- 1State Grid Electric Power Research Institute, Nanjing, China
- 2NARI Group Corporation, Nanjing, China
- 3NARI Technology Co., Ltd., Nanjing, China
The rise of an integrated energy system requires the integration of multiple sources of energy to be embraced and transited over the power grid; that means the information and communication systems of traditional power systems will be extended, and their complexity will be increased. As the information and communication systems play a more important role in the infrastructure of the power system, a cyber-attack on them may have an impact on the power system and cause a serious threat to the integrated energy system. To analyze the threat to the complex and integrated system, some researchers provide some modeling methods to study the impact of cyber-attacks on the information and communication systems, such as the Attack Tree Model, Attack Graph Model, Petri Net Model for cyber-attack, Attack Description Language Model, State Transition Graph Model, etc. However, these modeling methods have some shortcomings. For example, they cannot describe the systematical cyber-attack and show the secure status during the cyber-attack; it is hard for them to analyze the larger and more complicated information and communication systems. To overcome the shortages, in this paper, a correlated matrix-based object-oriented model is proposed for cyber-attack modeling. With this model, the relationship between the attacker and victim can be directly built; the cyber-attack path and packets from the attacker can be tracked; and the status of the nodes and links can be shown during a cyber-attack. There are two steps to build the cyber-attack model. Firstly, the procedure and approach of the cyber-attack will be modeled by an object-oriented method; then, a correlated matrix model will be built for network topology, attack path, and attack procedure. By combining these two models, the whole cyber-attack model is created. Finally, to demonstrate the modeling method and its benefits, we use the MITM (Man-in-the-middle Attack) attack on measurement data of an AVC (Automation Voltage Control) system as examples, and build a hardware-in-the-loop (HIL) co-simulation platform to verify the model.
1 Introduction
The increasing usage of multiple sources of energy, such as renewable energy and distributed energy, leads to the instability of energy utilization and energy supply (Li et al., 2021), which puts forward higher requirements for data acquisition and control systems. Due to the measurement and control mechanisms increasingly depending on the information and communication systems (Zhao et al., 2011; Liu et al., 2012), the tight interdependence between communication and the integrated energy system makes it more vulnerable to cyber-attacks (Tong and Ni, 2019), especially for the power system. Hackers’ attacks on communication and information systems can directly or indirectly affect the measurement and control of power systems, further affect the safe and stable operation of power systems, and even lead to large-scale power outages.
Therefore, the security of networks and information systems has attracted more and more attention all over the world. Facing endless cyber-attack cases, it is difficult for administrators to analyze and predict the impact of endless cyber-attacks on the network only by the research of individual cyber-attack behavior. Thus, it is necessary to model the overall situation and attack process on the network, predict the possible path and probability of cyber-attack, and realize the security assessment of the network state to provide a reference for safety measures. At present, many modeling methods for cyber-attacks have been proposed, including attack language, attack tree, attack graph, state transition graph, etc., and these methods have their respective advantages and disadvantages as following:
(1) Attack tree model: A tree structure is used to describe the attack on the system. The total target of the attack is regarded as the root node of the tree, and the subtarget of the total target is regarded as the sub node. Each path from the root node to the leaf node represents a complete attack process to achieve the attack target. For example, the paper (Lu et al., 2003) proposes to build an attack tree model in a recursive or progressive way to directly show the attack steps of attackers. In the reference (Ding et al., 2018), the attack tree modeling method is used to analyze the impact of SCADA-oriented network attacks on power systems. However, the attack tree is limited to description and formal analysis, which is too subjective, and its scale problem makes it unsuitable for large-scale network environments.
(2) Attack graph model: It is composed of a set of attack plans that attackers can use to destroy the network system by simulating attacks on existing security vulnerabilities and finding all attack paths that can reach the target (Wang et al., 2009). Compared with attack trees and Petri nets, attack graphs are more powerful in describing network attack processes. Through the attack graph, we can show how an attacker attempts to invade the communication or information system from the initial state to the target state. A complete attack graph is a possible operation sequence to reach the target. For example, in reference (Wang et al., 2016), based on the improved attack graph algorithm, the cross-space cascading fault assessment of power information physical systems is realized; in reference (Luo et al., 2020), a dynamic risk assessment model is proposed based on the Bayesian attack graph with the atomic attack probability calculation; and in reference (Li et al., 2022), the forward risk probability update algorithm and the forward-backward combined risk probability update algorithm are introduced to improve the attack graph model to reflect real-time network attack events. There are two kinds of typical attack graph generation method: one is state transition, which can generate a complete attack graph by an algorithm, but it often causes “state space explosion” in large-scale commercial networks; the other is host centric, which can be used in large-scale networks, but its disadvantage is that it can’t list all attack paths.
(3) Attack network model based on Petri Net: It is composed of location, transition, arc, and token. The location corresponds to the nodes in the attack network, and the attack behavior is described by the transition of tokens between locations. This method is preferable to represent the state, the action, and the progress of the attack (Schneider et al., 2006). For example, Steffan comprehensively uses graph theory, Petri Net, and other technologies to describe network attacks and expounds the correlation of cyber-attacks (Steffan and Schumachar, 2002). In reference (Lin et al., 2007), Petri Net is used to model and analyze the network penetration attack testing process. In the reference (Li et al., 2018a), the stochastic Petri net based model is used to analyze the topology attacks on the power system. In reference (Sinha et al., 2021), a novel Cyber Physical Defense Framework is proposed to analyze and deal with the cyber-attack on the smart grid by the hierarchical Petri Net model and recovery method. However, due to the limitation of scale, it is difficult to analyze the communication and information system with large scale and complex network topology.
(4) Network Attack Language: It is the earliest modeling method to describe network attack. It describes network attack through a formal description language, including NASL (Nessus Attack Scripting Language), STATL (State/Transition-based Attack Description Language), and object-oriented language modeling, etc., which directly describes one or a category of attack behavior. For example, in reference (Eckmann et al., 2002), STATL language is used to describe the attack behavior by state and state transition; in reference (Vigna and Kemmerer, 1999), STATL language is used to provide intrusion feature library for network intrusion detection system; and in reference (Zhu et al., 2004), object-oriented method and AKDL (Attack Knowledge Description Language) language is used to realize attack knowledge modeling for security defense system. The method of network attack language is suitable for engineering applications, but it is not suitable for describing staged attack behavior, nor can it show the security situation of the whole communication and information system.
(5) State transition graph modeling: This modeling method is based on the finite state machine model to represent the attack process. The intrusion process of attackers can be regarded as the procedure of improving their operational authority by taking advantage of the vulnerabilities and misconfigurations in communication and information systems. For example, in references (Ma and Wang, 2013), an attack graph construction method based on intelligent state transition and authority improvement is proposed to realize the analysis of large-scale complex network attacks; in reference (Prabha and Anitha, 2010) and (Zhou et al., 2005), the author provides a Hidden Markov Model based model (HMM-based) to detect distributed denial of service (DDoS) attacks. However, this model only describes the state transition in the specific node, but the whole network is ignored. Moreover, the state in this model is only a symbol, and its meaning is not clear (Wang et al., 2009).
As more and more distributed energy resources from different energy networks are integrated through the power system, a large number of distributed sensors and controllers for the distributed energy resources will be introduced, which rapidly increases the diversity and complexity of the communication network (Huang et al., 2022). To analyze the cyber-attacks and security situation for this complex network, the network topology, attack path, and attack behavior should be considered in the cyber-attack model. However, the traditional modeling methods mentioned above show a lack of description of network topology and the attack path, which makes it difficult to find out the potential security problems in a network or estimate the security situation of the network when a cyber-attack occurs. Thus, this paper provides a new method of the correlated matrix based object-oriented modeling method to solve this drawback. The main features and contributions of this modeling method are as follows:
1) By applying the object-oriented analysis method, we can directly display the relationship between the attacker and the attacked object and show the possible attack path.
2) The topology of communication and information networks can be described by the correlated matrix, which provides an effective way of analyzing the transmission path of attack packets.
3) The status of the nodes and links during a cyber-attack can be displayed, which helps us evaluate the impact of a cyber-attack.
To introduce the modeling method, this paper is organized as follows. Firstly, the background and traditional modeling methods are introduced; then, the definition and modeling process of the correlated matrix based object-oriented modeling method are provided; after that, a scenario of the MITM (Man in the Middle Attack) attack is applied to demonstrate how to use the modeling method; to validate the MITM attack model, we build a hardware-in-the-loop (HIL) co-simulation platform to emulate the MITM attack on the real route and study the impact on the power system; finally, we conclude this paper.
2 Object-oriented modeling for cyber-attack
The model of cyber-attack is an abstract description of the security problems existing in the network, the process of attack behavior, and the attack rules and approaches applied by the attacker. It describes the premise, target, consequence, and other characteristics of the attack process; identifies the relationship among the vulnerabilities from the perspective of attack; describes the attack path of the attacker; and provides a reference for the formulation of system protection measures.
The object-oriented method is a way to understand and describe the objective world. The characteristic of this method is that the attributes describing the static characteristics of things and the operations representing their dynamic behaviors are put together as a whole, and an objective world model can be established with limited steps (Rumbaugh et al., 2004). It plays an important role in the fields of computer science and information technology because its characteristics are consistent with the thinking methods of human habits (Rumbaugh et al., 2004).
Due to the characteristics of network attack behavior, the model constructed by object-oriented can clearly describe the method and process of network attack. At the same time, it can also show the system vulnerability intuitively to a network security administrator and trace the steps of the attacker successfully attacking the system. It provides an effective method for network security administrators to discover attack behavior and improve system security.
2.1 Basic concepts
When using an object-oriented method to model the attack of a communication information system, it is necessary to abstract the real system and define some basic concepts.
Definition 1. Network object (N): The instance of a communication link or information node is encapsulated as a network object, which can be a communication node in the communication and information system, such as router, switch, SDH (Synchronous Digital Hierarchy) equipment, etc., or a communication link between communication nodes, such as an optical fiber link, wireless communication link, etc., or a substation or data center as a system level abstraction.
Definition 2. Attribute of a network object, or network attribute (A): Network attribute is the representation of the state characteristics of the object being attacked, including service, vulnerability, bandwidth, hardware resources, system version, etc. Attribute of a network object can be identified by <N, V > tuple, where N is the name of the attribute, V is the specific value for the attribute, which is identified by 0, 1, and −1. 0 means that the object has no corresponding attribute, 1 indicates that the attribute of the component is not exploited by the attacker, −1 indicates that the attribute of the component has been exploited by the attacker.
Definition 3. Method of network object, or network method (M): Network method is defined as the method for a network object to process the received packet or user operation request, and it can also be defined as the processing method of attack behavior, such as refusal reply for port scanning behavior, packet filtering, etc.; Network method can be represented by <N, V > tuple, in which N represents the name of the method, V represents the specific value of N by 0, 1, and −1, where 0 means that the method does not exist, 1 means that the method is valid, and −1 means that the method has been used by an attacker.
Definition 4. Attack behavior object (ON): By encapsulating the attack instance into an attack behavior object, it can be represented as a single attack or a compound attack. A successful attack behavior will change the attributes of one or more network objects.
Definition 5. Attack Attribute (OA): Attack attribute defines the operation of an attack behavior object. As the precondition, when one or more attack attributes are fully satisfied, the attack action will be triggered. The attack attribute can be identified by <N, V > tuple, where N is the name of the attribute, V is the specific value for the attribute, which is identified by 0 and −1, where 0 means that the attribute of attack behavior is ineffective and −1 means that the attribute of attack behavior is effective.
Definition 6. Attack method (OM): Attack method is the description of the attack action of the attack behavior object. When the premise of meeting the attack behavior attribute, one or more attributes of the network object will be modified by attack method to complete the attack action. Attack method can be identified by <N, V > tuple, where N is the name of the method, V is the specific value of the method, which is identified by 0 and −1, where 0 means the method is ineffective and −1 means the attack method is effective.
Definition 7. Class (C): A class is a collection of similar objects with the same name, relationship, attribute, and method. According to different objects, they can be divided into communication link classes, communication node classes, communication and information node classes, attack behavior classes, attack (transit) path classes, etc.
2.2 Representation of the model
When the object-oriented method is used to model the attack on communication and information systems, the attack process can be abstracted as the object of communication and information system changing from its initial state to the target state after the operation performed by the attack behavior object. And the attack behavior can also be regarded as the operation process on the network object for changing its attributes.
The attack behavior is encapsulated in the attack object, whose attribute OA is used to describe the target and the operations on the attacked object. The target of the attack is a set of state changes, which indicates the possibility that the attribute A of the network object may be changed after the attack. For example, the buffer overflow attack can enable the attacker to obtain privileges from the network object, or implant Trojans in the network object, or maybe not cause any consequences.
The operation process of the attack behavior is identified by the attack method OM, such as scanning the port and vulnerability of the network object to determine whether the attack can be launched. On the other hand, the network method M defines the protection method for the network object, such as packet filtering, preventing packets from the specific port, etc.
2.3 Instance of modeling
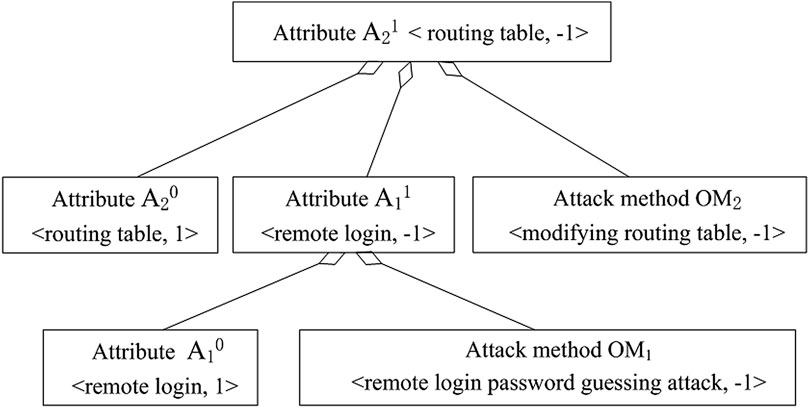
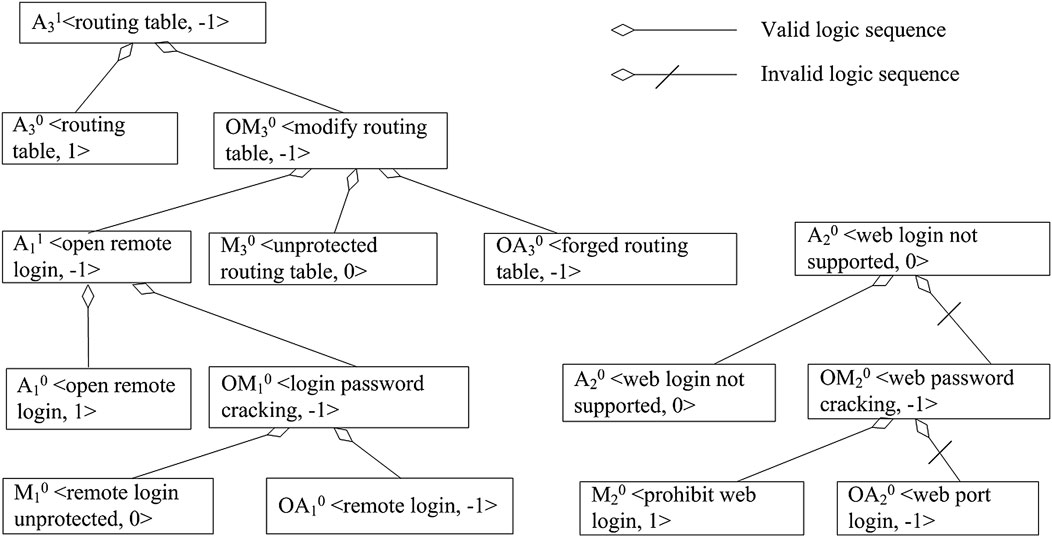
Take an attack on a router as an example: the attacker discovers a router by scanning, and remotely attacks it with open remote login permission, brutally breaks the login password of the router by using the password guessing attack method, and then remotely launches the router and modifies the routing table configuration to complete the attack on the router. The object-oriented method for cyber-attack modeling is shown in Figure 1.
As shown in Figure 1, router N1 contains attributes A10 of remote login, and A20 of routing table, and attack behavior ON1 contains attack methods OM1 of remote login password guessing attack, and OM2 of modifying the routing table. I the prerequisite of the attribute A10 matching the method OM1, the attacker will change the attribute A10 to the attribute A11 of the attacker’s login; due to the prerequisite of the attribute A11, the attacker tries to change the attribute A20 by the method OM2. If the attribute A20 matches the attack method OM2, the routing table will be modified, and the attribute A20 will be changed to the attribute A21.
3 Matrix modeling of network attack
Object-oriented network attack modeling methods can be described by a formal specification language or a knowledge description language (/knowledge base). Although these methods can effectively show the attack means, the system weaknesses, and the consequences of the attack, they have some limitations in describing the network attack on a complex communication and information system, such as the transmission path of the attacker’s packets in the network, the role of each intermediate node in the attack process, and the impact of topology on the attack effect. Therefore, designing a network attack model that can describe the topology of communication information systems is an important extension of the existing attack model.
This paper proposes a correlated matrix-based object-oriented modeling method for cyber-attack modeling and analysis, which extends the object-oriented modeling method for network attack and effectively describes the evolution process of a communication and information network from the initial state to the state after several different attacks.
The modeling process for cyber-attack is as follows: first, communication and information networks are modelled in a matrix; then, considering the topology of communication and information networks, the cyber-attack is modeled in a matrix; based on that, by iterated logical matching between the matrix of communication and information networks and the matrix of cyber-attack, the network attack process will be represented, and the final status matrix of communication and information networks is generated.
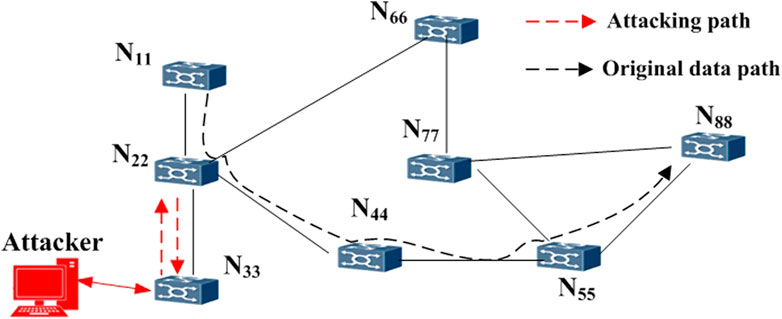
Take a communication and information system with eight communication and information nodes and nine full-duplex communication links as an example to illustrate the modeling process for a cyber-attack. The topology of the communication information network is shown in Figure 2.
3.1 Matrix modeling of communication information network
Definition 8. Matrix of communication network object: The attributes and methods of the network object N and can be identified by the matrix [A M]. A is the vector set of network attributes, which may contain link bandwidth, CPU performance, memory, remote login and services, etc.; M is the vector set of object methods, which may contain password protection for remote login, specific data filtering, virus protection, etc.Based on the node and link model, a communication network object correlated matrix N (Network) with 26 communication information object elements is established to describe the topology and characteristics of the communication system. The matrix N is a large sparse matrix whose structure is shown in Eq. 1.The 8 × 8 matrix N can describe the state of each object element in the whole communication network. Where: Nij = [A M], if i = j, then Nij represents a communication or information node in the communication network; if i ≠ j, Nij is a unidirectional link from node Nii to Njj in the communication network; if there is no link connecting node Nii to Njj, the corresponding Nij and Nji in the matrix are represented by 0 (Li et al., 2018b). The state of the elements in the N matrix is represented by the superscript of the elements. For example, N110 represents the initial state of the object element N11.
3.2 Matrix modeling of attack (behavior) object
Definition 9. Matrix of attack behavior object: the attributes and methods of attack behavior object ON can be identified by the matrix [OA OM]. OA is the vector set of attack attributes, which may contain an attacking port number, an attacking IP address, a number of attack packets, etc. OM is the vector set of attack methods, which may include consumption of link bandwidth, consumption of system resources, modification of configuration information, planting of Trojans, etc.Similar to the matrix modeling of communication and information networks, the matrix modeling of cyber-attack can be established for the attack behavior on the communication and information networks with eight communication or information nodes and nine communication links through the matrix modeling, and the attack path, attack method, and attack process can be described by the attack object correlated matrix ON (Operating Network). In the ON matrix, the attack sequence is represented by the superscript of the attack object ON. For example, ON330 represents the first attack on the N33 object element. The structure of the attack object matrix is shown in Eq. 2.
The ON matrix is also 8 × 8. The elements in the matrix can describe the path and method of the attacker attacking the target object through the nodes and links of the communication network. Where: ONij = [OA OM], if i = j, ONij represents an attack on a communication information node in the communication network or the attack packet passing through; If the attack object ONij does not exist, or the attack packet does not pass through the object, the corresponding ONij in the matrix is represented by 0 (Li et al., 2018a). If i ≠ j, ONij represents that the attacker attacks a unidirectional link from Nii to Njj in the communication network or uses this link to transit attack packets to the target object; if the attacker neither attacks nor uses the link from Nii to Njj, the corresponding ONij and ONji in the matrix are represented by 0 (Li et al., 2018b).
3.3 Matrix modeling and analysis of the attack process
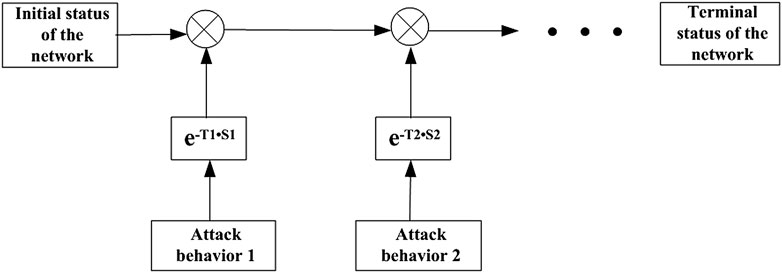
In Sections 3.1, 3.2, the communication and information system network model and the cyber-attack model are established. Based on this, the attack process correlated matrix model is established. Through the model, the process and path of network attack and the probability of attack success are described; at the same time, it can also describe the state changes of communication and information nodes after network attacks and provide the corresponding association model for the analysis and modeling of network attacks. The modeling framework and analysis process for the network attack can be represented in Figure 3.
In the diagram, the occurrence and duration of the cyber-attack can be represented by a pure delay component e−T1S1, where T1 represents the time when the network attack occurs and S1 represents the duration of the attack. Considering that the cyber-attack on the target system is step-by-step, multiple interactions between the communication information network matrix model and the attack matrix model are designed for the modeling. The logical relationship of the interaction is mainly represented in the algorithm, which is represented as “⊗” in Figure 3.
Definition 10. Logical relation (⊗): It describes the logical operation between the elements of an attack behavior object and a network object, including the logical matching between the attribute of attack behavior and the method of the network object, and the logical matching between the method of attack behavior and the attribute of the network object.A simple attack case can illustrate how the logical relation (⊗) works. When the attacker finds the remote router through remote scanning and logs into its configuration interface by cracking the login password of the router, he can modify the router’s routing table, configure a packet forwarding route for the specific IP address and port number, so that the relevant packets will be forwarded to the attacker; then the attacker tampers the packets and sends them back to the corresponding router; and the router forwards the tampered packets to the target communication information node, so as to complete the MITM attack process. The matrix modeling of the attack process is shown in Eq. 3. The logic matching rules for each vector in the matrix model are as follows:
1. When matching the attack behavior object ONij and the network object Nij, a logical match between the OA of the object ONij and the M of the object Nij is performed first. If a method Mi matches an attack attribute OAi, the attack behavior will be filtered; on the contrary, the attack behavior will be effective.
2. If the attack behavior is effective, a logical match between the OM of the object ONij and A of the object Nij will be performed, which means that the attack method operates on the attribute of the network object. If it is effective, the attribute A of the object Nij will be modified, and the attack will be successful; on the contrary, the attribute A of the object Nij is not modified, and the attack fails or the attack can utilize the attribute.
4 Modeling examples
4.1 Scenario of the MITM attack on AVC measurement
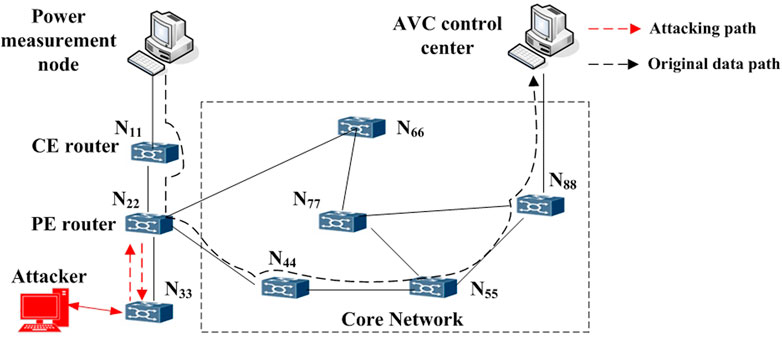
The AVC control runs on the power dispatching data network. Based on the communication network topology in Figure 2, a simple AVC control communication network is shown to illustrate the modeling process in Figure 4. The dotted line represents the normal data path for the measured data and the AVC control command. The red dotted line represents the process of modifying the routing table after the attacker invades the router, so that the measured data returns to the normal routing path via the tampered routing path. In this case, the attacker only modifies the upstream data for measurement and does not modify the downstream data for AVC control command.
When the communication network is normal, the AVC control center collects the power measurement information from the power measurement node every 5 s. By calculation, the AVC control center sends the corresponding voltage regulation value to the corresponding generator unit through the communication special line. Generally, the transmission path of the measurement information starts from the power measurement node via the CE (Customer Edge) router to connect to the core network of power dispatching via the PE (Provider Edge) router, and then connects to the AVC control center through the opposite end router. After receiving the measurement data, the AVC control center will send the voltage regulation to each generator unit through a private communication line. If the attacker successfully costs S1 minutes to intrude into the PE router at T1 time, modifies the routing configuration, establishes a bypass routing transmission path filtered based on the IP address and port number of the packet, and forwards the voltage measurement data of the power measurement node to the attacker, the attacker tampers with the normal measurement data by MITM (false data injection) attack at T2 time (T2 > T1 + S1). The duration of data tampering is S2 minutes (S2 > 5 s in order to achieve the corresponding attack effect), and the tampered data are returned to the intruded PE router. Then the intruded PE router sends the tampered data to the AVC control center through the normal path. After receiving the tampered data, the AVC control center will make a wrong judgment and result in the AVC deficient control or over control while the AVC control channel has not been attacked.
4.2 Modeling for the MITM attack on AVC measurement
The procedure of modeling for the above network attacks is as follows:
1. Establish the initialization matrix of the communication information network according to the topology of the communication information system;
2. Establish the matrix of attack behavior objects according to the attack target and mode. If the attacker launches attacks on different targets in different time slots, it is necessary to establish a different matrix of attack behavior objects according to the different attack targets and time slots, and match them with the matrix of communication network objects separately according to the time sequence;
3. Based on the communication information network matrix and the attack object matrix, the final state matrix of the communication information network is obtained by using multiple iterative logical matching.
The cyber-attack can be simplified into two processes: the attack on the router and the attack on the transmitted data. In the model, we can simplify the matrix by assuming the power measurement node as a part of object N11 and the AVC control center as a part of object N88, and the MITM attack model can be represented as Eq. 3.
Among them, the router’s attack object ON220 (the sequence of attack behavior is represented by a superscript, ON220 represents the first attack on an N22 network object, and the sequence number is 0) contains two vectors: the elements of the attack behavior attribute vector OA0 include: OA10 < remote login, −1>, OA20 < web port login, −1>, OA30 < forged routing table, −1>, etc.; the elements of the attack behavior method vector OM0 include: OM10 < login password cracking, −1>, OM20 < web password cracking, −1>, OM30 < modify routing table, −1>, and the values of these elements are −1. Since the attack methods and attributes will not change in the attack path, the values of ON330, ON320, and ON220 are the same. The router object N220 contains two vectors: The elements of the network object attribute vector A0 include: A10 < open remote login, 1>, A20 < web login not supported, 0>, A30 < routing table, 1>, etc.; the elements of the network object method vector M0 include: M10 < remote login unprotected, 0>, M20 < prohibit web login, 1>, M30 < unprotected routing table, 0>, etc. The values of OA0 and OM0 constitute the attack state matrix of ON220, and the values of A0 and M0 constitute the network object state matrix of N220. By logical matching of ON220 and N220, the new state of the network object N221 is obtained, which is shown in Eq. 4.
The logical matching process and method of the network object N220 and the attack behavior object ON220 are shown in Figure 5.
According to the matching logic diagram, the attack will change the attribute A3 of N22 (the routing table is modified), and the state of attribute A3 will change from A30 to A31. Similarly, by establishing corresponding logical matches for other elements in the model, the final result of attack modeling on the router can be obtained, which is represented in the modified routing table, which belongs to the attribute A3 of network object N22.
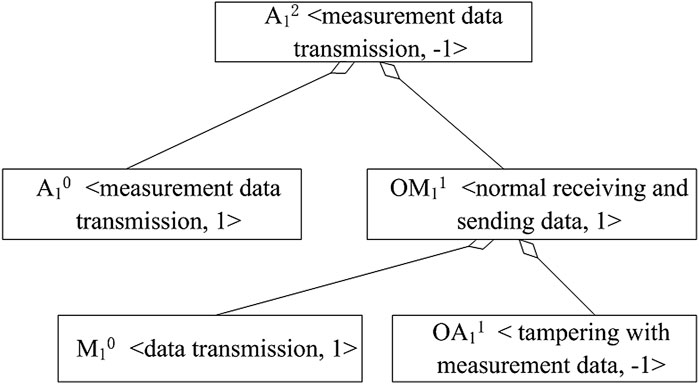
The attack on the transmission data starts from ON331 (ON331 represents an attack with an attack order of 1 against N33 elements), which contains two vectors: the element of the attack behavior attribute vector OA1 includes: OA11 < tampering with measurement data, −1>; the element of the attack behavior method vector OM1 includes: OM11 < normal receiving and sending data, 1>. The router object N330 contains two vectors: the elements of the network object attribute vector A0 include: A10 < measurement data transmission, 1>, etc.; the elements of the network object method vector M0 include: M10 < data transmission, 1>, etc. The values of OA1 and OM1 constitute the attack state matrix of ON331, and the values of A0 and M0 constitute the network object state matrix of N330. By logical matching of N330 and ON331, the new state of the network object N332 is obtained, which is shown in Eq. 5. Since the attributes and methods of other network objects in Eq. 3, such as N221, N440, N550, and N660, are the same as those of N330, and since the attributes and methods of the attack behavior object are the same as those of object ON331, the logical matching of the above network objects and attack behavior objects can be represented in Eq. 5.
The logical matching process and method of the network object N330 and the attack behavior object ON331 are shown in Figure 6:
According to the matching logic diagram, the attack will cause the change of attribute A1 of N33 (tampering of measurement data), and the state of attribute A1 will change from A10 to A12. Similarly, by establishing corresponding logical matches for other elements in the model, the final result of attack modeling on transmitted data can be obtained, which indicates that the attack does not modify the attributes A1 of the measurement data.
By analysis and calculation of Eqs 4, 5, it can be seen that in this case of MITM network attack, the attributes of object N22 and object N33 are modified by the attacker, while the attributes of other nodes and terminal nodes in the communication information network of the AVC control system are not changed, and the terminal data transmission of measurement and AVC control system is not affected. By analyzing the network attack model, it can be seen that the attack behavior can only be found by analyzing the attributes of each router in the transmission path, but it is hard to find the attack behavior by analyzing the status of the terminal equipment and detecting packets.
4.3 HIL co-simulation for the MITM attack model
To verify the cyber-attack process and the impact, we built a HIL co-simulation platform to emulate the real cyber-attack on a virtual AVC control system.
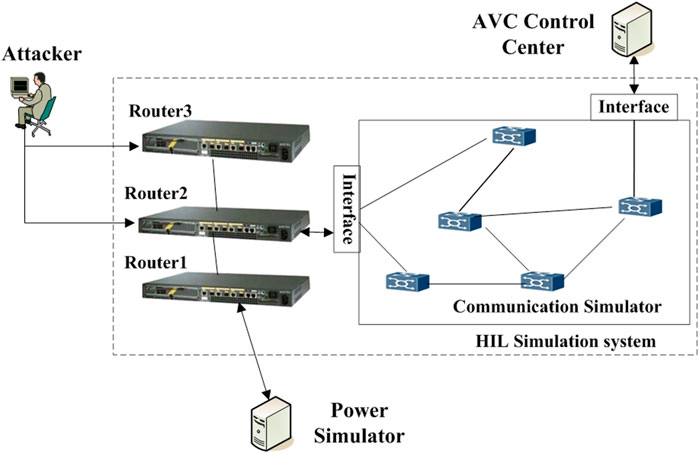
4.3.1 Implementation of the MITM attack
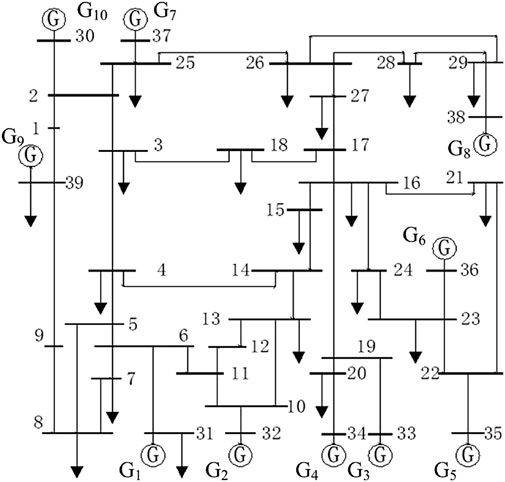
As shown in Figure 7, the HIL co-simulation platform consists of a power simulator, a communication simulator, a power control center, an attacker, and routers which work as both the communication equipment and the HIL interface to connect the attacker and simulators. The DIgSILENT Power Factory is used as a power simulator, where the IEEE 39-bus model (as shown in Figure 8) is used as a physical power system to simulate AVC function; the AVC control function is coded in C++, which collects the power system status, calculates the control values, and sends the control signals to the related power nodes in the power simulator every 5 s; the communication simulation software QualNet is used to build and simulate a virtual communication network, which runs in real time and provides the interface for external devices, by which the real-life packets can be caught and forwarded in the virtual network; the attacker is a program running on another computer, which can change the contents of communication packets; as the HIL interface, routers work as a bridge to connect power simulator, communication simulator, power control center, and attacker together, and the attack strategy and process can be emulated on them.
In the platform, the network objects N11, N22, and N33 are separately related to Router1, Router2, and Router3, and the other network objects are modeled in the communication simulator, as shown in Figure 7. Router1 and Router2 work as hardware interfaces to forward the packets from the power simulator to the communication simulator QualNet; Router3 works as the interface for emulating attack processes by configuring the router’s access control list (ACL), which blocks the regular data transmission and forwards data to the attacker. When HIL co-simulation begins, it will show the attacker how to exploit the weakness and attack the virtual AVC control system.
During the co-simulation, the DIgSILENT sends the power status data to the AVC control center; the control center sends voltage adjustment commands to generators G3 and G4 via the routers and virtual network. The regular path for measuring data forwarding to the AVC control center is from Router1 via Router2 to the virtual network built in QualNet. However, in the scenario of the MITM attack, after the attacker attacked the Router2 via the Router3, changed the routing rules, and created the by-pass traffic focusing on the specific power node measurement data to fudge the measurement data; after the packets of fudged measurement data passing through the virtual network, they are transmitted to the AVC control center; then, the AVC control center makes a wrong control decision based on the fake measurement data, and sends the control packets to the communication simulator; passing through the virtual network and router, the control packets are forwarded to the power simulator to continue the power simulation.
4.3.2 Result of simulation
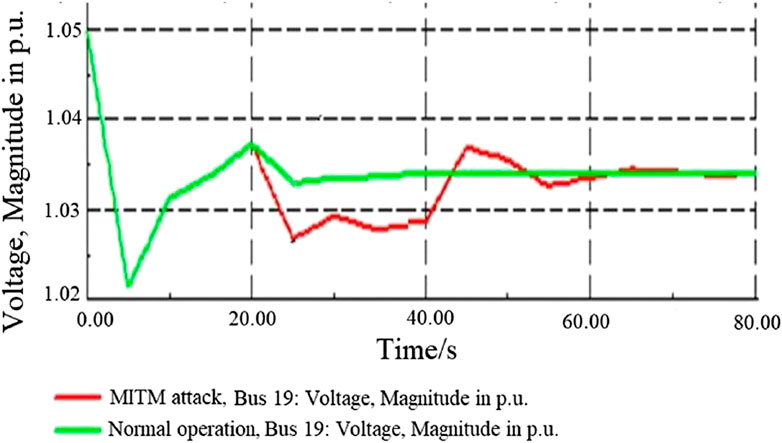
Case 1. Normal operation. Case 1 is the normal operating scenario. After a power system failure happens, AVC adjusts the voltage magnitudes of every generator with a time interval of 5 s. The voltage adjustment command is sent out to generators G3 and G4. If the status of Router1 and Router2 is normal, the measurement data for the voltage of bus 19 can be correctly transmitted, and the voltage adjustment can be properly executed. The simulation result of the voltage magnitude of bus 19 is the green curve shown in Figure 9.
Case 2. Impact of MITM attack. Case 2 is an MITM attack scenario. When the attacker changes the routing path of the Router2 and creates a by-pass traffic focusing on the measurement data of voltage on bus 19, the attacker can intercept the measurement data, buffer it, and resend it in the next measurement data transmission cycle. As a result, the AVC control gives false control, and the voltage adjustment in G3 and G4 cannot be executed properly. The simulation result of the voltage magnitude of bus 19 is the red curve shown in Figure 9.
4.3.3 Discussion
With the HIL co-simulation platform, the MITM attack can be emulated. The attack process and the status change of real network equipment will be displayed, as well. By analyzing the attack process, it can be found that since the attacker does not directly attack the measurement equipment and control center but attacks the equipment in the communication link with relatively weak security, the attack behavior is relatively stealthy, and it is difficult to find the attack through the security defense equipment installed in the terminal of the communication system. Therefore, when modeling the cyber-attack, the network topology should be considered, and each node in the communication system should be modeled.
5 Conclusion
This paper presents a correlated matrix based object-oriented modeling method for network attack analysis, which realizes the modeling of network attack method, attack path, attack steps, and the propagation path of attack behavior in communication and information network. In addition, this method benefits computers by building models fast and efficiently for large and complex communication networks and network attacks. The comparison of the mentioned modeling methods is shown in Supplementary Table S1. Based on this modeling method, an attack case of MITM attack on the measurement data of the AVC control system is analyzed, which indicates the usage and advantages of this modeling method. Finally, we built a HIL co-simulation platform to emulate the MITM attack process and study the impact on the power system. As the method proposed in this paper has good scalability, it also has some deficiencies, as follows.
1) Through the correlated matrix, it is difficult to directly display the attack behavior and its impact;
2) The structure of correlated matrix is relatively large, and its construction is not well-regulated and universal;
3) This modeling method just shows the cyber-attack model, but the probability of attack discovery and defense is not represented.
And we plan to follow the following aspects to further improve the method:
1) Further research for finding the potential attack behavior or evaluating the weak link of the system according to the attack model;
2) Further improvement for the construction method and operation rules of matrix model to make it more expressive and universal;
3) Further research on the “premise and consequence” method to design a matrix model of multiple preconditions;
4) Further research for the representation method of “time and probability” to realize the modeling and calculation for the probability of attack discovery.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding author.
Author contributions
HT was responsible for proposing the modeling method and the specific work in this paper. JX, XL, and LZ carried out some of the calculation work.
Funding
The authors declare that this study received funding from National Natural Science Foundation of China-State Grid Corporation of China Joint Fund Project. The funder was not involved in the study design, collection, analysis, interpretation of data, the writing of this article or the decision to submit it for publication.
Conflict of interest
HT, JX, XL, and LZ were employed by State Grid Electric Power Research Institute, NARI Group Corporation, and NARI Technology Co., Ltd.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Supplementary material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fenrg.2022.774645/full#supplementary-material
References
Ding, M., Li, X., and Zhang, J. (2018). Effect of scada-oriented cyber attack on power system reliability. Power Syst. Prot. Control 46 (11), 37–45. doi:10.7667/PSPC170784
Eckmann, S. T., Vigna, Giovanni, Kemmerer, R. A., et al. (2002). Statl: an Attack Language for state-based intrusion detection. J. Comput. Secur. 10 (1), 71–103. doi:10.3233/jcs-2002-101-204
Huang, B., Li, Y., Zhan, F., Sun, Q., and Zhang, H. (2022). A distributed robust economic dispatch strategy for integrated energy system considering cyber-attacks. IEEE Trans. Ind. Inf. 18 (2), 880–890. doi:10.1109/TII.2021.3077509
Li, B., Lu, R., Choo, K. K. R., Wang, W., and Luo, S. (2018a). On reliability analysis of smart grids under topology attacks: a stochastic petri net approach. ACM Trans. Cyber-Phys. Syst. 3 (1)–25. doi:10.1145/3127021
Li, J., Ling, X., Li, C., Li, Z., Yang, J., Zhang, L., et al. (2022). Dynamic network security analysis based on Bayesian attack graphs. Comput. Sci. 49 (3), 62–69. doi:10.11896/jsjkx.210800107
Li, M., Ni, M., Xue, Y., Chen, X., and Ding, W. (2018b). “Hybrid calculation architecture of cyber physical power system based on correlative characteristic matrix model,” in IEEE 8th Annual International Conference on CYBER Technology in Automation, Control, and Intelligent Systems (CYBER), Tianjin, China, 19-23 July 2018. doi:10.1109/CYBER.2018.8688204
Li, X., Wang, W., and Wang, H. (2021). A novel bi-level robust game model to optimize a regionally integrated energy System with large-Scale centralized renewable-energy Sources in Western China. Energy 228 (10), 120513. doi:10.1016/j.energy.2021.120513
Lin, Z. Z., Wen, F. S., Yung, C. C., and Po, W. K. (2007). Applications of petri nets in power systems. Proc. Chin. Soc. Univ. Electr. Power Syst. Automation 19 (5), 57–66. doi:10.3969/j.issn.1003-8930.2007.05.003
Liu, C. C., Stefanov, A., Hong, J., and Panciatici, P. (2012). Intruders in the grid. IEEE Power Energy Mag. 10 (1), 58–66. doi:10.1109/MPE.2011.943114
Lu, J., Huang, L., and Wu, S. (2003). An attack tree approach for network attack modeling. Comput. Eng. Appl. 39 (27), 160–163. doi:10.3321/j.issn:1002-8331.2003.27.051
Luo, Z., Yang, X., Liu, J., and Xu, R. (2020). Network intrusion intention analysis model based on Bayesian attack graph. J. Commun. 41 (9), 160–169. doi:10.11959/j.issn.1000-436x.2020172
Ma, Y., and Wang, L. G. (2013). Attack graph construction method based on intelligent state transition and permission improvement. Comput. Sci. 40 (9), 156–158.
Prabha, S., and Anitha, R. (2010). Mitigation of application traffic DDoS attacks with trust and AM based HMM models. Int. J. Comput. Appl. 6 (9), 26–34. doi:10.5120/1101-1443
Rumbaugh, B. J., Blaha, M. R., Lorensen, W., Eddy, F., and Premerlani, W. (2004). Object-oriented modeling and design. Upper Saddle River: Prentice-Hall. ISBN: 0136298419.
Schneider, K., Liu, C. C., and Paul, J. P. (2006). Assessment of interactions between power and telecommunications infrastructures. IEEE Trans. Power Syst. 21 (3), 1123–1130. doi:10.1109/TPWRS.2006.876692
Sinha, A., Mohandas, M., Pandey, P., and Vyas, O. P. (2021). Cyber physical defense framework for distributed smart grid applications. Front. Energy Res. 8, 621650. doi:10.3389/fenrg.2020.621650
Steffan, J., and Schumachar, M. (2002). “Collaborative attack modeling,” in Conf. 2002 Acm Symposium on Applied Computing, Madrid, Spain, March 11 - 14, 2002. doi:10.1145/508791.508986
Tong, H., Ni, M., Zhao, L., and Li, M. (2019). Flexible hardware-in-the-loop testbed for cyber physical power system simulation. IET Cyber-phys. Syst. 4 (4), 374–381. doi:10.1049/iet-cps.2019.0001
Vigan, G., and Kemmerer, R. A. (1999). Netstat: a network-based intrusion detection system. J. Comput. Secur. 7 (1), 37–71. doi:10.3233/jcs-1999-7103
Wang, G. Y., Wang, H. M., Chen, Z. J., and Xian, M. (2009). Research on computer network attack modeling based on attack graph. J. Natl. Univ. Def. Technol. 31 (4), 74–80. doi:10.1360/972009-1549
Wang, Y., Gao, K., Zhao, T., and Qiu, J. (2016). Assessing the harmfulness of cascading failures across space in electric cyber-physical system based on improved attack graph. Proc. CSEE 36 (6), 1490–1499. doi:10.13334/j.0258-8013.pcsee.2016.06.004
Zhao, J., Wen, F., Xue, Y., et al. (2011). Modeling analysis and control research framework of cyber physical power systems. Automation Electr. Power Syst. 35 (16), 1–8. doi:10.1016/B978-0-444-53599-3.10005-8
Zhou, D., Zhang, H., Zhang, S., and Hu, X. (2005). A DDoS attack detection method based on hidden Markov model. J. Comput. Res. Dev. 42 (9), 1594. doi:10.1360/crad20050921
Keywords: integrated energy system, object-oriented method, correlation matrix, cyber-attack, automation voltage control system
Citation: Tong H, Xu J, Li X and Zhang L (2022) Cyber-attack research for integrated energy systems by the correlated matrix based object-oriented modeling method. Front. Energy Res. 10:774645. doi: 10.3389/fenrg.2022.774645
Received: 12 September 2021; Accepted: 13 July 2022;
Published: 19 August 2022.
Edited by:
Yateendra Mishra, Queensland University of Technology, AustraliaReviewed by:
Yushuai Li, University of Oslo, NorwayJiwei Tian, Air Force Engineering University, China
Copyright © 2022 Tong, Xu, Li and Zhang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Heqin Tong, dG9uZ2hlcWluQHNnZXByaS5zZ2NjLmNvbS5jbg==
 Heqin Tong
Heqin Tong Jianbing Xu1,2,3
Jianbing Xu1,2,3