- 1College of Computer Science and Information Engineering, Xiamen Institute of Technology, Xiamen, China
- 2College of Computer and Cyber Security, Fujian Normal University, Fuzhou, China
- 3Digital Fujian Internet-of-Things Laboratory of Environmental Monitoring, Fujian Normal University, Fuzhou, China
Quantum communication networks are connected by various devices to achieve communication or distributed computing for users in remote locations. In order to solve the problem of generating temporary session key for secure communication in optical-ring quantum networks, a quantum key agreement protocol is proposed. In the key agreement protocols, an attacker can impersonate a legal user to participate in the negotiation process and eavesdrop the agreement key easily. This is often overlooked in most quantum key agreement protocols, which makes them insecure in practical implementation. Considering this problem, the function of authenticating the user’s identity is added in the proposed protocol. Combining classical hash function with identity information, we design the authentication operation conforming to the characteristics of quantum search algorithm. In the security analysis of the proposed protocol, quantum state discrimination is utilized to show that the protocol is secure against common attacks and impersonation attack. In addition, only single photons need to be prepared and measured, which makes our protocol feasible with existing technology.
1 Introduction
Communication is the exchange and transmission of information between people in a certain way. With the development of communication technology, people pay more attention to the privacy and security of data. In the present communication networks, RSA public key scheme is widely used for secure communication since it depends on the mathematical problem of large integer decomposition. However, the famous quantum factorization algorithm proposed by Shor [1] shows that this scheme is no longer safe. To ensure the security of communication, the research of quantum cryptography attracts people’s attention. In contrast to the security of classical cryptography that are based on the assumption of computational complexity, the security of quantum cryptography relies on quantum-mechanics principles, which makes it unconditionally secure in theory. Since the first quantum key distribution protocol (BB84 protocol) was proposed [2], people try to solve some secure communication tasks with quantum cryptography, including quantum key distribution(QKD) [2–4], and quantum secure direct communication (QSDC) [5–7].
In addition to key distribution, key agreement (KA) is another major method of key establishment and plays a key role in the field of cryptography. In a key agreement protocol, two or more users in communication networks can agree on temporary session keys to achieve secure communication. As a significant cryptographic primitive, key agreement is flexibly used in multiparty secure computing, access control, electronic auctions, and so on. However, as the concept of quantum computer was put forward, classical key agreement was found to be as vulnerable to quantum computation as classical key distribution. Therefore, quantum key agreement (QKA) has been naturally proposed and has recently become a new research hotspot.
In 2004, [8] proposed the first two-party QKA protocol, which was designed based on the correlation of measurement results of EPR pairs. Unfortunately, this protocol is insecure, as shown in Ref. [9]. That same year, [10] proposed a fair and secure two-party QKA protocol based on BB84. Afterwards, researchers expands the number of negotiators from two to multiple parties to fit the actual scenarios. [11] proposed the first multi-party QKA (MQKA) protocol with Bell states and entanglement exchange in 2013. But in the same year, [12] pointed out that the protocol was unfair, then proposed a new MQKA protocol with single photons. Later [13] introduced two unitary operations and proposed the circle-type MQKA to improve the execution efficiency. Since then, many scholars have used various properties of quantum mechanics to design a few subtle MQKA protocols [14,15].
Actually, these protocols are only theoretically secure. Once they are used in practice, they will inevitably encounter the same problem as classical key agreement, namely, the impersonation attack. That is, an attacker may impersonate a legal user to participant in the protocol. Moreover, in classical key agreement protocols [16–19], the authentication of users is usually considered to protect against this particular attack. However, this is often overlooked in QKA. Although in some MQKA protocols, authentication of classical channels has been required to prevent classical messages from being tampered, message authentication is different from identity authentication. Therefore, in designing a secure QKA protocol, the authentication of users should be considered as in other authenticated quantum cryptographic protocols [20–24].
In this paper, an authenticated MQKA protocol for optical-ring quantum networks is proposed. The result shows that when all users perform the protocol honestly, they can get the correct negotiation key simultaneously. According to our analysis, the protocol in the network is secure against both common attacks and impersonation attacks.
2 Preliminaries
2.1 Review of Communication Network
Let us start with a brief review of quantum communication networks. A communication network is a data link in which isolated individuals share resources and communicate through physical connections of various devices. The classical communication networks mainly consists of three parts: transmission, switching and terminal. According to the topological structure, it can be divided into bus, star, tree, ring and mesh types. Evidently, different types of networks are flexibly applied to different scenarios. This also provides the foundation for the study of quantum communication networks.
Similar to classical communication networks, quantum communication networks can be classified into four types in terms of topology, which are: a passive-star network, an optical-ring network, a wavelength-routed network, and a wavelength-addressed bus network [25–27]. Among them, since the optical-ring topology is lower cost in the construction of the network, it is more conducive to promotion and studied by more people. In 2002, [28] have proposed an efficient multiuser quantum communication network, which can realize the QKD between arbitrary two users in the cascaded loop local networks. Inspired by them, we propose a multiparty quantum key agreement protocol in an optical-ring network.
Unlike the scheme of [28], the communication network in this paper only considers one loop, not a cascade. As shown in Figure 1, the network consist of three parts. 1) A third party. The third party is to facilitate communication between users on the network. 2) Users. Linked via coupled fibers and distributed in the communication network. 3) Switch. At each node, there is a “space optical switch”, which is usually closed. Whenever a session key is required to be established, the photons are transmitted through the optical fiber among all users.
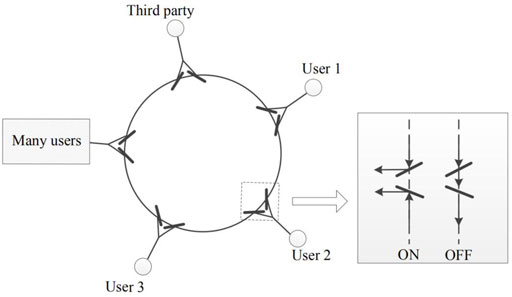
FIGURE 1. An optical-ring quantum communication network. The third party and users of the network are linked with their loop by the coupled fibers. By the “space optical switch”, the photons can be received by the right users.
2.2 Review of Quantum Search Algorithm
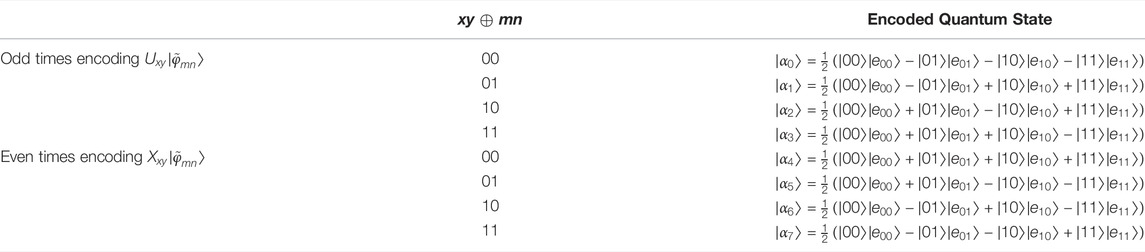
Let us introduce Grover’s search algorithm [29], which is used in the protocol. Suppose that we want to search a target |φmn⟩ = |mn⟩, m, n ∈ {0, 1}, in the database of a set of two-qubit states, i.e.,
where x, y ∈ {0, 1}. In order to search the target, two specific unitary operations need to be performed on
In this paper, since the global phase has no effect on results, it can be ignored.
In addition, the unitary operation Umn has two good properties, which have been used to design some quantum cryptographic protocols [30,31]. We suppose that a total of r operations of Umn are performed on a two-qubit state. On the one hand, when the number of r is odd, there is
where m = m1 ⊕ m2 ⊕⋯ ⊕ mr and n = n1 ⊕ n2 ⊕⋯ ⊕ nr, the symble ⊕ indicates bitwise Exclusive OR. In combination with Eq. 2, we know that the deterministic measurements can be obtained by single-particle measurement with basis MBZ = {|0⟩, |1⟩} at last. When the number of executions is even, there is
where m = x ⊕ m1 ⊕ m2 ⊕⋯ ⊕ mr and n = y ⊕ n1 ⊕ n2 ⊕⋯ ⊕ nr. Then, the measurements can be obtained by single-particle measurement with basis MBX = {| + ⟩, | − ⟩}.
In our protocol, the user encodes his private input by unitary operation Umn. In addition, to assure that the protocol satisfies the characteristics of Grover’s algorithm after identity encoding, we design the identity encoding operations as U00 and U01U10 respectively. In the protocol, the user always encodes his identity information after private input encoding, that is, the encoded quantum state is
3 Quantum Key Agreement Protocol With Identity Authentication
Now, let us describe the proposed quantum key agreement protocol for optical-ring quantum communication networks, which can realize the key negotiation between arbitrary N users in the networks. In this network, a third party P0 is semi-trusted, who can perform the operation Umn. Suppose there are M users in the network and any N of them perform the quantum key agreement. That is, the switches for N users are turned on at the proper time, while the switches for the remaining M − N users are constantly off.
Without loss of generality, assume that the first N users participant in the negotiation, denoted as P1, P2, …, PN. They can not only perform the operations Umn and Vxy, but also have the ability to prepare and measure single particles. They want to negotiate a session key K with the help of P0, where K = S1 ⊕ S2 ⊕⋯ ⊕ SN, and Si is Pi’s private input with length of 2n. Furthermore, each user has an identity information IDi of length l. In order to ensure the legitimacy of these users’ identity, it is necessary for Pi(i = 1, 2, …, N) to complete the identity authentication with P0, who shares master key
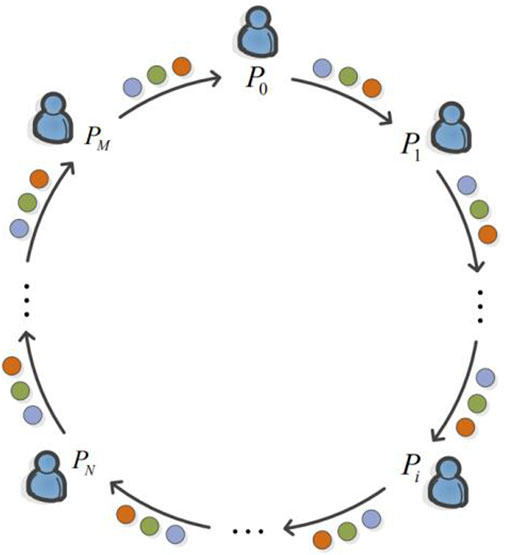
FIGURE 2. (Color online) The detailed performance of the proposed protocol, in which different colored circles represent the particles prepared by different users.
In this quantum communication network, multi parties are connected by a quantum channel and a classical public channel. The quantum channel consists usually of an optical fiber. The classical channel, however, can be any communication link. Users and the third party can send classical messages via the classical channel, and these messages cannot be tampered with by anyone. That is, this transmitted classical message is required to be authenticated. Typically, the public classical channel can be achieved by broadcasting. However, it is worth noting that message authentication is different from identity authentication. So, we still need to verify the identity of each user. In the following, a description of the procedure for the protocol is given.
Step 1: P0 and Pi(i = 1, 2, …, N) generate a random sequence r0 and ri respectively and declare them through the classical channel. Then P0 selects a hash function f: 2∗ → 2n and declares it. P0 and each user calculate their authenticated message
Step 2: Each user Pi(i = 1, 2, …, N) generates a random bit sequence Li = (li,1, li,2, …, li,2n) and Bi = (bi,1, bi,2, …, bi,2n) with length of 2n. In the process with Pi as an initiator, an ordered sequence Ti of n two-qubit states is prepared by Pi according to Li:
where, the tth quantum state is
Step 3: Pi performs the identity encoding operation on the tth quantum state of the sequence Ti according to the values of hi,t and bi,2t−1. Concretely, when hi,t ⊕ bi,2t−1 = 0, Pi performs U00; otherwise, he performs U01U10. Then the encoded sequence is denoted as
Step 4: At this point, Pi⊞1 opens his switch to receive the photons emitted by Pi. When Pi⊞1 receives the sequence
Step (g + 3) (g = 2, 3, …, N): Similar to Steps 4 and 3, Pi⊞g encodes his private input and identity information. After that, he sends the encoded sequence
Step (N + 4): When all users Pi(i = 1, 2, …, N) receive the sequence
1) When B2t−1 is 0, Pi measures the single photon with basis MBX directly to get the measurement result
2) When B2t−1 is 1, according to the classical bit sequence Li, the unitary operation
Obviously, each user Pi can obtain the agreement keys Ki = (ki,1, ki,2, ki,3, ki,4, …, ki,2N−1, ki,2N).
Step (N + 5): The eavesdropping detection process is executed. Namely, all users choose δn samples to detect whether malicious or forged users exist. Specifically, each user Pi randomly selects
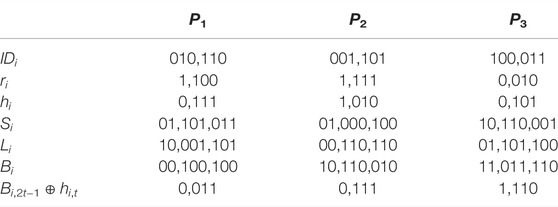
To illustrate the negotiation process more clearly, we give an example with (N = 3, M = 5). Similarly, we assume that P1, P2 and P3 are involved in key negotiation and the switches for P4 and P5 are always off. In this case, P1, P2 and P3 respectively hold secret inputs with length of 8 (i.e. n = 4), S1 = 01,101,011, S2 = 01,000,100, and S3 = 10,110,001 and identity information with length of 6, ID1 = 010,110, ID2 = 001,101, ID3 = 100,011. By the following steps, they can agree on a session key, K = S1 ⊕ S2 ⊕ S3.
In Step 1, each user Pi(i = 1, 2, 3) gets the random string ri. In addition, P0 generates r0. Then, they can obtain the hash values hi according to the selected hash function. In the next step, P1(P2, P3) generates two random 8-bit strings L1 and B1 (L2 and B2, L3 and B3). From L1(L2, L3), P1(P2, P3) prepares the single photons to obtain the two-particle sequence T1(T2, T3). The concrete values of these classical bit sequences are listed in Table 1.
After that, they proceed to the encoding phase of the protocol. The process with P1 as the initiator is described in detail, where the sequence T1 is back to P1 after being encoded by all users. Concretely, in Step 3, P1 performs the unitary operations U00 ⊗ U00 ⊗ U01U10 ⊗ U01U10 to encode his identity information. Afterwards, P1 transmits the encoded sequence
4 Analysis of the Protocol
For a quantum key agreement protocol, it is generally required to satisfy correctness and security, regardless of the structure of the communication network. That is, all users can get the correct session key by executing the protocol. Security, on the other hand, implies that no attacker can obtain any information about the session key without being detected. Analysis shows that it can resist not only common external and internal attacks, but also impersonation attack.
4.1 Correctness
Obviously, with the example of three users in previous section, we can easily know that the session keys obtained by all users are equal. In this section, we will give a more rigorous proof to give a more convincing conclusion.
Without loss of generality, the session key derived from the tth quantum state is taken as an example. That is, we discuss whether or not the following equation holds:
In the protocol, in order to obtain k1,2t−1k1,2t, P1 prepares the initial quantum state
In the protocol, when Oi,t = 0,
By calculation, we get
Obviously, C = B2t−1. So, in the protocol, the users can get the number of operations performed on the quantum state by calculating B2t−1. Where, when C = 0, the unitary operation is executed an even number of times; otherwise, it is executed an odd number of times.
Due to the good reciprocity of the unitary operation Uxy, Eq. 9 can be rewritten as:
In addition, since UxyUxy = I, the identity encoding operation
When C = 1, we get:
So, Eq. 12 is equivalent to
and
or
Therefore, the user P1 can perform different operations to extract the session key depending on the number of unitary operations.
As mentioned in Step (N + 4) of the protocol, when the number of unitary operations is even, according to Eq. 4, P1 directly measures the quantum state as in Eq. 15 with MBX to obtain
When the number of unitary operations is odd, according to Eqs. 2 and 3, P1 needs to perform the unitary operation
Apparently, the agreement key is the sum of the private inputs of all users regardless of whether the number of operations is odd or even. Similarly, the quantum state
In the same way, the user Pi can obtain
or
From Eqs. 18 and 21 or Eqs. 19 and 22, it is shown that all users receive the same agreement key, i.e., Eq. 8 holds. Therefore, the proposed protocol is correct.
4.2 Security
In this section, we analyze the security of the proposed protocol in the optical-ring quantum communication network. It not only proves that the protocol is secure against common external attacks and internal attacks, but also proves that impersonation attacks are also ineffective for this protocol.
4.2.1 External Attacks
Assuming Eve is an external attacker, who may try her best to eavesdrop on the private input Si, the session key K or the master key
Case 1: Eavesdropping user’s private input.
In the proposed protocol, each user has a private input. Since the private input constitutes the final session key, it is evident that it should be kept secret from others. Subsequently, we discuss that how Eve eavesdrops on the secret input of users.
During the process of the protocol, each user performs three operations: particle preparation, encoding private input and identity information, and single-particle measurement. Obviously, the disclosure of users’ private inputs only occurs after the encoding operations. So, Eve’s attacks mainly take place in the transmission of the particle sequence. In the following, we will consider two common attacks: intercept-resend attack and entangle-measure attack.
Intercept-resend attack. Eve firstly intercepts the particle sequence sent from Pj, and measures it. Based on the measurements, Eve re-prepares the sequence to send to Pj⊞1. In this way, Eve hopes to obtain the private input without being detected. However, this is impossible. In the protocol, the carrier particles after different encoding operation numbers belong to two sets of non-orthogonal states, which are in
or
where, the second set can be converted into {|00⟩, |01⟩, |10⟩, |11⟩} after the unitary operation Vxy. The identity encoding of user is determined by both hash values hj and random numbers Bj. Until step (N + 4) of the protocol, Eve does not know the value of Bj. Therefore, she can only perform random operations to obtain the information. That is, she randomly chooses the measurement base. Evidently, the probability that Eve selects a right measurement basis is approximately 50%. Then, a fake particle string is prepared and sent to Pj⊞1 based on the measurement results. In this case, Eve introduces an error with a probability of
Entangle-measure attack. Assuming that Eve wants to perform the entangle-measure attack, she can intercept the travelling sequence prepared by Pj⊟1, and apply entangling operation UE between her own ancillary particles and the intercepted particles. At last, she transmits the particles to Pj. Pj just encodes his private input and identity information directly in the particles. Afterwards, the encoding sequence is transmitted to Pj⊞1, at which point Eve intercepts again. Then, she measures the ancillary particles to infer the private input Sj.
Without loss of generality, the effect of Eve’s unitary operation UE can be shown as
where, |e00⟩, |e01⟩, |e10⟩, |e11⟩ are pure states determined by UE. The quantum state in the sequence intercepted by Eve again is shown in Table 3.
By simply calculating, we get the correlation between these eight states
Obviously, there is a linear correlation between the quantum states after different coding operations. As Chefles and Barnett [32] said, the necessary and sufficient condition for distinguishing the quantum states is linear independence. Therefore, these linearly correlated quantum states cannot be unambiguous discriminated, which means Eve cannot obtain the private input Sj through the entangle-measure attack.
Case 2: Eavesdropping the session key.
Here, we discuss whether Eve is able to eavesdrop on the session key K. Since K = S1 ⊕ S2 ⊕⋯ ⊕ SN, Eve can generally use two methods to obtain the value of K. One is that Eve tries to eavesdrop each value of Si to infer the agreement key. However, from the analysis of Case 1, we know that Eve cannot succeed. The other method involves directly eavesdropping on the value of K. According to the analysis above, we know that Eve is unable to distinguish between two linearly correlated sets of quantum states. So, Eve will always be detected if the number of encoding operations is unknown. Then, what if she was directly involved in the protocol? Namely, she might execute the impersonation attack.
In this protocol, a semi-trusted third party, P0, is introduced to help these parties accomplish this task. So, Eve may impersonates P0 (called
Case 3: Eavesdropping the master key.
We discuss whether it is possible for Eve to eavesdrop on the master key
4.2.2 Internal Attacks
Compared with external attackers, internal parties have greater capacity since they are involved in the execution of the protocol. In the following, we will discuss some attacks of users.
Case 1: Dishonest users’ collusion attacks.
In the case of a single dishonest user, even if he participates in the protocol, he cannot obtain the hash values of other parties from the information he knows. Therefore, he can be detected in step (N + 5) just like an external attacker. It is important to note that there is more than one dishonest user in a protocol, and the most serious case is only one honest user. Obviously, in this case, all dishonest users want to conspire to eavesdrop the private input of the only honest party and determine the final key K. If the protocol is secure in the extreme case, it is secure in others. Next, we will discuss this situation.
Since P0 is semi-trusted in the protocol, he cannot conspire with others. When Pj is the only honest one, other dishonest users will attack P0 and Pj. For simplicity, let us take the example of three users (N = 3, M = 3). The users P1 and P3 in particular position are assumed to be dishonest, denoted as
For one thing, we discuss the attack on P0, where the dishonest users wish to obtain the hash value h0. Through the above protocol, we know h0 = h1 ⊕ h2 ⊕ h3, which means it is determined by hash values of other users. In this case, since
For another, we discuss the attack on P2, in which the dishonest users wish to obtain the identity information h2, the private input S2, or determine the final key. Since
Case 2: A semi-trusted third party’s attack.
Here, P0 is semi-trusted. That is, he cannot conspire with others, but misbehave on his own. For clarity, we represent the dishonest third party as
Case 3: A dishonest user’s impersonation attack.
Users may also carry out impersonation attack in addition to the attacks described above. His purpose is to determine the agreement key by himself, and succeed in cheating others to accept this fake key. Even if Pi is part of the protocol, he cannot perform correct identity encoding operation without knowing Pj’s hash value. Because the master key
Based on the above analysis, we prove that the protocol in the context of quantum networks is secure.
4.3 Efficiency
In this section, we will discuss the particle efficiency of the proposed protocol. According to [33], the particle efficiency is defined as
where, c is the length of the final shared key string, q is the number of qubits transmitted in the quantum channel, and b is the number of classical bits transmitted for decoding. In our scheme, the length of the final shared key is (2 − δ)n, the number of transmitted qubits is n*N, and the number of transmitted classical bits is 2n*N. Therefore, the particle efficiency of the proposed protocol is
Without considering the detection of particles, the particle efficiency of the example presented in this paper is
Compared with [31] and [15], although they both perform multi-user quantum key agreement in an optical-ring communication network, there are differences in the specific negotiation process. Table 4 shows that our protocol is preferable as its readily accessible quantum resource, good security and high efficiency.
5 Conclusion
Before presenting our conclusion, we briefly discuss the hash function used in the protocol. In the protocol, we use the hash value to complete the authentication of the user. Only the legitimate user knows the correct hash value. In the absence of an impersonation attack, the hash values satisfy
In this paper, we study an authenticated quantum key agreement protocol, which is another main key establishment method in addition to quantum key distribution. This scheme enables key negotiation for any N users in optical-ring quantum networks. Each user in the protocol has his own identity information and shares a master key with a semi-trusted third party. With the help of the third party, they can simultaneously obtain the negotiated key. Security analysis shows that the protocol is secure against common attacks and impersonation attack. Furthermore, the implementation of the protocol only requires preparing and measuring single particles, which can be easily implemented with current technology. And, our method can be easily applied to other MQKA protocols with authentication in quantum networks, so that they can resist impersonation attack in practical. Since the implementation of the protocol is inevitably affected by noise, the threshold value for the error rate should be provided before implementing it. As mentioned in [34], the exact value of the threshold is determined by a variety of practical elements, such as the desired level of security, the noise level of channels, etc. Therefore, choosing an appropriate threshold is complex, which is also the case for many multi-party quantum cryptographic protocols. Combined with quantum state discrimination, we will study this issue in the future.
Data Availability Statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding authors.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Funding
This work was supported by the National Natural Science Foundation of China (Grants Nos. 61,772,134, 61,976,053 and 62,171,131), Fujian Province Natural Science Foundation (Grant No. 2022J01186), the research innovation team of Embedded Artificial Intelligence Computing and Application at Xiamen Institute of Technology (KYTD202003), and the research innovation team of Intelligent Image Processing and Application at Xiamen Institute of Technology (KYTD202101).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Shor PW. Polynomial-time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J Comput (1997) 26:1484–509. doi:10.1137/S0097539795293172
2. Bennett CH, Brassard G. Quantum Cryptography: Public Key Distribution and coin Tossing. In: Proc IEEE Int Conf Comput, Syst and Signal Process. Manhattan, New York: IEEE (1984). p. 175–9.
3. Gisin N, Ribordy G, Tittel W, Zbinden H. Quantum Cryptography. Rev Mod Phys (2002) 74:145–95. doi:10.1103/RevModPhys.74.145
4. Schwonnek R, Goh KT, Primaatmaja IW, Tan EYZ, Wolf R, Scarani V, et al. Device-independent Quantum Key Distribution with Random Key Basis. Nat Commun (2021) 12:1–8. doi:10.1038/s41467-021-23147-3
5. Long GL, Liu XS. Theoretically Efficient High-Capacity Quantum-Key-Distribution Scheme. Phys Rev A (2002) 65:032302. doi:10.1103/PhysRevA.65.032302
6. Sun Z, Song L, Huang Q, Yin L, Long G, Lu J, et al. Toward Practical Quantum Secure Direct Communication: A Quantum-memory-free Protocol and Code Design. IEEE Trans Commun (2020) 68:5778–92. doi:10.1109/TCOMM.2020.3006201
7. Zhang H, Sun Z, Qi R, Yin L, Long G-L, Lu J. Realization of Quantum Secure Direct Communication over 100 Km Fiber with Time-Bin and Phase Quantum States. Light Sci Appl (2022) 11:1–9. doi:10.1038/s41377-022-00769-w
8. Zhou N, Zeng G, Xiong J. Quantum Key Agreement Protocol. Electron Lett (2004) 40:1149–50. doi:10.1049/el:20045183
9. Tsai CW, Chong SK, Hwang T. Comment on “quantum Key Agreement Protocol with Maximally Entangled States”. Proc 20th Crypt Info Secur Conf (2010) 2010:47–9.
10. Chong SK, Hwang T. Quantum Key Agreement Protocol Based on Bb84. Opt Commun (2010) 283:1192–5. doi:10.1016/j.optcom.2009.11.007
11. Shi RH, Zhong H. Multi-party Quantum Key Agreement with Bell States and Bell Measurements. Quan Inf Process (2013) 12:921–32. doi:10.1007/s11128-012-0443-2
12. Liu B, Gao F, Huang W, Wen QY. Multiparty Quantum Key Agreement with Single Particles. Quan Inf Process (2013) 12:1797–805. doi:10.1007/s11128-012-0492-6
13. Sun ZW, Zhang C, Wang BH, Li Q, Long DY. Improvements on “multiparty Quantum Key Agreement with Single Particles”. Quan Inf Process (2013) 12:3411–20. doi:10.1007/s11128-013-0608-7
14. Sun Z, Yu J, Wang P. Efficient Multi-Party Quantum Key Agreement by Cluster States. Quan Inf Process (2016) 15:373–84. doi:10.1007/s11128-015-1155-1
15. Lin S, Zhang X, Guo GD, Wang LL, Liu XF. Multiparty Quantum Key Agreement. Phys Rev A (2021) 104:042421. doi:10.1103/PhysRevA.104.042421
16. Ateniese G, Steiner M, Tsudik G. Authenticated Group Key Agreement and Friends. In: Proceedings of the 5th ACM Conference on Computer and Communications Security (1998). p. 17–26. doi:10.1145/288090.288097
17. Teng J, Wu C, Tang C. An Id-Based Authenticated Dynamic Group Key Agreement with Optimal Round. Sci China Inf Sci (2012) 55:2542–54. doi:10.1007/s11432-011-4381-x
18. Zhang L, Wu Q, Qin B, Domingo-Ferrer J. Identity-based Authenticated Asymmetric Group Key Agreement Protocol. In: Int Comput Combinatorics Conf. Berlin, Heidelberg: Springer (2010). p. 510–9. doi:10.1007/978-3-642-14031-0_54
19. Chen Q, Wu T, Hu C, Chen A, Zheng Q. An Identity-based Cross-Domain Authenticated Asymmetric Group Key Agreement. Information (2021) 12:112–2489. doi:10.3390/info12030112
20. Zeng G, Zhang W. Identity Verification in Quantum Key Distribution. Phys Rev A (2000) 61:022303. doi:10.1103/PhysRevA.61.022303
21. Shi BS, Li J, Liu JM, Fan XF, Guo GC. Quantum Key Distribution and Quantum Authentication Based on Entangled State. Phys Lett A (2001) 281:83–7. doi:10.1016/S0375-9601(01)00129-3
22. Mihara T. Quantum Identification Schemes with Entanglements. Phys Rev A (2002) 65:052326. doi:10.1103/PhysRevA.65.052326
23. Wang Y, Lou X, Fan Z, Wang S, Huang G. Verifiable Multi-Dimensional (T,n) Threshold Quantum Secret Sharing Based on Quantum Walk. Int J Theor Phys (2022) 61:1–17. doi:10.1007/s10773-022-05009-w
24. Lou X, Wang S, Ren S, Zan H, Xu X. Quantum Identity Authentication Scheme Based on Quantum Walks on Graphs with Ibm Quantum Cloud Platform. Int J Theor Phys (2022) 61:1–15. doi:10.1007/s10773-022-04986-2
25. Kumavor PD, Beal AC, Yelin S, Donkor E, Wang BC. Comparison of Four Multi-User Quantum Key Distribution Schemes over Passive Optical Networks. J Lightwave Technol (2005) 23:268.
26. Elkouss D, Martinez-Mateo J, Ciurana A, Martin V. Secure Optical Networks Based on Quantum Key Distribution and Weakly Trusted Repeaters. J Opt Commun Netw (2013) 5:316–28. doi:10.1364/JOCN.5.000316
27. Fröhlich B, Dynes JF, Lucamarini M, Sharpe AW, Yuan Z, Shields AJ. A Quantum Access Network. Nature (2013) 501:69–72. doi:10.1038/nature12493
28. Xue P, Li CF, Guo GC. Conditional Efficient Multiuser Quantum Cryptography Network. Phys Rev A (2002) 65:022317. doi:10.1103/PhysRevA.65.022317
29. Grover LK. Quantum Mechanics Helps in Searching for a Needle in a Haystack. Phys Rev Lett (1997) 79:325–8. doi:10.1103/PhysRevLett.79.325
30. Hsu LY. Quantum Secret-Sharing Protocol Based on Grover's Algorithm. Phys Rev A (2003) 68:022306. doi:10.1103/PhysRevA.68.022306
31. Cao H, Ma W. Multiparty Quantum Key Agreement Based on Quantum Search Algorithm. Sci Rep (2017) 7:45046. doi:10.1038/srep45046
32. Chefles A, Barnett SM. Optimum Unambiguous Discrimination between Linearly Independent Symmetric States. Phys Lett A (1998) 250:223–9. doi:10.1016/S0375-9601(98)00827-5
33. Cabello A. Quantum Key Distribution in the Holevo Limit. Phys Rev Lett (2000) 85:5635–8. doi:10.1103/PhysRevLett.85.5635
Keywords: quantum communication, quantum key agreement, identity authentication, quantum search algorithm, unambiguous state discrimination
Citation: Gao L-Z, Zhang X, Lin S, Wang N and Guo G-D (2022) Authenticated Multiparty Quantum Key Agreement for Optical-Ring Quantum Communication Networks. Front. Phys. 10:962781. doi: 10.3389/fphy.2022.962781
Received: 06 June 2022; Accepted: 22 June 2022;
Published: 13 July 2022.
Edited by:
Tianyu Ye, Zhejiang Gongshang University, ChinaReviewed by:
Ma Hongyang, Qingdao University of Technology, ChinaXiaoping Lou, Hunan Normal University, China
Copyright © 2022 Gao, Zhang, Lin, Wang and Guo. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xin Zhang, eGlhb194aW5fMDlAMTYzLmNvbQ==; Song Lin, bGluczk1QGdtYWlsLmNvbQ==; Gong-De Guo, Z2dkQGZqbnUuZWR1LmNu
 Li-Zhen Gao1
Li-Zhen Gao1 Song Lin
Song Lin