- School of Mathematics and Computer Sciences, Nanchang University, Nanchang, China
A controlled quantum secure direct communication protocol based on four-qubit cluster states and quantum search algorithm is put forward, in which four users, a sender, a receiver and two controllers, are involved in achieving the secure transmission of secret message. The four-qubit cluster state can ensure the feasibility and security of the protocol because of its large persistency of entanglement. Meanwhile, the idea of quantum search algorithm is used to accomplish the task of encoding and decoding secret message. The proposed protocol can successfully avoid the information leakage problem and resist some common attacks including the outsider attacks and the internal attacks, and its qubit efficiency is up to 20%. Furthermore, compared with the previous quantum secure direct communication protocols, it can effectively resist the attacks from the dishonest receiver.
1 Introduction
Quantum key distribution (QKD) protocol was first proposed by Bennett and Brassard in 1984, in which two remote authorized users can create a shared private key [1]. The security of QKD protocol was theoretically proven in [2, 3]. Afterwards, this topic has attracted the focus of many scholars so that some interesting branches of QKD have been built, such as quantum teleportation (QT) [4], quantum secret sharing (QSS) [5], and quantum secure direct communication (QSDC) [6], etc. Different from QKD, QSDC is to transmit the secret directly through a quantum channel without establishing a random key to encrypt and decrypt them beforehand. In 2000, Long and Liu proposed the first QSDC protocol (LL00 protocol), in which the strategy of quantum block transmission was exploited to settle the problem of information leakage for the first time [6]. In 2002, Boström and Felbinger put forward a ping-pong QSDC protocol employing EPR pairs as the information carriers [7], which was insecure in a noisy quantum channel as shown by Wójcik [8]. Deng et al. presented a two-step quantum direct communication protocol based on EPR pairs, which clearly stated the definition and basic requirements of QSDC [9]. Hereafter, a number of QSDC protocols have been constructed based on non-entangled quantum states [10, 11] or entangled quantum states [12–17]. To better control QSDC protocol, the first controlled QSDC (CQSDC) was proposed in 2005, where a controller is added to supervise the secure communication between a sender and a receiver [18]. Subsequently, some CQSDC protocols have been developed constantly, where the communication is controlled by at least one controller [19–25]. Quantitative security analysis of QSDC has completed using Wyner’s wiretap channel theory in Refs. [26, 27]. The previous protocols need the use of quantum memory [6–25]. Regretfully, no practical quantum memory exists, so the quantum-memory-free technique has been developed [28] to make QSDC protocols be implemented without quantum memory. To counter this adverse effect of high noise and high loss in a realistic environment, a classical coding scheme was presented, which causes the secure channel capacity to be small, and a practical prototype based on the DL04 protocol [10] has been established [27]. The issue of small channel capacity can be solved by INCUM technique [29]. Moreover, measurement-device-independent QSDC [30–32], device-independent QSDC [33, 34], detector-device-independent QSDC [35] and full Bell-basis QSDC [36] have further advanced the development of QSDC. Some progress has been made experimentally. Proof-of-principle experiments of the DL04 protocol was completed in 2016 [37], experimental demonstration of QSDC with state-of-the-art atomic quantum memory [38] and long-distance QSDC experiment [39] were presented in 2017. Recently, the applications of QSDC have been reported [40–42]. Reference [40] demonstrated the feasibility of QSDC over GEO satellite, and the application of QSDC in both 6G [41] and secure quantum network [42] were studied.
Nowadays, another research hotspot is quantum search algorithm (QSA), put forward by Grover in 1996, which can find a marked item with very high probability from an unsorted database with size
In this paper, a novel controlled quantum secure direct communication protocol with four-qubit cluster states and quantum search algorithm is proposed. The sender Alice and the receiver Bob can successfully achieve the transmission of secret message with the qubit efficiency of 20% with the help of two controllers (Charlie 1, and Charlie 2) without any information leakage. Furthermore, the proposed protocol can not only resist some common attacks but also find the vicious behavior from the attackers. In addition, the proposed protocol outperforms the existing ones in terms of resisting the internal attacks.
The rest of the paper is organized as follows. Section 2 introduces QSA with two-qubit system briefly. An efficient CQSDC protocol based on four-particle cluster states and QSA is depicted in Sec.3. Section 4 analyzes the security of the proposed CQSDC protocol under various attacks. A performance comparison is shown in Section 5. Finally, the concluding remarks appear in Section 6.
2 Review of Grover’s Search Algorithm
We briefly review Grover’s search algorithm in this section [43, 44]. Assume that we want to search for a marked state
Where
Two operators in Eqs. 1, 2 are orderly conducted on initial state
Where
Subsequently, the operator
Lastly, the marked state can be found with
3 Description of the Proposed CQSDC Protocol
The CQSDC protocol, involving a honest sender Alice, a receiver Bob, and two controllers Charlie 1 and Charlie 2, employs four-particle cluster states and quantum search algorithm, which is presented in this section. If Alice is dishonest, the protocol doesn’t make any sense since the secret message is always known to Alice. Hence, let Alice be honest. Suppose that the secret message from Alice to Bob is a binary bit sequence
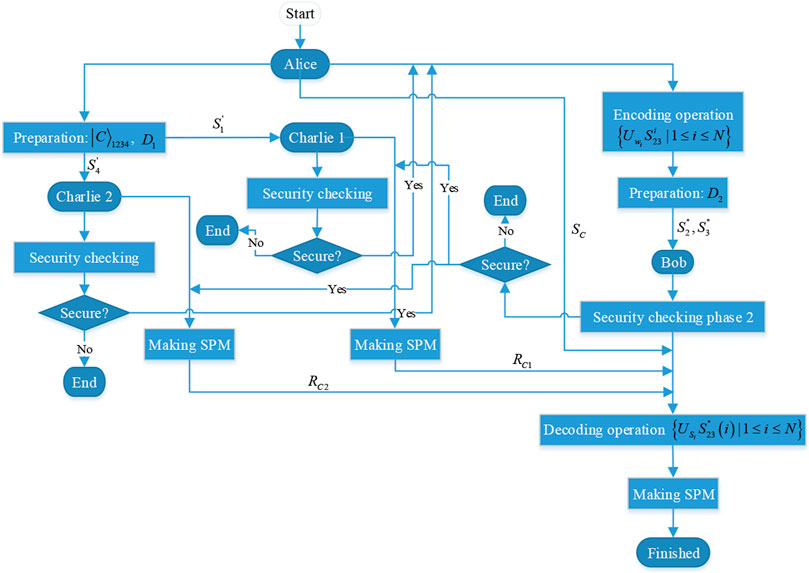
FIGURE 1. The executing process of the whole communication protocol. SPM denotes single-particle measurements with
3.1 Step 1 Preparation Phase
Alice generates
3.2 Step 2 Security Checking Phase 1
After confirming that Charlie 1 has received sequence
3.3 Step 3 Encoding Phase
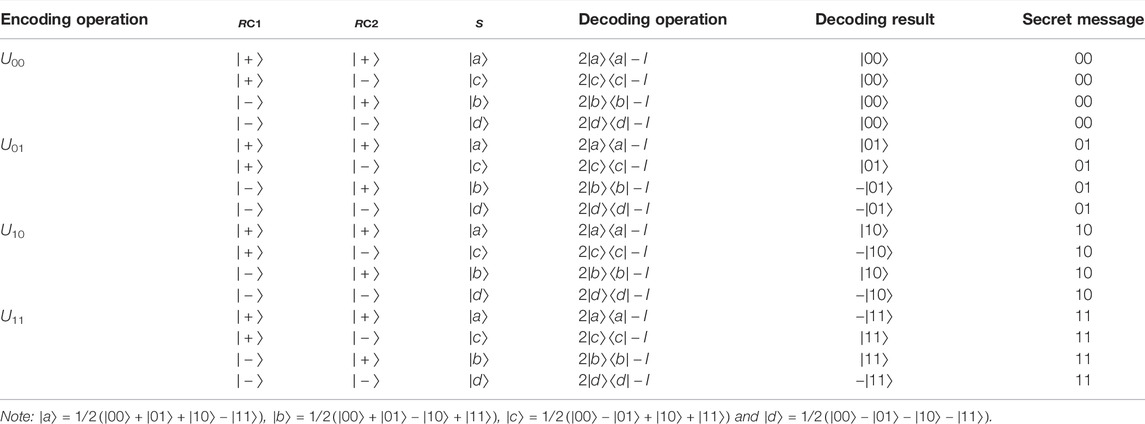
After checking the security of transmission above, Alice then encodes the secret message
Where
After the effect of the encoding operator
Alice orderly picks out photon 2 from
3.4 Step 4 Security Checking Phase 2
Upon receiving sequence
3.5 Step 5 Decoding Phase
Upon confirming that security checking phase 2 is secure, Bob removes all the decoy photons from Sequences
Where
Both
Table 2 shows Charlie 1 and Charlie 2 have four possible measurement outcomes
4 Security Analysis
Since the crucial issue of a feasible quantum communication protocol is its security, it is essential to discuss the security of the proposed communication protocol. The security of the proposed protocol is discussed from the outsider attacks and the internal attacks, and the analysis makes clear that the proposed protocol can protect the transmitted message from leaking out under various attacks. Namely, it is a feasible protocol.
4.1 The Controllers
The decoding operation
4.2 Outsider Attacks
4.2.1 Entangle-and-Measure Attack
The entangle-and-measure attack is also called auxiliary particle attack. If Eve wants to execute the entangle-measure attack, she intercepts the encoded particles in sequence
Where
In our protocol, the decoy photons have four possible states
Even though the transmitted particle states contain the secret information, Eve cannot read them out. Eqs. 11, 12 imply that the error rate introduced by the behavior of Eve’s eavesdropping will be
4.2.2 Measure-Resend Attack
Eve may try to perform the measure-resend attack on the encoded particles in the transmission process to steal Alice’s useful message. Eve has to know the full information of the state and reproduce another same state without being detected. Eve intercepts the encoded Sequences
4.2.3 Intercept-Resend Attack
As for the intercept-resend attack [60], Eve should replace the qubit sequence
4.2.4 Trojan Horse Attacks
Reference [61] pointed out that two-way quantum communication protocols are vulnerable to the Trojan horse attacks which includes two types: invisible photon eavesdropping attack (IPE) [61] and multi-photon signal attack [62]. However, since both the preparation of qubit sequence
4.3 Internal Attacks
Since the participants could possess more information than outsider eavesdroppers, the internal attacks are stronger than the outsider attacks. The internal attacks are made up of single attack and collusive attack [63, 64].
4.3.1 Single Attack
Single attack is a kind of eavesdropping from the dishonest Charlie 1, Charlie 2, or Bob. 1) If dishonest Charlie 1 (Charlie 2) wants to perform her single attack to extract the secret message, she needs to intercepts the encoded Sequences
4.3.2 Collusive Attack
The collusive attack is the most powerful internal attack in which two or more dishonest participants collude together to steal secret information without revealing their vicious behavior. Since Alice is honest, the collusive attack can be divided into two scenarios: case (a) the collusive attack of two dishonest participants (Charlie 1 and Charlie 2, Charlie 1 and Bob, Charlie 2 and Bob); case (b) the collusive attack of three dishonest participants (Charlie 1, Charlie 2 and Bob). Since the honest Alice share identity sequence
In the proposed protocol, the sender Alice must be honest and the ideal four-qubit entanglement resources are prepared by Alice. In real communication environment, due to inevitable imperfections of network nodes, every involved node maybe untrusted, that is, both trusted network nodes and untrusted network nodes exist in quantum communication networks [65]. The proposed communication scheme with four parties can be regarded as a mini quantum communication network, where the involved parties are equivalent to network nodes. Therefore, in a real scenario, the sender in our protocol maybe untrusted, which will cause the receiver to obtain fake message without being found. Fortunately, multipartite quantum correlations of graph states, a kind of strategy-independent physical resources, allow network nodes to create strong correlations before it performs distributed tasks, which is efficient and provides strong guarantees in quantum communication networks in the presence of untrusted network nodes [66]. Furthermore, multipartite EPR steering demonstrates that all the nodes in the quantum network can share entanglement even if the measurement devices of one party are untrusted, and even can count the number of untrusted nodes [65, 67, 68]. To put the presented scheme into practice, it is a good choice to use multipartite quantum correlations of graph states created by a graph state source to replace quantum entanglement resources generated by the honest sender for removing the adverse effect of untrusted parties.
5 Comparison
The definition of quantum efficiency suggested by Cabello [69], can be described as
6 Conclusion
This paper proposes a novel controlled quantum secure direct communication protocol based on a four-qubit cluster state and quantum search algorithm. It makes full use of the persistency property of the quantum resource, and two operators of QSA are used to achieve encoding operations and decoding operations, respectively. With the permissions of the controllers and Alice, the sender’s secret message can be successfully reconstructed by the receiver without any information leakage. Furthermore, the security of the proposed CQSDC protocol can be guaranteed and outperforms that of the existing protocol from the perspective of resisting the dishonest receiver, and its efficiency is as high as 20%.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author Contributions
Y-FY: Conceptualization, Methodology, Writing-Original Draft, Writing-Review and Editing. L-ZD: Data Curation, Writing-Review and Editing, Supervision. T-RQ: Conceptualization, Methodology, Writing-Review and Editing. X-MX: Conceptualization, Writing-Original Draft, Writing-Review and Editing.
Funding
This work is supported by the National Natural Science Foundation of China (Grant No. 61871205).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fphy.2022.875441/full#supplementary-material
References
1. Bennett CH, Gilles B. Quantum Cryptography: Public-Key Distribution and coin Tossing. In Proceedings of the International Conference on Computers, systems and signal Processing, Bangalore, India, 9 December 1984. New York: Bangalore Press. p. 175–9.
2. Shor PW, Preskill J. Simple Proof of Security of the BB84 Quantum Key Distribution Protocol. Phys Rev Lett (2000) 85(2):441–4. doi:10.1103/PhysRevLett.85.441
3. Lo H-K, Chau HF. Unconditional Security of Quantum Key Distribution over Arbitrarily Long Distances. Science (1999) 283(5410):2050–6. doi:10.1126/science.283.5410.2050
4. Bennett CH, Brassard G, Crépeau C, Jozsa R, Peres A, Wootters WK. Teleporting an Unknown Quantum State via Dual Classical and Einstein-Podolsky-Rosen Channels. Phys Rev Lett (1993) 70(3):1895–9. doi:10.1103/PhysRevLett.70.1895
6. GuiLu L, Liu XS. Theoretically Efficient High-Capacity Quantum-Key-Distribution Scheme. Phys Rev A (2002) 65(3):032302.
7. Kim B, Timo F. Deterministic Secure Direct Communication Using Entanglement. Phys Rev Lett (2002) 89(18):187902.
8. Antoni W. Eavesdropping on the “Ping-pong” Quantum Communication Protocol. Phys Rev Lett (2003) 90(15):157901.
9. Deng FG, GuiLu L, Liu XS. Two-step Quantum Direct Communication Protocol Using the Einstein-Podolsky-Rosen Pair Block. Phys Rev A (2003) 68(4):042317. doi:10.1103/physreva.68.042317
10. Deng FG, GuiLu L. Secure Direct Communication with a Quantum One-Time Pad. Phys Rev A (2004) 69(5):052319. doi:10.1103/physreva.69.052319
11. Chang Y, Xu C, Zhang S, Yan L. Quantum Secure Direct Communication and Authentication Protocol with Single Photons. Chin Sci Bull (2013) 58(36):4571–6. doi:10.1007/s11434-013-6091-9
12. Wang C, Deng F-G, Li Y-S, Liu X-S, Long GL. Quantum Secure Direct Communication with High-Dimension Quantum Superdense Coding. Phys Rev A (2005) 71(4):44305. doi:10.1103/physreva.71.044305
13. Lu Y, Wu JW, Lin ZS, Yin LG, GuiLu L. Quantum Secure Direct Communication with Entanglement Source and Single-Photon Measurement. Sci China: Phys Mech Astron (2020) 63(11):110311.
14. Farouk A, Zakaria M, Megahed A, Omara FA. A Generalized Architecture of Quantum Secure Direct Communication for N Disjointed Users with Authentication. Sci Rep (2015) 5:16080. doi:10.1038/srep16080
15. Cao HJ, Song HS. Quantum Secure Direct Communication with W State. Chin Phys Lett (2006) 23(2):290–2.
16. Cao W, Yang Y, Wen Q. Quantum Secure Direct Communication with Cluster States. Sci China Phys Mech Astron (2010) 53(7):1271–5. doi:10.1007/s11433-010-3210-3
17. Liu Z, Chen H, Liu W, Xu J, Wang D, Li Z. Quantum Secure Direct Communication with Optimal Quantum Superdense Coding by Using General Four-Qubit States. Quan Inf Process (2013) 12(1):587–99. doi:10.1007/s11128-012-0404-9
18. Gao T, Yan FL, Wang ZX. Controlled Quantum Teleportation and Secure Direct Communication. Chin Phys (2005) 14(5):892–7.
19. Wang J, Zhang Q, Tang C-j. Multiparty Controlled Quantum Secure Direct Communication Using Greenberger-Horne-Zeilinger State. Opt Commun (2006) 266(2):732–7. doi:10.1016/j.optcom.2006.05.035
20. Chen XB, Wang TY, Du JZ, Wen QY, Zhu FC. Controlled Quantum Secure Direct Communication with Quantum Encryption. Int J Quan Inf (2008) 6(3):543–51. doi:10.1142/s0219749908003566
21. Kao SH, Tsai CW, Hwang T. Enhanced Multiparty Controlled QSDC Using GHZ State. Commun Theor Phys (2011) 55(6):1007–11.
22. Li Y-h., Li X-l., Sang M-h., Nie Y-y., Wang Z-s. Bidirectional Controlled Quantum Teleportation and Secure Direct Communication Using Five-Qubit Entangled State. Quan Inf Process (2013) 12(12):3835–44. doi:10.1007/s11128-013-0638-1
23. Zheng X-y., Long Y-x. Controlled Quantum Secure Direct Communication with Authentication Protocol Based on Five-Particle Cluster State and Classical XOR Operation. Quan Inf Process (2019) 18(5):129. doi:10.1007/s11128-019-2239-0
24. FaezehMazloum K, Monireh H, NimaS A-N. Authenticated Controlled Quantum Secure Direct Communication Protocol Based on Five-Particle Brown States. Int J Theor Phys (2020) 59(5):1612–22.
25. Pan H-M. Controlled Bidirectional Quantum Secure Direct Communication with Six-Qubit Entangled States. Int J Theor Phys (2021) 60(8):2943–50. doi:10.1007/s10773-021-04866-1
26. Wu JW, Lin ZS, Yin LG, GuiLu L. Security of Quantum Secure Direct Communication Based on Wyner’s Wiretap Channel Theory. Quan Eng (2019) 1(4):e26. doi:10.1002/que2.26
27. Qi R, Sun Z, Lin Z, Niu P, Hao W, Song L, et al. Implementation and Security Analysis of Practical Quantum Secure Direct Communication. Light Sci Appl (2019) 8(1):22–8. doi:10.1038/s41377-019-0132-3
28. Sun Z, Song L, Huang Q, Yin L, Long G, Lu J, et al. Toward Practical Quantum Secure Direct Communication: a Quantum-memory-free Protocol and Code Design. IEEE Trans Commun (2020) 68(9):5778–92. doi:10.1109/tcomm.2020.3006201
29. GuiLu L, Zhang HR. Drastic Increase of Channel Capacity in Quantum Secure Direct Communication Using Masking. Sci Bull (2021) 66(13):1267–9.
30. Niu P-H, Zhou Z-R, Lin Z-S, Sheng Y-B, Yin L-G, Long G-L. Measurement-device-independent Quantum Communication without Encryption. Sci Bull (2018) 63(20):1345–50. doi:10.1016/j.scib.2018.09.009
31. Zhou Z, Sheng Y, Niu P, Yin L, Long G, Hanzo L. Measurement-device-independent Quantum Secure Direct Communication. Sci China Phys Mech Astron (2020) 63(3):230362. doi:10.1007/s11433-019-1450-8
32. Zou Z-K, Zhou L, Zhong W, Sheng Y-B. Measurement-device-independent Quantum Secure Direct Communication of Multiple Degrees of freedom of a Single Photon. Epl (2020) 131(4):40005. doi:10.1209/0295-5075/131/40005
33. Zhou L, Sheng Y-B, Long G-L. Device-independent Quantum Secure Direct Communication against Collective Attacks. Sci Bull (2020) 65(1):12–20. doi:10.1016/j.scib.2019.10.025
34. Zhou L, Sheng Y-B. One-step Device-independent Quantum Secure Direct Communication. Sci China Phys Mech Astron (2022) 65:250311. doi:10.1007/s11433-021-1863-9
35. Tao L, GuiLu L. Quantum Secure Direct Communication Based on Single-Photon Bell-state Measurement. New J Phys (2020) 22(6):063017.
36. Gao CY, Guo PL, Ren BC. Efficient Quantum Secure Direct Communication with Complete Bell-state Measurement. Quan Eng (2021) 3(4):e83. doi:10.1002/que2.83
37. Hu J-Y, Yu B, Jing M-Y, Xiao L-T, Jia S-T, Qin G-Q, et al. Experimental Quantum Secure Direct Communication with Single Photons. Light Sci Appl (2016) 5(9):e16144. doi:10.1038/lsa.2016.144
38. Zhang W, Ding D-S, Sheng Y-B, Zhou L, Shi B-S, Guo G-C. Quantum Secure Direct Communication with Quantum Memory. Phys Rev Lett (2017) 118(22):220501. doi:10.1103/physrevlett.118.220501
39. Zhu F, Zhang W, Sheng Y, Huang Y. Experimental Long-Distance Quantum Secure Direct Communication. Sci Bull (2017) 62(22):1519–24. doi:10.1016/j.scib.2017.10.023
40. Wang XF, Sun XJ, Liu YX, Wang W, Kan BX, Dong P, et al. Transmission of Photonic Polarization States from Geosynchronous Earth Orbit Satellite to the Ground. Quan Eng (2021) 3(3):e73. doi:10.1002/que2.73
41. You X, Wang C-X, Huang J, Gao X, Zhang Z, Wang M, et al. Towards 6G Wireless Communication Networks: Vision, Enabling Technologies, and New Paradigm Shifts. Sci China Inf Sci (2021) 64(1):110301. doi:10.1007/s11432-020-2955-6
42. GuiLu L, Pan D, Xue QK, Lajos H. An Evolutionary Pathway for the Quantum Internet Relying on Secure Classical Repeaters. Quan Commun Quan Signal Process (2022).
43. Grover LK. A Fast Quantum Mechanical Algorithm for Database Search. Proceedings of the 28th Annual ACM Symposium on the Theory of Computing. Philadelphia Pennsylvania USA. 22 May 1996. Philadelphia: ACM. p. 212–9. doi:10.1145/237814.237866
44. Grover LK. Quantum Mechanics Helps in Searching for a Needle in a Haystack. Phys Rev Lett (1997) 79(2):325–8. doi:10.1103/physrevlett.79.325
45. Zhang W-W, Li D, Song T-T, Li Y-B. Quantum Private Comparison Based on Quantum Search Algorithm. Int J Theor Phys (2013) 52(5):1466–73. doi:10.1007/s10773-012-1464-4
46. Hsu LY. Quantum Secret-Sharing Protocol Based on Grover’s Algorithm. Phys Rev A (2003) 68(2):022306. doi:10.1103/physreva.68.022306
47. Cao H, Ma W. Multiparty Quantum Key Agreement Based on Quantum Search Algorithm. Sci Rep (2017) 7:45046. doi:10.1038/srep45046
48. Wang C, Liang H, Song SY, GuiLu L. Quantum Direct Communication Based on Quantum Search Algorithm. Int J Quan Inf (2010) 8(3):443–50. doi:10.1142/s0219749910006071
49. Tseng H-Y, Tsai C-W, Hwang T. Controlled Deterministic Secure Quantum Communication Based on Quantum Search Algorithm. Int J Theor Phys (2012) 51(8):2447–54. doi:10.1007/s10773-012-1125-7
50. Kao S-H, Hwang T. Multiparty Controlled Quantum Secure Direct Communication Based on Quantum Search Algorithm. Quan Inf Process (2013) 12(12):3791–805. doi:10.1007/s11128-013-0636-3
51. Yin A, Lin W, He K, Han Z, Fan P. Controlled Bidirectional Quantum Secure Direct Communication Protocol Based on Grover's Algorithm. Mod Phys Lett A (2020) 35(28):2050228. doi:10.1142/s0217732320502284
52. Briegel HJ, Raussendorf R. Persistent Entanglement in Arrays of Interacting Particles. Phys Rev Lett (2001) 86(5):910–3. doi:10.1103/PhysRevLett.86.910
53. Raussendorf R, Briegel HJ. A One-Way Quantum Computer. Phys Rev Lett (2001) 86(22):5188–91. doi:10.1103/PhysRevLett.86.5188
54. Hein M, Dür W, Briegel H-J. Entanglement Properties of Multipartite Entangled States under the Influence of Decoherence. Phys Rev A (2005) 71(3):32350. doi:10.1103/physreva.71.032350
55. Kiesel N, Schmid C, Weber U, Tóth G, Gühne O, Ursin R, et al. Experimental Analysis of a Four-Qubit Photon Cluster State. Phys Rev Lett (2005) 95(21):210502. doi:10.1103/PhysRevLett.95.210502
56. Lu C-Y, Zhou X-Q, Gühne O, Gao W-B, Zhang J, Yuan Z-S, et al. Experimental Entanglement of Six Photons in Graph States. Nat Phys (2007) 3(2):91–5. doi:10.1038/nphys507
57. Wen K, Deng FG, GuiLu L. Secure Reusable Base-String in Quantum Key Distribution (2007). Available at: https://arxiv.org/abs/0706.3791 (Accessed October 8, 2021).
58. Li CY, Zhou HY, Wang Y, Deng FG. Secure Quantum Key Distribution Network with Bell States and Local Unitary Operations. Chin Phys Lett (2007) 22(5):1049–52.
59. Gao F, Qin S-J, Guo F-Z, Wen Q-Y. Cryptanalysis of Quantum Secure Direct Communication and Authentication Scheme via Bell States. Chin Phys. Lett. (2011) 28(2):020303. doi:10.1088/0256-307x/28/2/020303
61. Cai Q-Y. Eavesdropping on the Two-Way Quantum Communication Protocols with Invisible Photons. Phys Lett A (2006) 351:23–5. doi:10.1016/j.physleta.2005.10.050
62. Deng FG, Li XH, Zhou HY, Zhang ZJ. Improving the Security of Multiparty Quantum Secret Sharing against Trojan Horse Attack. Phys Rev A (2005) 72(4):440–50. doi:10.1103/physreva.72.044302
63. Liu B, Xiao D, Jia H-Y, Liu R-Z. Collusive Attacks to "circle-type" Multi-Party Quantum Key Agreement Protocols. Quan Inf Process (2016) 15(5):2113–24. doi:10.1007/s11128-016-1264-5
64. Ahmed E, Safia A, Hussein A, Safwat H. Improving the Security of Multi-Party Quantum Key Agreement with Five-Qubit Brown States. Comput Commun (2020) 159:155–60.
65. Lu H, Huang C-Y, Li Z-D, Yin X-F, Zhang R, Liao T-L, et al. Counting Classical Nodes in Quantum Networks. Phys Rev Lett (2020) 124(18):180503. doi:10.1103/physrevlett.124.180503
66. Huang CY, Lambert N, Li CM, Lu YT, Franco N. Securing Quantum Networking Tasks with Multipartite Einstein-Podolsky-Rosen Steering. Phys Rev A (2019) 99(1):012302. doi:10.1103/physreva.99.012302
67. He QY, Reid MD. Genuine Multipartite Einstein-Podolsky-Rosen Steering. Phys Rev Lett (250403201) 111(25):250403. doi:10.1103/PhysRevLett.111.250403
68. Li CM, Chen K, Chen YN, Zhang Q, Chen YA, Pan JW. Genuine High-Order Einstein-Podolsky-Rosen Steering. Phys Rev Lett (2015) 115(1):010402. doi:10.1103/PhysRevLett.115.010402
Keywords: security, cluster states, quantum communication, quantum search algorithm, controlled quantum secure direct communication
Citation: Yang Y-F, Duan L-Z, Qiu T-R and Xie X-M (2022) Controlled Quantum Secure Direct Communication Based on Four-Qubit Cluster States and Quantum Search Algorithm. Front. Phys. 10:875441. doi: 10.3389/fphy.2022.875441
Received: 14 February 2022; Accepted: 29 April 2022;
Published: 25 May 2022.
Edited by:
Raju Valivarthi, California Institute of Technology, United StatesReviewed by:
Che-Ming Li, National Cheng Kung University, TaiwanGui-Lu Long, Tsinghua University, China
Copyright © 2022 Yang, Duan, Qiu and Xie. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Long-Zhen Duan, bHpoZHVhbkAxMjYuY29t
 You-Feng Yang
You-Feng Yang Long-Zhen Duan*
Long-Zhen Duan*