- 1Electrical and Computer Engineering Department, Michigan State University, East Lansing, MI, United States
- 2Control Science Center, Air Force Research Laboratory, Dayton, OH, United States
- 3Computer Science and Engineering Department, Michigan State University, East Lansing, MI, United States
We consider perimeter defense problem in a planar conical environment with two cooperative heterogeneous defenders, i.e., a turret and a mobile vehicle, that seek to defend a concentric perimeter against mobile intruders. Arbitrary numbers of intruders are released at the circumference of the environment at arbitrary time instants and locations. Upon release, they move radially inwards with fixed speed towards the perimeter. The defenders are heterogeneous in terms of their motion and capture capabilities. Specifically, the turret has a finite engagement range and can only turn (clockwise or anti-clockwise) in the environment with fixed angular rate whereas, the vehicle has a finite capture radius and can move in any direction with unit speed. We present a competitive analysis approach to this perimeter defense problem by measuring the performance of multiple cooperative online algorithms for the defenders against arbitrary inputs, relative to an optimal offline algorithm that has information about the entire input sequence in advance. Specifically, we establish necessary conditions on the parameter space to guarantee finite competitiveness of any online algorithm. We then design and analyze four cooperative online algorithms and characterize parameter regimes in which they have finite competitive ratios. In particular, our first two algorithms are 1-competitive in specific parameter regimes, our third algorithm exhibits different competitive ratios in different regimes of problem parameters, and our fourth algorithm is 1.5-competitive in specific parameter regimes. Finally, we provide multiple numerical plots in the parameter space to reveal additional insights into the relative performance of our algorithms.
1 Introduction
With ever-expanding capabilities of Unmanned Aerial Vehicles (UAVs) and ground robots, collectively known as autonomous agents, it is now possible to deploy a team of autonomous agents for critical tasks such as surveillance (Ma’sum et al., 2013; Tavakoli et al., 2012), exploration (Howard et al., 2006; Koveos et al., 2007), and patrolling (Kappel et al., 2020). Although homogeneous agents can be used in such applications, a team of heterogeneous autonomous agents can outperform homogeneous autonomous agents because of the different capabilities of the agents and thus, there has been a considerable interest in employing heterogeneous autonomous agents for such applications (Santos and Egerstedt, 2018; Ramachandran et al., 2019; Ramachandran et al., 2021). A critical application for such autonomous agents is defending a region (commonly known as perimeter) such as airports, wildlife habitats, or a military facility from intrusive UAVs or poachers (Casey, 2014; Lykou et al., 2020) motivating fundamental algorithmic research for perimeter defense applications using heterogeneous defenders.
In this work, we address a perimeter defense problem in a conical environment. The environment contains two heterogeneous defenders, namely a turret and a mobile vehicle, which seek to defend a perimeter by capturing mobile intruders. The intruders are released at the boundary of the environment and move radially inwards with fixed speed toward the perimeter. Defenders have access to intruder locations only after they are released in the environment. Further, the defenders have distinct motion and capture capability and thus, are heterogeneous in nature. Specifically, the vehicle, having a finite capture radius, moves with unit speed in the environment whereas the turret has a finite range and can only turn clockwise or anti-clockwise with a fixed angular rate. Jointly, the defenders aim to capture as many intruders as possible before they reach the perimeter. This is an online problem as the input, which consists of the total number of intruders, their release locations, as well as their release times, is gradually revealed over time to the defenders. Thus, we focus on the design and analysis of online algorithms to route the defenders. Aside from military applications, this work is also motivated by monitoring applications wherein a drone and a camera jointly monitor the crowd entering a stadium.
Introduced in (Isaacs, 1999) as a target guarding problem, perimeter defense problem is a variant of pursuit evasion problems in which the aim is to determine optimal policies for the pursuers (or vehicles) and evaders (or intruders) by formulating it as a differential game. Versions with multiple vehicles and intruders have been studied extensively as reach-avoid games (Chen et al., 2016; Yan et al., 2018; Yan et al., 2019) and border defense games (Garcia et al., 2019; Garcia et al., 2020) and generally focus on a classical approach which requires computing solutions to the Hamilton-Jacobi-Bellman-Isaacs equation. However, this approach, due to the curse of dimensionality, is applicable only for low dimensional state spaces and simple environments (Margellos and Lygeros, 2011). Another work (Lee et al., 2020) addresses a class of perimeter defense problems, called perimeter defense games, which require the defenders to be constrained on the perimeter. We refer the reader to (Shishika and Kumar, 2020) for a review of perimeter defense games. Other recent works include (Guerrero-Bonilla et al., 2021) and (Lee and Bakolas, 2021) which consider an approach based on control barrier function or a convex shaped perimeter, respectively. All of these works consider mobile agents or vehicles that can move in any direction in the environment. Recently, (Akilan and Fuchs, 2017) considered a turret as a defender and introduced a differential game between a turret and a mobile intruder with an instantaneous cost based on the angular separation between the two. A similar problem setup with the possibility of retreat was considered in (Von Moll and Fuchs, 2020; Von Moll and Fuchs, 2021). Further, (Von Moll et al., 2022a) and (Von Moll et al., 2022b) considered a scenario in which the turret seeks to align its angle to that of the intruders in order to neutralize an attacker. All of these works assume that some information about the intruders is known a priori and do not consider heterogeneous defenders.
Online problems which require that the route of the vehicle be re-planned as information is revealed gradually over time are known as dynamic vehicle routing problems (Psaraftis, 1988; Bertsimas and Van Ryzin, 1991; Bullo et al., 2011). In these problems, the input (also known as demands) is static and therefore, the problem is to find the shortest route through the demands in order to minimize (maximize) the cost (reward). Examples of such metrics would be the total service time or the number of inputs serviced. In perimeter defense scenarios, the input (intruders) are not static. Instead, they are moving towards a specified region, making this problem more challenging than the former. With the assumption that the arrival process of the intruders is stochastic (Smith et al., 2009; Bajaj and Bopardikar, 2019; Macharet et al., 2020), consider the perimeter defense problem, in a circular or rectangular environment, as a vehicle routing problem using a single defender or multiple but homogeneous defenders. Recently (Adler et al., 2022) considered a problem of perimeter defense wherein either all of the attackers are known to the defenders at time 0 or the attackers are generated (i) uniformly randomly or (ii) by an adversary and determine how fast each defender must be in order to defend the perimeter. Although, in this work we consider worst-case scenarios, which is equivalent to the intruders being generated by an adversary, the speed of the defenders is fixed and we focus on designing cooperative online algorithms for the defenders. Other related works that do not make any assumptions on the intruders are (McGee and Hedrick, 2006; Francos and Bruckstein, 2021). However in these works, the aim is to design must-win algorithms, i.e., algorithms that detect every intruder in an environment.
Most prior works on perimeter defense problems have only considered defenders with identical capabilities. Further, they have either focused on determining an optimal strategy for scenarios with either few intruders or intruders generated by a stochastic process. The optimal strategy approaches do not scale with an arbitrary number of intruders released online. While stochastic approaches yield important insights into the average-case performance of defense strategies, they do not account for the worst-case in which intruders may coordinate their arrival to overcome the defense.
This work considers a perimeter defense problem with two heterogeneous defenders and focuses on worst-case instances. In particular, we establish fundamental guarantees as well as design online algorithms and provide analytical bounds on their performance in the worst-case. To evaluate the performance of online algorithms in the worst-case when faced with arbitrarily many intruders, we adopt a competitive analysis perspective (Sleator and Tarjan, 1985) which has also been studied in robotic exploration (Deng and Mirzaian, 1996), searching (Ozsoyeller et al., 2013), and design of state-space controllers (Sabag et al., 2022). Under this paradigm, an online algorithm
Previously, we introduced the perimeter defense problem for a single defender in linear environments using competitive analysis (Bajaj et al., 2021). This was followed by (Bajaj et al., 2022c), which are the conference version of this current paper and focused on the perimeter defense problem for a single vehicle and a single turret in conical environments, respectively. The main contributions of this work are as follows:
• Perimeter defense problem with heterogeneous defenders: We address a perimeter defense problem in a conical environment with two cooperative heterogeneous defenders, i.e., a vehicle and a turret, tasked to defend a perimeter. The vehicle has a finite capture radius and moves with unit speed, whereas the turret has a finite engagement range and turns in the environment with a fixed angular rate. We do not impose any assumption on the arrival process of the intruders. More precisely, an arbitrary number of intruders can be released in the environment at arbitrary locations and time instances. Upon release, the intruders move with fixed speed v towards the perimeter. Thus, the perimeter defense problem is characterized by six parameters: (i) angle θ of the conical environment, (ii) the speed v of the intruders, (iii) the perimeter radius ρ, (iv) the engagement range of the turret rt, (v) the angular rate of the turret ω, and (vi) the capture radius of the vehicle rc.
• Necessary condition: We establish a necessary condition on the existence of any c-competitive algorithm for any finite c. This condition serves as a fundamental limit to this problem and identifies regimes for the six problem parameters in which this problem does not admit an effective online algorithm.
• Algorithm Design and Analysis: We design and analyze four classes of cooperative algorithms with provably finite competitive ratios under specific parameter regimes. Specifically, the first two cooperative algorithms are provably 1-competitive, the third cooperative algorithm exhibits a finite competitive ratio which depends on the problem parameters and finally, the fourth algorithm is 1.5-competitive.Additionally, through multiple parameter regime plots, we shed light into the relative comparison and the effectiveness of our algorithms. We also provide a brief discussion on the time complexity of our algorithms and how this work can be extended to other models of the vehicle.The paper is organized as follows. In Section 2, we formally define the competitive ratio and our problem. Section 3 establishes the necessary conditions, Section 4 presents the algorithms and their analysis. Section 5 provides several numerical insights. Finally, Section 7 summarizes the paper and outlines future directions.
2 Problem formulation
Consider a planar conical environment (Figure 1) described by
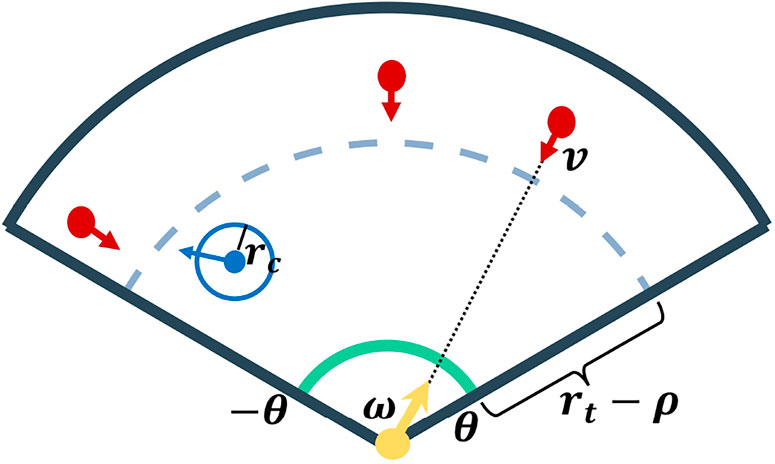
FIGURE 1. Problem Description. The vehicle is depicted by a blue dot and the blue circle around the vehicle depicts the capture circle. The direction of the vehicle is shown by the blue arrow. The yellow arrow depicts the turret (located at the origin of
Intruder i, located at
• intruder i is inside or on the capture circle of the mobile vehicle at time t, or
• intruder i is at most rt distance away from the origin and γt = θi holds, where γt denotes the heading of the turret at time instant t.
The intruder is said to be lost by the defenders if it reaches the perimeter without getting captured. The intruder is removed from
A problem instance
An online algorithm
Definition 1 (Competitive Ratio): Given a problem instance
The constant
Competitive analysis falls under a general framework of Request-Answer games and thus, can be viewed as a game between an online player and an adversary (Borodin and El-Yaniv, 2005). An adversary is defined as a pair
Problem Statement: Design online deterministic cooperative algorithms with finite competitive ratios for the defenders and establish fundamental guarantees on the existence of online algorithms with finite competitive ratio.
We start by determining a fundamental limit on the existence of c-competitive algorithms followed by designing online cooperative algorithms.
3 Fundamental limits
We start by defining a partition of the environment. A partition of
Let f1(α) = 2ω(ρ sin(α) − rc) + α − θ and f2(α) = 0.5ω(ρ sin(α) − rc) + α − θ. Let
Theorem 3.1: (Necessary Condition for finite
and let
Then, for any problem instance
Proof. Recall from Definition 1 that any online algorithm
Let
If neither the vehicle nor the turret captures the stream intruder, the stream never ends and the result follows as the optimal offline algorithm
We now determine the best locations, or equivalently the dominance regions of the environment, for the turret and the vehicle at time instant t. Note that the heading angle of the turret must not be equal to the angular coordinate of the vehicle at time instant t. This is because in such case, the burst arrives at (1, − θ) and thus, there always exist a location closer to angle −θ such that the vehicle or the turret can reach angular location −θ in less time. This implies that at time instant t, the environment consists of two dominance regions, each of which contains a defender. We denote the dominance region which contains the vehicle (resp. turret) as WVeh (resp. WTur) and determine them in the following two cases. These two cases arise based on whether the vehicle or the turret captures the ith intruder, each of which is considered below.
Case 1 (Vehicle captures the ith intruder): Let 2α1 and 2β1 be the angles of WVeh and WTur, respectively. The best location for the vehicle and the turret in this case can be summarized as follows. The vehicle must be located on the line joining the two endpoints of the perimeter within its WVeh
where by definition 2θ = 2α1 + 2β1 and the time taken by the vehicle to capture intruders at the other endpoint of the perimeter contained in its dominance region is 2(ρ sin(α1) − rc) (resp. 2(ρ − rc)) when
Suppose that α1 = ϵ, where ϵ > 0 is a very small number. Then, f(ϵ) = 2ωρ sin(ϵ) + ϵ − θ − 2rcω < 0. Now consider that α1 = θ − ϵ for the same ϵ. Then, as ρ sin(θ) > rc, it follows that f1(θ − ϵ) = 2ω(ρ sin(θ − ϵ) − rc) − ϵ > 0, for a sufficiently small ϵ. This means that for a sufficiently small ϵ > 0, f1(⋅) changes its sign in the interval [ϵ, θ − ϵ]. Thus, from Intermediate Value Theorem and using the fact that f1(α1) is continuous function of α1, it follows that there must exist an
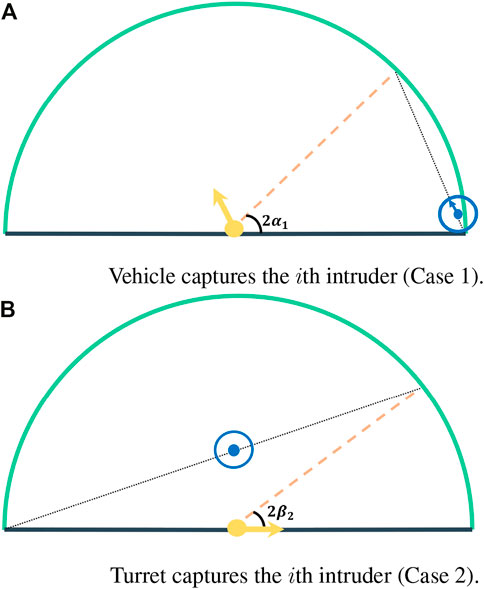
FIGURE 2. Depiction of the perimeter depicting the two cases under which one of the defenders captures the ith intruder. (A) Vehicle captures the ith intruder (Case 1). (B) Turret captures the ith intruder (Case 2).
Case 2 (Turret captures the ith intruder): Similar to Case 1, let 2α2 and 2β2 be the angles of WVeh and WTur, respectively (Figure 2B). As the turret captures the stream intruder, it follows that γt = θ. Further, the vehicle must be located at the midpoint of the line joining the two endpoints of the perimeter within its dominance region. Finally, the time taken by the vehicle to reach any endpoint of the perimeter must be equal to the time taken by the turret to turn to the same angle corresponding to that location. Mathematically, this yields
where we used the fact that 2θ = 2α2 + 2β2 and ρ sin(α2) − rc (resp. (ρ − rc)) denotes the time taken by the vehicle to capture intruders at the other endpoint of the perimeter contained in its dominance region when
As
Thus, we have established that for any online algorithm
Recall that
Remark 3.2: Since we do not impose any restriction on the number of intruders that can arrive in the environment, an adversary can repeat the input sequence designed in the proof of Theorem 3.1 any number of times. Thus, the lower bound derived in Theorem 3.1 holds asymptotically for when
We now turn our attention to designing online algorithms and deriving upper bounds on their competitive ratios. In the next section, we design and analyze four online algorithms, each with a provably finite competitive ratio in a specified parameter regime.
4 Online algorithms
In this section, we design and analyze online algorithms and characterize the parameter space in which these algorithms have finite competitive ratios. The parameter space of all of our algorithms is characterized by two main quantities:
• The time taken by the intruders to reach the perimeter in the worst-case and
• the time taken by the defenders to complete their respective motions.
Intuitively, the parameter space is obtained by comparing the aforementioned quantities2. Since the time taken by the intruders is inversely proportional to v, the (v, ρ) parameter space of our algorithms can be increased by designing the algorithms such that the time taken by the defenders to complete their motions is the least. We characterize the time taken by the defenders to complete their respective motions as epochs, which is formally defined as follows.
An epoch k for an algorithm is defined as the time interval which begins when at least one of the two defenders moves from its initial position and ends when both defenders return back to their respective initial positions. We denote the time instant when an epoch k begins as ks.
We now describe our first algorithm that has the best possible competitive ratio.
Algorithm 1. Sweep within Dominance Region Algorithm
1 Turret is at angle −θ
2 if α = arctan(
3 Vehicle is located at (ρ/cos(α) , θ − α)
4 for each epoch k do
5 Turn the turret clockwise to angle θ − 2α
6 Turn the turret anti-clockwise to angle −θ
7 end
8 else
9 Vehicle is located at (
10 for each epoch k do
11 Turn vehicle (resp. turret) anti-clockwise (resp. clockwise) until it reaches location (resp. angle) (
12 Turn vehicle (resp. turret) clockwise (resp. anti-clockwise) until it reaches location (resp. angle) (
13 end
14 end
4.1 Sweep within dominance region (SiR)
Algorithm SiR is an open-loop and memoryless algorithm in which we constrain the vehicle to move in an angular motion, i.e., either clockwise or anti-clockwise. This can be achieved by moving the vehicle with unit speed in the direction perpendicular to its position vector (see Figure 3A). By doing so, we aim to understand the worst-case scenarios for heterogeneous defenders and gain insights into the effect of the heterogeneity that arises due to the capture range of the defenders, i.e., the capture circle and the engagement range of the turret. We say that a defender sweeps in its dominance region if it turns, from its starting location, either clockwise or anti-clockwise to a specified location and then turns back to its initial location. Algorithm SiR is formally defined in Algorithm 1 and is summarized as follows.
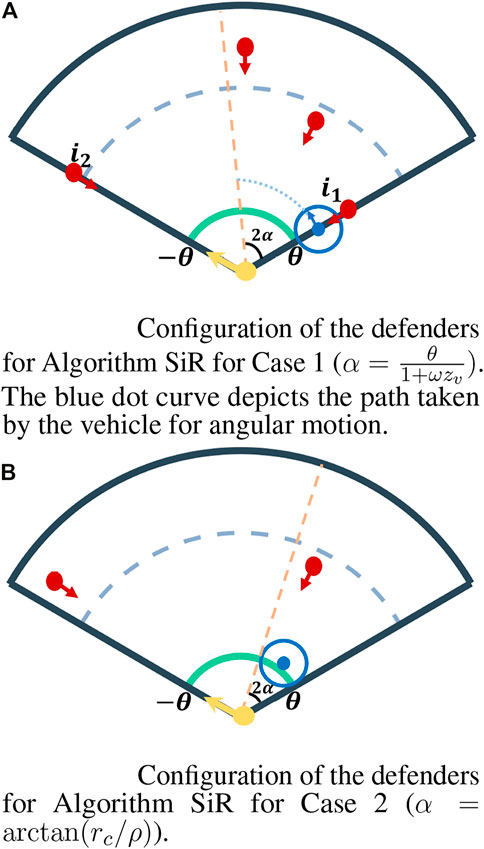
FIGURE 3. Partition (shown by the orange line) of the environment and the configuration of the defenders for the two cases of Algorithm SiR. (A) Configuration of the defenders for Algorithm SiR for Case 1 (
Algorithm SiR first partitions the environment
The vehicle’s location must be such that its capture circle covers the perimeter contained in its dominance region entirely, ensuring that any intruder that arrives in that dominance region is guaranteed to be captured. To achieve this, the boundary of the dominance region assigned to the vehicle must be tangent to its capture circle (see Figure 3B) which, through geometry, yields that
At time instant 0, the turret is at an angle −θ. The turret turns clockwise, with angular speed ω towards angle θ − 2α. Upon reaching angle θ − 2α, the turret turns anti-clockwise towards angle −θ. Note that the turret takes exactly
Case 1
Case 2
The following result characterizes the parameter regime in which Algorithm SiR is 1-competitive.
Theorem 4.1: Algorithm SiR is 1-competitive for a set of problem parameters that satisfy
Otherwise, Algorithm SiR is not c-competitive for any constant c.
Proof. Suppose that
If
Now consider that
Although Algorithm SiR is 1-competitive, note that for rt = ρ, the algorithm is not effective as Theorem 4.1 yields v ≤ 0. However, by allowing the vehicle to sweep the entire environment, it is still possible to capture all intruders for some small v > 0. This is addressed in a similar algorithm below.
4.2 Sweep in conjunction (SiCon)
At time instant 0, the turret is at angle θ and the vehicle is located at location (min{rt + rc, 1}, θ). The idea is to move the two defenders together in angular motion. Thus, the vehicle moves anti-clockwise with unit speed in the direction perpendicular to its position vector until it reaches the location (min{rt + rc, 1}, − θ). Similarly, the turret turns anti-clockwise, in conjunction with the vehicle, to angle −θ. Upon reaching −θ, the vehicle and the turret move clockwise until they reach angle θ. The defenders then begin the next epoch. As the two defenders move in conjunction,
The following result establishes that Algorithm SiCon is 1-competitive for specific parameter regimes.
Theorem 4.2: Algorithm SiCon is 1-competitive for a set of problem parameters which satisfy
Proof. As the proof is analogous to the proof of Theorem 4.1, we only provide an outline of this proof for brevity. In the worst-case, an intruder requires exactly
Remark 4.3: (Maneuvering Intruders). As the analysis of the fundamental limit (Theorem 3.1), Algorithm SiR, and Algorithm SiCon are independent of the nature of motion of the intruders, the results of Theorem 3.1, Algorithm SiR, and Algorithm SiCon apply directly to the case of maneuvering or evading intruders.
Recall that in Algorithm SiR, the idea was to partition the environment and assign a single defender in each dominance region. By doing so, we obtain valuable insight into the parameter regime wherein we are guaranteed to capture all intruders. However, we refrain from designing such algorithms in this work due to the following two reasons. First, such an algorithm requires that ratio of intruders captured by a defender to the total number of intruders that arrived in that corresponding defender’s dominance region is equal for both defenders. Otherwise, since the adversary has the information of the entire algorithm, it will release more intruders in the dominance region of the defender that has the lower ratio, which determines the competitive ratio of such an algorithm. Second, such algorithms are not cooperative and thus fall out of the scope of this paper. The objective of this work is to study how heterogeneous defenders can be used to improve the competitive ratio of a single defender. Thus, in the next algorithm, although we partition the environment, the defenders are not restricted to remain within their own dominance region.
Algorithm 2. Split and Capture Algorithm
1 Turret is at angle 0
2 Vehicle is located at (x1, ϕ1)
3 for each epoch k do
4 Compute
5 if
6 Turn the turret clockwise to angle θ
7 Turn the turret back to angle 0
8 else
9 Turn the turret anti-clockwise to angle −θ
10 Turn the turret back to angle 0
11 end
12 if
13 if |
14 Move vehicle to
15 else
16 Keep vehicle at (xi, ϕi) and capture intruders in Sj+1i
17 Move vehicle to
18 end
19 else
20 Keep vehicle at (xi, ϕi) and capture intruders in
21 end
22 end
4.3 Split and capture (Split)
The motivation for this algorithm is to utilize the vehicle’s ability to move in any direction while the turret rotates either clockwise or anti-clockwise. Since the turret can only turn either clockwise or anti-clockwise, the idea is to first partition the environment into two-halves and turn the turret towards the side which has higher number of intruders. By doing so, we hope to capture at least half of the intruders by the turret, assuming they are sufficiently slow, that arrive in every epoch. Further, while the turret moves to capture intruders on one side, the vehicle moves to the other side to capture intruders, ensuring that the defenders jointly capture more than half of the intruders that arrive in the environment in every epoch. Algorithm Split is formally defined in Algorithm 2 and is summarized as follows where we first describe the motion of the turret in every epoch followed by that of the vehicle.
The heading angle of the turret is always
Let
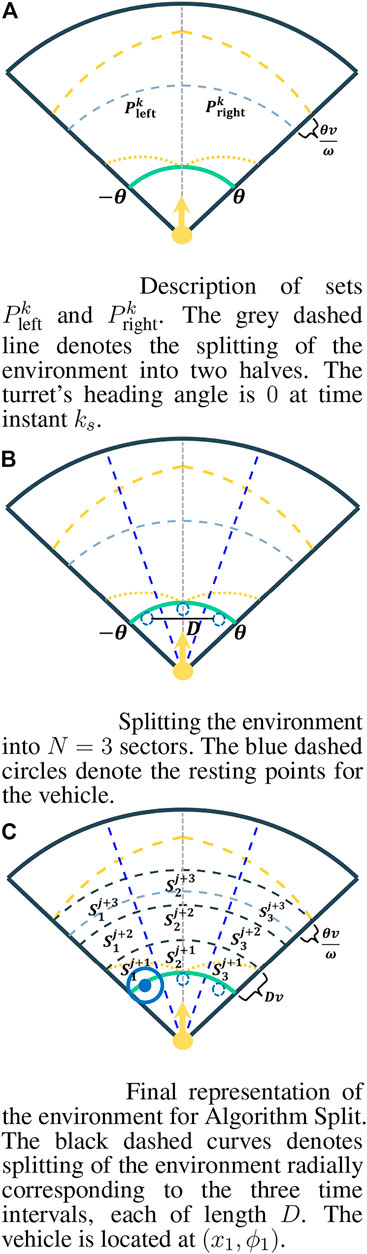
FIGURE 4. Description of Algorithm Split. The light grey dashed line denotes the splitting of the environment. The region between the yellow dashed curve and the yellow dot curve on the left (resp. right) side of the grey line denotes
Algorithm Split further divides the environment
Definition 2 (Resting points). Let Nl denote the lth sector, for every l ∈ {1, …, N} where N1 corresponds to the leftmost sector. Then, a resting point
Now, let D denote the distance between the two resting points that are furthest apart in the environment (see Figure 4B). Formally,
Observe that when N = 1, D = 0. This means that the vehicle captures all intruders that arrive in the environment by positioning itself to the unique resting point of the single sector.
Next, Algorithm Split radially divides the environment
Suppose that the vehicle is located at the resting point of sector Ni at the start of the jth epoch and let
Note that
We now describe comparison C2 jointly with the motion of the vehicle in the following two points:
• If the sector chosen as the outcome of C1 is No, o ≠ i, and the total number of intruders in the set
• If the sector chosen is Ni, then the vehicle stays at its current location (xi, ϕi) for 2D time units capturing intruders in
Note that the vehicle takes at most 2D time units in every case above. The vehicle then re-evaluates after 2D time. At time instant 0, the turret’s heading angle is 0 and the vehicle is located at (x1, ϕ1). The first epoch begins when the first intruder arrives in the environment.
We now describe two key requirements for the algorithm. The first requirement is to ensure that the defenders start their individual motion in an epoch at the same time instant. Recall that the turret requires exactly
Lemma 4.4. Any intruder with radial coordinate greater than
Proof. Without loss of generality, suppose that
The proof of Lemma 4.4 is established in the worst-case scenario which is that an intruder, with angular coordinate θ (resp. −θ), is located just above the range of the turret at the time instant when the turret’s heading angle is θ (resp. −θ) in an epoch k. This is because in an epoch k, the angle θ is the only heading angle that is visited by the turret once as the turret turns to all angles
Corollary 4.5: Suppose that the turret moves to capture intruders in
Recall that the adversary selects the release times and the locations of the intruders in our setup. Thus, with the information of the online algorithm, the adversary can release intruders such that all the intruders have their radial coordinates at most
For the vehicle, the requirement is that the intruders take at least 3D time units to reach the perimeter. This is to ensure that the vehicle can account for intruders that are very close to the perimeter at the start of an epoch. From Corollary 4.5, as the intruders with radial location greater than
Theorem 4.6: Let θs = arctan(rc/ρ) and
Proof. First observe that although the turret can capture intruders from one-half of the environment, the vehicle only captures at most two intervals out of all intervals that are in
If N is even then, the vehicle’s dominance region contains
Since at the start of every epoch k, the turret selects a dominance region based on the number of intruders on either side of the turret, it follows that the turret captures at least half of the total number of intruders that arrive in epoch k. This means that the turret captures intruders in all
Recall that the motion of the vehicle in Algorithm Split builds upon Algorithm SNP designed in (Bajaj et al., 2022), which was shown to be
Algorithm 3. Partition and Capture Algorithm
1 Turret’s heading angle is θ/3.
2 Vehicle is located at (zv, −θ/3).
3 for each epoch k ≥ 1 do
4 Compute
5 if |Ik| ≥
6 if |
7 Assign
8 else
9 Assign
10 end
11 else
12 if |
13 Assign Ik to the vehicle (resp. turret).
14 else
15 Assign
16 end
17 end
18 Turn the defenders in an angular motion to the respective endpoint of the assigned set.
19 Turn the defenders back to the initial position.
20 end
Remark 4.7 (Heterogeneity improves competitive ratio of Algorithm Split). The competitive ratio of Algorithm Split is at most 2, achieved when N → ∞. Further, for rt = 1, the parameter regime that required by Algorithm Split
Further note that if N is odd and N ≠ 1, then the competitive ratio of Algorithm Split is higher than that for N + 1. This is because when N is odd, the adversary can exploit the fact that there are higher number of intervals that the vehicle can lose as compared to that in the turret’s dominance region. Finally, for N = 2, Algorithm Split is 1-competitive. The explanation is as follows. For N = 2, the two sectors of the environment overlap the two dominance region. Thus, in this case, the turret captures all intruders in one dominance region while the vehicle remains stationary at the resting point of the second dominance region, ensuring that all intruders that are released in the environment are captured.
Given that the turret can only move clockwise or anti-clockwise and from the requirement that the defenders must start their motions at the same time instant, the parameter regime of Algorithm Split is primarily defined by the time taken by the turret to sweep its dominance region. This means that by reducing the time taken by the turret to complete its motion, it is possible to achieve an algorithm with higher parameter regime. This is exploited in our next algorithm which is provably 1.5-competitive.
4.4 Partition and capture (part)
Algorithm Part, formally defined in Algorithm 3, partitions the environment into three equal dominance region, each of angle
At the start of every epoch k, the turret’s heading angle, measured from the y-axis, is set to
Similarly, at the start of every epoch k, the vehicle is assumed to be located at
Let
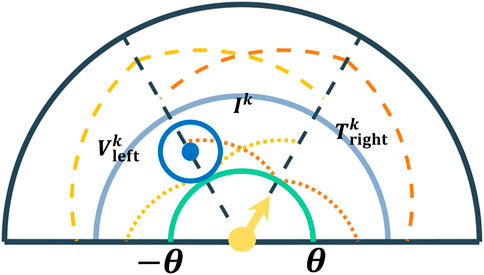
FIGURE 5. Description of Algorithm Part. The black dashed line denotes the partitioning of the environment, each of angle
We now describe the motion of the defenders. The objective is to move the defenders such that intruders from any two sets out of
Case 1: The set Ik contains maximum number of intruders, i.e.,
• If
• Otherwise, the vehicle is assigned the set Ik and the turret is assigned the set
Case 2:
• If
• Similarly, if
Once the sets are assigned, the vehicle turns as follows. If the set assigned to the vehicle is Ik, then the vehicle moves clockwise with unit speed in the direction perpendicular to its position vector until it reaches location
Before we describe the motion of the turret, we determine its angular speed to ensure that the defenders start an epoch at the same time instant. As we require that the defenders take the same amount of time to return to their starting locations in an epoch, we require that
We now describe the turret’s motion in an epoch. Similar to the motion of the vehicle, if the set assigned to the turret is Ik, then the turret turns to angle
Analogous to Lemma 4.4, we have the following lemma which ensures that any intruder that was not considered for comparison at the start of epoch k is considered for comparison at the start of epoch (k + 1).
Lemma 4: Any intruder which lies beyond the sets
Proof. The proof is analogous to the proof of Lemma 4.4 and has been omitted for brevity.
Corollary 4.9: Any intruder that lies beyond the set Ik at time instant ks will be contained in the set Ik+1 at the start of epoch (k + 1) if the conditions of Lemma 4.8 hold.
Proof. The proof directly follows from the fact that Lemma 4.8 holds for both the defenders and Ik represents the intersection of
Theorem 4.10: Algorithm Part is 1.5-competitive for any problem instance
Proof. Observe that from Lemma 4.8 and Corollary 4.9, every intruder is accounted for and no intruder that is not considered for comparison in a particular epoch is lost under the condition on v. Now, from the definition of Algorithm Part, the defenders are assigned two sets out of the total three in every epoch. Further, the assignment is carried out in a way that the sets with maximum number of intruders are assigned to the defenders in every epoch. Assuming that there exists an optimal offline algorithm that captures all intruders from all three sets then, from Definition 1, competitive ratio of Algorithm Part is at most
5 Numerical observations
We now provide numerical visualization of the bounds derived in this work and emphasize on the (v, ρ) and (ω, ρ) parameter regime. These plots allow the defenders to choose an appropriate online algorithm out of the four proposed, based on the values of the problem parameters.
5.1 (ω, ρ) Parameter regime
Figure 6 shows the (ω, ρ) parameter regime plot for fixed values of rt, rc, θ, and v and provides insights into the requirement of the angular speed ω for different values of the ρ. Note that the markers represent a lower bound on the angular speed of the turret.
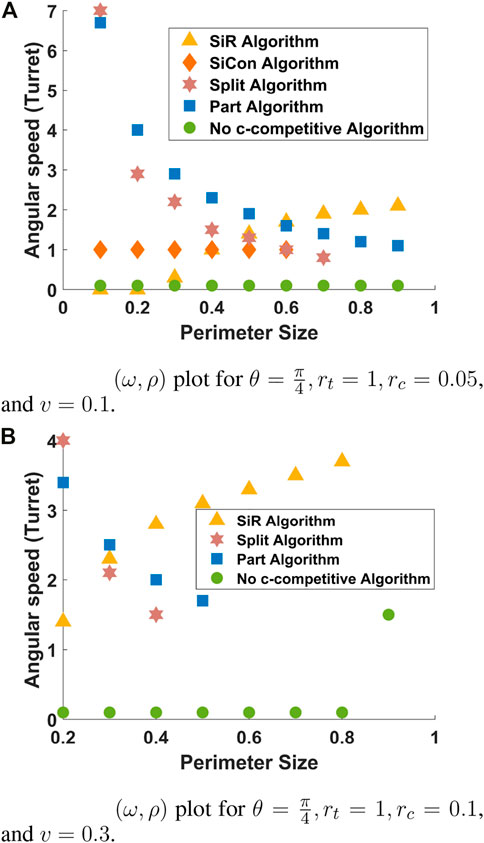
FIGURE 6.
In Figure 6A, the condition in Theorem 3.1 for the existence of c-competitive algorithms is represented by the green circles. For all values of 0.1 ≤ ρ ≤ 0.9, as the green circles are at ω = 0.1, it implies that there exists a c-competitive algorithm for all values of ω ≥ 0.1 and the values of v, rc, rt, and θ selected for this figure. We now provide insights into the requirement on ω for our algorithms. Algorithm SiR, represented by the yellow triangle, requires higher angular speed for the turret as the radius of the perimeter increases. However, Algorithm Split and Algorithm Part, represented by the red star and blue square respectively, require lower angular speed for the turret when the radius of the perimeter is sufficiently large. Although counter intuitive, this can be explained as follows. Recall that Algorithm Part and Algorithm Split require the two defenders to be synchronous and the vehicle moves with a fixed unit speed. As the perimeter size increases, the time taken by the vehicle to complete its motion increases, which in turn requires lower values of ω to ensure synchronicity. Observe that for ρ ≥ 0.8, there are no markers for Algorithm Split. This is because for ρ ≥ 0.8 and the values of θ, rt, rc, and v considered for this figure, the condition defined for Algorithm Split in Theorem 4.6 is not satisfied for any 0 < ω ≤ 7, implying that Algorithm Split is not c-competitive. Analogous conclusions can be drawn for Algorithms SiCon (resp. Part), represented by orange diamond (resp. blue square), for values of ρ ≥ 0.6 (resp. ρ ≥ 0.9). Finally, note that Algorithm SiCon requires ω ≥ 1 for all values of ρ ≤ 0.6. This is because in this algorithm, the turret is required to move with unit angular speed to maintain synchronicity with the vehicle.
Analogous observations can be drawn in Figure 6B. For instance, when ρ = 0.9 and ω ≥ 1.5, there always exists a c-competitive algorithm with a finite constant c. Equivalently, there does not exist a c-competitive algorithm for ω < 1.5, ρ = 0.9 and for the values of rt, rc, θ, and v selected. Similarly, as ρ increases, Algorithm SiR requires a faster turret whereas Algorithm Part and Algorithm Split can work with a slower turret to ensure synchronicity. Note that Algorithm Part and Split do not have markers beyond ρ = 0.6 and ρ = 0.5, respectively, which is lower than the values of ρ in Figure 6A. This implies that, although the values of rc are slightly higher than those in Figure 6A, it is more difficult to capture intruders given the higher value of v. Finally, there are no markers for Algorithm SiCon as it is not c-competitive for the values of parameters selected for this figure.
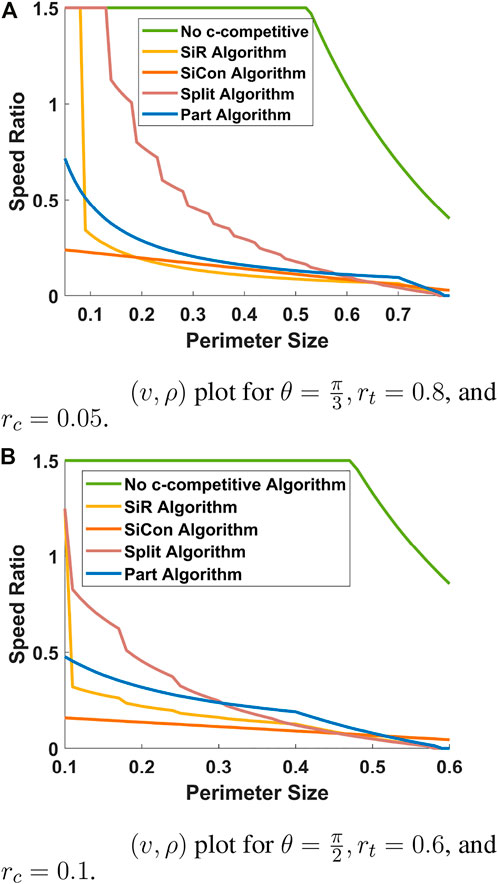
5.2 (v, ρ) Parameter regime
Figure 7 shows the (v, ρ) parameter regime for fixed values of θ, rc, and rt. Since, Algorithms Split, Part, SiCon require fixed but different values of ω, we set
Figure 7A shows the (v, ρ) parameter regime plot with θ, rt, and rc set to
Figure 7B shows the (v, ρ) parameter regime plot with θ, rt, and rc set to
6 Discussion
In this section, we provide a brief discussion on the time complexity of our algorithms and how this work extends to different models of the vehicle. We start with the time complexity of our algorithms.
6.1 Time complexity
We now establish the time complexity of each our algorithms and show that they can be implemented in real time if the information about the total number of intruders in every epoch is provided to the defenders.
Algorithm SiR and SiCon: Since Algorithm SiR and SiCon are open loop algorithms, the time complexity is O (1).
Algorithm Split: There are three quantities that must be computed at the start of every epoch of Algorithm Split, i.e.,
Algorithm Part: Similar to Algorithm Split, Algorithm Part computes
6.2 Different motion models for the vehicle
We now discuss how this work extends to different motion model of the vehicle.
Observe that the analysis in this work is based upon two quantities; first, the time taken by the intruders to reach the perimeter and second, the time taken by the defenders to complete the motion. This work can be extended to other models for the vehicle, for instance double integrator, by suitably modifying the time taken by the vehicle to complete its motion. By doing so, it may be that the parameter regimes may be lower than in Figure 7 but the bounds on the competitive ratios will remain the same. The reason that the parameter regimes will be lower is as follows. Note that the parameter regimes are characterized by the conditions determined for each of the algorithms. Essentially, these conditions are determined by requiring the intruders to be sufficiently slow such that they take more time to reach the perimeter than the time taken by the vehicle to complete its motion. For a different model of the vehicle, such as the Dubins model, the path and the time taken by the vehicle to complete its motion can be determined by suitably incorporating the turn radius. Precise dependence of the competitiveness of such realistic models will be a topic of a future investigation.
7 Conclusions and future extensions
This work analyzed a perimeter defense problem in which two cooperative heterogeneous defenders, a mobile vehicle with finite capture range and a turret with finite engagement range, are tasked to defend a perimeter against mobile intruders that arrive in the environment. Our approach was based on a competitive analysis that first yielded a fundamental limit on the problem parameters for finite competitiveness of any online algorithm. We then designed and analyzed four algorithms and established sufficient conditions that guaranteed a finite competitive ratio for each algorithm under specific parameter regimes.
Apart from closing the gap between the curve that represents Theorem 3.1 and the curve that represents Algorithm Split, key future directions include multiple heterogeneous defender scenarios with energy constraints. Analyzing the problem with a weaker model of the adversary, realistic motion motions, maneuvering intruders, or with asymmetric information are also potential extensions.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
SB contributed towards the problem formulation, algorithm design, conceptual analysis, the results and preparing the manuscript. AVM contributed towards problem formulation and the literature review section. DWC contributed towards the problem formulation. SDB and ET contributed towards evaluating and improving the analysis and the presentation. All authors contributed equally towards reading and revising the manuscript and approving the submitted version.
Funding
This research was supported by the Aerospace Systems Technology Research and Assessment (ASTRA) Aerospace Technology Development and Testing (ATDT) program at AFRL under contract number FA865021D2602. Approved for public release: distribution unlimited, case number: AFRL-2022-6028.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
1As the speed of the intruders is normalized by the speed of the vehicle, we use the speed of intruders and speed ratio interchangeably.
2The time taken by the defenders must be at most the time taken by the intruders to reach the perimeter.
3This case arises when the Algorithm Split moves the turret in the same direction for at least two consecutive epochs.
References
Adler, A., Mickelin, O., Ramachandran, R. K., Sukhatme, G. S., and Karaman, S. (2022). The role of heterogeneity in autonomous perimeter defense problems. arXiv preprint arXiv:2202.10433.
Akilan, Z., and Fuchs, Z. (2017). “Zero-sum turret defense differential game with singular surfaces,” in 2017 IEEE conference on control Technology and applications (CCTA), 2041–2048. doi:10.1109/CCTA.2017.8062754
Bajaj, S., and Bopardikar, S. D. (2019). “Dynamic boundary guarding against radially incoming targets,” in 2019 IEEE 58th conference on decision and control (CDC) (IEEE), 4804–4809.
Bajaj, S., Bopardikar, S. D., Torng, E., Moll, A. V., and Casbeer, D. W. (2022). Competitive perimeter defense with multiple vehicles. In IEEE transactions on robotics. Under Review.
Bajaj, S., Bopardikar, S. D., Von Moll, A., Torng, E., and Casbeer, D. W. (2022). “Perimeter defense using a turret with finite range and service times,” in 2023 American control conference (ACC) (IEEE).
Bajaj, S., Torng, E., and Bopardikar, S. D. (2021). “Competitive perimeter defense on a line,” in 2021 American control conference (ACC) (IEEE), 3196–3201.
Bajaj, S., Torng, E., Bopardikar, S. D., Von Moll, A., Weintraub, I., Garcia, E., et al. (2022). “Competitive perimeter defense of conical environments,” in 2022 IEEE 61st conference on decision and control (CDC) (IEEE), 6586–6593. doi:10.1109/CDC51059.2022.9993007
Bertsimas, D. J., and Van Ryzin, G. (1991). A stochastic and dynamic vehicle routing problem in the Euclidean plane. Operations Res. 39, 601–615. doi:10.1287/opre.39.4.601
Borodin, A., and El-Yaniv, R. (2005). Online computation and competitive analysis. Cambridge University Press.
Bullo, F., Frazzoli, E., Pavone, M., Savla, K., and Smith, S. L. (2011). Dynamic vehicle routing for robotic systems. Proc. IEEE 99, 1482–1504. doi:10.1109/jproc.2011.2158181
Chen, M., Zhou, Z., and Tomlin, C. J. (2016). Multiplayer reach-avoid games via pairwise outcomes. IEEE Trans. Automatic Control 62, 1451–1457. doi:10.1109/tac.2016.2577619
Deng, X., and Mirzaian, A. (1996). Competitive robot mapping with homogeneous markers. IEEE Trans. Robotics Automation 12, 532–542. doi:10.1109/70.508436
Francos, R. M., and Bruckstein, A. M. (2021). Search for smart evaders with swarms of sweeping agents. IEEE Trans. Robotics 38, 1080–1100. doi:10.1109/tro.2021.3104253
Garcia, E., Casbeer, D. W., Von Moll, A., and Pachter, M. (2020). Multiple pursuer multiple evader differential games. IEEE Trans. Automatic Control 66, 2345–2350. doi:10.1109/tac.2020.3003840
Garcia, E., Von Moll, A., Casbeer, D. W., and Pachter, M. (2019). “Strategies for defending a coastline against multiple attackers,” in 2019 IEEE 58th conference on decision and control (CDC) (IEEE), 7319–7324.
Guerrero-Bonilla, L., Nieto-Granda, C., and Egerstedt, M. (2021). “Robust perimeter defense using control barrier functions,” in 2021 international symposium on multi-robot and multi-agent Systems (MRS) (IEEE), 164–172.
Howard, A., Parker, L. E., and Sukhatme, G. S. (2006). Experiments with a large heterogeneous mobile robot team: Exploration, mapping, deployment and detection. Int. J. Robotics Res. 25, 431–447. doi:10.1177/0278364906065378
Isaacs, R. (1999). Differential games: A mathematical theory with applications to warfare and pursuit, control and optimization. Courier Corporation.
Kappel, K. S., Cabreira, T. M., Marins, J. L., de Brisolara, L. B., and Ferreira, P. R. (2020). Strategies for patrolling missions with multiple UAVs. J. Intelligent Robotic Syst. 99, 499–515. doi:10.1007/s10846-019-01090-2
Koveos, Y., Panousopoulou, A., Kolyvas, E., Reppa, V., Koutroumpas, K., Tsoukalas, A., et al. (2007). “An integrated power aware system for robotic-based lunar exploration,” in 2007 IEEE/RSJ international conference on intelligent robots and Systems (IEEE), 827–832.
Lee, E. S., Shishika, D., and Kumar, V. (2020). “Perimeter-defense game between aerial defender and ground intruder,” in 2020 59th IEEE conference on decision and control (CDC) (IEEE), 1530–1536.
Lee, Y., and Bakolas, E. (2021). “Optimal strategies for guarding a compact and convex target set: A differential game approach,” in 2021 60th IEEE conference on decision and control (CDC) (IEEE), 4320–4325.
Lykou, G., Moustakas, D., and Gritzalis, D. (2020). Defending airports from uas: A survey on cyber-attacks and counter-drone sensing technologies. Sensors 20, 3537. doi:10.3390/s20123537
Macharet, D. G., Chen, A. K., Shishika, D., Pappas, G. J., and Kumar, V. (2020). “Adaptive partitioning for coordinated multi-agent perimeter defense,” in 2020 IEEE/RSJ international conference on intelligent robots and Systems (IROS) (IEEE), 7971–7977.
Margellos, K., and Lygeros, J. (2011). Hamilton–Jacobi formulation for reach–avoid differential games. IEEE Trans. automatic control 56, 1849–1861. doi:10.1109/tac.2011.2105730
Ma’sum, M. A., Arrofi, M. K., Jati, G., Arifin, F., Kurniawan, M. N., Mursanto, P., et al. (2013). “Simulation of intelligent unmanned aerial vehicle (UAV) for military surveillance,” in 2013 international conference on advanced computer science and information Systems (ICACSIS), 161–166. doi:10.1109/ICACSIS.2013.6761569
McGee, T. G., and Hedrick, J. K. (2006). “Guaranteed strategies to search for mobile evaders in the plane,” in 2006 American control conference (IEEE), 2819–2824.
Ozsoyeller, D., Beveridge, A., and Isler, V. (2013). Symmetric rendezvous search on the line with an unknown initial distance. IEEE Trans. Robotics 29, 1366–1379. doi:10.1109/tro.2013.2272252
Ramachandran, R. K., Pierpaoli, P., Egerstedt, M., and Sukhatme, G. S. (2021). Resilient monitoring in heterogeneous multi-robot systems through network reconfiguration. IEEE Trans. Robotics 38, 126–138. doi:10.1109/tro.2021.3128313
Ramachandran, R. K., Preiss, J. A., and Sukhatme, G. S. (2019). “Resilience by reconfiguration: Exploiting heterogeneity in robot teams,” in 2019 IEEE/RSJ international conference on intelligent robots and Systems (IROS) (IEEE), 6518–6525.
Sabag, O., Lale, S., and Hassibi, B. (2022). “Competitive-ratio and regret-optimal control with general weights,” in 2022 IEEE 61st conference on decision and control (CDC) (IEEE), 4859–4864. doi:10.1109/CDC51059.2022.9993106
Santos, M., and Egerstedt, M. (2018). “Coverage control for multi-robot teams with heterogeneous sensing capabilities using limited communications,” in 2018 IEEE/RSJ international conference on intelligent robots and Systems (IROS) (IEEE), 5313–5319.
Shishika, D., and Kumar, V. (2020). “A review of multi agent perimeter defense games,” in International conference on decision and game theory for security (Springer), 472–485.
Sleator, D. D., and Tarjan, R. E. (1985). Amortized efficiency of list update and paging rules. Commun. ACM 28, 202–208. doi:10.1145/2786.2793
Smith, S. L., Bopardikar, S. D., and Bullo, F. (2009). “A dynamic boundary guarding problem with translating targets,” in Decision and control, 2009 held jointly with the 2009 28th Chinese control conference. CDC/CCC 2009 (IEEE), 8543–8548.
Tavakoli, M., Cabrita, G., Faria, R., Marques, L., and de Almeida, A. T. (2012). Cooperative multi-agent mapping of three-dimensional structures for pipeline inspection applications. Int. J. Robotics Res. 31, 1489–1503. doi:10.1177/0278364912461536
Von Moll, A., and Fuchs, Z. E. (2020). “Optimal constrained retreat within the turret defense differential game,” in 2020 IEEE conference on control Technology and applications (CCTA) (IEEE), 611–618.
Von Moll, A., and Fuchs, Z. (2021). “Turret lock-on in an engage or retreat game,” in American Control Conference. IEEE, 3188–3195. doi:10.23919/ACC50511.2021.9483106
Von Moll, A., Pachter, M., Shishika, D., and Fuchs, Z. (2022). Circular target defense differential games. Trans. Automatic Control 68. doi:10.1109/TAC.2022.3203357
Von Moll, A., Shishika, D., Fuchs, Z., and Dorothy, M. (2022). Turret–runner–penetrator differential game with role selection. Trans. Aerosp. Electron. Syst. 58, 5687–5702. doi:10.1109/TAES.2022.3176599
Yan, R., Shi, Z., and Zhong, Y. (2018). Reach-avoid games with two defenders and one attacker: An analytical approach. IEEE Trans. Cybern. 49, 1035–1046. doi:10.1109/tcyb.2018.2794769
Keywords: online optimization, perimeter defense, competitive ratio, pursuit evasion games, dynamic vehicle routing, cooperative agents
Citation: Bajaj S, Bopardikar SD, Moll AV, Torng E and Casbeer DW (2023) Competitive perimeter defense with a turret and a mobile vehicle. Front. Control. Eng. 4:1128597. doi: 10.3389/fcteg.2023.1128597
Received: 20 December 2022; Accepted: 18 January 2023;
Published: 27 February 2023.
Edited by:
Douglas Guimarães Macharet, Federal University of Minas Gerais, BrazilReviewed by:
Rui Yan, University of Oxford, United KingdomJonghoek Kim, Sungkyunkwan University, South Korea
Copyright © 2023 Bajaj, Bopardikar, Moll, Torng and Casbeer. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Shivam Bajaj, YmFqYWpzaGlAbXN1LmVkdQ==
 Shivam Bajaj
Shivam Bajaj Shaunak D. Bopardikar
Shaunak D. Bopardikar Alexander Von Moll
Alexander Von Moll Eric Torng
Eric Torng David W. Casbeer2
David W. Casbeer2