- 1Southeast University, Nanjing, China
- 2State Grid Jiangsu Electric Power Co., Ltd., Nanjing, China
- 3NARI Group Corporation, Nanjing, China
“Eventization” of power grid monitoring is an effective way to deal with massive alarm information. The existing event recognition method adopts the method of text information mining, and the overall recognition accuracy is not high. Therefore, this paper proposes a power grid monitoring event recognition method integrating knowledge graph and deep learning. First, the method constructs the knowledge graph of monitoring equipment and uses the improved GraphSAGE (graph sample and aggregate) algorithm to perform representation learning on the graph, and integrate the structural characteristics of monitoring equipment into the generated alarm vectors. Then, the GRU (Gated Recurrent Unit) neural network trains the alarm vectors and related events. In addition, this paper combines the proposed method with the existing monitoring expert system, and puts forward a monitoring event recognition strategy. Finally, through the case analysis and comparison of the actual data of the power grid, the effectiveness of the proposed method and strategy is verified, which further improves the accuracy of monitoring event recognition.
1 Introduction
With massive distributed resources connected to the power grid, the alarm information increases daily. The traditional signal-oriented monitoring method is easy to cause a large amount of alarm information to be accumulated in the alarm window, which brings enormous pressure to the monitoring personnel, resulting in missed judgments and misjudgments (Sun et al., 2019; Huang et al., 2021). In order to improve the processing efficiency of alarm information, the power grid dispatching department actively promotes the “eventization” of alarm information. First, the alarm information received by the system is divided according to topological location and time. Second, the divided alarms are summarized into monitoring events according to their triggering rules. On the one hand, it overcomes the dimensional disaster caused by massive alarm information. On the other hand, it converts the alarm information state which is difficult to accurately observe or estimate into easily observable monitoring events (Xia, Jia and Cao, 2014; Farhadi and Mohammed, 2015). Therefore, it is of tremendous research significance to develop effective monitoring event recognition methods to mine the connection between alarm information and power grid events.
Some scholars try to use computers to store the knowledge and experience provided by experts, carry out reasoning and judgment, and simulate the decision-making process of human experts. For example, Minakawa et al. (1995) summarized a series of rules for alarm information to build a rule expert system to analyze massive alarm information. On this basis, Wei et al. (2011) and Mu et al. (2012) integrated technologies such as multi-threading and abductive reasoning network (ARN) to form an online intelligent alarm processing system. However, the improved expert system still needs to be refined and maintained manually. The rules covered are limited, and only events that conform to the established rules can be identified. In the face of events that exceed the rules, such as the absence of alarm signals and false alarms, the expert system fails to make correct judgments.
In order to further improve the automation level of event recognition, event recognition methods based on text information mining have received extensive attention and research by scholars at home and abroad. This method uses natural language processing technology to convert the semantics in the text into digital information that computers can use. By learning the internal logic of alarms and events, the corresponding events can be inferred directly from alarms. Bai et al. (2019) and Pandey et al. (2020) used the text representation learning model Word2vec (Church, 2017) to vectorize the monitoring alarm information. Then, the recognition of monitoring events was successfully realized using neural networks to mine the logical correlation between alarms and events. However, the event recognition method based on text information mining only learns the features of the text-level. It lacks the feature learning of the equipment topology structure on the alarm content, which affects the overall recognition accuracy.
Therefore, this paper proposes a grid monitoring event recognition method that integrates knowledge graph (Pujara et al., 2013; Chen, Jia and Xiang 2020) and deep learning. By constructing a monitoring equipment knowledge graph and learning the representation of the graph, the topological structure features between the equipment are integrated into the generated alarm vectors. Then the alarm information and the corresponding monitoring events are trained through the neural network. In addition, this paper also combines this method with an expert system to generate a monitoring event recognition strategy.
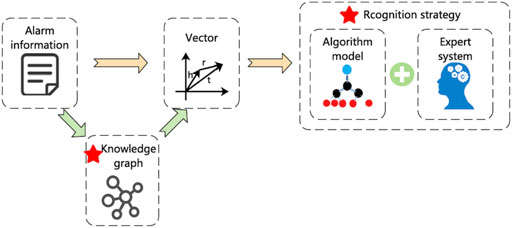
The main contribution of this paper is shown in Figure 1, including:
1) A vectorized model of alarm content based on knowledge graph and GraphSAGE is proposed. Using the knowledge graph instead of text as the representation learning object increases the learning of the topological structure features of the monitoring equipment and overcomes the shortcomings of the limited features learned by the text information mining method.
2) Considering the temporal characteristic between alarm information, it is proposed to use GRU neural network to train alarm information and events. Based on the GRU network, a dropout layer and a fully connected layer are added to further improve the classification effect of the model.
3) Combine the event recognition method proposed in this paper with the monitoring expert system to form an event recognition strategy. On the one hand, compared with the expert system, it broadens the scope of event recognition. On the other hand, because the expert system pre-filters the alarm information that meets the rules, the scope of event recognition is narrowed, and the false recognition rate is further reduced.
The content of this paper is arranged as follows: Chapter 2 proposes a vectorized model of monitoring alarm content based on knowledge graph and GraphSAGE. Chapter 3 uses GRU neural network to identify monitoring events based on the improved vectorized model. Chapter 4 proposes a recognition strategy that combines expert systems with event recognition methods. Chapter 5 analyzes and compares cases to verify the effectiveness of the proposed method and strategy. Chapter 6 concludes this article, and gives limitations and future perspectives of event recognition method.
2 Vectorized Model of Monitoring Alarm Content Based on Knowledge Graph and GraphSAGE
Massive alarm information provides the computer with a rich corpus. In order to enable the computer to understand the deep semantics contained in text information, monitoring alarm information must be converted into digital information.
The alarm information studied in this paper is generated by Supervisory Control and Data Acquisition (SCADA) system, which includes the following three parts:
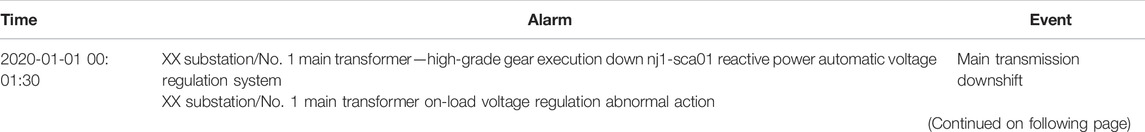
In the formula: S is the alarm information derived by the system, T is the alarm occurrence time, D is the alarm content, and A is the action state. For example, select an alarm message for analysis: “2020-05-01 00:00:24//XX Substation No. 4 Main Transformer No. 1 Capacitor 343 Switch//Open”.
It can be seen from formula 1 that the alarm is mainly composed of (alarm time, alarm content, action state), and the essence of the alarm content is the information of the equipment that triggers the alarm.
The traditional method of vectorizing alarm information is to use Word2vec to segment the text, then map each word to the vector space to obtain a word vector, and finally combine word vectors to obtain a text vector, and finally slice the word vector to obtain a text vector, as shown in Figure 2A.
1) Chinese word segmentation: The professional power words are imported into the thesaurus to form a power dictionary, and the alarm information is segmented by the jieba word segmentation tool (Day and Lee, 2016).
2) Vectorized modeling: The Word2vec model performs unsupervised training on monitoring alarm information to generate high-dimensional word vectors containing semantic features.
3) Neural network training: The generated word vectors are spliced into a complete alarm vector which is input into the neural network for training to obtain the mapping relationship between alarms and events.
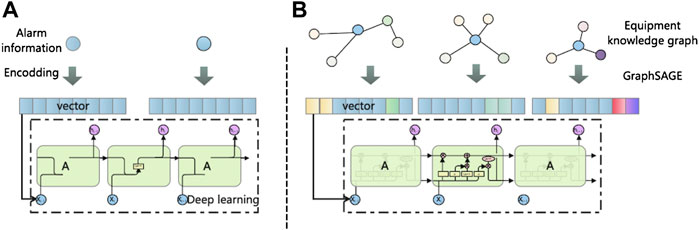
FIGURE 2. Vectorized model comparison. (A) is a text vectorization model, and (B) adds structural vectorization.
The alarm information can be vectorized by this method. However, the vector obtained by this method only involves the information at the text-level and does not consider the structural correlation existing in the alarm content. This structural association is embodied in the topological connection between monitoring equipment.
Therefore, this paper proposes a vectorized model of monitoring alarm content based on knowledge graph and GraphSAGE. For the vectorized processing of D (alarm content), constructing an equipment knowledge graph and then performing representation learning on the graph can replace the traditional direct vectorization of text. This method increases the learning of equipment structure information so that the output vector contains more features, as shown in Figure 2B.
1) Build an equipment knowledge graph: According to the existing power grid equipment model, the equipment information and topology are stored in the graph through knowledge graph technology.
2) Vectorized modeling: The equipment graph is learned by graph representation through the GraphSAGE model, and high-dimensional word vectors containing equipment text features and connection features are generated.
3) Neural network training: The alarm vector incorporating structural information is input into the neural network for training to achieve end-to-end mapping.
To make the equipment graph clearly indicate the attributes and relationships of each equipment, the nodes, attributes, and relationships in the graph are set as follows:
1) Node: Take various primary or secondary equipment entities in the equipment database as nodes in the graph, such as “generator”, “transformer”, “knife switch”, etc.
2) Attribute: The intrinsic characteristics of conceptual entities are used as node attributes, such as transformer type and transformer voltage are intrinsic characteristics of transformer, which can be used as attribute values of the “transformer” node.
3) Relationship: The nodes in the graph are connected according to the actual association of the entities, corresponding to the connection of different types of equipment.
After the equipment information is stored through the knowledge graph, it is necessary to perform graph representation learning on the graph to generate the vector of the equipment. Considering that the GraphSAGE graph representation learning algorithm can learn the characteristics of neighbor nodes and avoid the problem of GCN memory explosion (Kipf and Welling, 2016; Oh, Cho and Bruna, 2019). This paper uses GraphSAGE for vectorized learning of the equipment knowledge graph. However, since the connection conditions between equipment are not similar, the same equipment will have different connection conditions, resulting in the final learned vector not being unique. That is, the same equipment may learn multiple vector results. In response to this problem, this paper improves the GraphSAGE model, adds a weighted aggregation link at the end of the original model, and uses Algorithm 1 to unify the different vector representations of the same node, where n represents the number of possible vector representations for a node.
Algorithm 1. Consensus Algorithm.
The input of the consensus algorithm is divided into two parts, one part is the vector set V of the same node, and the other part is the set N that counts the occurrences of each vector. The unique vector V* of each node is obtained by adding the weighted average of each sub-vector.
3 Monitoring Event Recognition Method
Based on the improved vectorized model, this paper integrates the structural information between monitoring equipment into the vectorized representation of the alarm content. Since the grid alarm information occurs continuously within a period, it has a time sequence relationship. The GRU network can effectively train the temporal variation of alarm information (Shewalkar, 2019), so this paper builds a GRU-based neural network to identify monitoring events. The complete monitoring event recognition process is shown in Figure 3.
1) Extract the labeled alarm samples from the historical data, in which the alarm information is used as the sample, and the event corresponding to the alarm is the label.
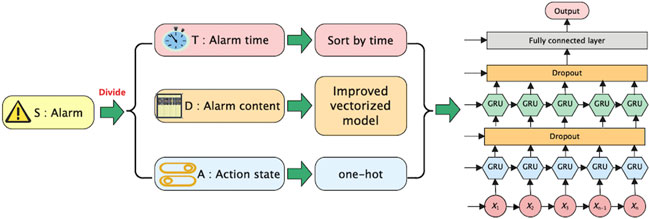
2) To perform vectorization processing on the alarm information, as can be seen from the above, it is only necessary to perform vectorization processing on T (alarm time), D (alarm content), and A (action state). First, since the “alarm time” set represents the sequence of alarm occurrences, this paper arranges the alarm information chronologically, using the structural sequence avoids the vectorized representation of the “alarm time” set. Second, the “alarm content” set and the “action state” set are vectorized as shown in Figure 4. The specific quantization process is shown in steps 3–5.
3) The equipment knowledge graph is built from top to bottom. Firstly, the primary or secondary equipment entities, the connection relationship between entities and the attributes of entities are obtained from the power grid monitoring database by means of knowledge extraction (Fan et al., 2012). Because there are many databases in the power grid and different database naming methods are different, it is necessary to adopt the method of knowledge fusion (Dong et al., 2015) to unify and standardize the extracted data. Finally, the normalized data is imported into the graph database (Webber, 2012) in the form of triples for visualization.
4) Through the improved GraphSAGE algorithm, the equipment knowledge graph is learned to obtain the unique vectorization result of each equipment, that is, the “alarm content” vector. The one-hot encoding method (El Affendi and Al Rajhi, 2018) is adopted for a limited set of “action state,” and M-bit vectors encode M actions. Then the “alarm content” vector and the “action state” vector are concatenated to obtain a vector representation of an alarm.
5) Since one monitoring event corresponds to multiple alarms, the alarms under the same monitoring event are combined into a chronological order matrix as input of neural network.
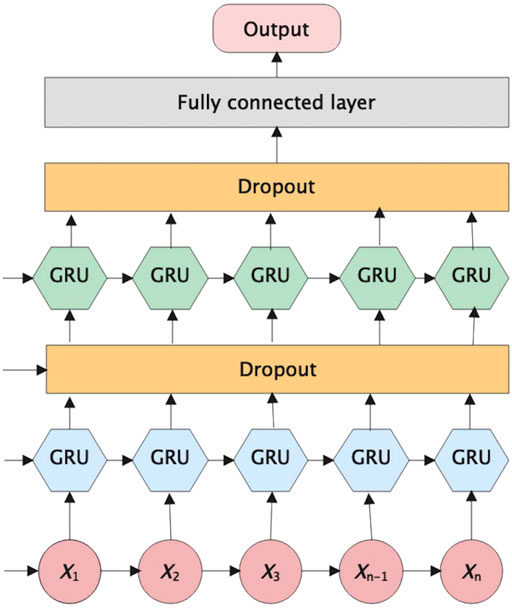
6) Build a GRU-based neural network to train the alarm vector, and the network architecture is shown in Figure 5.
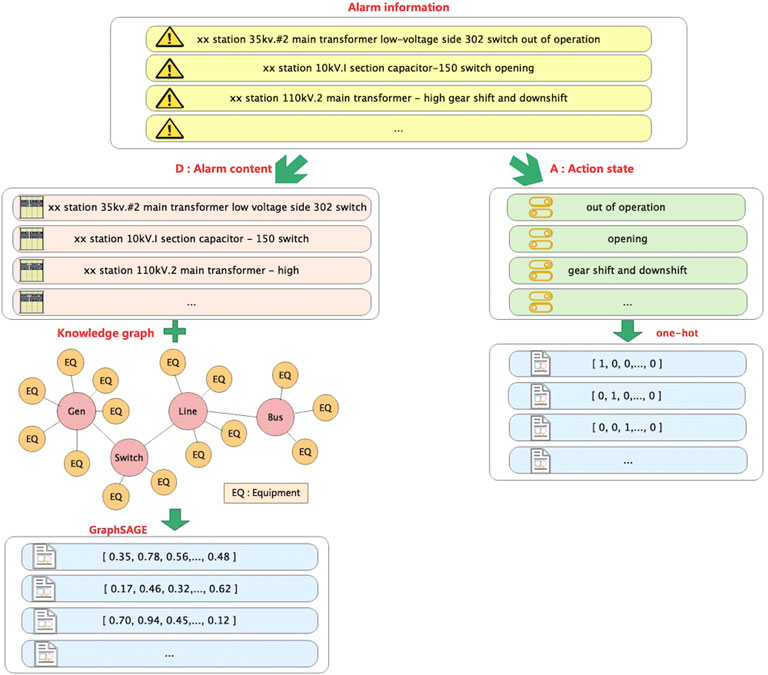
FIGURE 4. Vectorization model of monitoring alarm information based on knowledge graph and GraphSAGE.
Aiming at the problem that GRU is prone to overfitting, this paper introduces a Dropout layer into the network, which randomly discards some neurons during the training process, reduces the coupling between neurons, and improves the generalization ability of the network.
In order to better learn the internal relationship between the alarm vectors and improve the fitting degree of the network, this paper designs a two-layer GRU network. By changing the output of the first layer of GRU network, the original output of returning to the last time step is changed to return the whole time step, and then it is input to the second layer of GRU network after passing through the dropout layer.
The fully connected layer (Dense) belongs to the feature learning layer, which can change the features extracted by the network nonlinearly and improve the learning generalization ability of the network model. Finally, the output of the network is mapped to the (0,1) interval through the softmax classifier to classify and identify the alarm.
4 Monitoring Event Recognition Strategy
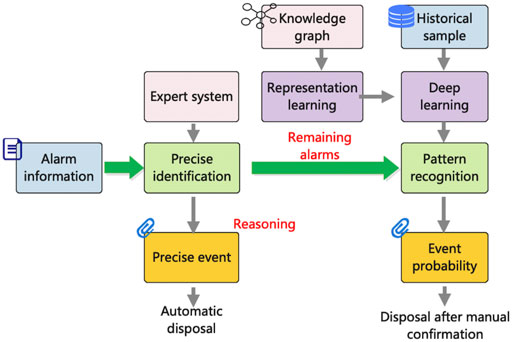
The core of the existing comprehensive intelligent alarm system is the event discrimination method based on the expert system. However, its fixed and strict knowledge structure can only judge and identify the events that meet the established rules. When the alarm information is missing or wrong, misjudgment will occur. The above-mentioned data-driven event recognition method has strong robustness and learning ability. Therefore, this paper proposes an event recognition strategy that combines traditional expert-system methods and event recognition methods, as shown in Figure 6. On the one hand, compared with a single expert system, the recognition strategy broadens the scope of event recognition; on the other hand, compared with the above event recognition method, the expert system narrows the scope of event recognition to reduce the false recognition rate.
The recognition strategy consists of two parts. One is the traditional monitoring expert system, which can accurately identify the alarm data through the expert system and automatically process the alarm data that conforms to the rules. The other part uses the data-driven monitoring event recognition method to identify the remaining alarms filtered by the expert system, output the possible events and their probability, and finally test the events with high probability manually.
5 Case Analysis
In this paper, the alarms and related events of a substation in Jiangsu Province in 2020 are primary data to identify monitoring events. There are 9586 alarm signals corresponding to 2480 events and 11 event types. Table 1 lists the corresponding situations of some alarms and events. The number of samples included in each event type is shown in Table 2.
Firstly, the equipment knowledge graph of the substation was constructed, and then the alarm information were divided according to formula 1, a total of 20 different action states were obtained, and a 20-dimensional vector was obtained by one-hot encoding. Secondly, according to the alarm information vectorization process in Chapter 3, the alarm information was represented by vectors. Thirdly, the alarm vectors and the corresponding event labels were put into the neural network for training. The number of neurons in the two-layer GRU network was set to 32 and 64, respectively, the random loss ratio of the Dropout layer was set to 0.2, and the number of neurons of the Dense layer was set to 128. The ratio of training set and test set was set to 8:2, and 300 epochs were trained.
In order to verify the superiority of the above models, this paper conducted three sets of comparative experiments, including 1) Case 1: The comparison between the traditional text vectorization model and the vectorization model based on knowledge graph and GraphSAGE, 2) Case 2: The comparison between other algorithm models such as CNN and the GRU-based recognition model built in this paper, 3) Case 3: The comparison between event recognition method and recognition strategy proposed in this paper.
The experiment adopted the recognition accuracy Ac as the evaluation index of event recognition. The confusion matrix is shown in Table 3. lTP, lFN, lFP, and lTN are the number of TP, FN, FP, and TN events, respectively.
5.1 Case 1
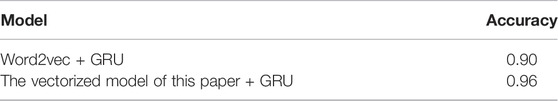
In order to verify the superiority of the vectorization model proposed in this paper, the experiment used the traditional text vectorization model and the vectorization model based on knowledge graph and GraphSAGE to generate 20 dimensional device vectors respectively, and the 20-dimensional action vectors were generated by means of one-hot encoding, and finally input them into the GRU neural network for training.
The comparison experiment was carried out with the accuracy rate Ac as the evaluation standard. The experimental results are shown in Table 4 (the data in the table are the weighted results of the accuracy rates of various events).
From the results in Table 4, It can be seen from the results that the accuracy of event recognition using the vectorization model constructed in this paper is significantly higher than that using word2vec text vectorization model, reaching 96% of the recognition accuracy. This shows that increasing the vectorized learning on the structure of alarm information and integrating the connection characteristics of monitoring equipment is helpful for the recognition of monitoring events.
5.2 Case 2
In order to verify the applicability of the classification and recognition model based on the GRU neural network built in this paper, the experiment used CNN, SVM, random forest, and the model in this paper to conduct comparative experiments, and the accuracy Ac was used as the evaluation standard. The experimental results are shown in Table 5.
From the experimental comparison of the classification and recognition models in Table 5, it can be concluded that:
1) The recognition accuracy of the neural network model constructed in this paper is higher than that of the traditional machine learning model.
2) After using Dropout, the performance of the model is improved. This shows that Dropout can effectively suppress overfitting and improve the model’s generalization ability.
3) After adding the fully connected layer, the model’s accuracy is further improved, which shows that the use of the fully connected layer can improve the fitting ability of the model.
5.3 Case 3
In order to verify the effectiveness of the recognition strategy, the experiment set up two sets of comparative experiments, one is the comparison of the expert system and the recognition strategy, and the other is the comparison of the event recognition method and the recognition strategy.
5.3.1 Expert System and Recognition Strategy
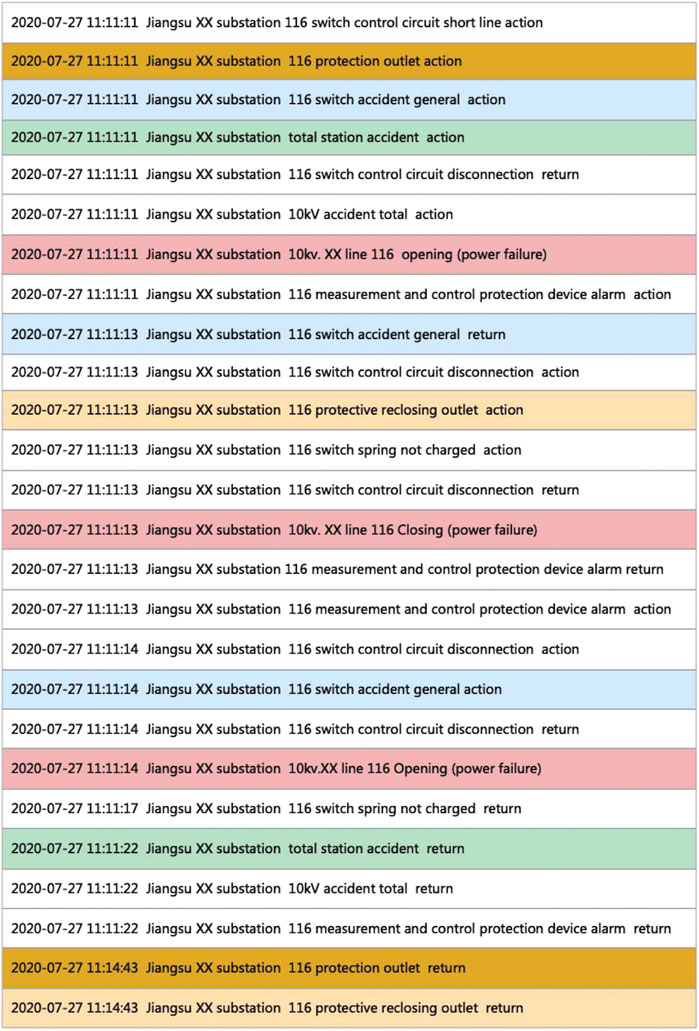
The experiment selected a set of alarm data from the experimental data as shown in Figure 7, including a total of 26 alarms, of which the alarms marked in red are the line switch signal alarms, namely “open”, “close” and “open” signal, yellow is the signal of “recloser exit”, green is the signal of “return of action of total accident signal”, dark yellow is the signal of “return of action of protection exit”. This group of alarms meet the rule definition of “permanent fault of line below 35 kV”, both the expert system and recognition strategy could perform accurate recognition.
Assuming that the “close” signal of the switch was lost, the “open-open” of the switch signal could not meet the rule definition of “permanent fault of the line below 35 kV”. According to the existing rules, the expert system would split this alarm event into two line-trip events, which was not as expected. Accurate recognition was still possible through the recognition strategy.
Assuming that the opening and closing signals of switch were out of sequence, swap the switch’s “open” signal and the switch’s “close” signal. At this time, the “close-open-open” of the switch signal could not meet the rule definition of “permanent fault of the line below 35 kV”. According to the existing rules, the expert system would split this alarm event into three line-trip events which did not meet the expectations. However, the recognition strategy could still identify accurately.
Through the above comparison with the expert system, it can be found that the recognition strategy can not only identify the signals that meet the rules but also identify the lack of signals or the disorder of the signals by adding the data-driven event recognition method, thus broadening the scope of expert system.
5.3.2 Event Recognition Method and Recognition Strategy
The event recognition method is data-driven, training and learning on historical data with labels and gives event results with high probability, which is challenging to identify with complete accuracy. That is, for the alarm signals that meet the established rules, the accuracy of the event recognition method can only approach the expert system and cannot be 100% accurate. Therefore, in the recognition strategy, the expert system first filters out the alarm signals that meet the rules, reducing the scope of subsequent data-driven identification and reducing the false recognition rate.
In order to verify the above theory, the experimnet added the recognition strategy to the experiment of Case 2, and it was found that the false recognition rate is reduced by 33.4%, which proves that the recognition strategy can further reduce the false recognition rate based on the event recognition method.
6 Conclusion
To improve the accuracy of monitoring event recognition, this paper proposes a power grid monitoring event recognition method that integrates knowledge graph and deep learning. Different from the vectorized modeling at the text-level of traditional alarm information, this paper adopts the vectorized model and integrates the features of alarm content structure. Besides, this paper combines the method with the existing monitoring expert system, further improves the accuracy of monitoring event recognition and provides a new idea for the “eventization” process of power grid monitoring.
In addition, there is still room for further research in this paper, such as the fusion of large amounts of data and the automation of graph construction need to be further improved; the scope of model application needs to be further expanded and the rules not included in the mining expert system need to be explored. The following work will try to apply the model to more substations and improve the model by analyzing and identifying wrong events to achieve high-precision intelligent recognition of monitoring events.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author Contributions
Conceptualization, Methodology, Writing — original draft, YY and QH; Resources, Funding acquisition, YL; Writing, SG; Supervision, XP and BH.
Funding
The authors gratefully acknowledge the support of the Science and Technology Program of State Grid Corporation of China (SGJS0000DKJS2000952).
Conflict of Interest
Authors YL, XP, and BH were employed by the company State Grid Jiangsu Electric Power Co., Ltd. Author SG was employed by the company NARI Group Corporation.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Bai, Z., Sun, G., Zang, H., Zhang, M., Shen, P., Liu, Y., et al. (2019). Identification Technology of Grid Monitoring Alarm Event Based on Natural Language Processing and Deep Learning in China. Energies 12 (17), 3258. doi:10.3390/en12173258
Chen, X., Jia, S., and Xiang, Y. (2020). A Review: Knowledge Reasoning over Knowledge Graph. Expert Syst. Appl. 141, 112948. doi:10.1016/j.eswa.2019.112948
Day, M. Y., and Lee, C. C. (2016). “Deep Learning for Financial Sentiment Analysis on Finance News Providers,” in 2016 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (IEEE), 1127–1134. doi:10.1109/asonam.2016.7752381
Dong, X. L., Gabrilovich, E., Heitz, G., Horn, W., Murphy, K., Sun, S., et al. (2015). From Data Fusion to Knowledge Fusion. arXiv preprint arXiv:1503.00302.
El Affendi, M. A., and Al Rajhi, K. H. S. (2018). “Text Encoding for Deep Learning Neural Networks: A Reversible Base 64 (Tetrasexagesimal) Integer Transformation (RIT64) Alternative to One-Hot Encoding with Applications to Arabic Morphology,” in 2018 Sixth International Conference on Digital Information, Networking, and Wireless Communications (IEEE), 70–74. doi:10.1109/dinwc.2018.8356998
Fan, J., Kalyanpur, A., Gondek, D. C., and Ferrucci, D. A. (2012). Automatic Knowledge Extraction from Documents. IBM J. Res. Dev. 56 (34), 5–1. doi:10.1147/jrd.2012.2186519
Farhadi, M., and Mohammed, O. A. (2015). Event-based Protection Scheme for a Multiterminal Hybrid DC Power System. IEEE Trans. Smart Grid 6 (4), 1658–1669. doi:10.1109/tsg.2015.2396995
Huang, L., Fang, X., Zhou, Z., Mei, J., and Wang, S. (2021). “Online Alarm Recognition of Power Grid Dispatching Based on PRADO,” in 2021 International Conference on Power System Technology (IEEE), 79–85. doi:10.1109/powercon53785.2021.9697881
Kipf, T. N., and Welling, M. (2016). Semi-supervised Classification with Graph Convolutional Networks. arXiv preprint arXiv:1609.02907.
Liuhong Wei, L., Wenxin Guo, W., Fushuan Wen, F., Ledwich, G., Zhiwei Liao, Z., and Jianbo Xin, J. (2011). An Online Intelligent Alarm-Processing System for Digital Substations. IEEE Trans. Power Deliv. 26 (3), 1615–1624. doi:10.1109/tpwrd.2011.2117445
Minakawa, T., Ichikawa, Y., Kunugi, M., Shimada, K., Wada, N., and Utsunomiya, M. (1995). Development and Implementation of a Power System Fault Diagnosis Expert System. IEEE Trans. Power Syst. 10 (2), 932–940. doi:10.1109/59.387936
Mu, J., Wu, W., Sun, H., Guo, Q., Zhang, Y., and Zhang, B. (2012). “An Online Intelligent Alarm-Processing System Based on Abductive Reasoning Network,” in 2012 IEEE Power and Energy Society General Meeting (IEEE), 1–5. doi:10.1109/pesgm.2012.6345528
Oh, J., Cho, K., and Bruna, J. (2019). Advancing Graphsage with a Data-Driven Node Sampling. arXiv preprint arXiv:1904.12935.
Pandey, S., Srivastava, A. K., and Amidan, B. G. (2020). A Real Time Event Detection, Classification and Localization Using Synchrophasor Data. IEEE Trans. Power Syst. 35 (6), 4421–4431. doi:10.1109/tpwrs.2020.2986019
Pujara, J., Miao, H., Getoor, L., and Cohen, W. (2013). “Knowledge Graph Identification,” in International semantic web conference (Berlin, Heidelberg: Springer), 542–557. doi:10.1007/978-3-642-41335-3_34
Shewalkar, A., Nyavanandi, D., and Ludwig, S. A. (2019). Performance Evaluation of Deep Neural Networks Applied to Speech Recognition: RNN, LSTM and GRU. J. Artif. Intell. Soft Comput. Res. 9 (4), 235–245. doi:10.2478/jaiscr-2019-0006
Sun, G., Ding, X., Wei, Z., Shen, P., Zhao, Y., Huang, Q., et al. (2019). Intelligent Classification Method for Grid-Monitoring Alarm Messages Based on Information Theory. Energies 12 (14), 2814. doi:10.3390/en12142814
Webber, J. (2012). “A Programmatic Introduction to Neo4j,” in Proceedings of the 3rd annual conference on Systems, programming, and applications: software for humanity, 217–218. doi:10.1145/2384716.2384777
Keywords: event recognition, knowledge graph, graph based neural network, GRU, recognition strategy
Citation: Yang Y, Hu Q, Liu Y, Pan X, Gao S and Hao B (2022) Power Grid Monitoring Event Recognition Method Integrating Knowledge Graph and Deep Learning. Front. Energy Res. 10:950954. doi: 10.3389/fenrg.2022.950954
Received: 23 May 2022; Accepted: 13 June 2022;
Published: 07 July 2022.
Edited by:
Bo Yang, Kunming University of Science and Technology, ChinaReviewed by:
Jianxiao Wang, Peking University, Beijing, ChinaJunjun Xu, Nanjing University of Posts and Telecommunications, China
Copyright © 2022 Yang, Hu, Liu, Pan, Gao and Hao. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Qinran Hu, cWh1QHNldS5lZHUuY24=
 Yinbin Yang
Yinbin Yang Qinran Hu
Qinran Hu Yi Liu2
Yi Liu2