- 1State Key Laboratory of Nuclear Resources and Environment, East China University of Technology, Nanchang, China
- 2School of Water Resources and Environmental Engineering, East China University of Technology, Nanchang, China
In order to improve the prediction accuracy of groundwater pollution diffusion path, this paper combines multivariate data fusion technology to predict and analyze the groundwater pollution diffusion path. Under the special two-strategy swarm game model of water pollution particle swarm, this paper introduces replication dynamics with bounded continuous time-delay. Moreover, considering the dynamic behavior in both cases of constant kernel function and exponential kernel function, the hawk-dove game model is a special case of the model we are discussing. In addition, this paper proposes a method combining leaching surface and flux concentration, and applies numerical simulation method to simulate and analyze transient leakage monitoring of similar point and line source pollution in planar two-dimensional heterogeneous aquifers. The experimental study verifies that the multivariate data fusion proposed in this paper can play an important role in the prediction of groundwater pollution diffusion path.
Introduction
Due to the complex formation of underground strata and extremely slow groundwater flow, groundwater pollution is characterized by slow process, difficult to find and difficult to manage. In particular, it is concealed and delayed in the early stage, and when it is found that the water quality has changed significantly, it has been polluted or seriously polluted (Bakhoum et al., 2020). Due to the continuous migration and circulation of groundwater, through runoff, discharge, water supply and other means, in the complex geological environment system, the groundwater system is closely hydraulically linked. Once groundwater is polluted, it is difficult to determine the scope of pollution and to restore it. Even if pollution and pollution sources are completely eliminated, it will take decades or even decades to restore water quality (Chao et al., 2020).
Sudden water pollution is very contingent and instantaneous, and a large amount of toxic and harmful pollutants are suddenly leaked in a relatively short period of time, which poses a great threat to the safety of water sources, and has high requirements for the timeliness of treatment and disposal., it is very difficult to deal with (Pandiarajan et al., 2019). Groundwater quality evaluation can quantitatively describe the pros and cons of groundwater environment. So far, twenty or thirty water quality evaluation methods have been widely used in the field of water environment (Rathi, 2021), such as single factor evaluation method, comprehensive index method, fuzzy mathematics method, etc. Literature (Ballen et al., 2021) used single factor evaluation method and fuzzy mathematics method to evaluate groundwater quality. Using the concept of section capacity, the water quality evaluation method was optimized to evaluate the water quality under different hydrological conditions. However, the usual water quality evaluation methods can only evaluate the excessive components and water quality grades of groundwater, and cannot determine the source of the excessive components in groundwater. Many scientific researchers have applied a variety of different methods to determine the source of groundwater pollution. Literature (Tshamala et al., 2021) applied genetic algorithm to the identification of groundwater pollution sources, and used a small amount of pollutant monitoring data to identify the source of groundwater pollution in regional sites. Literature (Santonastaso et al., 2021) established a simulation-optimization method and applied it to a polluted site. This method can use a small amount of pollutant data to deduce the amount of pollutants released by the pollution source at different times, so as to identify the groundwater of the site. Source of pollution. In the established pollution source identification index system, literature (MabvounaBiguioh et al., 2020) summarized and explored the key factors of groundwater pollution sources such as priority control of pollutants and pollution source characteristics, and used the means derived from the hazard level in the identification of groundwater pollution sources. Literature (Jongman et al., 2020) believes that the main method to identify the sources of trinitrogen pollution in groundwater is the combination of stable isotope tracing method and various identification methods. The existing exploration methods can effectively identify the sources of trinitrogen pollution in groundwater, but various pollution sources are not effective in identifying the sources of trinitrogen pollution in groundwater. The contribution ratio of three nitrogen pollution sources is not accurate and still needs to be improved. Literature (Bayat et al., 2021) used factor analysis in multivariate statistical methods to determine the source of groundwater pollution. Comparing the various pollution source identification methods mentioned above and the factor analysis method in the multivariate statistical method, by analyzing the relationship between the observed factors, the complex and multiple variables can be summarized into a small number of comprehensive factors, eliminating unnecessary factors. Intervention information to find out the main factors that lead to the deterioration of groundwater quality and their relative pollution sources does not require high continuity of the original water quality data, so this factor analysis method is often used in the identification of groundwater pollution sources.
Risk represents the probability of a certain damage or loss occurring in a certain period of time under a certain environment, and is composed of risk. Risk. Factor, risk. Receptor, risk. Accident, risk. Loss. Although a unified evaluation system for groundwater pollution risk has not yet been formed, after continuous exploration by domestic and foreign researchers, its concept has increasingly become scientific, comprehensive, and systematic (Motlagh and Yang, 2019). Literature (Kitajima et al., 2018) pointed out that the risk of groundwater pollution is the probability that groundwater is polluted under the action of human activities to reach its maximum acceptable pollution level, which is the result of the vulnerability of groundwater and the pollutants produced by human activities. Literature (Song et al., 2021) defines the risk of groundwater pollution as the possibility of occurrence of events that are caused by natural geological factors or human activities, but use groundwater as a medium for its circulation, thereby having a malignant impact on human health and the environment. Literature (Peng et al., 2021) used the mathematical expectation of groundwater pollution to express pollution risk. Literature (Tripathi and Chaurasia, 2020) used the DRASTIC model to evaluate the vulnerability of groundwater in the plain river network area (Shanghai), and then evaluated the risk of groundwater pollution in this area. Based on the DRASTIC-GIS model, the vulnerability of groundwater in typical regions was evaluated. Literature (Domańska et al., 2019) used the DRASTIC model and HYDRUS-1D and the MODFLOW simulation block of GMS to evaluate groundwater pollution risk. Literature (Bezagio et al., 2020) proposes a pollution risk assessment method for groundwater protection by realizing the visualization of solute transport model simulation, which can predict the pollution level and transport distance of specific pollutants in a site. Literature (Cope et al., 2019) used Hydrus-1D and VisualModflow to simulate the subsurface flow zone process and the saturated zone process simulation, respectively, and formulated their own pollution warning thresholds for the subsurface layer and the confining layer. The vulnerability of the aquifer to contamination was assessed and validated by applying hydrogeological and hydrothermal chemical methods, and the groundwater vulnerability of the site was mapped using the DRASTIC model. Literature (Kaushik et al., 2018) proposed a groundwater pollution risk assessment method with the objective of protecting the civil well, and used this method to conduct groundwater pollution risk assessment in a simple landfill. According to the inherent stochastic property of groundwater, a groundwater pollution risk assessment method based on uncertainty process simulation is summarized.
The migration and transformation process in groundwater is simulated and predicted that pollutants entering groundwater must pass through the vadose zone. Factors such as the lithology of the vadose zone and the height of the vadose zone can directly affect the pollution source intensity of the pollutants entering the groundwater. The more mature software for the transformation of pollutants in the vadose zone is HYDRUS-1D (Fereidooni et al., 2021). The HYDRUS-1D model (Zhang et al., 2018) can simulate groundwater moisture transport, thermal transport and the transport of various solutes. This model summarizes water transport, solute transport and crop root absorption, and is applicable to various boundary conditions such as atmospheric boundary and constant water head boundary. At present, the HYDRUS model has been widely used in many aspects such as nitrogen migration and water resource evaluation at home and abroad.
This paper combines the multivariate data fusion technology to predict and analyze the groundwater pollution diffusion path to improve the prediction accuracy of the groundwater pollution diffusion path.
Stability of replication dynamics with bounded continuously distributed delays
Model description and derivation
The concept of the evolutionary stable state of the water pollution particle swarm game is given. At the same time, the replication dynamics model with bounded continuous distribution time delay is deduced in detail under a special kind of game model of single water pollution particle swarm of two-strategy water pollution particle swarm.
Definition 1. PG=(X, F) is a single water pollution particle swarm game. If the social state
(1)
(2)There is a neighborhood
Then, the social state
Note 1. It can be seen from the above definition that the evolutionary stable state is actually a refinement of the Nash equilibrium, in which the first condition is the equilibrium condition and the second condition is the stability condition. It should be noted that although the ESS is still a static concept, condition 2) already reflects the dynamic idea. If social state y is the optimal response of
The legacy is that not all water pollution particle swarm games have evolutionary stable states.
Example 1. PG is a water pollution particle swarm game model with three strategies of single water pollution particle swarm. Therefore, the social state space is
It is easy to verify that the social state
In fact, for any social state
If we take
Therefore, condition 2) in Definition 1 cannot be established.
We assume that there is a water pollution particle swarm composed of a sufficiently large number of individuals, in which the individuals repeatedly interact with each other through random matching. In each strategy interaction, each individual has two strategies
Among them, c>a and b > d.
At time t, x(t) represents the individual share of choosing strategy
To sum up, we induce a water pollution particle swarm game PG with two strategies of single water pollution particle swarm from the classical non-cooperative two-person symmetric game. We set
Next, under the above-mentioned water pollution particle swarm game framework, considering the existence of bounded continuous distribution time delay, we deduce the replication dynamics model with bounded continuous distribution time delay in detail.
At the same time, we assume that
Among them, i = 1,2.
Note 2. When
Among them, i = 1,2. It should be noted that from the above equation, we can obtain the fixed-delay replication kinetic model of
Stability of evolutionary steady state under constant kernel function
In the equation, it is assumed that the kernel function
Next, we study the stability of the evolutionary stable state
Therefore, in order to discuss the stability of the constant solution
Among them,
According to the lemma, the zero solution of Eq. 5 is asymptotically stable if and only if all the eigenvalues of its corresponding eigenvalue equation have negative real parts. The corresponding feature equation can be obtained by simply changing the elements of the integral of Eq. 5.
That is,
Theorem 1. The evolutionary stable state g is asymptotically stable under replication dynamics 3) with bounded continuous distributed delays if and only if
Certification. Sufficiency. If
Proof by contradiction. We set
Without loss of generality, we assume
When performing variable substitution v = ws, we get
Further, we set the upper limit of the integral to be
Note that the first inequality holds because
Since
The above inequality states that k = 0 and
i) If
This contradicts hypothesis
(ii)If
Note that
This contradicts hypothesis
To sum up, we always have
Necessity. It is only necessary to prove that when
Note that when
Note that since the feature Eq. 10 has
Then,
Furthermore, it can be known from
Similarly, we can get:
Therefore, when
Furthermore, when
This shows that with the increase of, and if the root of the feature Eq. 10 returns to the imaginary axis, it is impossible to pass through the imaginary axis and enter the left half plane.
To sum up, as long as
In the hawk-dove game, two agents compete for resources with value V, and each agent has two strategies for him to choose, namely Hawk and Dove. If all individuals adopt the eagle strategy, the fight will end with one side injured, and the injured side will be at the cost of a decrease in fitness C.At the same time, individuals with two eagle strategies often have a 50% probability of defeating their opponents and a 50% probability of being injured. If one individual chooses the eagle strategy and the other chooses the dove strategy, the individual with the dove strategy withdraws and ends the competition. At this time, the eagle strategy individual enjoys the resource exclusively. In addition, if both agents choose the pigeon strategy, the individuals share the resource together. The eagle-dove game can be represented by the following matrix.
Among them, C > 0, V > 0. Further, we assume V < C, which means that the cost of injury is higher than the value of resources.
Obviously, the hawk-dove game model is a special case of the model discussed in our first section. At this point, the evolutionary stable state is
Taking C = 7 and V = 3, we numerically simulate the replication dynamics 6) with a bounded continuous distribution delay under a constant kernel function.
It can be seen from Figure 1 that the numerical solution of Eq. 7 converges to the evolutionary stable state
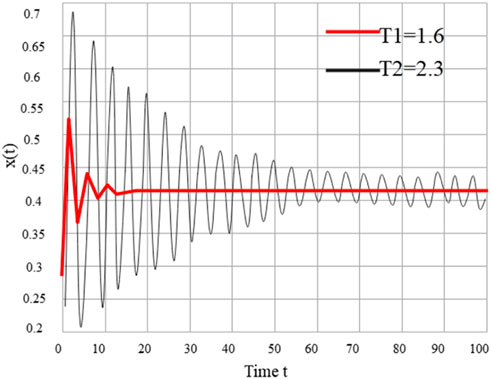
FiGURE 1. Numerical solution of Eq. 6 when 𝑉 = 3, 𝐶 = 7.
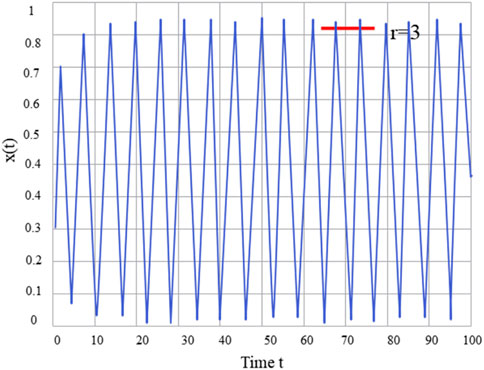
FIGURE 2. When 𝜏 = 3, the solution of Eq. 6 oscillates and does not converge.
Stability of evolutionary steady state under exponential kernel function
The stability of replication dynamics with bounded continuous time delays under constant kernel function is discussed. This section examines the stability of the evolutionary steady state when the kernel function has an exponential form. Note that the conclusions in this section are only a sufficient condition for the evolutionary stable state to be asymptotically stable. In fact, for general delay differential equations, it is difficult to obtain sufficient and necessary conditions for the stability of the solutions as in the previous section. This is the so-called conservative problem in the field of differential equations.
Below, we consider a replication dynamics model with bounded continuous distributed delays of the form.
Among them,
Note that in the above-mentioned time-delay evolution dynamics, the time-delay information at each moment is not equally important. The time lag information that is closer to the current time t has a greater impact on the current state. It can be said that the exponential kernel function is more general and more realistic than the constant kernel function. Similar to the discussion in the previous section, in order to examine the stability of the evolutionary stabilization strategy
Then the stability study of the solution
Further, linearizing Eq. 13 around
Among them,
Similar to the discussion in the previous section, it is easy to obtain the feature equation of the linearized Eq. 14 as follows:
That is,
When the time delay
Theorem 2. For sufficiently small delays τ, the evolutionary stable state 𝑥¯ is asymptotically stable under replica dynamics (12) with bounded continuously distributed delays.
The two roots
Therefore, the evolutionary stable state
Next, for a general time-delay τ, we obtain a sufficient condition for the evolutionary stable state 𝑥¯ to be asymptotically stable under replication dynamics (12). We look forward to finding a larger upper bound for delay τ in future work, which involves the conservation of equations and is also one of the key issues in the study of delay differential equations.
Theorem 3. Under replication dynamics (12) with bounded continuously distributed delays, the evolutionary stable state
Certification:
Separating the real and imaginary parts in the above formula, we get
If the real part of the characteristic root
Further, from the integral median theorem, we know that:
Among them,
Among them,
Note that by combining Eq. 18, we get:
This is a contradiction. Therefore, the real part is u < 0. This shows that when
At the end of the previous section, we validated our results by numerical simulations of replication dynamics with a bounded continuous distributed delay under a constant kernel function against the background of the hawk-dove game model. Next, we give a simple example of replication dynamics (12) with bounded continuous time-delay under the exponential kernel function under the eagle-dove game model with the same parameters. We briefly restate the eagle-dove game model, and its game matrix is as follows.
Among them, C > 0, V > 0, V < C. Continuing from the previous section, when C = 7, V = 3, it is easy to calculate the evolutionary stable state
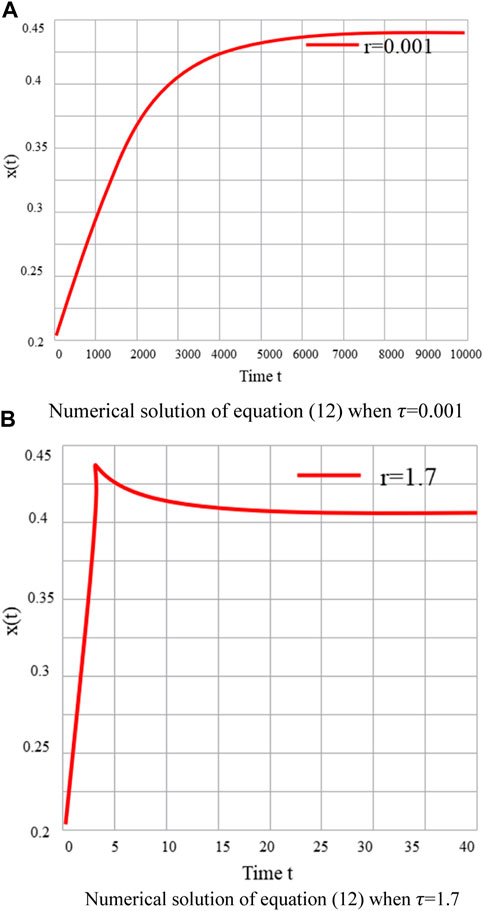
FIGURE 3. Simulation analysis diagram 3Prediction of groundwater pollution diffusion path based on multi-source data fusion. (A) Numerical solution of equation (12) when τ = .001; (B) Numerical solution of equation (12) when τ = 1.7).
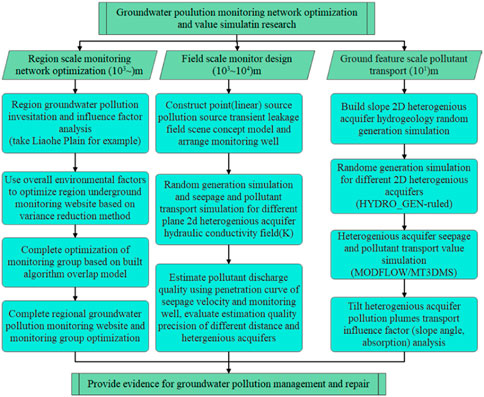
In this paper, a method combining leaching surface and flux concentration is proposed, and a numerical simulation method is applied to simulate and analyze transient leakage monitoring of similar point and line source pollution in a planar two-dimensional heterogeneous aquifer. On the stratigraphic characteristic scale, the stochastic simulation method is used to generate the profile two-dimensional heterogeneous anisotropic aquifer. Under the conditions of convective dispersion and adsorption, the migration and evolution of polluted plumes in this special heterogeneous formation are analyzed by numerical simulation method, which provides a reference for the monitoring and management of such polluted aquifers. The prediction of groundwater pollution diffusion path based on the total multi-source data fusion in this paper is shown in Figure 4.
Taking the identification of sudden pollution incidents as the ultimate goal, the four factors of environmental impact factors, emergency response factors, social impact factors, and groundwater system factors are used as the criterion layers. The identification index system of sudden pollution incidents is established by refining the supported indicators respectively, as shown in Figure 5. The selection of indicators in the indicator system is based on the principles of scientificity, systematicness, pertinence and operability.
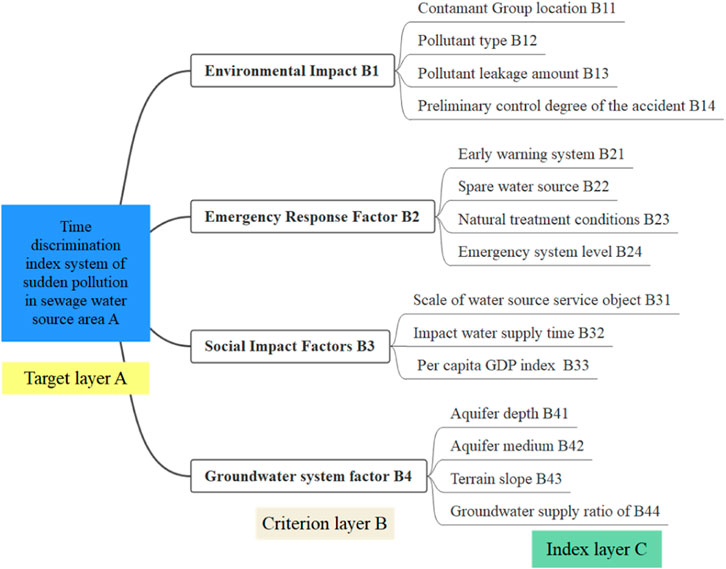
FIGURE 5. Indicator system for the identification of emergency disposal technologies for sudden pollution in groundwater sources.
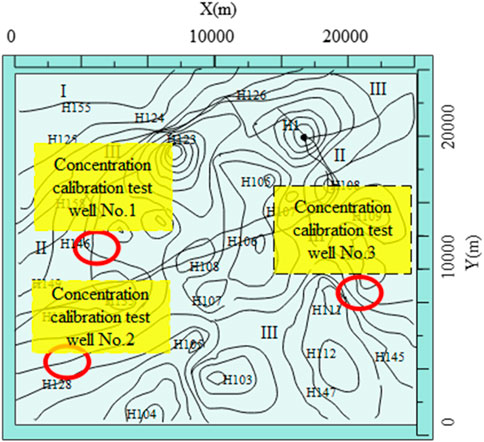
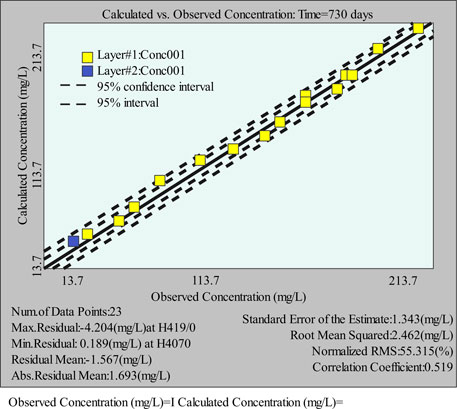
In order to further verify the reliability of the established mathematical model and model parameters, the experimental analysis is carried out, and the study is carried out in a certain area, as shown in Figure 6. From the concentration fitting diagram in Figure 7, a total of 23 observation points is taken in the model identification stage. It can be seen that the isolines of the measured and calculated concentrations also achieve a good fit as a whole. It shows that the established hydrogeological conceptual model and mathematical model are reasonable.
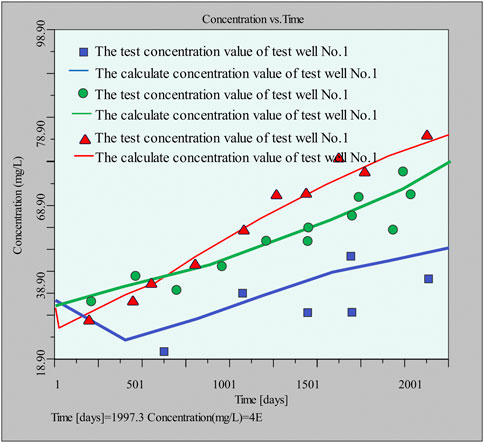
It is divided into six stress periods, and each 360 days is a stress period. From the inspection results, select three representative observation holes. It can be seen that the model identification and verification results prove that the established mathematical model, boundary conditions, hydrogeological parameters and source-sink terms are all reasonable, and the model can be used for the prediction of groundwater solute system (Figure 8).
The above research verifies that the multivariate data fusion proposed in this paper can play an important role in the prediction of groundwater pollution diffusion paths.
Conclusion
In recent years, with the acceleration of industrialization and urbanization, the demand for water has increased dramatically. The unreasonable exploitation of groundwater resources has led to the continuous deterioration of regional water resources, the increasingly serious water pollution, and the increasingly prominent contradictions in urban water supply, industry, agriculture and animal husbandry. At present, environmental problems such as ground subsidence, ground fissures, and ground subsidence have occurred in many areas, which have seriously affected the lives of local people and greatly restricted local economic development. Groundwater pollution refers to the phenomenon that the quality of groundwater is degraded under the influence of human activities, thereby changing the physical properties, chemical composition and biological characteristics of water. This paper combines the multivariate data fusion technology to predict and analyze the groundwater pollution diffusion path to improve the prediction accuracy of the groundwater pollution diffusion path. The experimental study verifies that the multivariate data fusion proposed in this paper can play an important role in the prediction of the groundwater pollution diffusion path.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
YZ: supervision; investigation XH: investigation YL: writting.
Funding
National Natural Science Foundation of China (No. 42107093, 42062017, U1967209); Open Fund for State Key Laboratory of Nuclear Resources and Environment, East China University of Technology (No. NRE 1927); Open Fund for Fundamental Science on Radioactive Geology and Exploration Technology Laboratory, East China University of Technology (No. RGET 1904).
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Bakhoum, J. P., Diop, N. A., Bodian, E. H. T., Mbaye, O., Diaw, P., Cisse, L., et al. (2020). Development of an on-site early warning water quality monitoring system for pesticide detection by absorption and photo-induced fluorescence. Environ. Sci. Pollut. Res. 27 (36), 45238–45249. doi:10.1007/s11356-020-10406-x
Ballen, S. C., Ostrowski, G. M., Steffens, J., and Steffens, C. (2021). Graphene oxide/urease nanobiosensor applied for cadmium detection in river water. IEEE Sensors J. 21 (8), 9626–9633. doi:10.1109/jsen.2021.3056042
Bayat, F., Didar, T. F., and Hosseinidoust, Z. (2021). Emerging investigator series: Bacteriophages as nano engineering tools for quality monitoring and pathogen detection in water and wastewater. Environ. Sci. Nano 8 (2), 367–389. doi:10.1039/d0en00962h
Bezagio, R. C., Colli, C. M., Romera, L. I. L., de Almeida, C. R., Ferreira, É. C., Mattia, S., et al. (2020). Improvement in cyst recovery and molecular detection of Giardia duodenalis from stool samples. Mol. Biol. Rep. 47 (2), 1233–1239. doi:10.1007/s11033-019-05224-5
Chao, D., Chen, J., Dong, Q., Wu, W., Qi, D., and Dong, S. (2020). Ultrastable and ultrasensitive pH-switchable carbon dots with high quantum yield for water quality identification, glucose detection, and two starch-based solid-state fluorescence materials. Nano Res. 13 (11), 3012–3018. doi:10.1007/s12274-020-2965-8
Cope, J. R., Kahler, A. M., Causey, J., Williams, J. G., Kihlken, J., Benjamin, C., et al. (2019). Response and remediation actions following the detection of Naegleria fowleri in two treated drinking water distribution systems, Louisiana, 2013–2014. J. water health 17 (5), 777–787. doi:10.2166/wh.2019.239
Domańska, M., Hamal, K., Jasionowski, B., and Łomotowski, J. (2019). Bacteriological contamination detection in water and wastewater samples using OD600. Pol. J. Environ. Stud. 28 (6), 4503–4509. doi:10.15244/pjoes/94838
Fereidooni, Z., Tahayori, H., and Bahadori-Jahromi, A. (2021). A hybrid model-based method for leak detection in large scale water distribution networks. J. Ambient Intell. Humaniz. Comput. 12 (2), 1613–1629. doi:10.1007/s12652-020-02233-2
Jongman, M., Carmichael, P. C., and Bill, M. (2020). Technological advances in phytopathogen detection and metagenome profiling techniques. Curr. Microbiol. 77 (4), 675–681. doi:10.1007/s00284-020-01881-z
Kaushik, M., Nandi, A. V., and Mungurwadi, V. B. (2018). Portable sensors for water pathogens detection. Mater. Today Proc. 5 (4), 10821–10826. doi:10.1016/j.matpr.2017.12.368
Kitajima, M., Sassi, H. P., and Torrey, J. R. (2018). Pepper mild mottle virus as a water quality indicator. NPJ Clean. Water 1 (1), 19–9. doi:10.1038/s41545-018-0019-5
Mabvouna Biguioh, R., Adogaye, S. B. B., Pete, N., Martial, P., Sanou Sobze, M., Kemogne, J. B., et al. (2020). Microbiological quality of water sources in the west region of Cameroon: Quantitative detection of total coliforms using micro biological survey method. BMC public health 20 (1), 346–347. doi:10.1186/s12889-020-8443-0
Motlagh, A. M., and Yang, Z. (2019). Detection and occurrence of indicator organisms and pathogens. Water Environ. Res. 91 (10), 1402–1408. doi:10.1002/wer.1238
Pandiarajan, S., Thambiratnam, S., and Sivaruban, I. R. B. (2019). Bio-monitoring and detection of water quality using Ephemeroptera, plecoptera and Trichoptera (EPT) complex in karanthamalai stream of eastern ghats. Indian J. Ecol. 46 (4), 818–822.
Peng, J., Xia, C. Q., Xu, Y., Li, R., Cui, L., Clegg, J. K., et al. (2021). Crystallization of CsPbBr3 single crystals in water for X-ray detection. Nat. Commun. 12 (1), 1531–1610. doi:10.1038/s41467-021-21805-0
Rathi, S. (2021). S-PLACE ga for optimal water quality sensor locations in water distribution network for dual purpose: Regular monitoring and early contamination detection–a software tool for academia and practitioner. Water Supply 21 (2), 615–634. doi:10.2166/ws.2020.333
Santonastaso, G. F., Di Nardo, A., Creaco, E., Musmarra, D., and Greco, R. (2021). Comparison of topological, empirical and optimization-based approaches for locating quality detection points in water distribution networks. Environ. Sci. Pollut. Res. 28 (26), 33844–33853. doi:10.1007/s11356-020-10519-3
Song, H., Zhou, Y., Li, Z., Zhou, H., Sun, F., Yuan, Z., et al. (2021). Inner filter effect between upconversion nanoparticles and Fe (ii)–1, 10-phenanthroline complex for the detection of Sn (ii) and ascorbic acid (AA). RSC Adv. 11 (28), 17212–17221. doi:10.1039/d1ra01925b
Tripathi, S. M., and Chaurasia, S. (2020). Detection of Chromium in surface and groundwater and its bio-absorption using bio-wastes and vermiculite. Eng. Sci. Technol. Int. J. 23 (5), 1153–1161. doi:10.1016/j.jestch.2019.12.002
Tshamala, A. K., Musala, M. K., Kalenga, G. K., and wa Mumapanda, H. D. (2021). Assessment of surface water quality in kakanda: Detection of pollution from mining activities. J. Environ. Prot. 12 (9), 561–570. doi:10.4236/jep.2021.129035
Keywords: multi-source data fusion, groundwater, pollution diffusion, path prediction, dynamics model
Citation: Zhang Y, Huo X and Luo Y (2023) Prediction of groundwater pollution diffusion path based on multi-source data fusion. Front. Environ. Sci. 10:1116309. doi: 10.3389/fenvs.2022.1116309
Received: 05 December 2022; Accepted: 19 December 2022;
Published: 05 January 2023.
Edited by:
Junyuan Guo, Chengdu University of Information Technology, ChinaReviewed by:
Wenjing Wang, Shandong University of Technology, ChinaHan Lian, Henan Polytechnic Institute, China
Copyright © 2023 Zhang, Huo and Luo. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Yanhong Zhang, eWFuaG9uZ3poYW5nQGVjdXQuZWR1LmNu
 Yanhong Zhang
Yanhong Zhang Xiaofeng Huo2
Xiaofeng Huo2