- 1School of Information Engineering, Nanchang University, Nanchang, China
- 2State Grid Shanghai Municupal Electric Power Company, Shanghai, China
- 3China Electric Power Research Institute, Beijing, China
When False Data Injection (FDI) attacks inject false data into the controllers of a microgrid, it can lead the controllers to make decisions based on inaccurate information, ultimately resulting in system collapse. This study presents a novel approach to dynamically adjust output voltage in Campus Microgrids (CMG). Initially, we use feedback linearization techniques to address the inherent nonlinear complexities in Distributed Generation (DG) dynamics. Moreover, during voltage regulation, controllers and sensors may be susceptible to FDI attacks. To address this, an elastic follower observer is introduced to mitigate the impact of false information injection attacks on voltage coordination, thus ensuring the robustness and stability of the system. Notably, our method reduces dependence on global information and fault boundaries within the communication network, thereby enhancing system elasticity and efficiency. In conclusion, through comprehensive simulation experiments, we evaluate the effectiveness and performance of our proposed strategy. The simulation results validate the success of our approach in voltage regulation and its efficiency in fault management. These findings bear significant implications for the advancement of voltage regulation strategies in distributed generation systems.
1 Introduction
A CMG serves as a self-contained energy system within a university campus, integrating diverse distributed energy sources, loads, and energy storage components. Operating on alternating current, the CMG can function independently or in coordination with the central power grid, establishing an interlinked network for energy distribution within the campus. This setup provides a degree of autonomy and flexibility, enabling the CMG to autonomously regulate energy generation, storage, and consumption, ensuring reliable and efficient power supply for the campus (Zhang et al., 2020).
The hierarchical control of CMG aims to achieve effective management of control at various levels within the microgrid, enhancing the robustness, stability, and performance of the system. This hierarchical structure typically includes the primary control layer, secondary control layer, and tertiary control layer. Primary control focuses on the operation and control of equipment within the CMG, with responsibilities such as voltage stabilization. Secondary control takes on a higher-level role, primarily concerned with voltage restoration and maintenance within the CMG. Secondary controls in CMGs can be broadly categorized into three main types: decentralized, centralized, and distributed. In decentralized control, each DG in a CMG operates independently based on local information, leading to challenges in achieving precise global control objectives (Gu et al., 2017). Centralized control relies on a central controller to compute and issue control commands to all DGs within the CMG, coordinating their actions to achieve the overall control objectives. The presence of a single point of failure introduces a potential risk (Qian et al., 2020). Distributed control relies on communication links between adjacent DGs to attain consensus through reciprocal information exchange. This collaborative communication plays a vital role in achieving coordinated actions among DGs for tasks in a distributed power system (Li et al., 2013; Li et al., 2021; Liu et al., 2022). It overcomes the limitations of centralized control, such as single point of failure, while retaining some of the advantages of decentralized control, such as local autonomy and fast response time. This approach yields a more robust and reliable control strategy that can adapt to dynamic changes within the CMG.
In recent years, there has been a discernible shift in the MG control domain towards an increased reliance on distributed control as the primary approach for secondary control in MGs (Bidram et al., 2013; Im et al., 2017; Hu et al., 2022). Numerous distributed control methods have been proposed by researchers to address specific challenges encountered in MG operation. For example, in (Zhou et al., 2018), a distributed consensus protocol is formulated to address accurate reactive, harmonic, and unbalanced power-sharing issues in MGs. This protocol ensures that DGs within the MG achieve a consensus on power sharing, thereby enhancing overall system performance. Another notable approach is presented in (Dehkordi et al., 2017), introducing distributed finite-time regulators for coordinating voltage in islanded MGs. This method facilitates effective coordination and control among DGs, even in islanded operation scenarios. Moreover, the investigation carried out in (Ning et al., 2021) focuses on the distributed secondary control of isolated AC MGs amid external disturbances. By considering external factors, this research aims to enhance the resilience and adaptability of MGs in challenging operational conditions. It's crucial to note that while these distributed secondary control strategies (Bidram et al., 2013; Dehkordi et al., 2017; Zhou et al., 2018; Ning et al., 2021; Hu et al., 2022) exhibit promising results, they often presume ideal conditions where components is considered perfect. In practical scenarios, MG systems may confront imperfections and uncertainties, necessitating further research in developing robust control strategies capable of addressing real-world challenges.
In practical microgrid systems, network anomalies and cyber attacks can significantly impact their operations. To address this challenge, various distributed control schemes have been proposed, aiming to establish resilient control strategies to ensure stable voltage and frequency regulation within the closed-loop system (Abhinav et al., 2017; Zhai et al., 2022a; Zhai et al., 2022b). Research (Li et al., 2022) explores the communication fault recovery capabilities of islanded AC MGs in distributed secondary voltage and frequency control when facing partial failures in communication links and specific types of data manipulation attacks. Additionally, an adaptive control approach proposed in (Dehkordi et al., 2019) is employed to restore the output voltage of DGs inverters considering noise, while investigating scenarios involving output voltage and frequency regulation, communication delays, and switch topology. Furthermore, considering the impact of cyber attacks (Deng et al., 2021), presents a current-sharing and voltage-resilience scheme to address challenges posed by communication delays and denial-of-service (DoS) attacks characteristic of isolated DC microgrids. Researchers in (Shen et al., 2023) propose a distributed resilient secondary control method for islanded AC microgrids, considering factors such as network security, communication overhead, and transmission delays in controller design. In practical scenarios, FDI attacks are prevalent in cyber attacks. These attacks primarily target controllers and sensors of nodes, rendering electrical components (such as controllers and sensors) vulnerable to attack in microgrids.
Centralized control strategies, as discussed in, introduce single point of failure and depend heavily on global information, making them vulnerable to communication failures and cyberattacks. Ideal Many distributed control methods, such as those in, assume perfect communication conditions, which is not realistic in practical scenarios where network anomalies and cyberattacks can occur. While some research has focused on resilience against cyberattacks, the solutions often do not comprehensively address the adaptive control strategies required to manage the complexities introduced by FDI attacks on both controllers and sensors.
The increasing complexity and integration of renewable energy sources into CMGs have heightened the susceptibility of these systems to cyberattacks, particularly FDI attacks. These attacks can lead to erroneous decisions by controllers, potentially causing system collapse. Existing studies have primarily focused on centralized control methods, which suffer from single points of failure and high dependency on global information. There is a pressing need for more resilient and distributed control strategies that can mitigate the effects of cyberattacks while maintaining system stability and efficiency (Dagar et al., 2021; Rafique et al., 2022; Khalid et al., 2023). This research is driven by the necessity to develop such robust control mechanisms that can dynamically adjust output voltage and ensure reliable operation in the face of cyber threats.
This work addresses the challenge of voltage regulation in CMGs under the threat of FDI attacks. We focus on developing a fully distributed control strategy that leverages feedback linearization and an elastic follower observer to enhance system resilience. Unlike previous approaches that rely heavily on centralized control and global information, our method reduces dependence on global data and fault boundaries within the communication network. The scope of this research encompasses the modeling of CMG dynamics, the design of resilient control strategies, and the validation of these strategies through comprehensive simulation experiments. The objective is to ensure robust voltage regulation and fault management in distributed generation systems within a university campus setting.
The primary contributions of this study are threefold. First, unlike (Bidram et al., 2013; Abhinav et al., 2017; Dehkordi et al., 2017; Zhou et al., 2018; Dehkordi et al., 2019; Deng et al., 2021; Ning et al., 2021; Zhai et al., 2022a; Zhai et al., 2022b; Hu et al., 2022; Li et al., 2022; Shen et al., 2023), this paper explores the challenges of regulating the output voltage of a distributed power supply under FDI attacks, where the attacks lead to the failure of controllers and sensors. We propose an innovative elastic follower observer designed to mitigate the impact of FDI attacks on voltage coordination, ensuring the robustness and stability of the CMG. Second, the resilient control strategy presented in this paper is fully distributed, due to the use of adaptive and boundary layer techniques. It effectively avoids the dependence on global information and fault parameters within the boundaries of the communication network. Compared to the strategy based on MG (Li et al., 2022) and MAS (Shen et al., 2023), the fault signals are less restrictive and the method in this paper ensures a more robust and flexible control system for distributed power supply. This approach provides a more flexible and robust control system compared to traditional centralized or decentralized methods. Third, through detailed simulation experiments, we demonstrate the effectiveness of our strategy in maintaining voltage stability and efficient fault management under various load conditions and cyberattack scenarios. These contributions represent significant advancements in the field of voltage regulation in distributed generation systems, providing a foundation for future research on resilient control strategies.
The paper is structured as follows: In Section II, we present a modeling framework aimed at addressing the output regulation challenge in CMGs. Section III conducts a detailed analysis of the problem statement and establishes models for controller and sensor failures induced by cyberattack. Section IV showcases the primary outcomes of our investigation. We introduce a pioneering elastic voltage regulation strategy founded on inclusion control. This strategy is meticulously crafted to adeptly manage voltage under communication failures, ensuring the stable and reliable operation of CMGs. Section V is dedicated to the verification and validation of the proposed control methods. Through a combination of simulation and experimental studies, we substantiate the effectiveness and performance of the proposed method in real-world scenarios. Finally, in the sixth section, we encapsulate the key findings and contributions of this paper. We conclude by discussing the implications of this study in the realm of CMG control, while also shedding light on potential avenues for future exploration and enhancement.
2 Methods
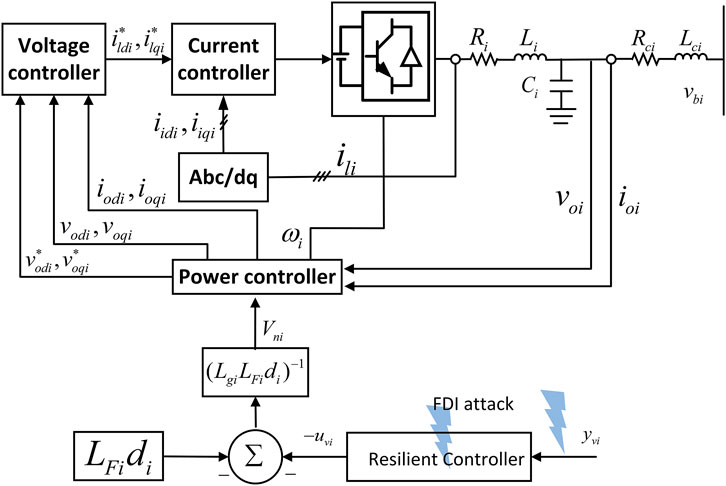
In this research, our focus is directed towards tackling the issue of regulating the output voltage in a CMG comprising DGs. Each DG incorporates components such as droop control, inner-loop voltage and current control, LC filter, secondary control, and the line model. Refer to Figure 1 for an illustration of this model.
The concise representation of the nonlinear dynamic model for the AC CMG is as follows:
where the state vector is
and
Expressions for dynamic parameters can be acquired from the source provided in (Bidram et al., 2013).
Then,
where
The virtual leader are illustrated as follows:
where
2.1 Problem statement
The interaction among the N DGs in the CMG is depicted through a graph
To depict the graph structure, we introduce the nonsymmetric Laplacian matrix
Assumption 1. The communication structure among the DGs is undirected, signifying specified directions in the flow of information among the nodes. Furthermore, the dynamics of the virtual leader are oriented towards all DGs.
Assumption 1 constitutes a foundational and standard premise for consensus control within MASs.
2.2 Attack model and analysis
The coupling between the information system and the physical system in the distributed control strategy makes the CMG architecture more vulnerable to cyber attacks. An attacker can inject malicious measurement data into the secondary controller and sensor of the power system, thereby destabilizing and disrupting the operation of the power grid.
Controller signals and sensor signals are most susceptible to FDI attacks during the communication process, assuming that the FDI attack model in the channel is:
where
Assumption 2. The time-varying parameters
Assumption 3. The magnitude of
where
Assumption 4. The time derivative of the sensor fault signal is limited and can be expressed as
The dynamic model for the i th DG is given by
The type of attack considered in this paper is FDI attack on both controllers and sensors. The result of the attack leads to partial malfunction and abnormal deviations in controller and sensor signals, as depicted in Eqs 7, 8. In industrial control systems, FDI attacks pose a significant security threat as Eqs 9, 10. The primary objective of this paper is to ensure that, despite the presence of FDI attacks, the output voltage of distributed power sources can still coordinate effectively.
2.3 Main result
In this section, our aim is to attain co-regulation of the output voltages, denoted as vodi, i = 1, 2, … , N, in a CMG. To accomplish this, we formulate a secondary voltage strategy that takes into account the FDI attacks. To estimate the system state, we introduce the following state observer for the i th DG:
where
and
The global dynamics is illustrated as follows:
where
Auxiliary controllers uvi in (7) based on observer-triggered states are designed as follows:
where
where χi being small positive scalars according Eqs 11-16, we can get Eqs 17-22. Then,
Denote Ψi =
Define
where ε = col{ε1, ε2, … , εN}. Let ξ = col{Ψ,
where β = [0,
Obtaining dynamics for ε is straightforward and can be expressed as:
where
Theorem 1. Given the satisfaction of Assumptions 1, 2, and 3, and the existence of suitable
where
Proof. Let’s examine the proposed Lyapunov function candidate
where
where μ and
The time derivative of V1 along the trajectory defined by (20) is derived as follows:
Applying Young’s inequality with positive constants χ1, we get:
Then,
It from (17) follows that:
Because of ςvi and γ(χ):
Case 1.
Case 2.
Case 3. Without loss of generality, let’s assume
Referring to (32)–(34), we can derive:
Given LvLTv ≤ BvBTv, it follows that:
and
Utilizing (35)–(37) in conjunction with (31), we derive:
Note that
and
By combining (39) and (40), we can deduce:
Since μ > 1/2c
It is noteworthy that (42) can be reformulated as:
Given 0<δ≤
V demonstrates exponential convergence towards a limited set:
where
Consequently, Ψi, ζi, and ρi for i = 1, 2, … , N are uniformly ultimately bounded. According Eqs 25-46, this completes the proof.
Therefore, the algorithm designed in this chapter can be able to achieve a reasonable regulation of the output voltage under the cyberattack to restore the voltage to the reference value.
3 Results and discussion
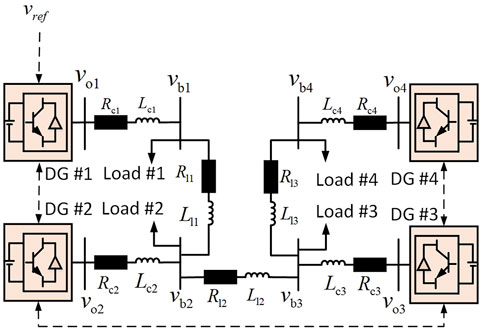
This section seeks to illustrate the practicality and effectiveness of the proposed strategy for resilient output voltage regulation. Simulations were conducted in the MATLAB/Simulink software environment using an CMG configuration illustrated in Figure 2, consisting of four DGs.
Table 1 furnishes the parameters corresponding to the DGs, lines, and loads as illustrated in Figure 2. The communication topology among DGs is depicted in Figure 2, with DG #1 receiving information from vref1.
The selected scenarios were deliberately crafted to offer a comprehensive assessment of the system’s performance across diverse conditions. The use of an undirected communication topology ensures efficient information exchange among DGs. Through these simulated scenarios, we gain a nuanced insight into the adaptability of the proposed approach, showcasing its robustness in the face of varying load conditions.
In this case scenario, we assess the efficacy of the proposed resilient voltage regulation approach during islanding, commencing at t = 0.0 s. The following four test scenarios were executed:
At t = 0.5 s, the secondary control for output voltage regulation is activated.
At t = 1s, load #2 is reduced by 50%.
At t = 1.5 s, 50% of load #2 is reinstated to its initial value.
Then,
We designate vref1 = 220 and select the control parameters for the output voltage algorithm as c = 1.5e+7. vti = 1, ιvi = 5 for i = 1, 2, … ,4. The initial values of ιi(t) are set as ιi(0.5) = 1 for i = 1, 2, … , N. The communication link faults are defined as follows: ζv1 = 0.5sin(2t+5)+0.55, ζv2 = 0.7, ζv3 = 0.1sint+0.7, ζv4 = 0.5sint+0.8, kv1 = 0.5cos(4t+9)+0.1, kv2 = 0.8, kv3 = 0.5cos(6t+7)+0.8, kv4 = 0.1cost+0.8, fv1 = 0.5cos(3t+5)+0.1, fv2 = 0.5sin(4t+9)+0.1, fv3 = 0.2, fv4 = 0.1cost.
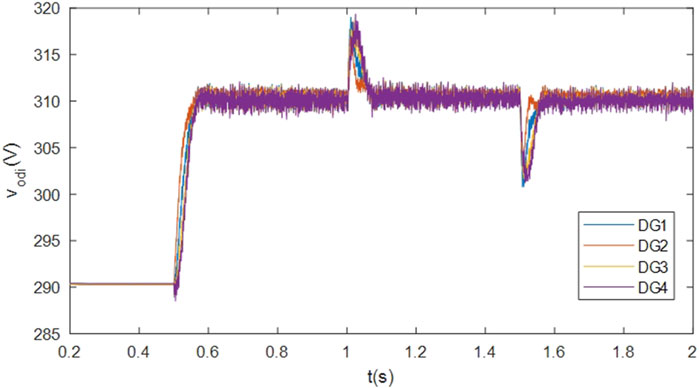
The efficacy of the output voltage regulation algorithm within the CMG is validated through diverse test scenarios. Initially, the algorithm utilizes primary control, dynamically adjusting the drop factor to ensure voltage stability, as illustrated in Figure 3. The primary control effectively maintains voltage stability. However, the operation in differential mode leads to voltage deviations from the nominal value.
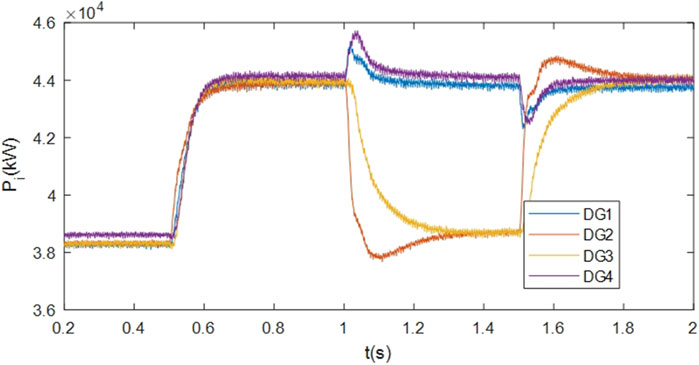
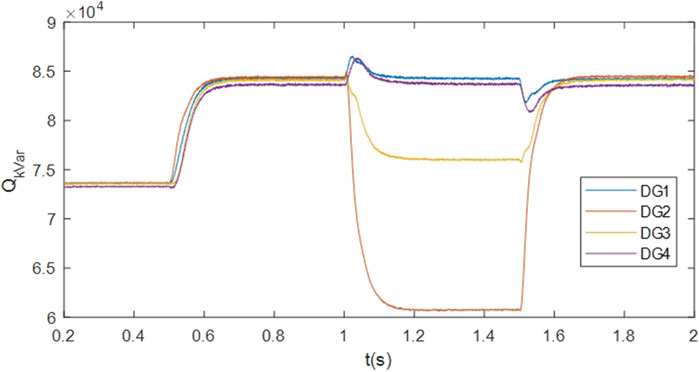
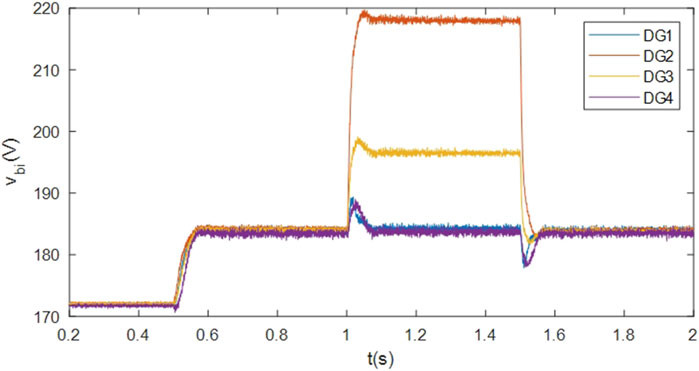
Following the initiation of the secondary control algorithm at t = 0.5s, the output voltages are effectively regulated to reference values vref. At t = 1s and t = 1.5 s, the implemented output voltage restoration strategy adeptly reinstates the target voltage level following temporary load disconnection and reconnection. Figures 4, 5, 6 provide additional insights into the variations in active power, reactive power, and bus voltages, serving to underscore the efficacy of the devised voltage regulation methodology.
In conclusion, the demonstrated strategy has been substantiated for its effectiveness in scenarios involving load shifting and plugging. This substantiation establishes the proposed approach as a resilient and dependable means to guarantee the stable operation of the MG. Such validation further strengthens the credibility and applicability of the proposed strategy in real-world contexts. In order to clearly show the implementation process, we summarize the pseudo-code of the algorithm proposed in this paper in Algorithm 1.
4 Conclusion
This paper introduces a secondary control strategy for adaptive AC automatic voltage regulation systems. Addressing the potential challenges posed by FDI attacks faced by DG in real-world scenarios, we propose an elastic control algorithm based on the output feedback of a state observer. This algorithm enhances communication flexibility while avoiding the necessity for global information in the communication network, thereby eliminating reliance on specific application fault parameters. The method exhibits resilience and adaptability to real constraints, ensuring stable and reliable operation of automatic control systems. In the future, we will work on islanded MG distributed secondary control under more complex attack structures using sliding mode control or studying hidden Markov models down the line.
Algorithm 1.Resilient Voltage Regulation Strategy.
1: Initialize parameters:
communication_faults ← {fault parameters}
observer parameters ← {
control gains ← {
2: Define dynamic model for AC CMG: function dynamic_model(state, control_input)
Retrieve dynamic parameters
Apply feedback linearization
Return transformed state end function
3: Define feedback linearization function: function feedback_linearization(state, dynamic_parameters)
Linearize the nonlinear dynamic equations
Return linearized state end function
4: Define state observer: function state_observer(state, estimated_state)
Compute observer output
Return observer output end function
5: Main Resilient Voltage Regulation Strategy: while system is operational do
for each DG i in 1 to
Update state observer estimates
Compute auxiliary control inputs
Update global dynamics:
Compute global tracking error
Update observer error
Apply control strategy based on observer-triggered states
if time in load_changes then
Apply load changes end if
end while
6: End of algorithm
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author contributions
HL: Conceptualization, Methodology, Writing–original draft. LH: Data curation, Formal Analysis, Writing–review and editing. ZD: Supervision, Visualization, Writing–review and editing. SW: Project administration, Supervision, Writing–review and editing.
Funding
The author(s) declare that financial support was received for the research, authorship, and/or publication of this article. The work was financially supported by Science and Technology Projects from State Grid Corporation of China, (5400-202317577A-3-2-ZN). The model simulation platform of this work is supported by the Mechanical Engineering Post-doctoral Research Station of Nanchang University.
Conflict of interest
Author ZD was employed by State Grid Shanghai Municupal Electric Power Company.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
The authors declare that this study received funding from Science and Technology Projects from State Grid Corporation of China. The funder had the following involvement in the study: data collection and analysis.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abhinav, S., Schizas, I. D., Ferrese, F., and Davoudi, A. (2017). Optimization-based AC microgrid synchronization. IEEE Trans. Industrial Inf. 13 (5), 2339–2349. doi:10.1109/TII.2017.2702623
Bidram, A., Davoudi, A., Lewis, F. L., and Guerrero, J. M. (2013). Distributed cooperative secondary control of microgrids using feedback linearization. IEEE Trans. Power Syst. 28 (3), 3462–3470. doi:10.1109/TPWRS.2013.2247071
Dagar, A., Gupta, P., and Niranjan, V. (2021). Microgrid protection: a comprehensive review. Renew. Sustain. Energy Rev. 149, 111401. doi:10.1016/j.rser.2021.111401
Dehkordi, N. M., Baghaee, H. R., Sadati, N., and Guerrero, J. M. (2019). Distributed noise-resilient secondary voltage and frequency control for islanded microgrids. IEEE Trans. Smart Grid 10 (4), 3780–3790. doi:10.1109/TSG.2018.2834951
Dehkordi, N. M., Sadati, N., and Hamzeh, M. (2017). Distributed robust finite-time secondary voltage and frequency control of islanded microgrids. IEEE Transations Power Syst. 32 (5), 3648–3659. doi:10.1109/TPWRS.2016.2634085
Deng, C., Guo, F., Wen, C., Yue, D., and Wang, Y. (2021). Distributed resilient secondary control for DC microgrids against heterogeneous communication delays and DoS attacks. IEEETransactions Industrial Electron. 17 (2), 1141–1153. doi:10.1109/TII.2020.2976830
Gu, W., Lou, G., Tan, W., and Yuan, X. (2017). A nonlinear state estimator-based decentralized secondary voltage control scheme for autonomous microgrids. IEEE Trans. Power Syst. 32 (6), 4794–4804. doi:10.1109/TPWRS.2017.2676181
Hu, J., Sun, Q., Wang, R., Wang, B., Zhai, M., and Zhang, H. (2022). Privacy-preserving sliding mode control for voltage restoration of AC microgrids based on output mask approach. IEEE Trans. Industrial Inf. 18 (10), 6818–6827. doi:10.1109/TII.2022.3141428
Im, W. S., Wang, C., Liu, W., Liu, L., and Kim, J. M. (2017). Distributed virtual inertia based control of multiple photovoltaic systems in autonomous microgrid. IEEE/CAA J. Automatica Sinica 4 (3), 512–519. doi:10.1109/JAS.2016.7510031
Khalid, H. M., Flitti, F., Mahmoud, M. S., Hamdan, M., Muyeen, S., and Dong, Z. Y. (2023). Wide area monitoring system operations in modern power grids: a median regression function-based state estimation approach towards cyber attacks. Sustain. Energy, Grids Netw. 34, 101009. doi:10.1016/j.segan.2023.101009
Li, X., Sun, Z., Tang, Y., and Karimi, H. R. (2021). Adaptive event-triggered consensus of multiagent systems on directed graphs. IEEE Trans. Autom. Control 66 (4), 1670–1685. doi:10.1109/tac.2020.3000819
Li, X., Wen, C., Chen, C., and Xu, Q. (2022). Adaptive resilient secondary control for microgrids with communication faults. IEEE Trans. Cybern. 52 (8), 8493–8503. doi:10.1109/tcyb.2021.3070820
Li, Z., Ren, W., Liu, X., and Fu, M. (2013). Consensus of multi-agent systems with general linear and Lipschitz nonlinear dynamics using distributed adaptive protocols. IEEE Trans. Autom. Control 58 (7), 1786–1791. doi:10.1109/TAC.2012.2235715
Liu, S., Sun, J., Zhang, H., and Zhai, M. (2022). Fully distributed event-driven adaptive consensus of unknown linear systems. IEEE Trans. Neural Netw. Learn. Syst. 34, 8007–8016. doi:10.1109/TNNLS.2022.3148824
Ning, B., Han, Q. L., and Ding, L. (2021). Distributed secondary control of ac microgrids with external disturbances and directed communication topologies: a full-order sliding-mode approach. IEEE/CAA J. Automatica Sinica 8 (3), 554–564. doi:10.1109/JAS.2020.1003315
Qian, T., Liu, Y., Zhang, W., Tang, W., and Shahidehpour, M. (2020). Event-triggered updating method in centralized and distributed secondary controls for islanded microgrid restoration. IEEE Trans. Smart Grid 11 (2), 1387–1395. doi:10.1109/TSG.2019.2937366
Rafique, Z., Khalid, H. M., Muyeen, S. M., and Kamwa, I. (2022). Bibliographic review on power system oscillations damping: an era of conventional grids and renewable energy integration. Renew. Energy Integr. 136, 107556. doi:10.1016/j.ijepes.2021.107556
Shen, H., Liu, Y.-A., Shi, K., Park, J. H., and Wang, J. (2023). Event-based distributed secondary control for AC islanded microgrid with semi-markov switched topology under cyber-attacks. IEEE Syst. J. 17 (2), 2927–2938. doi:10.1109/jsyst.2022.3204754
Zhai, M., Sun, Q., Wang, B., Liu, Z., and Zhang, H. (2022b). Cooperative fault-estimation-based event-triggered fault-tolerant voltage restoration in islanded AC microgrids. IEEE Trans. Automation Sci. Eng. 20, 1829–1837. doi:10.1109/TASE.2022.3186884
Zhai, M., Sun, Q., Wang, R., Wang, B., Liu, S., and Zhang, H. (2022a). Fully distributed fault-tolerant event-triggered control of microgrids under directed graphs. IEEE Netw. Sci. Eng. 9 (5), 3570–3579. doi:10.1109/tnse.2022.3176464
Zhang, Z., Baoge Zhang, B., and Wang, D. (2020). Battery/super-capacitor HESS applied in DC microgrid. Archives Electr. Eng. 69 (2), 379–388. doi:10.24425/aee.2020.133032
Zhou, J., Kim, S., Zhang, H., Sun, Q., and Han, R. (2018). Notice of removal: consensus-based distributed control for accurate reactive, harmonic, and imbalance power sharing in microgrids. IEEE Trans. Smart Grid 9 (4), 2453–2467. doi:10.1109/TSG.2016.2613143
Nomenclature
Keywords: voltage regulation control, fully distributed control, cyberattacks, distributed generation (DG), false data injection (FDI)
Citation: Liu H, Huang L, Dou Z and Wang S (2024) Campus microgrid protection: a unified approach against cyberattacks. Front. Energy Res. 12:1362412. doi: 10.3389/fenrg.2024.1362412
Received: 28 December 2023; Accepted: 30 May 2024;
Published: 19 July 2024.
Edited by:
Haris M. Khalid, University of Dubai, United Arab EmiratesReviewed by:
Xiaobo Dou, Southeast University, ChinaHoria Andrei, University Valahia of Targoviste, Romania
Copyright © 2024 Liu, Huang, Dou and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Huanan Liu, bGhubmN1QDEyNi5jb20=
†These authors have contributed equally to this work and share first authorship
 Huanan Liu
Huanan Liu Long Huang1†
Long Huang1†