- 1Information Security Center, State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, China
- 2School of Information Science and Technology, North China University of Technology, Beijing, China
- 3School of Cyber Science and Technology, Beihang University, Beijing, China
Quantum multicast is a significant transmission mode in a multiparty communication scenario. Multisource collaboration can further enhance the efficient multicast. However, it remains a challenge to realize quantum multicast with a cooperative way in a complex topology network. In this article, we propose a scheme of quantum cooperative multicast in a hybrid topology network. It provides information aggregation and simultaneous multipoint transmission services. First, collaborative information aggregation allows central network data to be integrated into the aggregation node. By exploiting the quantum multicast mode, the aggregation node can simultaneously deliver integrated quantum states to multiple targets. Second, our scheme is feasible for dynamic network expansion. It is capable of extending the network architecture iteratively, while the peer network requests can be handled in parallel. Finally, the new scheme shows great application potential in the distributed quantum network. It is a promising candidate for the implementation of quantum data disaster backup in future.
1 Introduction
Quantum communication [1–3] is a new subject in quantum information science. With a special network [4–10] dedicated to quantum communication, the quantum technique enables new features which cannot be achieved by its classical counterpart. With the rapid development of quantum technology, the application of quantum communication [11–19] has gradually changed with the trends of networking and globalization.
As one of the essential studies involved in large-scale quantum communication networks, quantum multicast between multiple users is an excellent group transmission technique. Quantum multicast uses a one-to-many or many-to-many association, in which quantum information is delivered simultaneously in a single transmission to many recipients. Compared with the point-to-point transmission, quantum multicast significantly improves the system performance in distributed network communication. In 2006, Shi and Soljanin [20] first investigated multicast in quantum networks and proposed a many-to-many quantum multicast scheme, in which quantum states generated by multiple sources can be simultaneously delivered to multiple targets. They focus on bottlenecks in a multicast scenario and studied lossless compression in a quantum network to reduce the edge capacity requirements. However, it should be under the condition that source nodes can generate enough copies of quantum states. Since the quantum no-cloning theorem [21] forbids the quantum information to be copied as the classical information, the quantum approximate cloning technique [13, 22, 23] has been proposed for preparing sufficient target states. In 2015, Wang et al. [23] utilized an asymmetric quantum cloning mechanism to achieve point-to-multipoint multicast communication, but the fidelity loss remains a problem. Under the quantum cloning mechanism, no matter what approach is taken to copy unknown quantum states, the output must differ from the initial state, resulting in lower fidelity.
Quantum cooperative multicast (QCM) is a novel method to realize many-to-many quantum network multicast. Compared with the quantum cloning mechanism in multicast, it contributes to high fidelity. In QCM, each source has partial information about the quantum state to be transmitted, and they cooperate with each other to achieve accurate multicast. In 2015, Xu et al first proposed the QCM protocol over the butterfly network. As the representative topology with bottleneck problems, butterfly networks here can provide a more general solution for non-trivial networks. Different from common cross-transmission, the goal of QCM is that two source nodes S1, S2 jointly send the integrated state
As the real communication occurs mostly in basic network topologies, like ring [24, 25], star [26], and hybrid topologies [27], it is necessary to extend the adaption of QCM in a typical network topology. The ring–star hybrid topology is one of the most popular network setups for a distributed network. In this configuration, the central network is set with the ring topology, whereas the peripheral networks connect the central network with the star topology. The central ring topologies allow messages to travel in one direction, which alleviates packet collision. When requesting messages from the server, data packets are delivered from one node to another until they reach the destination. The peripheral star topologies can be regarded as centralized management structures, where the central device responds to the request from the peripheral devices. This hybrid topology offers the advantages of both ring and star topologies, and it is feasible enough for network expansion.
In this study, we propose a quantum cooperative multicast scheme in a hybrid topology network. This hybrid topology [27] integrates the advantages of ring [24, 25] and star [26] networks to be consistent with a practical communication environment. Specifically, the central ring network provides an information aggregation server, whereas the peripheral star network responds to multipoint simultaneous transmission. Finally, the new scheme shows great potential in terms of expandability and applicability. We find it is a promising candidate for quantum data disaster backup in future.
2 Methods and Materials
We propose a quantum cooperative multicast scheme in a quantum hybrid topology network. Figure 1 shows the quantum hybrid network topology. In this configuration, our network architecture includes the central aggregation network and the peripheral multicast network. Here, each node
at the aggregation node ns, 0 ≤ s ≤ k − 1 and multicast to t subnodes ns1, ns2 ⋯ nst in the peripheral star network.
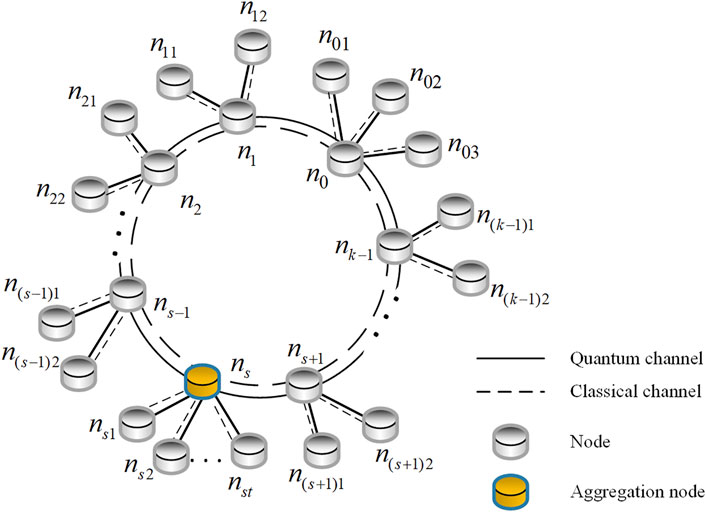
FIGURE 1. Quantum hybrid network topology. Each node
This state in Eq. 1 is called the integrated state. The amplitude of the integrated state corresponds to the trigonometric function of the finite k source’s information sum. It can be generated by local rotation operations
Here,
The complete scheme of QCM in a quantum hybrid topology network includes two parts: information aggregation and multicast transmission. The following Steps 1-4 implements information aggregation, while Step 5 executes multicast transmission.
Step 1. The k pairs of the Bell state
Step 2. Each node ni performs the operation
Step 3. Each node ni executes the encoding process.The node ns+1 (the next node of the aggregation node ns) executes the encoding process. ns+1 performs the local Bell measurement on its qubits (s + 1)′(s + 1) and transmits the Bell measurement result (BMR) to the next node ns+2 by the classical channel. When the BMR is
Step 4. The aggregation node ns performs the Z-basis measurement on qubit s. If the measurement result is
Step 5. Through t times circulation of Steps 1–4, the aggregation node ns obtains t copies of the integrated states
Algorithm 1. Information aggregation of QCM in a quantum hybrid topology network.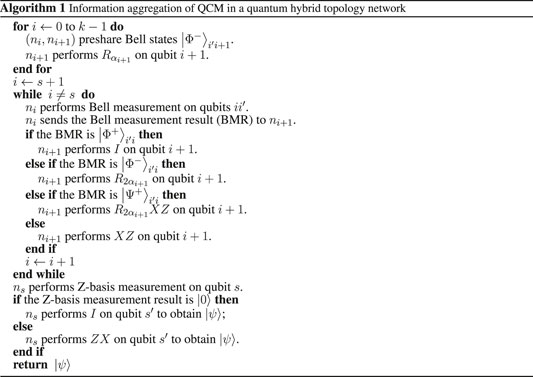 The information aggregation algorithm runs t times to generate t copies of the integrated state
The information aggregation algorithm runs t times to generate t copies of the integrated state
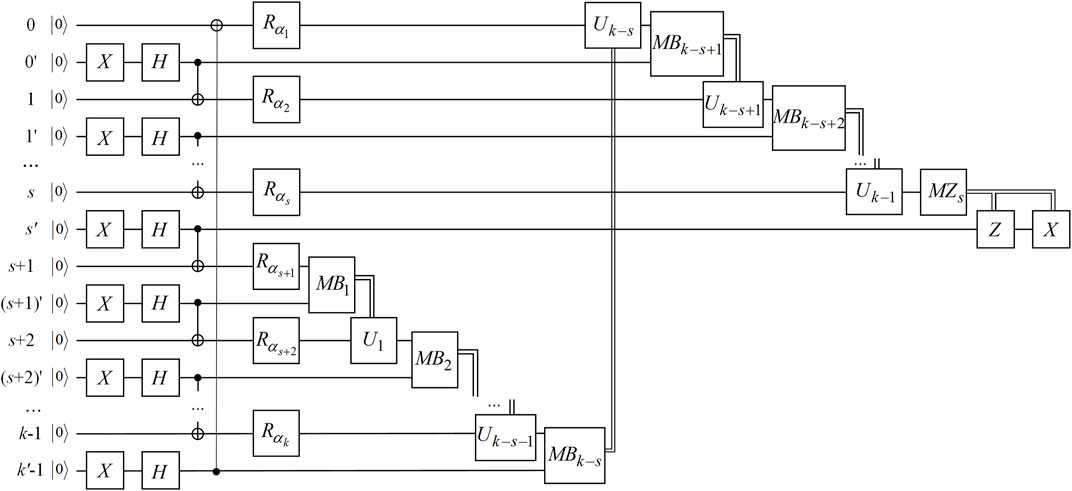
FIGURE 2. Quantum circuit for generating the integrated state
3 Results
The scheme pre-shares k pairs of the Bell states
Each node ni implements the rotation operation
Then, beginning with the node ns+1 (the next node of the aggregation node ns), the local Bell measurement (BM) is performed on (s + 1) (s + 1)′ and the Bell measurement result (BMR) is transmitted to the next node ns+2 by the classical channel. After performing the corresponding unitary operation (I,
Along the counterclockwise direction around the central ring network, the node ns−1 finally finishes the encoding process, and the quantum state in step 3 becomes
Consequently, the information of each node ni can be aggregated at the aggregation node ns. The aggregation node ns measures the qubit s with Z-basis to get the final integrated state in step 4:
Up to this step, a round of information aggregation for the integrated state
While the channel capacity is large enough, adjacent nodes in a central ring network can also pre-share t pairs of Bell states
4 Discussion
We now discuss the performance comparison, the extendibility, and the application scenario for the proposed quantum cooperative multicast scheme in a quantum hybrid topology network.
4.1 Performance Comparison and Analysis
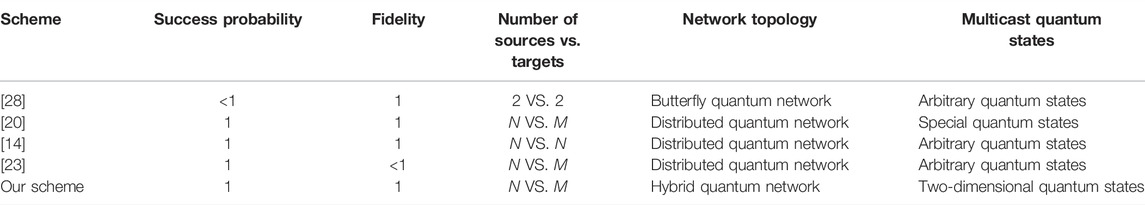
Existing quantum multicast protocols [14, 20, 23, 28] introduce quantum information technologies widely. Apart from our scheme, Xu’s protocol [28] is the first quantum cooperative multicast scheme, while Shi’s protocol [20] is about the lossless compression of special multicast quantum states. Kobayashi’s protocol [14] represents the quantum simulation of a classical linear network coding scheme in the N-to-N multicast model, and Wang’s protocol [23] involves quantum approximate cloning technology.
We make a comparison between the multiple aspects of our scheme and the existing quantum multicast protocols in Table 1. In Table 1, our scheme and Refs. [14, 20, 23] have the same perfect success probability to obtain the desired information, which is better than the determinacy in Ref. [28]. The fidelity of most schemes can reach 1, except for the quantum cloning method [23]. In terms of the number of communicating parties, our scheme and Refs. [20, 23] enable an arbitrary number of parties to quantum multicast, while [14, 28] are bound by the same amount of senders and receivers. Only lossless compression technology [20] can hardly multicast arbitrary quantum states. However, the network topology in our schemes is quite unique among the quantum multicast protocols [14, 20, 23]. This is determined by the information aggregation and multicast mode in our scheme. The information aggregation is dedicated to ring topology, while the multicast transmission occurs in the peripheral star topology. In addition, compared with the baseline scheme, for example, which directly distributes NM Bell pairs from N sources to M targets at a distance, our scheme distributes entangled resources among neighbor nodes to reduce decoherence.
4.2 Extendibility
As the worldwide demand for quantum communication rises, a large-scale, distributed and complicated quantum network should be studied. The topology with better extendibility will further improve multicast efficiency and meet the demands of complicated network applications. The proposed quantum cooperative multicast scheme has strong scalability. It is implemented in a hybrid network topology, which could be part of a larger network.
4.2.1 Iterative Network
The hybrid topology in our scheme enables networks to be extended iteratively, which can cover a larger communication range. Based on the coverage of the local area network (LAN), there are strict differences in network levels. Here, we use “network level” to indicate the affiliation of networks within the LAN. As shown in Figure 3, we present three levels of network scenarios in an iterative network. The outmost networks are regarded as the level 3 network, which is denoted by the light blue area. These aggregation nodes of the level 3 network can contribute to a level 2 network marked with the dark blue area. This level 2 network is also equipped with aggregation nodes, contributing to a level 1 network marked with the gray area. This proves that our network is efficient in expanding the topology iteratively. We can observe that each level of the network conforms to the hybrid topology, satisfying the characteristics of a fractal network.
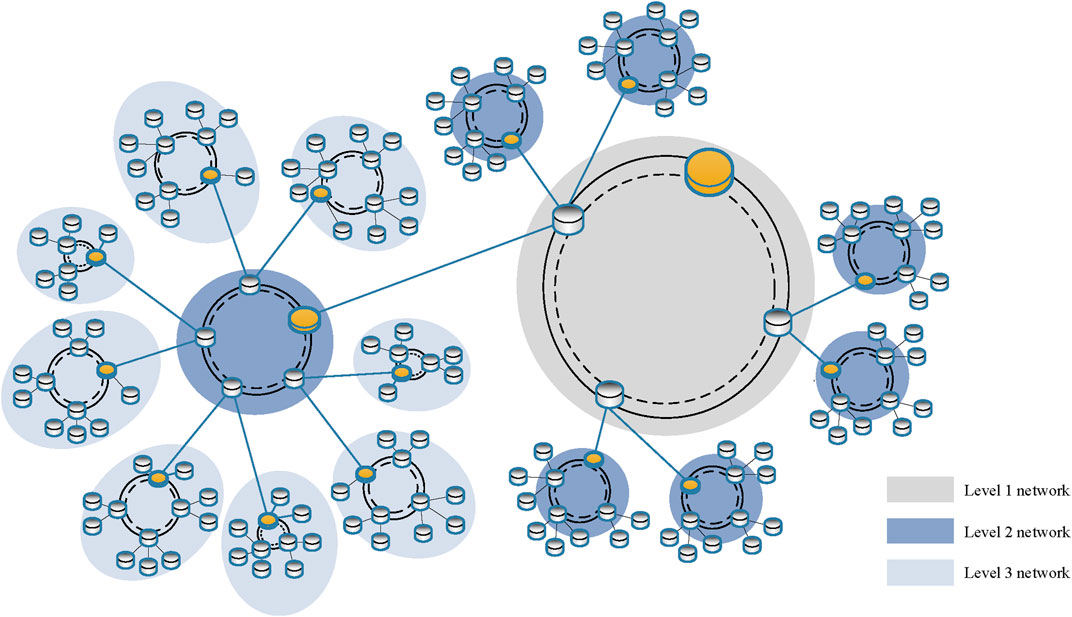
FIGURE 3. Iterative network. Networks with the same background color are peer networks. The aggregation node in the lower level network (marked in yellow) is connected to the central network of the upper level network.
Due to this topological feature, the higher level network can aggregate all the information of the connected lower level network. For example, each aggregation node of the level 3 network aggregates the information from its central network and multicasts it to the subnode which is located on the central ring of the level 2 network. Once the aggregation node of the level 2 network performs information aggregation, it does aggregate all the connected level 3 network information. Hence, the highest level network can aggregate the information of the whole iterative network.
Meanwhile, instead of being transmitted to a specific local area network, the aggregate information is spread to a vast distributed network. Each node in the central ring network of the level 1 network can be an aggregation node to aggregate the information and multicast it toward the aggregation nodes in level 2 networks. Similarly, other nodes in the central network of the level 2 network can also be aggregation nodes. While they aggregate the information over the level 2 central network, these nodes perform operation I, instead of the rotation operation
This hierarchical iterative network coincides with the practical network environment. If the whole country is regarded as a local area network, the level 1 network refers to the “provincial backbone line,” which is generally set up in the provincial capital of each region and the secondary trunk line generally with the province to cover the scope. Therefore, all network nodes set in the province belong to the level 2 network. The level 3 network is actually the local network, which is divided by the city as the region. Each level of the network itself conforms to the hybrid topology, and the upper and lower level networks are connected by a star mode. At the highest level of the network, provincial capitals will be able to collect and aggregate information from all their cities. Conversely, the corresponding aggregated information can spread from provincial capitals to cities. Compared with a larger single circle or several star networks, this hierarchical iterative network benefits the entire network information management.
4.2.2 Side-by-Side Network
A side-by-side network [29] is also possibly derived from our hybrid topology structure. Here, the side-by-side network means that multiple quantum networks are connected at the same level of the network. The situation is shown in Figure 4. It is worth noting that the side-by-side network allows peer networks to share central ring network nodes. This type of collaborative multicast architecture can handle requests on peer networks in parallel. If new clients or devices are added, our network allows parallel expansion to be a side-by-side network. In this case, a large number of clients on different networks can participate in information aggregation simultaneously.
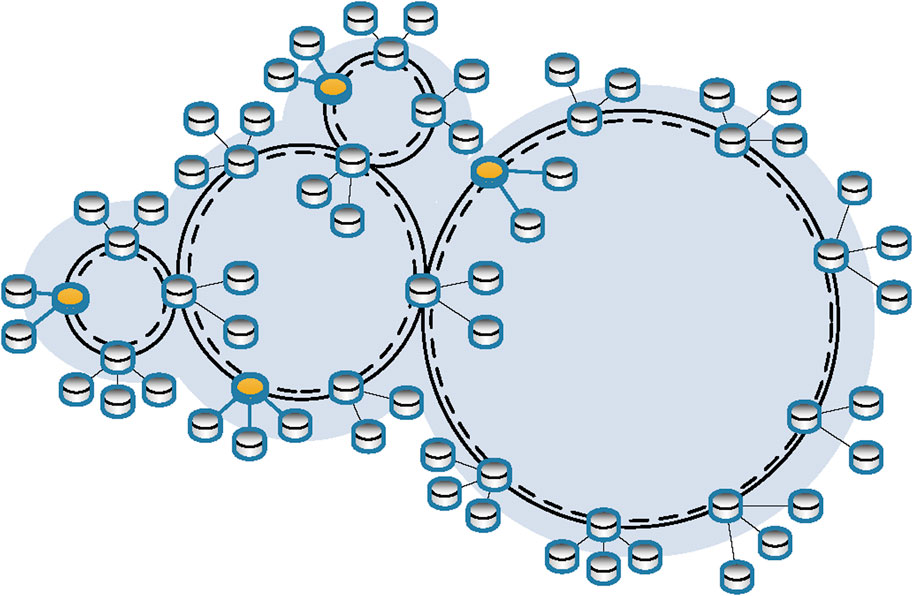
FIGURE 4. Side-by-side network. Several peer networks with the same background color are connected by a side-by-side network, which allows these peer networks to share central ring network nodes.
The extensibility of our scheme is significantly meaningful for large-scale network communication. It can not only effectively divide the network to refine the communication scale but also iteratively expand the network scope. Hence, this extensibility is sufficient for the dynamic network requirements.
4.3 Application Scenario
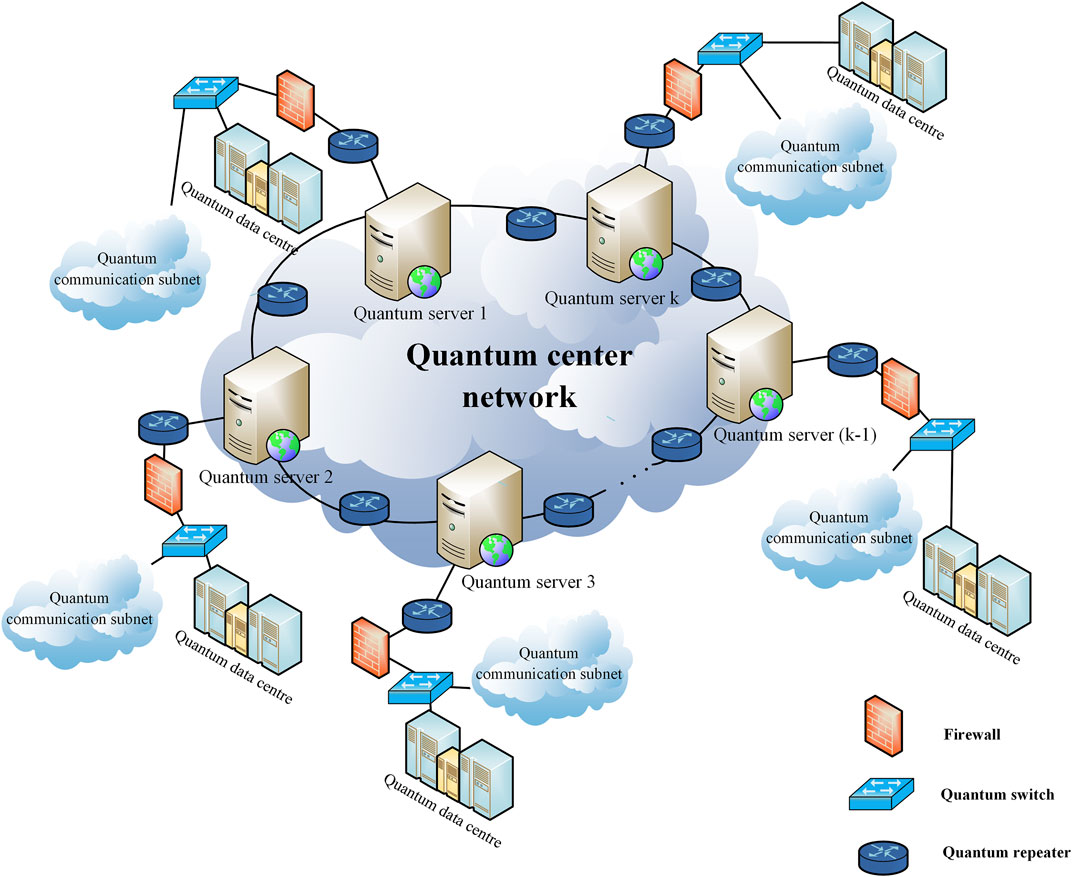
Our quantum cooperative multicast scheme is implemented in a hybrid topology network. In this scheme, the central ring network provides an information aggregation server, while the peripheral star network responds to multicast transmission. This solution pattern could be employed in various application scenarios of large-scale quantum networks in future, such as a backup system for disaster recovery. In this section, we describe a quantum disaster recovery plan in a hybrid topology network. As an application of the present scheme, this plan offers risky node information aggregation and multipoint simultaneous backup services.
We first introduce three basic network configurations in this plan: quantum repeaters, quantum switches, and firewall. With the ability of the entanglement generation, quantum repeaters [30–32] are the most popular devices in the quantum network. It is also a promising technology for enabling multicast over long distances. Quantum switches [33, 34] provide network interfaces to connect quantum communication networks. If quantum clients in a peripheral network request for aggregating information of the central network, the quantum switch is responsible for generating the adjacency of the clients to which they connect. In addition, we use the symbol of the firewall to represent the security defense. Since each node ni is associated with partial information about the integrated state, it might reduce the security level. In general, many quantum information security technologies, such as quantum identity authentication [35] and quantum homomorphic encryption [36], can also be applied to maintain internet security. Specifically, we implement quantum distillations [37] on entanglement resources over the central network. Even if potential risks exist in the network equipment, secure communications can be established. Now, we describe a plan of quantum data disaster backup based on the proposed scheme. The preliminary design is plotted in Figure 5.
Suppose each quantum server Si, i = {1, 2, … , k} in the central network administers local database, which is represented as
1) The center network checks the high-risk servers
2) The Bell pairs are distributed between adjacent nodes via quantum repeaters, forming a ring central network. Here, the Bell state needs to be distilled before entanglement distribution.
3) Algorithm 1 is adopted to aggregate information about potential faulty nodes
4) Once the facilities are broken down, the aggregation node Sa multicasts the aggregated information securely to the peripheral star subnet through quantum switches.
Overall, the proposed quantum cooperative multicast scheme can achieve non-local information aggregation and multipoint backup, satisfying the basic demand of a quantum data disaster backup.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Funding
This work is supported by the NSFC (Grant Nos. 92046001, 61671087, 61962009, 62176273, and 61971021), the Fundamental Research Funds for the Central Universities (Grant No. 2019XD-A02), the Fundamental Research Funds for Beijing Municipal Commission of Education, the Open Foundation of Guizhou Provincial Key Laboratory of Public Big Data (Grant Nos. 2018BDKFJJ018, 2019BDKFJJ010, and 2019BDKFJJ014), the BUPT Excellent Ph.D. Students Foundation (Grant No. CX2021223), the Scientific Research Launch Funds of North China University of Technology, and Beijing Urban Governance Research Base of North China University of Technology.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Dynes JF, Wonfor A, Tam WWS, Sharpe AW, Takahashi R, Lucamarini M, et al. Cambridge Quantum Network. Npj Quan Inf (2019) 5:101. doi:10.1038/s41534-019-0221-4
2. Yu Y, Ma F, Luo XY, Jing B, Sun PF, Fang RZ, et al. Entanglement of Two Quantum Memories via Fibres over Dozens of Kilometres. Nature (2020) 578:240–5. doi:10.1038/s41586-020-1976-7
3. Bhaskar MK, Riedinger R, Machielse B, Levonian DS, Nguyen CT, Knall EN, et al. Experimental Demonstration of Memory-Enhanced Quantum Communication. Nature (2020) 580:60–4. doi:10.1038/s41586-020-2103-5
4. Lloyd S, Shapiro JH, Wong FNC, Kumar P, Shahriar SM, Yuen HP. Infrastructure for the Quantum Internet. SIGCOMM Comput Commun Rev (2004) 34:9–20. doi:10.1145/1039111.1039118
7. Hahn F, Pappa A, Eisert J. Quantum Network Routing and Local Complementation. npj Quan Inf (2019) 76(5). doi:10.1038/s41534-019-0191-6
9. Pirker A, Dur W. A Quantum Network Stack and Protocols for Reliable Entanglement-Based Networks. New J Phys (2018) 21(3):033003.
10. Pant M, Krovi H, Towsley D, Tassiulas L, Jiang L, Basu P, et al. Routing Entanglement in the Quantum Internet. npj Quan Inf (2019) 25(5). doi:10.1038/s41534-019-0139-x
11. Peev M, Pacher C, Alleaume R, Barreiro C, Bouda J, Boxleitner W, et al. The Secoqc Quantum Key Distribution Network in vienna. New J Phys (2009) 11:075001. doi:10.1364/ofc.2009.othl2
12. Sasaki M, Fujiwara M, Ishizuka H, Klaus W, Wakui K, Takeoka M, et al. Field Test of Quantum Key Distribution in the Tokyo Qkd Network. Opt Express (2011) 19:10387–409. doi:10.1364/oe.19.010387
13. Hayashi M, Iwama K, Nishimura H, Raymond R, Yamashita S Quantum Network Coding. Annu Symp Theor Aspects Comput Sci (2007) 4393:610–21.
14. Kobayashi H, LeGall F, Nishimura H, Roetteler M. Perfect Quantum Network Communication Protocol Based on Classical Network Coding. Proc IEEE Int Symp Inf Theor (2010) 41:2686–90. doi:10.1109/isit.2010.5513644
15. Satoh T, Gall FL, Imai H. Quantum Network Coding for Quantum Repeaters. Phys Rev A (2012) 86(3):032331. doi:10.1103/physreva.86.032331
16. Satoh T, Ishizaki K, Nagayama S, Van Meter R. Analysis of Quantum Network Coding for Realistic Repeater Networks. Phys Rev A (2016) 93(3):32302. doi:10.1103/physreva.93.032302
17. Takaaki M, Takahiko S, Shota N, Rodney VM. Analysis of Measurement-Based Quantum Network Coding over Repeater Networks under Noisy Conditions. Phys Rev A (2018) 97(6):062328.
18. Iwama k., Nishimura H, Raymond R, Yamashita S. Quantum Network Coding for General Graphs. Physics (2006) 2006:0611039.
19. Leung D, Oppenheim J, Winter A. Quantum Network Communication-The Butterfly and beyond. IEEE Trans Inform Theor (2010) 56:3478–90. doi:10.1109/tit.2010.2048442
20. Shi Y, Soljanin E. On Multicast in Quantum Networks. In: 2006 40th Annual Conference on Information Sciences and Systems (2006). doi:10.1109/ciss.2006.286589
21. Wootters WK, Zurek WH. A Single Quantum Cannot Be Cloned. Nature (1982) 299:802–3. doi:10.1038/299802a0
22. Bruß D, Divincenzo DP, Ekert A, Fuchs CA, Macchiavello C, Smolin JA. Optimal Universal and State-dependent Quantum Cloning. Phys Rev A (1998) 57(4):2368–78. doi:10.1103/physreva.57.2368
23. Wang XJ, An LX, Meng FX, Yu XT, Zhang ZC. A Multicast Scheme Based on Fidelity Metrics in Quantum Networks. IEEE Access (2019) 7:65703–13. doi:10.1109/access.2019.2915931
24. Ganguly S, Varsou AC, Izmailov R. Waveband Routing on Logical Topologies Constructed over a Ring Network. In: Workshop on High Performance Switching and Routing (2004).
25. Shirichian M, Sara T. Protocol for Routing Entanglement in the Quantum Ring Network. In: 2018 9th International Symposium on Telecommunications (IST) (2018). p. 658–63. doi:10.1109/istel.2018.8661126
26. Dietzfelbinger M, Madhavapeddy S, Sudborough IH. Three Disjoint Path Paradigms in star Networks. In: Proc.ieee Symp.parallel and Distributed Processing (1991). p. 400–6.
27. Das G, Parthiban R, Tucker RS, Leckie C. Traffic Aggregation in Hybrid Ring-star Optical Networks. In: TENCON 2005 2005 IEEE Region 10 (2005). doi:10.1109/tencon.2005.301054
28. Xu G, Chen XB, Li J, Wang C, Yang YX, Li Z. Network Coding for Quantum Cooperative Multicast. Quan Inf Process (2015) 14:4297–322. doi:10.1007/s11128-015-1098-6
29. Pirker A, Wallnöfer J, Dür W. Modular Architectures for Quantum Networks. New J Phys (2018) 20:053054–87. doi:10.1088/1367-2630/aac2aa
30. Briegel HJ, Dür W, Cirac JI, Zoller P. Quantum Repeaters: The Role of Imperfect Local Operations in Quantum Communication. Phys Rev Lett (1998) 81:5932–5. doi:10.1103/physrevlett.81.5932
31. Dür W, Briegel HJ, Cirac JI, Zoller P. Quantum Repeaters Based on Entanglement Purification. Phys Rev A (1999) 59:169–81. doi:10.1103/physreva.59.169
32. Pant M, Krovi H, Englund D, Guha S. Rate-distance Tradeoff and Resource Costs for All-Optical Quantum Repeaters. Phys Rev A (2017) 95:012304. doi:10.1103/physreva.95.012304
33. Davidovich L, Maali A, Brune M, Raimond JM, Haroche S. Quantum Switches and Nonlocal Microwave fields. Phys Rev Lett (2018) 71(15):2360–3. doi:10.1103/PhysRevLett.71.2360
34. Ahufinger V, Mebrahtu A, Corbalan R, Sanpera A. Quantum Switches and Quantum Memories for Matter-Wave Lattice Solitons. New J Phys (2006) 9(1):284–7.
35. Zhang Z, Zeng G, Zhou N, Xiong J. Quantum Identity Authentication Based on Ping-Pong Technique for Photons. Phys Lett A (2006) 356(3):199–205. doi:10.1016/j.physleta.2006.03.048
36. Broadbent A, Jeffery S. Quantum Homomorphic Encryption for Circuits of Low T-Gate Complexity. In: Crypto 2015 (2014).
Keywords: quantum cooperative multicast, quantum hybrid topology network, quantum network, quantum multicast, information aggregation
Citation: Chen S-, Xu G, Chen X-, Shang T and Yang Y- (2022) Quantum Cooperative Multicast in a Quantum Hybrid Topology Network. Front. Phys. 10:842035. doi: 10.3389/fphy.2022.842035
Received: 23 December 2021; Accepted: 21 March 2022;
Published: 28 April 2022.
Edited by:
Zoltán Zimborás, University College London, United KingdomCopyright © 2022 Chen, Xu, Chen, Shang and Yang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xiu-Bo Chen, Zmx5b3ZlcjEwMEAxNjMuY29t
 Si-Yi Chen
Si-Yi Chen Gang Xu
Gang Xu Xiu-Bo Chen1*
Xiu-Bo Chen1*