
94% of researchers rate our articles as excellent or good
Learn more about the work of our research integrity team to safeguard the quality of each article we publish.
Find out more
REVIEW article
Front. Blockchain, 16 May 2019
Sec. Blockchain for Web3 and the Metaverse
Volume 2 - 2019 | https://doi.org/10.3389/fbloc.2019.00003
About a decade ago the fundamental operating principle of the Blockchain was introduced. It took several years before the technology gained widespread recognition in industry and academic communities outside of the computer science sphere. Since then many academic communities have taken up the topic, but so far no well-defined research agenda has emerged: research topics are scattered and rigorous approaches are scarce. More often than not, use cases implemented by industry apply a trial and error approach and there exists a dearth of theory-based academic papers on the topic following robust methodologies. Being a nascent research topic, case studies on Blockchain applications are a suitable approach to systematically transfer industry experience into research agendas which benefit both theory development and testing as well as design science research. In this paper I offer guidelines and suggestions on how to design and structure Blockchain case studies to create value for academia and the industry. More specifically, I describe Blockchain characteristics and challenges, present existing Blockchain case studies, and discuss various types of case study research and how they can be useful for industry and academic research. I conclude with a framework and a checklist for Blockchain case study research.
Within roughly a decade the Blockchain has shifted from a rather obscure and poorly understood topic into a phenomenon that has gained widespread mass media attention and attracts academics and practitioners alike. The growth in size of selected Blockchain networks, as measured by the number of unique addresses participating in daily activities, exhibits an exponential development following Metcalfe's law (Alabi, 2017). In spite of a sharp drop in the prices of Bitcoin and other cryptocurrencies at the end of the year 2017, the general Blockchain market size is still estimated to grow from USD 242 million in 2016 to USD 7,684 million by 2022, at a compound annual growth rate of 79.6% (MarketsandMarkets., 2017).
The emergence of Blockchain publications in leading academic journals has shown a substantial time lag in comparison to industry adoption. Outside of the computer science and cryptography communities, the first academic journal publications discussing Bitcoin appeared around 2012, followed by papers dealing with the Blockchain and DLT (Distributed Ledger Technology) around 2015. This delay has partly to do with lengthy review cycles of top-tier academic journals, but also with the complexity of the technology in combination with poorly understood and unclear use cases. This situation has changed with the emergence of publications targeting a broader audience, in which the authors speculate about potential application scenarios for the technology (Swan, 2015; Tapscott and Tapscott, 2016; Iansiti and Lakhani, 2017). Many of the suggested use cases are far-reaching in terms of their potential implications and cover a wide range of industries and applications, including financial services, transportation and supply chain management, media and entertainment, education, tourism, public services, consumer services, voting, and academic peer reviews (Yli-Huumo et al., 2016; Bahga and Madisetti, 2017; Lacity, 2018a; Önder and Treiblmaier, 2018; Treiblmaier, 2018; Treiblmaier and Beck, 2019a,b).
The relevance of the Blockchain for the Information Systems community is 2-fold. First, researchers with an interest in the implications of the technology may want to better understand the behavioral (on an individual, group, and organizational level) and economic impacts of the Blockchain as well as its antecedents. Second, design science researchers may want to focus on the application of Blockchain technology to design and implement novel and innovative artifacts, which also includes the potential transformation of software development and business processes (Sillaber et al., 2018). While academia focuses largely on enhancing and refining existing frameworks and theories, as well as creating new ones, the industry needs advice and practical solutions.
The current lack of long-term experience with the Blockchain is aggravated by the fact that the technology is not yet mature, and therefore still under development. In their search for barriers to Blockchain adoption, Holotiuk et al. (2018) identified the lack of Blockchain use cases as a key challenge. A well-structured research agenda that encourages the systematic and comprehensive documentation of the findings of Blockchain case studies is therefore needed to ensure the cumulative compilation of knowledge and to provide guidance for the industry. Ideally, such a research agenda builds on previous research and allows for the comparability and straightforward integration of new findings. Given the flexibility and broad applicability of case studies (Cavaye, 1996), they are well-suited for investigating nascent phenomena and structuring a research domain. They have the potential to bring together academic rigor and practical relevance, while simultaneously ensuring a substantial amount of methodological freedom (Yin, 2014; Ridder, 2017).
Beck et al. (2017) suggest a list of Blockchain research topics for the IS community, including new business models, disruption, implementation types, sustainability issues, organizational implications, application development, Internet of Things (IoT) applications, challenges of implementing business logic, and limits of applications. Notably, all of these topics can be investigated with the help of carefully designed, executed and documented case studies. Existing Blockchain case studies are rare and are often published as anecdotes without a clearly defined structure, which makes it hard to critically evaluate them and to use them as a solid basis for further research or recommendations for the industry. It is therefore my goal to provide suggestions on how anecdotal evidence can be turned into systematic knowledge by considering the principles and guidelines of academic case study research.
In section Blockchain: Definitions, Characteristics and Challenges I present definitions, characteristics and challenges of the Blockchain, to lay a foundation for the remainder of this paper. In section Case Study Research and the Blockchain I differentiate between four types of theory-based case study research, each of which has its respective strengths and weaknesses, and provide an overview of existing Blockchain case studies, which cover one or more use cases, respectively. In section Designing and Reporting Blockchain Case Studies I present a generic framework for Blockchain case study research, followed by a proposed structure for systematic Blockchain case study papers. I end the paper with a brief conclusion in section Conclusion.
The Blockchain is a technology, or rather a combination of technologies (Narayanan and Clark, 2017), that is still under development. In a recent white paper the IEEE states that the “Blockchain, as an industry, has entered its Cambrian phase” (Peck, 2017, p. 1), alluding to the rapid diversification of various life forms during that period.
The term Blockchain originates from the original description of Bitcoin by the mysterious author (or group of authors) identified as Satoshi Nakamoto (2008). Nakamoto never actually uses the term “Blockchain” in his/her/their seminal paper, but instead describes how transactions, hashes, and nonces can be grouped together into a block-based data structure in which the single blocks are chained together by including the hash of a previous block. Since then, the term Blockchain has gained widespread public attention and is most commonly used to denote what can be more loosely described as “trustless systems,” indicating that the amount of trust required of individual actors is minimized. Most authors, however, do not care so much about a chain of blocks, but rather about the underlying characteristics of the technology which facilitate the creation of decentralized systems whose functioning does not necessitate specific trustworthy entities. It therefore makes sense to also consider the broader term “Distributed Ledger Technology” (DLT) in any paper dealing with the Blockchain in order to also include technologies that do not exhibit a chain-like structure, such as, for example, Tangle, a directed acyclic graph (DAG) used by IOTA, which entangles a stream of individual transactions. Another solution based on directed acyclic graphs is Hashgraph, a DLT with a consensus mechanism that does not rely on an energy-consuming proof-of-work mechanism. The major advantage of avoiding a linear block chain lies mainly in the faster throughput of the transactions (Schueffel, 2017).
Table 1 lists several Blockchain and DLT definitions. The core of every Blockchain/DLT system is the distributed storage of data across multiple ledgers that can be spread across institutions and countries. While Meiklejohn et al. (2016) specifically refer to the Bitcoin Blockchain, all other definitions are more generic. The key characteristics include the distributed nature of the Blockchain, the immutability of the data, and the necessity of achieving consensus on which transactions are to be recorded. Each of these characteristics, and several others, are discussed in more detail in the following section. To date, no generally accepted definition of the Blockchain has emerged. It is therefore necessary to clearly describe the type of Blockchain/DLT being used in a specific case study and to outline the reasons for that particular choice.
The characteristics of the Blockchain, some of which might be only assumed or are currently under debate for technological, economic, business-related or legal reasons (Hoelscher, 2018; Kim and Justl, 2018; Posadas, 2018), enable a wide variety of applications across multiple industries. Table 2 lists important characteristics of the Blockchain that emerged from a review of the literature as well as from interviews I personally conducted with 24 experts between January and February 2018. The interviews each lasted between 12 and 23 min. All interviews were recorded, transcribed and analyzed according to recognized standards for qualitative content analysis and grounded theory development (Glaser and Strauss, 1967; Hsieh and Shannon, 2005). The experts were chosen from the member directory of a large Blockchain interest group in Austria and included representatives of organizations from various industries (e.g., finance, energy, transportation), interest groups, consulting agencies, governmental institutions and educational institutions. All of the interview partners had substantial previous experience with Blockchain technology, such as the implementation and evaluation of diverse use cases, industry consulting projects, or the mining of cryptocurrencies. More details can be found in Treiblmaier and Umlauff (2019).
The shown characteristics might not apply equally well to all types of Blockchain manifestations. A permissioned Blockchain run by members of a consortium, for example, represents a rather closed ecosystem with clearly defined participants and control structures that are (partly) centralized, which contrasts with permissionless Blockchains that offer free access for anyone. The inherent differences between these systems have repercussions regarding issues such as privacy, throughput, and the choice of consensus mechanisms.
Immutability is frequently mentioned as the central characteristic of the Blockchain, since it allows for the transformation of the “Internet of Information,” in which digital data can be copied without loss of accuracy, into the “Internet of Value,” in which units representing value can be transferred between peers and double spending can be prevented. Immutability is also highly desirable if transactions need to be tracked along the supply chain. However, this property comes at a cost. If data needs to be changed, which might be due to legal reasons (Posadas, 2018), the Blockchain does not pose the most efficient data structure to do so. Furthermore, participation in public Blockchains is pseudonymous (or pseudo-anonymous), not anonymous, which raises privacy issues as it does not preclude identification (Meiklejohn et al., 2016).
The transparency of Blockchains is achieved by allowing users read-only access to previous transactions and to inspect the content of smart contracts. This is especially important if products need to be tracked along the supply chain (Kshetri, 2018). Again, it is crucial to differentiate between permissioned and permissionless Blockchains, with the former being run by members of a consortium and access thus restricted. In contrast, permissionless Blockchains, such as Bitcoin, allow for the inspection of blocks by everyone. While transparency and accountability are desirable in many instances, this might not hold true for all use cases. For example, private users might be concerned about sensitive personal data, and organizations might fear the leakage of confidential financial information.
The programmability of the Blockchain has rapidly improved in recent years. Bitcoin uses a basic scripting language, called Script, which intentionally avoids complex operations such as loops. In order to overcome this perceived limitation, the platform Ethereum (Wood, 2014) introduced a Turing complete language called Solidity, which is currently the most popular language for the creation of so-called smart contracts (Szabo, 1997): self-executing computer programs that execute in a deterministic and pre-defined way. However, this deterministic execution frequently lacks the flexibility needed in legal contracts and highlights the difficulties of reducing contractual relationships and the complexities of the real world into computer code (Mik, 2017).
One of the most frequently cited characteristics of the Blockchain is its decentralized nature. This is not only true for the storage of data, but also for decision making and governance. Again, differences between Blockchain types exist, but in general no central authority is needed to validate transactions between peers. This leads to disintermediation, which, depending on the perspective, can be seen as both an advantage and a disadvantage. New governance structures can help to create more effective and efficient organizational structures and to reduce transaction costs. At the same time, disintermediation may be seen as a major threat for incumbents who hold strategic positions in existing supply chains and value networks (Treiblmaier, 2018).
Decentralization is made possible by innovative consensus protocols across a network of nodes. Such protocols make sure that the task of compiling transactions and creating new blocks follows strict rules which do not favor one peer over another. The most widely known consensus algorithm, which is implemented in Bitcoin, is called proof-of-work (PoW) mining and is based on solving a mathematically demanding puzzle with dynamically adjustable complexities (Yuan and Wang, 2018). During the evolution phase of Bitcoin, which saw a soaring exchange rate, miners invested more and more resources and PoW became notorious for its excessive use of energy. It is noteworthy, however, that PoW is only one out of a multitude of potential consensus algorithms used for permissionless networks, and various alternatives exist (e.g., proof-of-stake (PoS), which can be used in a hybrid form together with PoW; Byzantine fault tolerance-based consensus; crash fault tolerance-based consensus) (Nguyen and Kim, 2018). Summarizing, the Blockchain can lead either to the consolidation of existing or the creation of new power structures.
Finally, the Blockchain enables the distribution of trust, such that it does not necessitate high levels of confidence in single authorities. Greiner and Wang (2015) introduced the notion of trust-free systems which use the Blockchain to create a verified, immutable, and available record of transactions that is governed by the system itself. However, as Hawlitschek et al. (2018) point out, the conceptualization of trust depends on the context, which is in their study the sharing industry, and will depend on creating trusted interfaces. However, the potential elimination of existing relationships and the emergence of an economy that is controlled by automatically executed processes is not without dispute, as the disappearance of personal relationships might lead to undesirable consequences.
I do not list all of the characteristics of the Blockchain mentioned in the (gray and academic) literature, such as the data being chronological, time-stamped, and cryptographically sealed (Deloitte., 2017), since those are usually means to an end. However, such characteristics should also be discussed in case studies if they represent an important factor in the respective research project. I recommend that every case study contains some reflection on why the respective characteristics of that particular Blockchain configuration were chosen from among the alternatives, why they were important, how they were applied, and what (un)intended consequences arose from their application.
The substantial interest surrounding the Blockchain has been fueled by the great variety of possible use cases and its potential applicability in many industries (Tapscott and Tapscott, 2016). However, actual implementations must be assimilated within existing complex social, economic, institutional, regulatory and physical systems (Lacity and Willcocks, 2018), which can generate the numerous practical problems of implementation shown in Table 3.
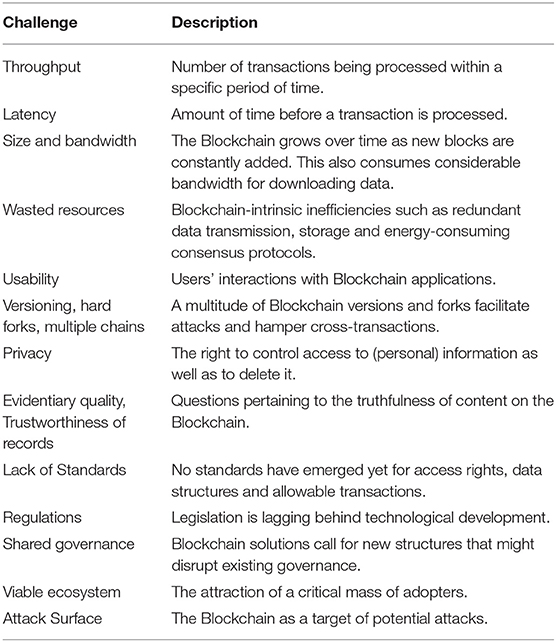
Table 3. Blockchain challenges (Swan, 2015; Lemieux, 2016; Kshetri, 2017; Lacity, 2018b; Saad et al., 2019).
Swan (2015) lists various technical challenges, such as throughput, which determine the scalability of the Blockchain solution. This is mostly an issue for public Blockchains that depend on an elaborate consensus mechanism between peers. The Bitcoin network with a theoretical maximum of 7 transactions per second (tps) lags far behind the processing power of VISA (2,000 tps), Twitter (5,000 tps) and advertising networks (>100,000 tps). A performance analysis of Hyperledger Fabric and Ethereum, two popular Blockchain platforms, showed that the former consistently outperformed the latter, but the authors still conclude that “both platforms are still not competitive with current database systems in term of performances in high workload scenarios” (Pongnumkul et al., 2017, p. 1). Another related issue is latency, the processing time for a transaction in a network, which, in the case of Bitcoin, amounts to 10 min. This processing time has been chosen on purpose to avoid chain splits, and will not be reduced in the future. Furthermore, in order to increase security it is recommended to wait for several confirmed transactions, which further increases latency (Swan, 2015). Again, the situation might look quite different for permissioned networks that are less prone to threats such as double-spending attacks due to deliberately chosen validators. Further challenges include the ever-increasing size of Blockchains, which consumes a considerable amount of bandwidth due to redundancies in data storage and transfer, and which constitutes a waste of resources, which is most obvious in the case of the PoW consensus mechanism that essentially trades energy for security. The proliferation of different Blockchains furthermore leads to an increasingly complex and hard to use infrastructure that hampers communication between chains and facilitates attacks on smaller chains.
Privacy and the Blockchain is a complex issue which arises mainly due to the immutability of data on the Blockchain. The situation is especially complex for personal data relating to an identified or identifiable natural person. The European Union's General Data Privacy Regulation (GDPR), which took effect on May 25, 2018, provides a set of regulations to ensure that individuals within the EU and those that conduct transactions within the EU can guarantee the protection of individual data. The GDPR, however, was written with a centralized entity in mind that has the power to control access rights, which is not case when Blockchain technology is used. It is thus unclear how Blockchain technology will comport with the GDPR (Posadas, 2018). However, as Kshetri (2017) points out, the Blockchain also bears the potential to strengthen cybersecurity and privacy by deterring cybercriminals and unauthorized data manipulators. Additionally, it offers the possibility of allowing individuals to control their own private data. It does not, however, guarantee the reliability of information and has limitations as a solution for keeping trustworthy digital records (Lemieux, 2016).
Lacity (2018b) lists various managerial challenges that include the specification of standards for access rights, data structures, and allowable transactions. Furthermore, she points out that current legislation lags behind technological developments, which creates insecurity on the side of organizations. A largely unexplored area is the need for new organizational structures that are able to cope with the idiosyncrasies of the Blockchain (see also Treiblmaier, 2018). Additionally, a major success factor of any technological solution is the attraction of a critical mass of adopters beyond the core originators, which is currently unclear for many Blockchain solutions that are still in an embryonic stage.
Finally, it must not be forgotten that the Blockchain is a potential target for manifold attacks. Just because the current cryptographic system and the chain of transactions in Bitcoin have so far withstood external attacks does not mean that Blockchain systems in general are resistant to all kinds of attacks. Saad et al. (2019) differentiate between three different attack areas, namely cryptographic constructs, the distributed architecture of the system, and the application context. They discuss a variety of potential attacks, including Blockchain forks, stale blocks and orphaned blocks, selfish mining, the 51% attack, DNS (domain name system) attacks, distributed denial of service attacks, consensus delays, Blockchain ingestion, double spending, and wallet theft.
A comparison between Tables 2, 3 reveals various challenges (which might turn into serious problems during implementation or runtime) that are inextricably linked to the basic characteristics of the Blockchain. For example, conflicting goals such as creating publicly available solutions that guarantee security and privacy pose major technological, legal and organizational challenges. The same holds true if legal regulations demand the removal of data upon request, which contradicts immutability as a basic characteristic of the Blockchain. These are just some examples out of many potential areas of conflict that need to be carefully documented in case studies.
In his seminal book on case study research, Yin (2014) gives a 2- fold definition for case studies in which he differentiates between scope and features. More specifically, he defines a case study as “an empirical inquiry that investigates a contemporal phenomenon (the ‘case') in depth and within its real-world context, especially when the boundaries between phenomenon and context may not be clearly evident” (p. 16). Since the phenomenon and the context are sometimes hard to distinguish, the features of a case also need to be considered (p. 17): “a case study inquiry copes with the technically distinctive situation in which there will be many more variables of interest than data points, and as one result relies on multiple sources of evidence, with data needing to converge in a triangulating fashion, and as another result benefits from the prior development of theoretical propositions to guide data collection and analysis.” Yin explicitly differentiates between rigorous case studies and teaching cases, with the latter having less strict formal requirements.
Burns (2000, p. 459) laments that “the case study has unfortunately been used as a ‘catch – all' category for anything that does not fit into experimental, survey, or historical methods.” Much too often, case study research is reduced to being exclusively exploratory without having a proper methodological foundation. As a potential solution, Ridder (2017) presents a comprehensive and differentiated perspective and introduces a portfolio approach in which he presents four case study research designs, each of which exhibits different strengths. These designs, labeled “no theory first”, “gaps and holes,” “social construction of theory” and “anomalies,” provide different contributions for building, developing and testing theory, and are discussed in more detail in the following section.
Case studies have a long tradition in IS. Benbasat et al. (1987) introduce case study research as a viable alternative to quantitative techniques that offers several advantages, such as independence from large samples sizes or distributional assumptions, as well as the potential of case studies to analyze a phenomenon within its context (i.e., an idiographic research strategy). Lee (1989) presents a scientific methodology for case studies and identifies four major problems, namely making controlled observations, making controlled deductions, allowing for replicability, and allowing for generalizability. He then describes how the alleged shortcomings of case studies can be overcome by using “natural controls” (e.g., by observing one person in varying, naturally occurring external situations), using logical reasoning for making deductions, adapting predictions while keeping the same theory and, finally, replicating case studies in different settings to ensure their generalizability. Lee furthermore suggests four considerations that can be used for a general assessment: (1) Does the case study consider any predictions through which the theory can be disproven?; (2) Are all the predictions internally consistent?; (3) Does the case study corroborate the theory through empirical testing?; and (4) Does the case study eliminate rival theories?
Cavaye (1996) investigates case study research in IS and concludes that “case study research can be used in the positivist and interpretivist traditions, for testing and building theory, with a single or multiple case study design, using qualitative or mixed methods” (p. 227). Dubé and Paré (2003) focused on rigor in information systems positivist case research by investigating contemporaneous practices. They identified and coded 183 case articles from seven major IS journals and concluded “that while modest progress has been made with respect to some specific attributes or criteria, the findings are somewhat disappointing and there are still significant areas for improvement” (p. 620). They especially lament the fact that descriptive case studies lag far behind explanatory and exploratory studies with respect to several attributes. The core of their paper comprises detailed recommendations on how to improve case study research designs, which include the use of clear research questions, a priori specification of constructions, discussion of theory and units of analysis, description of the study context and roles of investigators, elucidation of the data collection process, use of multiple data collection methods, data triangulation, clarification of the data analysis process, use of field notes, empirical testing, application of cross-case patterns, and a comparison with extant literature.
Wynn and Williams (2012) introduce principles for case study research from a critical realist perspective. They derive their principles directly from ontological (e.g., independent reality, open systems) and epistemological (e.g., mediated knowledge, unobservability of mechanisms) assumptions of critical realism and propose five methodological principles, namely the explication of events, explication of structure and content, retroduction, empirical corroboration, and triangulation, as well as the use of multiple methods.
A completely different approach is proposed by Avison et al. (2017): the French New Novel tradition. They argue that this style presents the richness of the problem situation and leaves it up to the reader to discover meaning from the narrative. As such, their approach does not provide specific guidelines and the authors themselves state that “there is no consensus on the techniques required to develop a narrative of this genre” (p. 267). However, they also provide a detailed analysis as to how this approach can be simultaneously demanding as well as inspiring, and might provide an antidote to publications that blindly follow a “formula.” In a similar vein, my intention in this paper is not to favor a particular style or technique, but rather to illustrate the full range of available possibilities. Understanding different types of case studies thus presents an ideal starting point.
As indicated in the previous section, case study research is a far wider-ranging and more powerful approach than many researchers might realize. Ridder (2017) presents a comprehensive typology that is based on the seminal work of four authors, namely Eisenhardt (1989) (no theory first, NTF), Yin (2014) (gaps and holes, GAH), Stake (1995) (social construction of reality, SCR), and Burawoy (2009) (anomalies, ANO). In Table 4 I highlight the main features of the respective approaches. A more detailed comparison can be found in Ridder (2017).
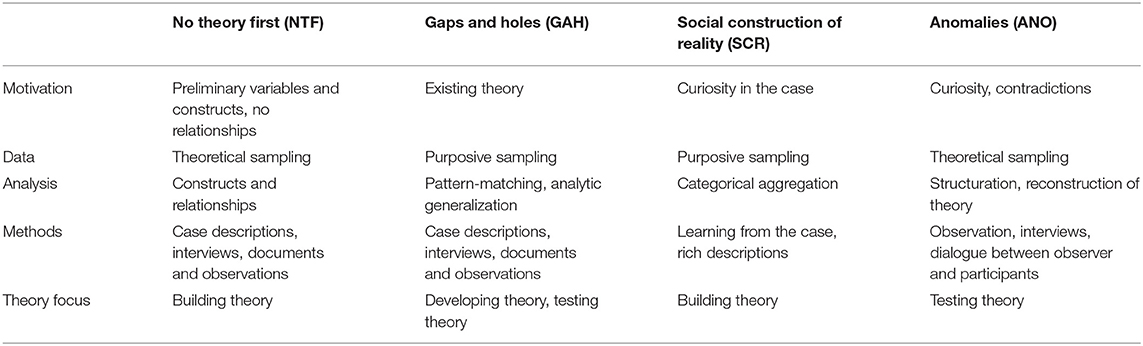
Table 4. Case study research designs and their theoretical contributions (cf. Ridder, 2017).
The general motivation for a specific case study distinguishes the four academic approaches. Whereas, an NTF study starts with a couple of preliminary variables and constructs, but no assumed relationships, the research question in GAH is based on existing theory and strives to answer “how and why” questions. The main driving force behind SCR is the researchers' curiosity to understand a particular phenomenon, while an ANO case study specifically investigates why a specific situation cannot be explained by existing theory. Data collection also differs based on the design. Purposive sampling, which is used in GAH as well as SCR, chooses members of a population for inclusion in a study based on the researchers' judgment. The sampling approach in GAH is highly dependent on the goal of the case study, which might suggest the selection of extreme or unusual cases as well as common or revelatory cases. In SCR the case is either of general interest or may help to better understand a theoretical issue. Theoretical sampling is a variation of purposive sampling with a stronger focus on identifying important theoretical constructs and their relationships (Ridder, 2017).
As far as data analysis is concerned, the focus of NTF lies on the identification of emerging constructs within the case or between cases. GAH, in which a tentative theory exists, focuses on the correspondence between the researchers' framework or propositions and the data. The goal of SCR is to learn from the case and to come up with a categorical aggregation. Finally, data is also aggregated in an ANO study with a focus of theory reconstruction. In each study type, the methodological approach closely follows the intended research goal. In NTF, interviews, documents and observations can be used to discover relevant constructs and relationships. Similarly, a GAH approach relies on the confrontation of existing theory-based constructs and relationships with case descriptions resulting from interviews, documents and observations. In order to understand construct reality, a rich description of a particular case is completed in SCR, while an ANO approach relies on observation, interviews and dialogue between observer and participants to better understand why existing theoretical explanations have failed (Ridder, 2017).
Eisenhardt and Graebner (2007), p. 30 point out that “Theory building from case studies is an increasingly popular and relevant research strategy,” which is closest aligned with the NTF approach. Similarly, SCR strives to build theory from the rich descriptions gained during the analysis process, while the focus of GAH is more on developing and testing theory, and the goal of ANO is to test theory by emphasizing contradictions between existing theory and reality.
Case study researchers also have a substantial amount of freedom as far as the mode of argumentation is concerned. Dubois and Gadde (2002) highlight the different strengths of deductive, inductive and abductive approaches. Deduction works best for developing propositions from current theory and making them testable, induction strives to systematically generate theory from data, and abduction can be used for the discovery of new variables and relationships.
It is a salient feature of the Blockchain that its characteristics allow for the creation of a multitude of (potential) use cases (Tapscott and Tapscott, 2016; Dieterich et al., 2017; Morabito, 2017; White, 2017; Lacity, 2018a; Leonard and Treiblmaier, 2019; Treiblmaier and Umlauff, 2019): cryptocurrencies, examples for smart contracts, crowdfunding, prediction markets, energy markets, smart property, settlements, processing, authenticity, traceability of products along the supply chain and visibility in data exchange, trade financing, international payments, know your customer (KYC), identity management, provenance, property, ownership, rights management, governance, digital certificates, digital identity, digital asset registry, escrow transfers, electronic voting, verified corporate due diligence, verified customer reviews, performance management systems, betting, tokenized incentive economies, digital rights, derivates markets, remittances, sustainability. This non-exhaustive list of use cases illustrates the potential of the Blockchain to transform organizations and their relationships. A comprehensive description of the respective use case is at the core of every case study and determines the methods being chosen.
In order to identify existing Blockchain case studies, I followed the guidelines for systematic literature reviews as suggested by Tranfield et al. (2003) and Watson (2015) and applied in Ngai et al. (2008) as well as (Ngai and Gunasekaran, 2007). performed a database search using the terms “Blockchain” or “Distributed Ledger Technology (DLT),” in any combination with “case study,” “use case” or “case.” The databases I used were Business Source Premier from EBSCOhost and ScienceDirect as well as publicly available information on Google Scholar and ResearchGate. Furthermore, I screened the references of the selected publications to identify further papers of relevance. During the identification and selection process, it turned out that it was difficult to differentiate between full-fledged case studies and the documentation of single use cases, since many use cases were performed in close cooperation with the industry and embedded within more comprehensive projects. Furthermore, the term “case study” is frequently used for any kind of report in which project findings are reported, regardless of whether a rigorous approach was applied.
To select existing Blockchain cases studies, I decided to use as a relevant criterion the development or thorough discussion of (a) a prototype or an application, (b) a solution for a specific company, or (c) a solution for a particular industry. I did not include any white papers, which are frequently used by so-called ICOs (initial coin offerings) to promote their product and occasionally also refer to use cases. Table 5 lists the case studies that fulfill those selection criteria. I describe the methodological approach used in each case and the degree to which each study fulfills my recommendations for Blockchain case study research: the description of relevant Blockchain characteristics (cf. Table 2), the description of potential challenges that needed to be overcome (cf. Table 3), the research design with a focus on the underlying theoretical approach (cf. Table 4), and an evaluation of the outcome.
It turned out that Blockchain case studies are highly fragmented. Hardly any of them apply the suggested procedures for case studies that can be found in the academic literature. For example, I found only two case studies explicitly referring to theory. One is from Albrecht et al. (2018), who apply Diffusion of Innovations theory, the Technology-Organization-Environment framework and institutional economics to investigate Blockchain use cases in the energy sector. The other one is from (Pazaitis et al., 2017), who build their study about the Blockchain and value systems in the sharing economy on the theory of value. Nonetheless, all of the case studies provide some insight on topics of interest to the industry and from which some insights can be drawn.
Figure 1 presents a framework illustrating how Blockchain use cases, case study research, the creation of artifacts and the creation, development and testing of theory are connected. The starting point is a specific phenomenon, most likely an envisioned Blockchain use case as listed above, embedded in its real-world context. In a first step, a careful preparation of the case is needed, in which it is crucial to outline the design of the study, including the motivation for applying Blockchain technology, data sources and the context. As is shown in this paper, case study research is a fairly flexible and multifaceted research approach that accommodates different methodological designs, but I still recommend to explicitly outline the basic structure and the goals of the project and how they influence the choice of methods. A crucial part of any Blockchain case study is the description of the relevant Blockchain characteristics (as shown in Table 2) and how they potentially contribute to the solution for a specific problem.
After outlining the justification for why a Blockchain-based approach is used, there are two basic streams of research, which can be differentiated by their goals of either focusing on theory or creating an artifact. Yin (2014) writes that “some theory development as part of the design phase is highly desired” (p. 37), but, as was shown above, alternative academic case study designs exist (Ridder, 2017), or researchers may decide to create a teaching or industry case. If the focus is on the creation of theory, analytic generalization is applied, which is a two-step process that involves the illustration of how the findings of a case study bear upon a particular theory, theoretical construct, or theoretical sequence of events as well as the application of the same theory to implicate similar situations (Yin, 2010). If the goal is the creation of an artifact, practical recommendations are needed which enable replication studies to track and trace the design, development and implementation process.
Theory-oriented research aims at theoretical implications for further use cases, but does not necessarily preclude the creation of a design science artifact. In a frequently cited case study, Markus (1983) reports on the implementation of a financial information system, but also applies and evaluates three different theories of resistance in the same study. She thus illustrates how a theoretical perspective can actually help in the solution of a practical problem. The generation of a design science artifact, which in the case of Blockchain might be a prototype, a full-fledged application or the implementation of a smart contract, has practical implications for the final evaluation of the use case. Either the original goal is achieved—(“success story”),—which calls for further replication studies in different scenarios, or the deviation from the originally specified project goals necessitates several modifications. Failures should therefore be documented, which is something that rarely happens in the industry, but should be a hallmark of academic research. It has to be noted, however, that design science research does not have to exclusively focus on design artifacts. As Baskerville et al. (2018) highlight, design theorizing is an expected norm in design science research, which implies that there is “some reflection on the advance in design knowledge that is being made” (p. 363).
A careful documentation of the deviations between initial expectations and concrete implementations is highly beneficial for future related studies. In the case of the Blockchain those experiences are especially important since, for example, the engineering process for smart contracts needs to be designed to account for the immutability of the Blockchain (Sillaber et al., 2018). Other than in traditional software design, Blockchain-oriented design needs to prepare for all contingencies already during the conceptualization phase of a project. Currently there is a lack of research that evaluates the extent to which this is possible. The goal of the framework shown in Figure 1 is to give a rough overview of how case studies and their related methodological and epistemological approaches can be connected.
The checklist in Table 6, which is loosely based on recommendations for systematic reviews from Moher et al. (2009), includes various sections (topics) to be included and discussed in a Blockchain case study. The actual structure clearly depends on the chosen design (e.g., research case, teaching case, industry case), but several principles might equally apply for different designs. As is the case in any academic paper, the abstract should highlight the major findings of the study in a nutshell, and will not be discussed any further herein.
In order to put a case study into context, researchers initially need to clearly outline the goal(s) of the project, as well as the justification for applying a Blockchain-based solution in this specific setting. Ideally, similar cases from the literature are considered. Defining and describing the type of Blockchain being evaluated and/or deployed (cf. Table 1) as well as the organizational context of the study is crucial to examining the fit between them. This includes all conditions and circumstances that are of relevance for the project, including internal and external driving forces as well as existing organizational structures and top management support. Numerous decision trees can be found in the literature that scrutinize the general applicability of the Blockchain. A recent white paper from the World Economic Forum (2018, p. 6) summarizes decisive filter questions that help organizations to identify those scenarios in which a Blockchain application may not be appropriate. Most importantly, these scenarios include settings in which there are no intermediaries or brokers that need to be removed, no digital assets are used, and no permanent authoritative record of a digital asset can be created. For a comprehensive description of a Blockchain project at a conceptual stage, Feig (2018) recommends asking the following ten questions: (1) Who are the users?, (2) What data do users input?, (3) Are any inputs irreversible?, (4) Who are the peers?, (5) How do peers create blocks?, (6) What do peers validate?, (7) How do peers validate?, (8) How do peers reach consensus?, (9) Is the Blockchain immutable?, and (10) How are peers incentivized? In short, the first part of any Blockchain case study must lay the foundation for the rest of the paper by pinpointing the organizational setting as well as the technology and its intended purpose. Researchers especially need to document how they apply the respective characteristics of the Blockchain (cf. Table 2) and how they tackle the major challenges that arise during an implementation (cf. Table 3). Both industry and academia are at an early stage of Blockchain development and the careful description and documentation of case studies can help the industry to build on previous success stories and avoid pitfalls.
Subsequently, the methodology of the project needs to be introduced and explained, which differs significantly based on the role of theory. If the research is explicitly theory-focused, the four different designs shown in Table 4—NTF, GAH, SCR, and ANO—need to be described in detail. The respective selection obviously impacts the choice of methods and data sources as well as the interpretation of the findings. If the focus is more on the creation of artifacts, the traceability and documentation of the case are paramount. However, this does not preclude theorizing, which can be done in an “interior mode” (i.e., producing theory for design and action) and an “exterior mode” (theorizing about artifacts in use) (Baskerville et al., 2018). A comprehensive documentation of the data collection process is needed for all types of cases studies, while an in-depth description of the variables, which might include latent constructs, and their respective relationships is especially important for theory-related Blockchain studies. Independent of the type of case study, a certain amount of rigor is needed for the research design as well as for data collection and analysis processes (Darke et al., 1998).
The presentation of the Blockchain results, again, heavily depends on the chosen design, but I recommend the inclusion of an additional discussion on how the characteristics of the Blockchain (cf. Table 2) were applied and how the Blockchain challenges (cf. Table 3) were overcome. Depending on the overall goal of the case study, it might be useful to detail various business processes or the development of smart contracts which deviate from previous software engineering approaches. Sillaber et al. (2018) suggest an elaborated engineering process which takes into account the immutability of smart contracts and is not based on the traditional waterfall model, but rather details the following phases: conceptualization, implementation, approval, submission, execution, and finalization. Elaborating on these stages helps readers of Blockchain case studies to reproduce the development and deployment of smart contracts.
The discussion summarizes the main findings and their relevance for major stakeholders. Additionally, a comparison with previous research is advisable, which especially includes the identification and description of “surprising” results. Lacity (2018a, p. 48) suggests structuring Blockchain applications around four major components: (1) the application interface or access point (e.g., digital asset exchange, digital wallet, bridge/gateway services, interfaces with existing systems, IoT devices), (2) use cases (e.g., track & trace, payments, voting), (3) code bases (e.g., Hyperledger Fabric, Ethereum, Corda, Multichain), and (4) Blockchain protocols (i.e., specific rules regarding access and how transactions are structured, addressed, transmitted, routed, validated, sequenced, secured, and added to the permanent record). Her framework provides a possible structure to systematically discuss the findings.
In order to provide a comprehensive quality assessment, Yin (2014), p. 45) suggests an evaluation of construct validity, internal validity, external validity, and reliability. This is especially crucial for studies that build on previous research, develop and test theory, or strive to create a new research agenda. Given that the Blockchain is an evolving technology, a thorough analysis of limitations in light of the original research goals will help to critically shed light on its possibilities. As I have already noted above, the careful documentation and analysis of unsuccessful projects will also benefit future Blockchain endeavors. Carefully drafted conclusions and implications, which extend previous research, will further help to build a comprehensive Blockchain research agenda. Finally, if applicable, funding sources and the role of funders have to be specified.
In this paper I summarize key principles of various types of case study research and propose guidelines on how to design, conduct, and report Blockchain case studies. However, the structure I provide in this paper, along with suggestions on how to incorporate theory and ensure validity, is not meant as an exhaustive checklist to be used by reviewers in order to assess the overall quality of a publication. In other words, it should not be the case that the guidelines “become more important than the study” (Holtkamp et al., 2019) or that the paper is “written according to a ‘formula”' (Avison et al., 2017, p. 271). Instead, I concur with Klein and Myers (1999), p. 78) who write “while we believe that none of our principles should be left out arbitrarily, researchers need to work out themselves how (and which of) the principles apply in any particular situation.” I therefore believe that researchers will benefit most from this paper by consulting it prior to designing their study and selecting those parts that they deem useful for their specific research goals.
In a nutshell, I recommend that researchers
• provide a rationale for the use of Blockchain technology,
• define the type of Blockchain they use,
• describe the Blockchain characteristics that are relevant for their study and how they are implemented,
• discuss the Blockchain challenges encountered during the case study and how they influenced the outcome,
• justify the chosen case study type,
• outline the respective case study methodology,
• present and discuss the results appropriately for the specific case study type,
• provide a critical evaluation of their results,
• embed their results into a broader context, thus enabling incremental research.
Case study research provides a lot of freedom for academics and allows for the combination of various theoretical and practical approaches. By carefully designing their studies, researchers can ensure that they get the most out of this versatile approach. Blockchain technology is currently in its infancy and case study research provides many useful tools to systematically generate knowledge on which future research can build, be it theory-based or practically oriented. The recommendations I present in this paper are intended to enable such an incremental research agenda and I hope that many researchers will find them useful. Future research can easily adapt my recommendations to the investigation of other disruptive technologies.
The author confirms being the sole contributor of this work and has approved it for publication.
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Alabi, K. (2017). Digital blockchain networks appear to be following Metcalfe's Law. Electro. Commerce Res. Appli. 24, 23–29. doi: 10.1016/j.elerap.2017.06.003
Albrecht, S., Reichert, S., Schmid, J., Strüker, J., Neumann, D., and Fridgen, G. (2018). “Dynamics of blockchain implementation—A case study from the energy sector,” in Proceedings of the 51st Hawaii International Conference on System Sciences (Hawaii, USA).
Angrish, A., Craver, B., Hasan, M., and Starly, B. (2018). A case study for Blockchain in manufacturing: “FabRec”: A prototype for peer-to-peer network of manufacturing nodes. Procedia Manufact. 26, 1180–1192. doi: 10.1016/j.promfg.2018.07.154
Auricchio, A., Fontela, B., Goel, A., He, Y., Jungmair, C., and Roa, A. (2017). Ryanair: Impact of Blockchain on the Organizational Design of Ryanair, Report. Available online at: https://de.slideshare.net/AntonioAuricchio/the-impact-of-blockchain-on-ryanairs-dynamic-prices (accessed July 14, 2018).
Avison, D., Malaurent, J., and Eynaud, P. (2017). A narrative approach to publishing information systems research: inspiration from the French New Novel tradition. Eur. J. Inform. Syst. 26, 260–273 doi: 10.1057/s41303-016-0022-1
Baskerville, R., Baiyere, A., Gregor, S., Hevner, A., and Rossi, M. (2018). Design science research contributions: finding a balance between artifact and theory. J. Assoc. Inform. Syst. 19, 358–376. doi: 10.17705/1jais.00495
Beck, R., Avital, M., Rossi, M., and Thatcher, J. B. (2017). Blockchain technology in business and information systems research. Business Inform. Syst. Eng. 59, 381–384. doi: 10.1007/s12599-017-0505-1
Benbasat, I., Goldstein, D. K., and Mead, M. (1987). The case research strategy in studies of information systems. MIS Q. 11, 369–386. doi: 10.2307/248684
Biswas, K., Muthukkumarasamy, V., and Tan, W. L. (2017). “Blockchain based wine supply chain traceability system,” in Proceedings of the Future Technologies Conference (Vancouver).
Burawoy, M. (2009). The Extended Case Method. Four Countries, Four Decades, Four Great Transformations, and One Theoretical Tradition. Berkeley: University of California Press.
Cavaye, A. L. M. (1996). Case study research: a multifaceted research approach for IS. Inform. Syst. J. 6, 227–242. doi: 10.1111/j.1365-2575.1996.tb00015.x
Darke, P., Shanks, G., and Broadbent, M. (1998). Successfully completing case study research: combining rigour, relevance and pragmatism. Inform. Syst. J. 8, 273–289. doi: 10.1046/j.1365-2575.1998.00040.x
Deloitte. (2017). Key Characteristics of the Blockchain. Deloitte Touche Tohmatsu India LLP. Avaialble online at: https://www2.deloitte.com/content/dam/Deloitte/in/Documents/industries/in-convergence-blockchain-key-characteristics-noexp.pdf (accessed October 1, 2018).
Dieterich, V., Ivanovic, M., Meier, T., Zäpfel, S., Utz, M., and Sandner, P. (2017). Application of Blockchain Technology in the Manufacturing Industry. Working Paper, Frankfurt School Blockchain Center.
Dubé, L., and Paré, G. (2003). Rigor in information systems positivist case research: current practices, trends, and recommendations. MIS Q. 27, 597–635. doi: 10.2307/30036550
Dubois, A., and Gadde, L. (2002). Systematic combining: an abductive approach to case research. J. Business Res. 55, 553–560. doi: 10.1016/S0148-2963(00)00195-8
Eisenhardt, K., and Graebner, M. E. (2007). Theory building from cases: Opportunities and challenges. Acad. Manage. J. 50, 25–32. doi: 10.5465/amj.2007.24160888
Eisenhardt, K. M. (1989). Building theories from case study research. Acad. Manag. Rev. 14, 532–550. doi: 10.5465/amr.1989.4308385
Feig, E. (2018). A Framework for Blockchain-Based Applications. Available online at: https://arxiv.org/abs/1803.00892
Glaser, B., and Strauss, A. L. (1967). The Discovery of Grounded Theory: Strategies for Qualitative Research. Chicago: Aldine Publishing Company.
Government Office for Science. (2016). Distributed Ledger Technology: Beyond Block Chain. A report by the UK government chief scientific advisor. London: Government Office for Science.
Gräther, W., Kolvenbach, S., Ruland, R., Schütte, J., Torres, C. F., and Wendland, F. (2018). “Blockchain for education: lifelong learning passport,” in Proceedings of the 1st ERCIM Blockchain Workshop 2018, Reports of the European Society for Socially Embedded Technologies, eds W. Prinz and P. Hoschka (Amsterdam), 1–8.
Greiner, M., and Wang, H. (2015). “Trust-free systems - a new research and design direction to handle trust issues in p2p systems: the case of bitcoin,” in Proceedings of the Americas Conference on Information Systems.
Hawlitschek, F., Notheisen, B., and Teubner, T. (2018). The limits of trust-free systems: a literature review on blockchain technology and trust in the sharing economy. Electro. Commer. Res. Appl. 29, 50–63. doi: 10.1016/j.elerap.2018.03.005
Hoelscher, J. (2018). Taking the lead on Blockchain: as the technology behind Bitcoin finds new uses, internal auditors must assess how the risks may impact the organization. Internal Audi. 75, 19–21
Holotiuk, F., Pisani, F., and Moormann, J. (2018).“Unveiling the key challenges to achieve the breakthrough of Blockchain: Insights from the payments industry,” in Proceedings of the 51st Hawaii International Conference on System Sciences (Waikoloa), 3537–3546.
Holtkamp, P., Soliman, W., and Siponen, M. (2019).“Reconsidering the role of research method guidelines for qualitative, mixed-methods, and design science research,” in Proceedings of the 52nd Hawaii International Conference on System Sciences (Maui), 6280–6289.
Hsieh, H.-F., and Shannon, S. E. (2005). Three approaches to qualitative content analysis. Qualit. Health Res. 15, 1277–1288. doi: 10.1177/1049732305276687
Karamitsos, I., Papadaki, M., and Barghuthi, N. B. A. (2018). Design of the Blockchain smart contract: a use case for real estate. J. Inform. Secur. 9, 177–190. doi: 10.4236/jis.2018.93013
Khaqqi, K. N., Sikorski, J. J., Hadinoto, K., and Kraft, M. (2018). Incorporating seller/buyer reputation-based system in blockchain-enabled emission trading application. Appl. Energy 209, 8–19. doi: 10.1016/j.apenergy.2017.10.070
Kim, K., and Justl, J. M. (2018). Potential antitrust risks in the development and use of Blockchain. J. Tax. Regulat. Finan. Instit. 31, 5–16.
Klein, H. K., and Myers, M. D. (1999). A set of principles for conducting and evaluating interpretive field studies in information systems. MIS Q. 23, 67–94. doi: 10.2307/249410
Kshetri, N. (2017). Blockchain's roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 41, 1027–1038. doi: 10.1016/j.telpol.2017.09.003
Kshetri, N. (2018). Blockchain's roles in meeting key supply chain management objectives. Int. J. Inform. Manage. 39, 80–89. doi: 10.1016/j.ijinfomgt.2017.12.005
Lacity, M. (2018a). A Manager's Guide to Blockchain for Business: From Knowing What to Knowing How, Warwickshire, UK: SB Publishing.
Lacity, M. (2018b). Addressing key challenges to making enterprise Blockchain applications a reality, MIS Q. Execut. 17, 201–222.
Lacity, M. C., and Willcocks, L. P. (2018). Robotic Process and Cognitive Automation: The Next Phase, Steve Brooks Publishing.
Lee, A. S. (1989). A scientific methodology for MIS case studies. MIS Q. 13, 33–50. doi: 10.2307/248698
Lemieux, V. L. (2016). Trusting records: is blockchain technology the answer? Records Manag. J. 26, 110–139. doi: 10.1108/RMJ-12-2015-0042
Leonard, D., and Treiblmaier, H. (2019). “Can cryptocurrencies help to pave the way to a more sustainable economy? Questioning the economic growth paradigm,” in Business Transformation through Blockchain—Volume I, eds H. Treiblmaier and R. Beck (Cham: Palgrave Macmillan). doi: 10.1007/978-3-319-99058-3_7
Li, Z., Barenji, A. V., and Huang, G. Q. (2018). Toward a blockchain cloud manufacturing system as a peer to peer distributed network platform. Robot. Comput. Integ. Manufact. 54, 133–144. doi: 10.1016/j.rcim.2018.05.011
Lucena, P., Binotto, A. P. D., da Silva Momo, F., and Kim, H. (2018). “A case study for grain quality assurance tracking based on a Blockchain business network,” in Symposium on Foundations and Applications of Blockchain (FAB'18) (Los Angeles, USA).
MarketsandMarkets. (2017). Blockchain Market by Provider, Application (Payments, Exchanges, Smart Contracts, Documentation, Digital Identity, Supply Chain Management, and GRC Management), Organization size, Industry Vertical, and Region - Global Forecast to 2022. Market Report, MarketsandMarkets.com.
Markus, M. L. (1983). Power, politics, and MIS implementation. Commun. ACM 26, 430–444. doi: 10.1145/358141.358148
McConaghy, M., McMullen, G., Parry, G., McConaghy, T., and Holtzman, D. (2017). Visibility and digital art: blockchain as an ownership layer on the Internet. Strat. Change 26, 461–470. doi: 10.1002/jsc.2146
Meiklejohn, S., Pomarole, M., Jordan, G., Levchenko, K., McCoy, D., Voelker, G. M., et al. (2016). A fistful of Bitcoins: characterizing payments among men with no names. Commun. ACM 59, 86–93. doi: 10.1145/2896384
Mengelkamp, E., Gärttner, J., Rock, K., Kessler, S., Orsini, L., and Weinhardt, C. (2018). Designing microgrid energy markets. a case study: the brooklyn microgrid. Appl. Energy 210, 870–880. doi: 10.1016/j.apenergy.2017.06.054
Mik, E. (2017). Smart contracts: terminology, technical limitations and real world complexity. Law, Innovat. Technol. 9, 269–300. doi: 10.1080/17579961.2017.1378468
Moher, D., Liberati, A., Tetzlaff, J., and Altman, D. G. (2009). Preferred reporting items for systematic reviews and meta-analyses: the PRISMA statement. PLoS Med. 6:e1000097. doi: 10.1371/journal.pmed1000097
Mougayar, W. (2016). The Business Blockchain: Promise, Practice, and Application of the Next Internet Technology, Hoboken, NJ: Wiley.
Narayanan, J., and Clark, J. (2017). Bitcoin's academic pedigree: the concept of cryptocurrencies is built from forgotten ideas in the research literature. ACM Queue 15, 1–30.
Ngai, E. W. T., and Gunasekaran (2007). A review for mobile commerce research and applications. Decis. Supp. Syst. 43, 3–15. doi: 10.1016/j.dss.2005.05.003
Ngai, E. W. T., Moon, K. K. L., Riggins, F. J., and Yi, C. Y. (2008). RFID research: an academic literature review (1995-2005) and future research directions. Int. J. Prod. Econ. 112, 510–520. doi: 10.1016/j.ijpe.2007.05.004
Nguyen, G.-T., and Kim, K. (2018). A survey about consensus algorithms used in Blockchain. J. Inform. Process. Syst. 14, 101–128. doi: 10.3745/JIPS.01.0024
O'Dair, M., and Beaven, Z. (2017). The networked record industry: How blockchain technology could transform the record industry. Strat. Change 26, 471–480. doi: 10.1002/jsc.2147
Olsen, R., Battiston, S., Caldarelli, G., Golub, A., Nikulin, M., and Ivliev, S. (2018). Case study of Lykke exchange: architecture and outlook. J. Risk Fina. 19, 26–38. doi: 10.1108/JRF-12-2016-0168
Önder, I., and Treiblmaier, H. (2018). Blockchain and tourism: three research propositions. Ann. Tour. Res. 72:5. doi: 10.1016/j.annals.2018.03.005
Pazaitis, A., De Filippi, P., and Kostakis, V. (2017). Blockchain and value systems in the sharing economy: the illustrative case of Backfeed. Technol. Forecast. Social Change 125, 105–115. doi: 10.1016/j.techfore.2017.05.025
Peck, M. (2017). Reinforcing the Links of the Blockchain. IEEE Future Directions Initiative White Paper.
Pongnumkul, S., Siripanpornchana, C., and Thajchayapong, S. (2017). “Performance analysis of private Blockchain platforms in varying workloads,” in 26th International Conference on Computer Communication and Networks (ICCCN) (Vancouver).
Posadas, D. V. (2018). The internet of things: the GDPR and the Blockchain may be incompatible. J. Internet Law 21, 1–29.
Ridder, H.-G. (2017). The theory contribution of case study research designs. Business Res. 10, 281–305. doi: 10.1007/s40685-017-0045-z
Saad, M., Spaulding, J., Njilla, L., Kamhoua, C., Nyang, D.-H., and Mohaisen, A. (2019). “Overview of attack surfaces in Blockchain,” in Blockchain for Distributed System Security, eds S. S. Shetty, C. A. Kamhoua, and L. L. Njilla (Hoboken, NJ: Wiley-IEEE Press), 51–66.
Schueffel, P. (2017). Alternative distributed ledger technologies: blockchain vs. tangle vs. hashgraph - a high-level overview and comparison. SSRN Electro. J. 3144241, 1–8. doi: 10.2139/ssrn.3144241
Sikorski, J. J., Haughton, J., and Kraft, M. (2017). Blockchain technology in the chemical industry: machine-to-machine electricity market. Appl. Energy Elsevier 195, 234–246. doi: 10.1016/j.apenergy.2017.03.039
Sillaber, C., Gallersdörfer, U., Waltl, B., Felderer, M., and Treiblmaier, H. (2018). “Toward an integrated process model for smart contract engineering,”in Pre-ICIS Workshop on Blockchain and Smart Contract (San Francisco, USA), p. 82–86.
Strugar, D., Hussain, R., Mazzara, M., Rivera, V., Lee, J.-Y., and Mustafin, R. (2018). “On M2M micropayments: a case study of electric autonomous vehicles,” in IEEE International Conference on Blockchain (Blockchain-2018) (Halifax, NS).
Sullivan, C., and Burger, E. E. (2017). Residency and blockchain. Compu. Law Secur. Rev. 33, 470–481. doi: 10.1016/j.clsr.2017.03.016
Szabo, N. (1997). The Idea of Smart Contracts. Nick Szabo's papers and concise tutorials. Available online at: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/idea.html (accessed May 1, 2018).
Tapscott, D., and Tapscott, A. (2016). Blockchain Revolution: How the Technology behind Bitcoin is Changing Money, Business, and the World. New York, NY: Penguin.
Tranfield, D., Denyer, D., and Smart, P. (2003). Towards a methodology for developing evidence-informed management knowledge by means of systematic review. Br. J. Manage. 14, 207–222. doi: 10.1111/1467-8551.00375
Treiblmaier, H. (2018). The impact of the Blockchain on the supply chain: a theory-based research framework and a call for action. Supply Chain Manage. 23, 545–559. doi: 10.1108/SCM-01-2018-0029
Treiblmaier, H., and Beck, R. (2019a). Business Transformation Through Blockchain—Volume I. Cham: Palgrave Macmillan.
Treiblmaier, H., and Beck, R. (2019b). Business Transformation Through Blockchain – Volume II. Cham: Palgrave Macmillan.
Treiblmaier, H., and Umlauff, U. (2019). “Blockchain and the future of work: a self-determination theory approach,” in Blockchain Economics: Implications of Distributed Ledger Technology, eds M. Swan, J. Potts, S. Takagi, P. Tasca, and F. Witte (New Jersey, NJ), 105–124. doi: 10.1142/9781786346391_0006
Treiblmaier, H., and Zeinzinger, T. (2018). “Understanding the Blockchain through a gamified experience: a case study from Austria,” 25th European Conference on Information Systems (Portsmouth: UK).
Watson, R. T. (2015). Beyond being systematic in literature reviews in IS. J. Inform. Technol. 30, 185–187. doi: 10.1057/jit.2015.12
White, G. R. T. (2017). Future applications of blockchain in business and management: A Delphi Study. Strate. Change 26, 439–451. doi: 10.1002/jsc.2144
Wood, G. (2014). Ethereum: a secure decentralised generalised transaction ledger. Ethereum Project Yellow Paper, 1–32.
World Economic Forum (2018). Blockchain Beyond the Hype: A Practical Framework for Business Leaders, White Paper, World Economic Forum, Geneva: Switzerland.
Wynn, J. D., and Williams, C. K. (2012). Principles for conducting critical realist case study research in Information Systems. MIS Q. 36, 787–810. doi: 10.2307/41703481
Yin, R. (2010). “Analytic generalization,” in Encyclopedia of Case Study Research, eds J. Albert, G. Mills, and E. Wiebe (Thousand Oaks, CA: SAGE Publications, Inc.), 21–23.
Ying, W., Jia, S., and Du, W. (2018). Digital enablement of Blockchain: Evidence from HNA group, Int. J. Inform. Manag. 39, 1–4. doi: 10.1016/j.ijinfomgt.2017.10.004
Yli-Huumo, J., Ko, D., Choi, S., Park, S., and Smolander, K. (2016). Where is current research on blockchain technology? A systematic review. PLoSONE 11:0163477. doi: 10.1371/journal.pone.0163477
Yuan, Y., and Wang, F.-Y. (2018). Blockchain and cryptocurrencies: model, techniques, and applications. IEEE Trans. Syst. Man Cyber. 48, 1421–1428. doi: 10.1109/TSMC.2018.2854904
Keywords: blockchain, blockchain characteristics, distributed ledger technology, case study, use case, theory development, case study checklist, case study framework
Citation: Treiblmaier H (2019) Toward More Rigorous Blockchain Research: Recommendations for Writing Blockchain Case Studies. Front. Blockchain 2:3. doi: 10.3389/fbloc.2019.00003
Received: 06 February 2019; Accepted: 02 May 2019;
Published: 16 May 2019.
Edited by:
Victoria L. Lemieux, University of British Columbia, CanadaReviewed by:
Hrvoje Stancic, Faculty of Humanities and Social Sciences, University of Zagreb, CroatiaCopyright © 2019 Treiblmaier. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Horst Treiblmaier, SG9yc3QuVHJlaWJsbWFpZXJAbW9kdWwuYWMuYXQ=
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Research integrity at Frontiers

Learn more about the work of our research integrity team to safeguard the quality of each article we publish.