
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
ORIGINAL RESEARCH article
Front. Phys. , 02 November 2023
Sec. Interdisciplinary Physics
Volume 11 - 2023 | https://doi.org/10.3389/fphy.2023.1277361
This article is part of the Research Topic Advanced Signal Processing Techniques in Radiation Detection and Imaging View all 13 articles
Given the improved capabilities of radar systems, addressing unfamiliar signals presents a challenge for radar jamming technology. To tackle this issue, this study proposes an adaptive technique for optimizing jamming waveforms to suppress multiple false targets in escort jamming scenarios. The objective is to minimize the detectability of false targets by fine-tuning phase modulation and individual waveform parameters. The optimization model adjusts the energy and delay of jamming waveform segments using intercepted radar signal phase modulation and direct forwarding. Real-time adaptation is achieved through the utilization of a genetic algorithm and radar constant false alarm rate detection based on received emissions. The key findings highlight the advantages of adaptivity in effectively suppressing false targets under diverse conditions. The technique successfully learns efficient waveforms through feedback, even without specific knowledge of the radar system. The optimized waveforms maintain consistent jamming impact across different constant false alarm rate settings, surpassing the limitations associated with fixed assumptions. The introduction of phase modulation enhances the resilience of false targets by creating noise-like characteristics. Remarkably, robust jamming is achieved with only 12 false targets, reducing complexity. The unified waveform design is particularly suitable for single platform jamming, eliminating the need for multiple jammers. Furthermore, the optimized waveforms demonstrate improved coverage of real targets under position errors. As a result, the approach exhibits versatility across various signals, processing methods, and scenarios. This study suggests that increased adaptability and the incorporation of machine learning techniques contribute to the advancement of radar jamming capabilities. By optimizing jamming waveforms, the adaptive approach presented in this study may enhance the effectiveness of countering advanced radar systems.
The disruption of radar performance is a crucial aspect for military forces and the aerospace industry interested in degrading an adversary’s radar capabilities. Among the various approaches, false target jamming has proven to be highly effective in confusing radar systems by introducing false target echoes into the radar return signal. In recent times, considerable research efforts have been devoted to multi-false target suppression jamming, which involves generating a multitude of false targets to overwhelm the radar’s ability to detect genuine targets. However, existing methods for generating the jamming waveform often rely on predetermined assumptions regarding radar signal parameters and detection algorithms. Consequently, these techniques have limited adaptability to accommodate diverse and evolving radar systems [1–3].
False target jamming is a technique utilized to deceive radar operators or disrupt automatic tracking systems by generating radar echoes that imitate legitimate target returns [4]. To accomplish this, the jammer detects the radar pulse, amplifies it, and transmits the signal again with suitable delays, thereby simulating target echoes at false distance ranges [5]. Multi-false target jamming involves generating a multitude of false echoes, which impairs the radar’s ability to differentiate genuine targets from the false ones [6]. Consequently, this suppression effect significantly deteriorates the radar’s detection capability.
Multi-false target suppression jamming refers to a specific form of false target jamming that aims to overpower the radar’s signal processing by inundating it with an abundance of false targets [7, 8]. In this technique, the jammer produces replicated radar pulses that correspond to multiple closely-positioned false targets surrounding the desired target [9]. The presence of numerous false targets in close proximity serves to obscure the genuine target and overwhelms the radar’s display and tracking processing. Compared to generating only a small number of isolated false targets, multi-false target jamming poses a greater challenge for the radar system to mitigate.
The effectiveness of multi-false target jamming is significantly influenced by the radar’s constant false alarm rate (CFAR) detection method [10–12]. CFAR adjusts the detection threshold based on estimated noise and clutter levels to maintain a desired target false alarm probability. By incorporating the presence of multi-false targets in the threshold determination, CFAR detection can partially mitigate the impact of jamming. Consequently, it is crucial to optimize the jamming waveform in consideration of the radar’s CFAR implementation.
Numerous research studies have focused on the optimization of multi-false target jamming waveforms in the context of specific CFAR detection scenarios. Shi et al. [13] conducted an analysis of the effects of jamming on a linear frequency modulation radar utilizing cell-averaging CFAR detection. They derived expressions for false target amplitude and spacing. Zhang et al. [14] proposed an intermittent sampling method to enhance the effectiveness of jamming against CFAR detection. Zheng et al. [15] investigated the influence of closely spaced false targets on various CFAR techniques. However, most existing analyses assume a priori knowledge of the radar parameters and fixed CFAR settings, which are typically known to the jammer.
The adaptability and effectiveness of jamming can be enhanced by optimizing the jamming waveform in response to radar emissions and the detection process. Recent studies have started exploring cognitive methods for adapting the jamming waveform. For instance, Jiang et al. [16] conducted joint optimization of the spacing and amplitude of false targets based on detection outcomes. Li et al. [17] proposed a “smart” false target approach that involved evolutionary optimization of the waveform. Although these approaches show promise, most adaptive optimizations have been tailored to specific signal types or variants of CFAR. To enable real-time adaptation for multi-false target suppression jamming, it would be advantageous to develop a more flexible jamming module capable of responding to diverse radar signals and unknown CFAR processing methods.
Phase modulation [18] is a technique that can be employed to manipulate the radar signal within the false target jamming waveform, thereby introducing complexity to pulse compression processing. By applying pseudo-random phase codes to modulate the replicated radar pulses prior to retransmission, the correlation between these pulses and the radar receiver’s matching filter is reduced. This transformation results in false targets resembling noise-like returns, thereby enhancing the effectiveness of the jamming. Yuan and Tao [8] demonstrated the efficacy of incorporating phase modulation into successive radar pulse segments to deceive mainlobe tracking. Expanding the application of such phase modulation techniques to multi-false target jamming waveforms has the potential to further enhance the resilience of jamming efforts.
The integration of evolutionary optimization methods, such as genetic algorithms, into the adaptation process enables efficient waveform optimization when faced with an unknown radar adversary [18, 19]. By treating waveform parameters, such as false target positions and amplitudes, as genes, the jammer can iteratively modify them to minimize an objective function associated with jamming effectiveness, such as reducing detectable false targets. Genetic algorithms facilitate exploration of the vast solution space to identify jamming waveforms that effectively counter specific radar detection schemes [20–23].
Therefore, in light of scientific progress across various disciplines, such as electronics, researchers have undertaken numerous investigations aimed at improving and optimizing electronic systems [24–28]. Past studies have primarily concentrated on the assessment of essential tools within satellite and military sectors [29–33]. Furthermore, recent scholarly focus has been directed towards the exploration of satellite-based communication systems and wireless technologies that eliminate the need for wired connections [34–38]. The incorporation of radar systems in communication and military domains has also garnered significant attention within the scientific community over the past decade [39–43]. Prior research endeavors have encompassed the utilization of diverse methodologies, including modeling and analytical approaches, to address these subjects [44–48]. Moreover, previous studies have proposed different models and optimization techniques to advance the understanding and application of these systems [49–53].
An adaptive optimization approach for the design of multi-false target suppression jamming waveforms based on genetic algorithms and phase modulation is proposed in this study. The aim is to achieve robust jamming performance against various radar signals and unknown CFAR processing settings. A formulation of an optimization model is presented to minimize the detectability of false targets by adjusting the contributions of individual false targets within a segmented, phase-modulated jamming waveform. Real-time adaptation of waveform parameters is enabled by a genetic algorithm, which utilizes feedback from received radar emissions and evaluation through CFAR detection. The proposed adaptive methodology utilizing genetic algorithms and phase modulation offers a more flexible real-time approach for countering modern radar systems compared to previous fixed analyses or optimizations. By continuously evaluating CFAR detection outcomes in response to transmitted jamming waveforms, effective waveforms tailored to the current radar signal and processing scheme can be learned by the jammer, even without specific knowledge of the threat parameters. This research explores the potential benefits of increased adaptability and machine learning techniques in the established field of radar jamming.
An investigation is conducted in this study on an adaptive technique for optimizing jamming waveforms to counter diverse radar signals and CFAR processing methods. Existing jamming waveform designs, based on fixed radar knowledge, exhibit limited adaptability against modern agile radars. To address this limitation, an optimization model is proposed to minimize the detectability of false targets by tuning the phase modulation and individual parameters of the jamming waveform. Real-time optimization of the waveform is achieved using a genetic algorithm that leverages CFAR evaluations to refine the jamming approach. The robustness against varying radar emissions and detection schemes is improved by this adaptive methodology. The effectiveness of the proposed technique is validated through simulations conducted under different scenarios involving radar signals, CFAR settings, and target position errors. The results demonstrate the benefits of adaptation in enhancing the suppression of multi-false targets through jamming, laying the foundation for real-time optimization of jamming waveforms across diverse scenarios.
This jamming technique is specifically designed for escort jamming scenarios where the jammer is positioned closer to the radar system than the protected target. During the flight process, the radar signal is intercepted, modulated, delayed, and transmitted, as depicted in Figure 1.
The radar CFAR detector maintains a consistent probability of false alarms by continuously estimating the noise from the data in real time. The detection process involves comparing the estimated values of the detection cells with the noise signal to determine the presence of a target. Figure 2 provides an illustrative representation of the CFAR processing window, highlighting its conceptual framework.
This study investigates the jamming method specifically targeting ML-CFAR, which encompasses various techniques such as cell-averaging CFAR (CA-CFAR), greatest of CFAR (GO-CFAR), and smallest of CFAR (SO-CFAR). Among these ML-CFAR methods, the SO-CFAR approach exhibits certain advantages in terms of detection performance in multi-target scenarios. Therefore, this study examines the impact of jamming suppression under the conditions of SO-CFAR. In the SO-CFAR method, the normalization factor T is determined based on the reference cell length N and the desired false alarm rate (Pfa). The relationship between these parameters is expressed as follows [54]:
The threshold value under SO-CFAR condition is as follows:
where
Pseudo-random sequence phase modulation is a widely employed technique for modulating signal phases due to its ease of implementation in engineering and its proven effectiveness in practical applications. The expression of this modulation method is as follows:
where
where
The jammer utilizes a segmented reconstruction method to generate a jamming waveform by combining the radar signal after pseudo-random phase modulation with the intercepted complete radar signal. The reconstructed signal, denoted as
Illustrating the jamming effect, Figure 4 showcases the schematic diagram of the jamming signal after pulse compression. Taking the example of a Linear Frequency Modulated (LFM) signal, the transmitted radar signal is defined as follows:
By delaying and superimposing the signal “xs2″ on each segment of the jamming waveform, the resulting jamming signal can be expressed as follows:
Here, Am represents the amplitude of
Figure 4 showcases the effects of both the jamming signal and target echo after the application of matched filtering. The transmitted radar signal undergoes pulse compression processing, resulting in the generation of a false target signal. The radar signal is modulated by the pseudo-random phase of the jammer, and during the radar pulse compression processing, a noise-like jamming signal is formed alongside the false target.
To achieve different jamming effects, the delay of each superimposed signal and the amplitude of the signal on different segments are flexibly adjusted. As mentioned in [13], effectively covering a real target does not require a large number of false targets. Thus, in this study, the number of false targets generated was set to 12, with six on each side. The segmented reconstructed jamming waveform comprises sixteen parts, with twelve being directly transmitted radar signals and four being transmitted radar signals after pseudo-random phase modulation.
The adaptive jamming module enables the jammer to adaptively generate optimized multi-false target jamming waveforms in various radar signal environments. This module incorporates an adaptive genetic algorithm to optimize the jamming waveform after segmented reconstruction. The optimized jamming waveform is evaluated using radar CFAR detection. The schematic diagram of the adaptive jamming module is presented in Figure 5.
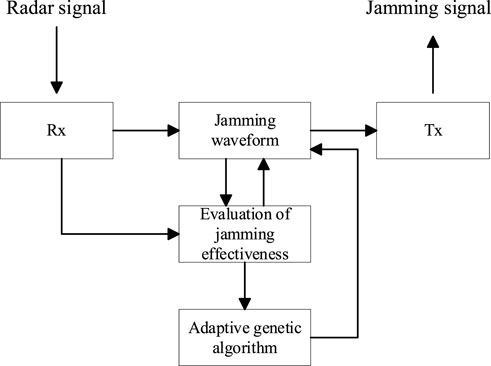
FIGURE 5. Schematic diagram of the adaptive jamming module for multi-false target jamming optimization.
In this study, the optimization of parameters involved determining the delay time for each segmented signal and the signal amplitude for each superimposed signal. The following general constraints were established during the parameter optimization process (Table 1):
(1) The number of superimposed signals was set to 16. Based on previous studies (References [13–15]), it was observed that the false target is symmetrically reduced on both sides of the real target. Hence, the chosen number of false targets was 12, with 6 on each side.
(2) The delay time, denoted as t, was set within the range of 0.1 μs to 1 µs, with an accuracy of 0.01 µs.
(3) The amplitude of the signal corresponding to the pseudo-random phase modulation ranged from 0.4 to 2, while the amplitude of the signal corresponding to the transmitted radar signal ranged from 0.1 to 1. The accuracy for both amplitude settings was set to 0.1.
Correlation reception and CFAR are widely used signal processing techniques in radar systems. These techniques serve to enhance the Signal-to-Noise Ratio (SNR) of the received signal and enable adaptive adjustment of the target detection threshold. In this study, the objective function is established based on the CFAR threshold, taking into consideration the ability of the modulated jamming signal to generate multiple realistic false targets around the real target.
The optimized objective function is defined as the average deviation between the threshold value and the echo power of the real target within a range of ±300 m after pulse compression. The expression of the objective function is as follows:
where -N1 represents the CFAR detection cell corresponding to the real target R1 within a range of ±300 m, and fs denotes the signal sampling interval. In Eq 8, the variable N denotes the number of reference cells employed in the SO-CFAR detection process. Zi represents the SO-CFAR detection threshold, which is associated with the reference cell N as described in Section 2.2. Pi represents the signal power value after pulse compression. The weighting of real and false targets plays a crucial role as it directly influences the effectiveness of jamming by considering the detection of genuine targets resulting from echoes and spurious targets generated by jamming signals.
In Eq 9, the parameter am denotes the weight assigned to the impact of detecting the positions of the real and false targets on the objective function. When a false target is detected by radar CFAR, am is set to 0.05. Conversely, when a false target is not detected, am is set to 1. If a real target is detected, am is set to 0.0001 (m = 0); otherwise, am is set to 1 (m = 0). By combining the detection results for different reference cells as an objective function, the adaptability of the optimized jamming waveform for CFAR detection under various reference cell conditions can be improved. In this study, the average values of N = 8 and N = 16 were selected, as shown in Eq 10. It is evident that a larger objective function corresponds to a greater signal distance threshold, resulting in a more effective suppression effect.
In this study, a genetic algorithm with real code [18] is employed to optimize the proposed multi-false target jamming waveform. The implementation steps are outlined as follows:
Step 1:. Real number coding is utilized to encode the parameters to be optimized.
Step 2:. Population initialization is performed by setting the initial population size to 20.
Step 3:. Fitness evaluation is conducted by assigning the individual fitness values as the negation of the objective functions, which can be expressed as:
Step 4:. Selection is carried out using a random league operator for the purpose of selection.
Step 5:. Crossover is performed using the BLX mixed crossover operator. The crossover probability is set to 1, and the crossover range coefficient is set to 1/4.
Step 6:. Mutation is implemented using a single point Gaussian mutation. Additionally, an adaptive mutation operator is introduced to prevent convergence to local optima and enhance the convergence speed.
Step 7:. Fitness calculation is performed to evaluate the fitness of each individual in the population.
Step 8:. A new population is generated by selecting the top 20 individuals with the highest fitness from the two generations, which will serve as the new parental generation.
Step 9:. The termination criterion is set to 100 (or 200) iterations. If the criterion is not satisfied, the process repeats steps 4 to 9.
Signal 1 utilized in this study is LFM signal. The specific parameter configurations for Signal 1 and the SO-CFAR technique can be found in Table 2.
Based on the parameter configurations provided in Table 2, simulations were conducted to evaluate the jamming waveform after pulse compression and the detection results under SO-CFAR conditions. The outcomes of these simulations are depicted in Figure 6.
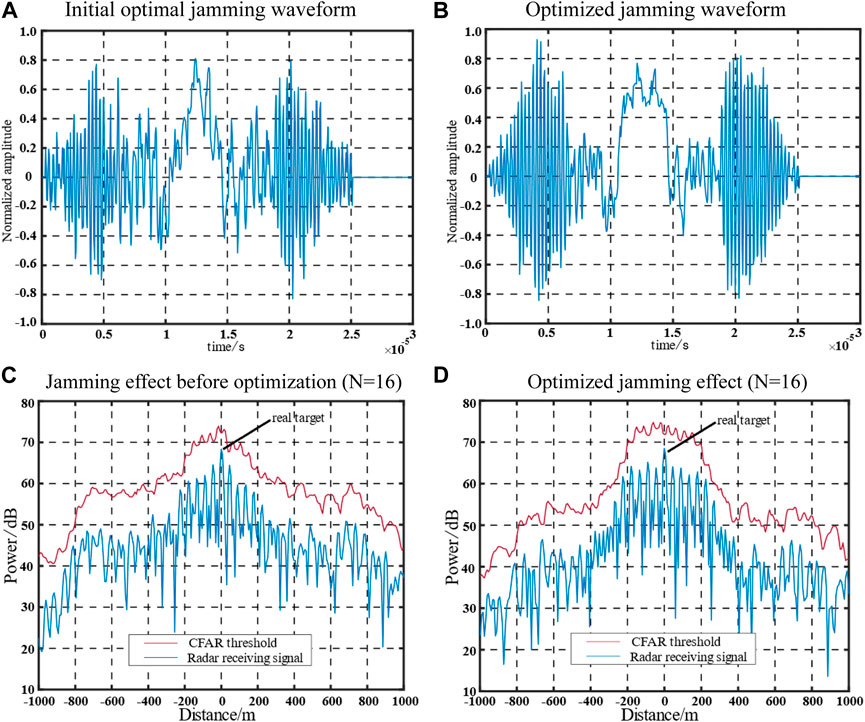
FIGURE 6. Comparison of jamming waveforms and their effects before and after optimization under SO-CFAR conditions.
Figure 6 illustrates the results of the Signal-to-Clutter-plus-Noise Ratio (SCNR) processing for the jamming waveform before and after optimization, as well as the pulse compression outcomes and the reference cells used with 16 reference cells. The pulse compression of the jamming signal generates a total of 12 false target signals. Notably, the presence of a pseudo-random phase modulation component in the radar signal leads to the generation of a sequence of jamming noises between the outermost false target and the false target after pulse compression.
To assess the optimization effectiveness of the proposed jamming model, the Monte Carlo method is employed. The multi-false-target jamming waveform is optimized using a genetic algorithm, and the experimental results are presented in Figure 7.
Figure 7A showcases the optimization effect achieved by the jamming optimization model through 20 Monte Carlo simulations, under the specified simulation experimental conditions in Section 4.1. The model demonstrates convergence of the objective function within approximately 70 iterations.
In Figure 7B, the results of the 20 Monte Carlo simulation experiments are presented. It is observed that the optimized objective function value is, on average, 2.6658 dB higher than the average optimal value of the initial population before optimization. The optimized objective function is determined based on the average difference between the threshold value of the real target within 300 m and the power value of the target echo after pulse compression. This optimization approach maximizes the detection threshold around the target while maintaining a fixed Jamming-to-Signal Ratio (JSR).
Furthermore, the application of the jamming method discussed in this study, particularly in escort jamming scenarios, may introduce errors in the position estimation of the target. When there is a position estimation error in the target, the jamming effects before and after jamming waveform optimization are depicted in Figures 8, 9.
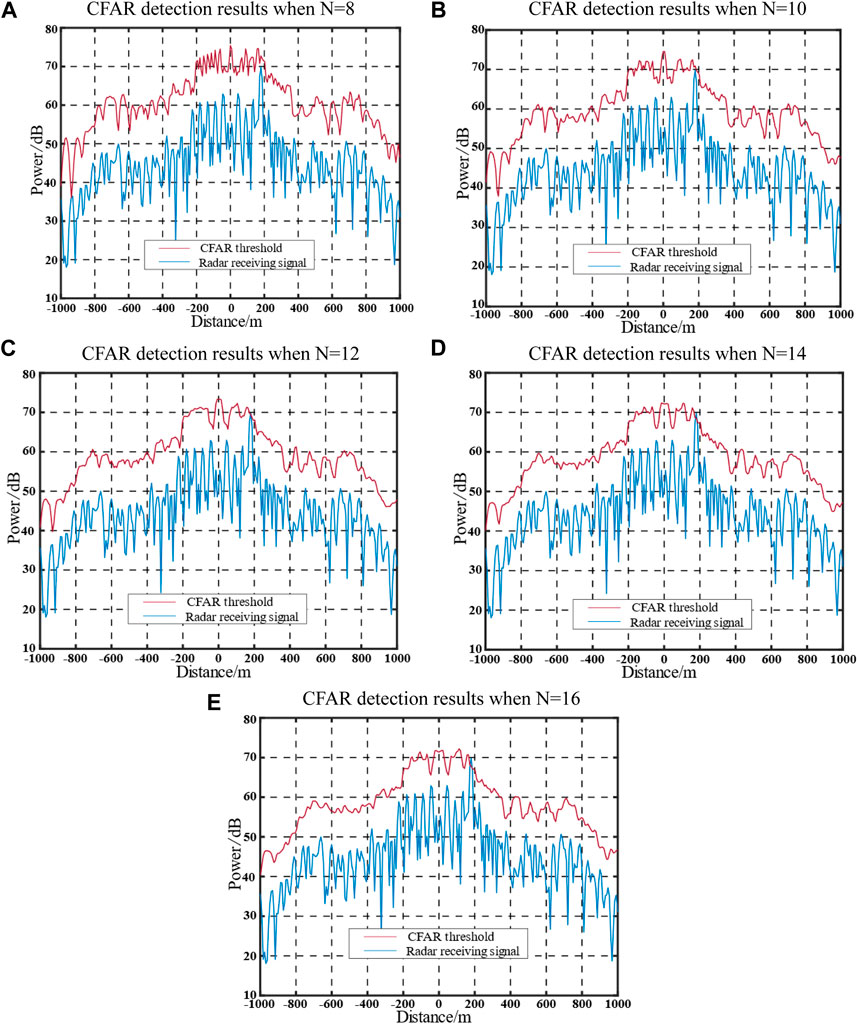
FIGURE 8. Jamming effect before optimization with an actual target position estimation error of 180 m.
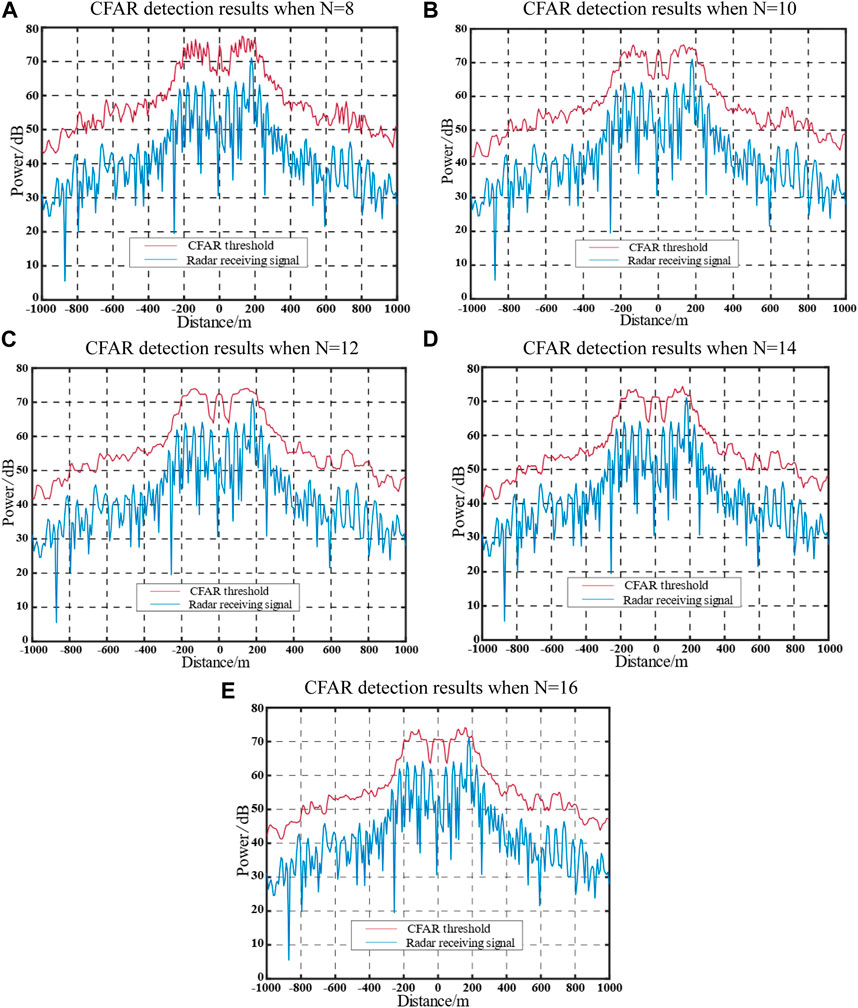
FIGURE 9. Jamming effect after optimization with an actual target position estimation error of 180 m.
Figures 8, 9 reveal the impact of a real target position estimation error of 180 m (the maximum error range after optimization) on the jamming effects. It is observed that, except for N = 8, the jamming waveform before optimization fails to adequately cover the real target under the conditions of other reference cells. However, the optimized jamming waveform demonstrates effective coverage for the real target.
In practical scenarios, the estimation error often exhibits a certain degree of randomness. To account for this, a normal distribution with a random error of 180 m was added to the real target. The objective function values before and after optimization were measured at 69.193 dB (initial best) and 71.8422 dB for the jamming waveforms, respectively. The difference between the group values before and after optimization was calculated at 2.6519 dB, slightly lower than the average optimization value. In conjunction with the Monte Carlo method, this difference signifies the probability of detecting the real target under error conditions in 100 detections.
Table 3 presents the detection probability of the real target under error conditions for different reference cell settings. It is observed that the detection probability is lower under error conditions, indicating a stronger suppression effect of the jamming waveform. Additionally, the optimized jamming waveform demonstrates better coverage of the real target compared to the non-optimized waveform across different reference cell conditions. Consequently, the optimized jamming waveform exhibits superior jamming effectiveness and increased adaptability under varying conditions.
The effectiveness of the optimized waveform jamming results for signal 1 was validated. In comparison to the jamming method that employs numerical derivation of the LFM pulse SO-CFAR [13] (referred to as the calculation method), the proposed method yields a value when N = 8. This study introduces an optimization approach considering different reference cell conditions. The outcomes of utilizing the LFM radar SO-CFAR detector with this method are illustrated in Figures 10, 11.
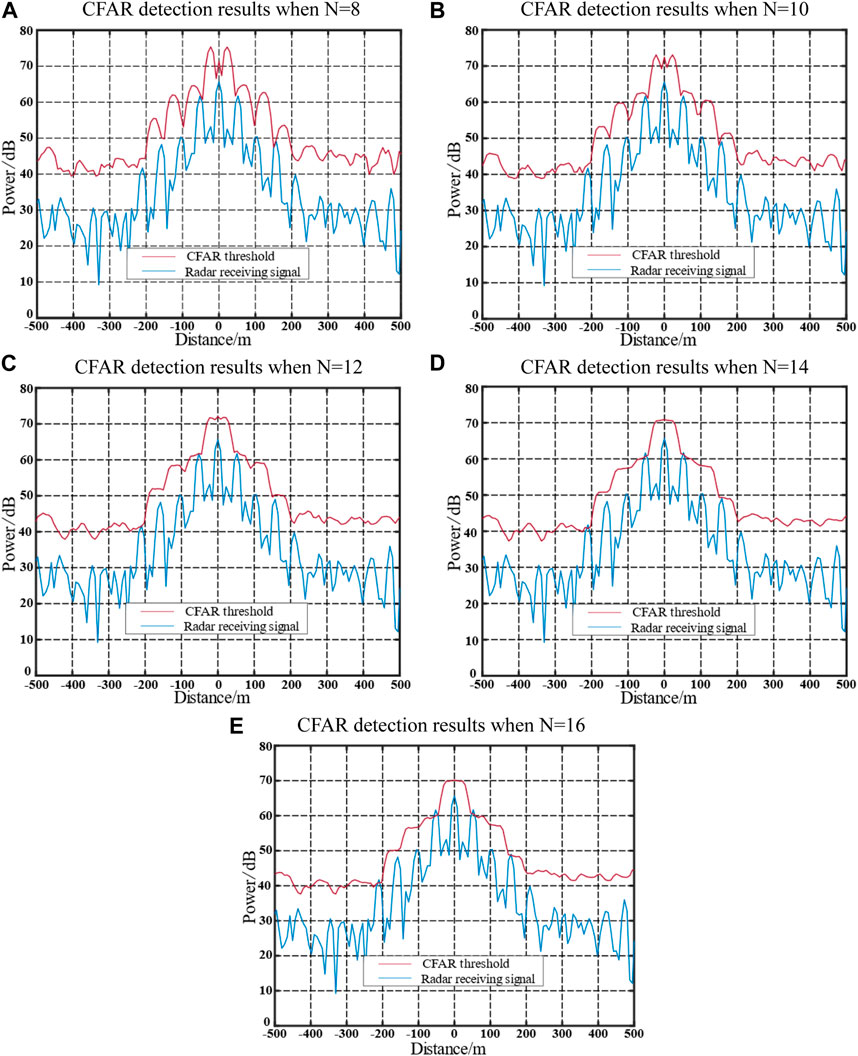
FIGURE 10. Detection results of jamming technique using numerical derivation of LFM pulse radar SO-CFAR.
Figure 10 illustrates the detection results obtained from the generated waveform, assuming that the radar SO-CFAR reference cell is N = 8. When the reference cells used by the radar do not align with the jamming assumption, an increase in the reference cell count (N) results in a higher probability of detecting false targets at the edges. This is attributed to the gradual decrease in the nominal factor T of SO-CFAR as N increases, making it more likely to detect false targets that were derived under the original conditions. The radar can detect the primary false target, which is the false target closest to the true target, as depicted in Figures 8D, E. This occurs because an increase in the number of reference cells causes a portion of the false target energy to be averaged over a larger number of cells. Consequently, the threshold is not effectively raised, leading to the detection of the peak of the primary false target.
Figure 11 showcases the effectiveness of optimizing the multi-false target jamming waveform using the adaptive jamming module. The introduction of two radar signals with pseudo-random phase modulation at the beginning and end of the reconstructed section of the jamming waveform gradually increases the edge CFAR detection threshold, resulting in a significant reduction in the detection probability of the outermost false target. Additionally, by dispersing part of the energy among each false target, the issue of increased detection probability due to changes in CFAR detection reference cells is mitigated. The adaptive genetic algorithm ensures a reasonable distribution of signal energies for different forms of the jamming waveform, leading to an improved threshold value within ±300 m around the target and effectively enhancing the jamming-shielding effect on the real target. To validate these conclusions, the Monte Carlo method is employed to evaluate the two jamming techniques under various conditions. The detection probability of both true and false targets is calculated by analyzing the detection results under different reference cell conditions, with each scenario repeated 100 times. The obtained results are presented in Figure 12.
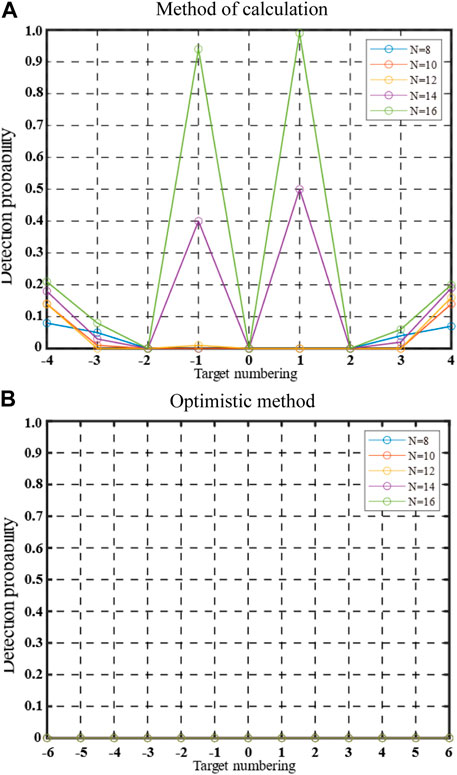
FIGURE 12. Detection probabilities of real and false targets in different CFAR reference cells under different jamming methods.
In Figure 12, the detection probability for the real target is represented on the x-axis. The detection probability of a false target, corresponding to the relative distance from the left and right sides of the true target, ranges from ±1 to ±4 (±6). In the N = 8 reference cell setting scenario, the calculation method demonstrates effective jamming suppression, with all positions meeting the requirement of a detection probability less than 0.1. However, as the number of reference cells varies, the detection probability for the outermost false target gradually increases from 0.09 to 0.15, 0.20, 0.26, and 0.27. Notably, the detection probability of the two main false targets closest to the target significantly rises in the N = 14 and N = 16 scenarios, reaching 0.48 (N = 14) and 0.98 (N = 16). These findings indicate that the jamming waveform cannot adapt to changes in CFAR detection reference cells solely by calculating the amplitude and number of false targets in a specific scene. The estimation of a predetermined number of CFAR reference cells can be challenging, thereby affecting the adaptability of the multi-false target jamming method. The proposed method for optimizing the multi-false target jamming waveform in different reference cell scenarios addresses this limitation. Under the N = 10 condition, the second false target on the left side of the real target exhibits the highest detection probability, reaching 0.14. After optimization, the jamming waveform demonstrates good adaptability and maintains a stable jamming effect under the SO-CFAR detection conditions.
Given the diverse operating modes and intricate signal styles of modern radars, an approach involving the addition of two distinct signals is employed, with Signal 1 serving as the foundation. The specific signals utilized in this study are outlined in Table 4.
The adaptive optimization technology for multi-false target jamming waveforms, as proposed in this study, was applied to jam the radar in the presence of these two signal conditions. The optimization process and the outcomes of the 20 Monte Carlo experiments are depicted in Figure 13.
Figure 13 presents the simulation outcomes, encompassing the iterative curve and statistical analysis of the optimization results, under various signal conditions. The proposed jamming optimization method demonstrates a considerable level of improvement compared to the initial population’s optimal value across different signal scenarios. Notably, Signals 2 and 3 require approximately 180 and 120 times more iterations, respectively, compared to Signal 1. After optimization, the average objective function for Signals 2 and 3 increases by 2.67 dB and 3.1607 dB, respectively, compared to their pre-optimized values.
Figure 14 showcases the detection results obtained from the optimized adaptive jamming module using the Numerical Derivation of LFM Pulse Radar (NLFM) waveform. The subfigures demonstrate the CFAR detection results under different reference cell conditions, providing insights into the effectiveness of the optimization process.
Figure 15 presents the detection probabilities of real and false targets for different CFAR reference cell configurations using the NLFM waveform. The figure illustrates the impact of various methods on the detection performance, highlighting the differences in detection probabilities under different reference cell conditions.
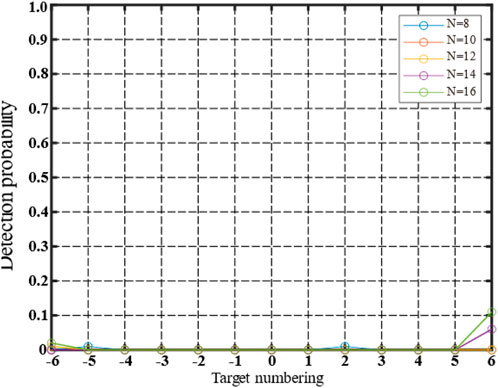
FIGURE 15. Detection probabilities of real and false targets in different CFAR reference cells under different methods (NLFM).
The false-target detection probability for each position of the optimized jamming waveform in a nonlinear frequency modulation signal (refer to Figures 12, 13) demonstrates a symmetrical pattern. When N = 16, the edge false target, specifically the sixth false target on the right side of the true target, displayed the highest probability of being detected at the edge, reaching 0.1. However, false targets at other positions exhibited consistently low detection probabilities. Notably, the jamming waveform generated showcased improved jamming effectiveness when tested under various reference cell conditions.
Following the optimization of the jamming waveform under Signal 3, the detection outcomes for different CFAR detection reference cell conditions, along with the detection probabilities of both real and false targets, are presented in Figures 16, 17.
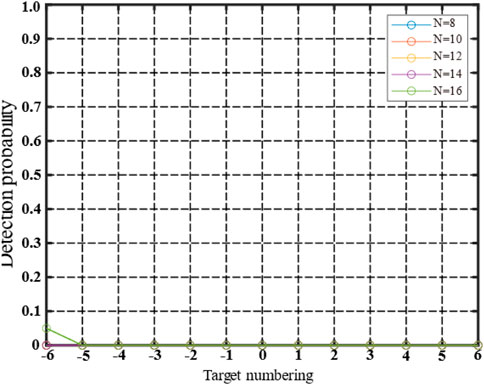
FIGURE 17. Detection probabilities of real and false targets in different CFAR reference cells under different methods (PCM).
Under phase-coding conditions (refer to Figures 16, 17), the optimized jamming waveform demonstrates enhanced stability in achieving effective jamming. Specifically, when N = 16, the position exhibiting the highest detection probability is the sixth false target situated to the left of the true target, with a detection probability of 0.05. Consequently, the application of the suggested adaptive technology for optimizing multi-false target jamming waveforms can lead to improved jamming effects when employed with phase-coded signals.
In the presence of radar disturbances, the nature of the signal can undergo changes. To validate the operational efficacy of adaptive jamming modules, three sets of experiments were conducted. Experiment 1 involved the transformation of Signal 1 into Signal 2 through jamming. In Experiment 2, Signal 2 was transformed into Signal 3 following jamming. Similarly, in Experiment 3, Signal 3 was transformed back into Signal 1 after jamming. Figure 18 illustrates the optimization process in the context of a mutation in the radar signal.
Figure 18 illustrates the occurrence of the jamming transition phase, denoted as t10, when there is a change in the signal type. During this phase, the jammer utilizes the previously optimized jamming waveform. It is evident that the adaptive jamming module is capable of optimizing the suppression jamming waveform for multi-false targets following changes in the radar signal. Throughout the iterative process, the objective function gradually increases over time, indicating an improvement in the confrontational performance within the new signal environment. The simulation results strongly support the effectiveness of the technology employed for adaptive optimization of jamming waveforms in suppressing multiple false targets. Consequently, this method achieves a certain level of adaptability in jamming.
The conventional approach for suppressing multi-false target jamming involves employing reference cells in the parameter design for CFAR detection. However, obtaining these parameters can be challenging. Moreover, changing the number of CFAR detection reference cells results in a decrease in the effectiveness of jamming. To enhance the jamming effect of multi-false target suppression jamming waveforms, a segmented reconstruction technique is applied to pseudo-random phase-modulated radar signals and intercepted radar signals. Additionally, an adaptive jamming module is developed by incorporating an adaptive genetic algorithm and radar CFAR detection technology. This method enables the adjustment of delay and energy distribution for each component of the improved multi-false target suppression jamming waveform based on different radar signal conditions.
The simulation findings demonstrate that the optimized waveform produces enhanced jamming outcomes when applied to CFAR detection with different reference cell setups. This research proposes a jamming approach that exhibits improved adaptability to multiple CFAR detections using ML-CFAR, in contrast to the amplitude and interval arrangement described in [16]. The key distinction lies in the fact that the suggested method considers waveform optimization based on varying reference cell conditions, rather than being restricted to a fixed configuration.
In contrast to previous studies such as Rao et al. [11] which utilized up to 18 false targets, this research demonstrates that effective jamming can be achieved with only 12 false targets. This reduction in the number of false targets not only decreases complexity but also alleviates processing requirements. The achievement of effective jamming with fewer false targets is made possible by the optimization approach, which concentrates the jamming energy in an efficient pattern.
To ensure the adaptability of the method in question when the number of reference cells is altered, further verification is necessary. While the multi-false target jamming method described in [17] focuses solely on false-target detection, the disruptive approach proposed in this study takes into account the detection of both false targets and real target echoes. This comprehensive evaluation of jamming performance offers a more thorough assessment by considering both the masking of real targets and the detectability of false targets.
In [55], the introduction of jamming noise between different false targets through jammer coordination was explored. In contrast, this study integrates multiple functions into a single waveform, resulting in a reduced number of jammers and more efficient control requirements for multi-jammer coordination during practical implementation. This unified waveform optimization approach proves to be more suitable for single platform jamming applications. Moreover, unlike previous jamming methods, the proposed approach in this study establishes adaptability in generating multi-false target jamming waveforms. It demonstrates versatility in adapting to diverse scenarios and enhancing radar jamming capabilities. While adaptive algorithms developed in studies such as [14–16] primarily focused on fixed false target patterns, this technique optimizes the entire waveform, enabling it to better respond to varying signals and CFAR processes.
Nonetheless, within the adaptive jamming module, the genetic algorithm currently employed solely enhances the adaptive mutation rate; however, it necessitates a larger number of iterations to achieve convergence. It is recommended that future research explores the potential of enhancing real-time performance by incorporating alternative optimization algorithms. This includes reducing the generation time of the optimized jamming waveform and improving the responsiveness of the adaptive jamming module. Hybrid approaches that combine genetic algorithms with faster techniques like particle swarm optimization [56, 57] have the potential to expedite the adaptation process. In conclusion, while the study demonstrates promising adaptivity, further improvements in speed and complexity are required to enhance its practical applicability.
The optimization of jamming waveforms is a significant area of study aimed at enhancing the adaptability and resilience of radar countermeasures. Traditional fixed jamming techniques are limited in their effectiveness against modern radar systems, which are becoming increasingly advanced and agile. This study focuses on an adaptive approach to optimize multi-false target jamming waveforms, specifically designed to counter diverse radar signals and unknown CFAR processing methods. The proposed technique introduces an optimization model that minimizes the detectability of false targets by adjusting phase modulation and individual waveform parameters. Real-time adaptation is achieved using a genetic algorithm, which evaluates the jamming performance based on CFAR assessments. This approach offers a flexible methodology for countering modern radar systems compared to pre-defined methods used in the past.
The results demonstrate the effectiveness of adaptive optimization in suppressing false targets. The optimized waveforms maintain consistent jamming impact across various CFAR reference cell conditions, overcoming limitations of previous techniques that relied on fixed assumptions. Only 12 false targets were needed to achieve robust jamming, reducing complexity compared to existing approaches. The unified waveform design is suitable for single platform jamming applications, eliminating the need for multiple coordinated jammers.
The introduction of phase modulation enhances the noise-like characteristics of false targets, thereby improving resilience. The genetic algorithm enables the jammer to learn effective waveforms even without specific knowledge of the threat radar system. Although the convergence speed could be further improved, the adaptivity of the approach provides versatility across different scenarios and signals. This study highlights the potential of increased adaptability and the application of machine learning techniques to strengthen the field of radar jamming. The proposed methodology demonstrates promising adaptivity, laying the foundation for real-time optimization of jamming waveforms in operational settings. However, practical implementation would require additional improvements in terms of speed, scalability, and complexity. Hybrid optimization algorithms that combine genetic techniques with faster methods like particle swarm optimization could expedite the adaptation process.
The study presents an initial investigation of adaptive jamming waveform optimization within an escort jamming scenario, considering simplified assumptions. Further research should explore scenarios involving multiple targets and jammers, which present greater complexity. The effectiveness of the proposed technique against actual fielded radar systems needs to be validated. Additional intelligence about the threat radar could help constrain the optimization search space, leading to improved convergence. This study demonstrates the potential benefits of adaptivity and establishes a foundation for further development toward real-world jamming applications.
In conclusion, this research introduces an adaptive jamming waveform optimization technique that exhibits versatility across signals, CFAR processes, and scenarios. The methodology provides a valuable framework for enhancing the resilience and flexibility of radar countermeasures through learning and optimization. Although further improvements are necessary, this approach has the potential to overcome limitations in predefined jamming methods, thereby enhancing the effectiveness of electronic warfare systems against modern agile radar threats. The concepts explored in this study can serve as a guide for the further development of cognitive jamming capabilities.
The original contributions presented in the study are included in the article/Supplementary material, further inquiries can be directed to the corresponding author.
YW: Conceptualization, Formal Analysis, Investigation, Software, Validation, Writing–original draft. CW: Conceptualization, Formal Analysis, Investigation, Project administration, Supervision, Visualization, Writing–review and editing. QS: Formal Analysis, Investigation, Methodology, Software, Writing–review and editing. JH: Conceptualization, Formal Analysis, Investigation, Methodology, Validation, Writing–review and editing. NY: Conceptualization, Investigation, Project administration, Supervision, Writing–review and editing.
The author(s) declare that no financial support was received for the research, authorship, and/or publication of this article.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
1. Frazer G, Balleri A, Jacob G. Deception jamming against Doppler beam sharpening radars. IEEE Access (2020) 8:32792–801. doi:10.1109/access.2020.2973191
2. Liu J, Zhang L, Zhao S, Liu N, Yu H. Anti-deception jamming method for active/passive radar based on distributed architectures. J Xidian Univ (2018) 45(3):1–6.
3. Feng D, Tao H, Yang Y, Liu Z. Jamming de-chirping radar using interrupted-sampling repeater. Sci China Inf Sci (2011) 54:2138–46. doi:10.1007/s11432-011-4431-4
4. Yao Y, Zhao J, Wu L. Waveform optimization for target estimation by cognitive radar with multiple antennas. Sensors (2018) 18(6):1743. doi:10.3390/s18061743
5. Wei Z, Liu Z, Peng B, Shen R. ECCM scheme against interrupted sampling repeater jammer based on parameter-adjusted waveform design. Sensors (2018) 18(4):1141. doi:10.3390/s18041141
6. Zhao Z, Yuan J, Li M. Research on adaptive waveform optimization design of anti-jamming radar. J Phys Conf Ser (2020) 1650:022111. doi:10.1088/1742-6596/1650/2/022111
7. Sun J, Yu J, Peng S. The interference effect of jamming UAV formation anginst the netted radar. Electron Inf Warfare Tech (2016) 3:1–7.
8. Yuan T, Tao JF, Li XC. Main lobe track deception jamming method based on association rule. Syst Eng Electro (2018) 40(2):273–9.
9. Xie K, Chen Y-G, Wang L-D, Li C-J. A study on effectiveness evaluation of multiple false target jamming. Xiandai Leida(Modern Radar) (2006) 28(5):87–90.
10. Liao MF, Wang Y. Setting method of dense-false-target jamming by delay-overlapping copied radar pluses. Fire Control Command Control (2018) 43(4):75–8.
11. Rao B, Gu Z, Nie Y. Deception approach to track-to-track radar fusion using noncoherent dual-source jamming. IEEE Access (2020) 8:50843–58. doi:10.1109/access.2020.2980010
12. Tan M, Wang C, Xue B, Xu J. A novel deceptive jamming approach against frequency diverse array radar. IEEE Sensors J (2020) 21(6):8323–32. doi:10.1109/jsen.2020.3045757
13. Shi L, Zhou Y, Li D, Wang X, Xiao S. Multi-false-target jamming effects on the LFM pulsed radar’s CFAR detection. J Syst Eng Electron (2005) 27(5):818–22.
14. Zhang Y-r., Li Y-j., Li M-l., Gao M-g., Fu X-j. Suppress jamming technique of multiple false targets on interrupted-sampling and non-uniform periodic repeater. ACTA ELECTONICA SINICA (2016) 44(1):46. doi:10.3969/j.issn.0372-2112.2016.01.008
15. Zheng GY, Liu GZ, Wang FZ. Analysis of multi-false target interference effect under constant false alarm detection. High Power Laser Part Beams (2015) 10:241–5.
16. Jiang YL, Zhang JD, Li Y. Dense false target jamming algorithm with joint interval and amplitude phase optimization. Electron Inf Warfare Tech (2023) 38(1):1–9.
17. Li DQ, Li XH, Sheng Y, Wang Q. A smart multiple false target jamming technique. J Mod Defence Tech (2010) 38(3):108–13.
18. Sun JW, Wang C, Shi QZ, Ren WB, Yao ZK, Yuan NC. Intelligent optimization of phase-modulation waveform based on genetic algorithm. Syst Eng Electro (2022) 44(3):722–9. doi:10.12305/j.issn.1001-506X.2022.03.02
19. Sun J, Wang C, Shi Q, Ren W, Yao Z, Yuan N. Intelligent optimization methods of phase-modulation waveform. J Syst Eng Electro (2022) 33(4):916–23. doi:10.23919/jsee.2022.000089
20. Du C, Cong Y, Zhang L, Guo D, Wei S. A practical deceptive jamming method based on vulnerable location awareness adversarial attack for radar HRRP target recognition. IEEE Trans Inf Forensics Security (2022) 17:2410–24. doi:10.1109/tifs.2022.3170275
21. Wu X, Wang X, Lu H. Study of intermittent sampling repeater jamming to SAR. J Astronaut (2009) 30(5):2043–8.
22. Zhao G. Principle of radar countermeasure. Xi’an, China: Xidian University Publishing House (2012).
23. Zhao S-s., Zhang L-r., Zhou Y, Liu N. Measurement fusion method against false-target jamming for radar network. J Univ Electron Sci Tech China (2014) 43(2):207–11.
24. Jiang Y, Li X. Broadband cancellation method in an adaptive co-site interference cancellation system. Int J Electro (2022) 109(5):854–74. doi:10.1080/00207217.2021.1941295
25. Li A, Masouros C, Swindlehurst AL, Yu W. 1-bit massive MIMO transmission: embracing interference with symbol-level precoding. IEEE Commun Mag (2021) 59(5):121–7. doi:10.1109/mcom.001.2000601
26. Miaofen L, Youmin L, Tianyang W, Fulei C, Zhike P. Adaptive synchronous demodulation transform with application to analyzing multicomponent signals for machinery fault diagnostics. Mech Syst Signal Process (2023) 191:110208. doi:10.1016/j.ymssp.2023.110208
27. Pan S, Lin M, Xu M, Zhu S, Bian L-A, Li G. A low-profile programmable beam scanning holographic array antenna without phase shifters. IEEE Internet Things J (2021) 9(11):8838–51. doi:10.1109/jiot.2021.3116158
28. Xu B, Guo Y. A novel DVL calibration method based on robust invariant extended Kalman filter. IEEE Trans Vehicular Tech (2022) 71(9):9422–34. doi:10.1109/tvt.2022.3182017
29. Jiang H, Chen S, Xiao Z, Hu J, Liu J, Dustdar S, et al. Pa-count: passenger counting in vehicles using wi-fi signals. IEEE Trans Mobile Comput (2023) 1–14. doi:10.1109/tmc.2023.3263229
30. Jiang Y, Liu S, Li M, Zhao N, Wu M. A new adaptive co-site broadband interference cancellation method with auxiliary channel. Digital Commun Networks (2022). doi:10.1016/j.dcan.2022.10.025
31. Zhao J, Gao F, Jia W, Yuan W, Jin W. Integrated sensing and communications for UAV communications with jittering effect. IEEE Wireless Commun Lett (2023) 12(4):758–62. doi:10.1109/lwc.2023.3243590
32. Zhao Z, Xu G, Zhang N, Zhang Q. Performance analysis of the hybrid satellite-terrestrial relay network with opportunistic scheduling over generalized fading channels. IEEE Trans Vehicular Tech (2022) 71(3):2914–24. doi:10.1109/tvt.2021.3139885
33. Zhou G, Li W, Zhou X, Tan Y, Lin G, Li X, et al. An innovative echo detection system with STM32 gated and PMT adjustable gain for airborne LiDAR. Int J Remote Sensing (2021) 42(24):9187–211. doi:10.1080/01431161.2021.1975844
34. Li M, Wang T, Chu F, Han Q, Qin Z, Zuo MJ. Scaling-basis chirplet transform. IEEE Trans Ind Electro (2020) 68(9):8777–88. doi:10.1109/tie.2020.3013537
35. Xu X, Sun Y, Tian X, Zhou L, Li Y. A novel orientation determination approach of mobile robot using inertial and magnetic sensors. IEEE Trans Ind Electro (2022) 70(4):4267–77. doi:10.1109/tie.2022.3177762
36. Yin L, Wang L, Keim BD, Konsoer K, Yin Z, Liu M, et al. Spatial and wavelet analysis of precipitation and river discharge during operation of the Three Gorges Dam, China. Ecol Indicators (2023) 154:110837. doi:10.1016/j.ecolind.2023.110837
37. Zhou D, Sheng M, Li J, Han Z. Aerospace integrated networks innovation for empowering 6G: a survey and future challenges. IEEE Commun Surv Tutorials (2023) 25:975–1019. doi:10.1109/comst.2023.3245614
38. Zhou G, Deng R, Zhou X, Long S, Li W, Lin G, et al. Gaussian inflection point selection for LiDAR hidden echo signal decomposition. IEEE Geosci remote sensing Lett (2021) 19:1–5. doi:10.1109/lgrs.2021.3107438
39. Ban Y, Liu X, Yin Z, Li X, Yin L, Zheng W. Effect of urbanization on aerosol optical depth over Beijing: land use and surface temperature analysis. Urban Clim (2023) 51:101655. doi:10.1016/j.uclim.2023.101655
40. Li R, Zhang H, Chen Z, Yu N, Kong W, Li T, et al. Denoising method of ground-penetrating radar signal based on independent component analysis with multifractal spectrum. Measurement (2022) 192:110886. doi:10.1016/j.measurement.2022.110886
41. Liu H, Li J, Meng X, Zhou B, Fang G, Spencer BF. Discrimination between dry and water ices by full polarimetric radar: implications for China’s first martian exploration. IEEE Trans Geosci Remote Sensing (2022) 61:1–11. doi:10.1109/tgrs.2022.3228684
42. Yao Y, Shu F, Li Z, Cheng X, Wu L. Secure transmission scheme based on joint radar and communication in mobile vehicular networks. IEEE Trans Intell Transportation Syst (2023) 24:10027–37. doi:10.1109/tits.2023.3271452
43. Yin L, Wang L, Li T, Lu S, Yin Z, Liu X, et al. U-Net-STN: a novel end-to-end lake boundary prediction model. Land (2023) 12(8):1602. doi:10.3390/land12081602
44. Chen J, Liu Z, Yin Z, Liu X, Li X, Yin L, et al. Predict the effect of meteorological factors on haze using BP neural network. Urban Clim (2023) 51:101630. doi:10.1016/j.uclim.2023.101630
45. Cheng B, Wang M, Zhao S, Zhai Z, Zhu D, Chen J. Situation-aware dynamic service coordination in an IoT environment. IEEE/ACM Trans Networking (2017) 25(4):2082–95. doi:10.1109/tnet.2017.2705239
46. Li A, Masouros C, Vucetic B, Li Y, Swindlehurst AL. Interference exploitation precoding for multi-level modulations: closed-form solutions. IEEE Trans Commun (2020) 69(1):291–308. doi:10.1109/tcomm.2020.3031616
47. Yin Z, Liu Z, Liu X, Zheng W, Yin L. Urban heat islands and their effects on thermal comfort in the US: new York and New Jersey. Ecol Indicators (2023) 154:110765. doi:10.1016/j.ecolind.2023.110765
48. Zhu W, Chen J, Sun Q, Li Z, Tan W, Wei Y. Reconstructing of high-spatial-resolution three-dimensional electron density by ingesting SAR-derived VTEC into IRI model. IEEE Geosci Remote Sensing Lett (2022) 19:1–5. doi:10.1109/lgrs.2022.3178242
49. Bai X, He Y, Xu M. Low-thrust reconfiguration strategy and optimization for formation flying using Jordan normal form. IEEE Trans Aerospace Electron Syst (2021) 57(5):3279–95. doi:10.1109/taes.2021.3074204
50. Ding G, Anselmi N, Xu W, Li P, Rocca P. Interval-bounded optimal power pattern synthesis of array antenna excitations robust to mutual coupling. IEEE Antennas Wireless Propagation Lett (2023) 1–5. doi:10.1109/lawp.2023.3291428
51. Qian L, Zheng Y, Li L, Ma Y, Zhou C, Zhang D. A new method of inland water ship trajectory prediction based on long short-term memory network optimized by genetic algorithm. Appl Sci (2022) 12(8):4073. doi:10.3390/app12084073
52. Xu B, Wang X, Zhang J, Guo Y, Razzaqi AA. A novel adaptive filtering for cooperative localization under compass failure and non-Gaussian noise. IEEE Trans Vehicular Tech (2022) 71(4):3737–49. doi:10.1109/tvt.2022.3145095
53. Zhou G, Zhang R, Huang S. Generalized buffering algorithm. IEEE access (2021) 9:27140–57. doi:10.1109/access.2021.3057719
54. Richards MA. Fundamentals of radar signal processing. New York, NY, United States: McGraw-Hill Education (2014).
55. Hang Y, Yu JY, Su RL, Li CX. Effect analysis and optimization of dense false target jamming scheme. Fire Control Radar Tech (2023) 52(1):130–4.
56. Reddy BR, Kumari MU. Polyphase orthogonal waveform using modified particle swarm optimization algorithm for MIMO radar. In: Proceedings of the IEEE International Conference on Signal Processing, Computing and Control; March 2012; Solan, India (2012). p. 1–6.
Keywords: multi-false-target, jamming waveform optimization, adaptive optimization, genetic algorithm, cognitive jamming
Citation: Wang Y, Wang C, Shi Q, Huang J and Yuan N (2023) Adaptive optimization technology of segmented reconstruction signal based on genetic algorithm for enhancing radar jamming effect. Front. Phys. 11:1277361. doi: 10.3389/fphy.2023.1277361
Received: 14 August 2023; Accepted: 19 October 2023;
Published: 02 November 2023.
Edited by:
Yayun Cheng, Harbin Institute of Technology, ChinaReviewed by:
Abraão Nascimento, Federal University of Pernambuco, BrazilCopyright © 2023 Wang, Wang, Shi, Huang and Yuan. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Chao Wang, d3lxMTk5NjY0QDE2My5jb20=
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.