- 1Qilu University of Technology (Shandong Academy of Sciences), Qingdao, China
- 2Department of Mechanical and Energy Engineering, Southern University of Science and Technology, Shenzhen, China
- 3State Grid Anhui Electric Power Company Hefei Power Supply Company, Hefei, China
The information security has an irreplaceable position in the smart grid (SG). In order to avoid the malicious attack and ensure the information security, the cryptographic techniques are essential. This paper focuses on the encryption techniques to ensure the information security of SG. Firstly, an unusual 7-dimensional complex chaotic system (7D-CCS) combined with the cubic memristor is introduced. Besides its phase portraits, Lyapunov exponent, 0–1 test, complexity, and bifurcation diagram are investigated. Then, with the proposed 7D-CCS, we design a data encryption algorithm to ensure the encryption security. Finally, the data and monitoring images in SG are encrypted by the designed encryption scheme. Besides, the encryption performance is given in detailed. The experimental results show that the proposed encryption scheme has quite good encryption performance. Therefore, it can ensure the information security of SG.
1 Introduction
The SG is a system based on communication and information technology in the generation, delivery, and consumption of energy power. It (Ferrag et al., 2018; Kimani et al., 2019) begins to involve application areas such as smart factory, traffic network and gas system (as shown in Figure 1).
The SG has great openness and interconnection, and there may be some potential problems in information collection and communication. The control of all infrastructure in SG relies on the internet. Therefore, the information security and privacy preservation in the SG is extraordinarily important (Li et al., 2022a). If the SG is maliciously attacked, the fact that data loss and tampering may happen (Li et al., 2019). It will seriously affect the normal operation of the SG, which will even lead to the consequences of system instability (Li et al., 2015; Li et al., 2022d). Then the safe and smooth operation of the SG is challenging to realize. As an example, remote data acquisition systems are usually installed in SG, which can be accessed without authorization and passwords. These devices are easily attacked or controlled by illegal users. Once the infrastructure has been maliciously controlled in unsupervised situation and it may bring huge economic losses. In addition, due to the inherent uncertainty of renewable energy (Li et al., 2022b; Li et al., 2022c), the safe operation of power systems with high-penetration renewables is facing greater challenges.
In sharp contrast to the important position of SG, the attention to its network and information security are still insufficient, which is also the reason for the frequent occurrence of power system accidents. Therefore, in the SG, designing an encryption algorithm to achieve information security is essential.
Many scholars have developed numerous researchs for the information security of SG. In May 2021, on the basis of the homomorphic encryption, Zhao et al. (2021) proposed a data aggregation and realtime electricity price billing scheme to reduce the computing cost. In July 2021, Singh et al. (2021) proposed a data aggregation model on the basis of the deep learning and homomorphic encryption. In May 2021, based on the partially homomorphic encryption (PHE), Wu et al. (2021) introduced a privacy-preserving distributed optimal power flow (OPF) algorithm. In January 2022, Hussain et al. (2021) preserved the privacy of customers by the homomorphic encryption in the SG.
Even though academics have studied excellent approaches for the information security of SG, there yet be two issues to be handled:
1) The homomorphic encryption contains a certain amount of operations, which is difficulity to be implemented.
2) For the sake of guaranteeing the information security, there exist a heavy computation burden caused by the homomorphic encryption.
Since the mid-1990s, many scholars have found that there is a close relationship between chaotic system and cryptography. A chaotic system has a series of features, such as sensitivity to the initial value, system parameters, ergodicity, unpredictability of orbit, and good pseudo-randomness. These characteristics can just meet the requirements of encryption. Therefore, chaos has been extensively applied in numerous realms, such as chaos control (Tian et al., 2021; Li et al., 2020), chaotic spread spectrum communication (Yuan et al., 2021; Xiao et al., 2018), secure communication (Zhao et al., 2020; He et al., 2020), chaos optimization (Shi et al., 2008) and so on. Besides, the application of chaos in cryptography is not difficulity to be realized. The algorithm exhibits great performances with fast encryption speed and large key space. These advantages make the algorithm suited for encrypting a lot of data. Then it extremely simplifies the design of traditional sequence cipher. Therefore, chaos has unique superiority in the realm of encryption and broad development prospects.
To address the issues as mentioned above, a data encryption algorithm combined with the chaotic sequence is introduced. Then an unusual 7D-CCS with cubic memristor is put forward to create pseudo-random sequences. The 7D-CCS has complex dynamic characteristics and can generate pseudorandom sequences with high pseudorandomness. The originality and contributions of this paper are summed up as follows.
1) The designed algorithm only includes scrambling and diffusion operation. It is easy to be implemented.
2) Based on the cubic memristor, the 7D-CCS is proposed to create pseudo-random sequences with good pseudorandomness to ensure the information security. Besides, the 7D-CCS is easy to generate key sequence.
The rest of this paper is organized as follows: In Section 2, the features of the 7D-CCS are introduced. In Section 3, design an encryption scheme. Besides, it is compared with that of others by some preformance indexes. In Section 4, the data and monitoring images in SG are processed by the proposed encryption scheme, and the security analysis are provided. Conclusions are given in Section 5.
2 The 7D-CCS with cubic memristor
The mathematical expression (Yang et al., 2019) of cubic nonlinear memristor is
where a, b are the positive constants. φ is an independent variable.
Then the derivative of memristor W(φ) is defined by
The real chaotic system with the cubic nonlinear memristor is given by
where α, β, r, d are positive constants. x, y, z are independent variables.
System 3) is extended to the complex field, where x = x1 + jx2, y = x3 + jx4, z = x5 + jx6 and φ = x7. xi(i = 1, …, 7) are independent variables. j is the imaginary number.
In system (3), the real and imaginary parts are divided. We can get:
Finally, through the chao attractor, Lyapunov exponents, bifurcation diagram, 0–1 test, and complexity analysis, we discuss the dynamic features of the system (4).
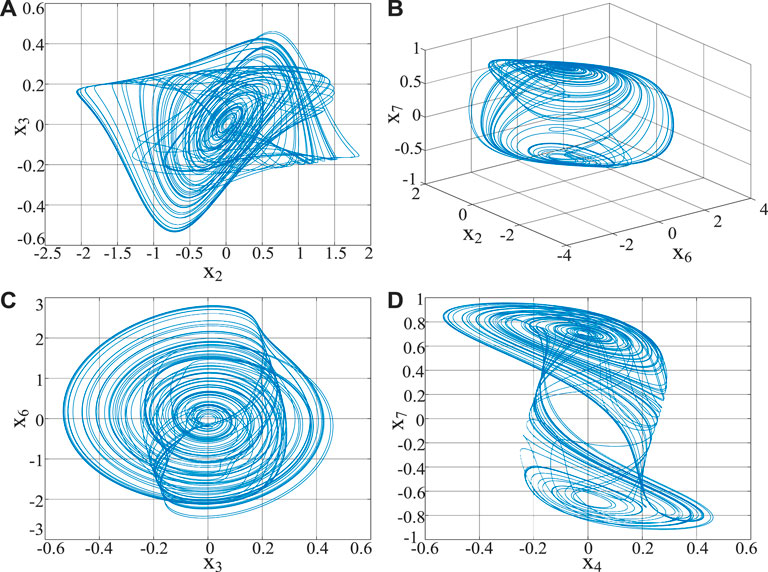
2.1 Chaos attractor
Set α = 10,
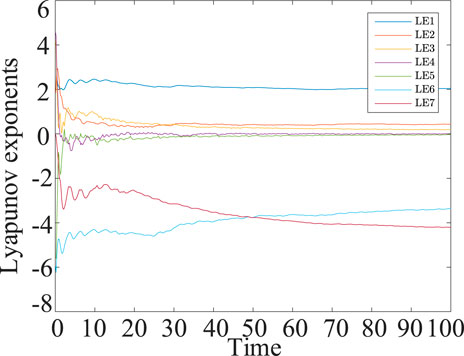
The Lyapunov exponent (Sutter et al., 2021), one of the numerical features, is used to recognize chaotic motion quantitatively. If the motion in this direction is stable, the value is negative. If the motion in this direction is unstable, the value is positive. If Lyapunov exponents include positive, negative values and zero, the system is chaotic. In the system (4), the Lyapunov exponents are LE1 = 2.041, LE2 = 0.425, LE3 = 0.189, LE4 = 0, LE5 = -0.041, LE6 = -3.355, LE7 = -4.205. The Lyapunov exponents are showed in Figure 3. The Lyapunov exponent of the 7D-CCS is (+, +, +, 0, -, -, -). Hence, the 7D-CCS is chaotic.
2.2 Bifurcation diagram of the 7D-CCS
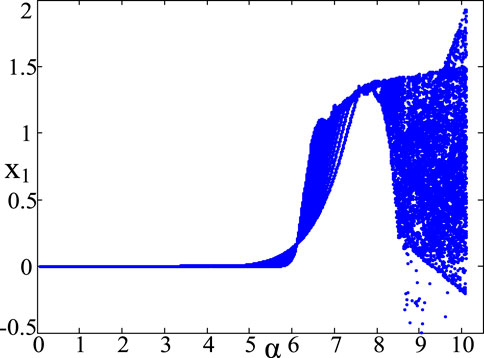
The bifurcation diagram (Marszalek and Sadecki, 2019) could distinctly show the complete process of the nonlinear system into chaos. In the bifurcation diagram, if there exist a large number of point of density caused by the infinite bifurcation, it indicates that the system is chaotic. In Figure 4, the bifurcation diagram of the 7D-CCS is shown. As shown in the Figure 4, with the change of α, the system continually forks among different states. Finally, the system 4) comes to a chaotic state.
2.3 0-1 test
The 0–1 test Karimov et al. (2021) is a method which directly calculate p(n) and q(n) to judge the state of nonlinear system. The 0–1 test method is as follows:
Step 1: Let X(k)(k = 1, 2, …, N) be a test sequence.
Step 2: Calculate the sequence p(n) and q(n):
where c ∈ (0, π).
If the trajectory diagram of p(n)-q(n) is represented by the Brownian motion, system is in a chaotic state The “0–1 test” diagram of 7D-CCS is exhibited in Figure 5. Then the Brownian motion can be seen. Hence, the system 4) is chaotic.
2.4 Complexity analysis of 7D-CCS
The SE (Yu et al., 2020) and C0 (Chen et al., 2020) algorithm, based on Fourier transform and wavelet transform, are spectral entropy algorithm until now. When the two parameters vary, the chromatogram is introduced to verify and analyze the complexity. The chromatogram of 7D-CCS is exhibited in Figure 6. The lighter the hue is, the lower the complexity is.
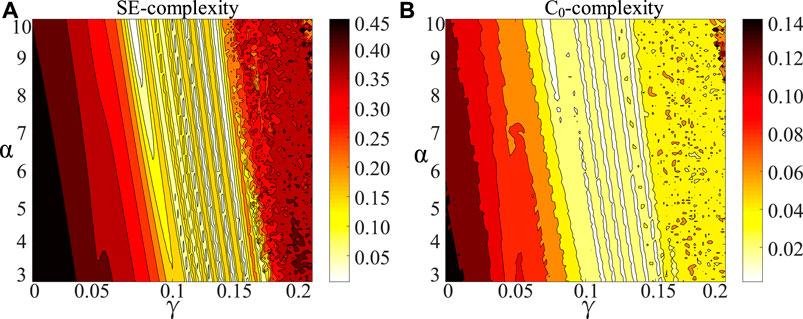
FIGURE 6. The chromatogram, (A) x1 sequence chromatogram by SE algorithm (B) x1 sequence chromatogram by C0 algorithm.
Based on these performance metrics, the nonlinear dynamic features of 7D-CCS are discussed. Set α = 10, d = 9/7, β = 100/7, r = 0.1, a = 1/7, and b = 2/7. Then the pseudo random sequences are created by the 7D-CCS. They can meet the requirements of the designed algorithm.
3 The designed algorithm and its discussion
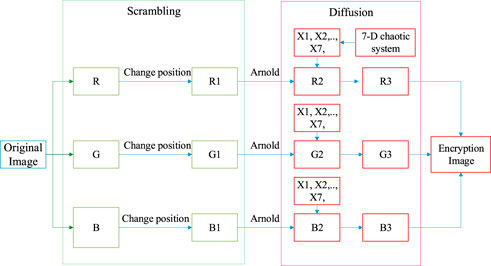
Based on the system (4), a novel data encryption algorithm is introduced. The designed algorithm is exhibited in Figure 7. The procedures of algorithm are as follows:
Step1: The experiment environment is Intel (R) Core (TM) i5-9300H CPU at 2.40GHz, and the random-access memory (RAM) adopted is 8 GB. The R, G and B channel are get by separating the image channel.
Step2: Use random function to randomly transform the position of the three primary color pixel value. Call them R1, G1 and B1.
Step3: Transform the position of the three primary color pixel value according to Arnold transform. Name them R2, G2 and B2. Arnold transform is as follows:
where M and N are the row and column of the image matrix. The pseudo-random matrices A and B with the sizes of M × N are generated from the proposed chaotic sequence. Let the coordinates of pixels in digital image be
Step4: XOR the generated seven dimensional pseudo-random sequence with R2, G2 and B2 image seven times, and the order of XOR is random.
Set α = 10,

FIGURE 8. The diagram of experimental results, (A) Standard test picture Lena (B) Scrambled picture (C) Encrypted picture (D) Decrypted picture.
3.1 Reconstruction quality analysis
The peak signal-to-noise ratio (PSNR) is introduced to investigate the visual quality of the reconstructed image. When the PSNR is greater than 30 dB but less than 40 dB, the distortion of image is small. The PSNR method is as follows:
Step 1: Calculate the mean square deviation (MSE):
Step 2: Calculate PSNR:
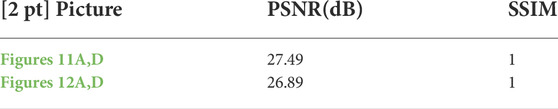
where f, g are the pixel values of original image and decrypted image. M and N represent the row and column of the image matrix, respectively. Calculate the PSNR between Figure 8A and Figure 8D and it is approximately 30 dB. The distortion of Figure 8A and Figure 8A is small.
The structural similarity (SSIM) is another quota to estimate the similarity of two images. The formula is as follows:
where ux is the mean of image X. uy is the mean of image Y. σX is the variance of image X. σY is the variance of image Y. σXY is the covariance of images X and Y. In order to avoid instability, when denominator is up to zero, C1 and C2 are two constants with small value.
The scope of SSIM is [0, 1]. When the value approaches to 1, it represents the good resemblance between the two images When the value approaches to 0, it indicates less resemblance. Calculate the SSIM between Figure 8A and Figure 8D and it is 1. The calculation results show that the structure of the Figure 8D is the same as that of the Figure 8A.
3.2 Correlation coefficient
In order to prevent the original information from being cracked through the similarity between pixels, it is very necessary to remove the correlation between adjacent pixels. Firstly, choose N pairs of pixels in the original image randomly. Then noted them as(ui, vi), i ∈ [1, N]. The formula of the correlation coefficient is shown as follows:
where E is the mean value of pixel. D is the variance of pixels. Cov is the covariance of pixels ruv is the correlation coefficient.
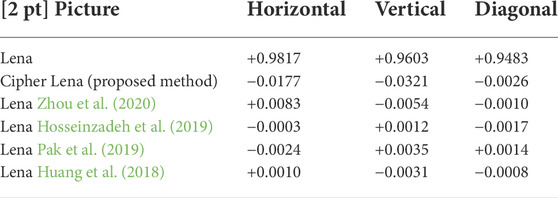
In plaintext and ciphertext images, 8,000 pairs of adjacent pixel values are haphazardly choose from the horizontal, vertical and diagonal directions. The correlation coefficient between two adjacent pixels is calculated. The value of the correlation coefficient of adjacent pixels is from -1 to 1. If the value is approach to 1, the correlation is high. Correspondingly, the adjacent pixels are basically uncorrelated if the value is close to -1. From the Table 1, we can know that the correlation coefficient of the designed algorithm is lower than that of other algorithms.
It shows that the designed algorithm can almost break the correlation between pixels.
3.3 Histogram
In digital image, the distribution of each gray level can be counted by the histogram. The Figure 9 shows that the pixel distribution of each pixel level of the three primary color matrixes. Figure 9A, Figure 9B and Figure 9C show fluctuates greatly, and the peak and trough values differ extremely. The frequency of some pixel values is large, while that of others is very small. After encryption, as shown in Figures 9D–F, the pixel distribution of each pixel level of the three primary color matrices is relatively uniform, and the value frequency of each pixel value is basically the same, which well conceals the distribution law of the original image.
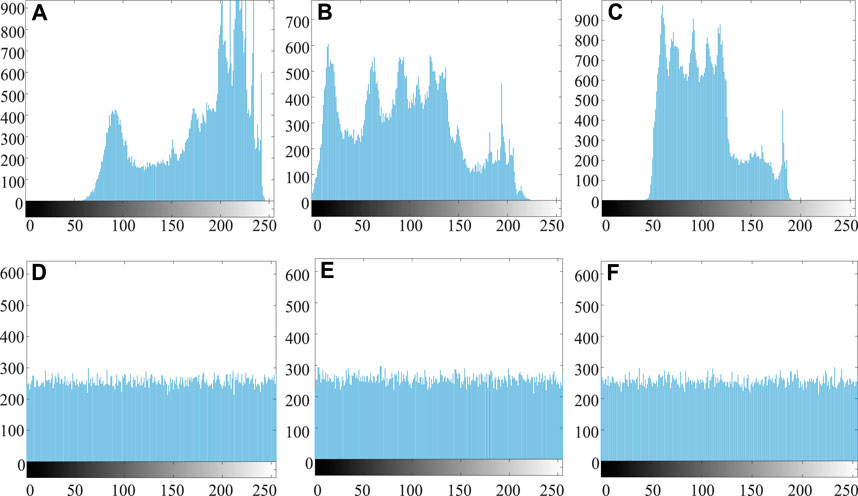
FIGURE 9. The histogram of “Lena”, (A) R channel in plain image (B) G channel in plain image (C) B channel in plain image (D) R channel in cipher image (E) G channel in cipher image (F) B channel in cipher image.
3.4 Information entropy
To the pixel values, the mean uncertainty can be reflected by the information entropy. The formula is exhibited as follows:
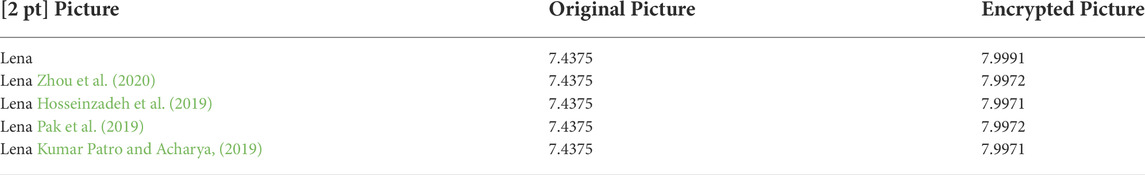
where p(xi) is the probability of gray value. The larger the image information entropy is (the maximum value is 8), the more equivalent the distribution of pixels is. The nonrandom distribution of image pixels indicates that the encryption effect is quite good. As shown in Table 2, in this algorithm, compared with other algorithms, the information entropy of encrypted image is more approach to 8. We could know that the proposed method has enough ability to withstand differential attacks.
3.5 Security key space
Assume the accuracy of the computer memory is 1015, then the size of the key space of each key is 1015. There are 7 variable values and 6 system parameter values in system 4) and the key space can reach
4 The encryption scheme of smart grid
4.1 The simulation of image encryption
In the SG, in order to confirm the operation status of the equipment, the remote data acquisition system should transmit the monitoring image to the control center. When the control center finds the equipment failure, it will shut down the equipment for maintenance.
However, in the remote data acquisition system, the monitoring images are easy to be obtained by illegal users because it do not need authorization and password. When the equipment is in normal operation, the illegal user transmits the monitoring image of equipment failure to the control center, resulting in the shutdown of the equipment. Then it will bring huge economic losses.
Therefore, in the remote data acquisition system, it is of practical significance to encrypt the monitoring image in real time, and they can be encrypted and transmitted immediately. Then the illegal user can not obtain the monitoring image.
The “Picture 1” and “Picture 2” transmitted in SG will be encrypted by using the above algorithm. The size of “Picture 1” is 660 × 783. The size of “Picture 2″ is 456 × 639. The encryption process of “Picture 1” is exhibited in Figure 10. Figure 10A is the original “Picture 1”. Figure 10B is the scrambled “Picture 1”. Figure 10C is the encrypted “Picture 1”. The characters in the original image cannot be identified directly from this image and Figure 10D is the decrypted “Picture 1”.
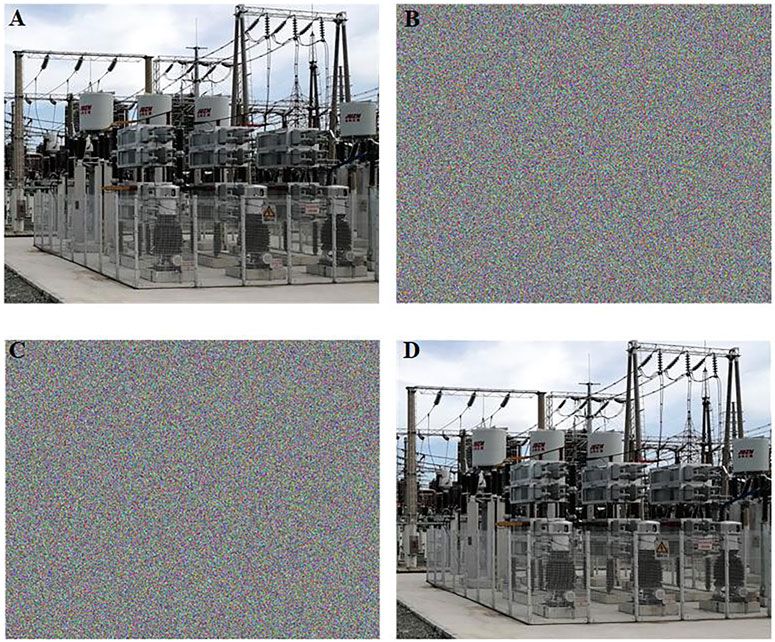
FIGURE 10. The diagram of experimental results, (A) Electronic equipment Picture 1 (B) Scrambled Picture 1 (C) Encrypted Picture 1 (D) Decrypted Picture 1.
The encryption of “picture 2” is similar to that of “picture 1”, which is shown in the Figure 11. Figure 11A is the original “Picture 2”. Figure 11B is the scrambled “Picture 2”. Figure 11C is the encrypted “Picture 2”. The characters in the original image cannot be identified directly from this image and Figure 11D is the derypted “Picture 2”.
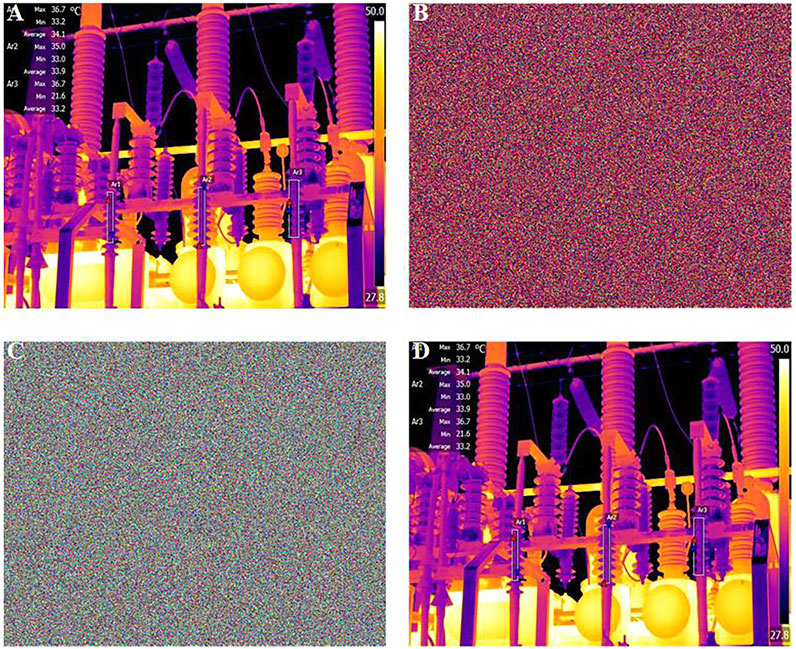
FIGURE 11. The diagram of experimental results, (A) Electronic equipment Picture 2 (B) Scrambled Picture 2 (C) Encrypted Picture 2 (D) Decrypted Picture 2.
Then the metrics mentioned in Section 3 are used to analyze them.
4.1.1 Histogram
According to the Figure 12 and Figure 13, after encryption, the pixel distribution of each pixel level of the three primary color matrices is relatively uniform.
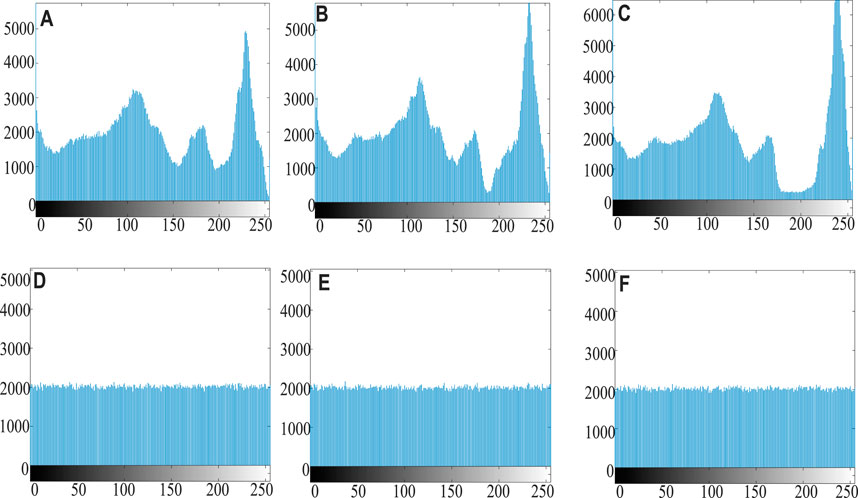
FIGURE 12. The histogram of the “picture 1”, (A) R channel in plain picture 1 (B) G channel in plain picture 1 (C) B channel in plain picture 1 (D) R channel in cipher picture 1 (E) G channel in cipher picture 1 (F) B channel in cipher picture 1.
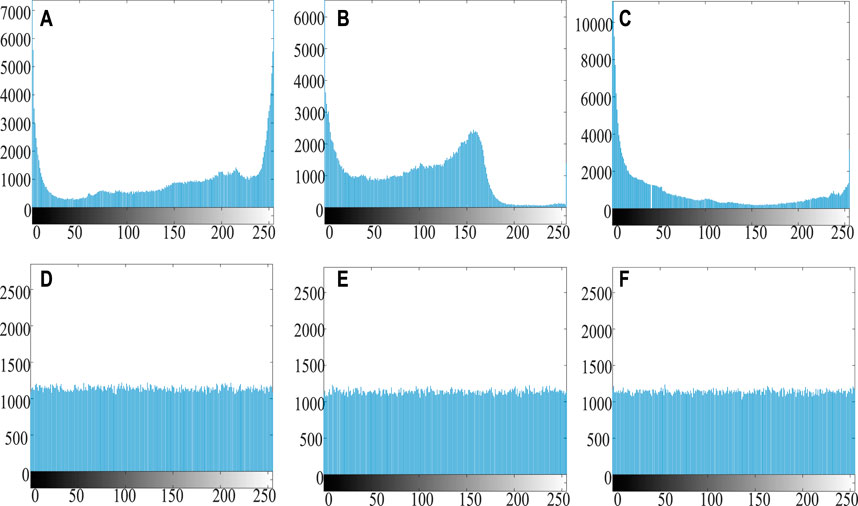
FIGURE 13. The histogram of the “picture 2”, (A) R channel in plain picture 2 (B) G channel in plain picture 2 (C) B channel in plain picture 2 (D) R channel in cipher picture 2 (E) G channel in cipher picture 2 (F) B channel in cipher picture 2
4.1.2 Correlation coefficient
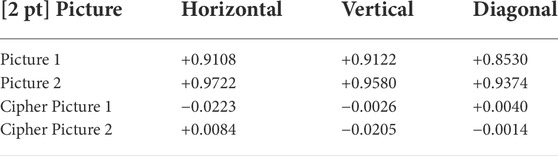
Compare the cipher image with the original image, the adjacent pixels have almost no correlation, even negative correlation. That can be known in the Table 3.
4.1.3 Information entropy
In the Table 4, the information entropy is close to 8 (max is 8). The results show that encrypted images are resistant to differential cryptanalysis.
4.1.4 Sensitivity of key
The initial conditions is (0.10001, 0.10001, 0.10001, 0.10001, 0.10001, 0.10001, 0.10001). In system (3), the value of system parameters remain unchanged. The cipher picture 1 and 2 are decrypted by the generated key which is in the above initial conditions. The Figure 14 is the decryption result of the wrong key. According to the Figure 14, with small change of key, it cannot successfully decrypt the picture 1 and 2. We could know that the proposed algorithm has great sensitivity to the key.
4.1.5 Reconstructed image quality
According to the Table 5, the quality loss of reconstructed images is relatively small. They are the same as the original images.
4.2 Data encryption
The dataset used to check the security of above algorithm is the temperature data in the SG. The Modbus Protocol is used to transmit temperature data. In the Modbus protocol, the data is as follows:0x13 0x04 0x00 0x00 0x00 0x01 0x32 0xB8
Where is 8 bytes and hexadecimal.
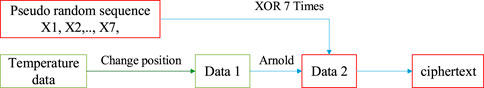
The flow chart of data encryption algorithm is shown in Figure 15. The steps are as follows.
Step1: Use random function to randomly change the position of the temperature data. Name it Data 1.
Step2: Change the position of Data 1 according to Arnold transform. Name it Data 2.
Step3: XOR the generated seven dimensional pseudo-random sequence with Data 2 seven times, and the order of XOR is random.
The ciphertext data composition is as follows: 0xFC 0xCF 0xFC 0xFC 0xFC 0xFC 0xF8 0xF8 where is 8 bytes and hexadecimal.
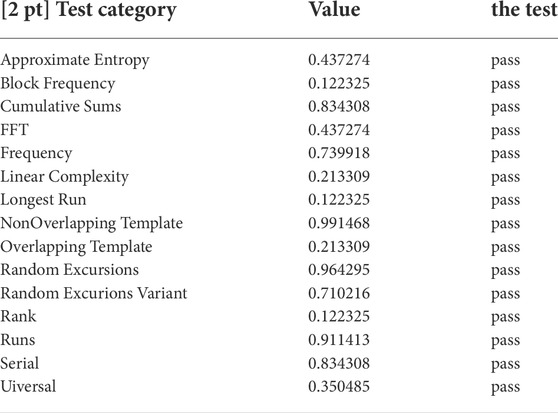
After decryption, the data composition is the same as the initial data. The security of cipher text mainly depends on whether the key is random. If the key is random and variable, the security of ciphertext can be guaranteed. Next, from the NIST test to analyze the randomness of the key.
The NIST statistical test suit is composed of 15 statistical tests, which can detect the randomness of the sequences created by the 7D-CCS. Generally speaking, the statistical test is successful when the test result is between 0.01 and 1. Bsides, the test sequence has excellent randomness if the value is large. For simplicity, 20, 000, 000 real numbers, created by the 7D-CCS, are adopted as the test data in the NIST test. The NIST test results are shown in Table 6, which are between 0.01 and 1. It means that the statistical tests are successful. Then it also verified that the key has quite good randomness.
5 Conclusions
Based on the 7D-CCS, a data process scheme is introduced. First of all, the 7D-CCS with memristor is proposed, which is derived from the real 4D chaotic system with the cubic nonlinear memristor. Secondly, the dynamic characteristics are analyzed by some performance indexs. Thirdly, the standard test image Lena is selected as encrypted object. Then compare it with others. Finally, the temperature data and monitoring images are encrypted in the verification experiments.
Simulations include PSNR, SSIM, histogram analysis, information entropy analysis, correlation analysis, sensitivity of key analysis, key space analysis and NIST test.
The experimental results indicate that the designed algorithm has excellent security performance. Therefore, the designed algorithm is suitable for SG in which the high security is required.
Besides, there are many tasks needed to be further studied.
1) At present, only the security of the designed algorithm is analyzed. The field experiments need to be carried out.
2) In the research of SG, the efficiency of data encryption is also critical. The encryption time should be considered in the future research work.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding authors.
Author contributions
Conceptualization, LK and ZH; methodology, LK, ZH, and CJ; software, ZH; validation, ZH and CJ; formal analysis, FZ and ZH; investigation, HuL and HaL; resources, WK and JL; data curation, WK and JW.
Funding
This work is funded by Major scientific and technological innovation projects of Shandong Province (Nos. 2019JZZY010731 and 2020CXGC010901), the project of “Youth Innovation and technology support plan” for colleges and universities in Shandong Province (2021KJ025), International Collaborative Research Project of Qilu University of Technology (No. QLUTGJHZ2018020).
Conflict of interest
JL is employed by the Company State Grid Anhui Electric Power Company Hefei Power Supply Company.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Chen, H., He, S., Pano Azucena, A. D., Yousefpour, A., Jahanshahi, H., López, M. A., et al. (2020). A multistable chaotic jerk system with coexisting and hidden attractors: Dynamical and complexity analysis, fpga-based realization, and chaos stabilization using a robust controller. Symmetry 12, 569. doi:10.3390/sym12040569
Ferrag, M. A., Maglaras, L. A., Janicke, H., Jiang, J., and Shu, L. (2018). A systematic review of data protection and privacy preservation schemes for smart grid communications. Sustain. Cities Soc. 38, 806–835. doi:10.1016/j.scs.2017.12.041
He, W., Luo, T., Tang, Y., Du, W., Tian, Y.-C., and Qian, F. (2020). Secure communication based on quantized synchronization of chaotic neural networks under an event-triggered strategy. IEEE Trans. Neural Netw. Learn. Syst. 31, 3334–3345. doi:10.1109/TNNLS.2019.2943548
Hosseinzadeh, R., Zarebnia, M., and Parvaz, R. (2019). Hybrid image encryption algorithm based on 3d chaotic system and choquet fuzzy integral. Opt. Laser Technol. 120, 105698. doi:10.1016/j.optlastec.2019.105698
Huang, L., Cai, S., Xiong, X., and Xiao, M. (2018). On symmetric color image encryption system with permutation-diffusion simultaneous operation. Opt. Lasers Eng. 115, 7–20. doi:10.1016/j.optlaseng.2018.11.015
Hussain, I., Samara, G., Ullah, I., and Khan, N. (2021). “Encryption for end-user privacy: A cyber-secure smart energy management system,” in 2021 22nd International Arab Conference on Information Technology (ACIT), 1. doi:10.1109/ACIT53391.2021.9677341
Karimov, T. I., Druzhina, O. S., Karimov, A. I., Kolev, G. Y., and Butusov, D. N. (2021). “Comparison of bifurcation diagrams for numerical and analog chaotic systems,” in 2021 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), 124. doi:10.1109/ElConRus51938.2021.9396558
Kimani, K., Oduol, V., and Langat, K. (2019). Cyber security challenges for iot-based smart grid networks. Int. J. Crit. Infrastructure Prot. 25, 36–49. doi:10.1016/j.ijcip.2019.01.001
Kumar Patro, K. A., and Acharya, B. (2019). An efficient colour image encryption scheme based on 1-d chaotic maps. J. Inf. Secur. Appl. 46, 23–41. doi:10.1016/j.jisa.2019.02.006
Li, G., Wang, Z., Han, Z., and Bai, X. (2015). A multifeature fusion approach for power system transient stability assessment using pmu data. Math. Problems Eng., 1–10. doi:10.1155/2015/786396
Li, Y., Li, J., and Wang, Y. (2022a). Privacy-preserving spatiotemporal scenario generation of renewable energies: A federated deep generative learning approach. IEEE Trans. Ind. Inf. 18, 2310–2320. doi:10.1109/TII.2021.3098259
Li, Y., Li, K., Yang, Z., Yu, Y., Xu, R., and Yang, M. (2022b). Stochastic optimal scheduling of demand response-enabled microgrids with renewable generations: An analytical-heuristic approach. J. Clean. Prod. 330, 129840. doi:10.1016/j.jclepro.2021.129840
Li, Y., Wang, B., Yang, Z., Li, J., and Li, G. (2022c). Optimal scheduling of integrated demand response-enabled community-integrated energy systems in uncertain environments. IEEE Trans. Ind. Appl. 58, 2640–2651. doi:10.1109/TIA.2021.3106573
Li, Y., Zhang, M., and Chen, C. (2022d). A deep-learning intelligent system incorporating data augmentation for short-term voltage stability assessment of power systems. Appl. Energy 308, 118347. doi:10.1016/j.apenergy.2021.118347
Li, Y., Li, Z., and Chen, L. (2019). Dynamic state estimation of generators under cyber attacks. IEEE Access 7, 125253–125267. doi:10.1109/ACCESS.2019.2939055
Li, Z., Yuan, Y., and Wang, H.-N. (2020). “Fuzzy adaptive time-delay feedback controlling chaos in buck converter,” in 2020 Chinese Control And Decision Conference (CCDC), 4732–4737. doi:10.1109/CCDC49329.2020.9164013
Marszalek, W., and Sadecki, J. (2019). Complex two-parameter bifurcation diagrams of a simple oscillating circuit. IEEE Trans. Circuits Syst. Ii. 66, 687–691. doi:10.1109/TCSII.2018.2871063
Pak, C., An, K., Jang, P., Kim, J., and Kim, S. (2019). A novel bit-level color image encryption using improved 1d chaotic map. Multimed. Tools Appl. 78, 12027–12042. doi:10.1007/s11042-018-6739-1
Shi, Z.-B., Yu, T., Zhao, Q., Li, Y., and bin Lan, Y. (2008). Comparison of algorithms for an electronic nose in identifying liquors. J. Bionic Eng. 5, 253–257. doi:10.1016/S1672-6529(08)60032-3
Singh, P., Masud, M., Hossain, M. S., and Kaur, A. (2021). Blockchain and homomorphic encryption-based privacy-preserving data aggregation model in smart grid. Comput. Electr. Eng. 93, 107209. doi:10.1016/j.compeleceng.2021.107209
Sutter, D., Fawzi, O., and Renner, R. (2021). Bounds on lyapunov exponents via entropy accumulation. IEEE Trans. Inf. Theory 67, 10–24. doi:10.1109/TIT.2020.3026959
Tian, K., Grebogi, C., and Ren, H.-P. (2021). Chaos generation with impulse control: Application to non-chaotic systems and circuit design. IEEE Trans. Circuits Syst. I. 68, 3012–3022. doi:10.1109/TCSI.2021.3075550
Wu, T., Zhao, C., and Zhang, Y.-J. A. (2021). Privacy-preserving distributed optimal power flow with partially homomorphic encryption. IEEE Trans. Smart Grid 12, 4506–4521. doi:10.1109/TSG.2021.3084934
Xiao, L., Xuan, G., and Wu, Y. (2018). “Research on an improved chaotic spread spectrum sequence,” in 2018 IEEE 3rd International Conference on Cloud Computing and Big Data Analysis (ICCCBDA), 420–423. doi:10.1109/ICCCBDA.2018.8386553
Yang, N., Xu, C., Wu, C., Jia, R., and Liu, C. (2019). Fractional-order cubic nonlinear flux-controlled memristor: Theoretical analysis, numerical calculation and circuit simulation. Nonlinear Dyn. 97, 33–44. doi:10.1007/s11071-019-04920-y
Yu, F., Liu, L., Shen, H., Zhang, Z., Huang, Y., Shi, C., et al. (2020). Dynamic analysis, circuit design, and synchronization of a novel 6d memristive four-wing hyperchaotic system with multiple coexisting attractors. Complexity, 1–17. doi:10.1155/2020/5904607
Yuan, G., Chen, Z., Gao, X., and Zhang, Y. (2021). Enhancing the security of chaotic direct sequence spread spectrum communication through wfrft. IEEE Commun. Lett. 25, 2834–2838. doi:10.1109/LCOMM.2021.3096388
Zhao, Y., Yang, Q., Li, D., and An, D. (2021). “A data aggregation and real-time electricity billing scheme based on homomorphic encryption in smart grid,” in 2021 33rd Chinese Control and Decision Conference (CCDC), 2545–2550. doi:10.1109/CCDC52312.2021.9601443
Zhao, Y., Zhang, W., Su, H., and Yang, J. (2020). Observer-based synchronization of chaotic systems satisfying incremental quadratic constraints and its application in secure communication. IEEE Trans. Syst. Man. Cybern. Syst. 50, 5221–5232. doi:10.1109/TSMC.2018.2868482
Keywords: smart grid, chaotic system, data encryption, memristor, information security
Citation: Kou L, Huang Z, Jiang C, Zhang F, Ke W, Wan J, Liu H, Li H and Lu J (2022) Data encryption based on 7D complex chaotic system with cubic memristor for smart grid. Front. Energy Res. 10:980863. doi: 10.3389/fenrg.2022.980863
Received: 29 June 2022; Accepted: 22 July 2022;
Published: 12 September 2022.
Edited by:
Dan Lu, Alfred University, United StatesReviewed by:
Guoliang Ye, Dongguan University of Technology, ChinaJiyu Cheng, Shandong University, China
Xinmiao Ding, Shandong Institute of Business and Technology, China
Copyright © 2022 Kou, Huang, Jiang, Zhang, Ke, Wan, Liu, Li and Lu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Cuimei Jiang, SmlhbmdjdWltZWkyMDA0QDE2My5jb20=; Fangfang Zhang, emhmZjR1QDE2My5jb20=
 Lei Kou
Lei Kou Zhe Huang1
Zhe Huang1 Wende Ke
Wende Ke