualization, formal analysis, funding acquisition, investigation, methodology, project administration, software, supervision, validation, writing–review and editing, and visualization.
The author(s) declare that financial support was received for the research and/or publication of this article. This work is supported by the National Science and Technology Council, Taiwan (Grants Nos 107-2112-M-006-005-MY2, 109-2112-M-006-010-MY3, 112-2628-M-006-007-MY4, 111-2119-M-001-004, 112-2119-M-001-006, and 111-2112-M-005-007-MY4), the Higher Education Sprout Project, Ministry of Education to the Headquarters of University Advancement at the National Cheng Kung University (NCKU), the National Center for Theoretical Sciences, the 2024 Academia Sinica Investigator Award (AS-IA-110-M02), and the Foxconn Research Institute, Taipei, Taiwan.
The authors are grateful to Jean-Daniel Bancal, Gelo Tabia, and Yanbao Zhang for many enlightening discussions and to an anonymous referee for helpful suggestions.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fphy.2024.1434095/full#supplementary-material
1Note that the same task is called device-independent verification in [102].
2If a third party is involved in the Bell test, as in the case of 2.1.2.2, and 3.1.2, we denote by
3Here, the inequality is optimized in the sense that it provides the largest possible asymptotic confidence-gain rate, cf. Equation 23.
1. Rosset D, Ferretti-Schöbitz R, Bancal JD, Gisin N, Liang YC. Imperfect measurement settings: implications for quantum state tomography and entanglement witnesses. Phys Rev A (2012) 86:062325. doi:10.1103/PhysRevA.86.062325
2. Moroder T, Kleinmann M, Schindler P, Monz T, Gühne O, Blatt R. Certifying systematic errors in quantum experiments. Phys Rev Lett (2013) 110:180401. doi:10.1103/PhysRevLett.110.180401
3. van Enk SJ, Blume-Kohout R. When quantum tomography goes wrong: drift of quantum sources and other errors. New J. Phys (2013) 15:025024. doi:10.1088/1367-2630/15/2/025024
4. Scarani V. The device-independent outlook on quantum physics. Acta Phys Slovaca (2012) 62:347. doi:10.2478/v10155-012-0003-4
5. Brunner N, Cavalcanti D, Pironio S, Scarani V, Wehner S. Bell nonlocality. Rev Mod Phys (2014) 86:419–78. doi:10.1103/RevModPhys.86.419
6. Acín A, Gisin N, Masanes L. From Bell’s theorem to secure quantum key distribution. Phys Rev Lett (2006) 97:120405. doi:10.1103/PhysRevLett.97.120405
7. Bennett CH, Brassard G. Quantum cryptography: public key distribution and coin tossing. Theor Comput Sci (2014) 560:7–11. doi:10.1016/j.tcs.2014.05.025
8. Ekert AK. Quantum cryptography based on Bell’s theorem. Phys Rev. Lett (1991) 67:661–3. doi:10.1103/PhysRevLett.67.661
9. Gisin N, Ribordy G, Tittel W, Zbinden H. Quantum cryptography. Rev Mod Phys (2002) 74:145–95. doi:10.1103/RevModPhys.74.145
10. Mayers D, Yao A. Quantum cryptography with imperfect apparatus. In: Proceedings 39th annual symposium on foundations of computer science (cat. No.98CB36280) (1998). p. 503–9. doi:10.1109/SFCS.1998.743501
11. Mayers D, Yao A. Self testing quantum apparatus. Quan Info Comput (2004) 4:273–86. doi:10.26421/qic4.4-3
12. Bell JS. On the Einstein Podolksy Rosen paradox. Physics (1964) 1:195–200. doi:10.1103/PhysicsPhysiqueFizika.1.195
13. Werner RF. Quantum states with Einstein-Podolsky-Rosen correlations admitting a hidden-variable model. Phys Rev A (1989) 40:4277–81. doi:10.1103/PhysRevA.40.4277
14. Horodecki R, Horodecki P, Horodecki M, Horodecki K. Quantum entanglement. Rev Mod Phys (2009) 81:865–942. doi:10.1103/RevModPhys.81.865
15. Brunner N, Pironio S, Acin A, Gisin N, Méthot AA, Scarani V. Testing the dimension of Hilbert spaces. Phys Rev Lett (2008) 100:210503. doi:10.1103/PhysRevLett.100.210503
16. Bancal JD, Gisin N, Liang YC, Pironio S. Device-independent witnesses of genuine multipartite entanglement. Phys Rev Lett (2011) 106:250404. doi:10.1103/PhysRevLett.106.250404
17. Moroder T, Bancal JD, Liang YC, Hofmann M, Gühne O. Device-independent entanglement quantification and related applications. Phys Rev Lett (2013) 111:030501. doi:10.1103/PhysRevLett.111.030501
18. Tóth G, Moroder T, Gühne O. Evaluating convex roof entanglement measures. Phys Rev Lett (2015) 114:160501. doi:10.1103/PhysRevLett.114.160501
19. Liang YC, Rosset D, Bancal JD, Pütz G, Barnea TJ, Gisin N. Family of Bell-like inequalities as device-independent witnesses for entanglement depth. Phys Rev Lett (2015) 114:190401. doi:10.1103/PhysRevLett.114.190401
20. Arnon-Friedman R, Bancal JD. Device-independent certification of one-shot distillable entanglement. New J Phys (2019) 21:033010. doi:10.1088/1367-2630/aafef6
21. Chen SL, Ku HY, Zhou W, Tura J, Chen YN. Robust self-testing of steerable quantum assemblages and its applications on device-independent quantum certification. Quantum (2021) 5:552. doi:10.22331/q-2021-09-28-552
22. Chen SL, Budroni C, Liang YC, Chen YN. Natural framework for device-independent quantification of quantum steerability, measurement incompatibility, and self-testing. Phys Rev Lett (2016) 116:240401. doi:10.1103/PhysRevLett.116.240401
23. Chen SL, Budroni C, Liang YC, Chen YN. Exploring the framework of assemblage moment matrices and its applications in device-independent characterizations. Phys Rev A (2018) 98:042127. doi:10.1103/PhysRevA.98.042127
24. Bancal JD, Sangouard N, Sekatski P. Noise-resistant device-independent certification of Bell state measurements. Phys Rev Lett (2018) 121:250506. doi:10.1103/PhysRevLett.121.250506
25. Renou MO, Kaniewski J, Brunner N. Self-testing entangled measurements in quantum networks. Phys Rev Lett (2018) 121:250507. doi:10.1103/PhysRevLett.121.250507
26. Quintino MT, Budroni C, Woodhead E, Cabello A, Cavalcanti D. Device-independent tests of structures of measurement incompatibility. Phys Rev Lett (2019) 123:180401. doi:10.1103/PhysRevLett.123.180401
27. Wagner S, Bancal JD, Sangouard N, Sekatski P. Device-independent characterization of quantum instruments. Quantum (2020) 4:243. doi:10.22331/q-2020-03-19-243
28. Chen SL, Miklin N, Budroni C, Chen YN. Device-independent quantification of measurement incompatibility. Phys Rev Res (2021) 3:023143. doi:10.1103/PhysRevResearch.3.023143
29. Sekatski P, Bancal JD, Wagner S, Sangouard N. Certifying the building blocks of quantum computers from Bell’s theorem. Phys Rev Lett (2018) 121:180505. doi:10.1103/PhysRevLett.121.180505
30. Sekatski P, Bancal JD, Ioannou M, Afzelius M, Brunner N. Toward the device-independent certification of a quantum memory. Phys Rev Lett (2023) 131:170802. doi:10.1103/PhysRevLett.131.170802
31. Zhou L, Sheng YB, Long GL. Device-independent quantum secure direct communication against collective attacks. Sci Bull (2020) 65:12–20. doi:10.1016/j.scib.2019.10.025
32. Bernhard C, Bessire B, Montina A, Pfaffhauser M, Stefanov A, Wolf S. Non-locality of experimental qutrit pairs. J Phys A: Math Theo (2014) 47:424013. doi:10.1088/1751-8113/47/42/424013
33. Bancal JD, Sheridan L, Scarani V. More randomness from the same data. New J. Phys (2014) 16:033011. doi:10.1088/1367-2630/16/3/033011
34. Schwarz S, Bessire B, Stefanov A, Liang YC. Bipartite Bell inequalities with three ternary-outcome measurements—from theory to experiments. New J. Phys (2016) 18:035001. doi:10.1088/1367-2630/18/3/035001
35. Popescu S, Rohrlich D. Quantum nonlocality as an axiom. Found Phys (1994) 24:379–85. doi:10.1007/BF02058098
36. Barrett J, Linden N, Massar S, Pironio S, Popescu S, Roberts D. Nonlocal correlations as an information-theoretic resource. Phys Rev A (2005) 71:022101. doi:10.1103/PhysRevA.71.022101
37. Lin PS, Rosset D, Zhang Y, Bancal JD, Liang YC. Device-independent point estimation from finite data and its application to device-independent property estimation. Phys Rev A (2018) 97:032309. doi:10.1103/PhysRevA.97.032309
38. Aspect A, Dalibard J, Roger G. Experimental test of Bell’s inequalities using time-varying analyzers. Phys Rev Lett (1982) 49:1804–7. doi:10.1103/PhysRevLett.49.1804
39. Tittel W, Brendel J, Zbinden H, Gisin N. Violation of Bell inequalities by photons more than 10 km apart. Phys Rev Lett (1998) 81:3563–6. doi:10.1103/PhysRevLett.81.3563
40. Weihs G, Jennewein T, Simon C, Weinfurter H, Zeilinger A. Violation of Bell’s inequality under strict einstein locality conditions. Phys Rev Lett (1998) 81:5039–43. doi:10.1103/PhysRevLett.81.5039
41. Rowe M, Kielpinski D, Meyer V, Sackett CA, Itano WM, Monroe C, et al. Experimental violation of a Bell’s inequality with efficient detection. Nature (2001) 409:791–4. doi:10.1038/35057215
42. Barrett J, Collins D, Hardy L, Kent A, Popescu S. Quantum nonlocality, Bell inequalities, and the memory loophole. Phys Rev A (2002) 66:042111. doi:10.1103/PhysRevA.66.042111
43. Gill RD Accardi contra Bell (cum mundi): the impossible coupling, 42. Beachwood, OH: Lecture Notes-Monograph Series (2003). 133–54.
44. Hensen B, Bernien H, Dreau AE, Reiserer A, Kalb N, Blok MS, et al. Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres. Nature (2015) 526:682–6. doi:10.1038/nature15759
45. Shalm LK, Meyer-Scott E, Christensen BG, Bierhorst P, Wayne MA, Stevens MJ, et al. Strong loophole-free test of local realism. Phys Rev Lett (2015) 115:250402. doi:10.1103/PhysRevLett.115.250402
46. Giustina M, Versteegh MAM, Wengerowsky S, Handsteiner J, Hochrainer A, Phelan K, et al. Significant-loophole-free test of Bell’s theorem with entangled photons. Phys Rev Lett (2015) 115:250401. doi:10.1103/PhysRevLett.115.250401
47. Colbeck R. Quantum and relativistic protocols for secure multi-party computation. Cambridge, United Kingdom: University of Cambridge (2006). Ph.D. thesis.
48. Pironio S, Acín A, Massar S, de la Giroday AB, Matsukevich DN, Maunz P, et al. Random numbers certified by Bell’s theorem. Nature (2010) 464:1021–4. doi:10.1038/nature09008
49. Acín A, Brunner N, Gisin N, Massar S, Pironio S, Scarani V. Device-independent security of quantum cryptography against collective attacks. Phys Rev Lett (2007) 98:230501. doi:10.1103/PhysRevLett.98.230501
50. Pironio S, Acín A, Brunner N, Gisin N, Massar S, Scarani V. Device-independent quantum key distribution secure against collective attacks. New J. Phys (2009) 11:045021. doi:10.1088/1367-2630/11/4/045021
51. Pironio S, Massar S. Security of practical private randomness generation. Phys Rev A (2013) 87:012336. doi:10.1103/PhysRevA.87.012336
52. Nieto-Silleras O, Bamps C, Silman J, Pironio S. Device-independent randomness generation from several Bell estimators. New J. Phys (2018) 20:023049. doi:10.1088/1367-2630/aaaa06
53. Bierhorst P, Knill E, Glancy S, Zhang Y, Mink A, Jordan S, et al. Experimentally generated randomness certified by the impossibility of superluminal signals. Nature (2018) 556:223–6. doi:10.1038/s41586-018-0019-0
54. Bourdoncle B, Lin PS, Rosset D, Acín A, Liang YC. Regularising data for practical randomness generation. Quan Sci Technol (2019) 4:025007. doi:10.1088/2058-9565/ab01e8
55. Zhang Y, Fu H, Knill E. Efficient randomness certification by quantum probability estimation. Phys Rev Res (2020) 2:013016. doi:10.1103/PhysRevResearch.2.013016
56. Knill E, Zhang Y, Bierhorst P. Generation of quantum randomness by probability estimation with classical side information. Phys Rev Res (2020) 2:033465. doi:10.1103/physrevresearch.2.033465
57. Metger T, Fawzi O, Sutter D, Renner R. Generalised entropy accumulation. In: 2022 IEEE 63rd annual symposium on foundations of computer science (FOCS) (2022). p. 844–50. doi:10.1109/FOCS54457.2022.00085
58. Arnon-Friedman R, Renner R, Vidick T. Simple and tight device-independent security proofs. SIAM J Comput (2019) 48:181–225. doi:10.1137/18m1174726
59. Dupuis F, Fawzi O, Renner R. Entropy accumulation. Commun Math Phys (2020) 379:867–913. doi:10.1007/s00220-020-03839-5
60. Zhang Y, Glancy S, Knill E. Asymptotically optimal data analysis for rejecting local realism. Phys Rev A (2011) 84:062118. doi:10.1103/PhysRevA.84.062118
61. Gill RD Time, finite statistics, and Bell’s fifth position, 5. Växjö, Sweden: Math. Modelling in Phys. Engi., and Cog. Sc. (2003). p. 179–206. Proc. Foundations of Probability and Physics-2 (Växjö: Växjö University Press).
62. Liang YC, Zhang Y. Bounding the plausibility of physical theories in a device-independent setting via hypothesis testing. Entropy (2019) 21:185. doi:10.3390/e21020185
63. Clauser JF, Horne MA, Shimony A, Holt RA. Proposed experiment to test local hidden-variable theories. Phys Rev Lett (1969) 23:880–4. doi:10.1103/PhysRevLett.23.880
64. Vidal G, Werner RF. Computable measure of entanglement. Phys Rev A (2002) 65:032314. doi:10.1103/PhysRevA.65.032314
65. Peres A. Separability criterion for density matrices. Phys Rev Lett (1996) 77:1413–5. doi:10.1103/PhysRevLett.77.1413
66. Navascués M, Pironio S, Acín A. Bounding the set of quantum correlations. Phys Rev Lett (2007) 98:010401. doi:10.1103/PhysRevLett.98.010401
67. Navascués M, Pironio S, Acín A. A convergent hierarchy of semidefinite programs characterizing the set of quantum correlations. New J. Phys (2008) 10:073013. doi:10.1088/1367-2630/10/7/073013
68. Doherty AC, Liang YC, Toner B, Wehner S. The quantum moment problem and bounds on entangled multi-prover games. 23rd Annu IEEE Conf. Comput Comp 2008, Ccc’08 (2008) 199–210. doi:10.1109/CCC.2008.26
69. Collins D, Gisin N, Linden N, Massar S, Popescu S. Bell inequalities for arbitrarily high-dimensional systems. Phys. Rev. Lett. (2002) 88:040404. doi:10.1103/PhysRevLett.88.040404
70. Kaszlikowski D, Kwek LC, Chen JL, Żukowski M, Oh CH. Clauser-Horne inequality for three-state systems. Phys Rev A (2002) 65:032118. doi:10.1103/PhysRevA.65.032118
71. Acín A, Durt T, Gisin N, Latorre JI. Quantum nonlocality in two three-level systems. Phys Rev A (2002) 65:052325. doi:10.1103/PhysRevA.65.052325
72. Liang YC. Correlations, Bell inequality violation and quantum entanglement. Bribsane, Australia: University of Queensland (2008). Ph.D. thesis.
73. Lu H, Zhao Q, Li ZD, Yin XF, Yuan X, Hung JC, et al. Entanglement structure: entanglement partitioning in multipartite systems and its experimental detection using optimizable witnesses. Phys Rev X (2018) 8:021072. doi:10.1103/PhysRevX.8.021072
74. Bancal JD, Barrett J, Gisin N, Pironio S. Definitions of multipartite nonlocality. Phys Rev A (2013) 88:014102. doi:10.1103/PhysRevA.88.014102
75. Curchod FJ, Gisin N, Liang YC. Quantifying multipartite nonlocality via the size of the resource. Phys Rev A (2015) 91:012121. doi:10.1103/PhysRevA.91.012121
76. Gühne O, Tóth G, Briegel HJ. Multipartite entanglement in spin chains. New J. Phys (2005) 7:229. doi:10.1088/1367-2630/7/1/229
77. Sørensen AS, Mølmer K. Entanglement and extreme spin squeezing. Phys Rev Lett (2001) 86:4431–4. doi:10.1103/PhysRevLett.86.4431
78. Mermin ND. Extreme quantum entanglement in a superposition of macroscopically distinct states. Phys Rev Lett (1990) 65:1838–40. doi:10.1103/PhysRevLett.65.1838
79. Šupić I, Bowles J. Self-testing of quantum systems: a review. Quantum (2020) 4:337. doi:10.22331/q-2020-09-30-337
80. Jebarathinam C, Hung JC, Chen SL, Liang YC. Maximal violation of a broad class of Bell inequalities and its implication on self-testing. Phys Rev Res (2019) 1:033073. doi:10.1103/PhysRevResearch.1.033073
81. Kaniewski J. Weak form of self-testing. Phys Rev Res (2020) 2:033420. doi:10.1103/PhysRevResearch.2.033420
82. Summers SJ, Werner R. Maximal violation of Bell’s inequalities is generic in quantum field theory. Commun Math Phys (1987) 110:247–59. doi:10.1007/BF01207366
83. Popescu S, Rohrlich D. Which states violate Bell’s inequality maximally? Phys Lett A (1992) 169:411–4. doi:10.1016/0375-9601(92)90819-8
84. Braunstein SL, Mann A, Revzen M. Maximal violation of Bell inequalities for mixed states. Phys Rev Lett (1992) 68:3259–61. doi:10.1103/PhysRevLett.68.3259
85. Tsirelson BS. Some results and problems on quantum Bell-type inequalities. Hadronic J. Suppl (1993) 8:329–45.
86. Bancal JD, Navascués M, Scarani V, Vértesi T, Yang TH. Physical characterization of quantum devices from nonlocal correlations. Phys Rev A (2015) 91:022115. doi:10.1103/PhysRevA.91.022115
87. Yang TH, Navascués M. Robust self-testing of unknown quantum systems into any entangled two-qubit states. Phys Rev A (2013) 87:050102. doi:10.1103/PhysRevA.87.050102
88. Yang TH, Vértesi T, Bancal JD, Scarani V, Navascués M. Robust and versatile black-box certification of quantum devices. Phys Rev Lett (2014) 113:040401. doi:10.1103/PhysRevLett.113.040401
89. van Dam W, Gill R, Grunwald P. The statistical strength of nonlocality proofs. IEEE Trans Inf Theor (2005) 51:2812–35. doi:10.1109/TIT.2005.851738
90. Zhang Y, Glancy S, Knill E. Efficient quantification of experimental evidence against local realism. Phys Rev A (2013) 88:052119. doi:10.1103/PhysRevA.88.052119
91. Kullback S, Leibler RA. On information and sufficiency. Ann Math Stat (1951) 22:79–86. doi:10.1214/aoms/1177729694
93. Minka T. The lightspeed Matlab toolbox (2017). Available from: https://github.com/tminka/lightspeed (Accessed October 15 2024).
94. Liang YC, Doherty AC. Bounds on quantum correlations in Bell-inequality experiments. Phys Rev A (2007) 75:042103. doi:10.1103/PhysRevA.75.042103
95. Greenberger DM, Horne MA, Zeilinger A. Bell’s theorem, quantum theory and conceptions of the universe. Dordrecht: Kluwer: Going Beyond Bell’s Theorem (1989). p. 69–72.
97. Kaniewski J. Analytic and nearly optimal self-testing bounds for the Clauser-Horne-Shimony-Holt and Mermin inequalities. Phys Rev Lett (2016) 117:070402. doi:10.1103/PhysRevLett.117.070402
98. Eisert J, Hangleiter D, Walk N, Roth I, Markham D, Parekh R, et al. Quantum certification and benchmarking. Nat Rev Phys (2020) 2:382–90. doi:10.1038/s42254-020-0186-4
99. Tan TR, Wan Y, Erickson S, Bierhorst P, Kienzler D, Glancy S, et al. Chained Bell inequality experiment with high-efficiency measurements. Phys Rev Lett (2017) 118:130403. doi:10.1103/PhysRevLett.118.130403
100. Bancal JD, Redeker K, Sekatski P, Rosenfeld W, Sangouard N. Self-testing with finite statistics enabling the certification of a quantum network link. Quantum (2021) 5:401. doi:10.22331/q-2021-03-02-401
101. Wills P, Knill E, Coakley K, Zhang Y. Performance of test supermartingale confidence intervals for the success probability of Bernoulli trials. J. Res Natl Inst Stan (2020) 125:125003. doi:10.6028/jres.125.003
102. Gočanin A, Šupić I, Dakić B. Sample-efficient device-independent quantum state verification and certification. PRX Quan (2022) 3:010317. doi:10.1103/PRXQuantum.3.010317
103. Zhang Y, Seshadri A, Knill E. Confidence-interval construction with non-i.i.d. spot-checking trials and its application in quantum information. Optica Quantum 2.0 Conference and Exhibition. Denver, Colorado: Optica Publishing Group (2023). Technical Digest Series, QTu3A.20. doi:10.1364/QUANTUM.2023.QTu3A.20
Keywords: device-independent, hypothesis testing, self-testing, quantum information, quantum entanglement, quantum properties, Bell test
Citation: Chang W-G, Chen K-C, Chen K-S, Chen S-L and Liang Y-C (2024) Device-independent certification of desirable properties with a confidence interval. Front. Phys. 12:1434095. doi: 10.3389/fphy.2024.1434095
Received: 17 May 2024; Accepted: 25 September 2024;
Published: 06 November 2024.
Edited by:
Xiao Yuan, Peking University, ChinaCopyright © 2024 Chang, Chen, Chen, Chen and Liang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Yeong-Cherng Liang, eWNsaWFuZ0BtYWlsLm5ja3UuZWR1LnR3
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.