
95% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
BRIEF RESEARCH REPORT article
Front. Energy Res. , 21 April 2021
Sec. Smart Grids
Volume 9 - 2021 | https://doi.org/10.3389/fenrg.2021.666130
This article is part of the Research Topic New Solutions for Smart Grids with High-Penetration Distributed Energy Resources View all 19 articles
Existing coordinated cyber-attack detection methods have low detection accuracy and efficiency and poor generalization ability due to difficulties dealing with unbalanced attack data samples, high data dimensionality, and noisy data sets. This paper proposes a model for cyber and physical data fusion using a data link for detecting attacks on a Cyber–Physical Power System (CPPS). The two-step principal component analysis (PCA) is used for classifying the system’s operating status. An adaptive synthetic sampling algorithm is used to reduce the imbalance in the categories’ samples. The loss function is improved according to the feature intensity difference of the attack event, and an integrated classifier is established using a classification algorithm based on the cost-sensitive gradient boosting decision tree (CS-GBDT). The simulation results show that the proposed method provides higher accuracy, recall, and F-Score than comparable algorithms.
In recent years, a new type of coordinated cyber-physical attack has caused blackouts of the power grid and disrupted power systems. The main reason is that the coordinated attack on the power grid by hackers was not detected in time, and effective measures to prevent major accidents could not be implemented at the optimum time (Haes Alhelou et al., 2019; Lai et al., 2019). In the 2015 attack on the Ukrainian power grid, the attack point was not the power infrastructure, and the 0-day vulnerability was not used. Its attack cost is significantly lower than that of Stuxnet, Equation, and other attacks, but it is also more effective (Zhang et al., 2016; Koopman et al., 2019). Therefore, traditional security protection methods for power systems have their limitations, and it is urgent to research detection and defense methods for coordinated attacks on the Cyber–Physical Power System (CPPS) to identify attack types and intentions. It is crucial to establish a comprehensive active defense system to ensure the security of power systems (Chen et al., 2011; Dai et al., 2019; Wang X. et al., 2019).
Many scholars have investigated the detection and identification of coordinated attacks on the CPPS. The coupling relationship between the cyber side and the physical side has been considered in several studies (Drayer and Routtenberg, 2019; Shen et al., 2019), which focused on the fusion of the attack path on the information side and the attack object on the physical side. Xu and Abur (2017) combined a priori and a posteriori bad data detection and proposed a new decomposition method to solve the state estimation data corruption in cyber-attacks. Kurt et al. (2018) and Basin et al. (2016) used a dynamic equation of the measured variables with a joint transformation to detect false data injection (FDI) attacks in real time to improve the detection accuracy.
In summary, existing detection methods for cyber-attacks on the CPPS have the following limitations: (1) the cyberspace and the physical space are closely coupled and interact with each other. An attack detection from the cyber side or the physical side alone is not sufficient (Lin et al., 2016; Nath et al., 2019). (2) Attack detection methods based on physical power grid data ignore the impact of cyber network attacks on the performance of smart grids. The effects of power grid failures and cyber-attacks on the physical side are similar, and it is difficult to distinguish them based on data characteristics (Liu et al., 2016; Huang and Zhu, 2020). (3) A cyber-attack is characterized by unbalanced attack samples, high data dimensionality, and noise, and data with a long tail are common. Low detection accuracy of attacks and low real-time detection efficiency are typical (Osanaiye et al., 2018; Tian et al., 2019).
In this paper, the cyber-side alarm data and the physical-side measurement data are merged to establish a cyber-physical coupling state chain. A clustering method is designed to classify and distinguish different operating states of the CPPS. An oversampling algorithm is used to reduce the imbalance in the operating states’ samples. Subsequently, a coordinated cyber-attack detection algorithm based on the improved gradient boosting decision tree (GBDT) is proposed. The algorithm optimizes the cost-sensitive (CS) loss function, minimizing the error associated with the small sample size of attack data and providing high accuracy of attack detection and a high recall rate and F1-score.
The framework of the coordinated cyber-attack detection model is shown in Figure 1. The model exploits the data characteristics in different states, such as normal operation, fault operation, and coordinated attack of the CPPS. First, the data link of the cyber–physical operation state is established according to the coupling relationship. A clustering algorithm is used to classify the state data link, and a feature set is obtained under different operating conditions. Then, the adaptive synthetic sampling algorithm (ADASYN) is used to balance the majority of the samples and the minority of the samples in different state data sets. Finally, new CS conditions are added using the GBDT’s CS loss function to detect different coordinated cyber-attacks.
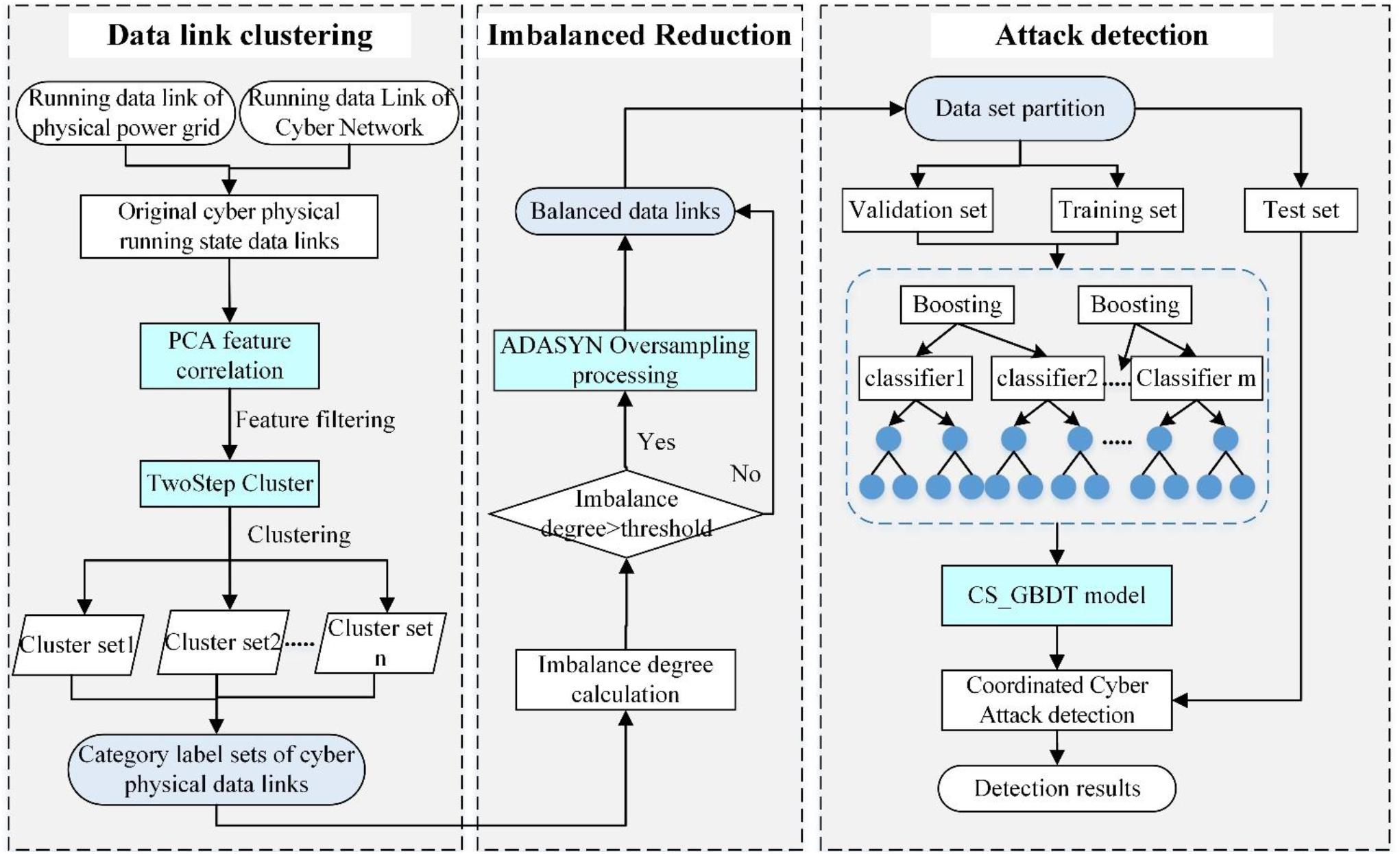
Figure 1. Framework of the coordinated cyber-attack detection model for the Cyber–Physical Power System (CPPS). CS-GBDT, CS gradient boosting decision tree; PCA, principal component analysis.
The physical grid measurement data reflect the real-time operating status of the grid under different working conditions. The measurement data of each section of the grid reflect the operating status at that moment. We do not consider the reasons for changes in the grid state (caused by cyber-attacks or general equipment failures); it can be described as a specific interval Δt(t1∼tn). According to the acquisition sequence, all state data fragments Sp(ti) consisting of the physical grid operating data link Qp(Δt) are defined as follows:
where Xp(ti) represents the h measured attributes obtained from the physical-side device Xp at time ti, including the voltage, current, phase angle, active power, and reactive power; Sp(ti) represents all the measurement data collected by m devices on the physical side at time ti.
The transmission delay and data packet loss rate typically reflect the performance status of a cyber-network. When the control signal or status information is lost during the transmission of the data packet because it exceeds the allowable proportion, the control of the device has been lost due to a network attack (Davarikia and Barati, 2018; Wang Q. et al., 2019). Three indicators (delay rate, packet loss rate, and threat degree) are established to characterize the operating data link of the cyber network.
1. The delay ratio (DR) is defined as follows:
where n is the number of communication links transmitting data, P′ is the number of data packet losses for link k, Pk is the number of data packets sent by link k, and PT is the threshold of the packet loss rate of link k.
1. The packet loss ratio (PR) indicator is defined as follows:
where m is the number of devices that send information, Tlsend is the sending time of data packet l, and Tlreceive is the receiving time of data packet l.
1. Threat degree Wth (ai,j). Assuming that n alarm events are generated within the sampling time window Δt, the address set of the information equipment is {IP1, IP2, …IPm}, and ai,j indicates that IPi contains j alarm events. The intrusion detection system (IDS) deployed in the power cyber network indicates that the original threat degree is W. The threat degree is redefined as follows to determine the impact of alarm events on the attack risk of the entire system:
where wij is the threat degree of alarm events ai,j, wi is the average value of the threat degrees of all alarm events in IPi, and ni is the number of all alarm events in IPi.
The three performance indicators of the operating status of the cyber network are used to establish the cyber system operating data link Qc(Δt) in the interval Δt(t1∼tn):
where Yc(ti) represents the Rdr, Rpr, and Wth obtained from the cyber-side device Yc at time ti; Sc(ti) represents the status data obtained from k devices on the cyber side at time ti.
We use topological mapping to couple and map the data links of the two heterogeneous networks to form a data link of the cyber–physical operating state. The grid can be divided into m areas according to the physical grid connectivity, and each area has n transmission lines. It is assumed that a line consists of k electrical components {X1, X2, …, Xk}, each line is connected to n communication devices {Y1, Y2, …, Yn}, and each communication device has a unique IP address {IP1, IP2, …, IPn} in the cyber network. We sequentially connect each electrical component number, line number, and connected area in the data chain to create an index table linking the <connected area number Area, line number Line, electrical component ID number, and information component IP address>. The cyber network operating data link Qc and the physical power grid operating data link Qp in the interval are compared using the index table, and the data are stored in the corresponding index.
The cyber network clock with a collection period of T is used, and we set the sampling time window to ε = [T−αT′,T], where α is the window size parameter. The larger the value, the longer the collection period is. In the sampling time window ɛ many identical state events may occur in the cyber–physical coupling state chain. Therefore, these repetitive events are filtered and compressed to form the cyber–physical operating state data link, which is expressed as follows:
There are no labels for the different state categories in the original cyber–physical operating state data link Q(ε). It is necessary to distinguish the different state categories using cluster analysis. In this paper, the two-step principal component analysis (PCA) clustering algorithm is proposed. The PCA algorithm is used to cluster, transform, and filter the correlated attributes to extract linear uncorrelated attributes (Jian et al., 2004). The two-step algorithm is used to cluster the attribute set; it reduces the computational complexity and provides high clustering accuracy (Dom et al., 2003; Northrup et al., 2004; Phelps et al., 2009). The algorithm steps are as follows:
Input: cyber–physical operating state data link Q(ε) = {x1, x2, …, xn}.
Output: D = {xi, Ci}, where Ci is the operating state of the clusters C = {C1, C2, …, Ck}.
Step 1: Feature selection for clustering. The PCA algorithm is used to map n attributes in the data link to m dimension (m < n). The correlated attributes are filtered using an orthogonal transformation to obtain m-dimensional new features, A = {A1, A2, …Am}. The centralizing mean is used to derive the covariance matrix XX^T, whose eigenvalues and eigenvectors are obtained. The data link set Q’(ε) is obtained after dimensionality reduction.
Step 2: Calculate the number of category clusters in the operating state. After the traversal process, the clustering feature (CF tree) growth in the balanced iterative reducing and clustering using hierarchies (BIRCH) algorithm is applied to the data link set Q’(ε). The data points in the data set are evaluated one by one to collect all data points in the dense area while generating the CF tree. The log-likelihood distance d(Cs,Ct) = ζs + ζt−ζ< s,t > between the two clusters is used to create many small subclusters. The Bayes information criterion (BIC) is used to calculate the number of possible division schemes for the state category.
Step 3: Determine the number of categories CJ in the Q’(ε). The agglomerative hierarchical clustering (AHC) method is used to merge the subclusters one by one, and the desired number of clusters is reached according to the R(k) between the two clusters.
where Ck and Ck+1 is a partition scheme with k or k+1 cluster numbers; dmin(Ck+1) and dmin(Ck) is the distance between the two smallest clusters in the scheme.
Step 4: Label the sample data in each operating state cluster. The data points in each cluster are determined; the data points xi in the state data link set Q’(ε) are regarded as single-point clusters according to the clustering results CJ. The logarithm similarity between xi and each cluster in CJ is determined. Given the distance d{{xi}, CJ}, xi is placed into the nearest cluster, and labels are generated for each operating state category C = {C1, C2,…, Ck}.
A coordinated cyber-attack event of the CPPS has a small probability and high risk. In the data link Q(ɛ) normal operation data account for the largest proportion, whereas the proportion of attack data is relatively small, resulting in unbalanced data. Therefore, the ADASYN algorithm is used to deal with the imbalance of the operating state classes (Qu et al., 2018; Wang et al., 2020). Balanced data distribution is obtained by adaptive synthetic oversampling. Different minority samples are given different weights to generate different numbers of samples. The algorithm process is as follows:
Input:D = {xi, Ci}, where xi is the cyber–physical operating state data link Q(ε), Ci is the class label. α is the imbalance threshold, Ck is a minority class, and Cl is the majority class.
Output: Balanced data set D′.
Step 1: Calculate the class imbalance, where . Calculate the number of samples to be synthesized based on the degree of imbalance G = (Lagrenum(Cl)−Smallnum(Ck))×β,β∈[0,1].
Step 2: Calculate the proportion of the majority class in the K-nearest neighbors (KNNs). ri = Δi/K, where Δi is the number of samples of the majority class in the KNN.
Step 3: Calculate the majority class surrounding each minority sample.
Step 4: Calculate the number of samples that need to be generated for each minority sample Ck.
Step 5: Select a minority sample among k neighbors around each minority sample and synthesize using Eq. (10). Repeat the synthesis gi times until the desired number of synthesized samples is obtained.
where si is the composite sample, X_i is the i-th sample in the minority sample, Xi ∈ [0,1], Xzi is a randomly selected minority sample among the KNNs of Xi.
Repeat the synthesis until the desired number of synthesized samples in Eq. (5) has been obtained.
The purpose of attack detection is to minimize the harm to the power grid caused by the attack. The harm caused by misinterpreting an attack as a normal event is far greater than that caused by misinterpreting a normal event as an attack (Huang et al., 2018). We propose using the CS function to improve the GBDT (Sakhnovich, 2011; Liao et al., 2016). The CS loss function replaces the standard cost loss function to prevent attack event misclassification. The improved CS loss function is defined as follows:
where K is the class of all attacks, C_k is the sample of the k-th attack, and p_k (x) is the probability of the k-th attack, w_k is the CS function, it can be divided into two costs, i.e., the missed detection cost and the misdetection cost
Coordinated cyber-attack detection is a multi-classification task. A total of K types of attacks are assumed. The sample x in the cyber–physical operating state set is obtained, and the CS-GBDT algorithm is used to determine which class the x sample belongs to. The specific steps of the algorithm are as follows:
Input: Balanced data set , loss function Loss (Ck, fk(x)), and the number of classifiers M.
Output: A strong learner for attack classification F(x).
Step 1: Initialize fk0(x) = 0, the number of categories classified k = 1,2,…K.
Step 2: Starting from t = 1 to t = M, there are M iterations in total, repeating steps 3 through 6, at last building M classifiers.
Step 3: The one-hot code for each class yi is generated. We calculate the probability of sending the k-th attack sample pk(x).
Step 4: Start from k = 1 to k = K, repeating steps 5 through 6, we generate K different CART classification trees f1(x), f2(x),…fK(x).
Step5: Calculate the negative gradient of each class in the m class and obtain the negative gradient error of the i-th sample corresponding to category k in the t-th iteration:
where N is the number of sample data.
We use the estimated residual {(x1, rk1),…(xN, rkN))} as an input to calculate the leaf node area of the m-th decision tree:
where Rmkj is the leaf node region Rmj of the m-th tree. K is the number of categories.
Step 6: Update the classifier fmk(x).
where J is the number of leaf nodes per tree.
Step 7: Build final classification tree with high accuracy used for attack detection.
We simulate the different fault states of the physical power grid caused by cyber-attacks on the IEEE39-bus system in the RT-LAB and OPNET co-simulation environment. We collect the DR, PR, and threat information at different times on the cyber side. The voltage, current, impedance, and other data are collected on the physical side. The 10 data sets are obtained. Each set contains 56 attributes, and the cumulative number of records is about 50,000, including five types of operating states in the CPPS, as follows:
(1) Normal operating state (S1): there is no network attack on the cyber side, and the power grid on the physical side is operating normally. (2) Distributed denial of service (DDOS) attack state (S2): the data in the communication system are blocked by a DDOS attack, affecting the normal operation of the power system, measurement acquisition, and control commands. (3) Data injection attack state (S3): malicious data injection into physical power grid disguised as a normal fault, resulting in the operator mistakenly assuming a short-circuit fault. (4) Protection device parameter tampering attack state (S4): the attacker tampers with the distance parameter of the protection device, causing a failure of the protection device to disconnect the fault area. (5) Fault operation state (S5): the physical power grid has a single-phase, two-phase, or short-circuit fault.
The data set 1 with 4,966 records is selected in the experiment. After implementing the two-step PCA clustering algorithm, the number of outliers is 89, and there are five operating states, as shown in Figure 2A. Cluster-3 (S2) has the largest number of records (1,325). The clustering superiority is 0.93, and the clustering importance is 0.85, accounting for 29.3% of the records. The smallest cluster is Cluster-4 (S5), with 59 records, accounting for 1.3% of all records. The clustering superiority is 0.97, and the clustering importance is 0.93. Clustering superiority is a measure of cluster separation (−1∼0.2 poor| 0.2∼0.5 medium| 0.5∼1 good), and clustering importance is a measure of cluster cohesion (0∼0.2 poor| 0.2∼0.6 medium| 0.6∼1 good) (Nair and Narendran, 1997).
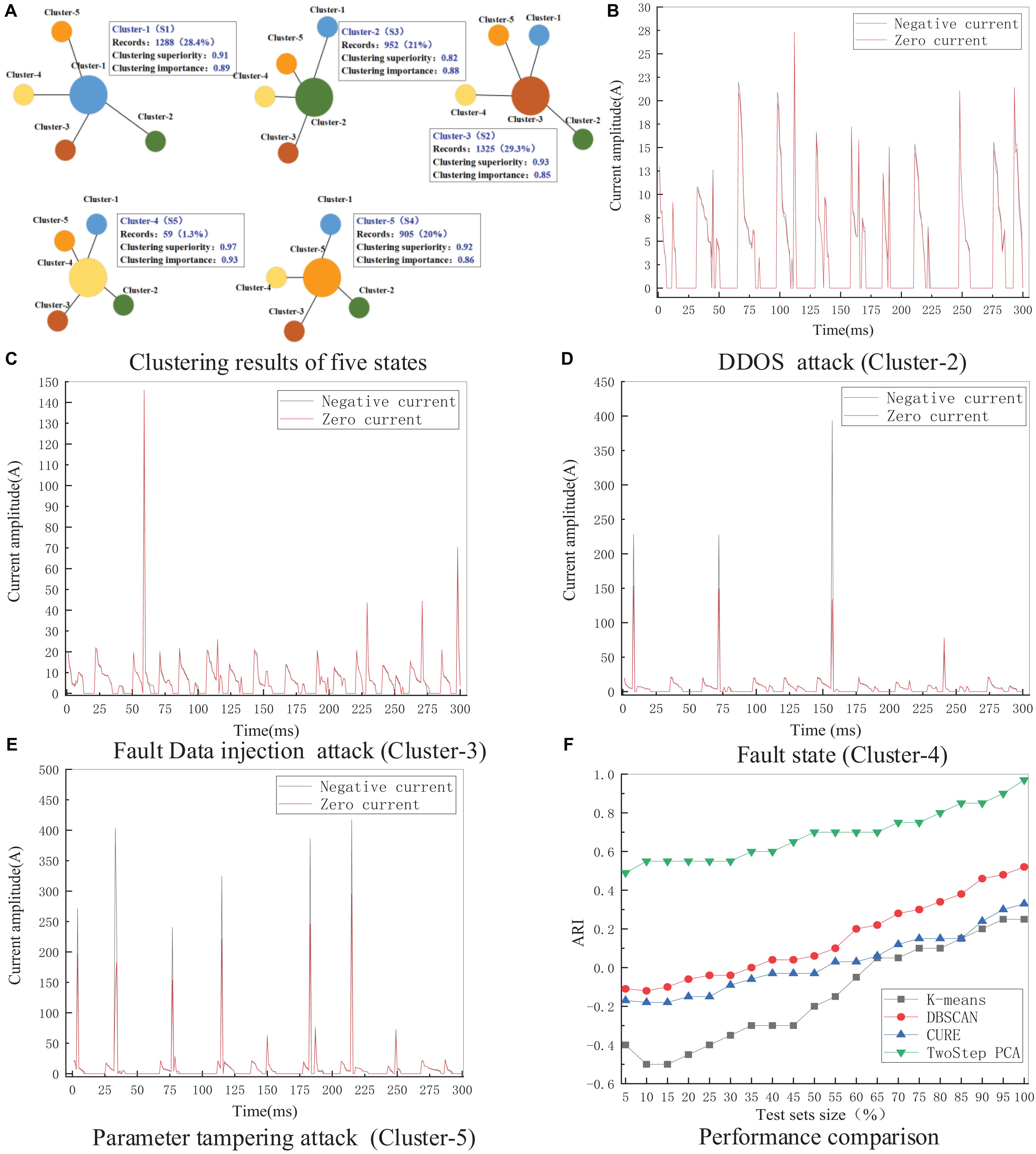
Figure 2. Clustering results of five states (A), Current amplitude under DDOS attack (B), Current amplitude under fault data injection attack (C), Current amplitude under fault state (D), Current amplitude under parameter tampering attack (E), Performance comparison (F).
According to the negative sequence current and zero sequence current amplitude of each cluster in the experiment, the curves of the three attack states and the fault state are obtained, as shown in Figures 2B–E. Cluster-2 is significantly different from the other four states, while Cluster-4 and Cluster-5 have high similarities. The reason is that Cluster-2 is an attack that causes network blocking and delay, which is significantly different from the other types of data tampering attacks. Cluster-3 and Cluster-5 are physical power grid failures caused by information tampering attacks. These states are similar to the changes occurring in the Cluster-4 power grid normal fault.
The adjusted Rand index (ARI) is used to measure the accuracy of the clustering results; ARI ∈ [−1,1], the closer the value is to 1, the better the clustering performance is. The index is calculated as follows:
where RI is the Rand coefficient, and E(RI) is the expected value of each class.
Four typical clustering algorithms are selected for performance comparison, i.e., K-means, density-based spatial clustering of applications with noise (DBSCAN), clustering using representatives (CURE), and BIRCH. In the experiment, the sample size of the test data set is randomly selected and ranges from 5 to 100% of the data set. The ARI values of the different algorithms are shown in Figure 2F. As the proportion of the test data set increases, the ARI increases significantly. The accuracy of the proposed two-step PCA method is 97% for a sample size of 100%, demonstrating the excellent performance of this method. The K-means algorithm has the lowest ARI values.
The number of samples in the operating state classes in 10 data sets before implementing the algorithm is shown in Figure 3A. The number of samples is imbalanced in the different operating states. The largest number of records (143,766) occurs in the S3 state, and the fewest number (3,080) is observed in the S5 state. The maximum class imbalance is 3.77. There are multiple minority and majority categories in the joint data set, showing multi-category imbalance.
The ADASYN algorithm is used to oversample the categories whose number is less than the threshold. We set the maximum imbalance threshold to 1.2. The results in the 10 data sets are shown in Figure 3B. The proportion of records in each dataset is close to 20%. The ADASYN algorithm uses local screening and sampling to reduce the influence of data imbalance on the false alarm rate of coordinated cyber-attack detection.
The balanced data set is divided into a training set (70% samples) and a test set (30% samples). The model loss parameters are set according to the improved CS loss function. There are 130 integrated base classifiers, and the depth of each independent tree (max_depth) is seven.
The receiver operating characteristic (ROC) curve obtained by classifying the test data set is shown in Figure 4A. The curves of the five categories are close to the (0,1) position, and the average area under the ROC curve (AUC) is 0.982. This result shows that the attack detection model has a low false alarm rate and high accuracy.
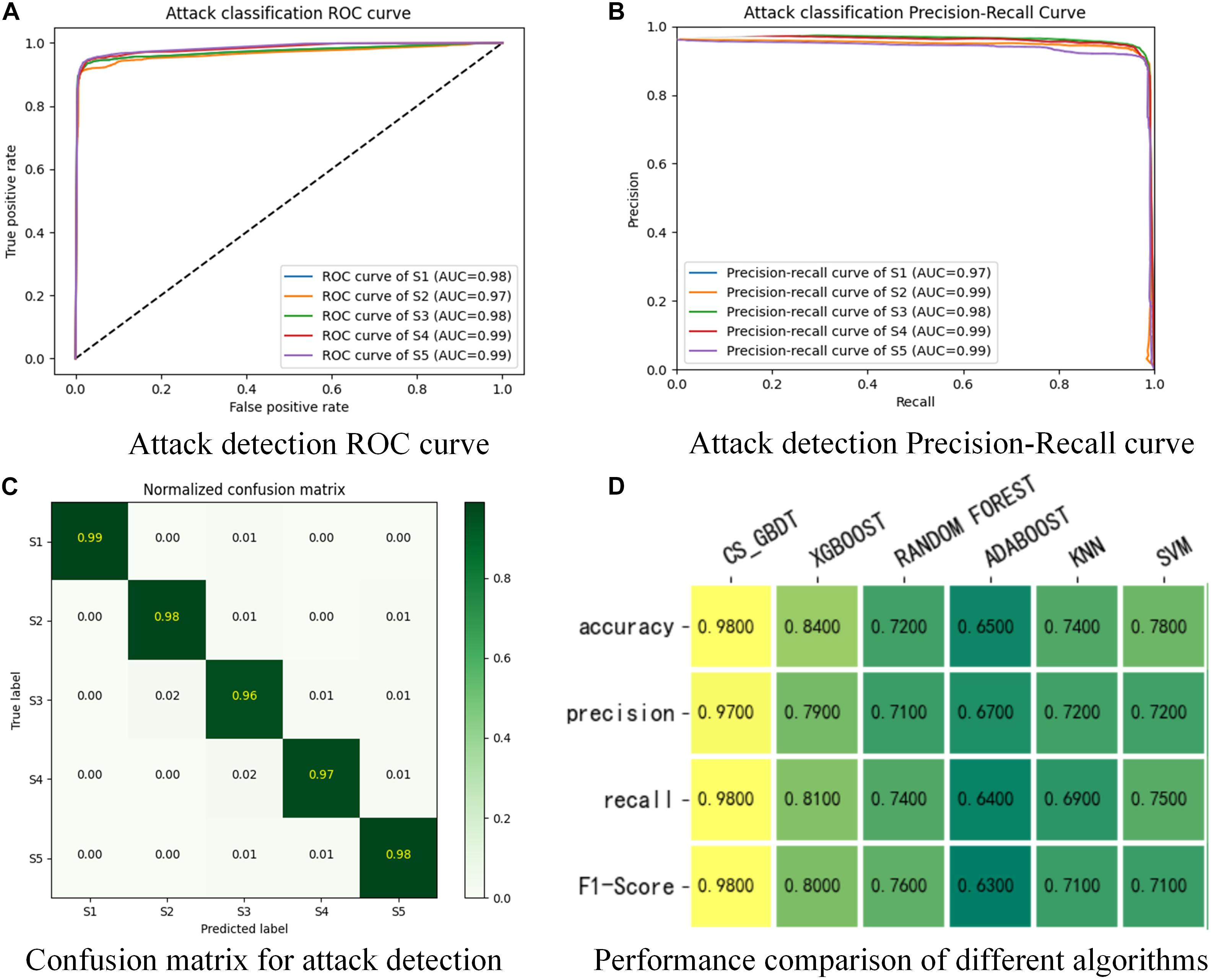
Figure 4. Attack detection receiver operating characteristic (ROC) curve (A), Precision-Recall curve (B), Confusion matrix (C), and Performance comparison (D). AUC, area under the ROC curve; CS-GBDT, CS gradient boosting decision tree; KNN, K-nearest neighbors; SVM, support vector machine.
The precision-recall curve obtained by classifying the test data set is shown in Figure 4B. The precision-recall curve are all close to the (1,1) position, indicating that the attack detection model has high recall and accuracy, even when the ratio of positive and negative samples is large. Therefore, the proposed attack detection model has a high classification accuracy for unbalanced data.
The confusion matrix of the attack detection results is shown in Figure 4C. The detection accuracy for the DDOS blocking attack (S2) is 98%, that of the data injection attack (S3) is 96%, that of the protection device parameter tampering attack (S4) is 97%, that of the normal operation (S1) is 99%, and that of the fault operation (S5) is 98%. These results demonstrate that the proposed coordinated cyber-attack detection model accurately detects coordinated attack events on the network and distinguishes attack states from the fault operation state, with a maximum false-positive rate of only 4%.
Finally, the proposed model is compared with typical classification algorithms, including the KNN, Xgboost, Random Forest, Adaboost, and support vector machine (SVM). The overall accuracy, average recall, average precision, and average F1-score of the algorithms are shown in Figure 4D. The recall and precision of the CS-GBDT algorithm are higher than 97%. The algorithm performance is stable, and it provides better performance for detecting various attack events than comparable algorithms.
In this paper, a cyber–physical operating state data link was established using data fusion mapping. The two-step PCA clustering algorithm is proposed for accurate labeling of the different operating states of the network. A coordinated cyber-attack classifier based on the CS-GBDT was established that considers the imbalance of the attack status categories and the cost sensitivity of the attack event. The algorithm can detect attacks on the CPPS and distinguish different attack types. The proposed model has a low false alarm rate and high accuracy for attack detection. It is suitable for the detection of coordinated cyber-attack events with unbalanced attack sample data and high data dimensionality.
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author/s.
LW designed the model framework of the manuscript and experimental verification. PX contributed to the construction method of the cyber–physical operation state data link. ZQ contributed to design the two-step PCA algorithm for operating state clustering. XB completed the simulation experiment of attack classification detection. YD performed the data collection and researched balance processing algorithm of operating state classes. ZZ studied the classification algorithm of cyber cooperative attack based on CS_GBDT. YL built a simulation environment and improved the grammar and sentence structure of the full manuscript. All authors contributed to the article and approved the submitted version.
This manuscript was supported in part by the science and technology innovation development plan project of Jilin (20200401097GX).
PX was employed by Siping Power Supply Company of State Grid Jilin Electric Power Company Limited, China.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Basin, D., Cremers, C., Kim, T. H. J., Perrig, A., Sasse, R., and Szalachowski, P. (2016). Design, analysis, and implementation of ARPKI: an attack-resilient public-key infrastructure. IEEE Trans. Depend. Sec. Comput. 15, 393–408. doi: 10.1109/tdsc.2016.2601610
Chen, T. M., Sanchez-Aarnoutse, J. C., and Buford, J. (2011). Petri net modeling of cyber-physical attacks on smart grid. IEEE Trans. Smart Grid 2, 741–749. doi: 10.1109/tsg.2011.2160000
Dai, Q., Shi, L., and Ni, Y. (2019). Risk assessment for cyberattack in active distribution systems considering the role of feeder automation. IEEE Trans. Power Syst. 34, 3230–3240. doi: 10.1109/tpwrs.2019.2899983
Davarikia, H., and Barati, M. (2018). A tri-level programming model for attack-resilient control of power grids. J. Modern Power Syst. Clean Energy 6, 918–929. doi: 10.1007/s40565-018-0436-y
Dom, G., Shaw-Jackson, C., Matis, C., Bouffioux, O., Picard, J. J., Prochiantz, A., et al. (2003). Cellular uptake of Antennapedia Penetratin peptides is a two-step process in which phase transfer precedes a tryptophan-dependent translocation. Nucleic Acids Res. 31, 556–561. doi: 10.1093/nar/gkg160
Drayer, E., and Routtenberg, T. (2019). Detection of false data injection attacks in smart grids based on graph signal processing. IEEE Syst. J. 14, 1886–1896. doi: 10.1109/jsyst.2019.2927469
Haes Alhelou, H., Hamedani-Golshan, M. E., Njenda, T. C., and Siano, P. (2019). A survey on power system blackout and cascading events: Research motivations and challenges. Energies 12:682. doi: 10.3390/en12040682
Huang, L., and Zhu, Q. (2020). A dynamic games approach to proactive defense strategies against advanced persistent threats in cyber-physical systems. Comput. Sec. 89:101660. doi: 10.1016/j.cose.2019.101660
Huang, T., Satchidanandan, B., Kumar, P. R., and Xie, L. (2018). An online detection framework for cyber-attacks on automatic generation control. IEEE Trans. Power Syst. 33, 6816–6827. doi: 10.1109/tpwrs.2018.2829743
Jian, Y., David, Z., and Frangi, A. F. (2004). Two-dimensional PCA: a new approach to appearance-based face representation and recognition. IEEE Trans. Pattern Analysis Machine Intelligence 26, 131–137. doi: 10.1109/tpami.2004.1261097
Koopman, G., Mortier, D., Michels, S., Hofman, S., Fagrouch, Z., Remarque, E. J., et al. (2019). Influenza virus infection as well as immunization with DNA encoding haemagglutinin protein induces potent antibody-dependent phagocytosis (ADP) and monocyte infection-enhancing responses in macaques. J. Gen. Virol. 100, 738–751. doi: 10.1099/jgv.0.001251
Kurt, M. N., Yılmaz, Y., and Wang, X. (2018). Distributed quickest detection of cyber-attacks in smart grid. IEEE Trans. Inform. Forensics Sec. 13, 2015–2030. doi: 10.1109/tifs.2018.2800908
Lai, K., Illindala, M., and Subramaniam, K. (2019). A tri-level optimization model to mitigate coordinated attacks on electric power systems in a cyber-physical environment. Appl. Energy 235, 204–218. doi: 10.1016/j.apenergy.2018.10.077
Liao, Z., Huang, Y., Yue, X., Lu, H., Xuan, P., and Ju, Y. (2016). In silico prediction of gamma-aminobutyric acid type-A receptors using novel machine-learning-based SVM and GBDT approaches. BioMed. Res. Int. 2016:2375268.
Lin, H., Slagell, A., Kalbarczyk, Z. T., Sauer, P. W., and Iyer, R. K. (2016). Runtime semantic security analysis to detect and mitigate control-related attacks in power grids. IEEE Trans. Smart Grid 9, 163–178. doi: 10.1109/tsg.2016.2547742
Liu, X., Li, Z., and Li, Z. (2016). Optimal protection strategy against false data injection attacks in power systems. IEEE Trans. Smart Grid 8, 1802–1810. doi: 10.1109/tsg.2015.2508449
Nair, G. J., and Narendran, T. T. (1997). Cluster goodness: a new measure of performance for cluster formation in the design of cellular manufacturing systems. Int. J. Prod. Econ. 48, 49–61. doi: 10.1016/s0925-5273(96)00067-9
Nath, S., Akingeneye, I., Wu, J., and Han, Z. (2019). Quickest detection of false data injection attacks in smart grid with dynamic models. IEEE J. Emerg. Selected Top. Power Electron. 99, 1–10.
Northrup, A. B., Mangion, I. K., Hettche, F., and MacMillan, D. W. (2004). Enantioselective organocatalytic direct aldol reactions of α−oxyaldehydes: step one in a two-step synthesis of carbohydrates. Angewandte Chem. Int. Edition 43, 2152–2154. doi: 10.1002/anie.200453716
Osanaiye, O. A., Alfa, A. S., and Hancke, G. P. (2018). Denial of service defence for resource availability in wireless sensor networks. IEEE Access 6, 6975–7004. doi: 10.1109/access.2018.2793841
Phelps, R. A., Chidester, S., Dehghanizadeh, S., Phelps, J., Sandoval, I. T., Rai, K., et al. (2009). A two-step model for colon adenoma initiation and progression caused by APC loss. Cell 137, 623–634. doi: 10.1016/s9999-9994(09)00528-5
Qu, Z., Zhang, Y., Qu, N., Wang, L., Li, Y., and Dong, Y. (2018). Method for quantitative estimation of the risk propagation threshold in electric power CPS based on seepage probability. IEEE Access 6, 68813–68823. doi: 10.1109/access.2018.2879488
Sakhnovich, A. L. (2011). The time-dependent Schrödinger equation of dimension k+ 1: explicit and rational solutions via GBDT and multinodes. J. Phys. A: Math. Theoret. 44:475201. doi: 10.1088/1751-8113/44/47/475201
Shen, Y., Zhang, W. A., Ni, H., Zhang, D., and Yu, L. (2019). Guaranteed cost control of networked control systems with DoS attack and time-varying delay. Int. J. Control Automat. Syst. 17, 811–821. doi: 10.1007/s12555-018-0324-2
Tian, W., Ji, X., Liu, W., Liu, G., Lin, R., Zhai, J., et al. (2019). Defense strategies against network attacks in cyber-physical systems with analysis cost constraint based on honeypot game model. Comput. Mater. Continua 60, 193–211. doi: 10.32604/cmc.2019.05290
Wang, L., Qu, Z., Li, Y., Hu, K., Sun, J., Xue, K., et al. (2020). Method for extracting patterns of coordinated network attacks on electric power CPS based on temporal–topological correlation. IEEE Access 8, 57260–57272. doi: 10.1109/access.2020.2982057
Wang, Q., Tai, W., Tang, Y., Ni, M., and You, S. (2019). A two-layer game theoretical attack-defense model for a false data injection attack against power systems. Int. J. Elect. Power Energy Syst. 104, 169–177. doi: 10.1016/j.ijepes.2018.07.007
Wang, X., Tian, M., Cao, M., Li, X., Zhao, Y., Zhao, X., et al. (2019). Countermeasures to false data injection attacks on power system state estimation based on protecting measurements. J. Nanoelectron. Optoelectron. 14, 626–634. doi: 10.1166/jno.2019.2590
Xu, C., and Abur, A. (2017). A massively parallel framework for very large scale linear state estimation. IEEE Trans. Power Syst. 33, 4407–4413. doi: 10.1109/tpwrs.2017.2788360
Keywords: cyber-physical power system, coordinated cyber-attack, cluster analysis, oversampling, gradient boosting decision tree
Citation: Wang L, Xu P, Qu Z, Bo X, Dong Y, Zhang Z and Li Y (2021) Coordinated Cyber-Attack Detection Model of Cyber-Physical Power System Based on the Operating State Data Link. Front. Energy Res. 9:666130. doi: 10.3389/fenrg.2021.666130
Received: 09 February 2021; Accepted: 24 February 2021;
Published: 21 April 2021.
Edited by:
Liang Chen, Nanjing University of Information Science and Technology, ChinaReviewed by:
Donglai Wang, Shenyang Institute of Engineering, ChinaCopyright © 2021 Wang, Xu, Qu, Bo, Dong, Zhang and Li. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Lei Wang, NzUyOTUzNTkzQHFxLmNvbQ==
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.