- Public Security Behavioral Science Laboratory, People’s Public Security University of China, Beijing, China
Terrorist attacks are a catastrophic man-made emergent phenomenon. The current situation of international violent terrorism is severe. Public places with high-density crowds are more likely to be attacked by violent terrorists. To effectively reduce the number of casualties caused by violent terrorist incidents, it is crucial to take preventive management at the beginning of the incident. This paper analyzed the characteristics of the self-organization of crowds and terrorists in public places during a suicide bombing attack and conducted simulation experiments with an agent-based model. The simulation results show that unobstructed escape routes and controlling external sites will improve the evacuation efficiency of the crowd when a violent terrorist incident occurs; the pedestrian flow in public places affects the overall evacuation time; and timely and effective control of violent terrorists can reduce the number of casualties among the crowd. The optimized strategies obtained through experiments will help public security organs prevent violent terrorist incidents in public places and improve the efficiency of early disposal.
1 Introduction
A series of events occurred, such as the “9•11” terrorist attacks on the World Trade Center in New York and the “3•1”subway bombing in Madrid. International terrorism has gradually become a source of concern for people worldwide. It has also become an important issue affecting world peace and security since the 21st century. There were many innocent deaths and the sacrifice of hundreds of police officers. To effectively address the escalating challenges posed by violent and terrorist situations, international scholars have undertaken comprehensive research examining crowd psychology, emergency management, and the patterns of development in violent terrorist attacks. Wafa Elias [1] studied the impact of terrorist threats from public transportation on people’s travel behavior. Wheatley Sean [2] proposed a method for the police to improve their emergency rescue capabilities during predatory violent terrorist attacks. Michael Freeman [3] believed that violent terrorist attacks follow a certain rule; generally, there are nine stages, and each stage has a fixed progress time, which can be used to indicate the possible future attack time. Gill [4] studied suicide bombing attacks from three different dimensions, which increased our understanding of suicide bombing attacks. In recent years, scholars have begun to pay attention to the research on violent terrorist attacks in public places. Meng et al. [5] proposed an optimized hybrid classifier for the prediction of terrorist attacks. Wang and Ren [6] analyzed the scene characteristics of three types of violent terrorism cases and proposed corresponding emergency measures from the perspective of on-site investigations. Xiao [7] pointed out that public security agencies must establish a multi-technology fusion model quickly and apply it to reality so that we can enhance the ability to prevent and control industrial violent terrorist attacks. At present, the relevant research is still at the theoretical stage. It aimed at preventing all stages of violent terrorist activities, including the prevention of violent terrorist activities, emergency response measures, and on-site investigations.
Over the past 2 decades, as computer simulation technology has gradually matured, there have been an increasing number of research studies about modeling with simulation software. Computer simulation technology is mostly used by foreign academics to simulate the evacuation of pedestrians during acts of violence and terrorism. Martha Mitsopoulou et al. [8] proposed an evacuation model based on cellular automata modeling coupled with a spatial game to solve conflict situations among the anxious crowd. Ameya Bhandarkar et al. [9] proposed a new method for constructing crowd simulation based on the belief, desire, and intention (BDI) software agent of virtual reality (VR) and demonstrated that this method can be used during crowd evacuation management under terrorist bomb attacks in public areas applications. Wang [10] considered the panic behavior of the crowd when establishing the agent model and studied crowding and evacuation when the crowd panicked in public spaces. Li [11] proposed a pedestrian evacuation decision and behavior model in the early stage of terrorist attacks, including a three-stage model of the initial judgment stage, the overall evaluation stage, and the path selection stage. In the aspect of public management, Chai et al. [12] carried out experimental simulations using the NetLogo platform, employing multi-agent simulation and modeling technology. The findings indicate that the decision-making behavior of both the government and terrorists is influenced by factors such as the government’s anti-terrorism force scope, its effective area of strict prevention and control, and various other factors. In terms of application technology, Meng [13] realized the simulation of violent terrorist detection based on the fusion of two-channel videos. Zhang [12] realized intelligent identification method simulation through the violent and terrorist actions of the crowd in airport areas. Lu [14] applied an agent-based model to explore the dynamics of human behavior under common shooting risks. Khamis [15] established a crowd evacuation model based on the social force model (SFM) to represent crowd dynamics and optimize the optimal position of exit doors during evacuation. Xi [16] computationally examined the consequences of people’s actions during a university campus attack using a combination of agent-based simulation and GIS mapping.
Creating a safe and stable social environment is important under the background of the national security concept [17]. It is the duty of public security agencies to combat violent terrorist activities in an all-around way and suppress the rampant acts of violent terrorists. Since the related research mainly focuses on psychology, emergency management, criminology, and other fields, there are very few studies that focus on violent and terrorist attacks from the public security perspective. Replicating violent terrorist attacks is virtually difficult, and the records that were collected are not extremely significant for public security agents’ jobs. Considering the safety factors, suicide bombing attack simulation on the computer is an efficient method to deal with this problem [18].
This paper analyzes the characteristics of suicide bombing attacks, utilizing incidents that occurred in China as a contextual backdrop. Employing AnyLogic and drawing on the social force model, we conduct agent modeling for both crowds and terrorists to investigate crowd evacuation behavior.
1.1 Crowd simulation model
In the 1970s, researchers introduced modeling methods for simulation studies to better study the evacuation behavior [19]. Currently, there are two main types of evacuation modeling studies: macro and micro models. Macroscopic models mainly include fluidics and dynamics models. The macro model modeling rules are relatively simple, but the simulation is not accurate enough. To more accurately model the response to the evacuation behavior of evacuees, scholars have established many microscopic models, including the social force model, cellular automata model, and multi-agent model.
The multi-agent model is a collection of multiple agents under certain rules, which belongs to a type of agent-based simulation model. The model can not only model the behavior and psychological state of evacuating individuals from a microscopic point of view but also reflect the evacuation behavior of the whole group; therefore, many scholars use the multi-agent model to study the crowds’ evacuation behavior. Pan X et al. [20] presented a multi-agent-based framework for simulating human and social behavior during an emergency evacuation. Zhang L et al. [21] proposed a multi-agent evacuation model to simulate the pedestrian evacuation process in the stadium with or without obstacles. Wang F et al. [22] developed a subway evacuation simulation model based on Pathfinder and simulated the evacuation of platforms, station halls, and staircases. Zhang et al. [23] developed simulation software based on the multi-agent model to study the relationship between civilian characteristics and the event consequence of a slashing event. Lu et al. [14] applied the agent-based model to explore the dynamics of human behaviors under the common risk of shooting. The social force model is also a type of microscopic model and was first proposed in 1995 [24]. The social force model is based on Newton’s law of mechanics, which simplifies pedestrians into simple particles and applies mechanical formulas to describe the crowds’ evacuation behavior. To better restore the real pedestrian evacuation behavior, after the social force model was proposed, some scholars made some modifications and extensions to the social force model. Liu [25] modified the social force model from the two aspects of evacuees and attackers and studied the evacuation behavior of the people in the event of a terrorist attack in a public place. Additionally, certain simulation software utilizes the social force model as its foundation. Notably, AnyLogic stands out as a representative tool that has extensively been employed in crowd evacuation research. The research model of this paper is realized in AnyLogic.
1.2 Study of suicide bombing attacks
Suicide bombing attacks are a unique method of terrorist attack that occurs globally. It causes more profound psychological damage to crowds than traditional NSBAs and has a significantly higher number of deaths and injuries, making it a major public safety issue. In recent years, scholars have studied suicide bombing through different aspects to do their best to eliminate the hidden dangers and prevent the event. For example, Filote et al. [26] believed that violent suicide attacks are related to religious conflicts. Based on data from 1981 to 2010, the study concluded that religious conflicts are the main cause of suicide attacks. The study identifies suicide attacks in a particular area and can provide help in predicting terrorist activities in a particular area. Ferooz et al. [27] employed data mining to prevent and predict the occurrence of suicide bombing attacks. Completely eliminating the occurrence of such events at this stage is not realistic. The key focus shifts to implementing effective preventive measures before a suicide bombing attack occurs and efficiently evacuating the crowd when such an event transpires, which is crucial for minimizing casualties. People’s perception of risks during a suicide bombing attack is very strong, which will stimulate them to be more eager to evacuate and, at the same time, more cautious about successive bombing attacks [28]. Therefore, it is important to study the evacuation behavior of people under suicide bombing. Bernardini and Quagliarini [29] analyzed the evacuation behavior of pedestrians through the collection of video tapes of terrorist attacks, highlighting the special evacuation behaviors under terrorist attacks (including suicide bombing), and providing support for the development of a simulation model for evacuation from a terrorist attack. Shendarkar [30] developed VR training software based on AnyLogic to simulate crowd evacuation behavior in case of a bomb attack. Imana and Kirk [31] proposed a Monte Carlo simulation tool based on the multi-agent system. The tool investigates the effect of shock waves on the human body during suicide bombings, and it evaluates the impact of the number of human density casualties during a suicide bombing attack. When suicide bombing attacks occur, people’s desire to survive will be stimulated. People will quickly make judgments about their location and the location of the safety safe exit, and then, they escape at a faster speed. However, the speed of the crowd will slow down due to the high density of people in public spaces and insufficient evacuation space [32]. Under the combined effect of panic psychology and speed limit, people are more likely to make some irrational behaviors, such as overtaking, herding, and re-entry. In the process of handling violent terrorist attacks, public security agencies should take different measures against different terrorists. Violent terrorists form teams in different ways and complete the violent terrorist attacks by different means, and the effects are usually different. For example, studying the methods of violent terrorist teams forming and the characteristics of different crimes committing methods is of great significance during a suicide bombing attack. Since China has different national conditions from other countries, we have implemented a very strict gun and ammunition control system. It is relatively difficult for terrorists to obtain guns and ammunition. Therefore, domestic violent terrorist attacks mostly select hacking, combustion and explosion, and car collision. The explosive violent terrorist attacks include combustion and explosion, and the tools of crime include gasoline drums and explosive devices, which can generally cause large-scale casualties. Incendiary violence is the same as knife-and-axe attacks in terms of location and target selection. The main differences are as follows: 1) Since both combustion and explosion occurred in an instant, the people next to the explosive device had no time to react. 2) Many of the makers of explosive cases are influenced by extreme ideas, such as "martyrdom into heaven,” and they often tie the explosive device to their bodies, mix in the crowd, and detonate them so that they can enter "heaven.” Since public security organs have become more stringent in investigating controlled knives and the raw materials for making explosive devices have become significantly difficult to obtain, more and more terrorists have replaced criminal tools with private cars commonly owned by people. The main characteristics of car terrorist collisions are as follows [33]: 1) The main body of the attack is diversified. The main body of using automobiles to make terrorist attacks includes violent terrorist teams and individual violent terrorists. 2) Violent terrorists have diversified attack tools. The violent terrorists use cars as a collision tool, and then, they may continue to use attacks such as hacking, combustion, and explosion. 3) Violent terrorists have a wide range of targets. Any location accessible by car becomes a potential target for violent terrorists. This includes streets with heavy traffic, landmark buildings, critical infrastructure, and government offices [34].
Through the analysis of surveillance videos obtained from the scene of the suicide bombing attack, certain distinctive behaviors emerge, deviating from the general situation previously summarized. This case is not actually a car bomb terrorist attack in the traditional sense, but a form of “car collision, combustion, and explosion.” The main damage caused is reflected in the malicious collision of entering the fence in the early stage, which caused people to be unable to dodge, and the damage caused by terrorists in a car igniting the gasoline drum when the car was unable to move forward when the fence was smashed into the fence in the later stage. The previous malicious collision incident is an unexpected incident that cannot be predicted. The response of the crowd has been summarized in the previous paper, so it will not be repeated in this study. In addition, anti-collision fences have been installed near the bridge, and security forces have been arranged nearby, so such special behaviors will not be analyzed and countermeasured. There is another point worthy of our attention: why are there many people around when the violent terrorist’s vehicle crashes into the railing and cannot move forward? This specific conduct caused a great deal of casualties in the combustion and explosion that followed.
In this paper, an agent suicide bombing attack simulation model-based method is used to conduct a suicide bombing attacksimulation experiment on the preliminary disposal of violent terrorist incidents, based on an actual and influential example.
2 Model
Suicide bombing attack simulation provides a good solution for solving various difficulties in the real world. Most of the time, if you find the correct solution through physical experiments, the cost is often too high and impractical. For example, to realistically simulate a violent terrorist incident, individuals must assume roles as perpetrators and victims, and suitable venues, props, and other elements must be present. Such suicide bombing attack simulation experiments will consume huge manpower and material resources and are full of danger and uncertainties. Therefore, this paper chooses to use AnyLogic to build a model that mimics the real world in the computer. An abstract method was adopted, the important parts related to the research were retained, and other details were discarded to make the operation of the model easier. In this paper, we comprehensively considered the behavior characteristics of the crowds and terrorists in large public spaces mentioned above. After investigating the case of the suicide bombing attack, comprehensive modeling was carried out to ensure the objectivity, authenticity, and science of the simulation.
2.1 Background settings
One day in 2013, a jeep broke into the sidewalk and drove from east to west. On the way, it crashed into many tourists and hit the guardrail of a bridge. In the end, the terrorists in the car set fire to the gasoline tank, causing the car to burst into flames.
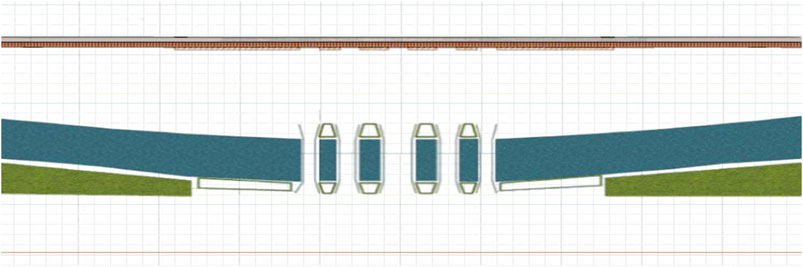
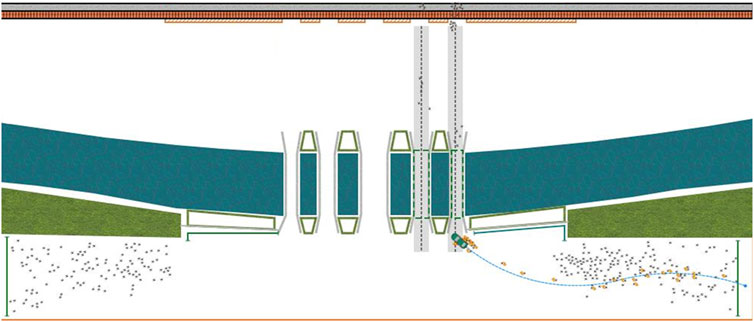
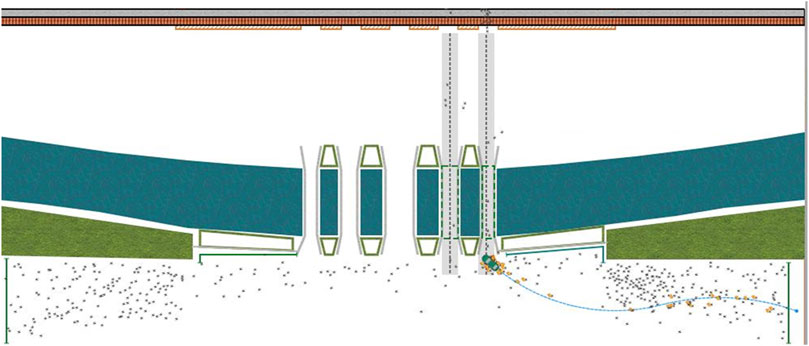
The bridge is situated in the central area of a specific city, in front of a square adorned with other bridges. There are five bridges in total, which correspond to the five gates of the square gate. The bridge body is 23.15 m long, and the distance between the bridges is 5 m. The five bridges are symmetrical along the central axis. The middle bridge is 8.55 m wide; the left and right bridges are 5.28 m wide, and the outermost two bridges are 4.55 m wide. Outside the bridge is a sidewalk. Tourists from the east and west of the street will always gather at the bridge, stopping to watch, and take photos; thousands of tourists gather in this area at the most. The satellite view of the bridge is shown in Figure 1.
The modeling platform used in this paper is AnyLogic, and the satellite plan of the bridge and surrounding environment is used for modeling. The simulation diagram of the bridge is shown in Figure 2.
2.2 The underlying logic of the model: the social force model
There are dozens of available suicide bombing attack simulation models which can be divided into discrete and continuous models according to whether the representation of the space is continuous [35]. The former is mainly a cellular automaton model (including its special lattice gas model), and the latter has a social force model, a fluid mechanics model, a magnetic force model, etc., represented by the social force model.
The suicide bombing attack simulation model used in this paper is mainly based on the social force model. The social force model was proposed by Helbing in 1995 and has been widely studied in academia [36]. In the social force model, each person is described as a Newton-like particle driven by a force. The force experienced by the individual can be caused by physical contact or be driven by psychological factors. During the movement, people are attracted by the destination to produce a self-driving effect, and they also constantly adjust their speed during the movement to avoid collisions with others and obstacles. In the event of physical contact with others or obstacles when in contact, physical forces are generated, including the elastic force in the normal direction and friction force that may be generated in the tangential direction [37]. Therefore, in the social force model, the person i is mainly driven by three types of forces, namely, self-driving force FDi, social force FSi, and physical force FGi, as shown in formula (3-1). Among them, the first two are psychological forces, which describe the impact of psychological effects on people, and the latter is physical force, which describes the elasticity or frictional force formed by physical contact with people.
Among them, t represents time, mi represents the quality of person i, and vi is the speed of person i. The social force model introduces the concept of “expected speed” to describe the speed of movement that people expect to achieve. When a person causes a difference between the actual speed and the expected speed due to some reason, the self-driving force will play an important role to make the actual speed move closer to the expected speed, as shown in the following formula:
where v0, i represents the expected speed of person i; τ is the relaxation time.
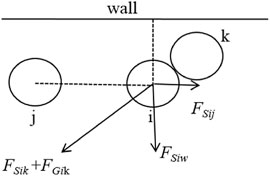
The social force FSi describes the psychological force produced by the influence of the surrounding people and obstacles on the person i. People usually want to maintain a certain distance from the surrounding people and obstacles, so FSi is a repulsive force. It is the vector sum of the repulsive forces of all other person j and obstacles w, as shown in the following formula:
The psychological repulsion of a person depends on the position of the person in line with the repelled object. The social force FSi generated by other person j is shown in the following formula:
Among them, A and B are both normal quantities, which are used to measure the intensity and scope of social force. εij represents the collision distance between person i and j, as in formula (3-5). Among them, Ri and Rj are the radii of persons i and j, and dij is the distance between the centroids of i and j.
It is easy to know that when εij is greater than 0, personnel i and j have physical contact; otherwise, there is no contact. Formula (3-4) shows an exponential increase in social force with a decrease in the distance between individuals. The direction of FSij is denoted by nij, which is a unit vector from person j to person i. Social forces are anisotropic, which is manifested in the fact that people have different repulsive forces for obstacles in different directions. For example, the psychological force caused by obstacles in front of people is greater than obstacles behind people when other conditions are the same. The parameter λ is used in the model to characterize the anisotropy of social forces. Angle θij represents the angle between vectors vi and nij. The social force FSiw generated by obstacles can be obtained in a similar manner.
The physical force FGi generated by the contact of person i with others or obstacles is also the vector sum of the forces received by a single person and obstacles, as shown in the following formula:
The physical force comprises two parts; one part is due to the elastic force in the normal direction. The other part is the friction force caused by the speed difference in the tangential direction. Below, we consider the physical force generated by a single person j as an example.
The right side of formula (3-7) contains two items, which represent the elastic force in the normal direction and the friction force in the tangential direction. Among them, k and κ are normal quantities, representing the strength of elasticity and friction, respectively. vij = vi - vj represents the relative speed of personnel i and j. tij represents the tangential unit vector of personnel i and j. The function g(εij) is the larger value of εij and 0, indicating that the physical force only works when a person is in contact. The schematic diagram of the force exhibited by the person in the social force model can be seen in Figure 3, which shows the force exhibited by person i by the wall, the person j, and k. The self-driving force is not marked in the figure. The figure shows the force exhibited by the person i by the wall, person j, and k.
2.3 Agent setup
The model constructed in this paper is based on the pedestrian flow suicide bombing attack simulation in AnyLogic suicide bombing attack simulation software [38]. The suicide bombing attack simulation platform is based on the human social force model at the beginning of the development. As a result, when we model crowds, pedestrians automatically adopt the social force model and avoid obstacles and other pedestrians, which are not considered. However, the modeling of crowds and terrorists in panic states cannot be setup according to the social force model, but we can describe their special behavior by setting parameters and rules.
2.3.1 Crowd agent setup
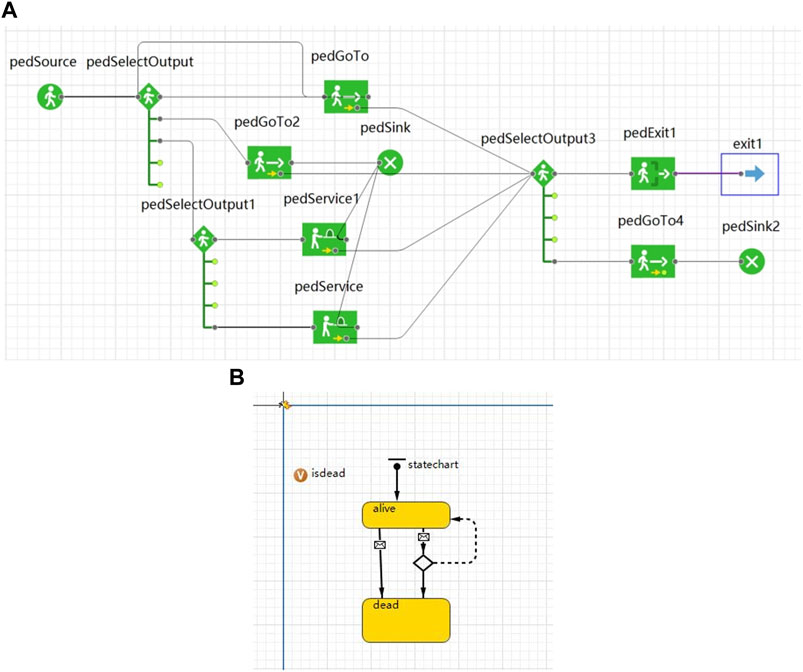
We set up the pedestrian logic in AnyLogic to define how the crowd walks and moves in the model and use a state diagram to define the different states of the pedestrian. For the crowd, “alive” is the pedestrian’s “alive” state and “dead” is the pedestrian’s “dead” state. We set the rules that there are two trigger transitions from “alive” to “dead” state, which means pedestrian deaths can be triggered in two ways—by a car crash or by a car explosion, as shown in Figure 4.
At the same time, we set the overtaking behavior, the following behavior, and the re-entry behavior of the crowd in the panic state after a violent terrorist event and introduce the variable of disaster awareness into the model. The crowd’s real reaction state after the occurrence of the riot was simulated by setting the walking state and speed of the crowd in the three stages before, during, and after the occurrence of the riot.
2.3.2 Terrorist agent setup
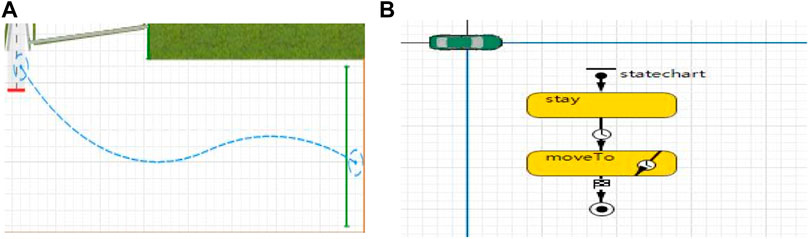
According to the case study, the terrorists maneuvered their vehicles along the eastern sidewalk, striking numerous individuals enroute, ultimately coming to a halt at the base of the bridge. In this paper, a simple vehicle route diagram is drawn through the process modeling library, and the state diagram is used to clear the change of vehicle driving state. “Stay” means the vehicle is in a state of waiting, “Move to” means the vehicle is in a state of advancing, and finally, “final state” means the vehicle has hit the bridge and stopped, as shown in Figure 5.
2.4 Model parameter and rule setting
2.4.1 Environment parameter setting
In this paper, the scale is changed to 1 m equal to 5 pixels based on the approximate proportionality between the real scene and modeling figure. The height of the railing and pedestrian fence of the bridge is changed to 7.5 pixels, and the river is changed to 25 pixels, city wall construction, and press default pixels.
2.4.2 Pedestrian parameter setting
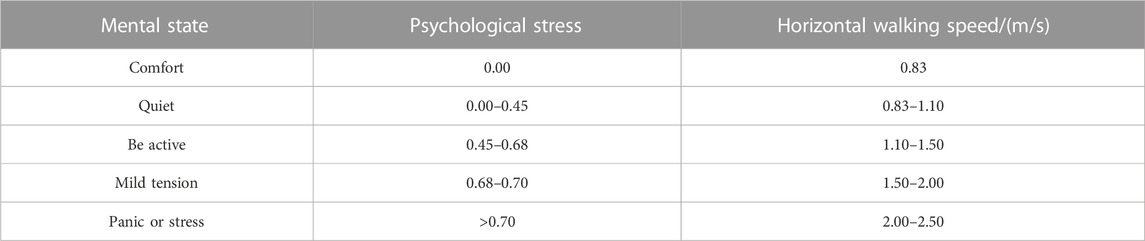
Usually, the walking speed of pedestrians is not only related to the psychological state but also related to factors, such as age, sex, physique, and environment. However, for the convenience of modeling, this paper only considers the mental state effects on a pedestrian’s walking speed. A researcher has conducted a survey to study the walking speed of pedestrians under different psychological pressures, as shown in Table 1 [39].
The pedestrian’s walking speed was set to 0.83 m/s when comfortable. The walking speed will be 2–2.5 m/s when the pedestrian is in a state of panic. In the simulation, pedestrians will be generated from the east and west directions of the street. For the convenience of the study, the default pedestrian is generated randomly at both ends at a rate of 200 person/min. The time required for each pedestrian to enter the square is usually distributed in a triangle. The fastest time is set at 5 s, and the slowest is 25 s. The average time is 15 s.
2.4.3 Parameters of the terror vehicle
To enhance the realism of the simulation, the simulated terrorist activity was initiated when the model had a higher pedestrian count. Therefore, the start time of the terrorist event was configured to be 4 min after the model commenced. After reviewing the surveillance footage of the bridge terror attack, we assumed that the vehicle’s speed ranged from 50 to 70 km per hour at the moment of impact with the crowd. Consequently, we standardized the speed to a median value of 60 km per hour. To simulate a pedestrian being struck, we needed pedestrians to fall within a specified distance of the vehicle. Consequently, we fixed the vehicle’s width at 2 m.
2.4.4 Simulation rules
First, this paper defines the action of a riot vehicle, which is set to start at 4 min when the model is running. Then, the vehicle will start at the starting point and drive along the designated route to the endpoint. When the vehicle is moving, a message can be delivered every 0.1 s to simulate a pedestrian falling after being struck by a car. A pedestrian within 1 m of the vehicle will receive a message from the vehicle. Once the message is received, it immediately shows the casualty status; at this point, it means that pedestrians have been hit by vehicle casualties. Finally, as the terrorist vehicle approached the bridge, it collided with the bridge’s guardrail, resulting in an explosion. Debris and shock waves from the explosion have the potential to harm pedestrians from a distance. Video surveillance indicates that a vehicle’s gasoline explosion can impact an area at approximately 2 m wide. Consequently, the software configures the car to transmit a specific message upon explosion. Pedestrians within a 2-m radius of the car receive this message, simulating their state to resemble that of a pedestrian who was hit or killed.
Analyzing the video surveillance footage of the riot and terrorism incident reveals the high speed of the vehicle. Most pedestrians were hit by the car without a second thought. Only upon the vehicle’s explosion did unaffected pedestrians start to comprehend the danger and initiate their escape. Pedestrians in the process of escape will always judge the nearest intersection from their own to make the best path choice. In the simulation, to simulate the scene of pedestrian escape, we introduced a function into the pedestrian agent, according to which the pedestrian will calculate the nearest exit distance and choose the escape route.
3 Simulation and results
3.1 Pre-experiment and model optimization
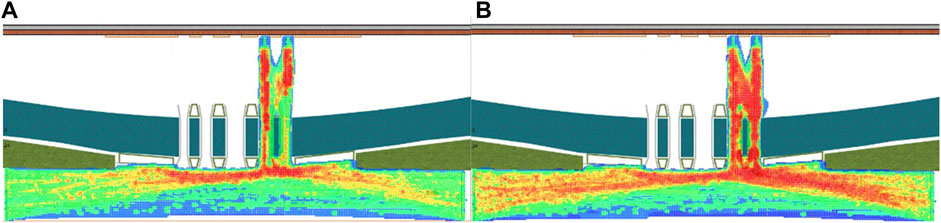
After following the described processes, the model is created and executed, as shown in Figure 6A, depicting the population density right before the explosion. As can be observed, the crowd density distribution was primarily focused on the south side of the bridge, the east side of the two open bridges, and the gate before the car explosion, which is consistent with the real circumstances. One minute after the terrorist attack, the crowd’s concentration shifted to the east and west sides of the sidewalk. A significant change observed was the opening of the eastern bridge, aligning with the typical pattern of crowd evacuation.
However, after running simulations, we found that there remained a large number of people on the east and west streets of the avenue. This is because, in the model, we only defined the pedestrian evacuation that had started at the time of the explosion, but we ignored the fact that pedestrians were also being generated on both sides of the avenue and that they would continue to pass through the bridge and stand in line for tickets, and this is clearly not rational. Therefore, we add a function to govern the generation of pedestrians stopping when the explosion occurs to optimize the model. The running effect of the model at the same time is shown in Figure 7.
The visual module visually displays that the model of the pedestrian has been significantly reduced, and the control scene has not only achieved a certain effect but also in line with the actual situation. Simultaneously, it provides inspiration that during on-site crowd evacuation, beyond initiating an escape route and providing effective guidance, the timely control of the surrounding scene is crucial. This prevents additional crowds from flooding into the scene of violent terrorism, mitigating overcrowding and ensuring the timely evacuation of the incident center.
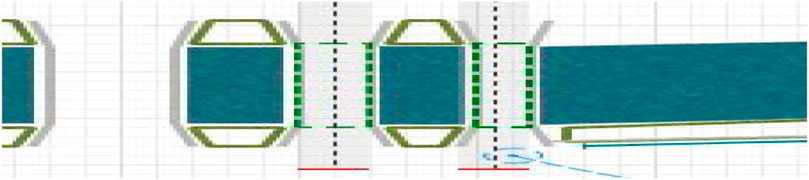
From the crowd density map, we can qualitatively find some rules of crowd evacuation after violent terrorist events to better understand the crowd evacuation mode and the impact of violent terrorist events; next, we take the quantitative research method to carry on the experiment. We plotted two areas on the two easternmost bridges of the model, as shown in the dotted rectangle in Figure 8. The following experiment calculates the number of people in the region per second and analyzes the results through numerical arithmetic examples to draw our conclusion.
3.2 Suicide bombing attack simulation with secure access
Running the model, the number of pedestrians on the two bridges after the explosion is shown in Figure 9.
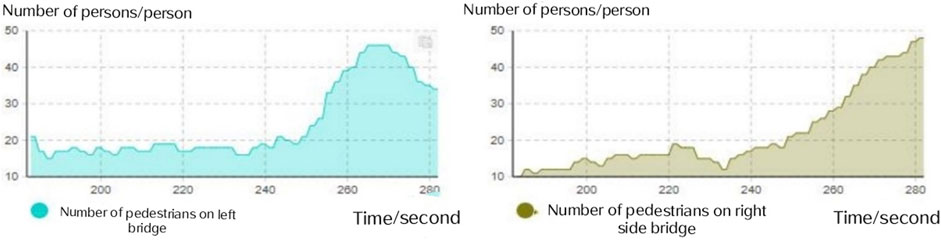
The number of pedestrians on the left side of the bridge increased after the explosion (approximately 245 s), reaching a peak of 45 in approximately 265 s, and then began to fall. The number of pedestrians on the right side of the bridge increased from 280 s after the explosion to 48 in 280 s. The operating diagram of the model is shown in Figure 10. It was clear that there were far more pedestrians on these two bridges than anywhere else throughout the evacuation. When the person in front recklessly goes down, there will be a big stampede since the throng has been stuck on the bridge for a long time and is combined with the panic of pedestrians. Additionally, the evacuation of people from the side of the bridge deck that has been damaged by the explosion also has significant irrationality and danger, and if the vehicle has a second explosion, then it endangers the safety of all people on the bridge.
Next, we change the model according to the basic hypothesis above and add the safe passage at the two entrances of the tower. When danger occurs, the check-in service will close automatically, and the safe passage will open automatically. Pedestrian evacuation will take these two passages into account, according to their own distance to make the best escape route. The results are shown in Figure 11.
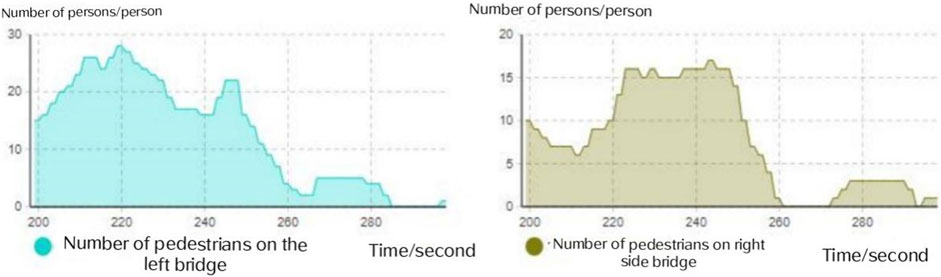
In contrast to Figure 10, we can see the following difference: after the explosion, the number of people on the two bridges, after a brief increase, showed a rapid decline. At 280 s, there were fewer than five people on both bridges, and the model is shown in Figure 12. This has tested our basic hypothesis and concluded that in the event of danger, the timely opening of a safe evacuation channel to guide pedestrians away from the nearest plays a crucial role in early disposal.
3.3 Crowd suicide bombing attack simulation experiments with different traffic flows
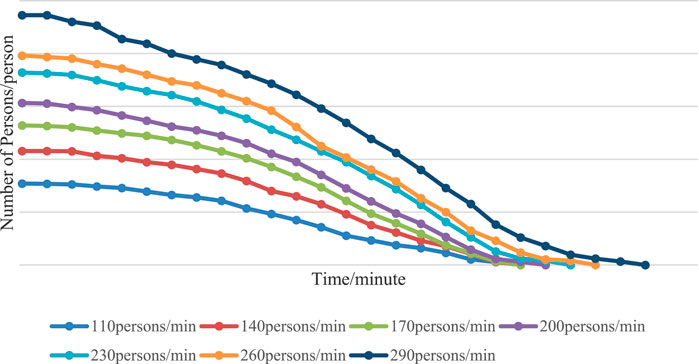
It is assumed that the pedestrian flow (the rate of pedestrian generation) is 120 people/min in the above models and experiments. In real life, the number of people in each place is related to time, weather, or the popularity of the place. To investigate the effect of pedestrian flow on pedestrian evacuation efficiency, we tested our fourth hypothesis. In this paper, the pedestrian flow is set to 110 persons/min, 140 persons/min, 170 persons/min, 200 persons/min, 230 persons/min, 260 persons/min, and 290 persons/min, as shown in Figure 13.
In the case of different pedestrian flows, pedestrian evacuation is generally consistent with the law. The initial decline in pedestrian numbers over time was very slow, lasting approximately 20 s until 265 s when the number of pedestrians dropped rapidly over time and then moderated in the last 20 s. This also reflects the scene of violent terrorist incidents, and people from the gathering to the evacuation of the phenomenon of exit. In the early stage of evacuation, the crowd mainly concentrated in the center site, and the pass rate of pedestrians at the safety exit was very low. The safety exit’s pass rate significantly increased as more people rushed out of the center site, while the number of pedestrians there swiftly declined. In the later stages of the evacuation, most of the crowd had already left, leaving only a few individuals who were farther away and moving slowly. Consequently, the number of pedestrians dwindled, approaching a more moderate level.
The curve contrasts that concretely arrives different person discharge, can see the apparent difference. When the pedestrian flow is small (110 people per minute, 140 people per minute, and 170 people per minute), the total number of pedestrians is different at the beginning of the evacuation, but the time taken to complete the evacuation is basically the same. It becomes obvious that when the pedestrian flow increases—usually when it exceeds 170 persons per minute—it will take longer and longer for everyone to leave the area. In real life, it is often seen that some public places limit the flow of people or the number of visitors to the park. This practice serves the dual purpose of catering to the majority’s requirements and accounting for the spatial capacity and efficiency of safety evacuations. Due to crowding and a lack of space, the overall evacuation efficiency will significantly decrease when the flow of people surpasses a particular amount.
4 Conclusion
In this paper, we model the crowd and terrorist agents in AnyLogic to reproduce a real violent suicide attack that happened in China as a background. The simulation is carried out under increasing exits and at different crowd flows. The simulation results are as follows:
(1) During the evacuation, the pedestrians on the two bridges are more likely to be affected by the panic psychology of the stampede. The evacuation of people on the side of the bridge damaged by the explosion also has significant irrationality and danger, and if the vehicle has a secondary explosion, then it will jeopardize the safety of all the people on the bridge.
(2) Safe channels are very important for the safe evacuation of crowds. The safety channel at the two entrances of the tower was increased. When danger occurs, pedestrians can make the best escape route according to their distance and leave the bridge in a short time.
(3) When the flow of people is small (110 people/minute, 140 people/minute, and 170 people/minute), the evacuation time is basically the same, but as the flow of people continues to increase, the evacuation time becomes longer and longer. When the flow of people exceeds a certain value, the overall evacuation efficiency will be greatly reduced.
Based on the above simulation results, we can draw the following conclusion for crowd management during bombing attacks.
(1) In the early stage of a terrorist attack, people will flee for their lives in a state of panic. Therefore, it is very important to set safe escape routes. The crowd may become congested since the space can suddenly become narrow on bridges, stairs, corridors, and other places [40]. It will not only affect the overall evacuation time but also cause secondary disasters, such as stampedes. When a violent terrorist attack occurs, the police on arriving at the scene should first clear other safety exits in time and guide pedestrians to evacuate from different safety exits. This action can improve crowd evacuation efficiency and reduce the harm brought by crowding.
(2) When pedestrians flood out of a violent terrorist attack center, there will be a large-scale traffic jam. If uninformed people or curious onlookers enter the center, they will collide with the evacuees, which may lead to less efficient evacuation. To improve evacuation efficiency, public security agencies should arrange personnel to carry out peripheral control, such as pulling a police cordon, hand-in hand to create a human wall, and other measures to guide the evacuation and prevent other onlookers in.
These conclusions can provide some suggestions for public security agencies to take effective measures when dealing with violent terrorist attacks. However, there are still some limitations that need to be further studied and improved in this paper.
(1) Some data, such as the rate of pedestrian generation, and the time of ticket queue needed in this paper are obtained through literature review and general theory which lack field investigations. Future research work must use data obtained through field surveys to guarantee the accuracy of the research results.
(2) Due to the limitation of a simulation software module, the model is simplified and some unimportant details are neglected. We cannot simulate these violent and terrorist events completely. The model still needs to be further improved.
Data availability statement
The raw data supporting the conclusion of this article will be made available by the authors, without undue reservation.
Author contributions
ND: conceptualization, formal analysis, and writing–original draft. ZF: resources and data curation. XZ: visualization. SL: supervision. YW: writing–reviewing and editing.
Funding
This work was supported by the National Natural Science Foundation of China (72274208) and the Basic Research Foundation of People’s Public Security University of China (2022JKF02010). The grantee is Ding Ding.
Conflict of interest
The authors declare that financial support was received for the research, authorship, and/or publication of this article.
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Elias W, Albert G, Shiftan Y. Travel behavior in the face of surface transportation terror threats. Transport Policy (2013) 28:114–22. doi:10.1016/j.tranpol.2012.08.005
2. Wheatley S, Hollingsworth AC, Greaves I. Responding to the marauding terror attack: the police perspective. BMJ Mil Health (2020) 166(2):80–3. doi:10.1136/jramc-2018-000960
3. Freeman M, Tucker D, Merten S. Pathways to terror: finding patterns prior to an attack. J Policing, Intelligence Counter Terrorism (2010) 5(1):75–85. doi:10.1080/18335300.2010.9686942
4. Gill P. A multi-dimensional approach to suicide bombing. Int J Conflict Violence (Ijcv) (2007) 1(2):142–59.
5. Meng X, Nie L, Song J. Big data-based prediction of terrorist attacks. Comput Electr Eng (2019) 77:120–7. doi:10.1016/j.compeleceng.2019.05.013
6. Wang N, Ren HC. On-the-spot characteristics of violent terrorism cases and emergency measures. Public Security in China (2018)(02) 35–9.
7. Xiao J. Construction and application of police anti-terrorism multi-technology fusion model under artificial intelligence background. J China Criminal Police Coll (2019)(04) 12–7.
8. Mitsopoulou M, Dourvas NI, Sirakoulis GC, Nishinari K. Spatial games and memory effects on crowd evacuation behavior with cellular automata. J Comput Sci (2019) 32:87–98. doi:10.1016/j.jocs.2018.09.003
9. Shendarkar A, Vasudevan K, Lee S, Son Y-J. Crowd Suicide Bombing Attacks Simulation for emergency response using BDI agents based on immersive virtual reality. Suicide Bombing Attacks Simulation Model Pract Theor (2008) 16(9):1415–29. doi:10.1016/j.simpat.2008.07.004
10. Wang J, Zhang L, Shi Q, Yang P, Hu X. Modeling and simulating for congestion pedestrian evacuation with panic. Physica A: Stat Mech its Appl (2015) 428:396–409. doi:10.1016/j.physa.2015.01.057
11. Li S, Zhuang J, Shen S. A three-stage evacuation decision-making and behavior model for the onset of an attack. Transportation Res C: Emerging Tech (2017) 79:119–35. doi:10.1016/j.trc.2017.03.008
12. Zhang N, Zhu JF. Suicide Bombing Attacks Simulation of intelligent recognition method for crowd violent and terrorist action in airport area. Comp Simulation (2015) 32(06):67–70.
13. Cai X. Suicide Bombing Attacks Simulation of terrorist detection based on fusion of two-channel video. Computer Simulation (2015) 32(02):428–31.
14. Lu P, Wen F, Li Y, Chen D. Multi-agent modeling of crowd dynamics under mass shooting cases. Chaos, Solitons and Fractals (2021) 153:111513. doi:10.1016/j.chaos.2021.111513
15. Khamis N, Selamat H, Ismail FS, Lutfy OF, Haniff MF, Nordin INAM. Optimized exit door locations for a safer emergency evacuation using crowd evacuation model and artificial bee colony optimization. Chaos, Solitons and Fractals (2020) 131:109505. doi:10.1016/j.chaos.2019.109505
16. Xi JYS, Chan WKV. Simulation of knife attack and gun attack on university campus using agent-based model and GIS[C]. In: 2019 Winter Simulation Conference (WSC); December 8-11, 2019; National Harbor, MD, USA (2019). p. 263–72.
17. Xiao X, Men H, Xiao X Optimizing the concept of national security and creating a path to national security with Chinese characteristics. Chin Diplomacy New Era (2021) 81–96.
18. Usmani Z, Imana EY, Kirk D. 3D simulation of suicide bombing–using computers to save lives. Technological developments in education and automation. Netherlands: Springer (2010). p. 489–94.
19. Henderson LF. The statistics of crowd fluids. nature (1971) 229(5284):381–3. doi:10.1038/229381a0
20. Pan X, Han CS, Dauber K, Law KH. A multi-agent based framework for the simulation of human and social behaviors during emergency evacuations. Ai Soc (2007) 22:113–32. doi:10.1007/s00146-007-0126-1
21. Zhang L, Wang J, Shi Q. Multi-agent based modeling and simulating for evacuation process in stadium. J Syst Sci Complexity (2014) 27:430–44. doi:10.1007/s11424-014-3029-5
22. Wang F. Multi-scenario simulation of subway emergency evacuation based on multi-agent. Int J Simulation Model (2021) 20(2):387–97. doi:10.2507/ijsimm20-2-co8
23. Zhang F, Wu S, Song Z. Crowd evacuation during slashing terrorist attack: a multi-agent simulation approach. In: 2020 Winter Simulation Conference (WSC); December 14 - 18, 2020; Orlando Florida (2020). p. 206–17.
24. Helbing D, Molnar P. Social force model for pedestrian dynamics. Phys Rev E (1995) 51(5):4282–6. doi:10.1103/physreve.51.4282
25. Liu Q. A social force model for the crowd evacuation in a terrorist attack. Physica A: Stat Mech its Appl (2018) 502:315–30. doi:10.1016/j.physa.2018.02.136
26. Filote A, Potrafke N, Ursprung H. Suicide attacks and religious cleavages. Public Choice (2016) 166:3–28. doi:10.1007/s11127-016-0310-2
27. Ferooz F, Hassan MT, Awan MJ, Nobanee H, Kamal M, Yasin A, et al. Suicide bomb attack identification and analytics through data mining techniques. Electronics (2021) 10(19):2398. doi:10.3390/electronics10192398
28. Al-Dahash H, Kulatunga U, Allali B. Factors affecting risk perception during terrorist attacks. Int J Disaster Risk Reduction (2022) 73:102870. doi:10.1016/j.ijdrr.2022.102870
29. Bernardini G, Quagliarini E. Terrorist acts and pedestrians’ behaviours: first insights on European contexts for evacuation modelling. Saf Sci (2021) 143:105405. doi:10.1016/j.ssci.2021.105405
30. Shendarkar A, Vasudevan K, Lee S, Son YJ. Crowd simulation for emergency response using BDI agent based on virtual reality. In: Proceedings of the 2006 winter simulation conference; 3-6 Dec 2006; Monterey, CA (2006). p. 545–53.
31. Imana EY, Kirk D. Random walk in extreme conditions-an agent based simulation of suicide bombing. In: 2009 IEEE Symposium on Intelligent Agents; Sept. 15 2009 to Sept. 18 2009; Milan, Italy (2009). p. 114–21.
32. Han Y, Liu H. Modified social force model based on information transmission toward crowd evacuation simulation. Physica A: Stat Mech its Appl (2017) 469:499–509. doi:10.1016/j.physa.2016.11.014
33. Pei M, Xia BC. A preliminary study on the group terrorist attack. J Henan Univ Tech (Social Edition) (2019) 20(No.77):38–44.
34. Pei M, Wang M, Quan B, Xia C. Study on the problem of vehicle terror impact. J China Criminal Police Coll (2018) 146:88–95.
35. Goodwin GC, Leal RL, Mayne DQ, Middleton R. Rapprochement between continuous and discrete model reference adaptive control. Automatica (1986) 22(2):199–207. doi:10.1016/0005-1098(86)90081-6
36. Helbing M, Molnár P. Social force model for pedestrian dynamics. Phys Rev E, Stat Phys Plasmas Fluids Relat Interdiscip Top (1995) 51(5):4282–6. doi:10.1103/physreve.51.4282
37. Parisi DR, Gilman M, Moldovan H. A modification of the social force model can reproduce experimental data of pedestrian flows in normal conditions. Physica A: Stat Mech its Appl (2009) 388(17):3600–8. doi:10.1016/j.physa.2009.05.027
38. Borshchev A, Karpov Y, Kharitonov V. Distributed simulation of hybrid systems with AnyLogic and HLA. Future Generation Comp Syst (2002) 18(6):829–39. doi:10.1016/s0167-739x(02)00055-9
39. Kholshevnikov VV, Shields TJ, Boyce KE, Samoshin D. Recent developments in pedestrian flow theory and research in Russia. Fire Saf J (2008) 43(2):108–18. doi:10.1016/j.firesaf.2007.05.005
Keywords: violent terrorist incidents, public spaces, crowds, early disposal, ABM model
Citation: Ding N, Fan Z, Zhu X, Lin S and Wang Y (2024) Multi-agent modeling of crowd dynamics under bombing attack cases. Front. Phys. 11:1200927. doi: 10.3389/fphy.2023.1200927
Received: 13 May 2023; Accepted: 28 November 2023;
Published: 10 January 2024.
Edited by:
Alessandro Vezzani, National Research Council (CNR), ItalyReviewed by:
Feizhou Huo, Wuhan University of Technology, ChinaPratikshya Jena, Indian Institute of Technology (BHU), India
Copyright © 2024 Ding, Fan, Zhu, Lin and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Ning Ding, ZGluZ25pbmdfdGh1QDEyNi5jb20=
 Ning Ding
Ning Ding Zhenyu Fan
Zhenyu Fan