- 1Department of Electrical Engineering and Computer Sciences, University of California Berkeley, Berkeley, CA, United States
- 2Department of Biomedical Engineering and Computational Biology Program, Oregon Health and Science University, Portland, OR, United States
A timely, accurate, and secure dynamic state estimation is needed for reliable monitoring and efficient control of microgrids. The synchrophasor technology enables system operators to obtain synchronized measurements in real-time and to develop dynamic state estimators for monitoring and control of microgrids. However, in practice, sensor measurements can be corrupted or attacked. In this study, we consider an AC microgrid comprising several synchronous generators and inverter-interface power supplies, and focus on securely estimating the dynamic states of the microgrid from a set of corrupted data. We propose a secure dynamic state estimator which allows the microgrid operator to reconstruct the dynamic states of the microgrid from a set of attacked or corrupted data without any assumption on attacks or corruptions. Finally, we consider an AC microgrid with the same topology as the IEEE 33-bus distribution system, and show that the proposed secure estimation algorithm can accurately reconstruct the attack signals.
1 Introduction
Future distribution systems will include interconnected microgrids (Lasseter, 2002)- (Hatziagyriou et al., 2007). Such systems are designed to operate in a distributed fashion dealing with various dynamic phenomena with different time scales (Ilić and Liu, 1996)- (Kundur et al., 2004). The functionality of control systems in microgrids is highly dependent on state estimation schemes used to observe the system over time. Traditional energy management systems are using static state estimation schemes designed from steady-state models (Schweppe and Wildes, 1970) (Abur and Expósito, 2004). With the high penetration of distributed energy resources (DER) on the generation side, and flexible loads and new demand-response technologies on the demand side, static state estimation schemes will not be able to capture power systems’ dynamics accurately (Zhao et al., 2019). Dynamic state estimation schemes will be needed to accurately capture the system dynamics. Such state estimation schemes, designed based on dynamical models, will play a significant role in microgrid monitoring and control (Modir and Schlueter, 1981)- (Meliopoulos, 2017). In this paper, we focus on the design of dynamic state estimation schemes which are secure to cyber-physical attacks.
Large-scale integration of inverter-interfaced power supplies and distributed controls requires a widespread deployment of the synchrophasor technology and communication networks in future distribution systems. This will lead to high-volume data exchange between different controllers which will make microgrids vulnerable to cyber-physical attacks. Corrupted data in controllers can disrupt power generators’ synchrony and result in a network-wide instability. Several attack detection schemes have been proposed in recent years (Pasqualetti et al., 2012) (Liu et al., 2014a). With false-data injection attacks, disturbances are injected to sensors and actuators to disrupt the measurements and computed control inputs. While it is possible to identify misbehaving agents (Pasqualetti et al., 2012) (Pasqualetti et al., 2013), such solutions require full knowledge of the cyber layer and are hard to scale. In (Mo et al., 2014), the authors propose a computationally-efficient scheme to detect deception attacks on sensors. While such solutions enable us to detect cyber attacks efficiently, these solutions do not mitigate all possible adverse effects. Robust game-theoretic schemes can lead to conservative results (Alpcan and Basar, 2003) (Srikantha and Kundur, 2016).
Cyber attacks can be modeled as noise or disturbance to the system. Basseville et al. (Basseville and Nikiforov, 1993) use noise filtration techniques to detect and remove malicious attacks, and the authors in Jiao et al. (2016) develop disturbance attenuation methods for cyber attack detection. Notice that noise filtration or disturbance attenuation techniques operate under certain statistical properties, e.g., white Gaussian noise signal. However, in practice, cyber attacks can be deliberately designed by a malicious attacker. In Abhinav et al. (2018), the authors propose attack-resilient controls for synchronization of islanded microgrids. The authors study the effect of attacks on sensors and actuators, and numerically demonstrate the effectiveness of their distributed controls on a modified IEEE 34-bus system.
In recent years, several researchers have focused on state estimation with security guarantees for both linear and nonlinear dynamical systems (Fawzi et al., 2014) (Hu et al., 2018). The current literature on linear dynamical systems can be classified into two classes: noiseless measurements, and noisy measurements. For systems with noiseless measurements, the studies in (Fawzi et al., 2014) (Chang et al., 2018) show that the state of the system can be accurately reconstructed under certain conditions. For systems with noisy measurements, sparse attack vectors can be distinguished from the measurement noise under certain conditions (Shoukry et al., 2014) (Farahmand et al., 2011). In Hu et al. (2018), the authors focus on secure state estimation for two classes of nonlinear systems without any assumption on the sensor attacks. They assume that the set of attacked sensors or actuators can potentially change with time, and propose a secure state estimator for those nonlinear systems. Finally, they consider a power system comprising a set of synchronous generators and storage units connected to each other via a set of electrical lines. The authors assume that the storage units use feedback linearization controls, and then design a secure estimator that enables the system operator to securely estimate the dynamic states of the power grid, i.e., the states of the synchronous generators, under cyber-physical attacks and communication failures.
Several dynamic state estimators have been proposed in the literature. However, the existing dynamic state estimators have the following drawbacks:
1. Loads are considered to be quasi-static, i.e., load dynamics are neglected. Unlike large power systems, microgrids are small footprint power systems comprising distribution assets, DERs, and loads. DERs are typically of inverter-interfaced power supplies with no inertia. These resources respond to disturbances as fast as their controls, and hence dynamics of flexible loads and DERs are strongly coupled in microgrids. More precisely, load dynamics have significant transient impacts in microgrids (Zhang et al., 2016) (Haddadi et al., 2013).
2. Controllers are considered to have specific structure. For example, storage units are assumed to use feedback linearization controls in Hu et al. (2018). DERs can use several types of distributed and centralized control schemes (Yazdanian and Mehrizi-Sani, 2014) (Hooshyar and Iravani, 2017).
In summary, load dynamics cannot be neglected in securely estimating dynamic states, and controllers cannot be limited to any specific structure. To overcome these drawbacks, we addressed two drawbacks of existing dynamic state estimators; first we design a secure dynamic state estimator for AC microgrids without using any linearization techniques or reducing the microgrid into a network of oscillators. Second, we do not have any specific structure assumptions in controller.
In this study, we focus on secure dynamic state estimation in AC microgrids under cyber attacks or communication failures. We consider an AC microgrid comprising several synchronous generators, inverter-interfaced power supplies, and electric loads controlled via a central controller (i.e., the microgrid operator) and several local controllers. The controllers use phasor measurement units (PMU) to maintain the system’s reliability. Each bus is equipped with a controller, transceiver, and measurement unit so that the controller can exchange its information with other controllers. The transceivers send the feedback information to the microgrid operator via a communication network. We make the following assumptions:
A.1 The communication paths from the central controller to different buses are secured while other communication paths and PMUs are subject to cyber attacks.
A.2 The set of attacked PMUs or communication paths can change with time.
A.3 Attacks can follow any particular model.
Note that typically, central controllers are protected against cyber attacks strongly, and that local controllers are more vulnerable to cyber attacks (CIP Standards, 2020). Thus, assumption 1 is reasonable. Here we consider cyber attacks which corrupts the communication paths and affects measurement units.
A practical example of cyber attacks in which the set of attacked sensors can change with time is provided in Liu et al. (2014b).
The contributions of this study are summarized as follows:
1. We extend our previous work (Hu et al., 2018) to AC microgrids and propose a secure state estimator for reconstructing the dynamic states of an AC microgrid using a set of measurements that can be corrupted. The proposed estimators are computationally efficient and enable microgrid operators to reconstruct dynamic states without any assumptions on attacks or corruptions.
2. We then consider an AC microgrid with the same topology as the IEEE 33-bus distribution system, and demonstrate the effectiveness of our estimators in accurately reconstructing the attack or corruption signals with realistic attack scenarios.
The paper is organized as follows: In Section 2, we review the secure state estimation for linear dynamical systems and in Section 3, we introduce the microgrid model adopted in this work. In Section 4, we formulate the dynamic state estimation problem for AC microgrids, and propose a dynamic state estimator for recovering dynamic states. Finally, in Section 5, we demonstrate the effectiveness of the proposed estimator using the IEEE 33-bus distribution system.
2 Preliminaries
We first introduce the error correction problem and compressed sensing. We then describe secure state estimation for linear dynamical systems.
2.1 Compressed Sensing
Let
Notice that ||x||0 equals the number of non-zero entries of x. Lemma 1 provides a sufficient condition for obtaining a unique solution to Eq. 1.
Lemma 1. (Candes et al., 2006) If the sparsest solution to Eq. 1 has ||x||0 = q and m ≥ 2q and all subsets of 2q columns of A are full rank, then the solution is unique.
2.2 The Error Correction Problem
Consider a full rank coding matrix
Hence, the classical error correction techniques can be transformed into reconstructing a sparse error vector e from the measurement vector
2.3 Secure State Estimation for Linear Dynamical Systems
Consider a discrete-time linear system as follows:
where
Let
where
By following a two-step procedure Candes et al. (2006) and Hayden et al. (2016) we can now reconstruct the initial state x [0] from y [k]’s, where k = 0, … , K−1 First, we compute the error vector Eq,K, and then solve for x [0]. To compute Eq,K, we pre-multiply Eq. 4 by
Using the second block row, we have:
where
Here, we approximate the l0-minimization problem with an l1-minimization problem to obtain a convex decoder (Candes and Tao, 2005) (Tropp, 2004).
Using the first block row of Eq. 5, we can now compute x [0] as follows:
The following result provides the conditions under which exists a unique solution to Eq. 8. The proof follows by using Lemma 1 and the fact that the null space of
Lemma 2.Chang et al. (2018). There exists a unique solution x [0] if all subsets of 2s columns of
The role of Lemma 2 guarantees accurate decoding when the assumption holds.
3 System Model
We first introduce the physical layer model of an AC microgrid with generators and loads. We then describe the cyber layer over which the microgrid operator relies to control its DERs, and introduce the cyber attacks that we are considering in this study.
3.1 Physical Layer
Consider a microgrid with m + n + l buses. m of the m + n + l buses, indexed by
We use the standard structure-preserving model to describe the microgrid’s dynamics (Bergen and Hill, 1981). This model that incorporates the dynamics of generators’ rotor angle and response of load power output to frequency deviations, allows us to preserve the structure of the grid, i.e., no load bus elimination is made. We introduce fictitious buses representing the internal generation voltages for synchronous generators and inverter-interfaced power supplies. Each of these buses is connected to either a synchronous generator or inverter-interfaced power supply bus via reactances that account for transient reactances and connecting lines. These reactances can be considered as transmission lines (Sauer and Pai, 1998). Therefore, in the augmented network, the number of buses is 2(m + n) + l. We further denote the set of fictitious buses for synchronous generators and inverter-interfaced power supplies by
Let Vi and θi denote the voltage magnitude and phase angle of bus
where
The dynamics of inverter-based power supplies can similarly be represented by a constant voltage behind reactance model, augmented to include a frequency-droop controller. For an inverter-based power supply at fictitious bus
where Di (in s/rad) is the speed-droop characteristic slope of the power supply.
In general, the relationship between the real power drawn at load bus
Here, we ignore reactive powers for generators and loads. Notice that reactive power analysis is unnecessary in this study.
3.2 Cyber Layer
Each bus i is equipped with a controller, transceiver, and measurement unit that allow bus i to communicate with the central controller (i.e., the microgrid operator) as well as other bus controllers. As mentioned earlier, fictitious buses represent the internal generation voltages for synchronous generators and inverter-interfaced power supplies. Each inverter-interfaced power supply is equipped with a controller, transceiver, and measurement unit so that the inverter-interfaced power supply at fictitious bus i can measure and communicate its internal voltage phase angle.
The rotor angle of synchronous generators has an electro-mechanic nature, and hence it cannot be measured via electric measurement units. However, we can estimate rotor angle by using other electric parameters of synchronous generators. In the literature, several studies are addressing the problem of estimating the rotor angle of synchronous generators (Tripathy et al., 2010) (Venkatasubramanian and Kavasseri, 2004). Each synchronous generator is equipped with a controller, transceiver, and measurement unit, and that the measurement unit at bus i is using a rotor angle estimator to compute the internal voltage phase angle for the synchronous generator at bus i.
A communication network connects the local controllers and the microgrid operator. This network allows the local controllers to send their feedback information, including rotors’ speeds and voltage phase angles, to the central controller. It also allows the microgrid operator to send different control commands to the local controllers. In this study, we assume that the communication paths from the microgrid operator to the local controllers are secure while other paths are not secure. Note that typically, central controllers are protected against cyber attacks strongly, and that local controllers are more vulnerable to cyber attacks (CIP Standards, 2020). In particular, we consider the following attack types:
• Attack 1: an attack that corrupts the communication paths from the transceivers to the central controller.
• Attack 2: an attack that affects measurement units.
We further assume that the set of attacked measurements can change with time. To illustrate different attack types, we refer the reader to Figure 1.
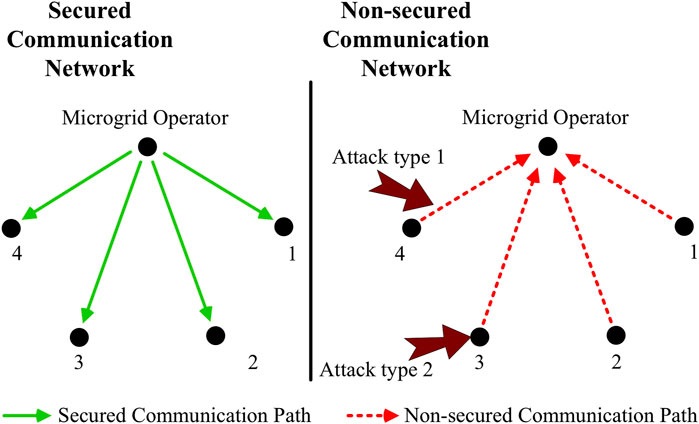
FIGURE 1. A graphical depiction of the cyber layer: consider a microgrid comprising four buses. The graph in left (sold lines) represents secured communication paths (i.e., communications path from the microgrid operator to bus controllers) while the graph in right (dotted lines) shows non-secured communication paths.
Next, we propose a secure dynamic state estimator for AC microgrids.
4 Secure State Estimation for AC Microgrids
Let us assume that the time is slotted in time slot of size δ. At each time slot k, the central controller receives the measured values of voltage phase angles, generators’ internal angles, and rotors’ speed. Let yi [k] denote the measurement vector received from bus
where ei [k] represents either a corruption or an attack signal injected by a malicious agent. In this study, the errors ei [k]’s do not follow any particular model. Hence,
Our goal is to reconstruct θi [k] for all
4.1 Discrete-Time System Model
We obtain a discrete-time approximation of the microgrid dynamics using the forward Euler discretization scheme. Let us begin with the synchronous generators, and use the same approach for inverter-interfaced power supplies and loads.
Synchronous Generators: For each synchronous generator at fictitious bus
where fij (θi[k], θj[k]) = γij[k] sin (θi[k] −θj[k] + ϕij),
Here we define some auxiliary variables for presentation purposes. There is no meaning to these parameters/variables. We defined the main variables and parameter in system model.
Notice that ωi,meas [k] equals
where
Notice that the coefficients of
Now, the state space model of the synchronous generator at fictitious bus
where the state vector
Notice that n(i) denotes the number of neighbors of node i in graph
Inverter-interfaced Power Supplies: The state space model of the inverter-interfaced power supply at fictitious bus
where xi [k] = θi [k] and
Loads: The state space model of the load at bus
where xi [k] = θi [k] and
4.2 Secure Dynamic State Estimator
Consider an enlarged system composed of all the system dynamics:
where
Consider K time slots k = 0, … , K−1, and collect the measurements corresponding the K time slots in vector
where
The number of columns of the matrix H [k] and the number of rows of the column vector ϵ [k] can be reduced from
Notice that we have γij [k] = γji [k] and ϕij = ϕji. Hence, the dimension of Ψ2 and
We now choose
where
In error correction, accurate decoding is guaranteed when the coding matrix (i.e.,
5 Numerical Results
Consider an AC microgrid comprising m = 3 synchronous generators, n = 25 inverter-interfaced power supplies, and l = 5 load buses. The microgrid topology is shown in Figure 2. This microgrid topology is a modified IEEE 33-bus distribution system from Baran and Wu (1989). Notice that in the augmented network, the number of buses is 61. The synchronous generator buses are buses
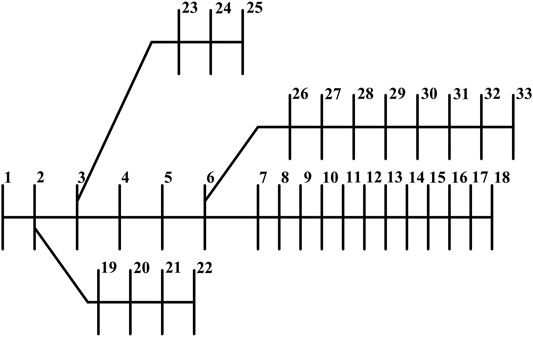
FIGURE 2. An AC microgrid comprising m = 3 synchronous generators, n = 25 inverter-interfaced power supplies, and l = 5 load buses.
The system is simulated for t = 20 s with a discretization step of δ = 1/60 seconds. We select the nominal loads
We demonstrate the effectiveness of our secure state estimation method through simulations of the two types of attacks:
1. Type A: attacks targeted at synchronous generators, i.e., measurements yi[k]’s, where
2. Type B: attacks targeted at inverter-interfaced power supplies, i.e., measurements yi [k]’s, where
For each of these attack types, we simulate three scenarios:
1. Scenario 1: There is no cyber attack on the microgrid.
2. Scenario 2: Measurements are attacked, and they are not protected by any secure state estimator.
3. Scenario 3: Measurements are attacked, and they are protected by the proposed dynamic state estimator.
5.1 Attack Type A: Synchronous Generator Attacks
The microgrid operator measures rotor angle from the three synchronous generator buses, and rotor angle and speed from the three fictitious synchronous generator buses. Hence, the operator has access to nine measurements that are subject to cyber attacks. We assume that from t = 1.1 s onwards, the attacker randomly chooses a set of five measurements out of the nine measurements and corrupts them with random signals at each time step. Figure 3 shows the simulation results for the three scenarios: 1) there is no attack (No Attack), 2) the measurements are attacked and they are not protected with any secure estimator (SE), and 3) the measurements are attacked and the microgrid operator uses the proposed SE. Notice that in Figure 3, we only show phase angles and rotor speeds of the three fictitious synchronous generator buses.
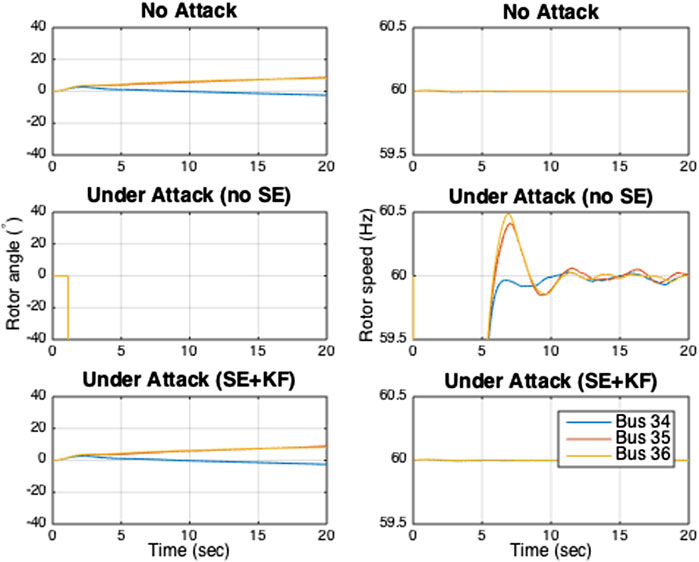
FIGURE 3. Phase angles and rotor speeds of the synchronous generators under attack Type A in the three scenarios.
In the microgrid without cyber attacks, the rotor speeds converge to 60 Hz after an initial transient period. As mentioned earlier, no secure estimation is used in Scenario 2 while the micorgrid operator uses the proposed secure state estimation to recover the system states in Scenario 3. Therefore, both rotor angles and speeds cannot be estimated correctly in Scenario 2, as shown in Figure 3. However, the operator can perfectly estimate both rotor angles and speeds in Scenario 3. Figure 4 shows the attack signal, secure estimator’s estimated attack signal, and the estimation error. The results show that the proposed dynamic state estimator accurately estimates the system state. Hence, the system’s dynamics are identical to the system without any attacks.
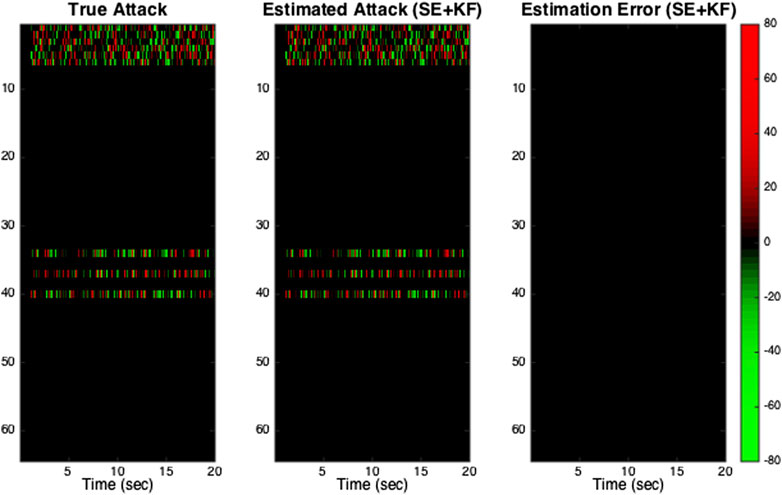
FIGURE 4. True and estimated attack signals: The rows and columns correspond to measurements and time steps, respectively. In the subfigures, the color indicates the attack signal: red is an attack with positive value, green is an attack with negative value, and black is no attack. Only measurements of the synchronous generators buses and their corresponding fictitious buses are corrupted by the attack. Notice that measurements 1–6 correspond to rotor angle and speed measurements from the fictitious synchronous generator buses, and measurements 34, 37 and 40 correspond to phase angle measurements from the synchronous generator buses. In subfigure “Estimation Error”, the black color indicates there is zero estimation error for all measurements at all times.
5.2 Attack Type B: Inverter-Interfaced Power Supply Attacks
The microgrid operator measures phase angles from the inverter-interfaced power supply buses. Hence, the operator has access to 50 measurements that are subject to cyber attack: 25 correspond to phase angle measurements of the inverter-interfaced power supply buses and 25 correspond to the phase angle measurements of the corresponding fictitious buses. We assume that from t = 1.1 s onwards, the attacker randomly chooses a set of five measurements out of the 50 measurements and corrupts them with random signals at each time step. The simulation results are shown in Figure 5 and Figure 6. The results show that both phase angles and rotor speeds are severely affected when the measurements are attacked and no secure estimator is used by the operator. However, the microgrid operator can perfectly recover the attack signals and restore the system’s normal dynamics as if there was no attack when secure state estimation is used.
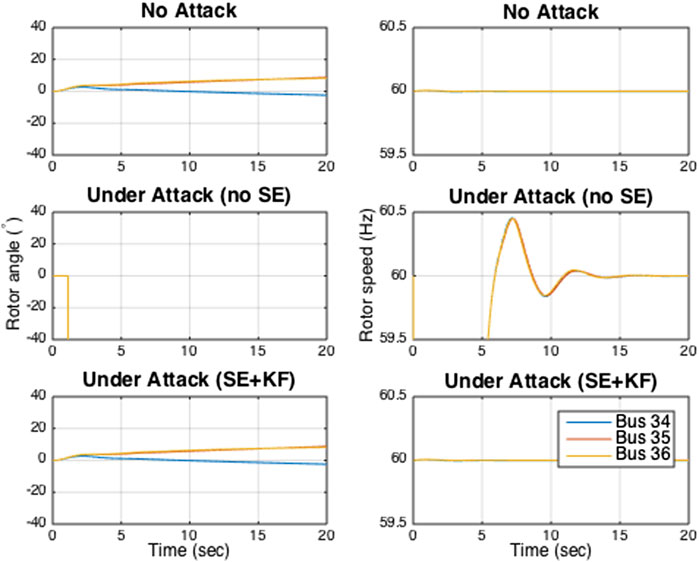
FIGURE 5. Phase angles and rotor speeds of the synchronous generators under attack Type B in the three scenarios.
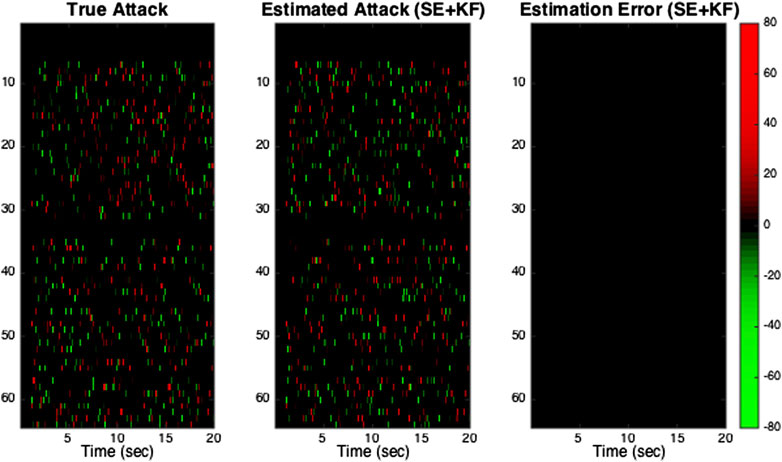
FIGURE 6. True and estimated attack signals: The rows and columns correspond to measurements and time steps, respectively. In the subfigures, the color indicates the attack signal: red is an attack with positive value, green is an attack with negative value, and black is no attack. Only measurements of the inverter-interfaced power supply buses and their corresponding fictitious buses are corrupted by the attack. In subfigure “Estimation Error”, the black color indicates there is zero estimation error for all measurements at all times.
6 Conclusion
We propose a secure state estimator for dynamic state estimation in AC microgrids under cyber physical attacks. We show that the microgrid operator can perfectly reconstruct the dynamic states in its AC microgrid using our estimator. We envision that the proposed approach ensures microgrid resilience and enables secure microgrid operations.
Data Availability Statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
1Without loss of generality, we consider tie-line buses that connect the microgrid to the grid, as load buses
References
Abhinav, S., Modares, H., Lewis, F. L., Ferrese, F., and Davoudi, A. (2018). “Synchrony in Networked Microgrids under Attacks,”. IEEE Trans. on Smart Grid. 9 (6), 6731–6741. doi:10.1109/tsg.2017.2721382
Abur, A., and Expósito, A. G. (2004). Power System State Estimation: Theory and Application. Marcel Dekker.
Alpcan, T., and Basar, T. (2003). A Game Theoretic Approach to Decision and Analysis in Network Intrusion Detection. Proc. 42nd IEEE Conf. Decis. Control. 3, 2595–2600. doi:10.1109/cdc.2003.1273013
Angel, A. D., Geurts, P., Ernst, D., Glavic, M. G., and Wehenkel, L. (2007). Estimation of Rotor Angles of Synchronous Machines Using Artificial Neural Networks and Local PMU-Based Quantities. Int. J. Neurocomput. 70 (16–18), 2668–2678. doi:10.1016/j.neucom.2006.12.017
Baran, M. E., and Wu, F. F. (1989). Network Reconfiguration in Distribution Systems for Loss Reduction and Load Balancing. IEEE Trans. Power Deliv. 4 (2), 1401–1407. doi:10.1109/61.25627
Basseville, M., and Nikiforov, I. V. (1993). Detection of Abrupt Changes: Theory and Application. Prentice Hall Englewood Cliffs. Vol. 104.
Bergen, A. R., and Hill, D. J. (1981). “A Structure Preserving Model for Power System Stability Analysis,” Power Apparatus And Systems. IEEE Trans. 1, 25–35. doi:10.1109/tpas.1981.316883
Bi, S., and Zhang, Y. J. (2014). Graphical Methods for Defense against False-Data Injection Attacks on Power System State Estimation. IEEE Trans. Smart Grid. 5 (3), 1216–1227. doi:10.1109/tsg.2013.2294966
Candes, E. J., and Tao, T. (2005). Decoding by Linear Programming. IEEE Trans. Info. Theor. 51 (12), 4203–4215. doi:10.1109/tit.2005.858979
Candes, E., Romberg, J., and Tao, T. (2006). Stable Signal Recovery From Incomplete and Inaccurate Measurements. Commun. Pure Appl. Math. 59 (8), 1207–1223. doi:10.1002/cpa.20124
Chang, Y. H., Hu, Q., and Tomlin, C. J. (2018). Secure Estimation Based Kalman Filter for Cyber Physical Systems against Sensor Attacks. Automatica. 95, 399–412. doi:10.1016/j.automatica.2018.06.010
CIP Standards (2020). Critical Infrastructure Protection. Available at: http://www.nerc.com/pa/Stand/Pages/CIPStandards.aspx.
Donoho, D. L., and Elad, M. (2003). Optimally Sparse Representation in General (Nonorthogonal) Dictionaries via L1 Minimization. Proc. Natl. Acad. Sci. 100 (5), 2197–2202. doi:10.1073/pnas.0437847100
Elad, M., and Bruckstein, A. M. (2002). A Generalized Uncertainty Principle and Sparse Representation in Pairs of Bases. IEEE Trans. Inf. Theor. 48 (9), 2558–2567. doi:10.1109/tit.2002.801410
Farahmand, S., Giannakis, G. B., and Angelosante, D. (2011). Doubly Robust Smoothing of Dynamical Processes via Outlier Sparsity Constraints. IEEE Trans. Signal. Process. 59 (10), 4529–4543. doi:10.1109/tsp.2011.2161300
Fawzi, H., Tabuada, P., and Diggavi, S. (2014). Secure Estimation and Control for Cyber-Physical Systems Under Adversarial Attacks. IEEE Trans. Automatic Control. 59 (6), 1454–1467. doi:10.1109/tac.2014.2303233
Gribonval, R., and Nielsen, M. (2003). Sparse Representations in Unions of Bases. IEEE Trans. Inf. Theor. 49 (12), 3320–3325. doi:10.1109/tit.2003.820031
Haddadi, A., Yazdani, A., Joos, G., and Boulet, B. (2013). A Generic Load Model for Simulation Studies of Microgrids. Proc. IEEE Power Energ. Soc. Gen. Meet., 1–5. doi:10.1109/pesmg.2013.6672962
Hatziagyriou, N., Asano, H., Iravani, R., and Marnay, C. (2007). MicroGrids. IEEE Power Energ. Mag. 5 (4), 78–94. doi:10.1109/MPAE.2007.376583
Hayden, D., Chang, Y. H., Goncalves, J., and Tomlin, C. (2016). Sparse Network Identifiability via Compressed Sensing. Automatica. 68, 9–17. doi:10.1016/j.automatica.2016.01.008
Hooshyar, A., and Iravani, R. (2017). Microgrid Protection. Proc. IEEE. 105 (7), 1332–1353. doi:10.1109/jproc.2017.2669342
Hu, Q., Fooladivanda, D., Chang, Y. H., and Tomlin, C. J. (2018). Secure State Estimation and Control for Cyber Security of the Nonlinear Power Systems. IEEE Trans. Control. Netw. Syst. 5 (3), 1310–1321. doi:10.1109/tcns.2017.2704434
Ilić, M., and Liu, S. (1996). Hierarchical Power Systems Control: Its Value in a Changing Industry. Springer.
Jiao, Q., Modares, H., Lewis, F. L., Xu, S., and Xie, L. (2016). “Distributed ℓ2-Gain Output-Feedback Control of Homogeneous and Heterogeneous Systems. Automatica. 71, 361–368. doi:10.1016/j.automatica.2016.04.025
Kundur, P., Paserba, J., Ajjarapu, V., Andersson, G., Bose, A., Canizares, C., et al. (2004). Definition and Classification of Power System Stability IEEE/CIGRE Joint Task Force on Stability Terms and Definitions. IEEE Trans. Power Syst. 19 (3), 1387–1401. doi:10.1109/tpwrs.2004.825981
Lasseter, R. (2002). MicroGrids. IEEE Power Eng. Soc. Winter Meet. 1, 305–308. doi:10.1109/PESW.2002.985003
Liu, L., Esmalifalak, M., Ding, Q., Emesih, V. A., and Han, Z. (2014a). Detecting False Data Injection Attacks on Power Grid by Sparse Optimization. IEEE Trans. Smart Grid. 5 (2), 612–621. doi:10.1109/tsg.2013.2284438
Liu, S., Chen, B., Zourntos, T., Kundur, D., and Butler-Purry, K. (2014b). A Coordinated Multi-Switch Attack for Cascading Failures in Smart Grid. IEEE Trans. Smart Grid. 5 (3), 1183–1195. doi:10.1109/tsg.2014.2302476
Manandhar, K., Cao, X., Hu, F., and Liu, Y. (2014). Detection of Faults and Attacks Including False Data Injection Attack in Smart Grid Using Kalman Filter. IEEE Trans. Control. Netw. Syst. 1 (4), 370–379. doi:10.1109/tcns.2014.2357531
Meliopoulos, A. P. S. (2017). Dynamic State Estimation-Based Protection: Status and Promise. IEEE Trans. Power Deliv. 32 (1), 320–330. doi:10.1109/tpwrd.2016.2613411
Mo, Y., Chabukswar, R., and Sinopoli, B. (2014). Detecting Integrity Attacks on Scada Systems. IEEE Trans. Control. Syst. Technol. 22 (4), 1396–1407. doi:10.1109/tcst.2013.2280899
Modir, H., and Schlueter, R. (1981). A Dynamic State Estimator for Dynamic Security Assessment. IEEE Trans. Power Apparatus Syst. PAS-100 (11), 4644–4652. doi:10.1109/tpas.1981.316806
Pajic, M., Weimer, J., Bezzo, N., Tabuada, P., Sokolsky, O., Lee, I., et al. (2014). Robustness of Attack-Resilient State Estimators. In ACM/IEEE International Conference on Cyber-Physical Systems. ICCPS). doi:10.1109/iccps.2014.6843720
Pasqualetti, F., Bicchi, A., and Bullo, F. (2012). Consensus Computation in Unreliable Networks: A System Theoretic Approach. IEEE Trans. Autom. Control. 57 (1), 90–104. doi:10.1109/tac.2011.2158130
Pasqualetti, F., Dorfler, F., and Bullo, F. (2013). Attack Detection and Identification in Cyber-Physical Systems. IEEE Trans. Autom. Control. 58 (11), 2715–2729. doi:10.1109/tac.2013.2266831
Sauer, P. W., and Pai, M. A. (1998). Power System Dynamics and Stability. Upper Saddle River, NJ, USA: Prentice-Hall.
Schweppe, F., and Wildes, J. (1970). Power System Static-State Estimation, Part I: Exact Model. IEEE Trans. Power Apparatus Syst. PAS-89 (1), 120–125. doi:10.1109/tpas.1970.292678
Shoukry, Y., and Tabuada, P. (2015). Event-Triggered State Observers for Sparse Sensor Noise/Attacks. IEEE Trans. Automatic Control. 99, 1–13. doi:10.1109/TAC.2015.2492159
Srikantha, P., and Kundur, D. (2016). A DER Attack-Mitigation Differential Game for Smart Grid Security Analysis. IEEE Trans. Smart Grid. 7 (3), 1476–1485. doi:10.1109/tsg.2015.2466611
Shoukry, Y., Nuzzo, P., Puggelli, A., Sangiovanni-Vincentelli, A. L., Seshia, S. A., and Tabuada, P. (2014). “Secure State Estimation for Cyber Physical Systems under Sensor Attacks: a Satisfiability Modulo Theory Approach,” arXiv pre-print.
Tripathy, P., Srivastava, S. C., and Singh, S. N. (2010). A Divide-by-Difference-Filter Based Algorithm for Estimation of Generator Rotor Angle Utilizing Synchrophasor Measurements. IEEE Trans. Instrumentation Meas. 59 (6), 1562–1570. doi:10.1109/tim.2009.2026617
Tropp, J. A. (2004). Greed Is Good: Algorithmic Results for Sparse Approximation. IEEE Trans. Inf. Theor. 50 (10), 2231–2242. doi:10.1109/tit.2004.834793
Venayagamoorthy, G. K., and Harley, R. G. (2005). MLP/RBF Neural-Networkbased Online Global Model Identification of Synchronous Generator. IEEE Trans. Ind. Electron. 52 (6), 1685–1695. doi:10.1109/tie.2005.858703
Venkatasubramanian, V., and Kavasseri, R. G. (2004). Direct Computation of Generator Internal States from Terminal Measurements. Proc. 37th Annu. Hawaii Int. Conf. Syst. Sci., 6. doi:10.1109/hicss.2004.1265193
Yazdanian, M., and Mehrizi-Sani, A. (2014). “Distributed Control Techniques in Microgrids,”. IEEE Trans. Smart Grid. 5 (6), 2901–2909. doi:10.1109/tsg.2014.2337838
Zhang, X., Chen, J., and Wang, C. (2016). Stability Analysis of Islanded Microgrids With Dynamic Loads. Proc. IEEE 14th Int. Conf. Control Automation, Robotics, Vis. 1–6. doi:10.1109/icarcv.2016.7838765
Keywords: distribution systems, secure estimation, AC microgrids, cyber security, IEEE 33-bus distribution system
Citation: Fooladivanda D, Hu Q and Chang YH (2021) Secure Dynamic State Estimation for Cyber Security of AC Microgrids. Front. Control. Eng. 2:734220. doi: 10.3389/fcteg.2021.734220
Received: 30 June 2021; Accepted: 03 August 2021;
Published: 18 August 2021.
Edited by:
Dan Ma, Northeastern University, ChinaReviewed by:
Bo Chen, Zhejiang University of Technology, ChinaShicheng Huo, Southeast University, China
Copyright © 2021 Fooladivanda, Hu and Chang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Young Hwan Chang, Y2hhbnlvQG9oc3UuZWR1
†These authors have contributed equally to this work
 Dariush Fooladivanda1†
Dariush Fooladivanda1† Young Hwan Chang
Young Hwan Chang